Integrate Physical Security and Information Security

Physical security is often managed by facilities, not by IT security, resulting in segmented security systems. Integrating physical and information security introduces challenges in:
- Understanding the value proposition of investment in governing and managing integrated systems, including migration costs, compared to separated security systems.
- Addressing complex risks and vulnerabilities of an integrated security system.
- Operationalizing enhanced capabilities created by adoption of emerging and disruptive technologies.
Our Advice
Critical Insight
- Integrate security in people, process, and technology to improve your overall security posture. Having siloed systems running security is not beneficial. Many organizations are realizing the benefits of consolidating into a single platform across physical security, cybersecurity, HR, legal, and compliance.
- Plan and engage stakeholders. Assemble the right team to ensure the success of your integrated security ecosystem, decide the governance model, and clearly define the roles and responsibilities.
- Enhance strategy and risk management. Strategically, we want a physical security system that is interoperable with most technologies, flexible with minimal customization, functional, and integrated, despite the challenges of proprietary configurations, complex customization, and silos.
Impact and Result
Info-Tech's approach is a modular, incremental, and repeatable process to integrate physical and information security to:
- Ensure the integration will meet the business' needs and determine effort and technical requirements.
- Establish GRC processes that include integrated risk management and compliance.
- Design and deploy an integrated security architecture.
- Establish security metrics of effectiveness and efficiency for senior management and leadership.
Integrate Physical Security and Information Security Research & Tools
Besides the small introduction, subscribers and consulting clients within this management domain have access to:
1. Integrate Physical Security and Information Security Storyboard – A step-by-step document that walks you through how to integrate physical security and information security.
Info-Tech provides a three-phased framework for integrating physical security and information security: Plan, Enhance, and Monitor & Optimize.
- Integrate Physical Security and Information Security Storyboard
2. Integrate Physical Security and Information Security Requirements Gathering Tool – A tool to map organizational goals to IT goals, facilities goals, OT goals (if applicable), and integrated security goals.
This tool serves as a repository for information about security integration elements, compliance, and other factors that will influence your integration of physical security and information security.
- Integrate Physical Security and Information Security Requirements Gathering Tool
3. Integrate Physical Security and Information Security RACI Chart Tool – A tool to identify and understand the owners of various security integration stakeholders across the organization.
Populating a RACI chart (Responsible, Accountable, Consulted, and Informed) is a critical step that will assist you in organizing roles for carrying out integration steps. Complete this tool to assign tasks to suitable roles.
- Integrate Physical Security and Information Security RACI Chart Tool
4. Integrate Physical Security and Information Security Communication Deck – A tool to present your findings in a prepopulated document that summarizes the work you have completed.
Complete this template to effectively communicate your integrated security plan to stakeholders.
- Integrate Physical Security and Information Security Communication Deck
Further reading
Integrate Physical Security and Information Security
Securing information security, physical security, or personnel security in silos may not secure much
Analyst Perspective
Ensure integrated security success with close and continual collaboration
From physical access control systems (PACS) such as electronic locks and fingerprint biometrics to video surveillance systems (VSS) such as IP cameras to perimeter intrusion detection and prevention to fire and life safety and beyond: physical security systems pose unique challenges to overall security. Additionally, digital transformation of physical security to the cloud and the convergence of operational technology (OT), internet of things (IoT), and industrial IoT (IIoT) increase both the volume and frequency of security threats.
These threats can be safety, such as the health impact when a gunfire attack downed wastewater pumps at Duke Energy Substation, North Carolina, US, in 2022. The threats can also be economic, such as theft of copper wire, or they can be reliability, such as when a sniper attack on Pacific Gas & Electric’s Metcalf Substation in California, US, damaged 17 out of 21 power transformers in 2013.
Considering the security risks organizations face, many are unifying physical, cyber, and information security systems to gain the long-term overall benefits a consolidated security strategy provides.

Ida Siahaan
Research Director, Security and Privacy Practice
Info-Tech Research Group
Executive Summary
Your ChallengePhysical security is often managed by facilities, not by IT security, resulting in segmented security systems. Meanwhile, integrating physical and information security introduces challenges in:
|
Common ObstaclesPhysical security systems integration is complex due to various components such as proprietary devices and protocols and hybrid systems of analog and digital technology. Thus, open architecture with comprehensive planning and design is important. However, territorial protection by existing IT and physical security managers may limit security visibility and hinder security integration. Additionally, integration poses challenges in staffing, training and awareness programs, and dependency on third-party technologies and their migration plans. |
Info-Tech's ApproachInfo-Tech’s approach is a modular, incremental, and repeatable process to integrate physical and information security that enables organizations to:
|
Info-Tech Insight
An integrated security architecture, including people, process, and technology, will improve your overall security posture. These benefits are leading many organizations to consolidate their siloed systems into a single platform across physical security, cybersecurity, HR, legal, and compliance.
Existing information security models are not comprehensive
Current security models do not cover all areas of security, especially if physical systems and personnel are involved and safety is also an important property required.
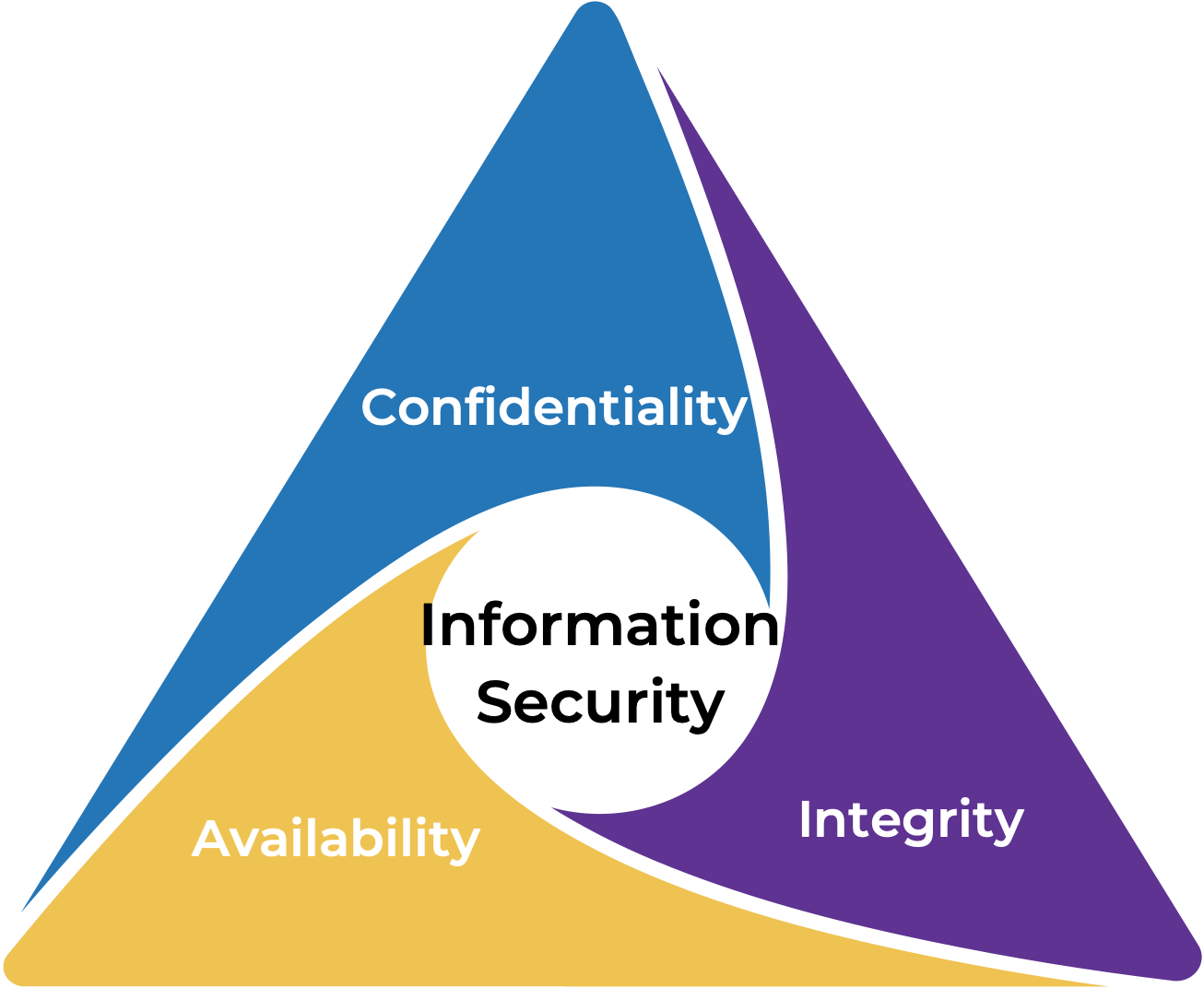
- The CIA triad (confidentiality, integrity, availability) is a well-known information security model that focuses on technical policies related to technology for protecting information assets.
- The US Government’s Five Pillars of Information Assurance includes CIA, authentication, and non-repudiation, but it does not cover people and processes comprehensively.
- The AAA model, created by the American Accounting Association, has properties of authentication, authorization, and accounting but focuses only on access control.
- Donn Parker expanded the CIA model with three more properties: possession, authenticity, and utility. This model, which includes people and processes, is known as the Parkerian hexad. However, it does not cover physical and personnel security.
CIA Triad
Parkerian Hexad
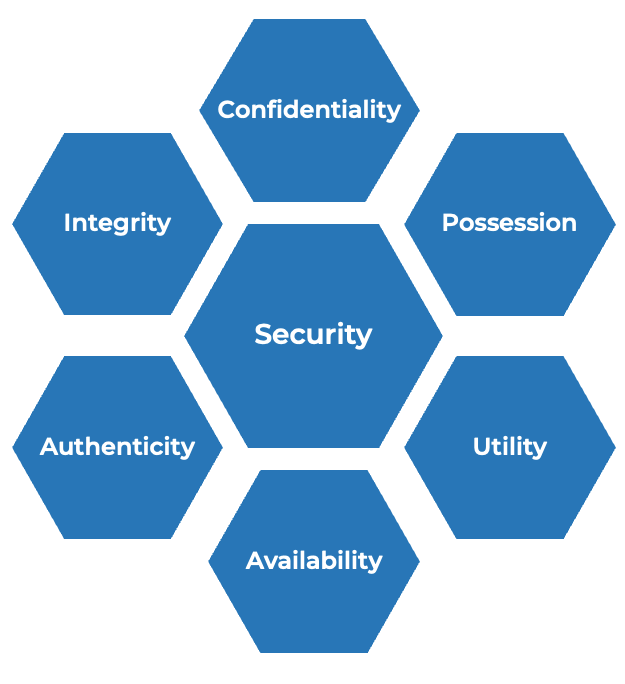
Sources: Parker, 1998; Pender-Bey, 2012; Cherdantseva and Hilton, 2015
Adopt an integrated security model
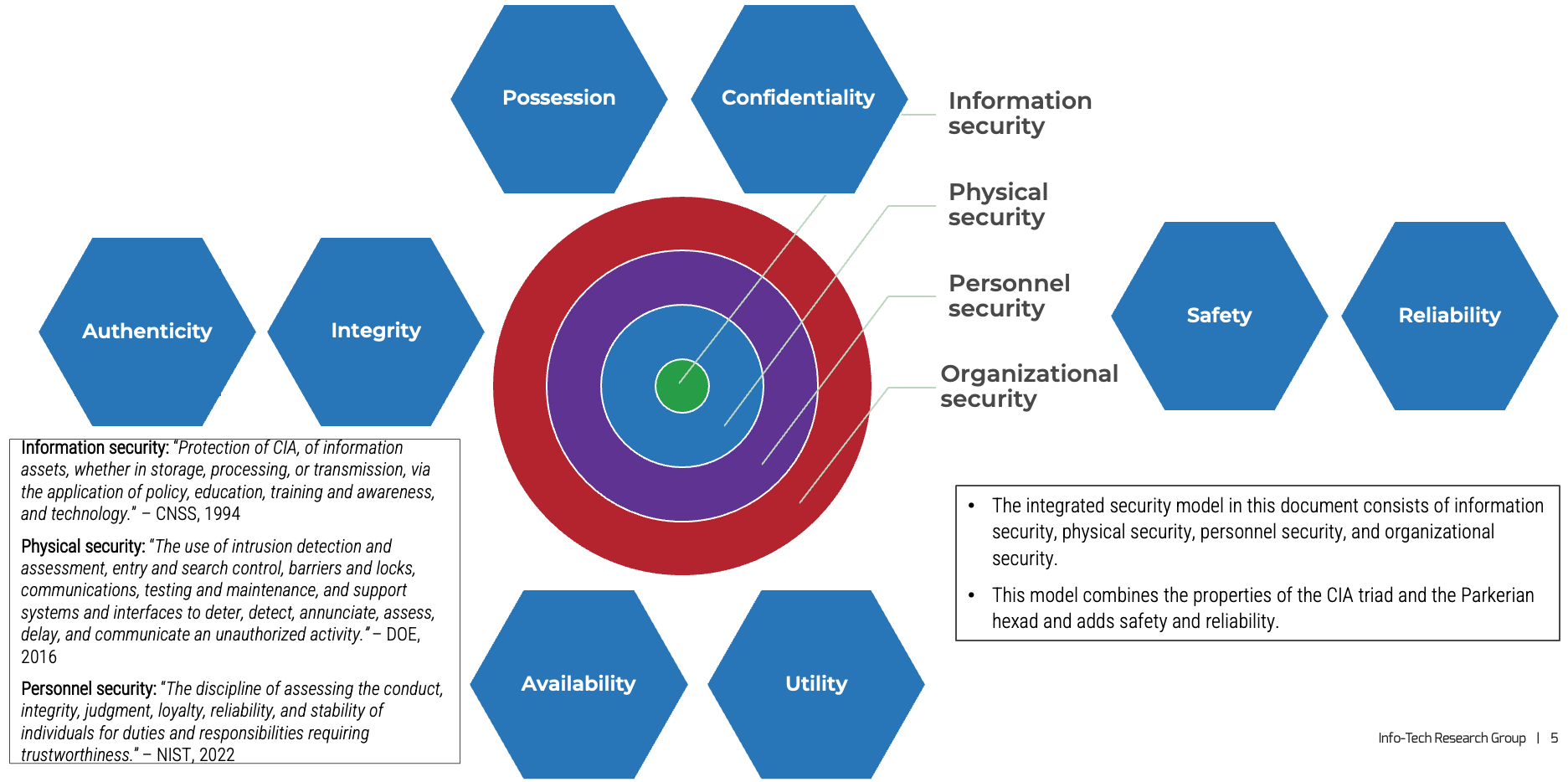
The security ecosystem is shifting from segregation to integration
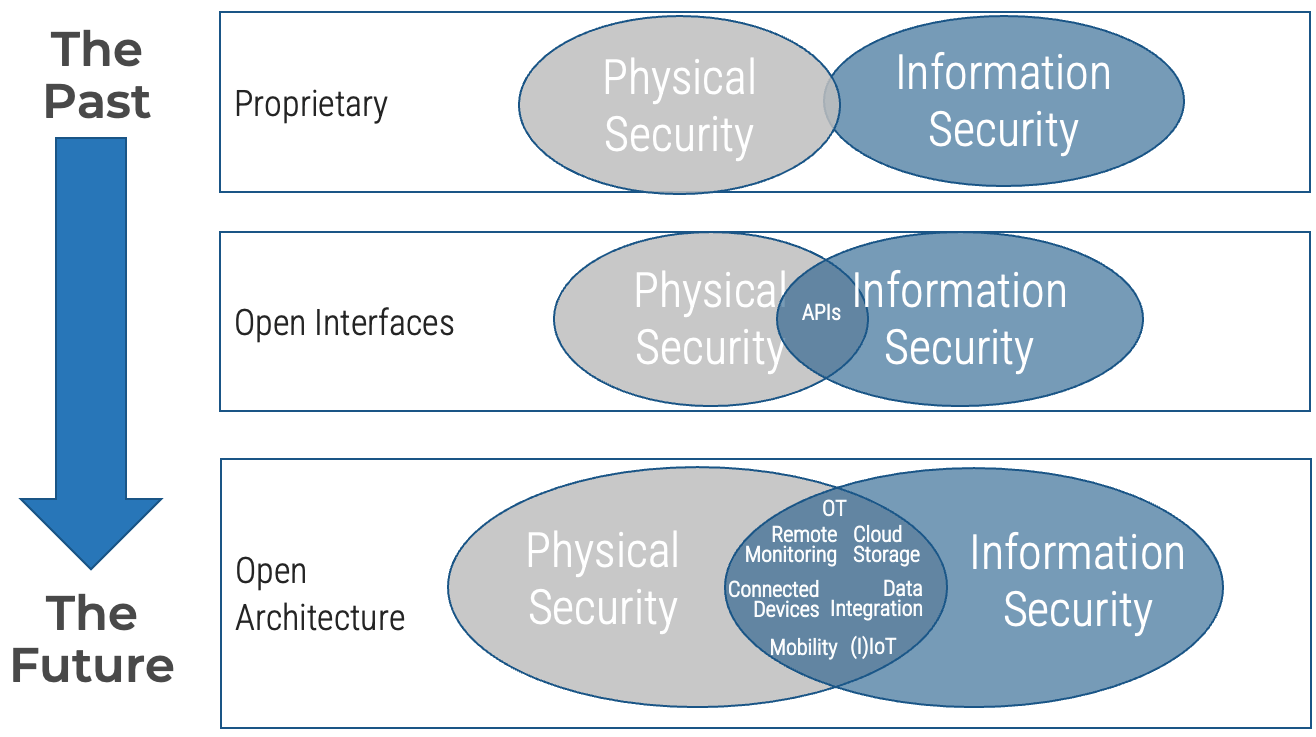
Sources: Cisco, n.d.; Preparing for Technology Convergence in Manufacturing, Info-Tech Research Group, 2018
Physical security includes:
-
Securing physical access,
e.g. facility access control, alarms, surveillance cameras -
Securing physical operations
(operational technology – OT), e.g. programmable logic controllers (PLCs), SCADA
Info-Tech Insight
Why is integrating physical and information security gaining more and more traction? Because the supporting technologies are becoming more matured. This includes, for example, migration of physical security devices to IP-based network and open architecture.
Reactive responses to physical security incidents
April 1995
Target: Alfred P. Murrah Federal Building, Oklahoma, US. Method: Bombing. Impact: Destroyed structure of 17 federal agencies, 168 casualties, over 800 injuries. Result: Creation of Interagency Security Committee (ISC) in Executive Order 12977 and “Vulnerability Assessment of Federal Facilities” standard.
(Source: Office of Research Services, 2017)
April 2013
Target: Pacific Gas & Electric’s Metcalf Substation, California, US. Method: Sniper attack. Impact: Out of 21 power transformers, 17 were damaged. Result: Creation of Senate Bill No. 699 and NERC- CIP-014 standard.
(Source: T&D World, 2023)
Sep. 2022
Target: Nord Stream gas pipelines connecting Russia to Germany, Baltic sea. Method: Detonations. Impact: Methane leaks (~300,000 tons) at four exclusive economic zones (two in Denmark and two in Sweden). Result: Sweden’s Security Service investigation.
(Source: CNBC News, 2022)
Dec. 2022
Target: Duke Energy Substation, North Carolina, US. Method: Gunfire. Impact: Power outages of ~40,000 customers and wastewater pumps in sewer lift stations down. Result: State of emergency was declared.
(Source: CBS News, 2022)
Info-Tech Insight
When it comes to physical security, we have been mostly reactive. Typically the pattern starts with physical attacks. Next, the impacted organization mitigates the incidents. Finally, new government regulatory measures or private sector or professional association standards are put in place. We must strive to change our pattern to become more proactive.
Physical security market forecast and top physical security challenges
Physical security market forecast
(in billions USD)
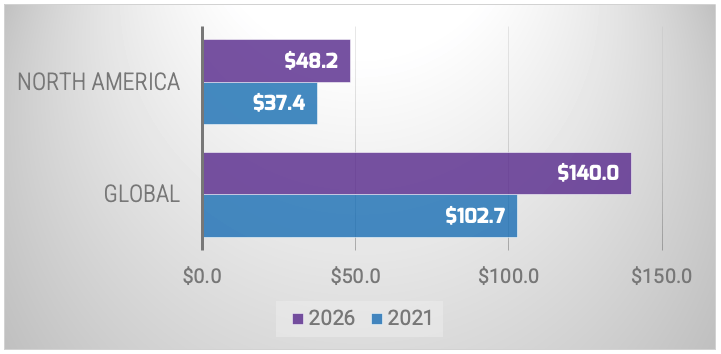
A forecast by MarketsandMarkets projected growth in the physical security market, using historical data from 2015 until 2019, with a CAGR of 6.4% globally and 5.2% in North America.
Source: MarketsandMarkets, 2022
Top physical security challenges
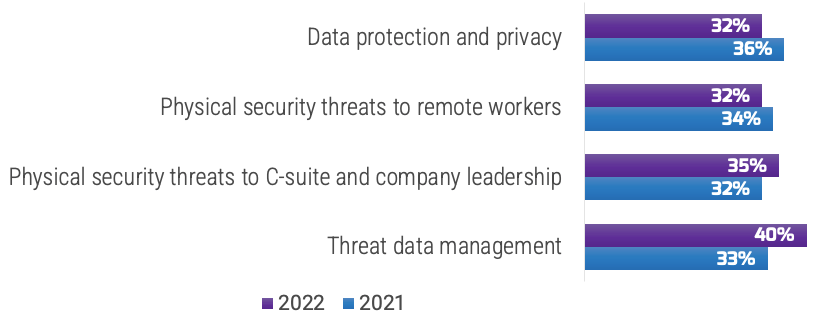
An Ontic survey (N=359) found that threat data management (40%) was the top physical security challenge in 2022, up from 33% in 2021, followed by physical security threats to the C-suite and company leadership (35%), which was a slight increase from 2021. An interesting decrease is data protection and privacy (32%), which dropped from 36% in 2021.
Source: Ontic Center for Protective Intelligence, 2022
Info-Tech Insight
The physical security market is growing in systems and services, especially the integration of threat data management with cybersecurity.
Top physical security initiatives and operations integration investments
We know the physical security challenges and how the physical security market is growing, but what initiatives are driving this growth? These are the top physical security initiatives and top investments for physical security operations integration:
Top physical security initiatives
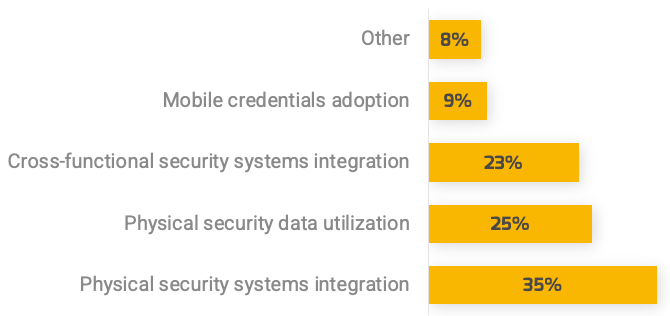
A survey by Brivo asked 700 security professionals about their top physical security initiatives. The number one initiative is integrating physical security systems. Other initiatives with similar concerns included data and cross-functional integration.
Source: Brivo, 2022
Top investments for physical security operations integration
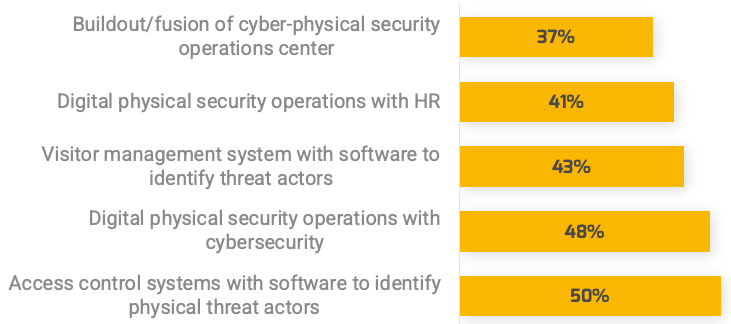
An Ontic survey (N=359) on areas of investment for physical security operations integration shows the number one investment is on access control systems with software to identify physical threat actors. Another area with similar concern is integration of digital physical security with cybersecurity.
Source: Ontic Center for Protective Intelligence, 2022
Evaluate security integration opportunities with these guiding principles
Opportunity focus
- Identify the security integration problems to solve with visible improvement possibilities
- Don’t choose technology for technology’s sake
- Keep an eye to the future
- Use strategic foresight
Piece by piece
- Avoid taking a big bang approach
- Test technologies in multiple conditions
- Run inexpensive pilots
- Increase flexibility
- Build a technology ecosystem
Buy-in
- Collaborate with stakeholders
- Gain and sustain support
- Maintain transparency
- Increase uptake of open architecture
Key Recommendations:
Focus on your master plan
Build a technology ecosystem
Engage stakeholders
Info-Tech Insight
When looking for a quick win, consider learning the best internal or external practice. For example, in 1994 IBM reorganized its security operation by bringing security professionals and non-security professionals in one single structure, which reduced costs by approximately 30% in two years.
Sources: Create and Implement an IoT Strategy, Info-Tech Research Group, 2022; Baker and Benny, 2013; Erich Krueger, Omaha Public Power District (contributor); Doery Abdou, March Networks Corporate (contributor)
Case Study
4Wall Entertainment – Asset Owner
Industry: Architecture & EngineeringSource: Interview
4Wall Entertainment is quite mature in integrating its physical and information security; physical security has always been under IT as a core competency.
4Wall Entertainment is a provider of entertainment lighting and equipment to event venues, production companies, lighting designers, and others, with a presence in 18 US and UK locations.
After many acquisitions, 4Wall Entertainment needed to standardize its various acquired systems, including physical security systems such as access control. In its integrated security approach, IT owns the integrated security, but they interface with related entities such as HR, finance, and facilities management in every location. This allows them to obtain information such as holidays, office hours, and what doors need to be accessed as inputs to the security system and to get sponsorship in budgeting.
In the past, 4Wall Entertainment tried delegating specific physical security to other divisions, such as facilities management and HR. This approach was unsuccessful, so IT took back the responsibility and accountability.
Currently, 4Wall Entertainment works with local vendors, and its biggest challenge is finding third-party vendors that can provide nationwide support.
In the future, 4Wall Entertainment envisions physical security modernization such as camera systems that allow more network accessibility, with one central system to manage and IoT device integration with SIEM and MDR.
Results
Lessons learned in integrating security from 4Wall Entertainment include:
- Start with forming relationships with related divisions such as HR, finance, and facilities management to build trust and encourage sponsorship across management.
- Create policies, procedures, and standards to deploy in various systems, especially when acquiring companies with low maturity in security.
- Select third-party providers that offer the required functionalities, good customer support, and standard systems interoperability.
- Close skill gaps by developing training and awareness programs for users, especially for newly acquired systems and legacy systems, or by acquiring expertise from consulting services.
- Complete cost-benefit analysis for solutions on legacy systems to determine whether to keep them and create interfacing with other systems, upgrade them, or replace them entirely with newer systems.
- Delegate maintenance of specific highly regulated systems, such as fire alarms and water sprinklers, to facilities management.
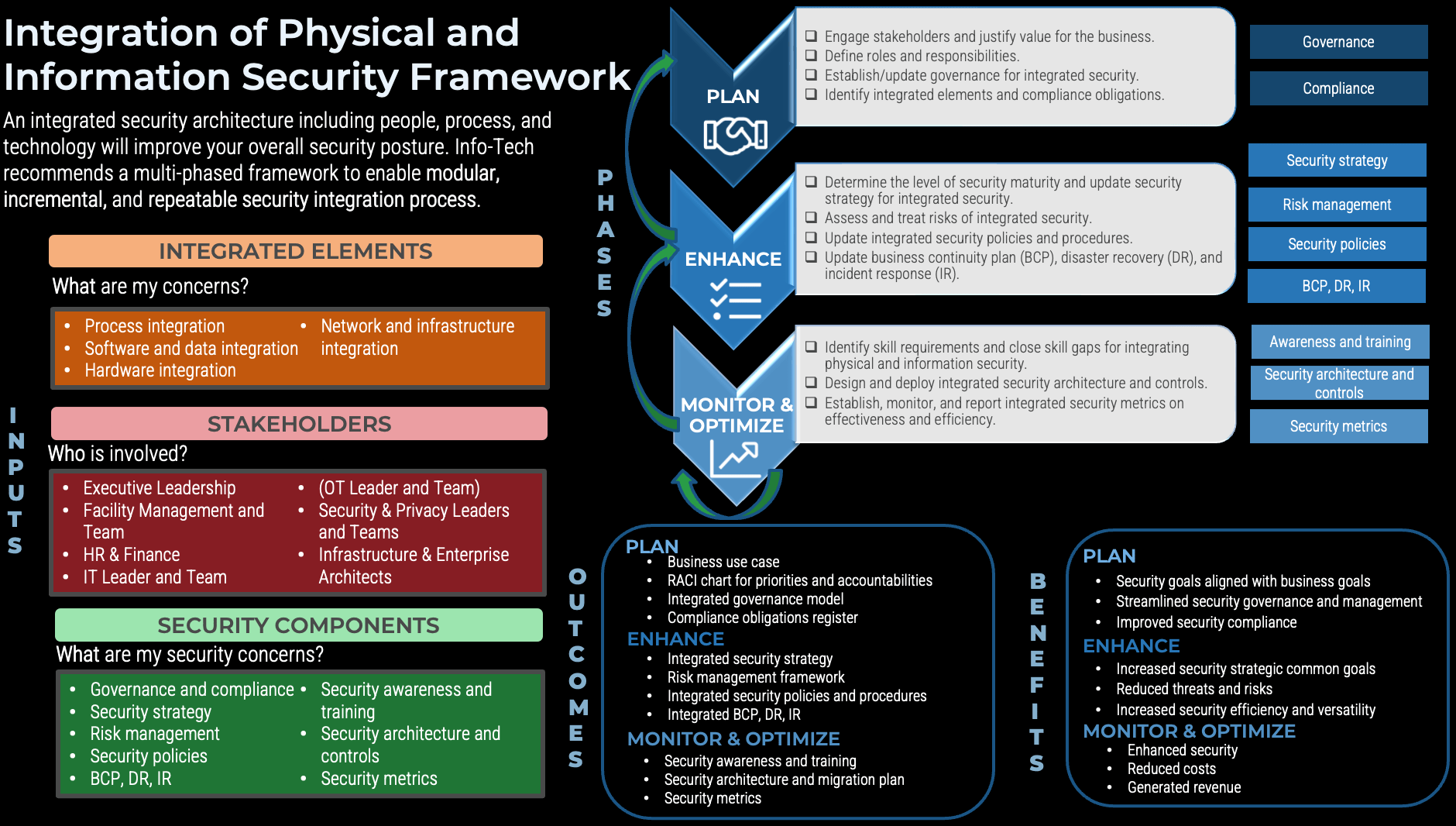
Tracking progress of physical and information security integration
Physical security is often part of facilities management. As a result, there are interdependencies with both internal departments (such as IT, information security, and facilities) and external parties (such as third-party vendors). IT leaders, security leaders, and operational leaders should keep the big picture in mind when designing and implementing integration of physical and information security. Use this checklist as a tool to track your security integration journey.
Plan
- Engage stakeholders and justify value for the business.
- Define roles and responsibilities.
- Establish/update governance for integrated security.
- Identify integrated elements and compliance obligations.
Enhance
- Determine the level of security maturity and update security strategy for integrated security.
- Assess and treat risks of integrated security.
- Establish/update integrated physical and information security policies and procedures.
- Update incident response, disaster recovery, and business continuity plan.
Monitor & Optimize
- Identify skill requirements and close skill gaps for integrating physical and information security.
- Design and deploy integrated security architecture and controls.
- Establish, monitor, and report integrated security metrics on effectiveness and efficiency.
Benefits of the security integration framework
Today’s matured technology makes security integration possible. However, the governance and management of single integrated security presents challenges. These can be overcome using a multi-phased framework that enables a modular, incremental, and repeatable integration process, starting with planning to justify the value of investment, then enhancing the integrated security based on risks and open architecture. This is followed by using metrics for monitoring and optimization.
-
Modular
- Implementing a consolidated security strategy is complex and involves the integration of process, software, data, hardware, and network and infrastructure.
- A modular framework will help to drive value while putting in appropriate guardrails.
-
Incremental
- Integration of physical security and information security involves many components such as security strategy, risk management, and security policies.
- An incremental framework will help track, manage, and maintain each step while providing appropriate structure.
-
Repeatable
- Integration of physical security and information security is a journey that can be approached with a pilot program to evaluate effectiveness.
- A repeatable framework will help to ensure quick time to value and enable immediate implementation of controls to meet operational and security requirements.
Potential risks of the security integration framework
Just as medicine often comes with side effects, our Integration of Physical and Information Security Framework may introduce risks too. However, as John F. Kennedy, thirty-fifth president of the United States, once said, "There are risks and costs to a program of action — but they are far less than the long-range cost of comfortable inaction."
Plan Phase
- Lack of transparency in the integration process can lead to lack of trust among stakeholders.
- Lack of support from leadership results in unclear governance or lack of budget or human resources.
- Key stakeholders leave the organization during the engagement and their replacements do not understand the organization’s operation yet.
Enhance Phase
- The risk assessment conducted focuses too much on IT risk, which may not always be applicable to physical security systems nor OT systems.
- The integrated security does not comply with policies and regulations.
Monitor and Optimize Phase
- Lack of knowledge, training, and awareness.
- Different testing versus production environments.
- Lack of collected or shared security metrics.
Data
- Data quality issues and inadequate data from physical security, information security, and other systems, e.g. OT, IoT.
- Too much data from too many tools are complex and time consuming to process.
Develop an integration of information security, physical security, and personnel security that meets your organization’s needs
Integrate security in people, process, and technology to improve your overall security posture
Having siloed systems running security is not beneficial. Many organizations are realizing the benefits of consolidating into a single platform across physical security, cybersecurity, HR, legal, and compliance.
Plan and engage stakeholders
Assemble the right team to ensure the success of your integrated security ecosystem, decide the governance model, and clearly define the roles and responsibilities.
Enhance strategy and risk management
Strategically, we want a physical security system that is interoperable with most technologies, flexible with minimal customization, functional, and integrated, despite the challenges of proprietary configurations, complex customization, and silos.
Monitor and optimize
Find the most optimized architecture that is strategic, realistic, and based on risk. Next, perform an evaluation of the security systems and program by understanding what, where, when, and how to measure and to report the relevant metrics.
Focus on master plan
Identify the security integration problems to solve with visible improvement possibilities, and don’t choose technology for technology’s sake. Design first, then conduct market research by comparing products or services from vendors or manufacturers.
Build a technology ecosystem
Avoid a big bang approach and test technologies in multiple conditions. Run inexpensive pilots and increase flexibility to build a technology ecosystem.
Deliverables
Each step of this framework is accompanied by supporting deliverables to help you accomplish your goals:
Integrate Physical Security and Information Security Requirements Gathering Tool
Map organizational goals to IT goals, facilities goals, OT goals (if applicable), and integrated security goals. Identify your security integration elements and compliance.
Integrate Physical Security and Information Security RACI Chart Tool
Identify various security integration stakeholders across the organization and assign tasks to suitable roles.
Key deliverable:
Integrate Physical Security and Information Security Communication Deck
Present your findings in a prepopulated document that summarizes the work you have completed.
Plan
Planning is foundational to engage stakeholders. Start with justifying the value of investment, then define roles and responsibilities, update governance, and finally identify integrated elements and compliance obligations.
Plan
Engage stakeholders
- To initiate communication between the physical and information security teams and other related divisions, it is important to identify the entities that would be affected by the security integration and involve them in the process to gain support from planning to delivery and maintenance.
-
Possible stakeholders:
- Executive leadership, Facilities Management leader and team, IT leader, Security & Privacy leader, compliance officer, Legal, Risk Management, HR, Finance, OT leader (if applicable)
- A successful security integration depends on aligning your security integration initiatives and migration plan to the organization’s objectives by engaging the right people to communicate and collaborate.
Info-Tech Insight
It is important to speak the same language. Physical security concerns safety and availability, while information security concerns confidentiality and integrity. Thus, the two systems have different goals and require alignment.
Similarly, taxonomy of terminologies needs to be managed,1 e.g. facility management with an emergency management background may have a different understanding from a CISO with an information security background when discussing the same term. For example:
In emergency management prevention means “actions taken to eliminate the impact of disasters in order to protect lives, property and the environment, and to avoid economic disruption.”2
In information security prevention is “preventing the threats by understanding the threat environment and the attack surfaces, the risks, the assets, and by maintaining a secure system.”3
Sources: 1 Owen Yardley, Omaha Public Power District (contributor); 2 Translation Bureau, Government of Canada, n.d.; 3 Security Intelligence, 2020
Map organizational goals to integrated security goals
Input
|
Output
|
Materials
|
Participants
|
- As a group, brainstorm organization goals.
- Review relevant corporate, IT, and facilities strategies.
- Record the most important business goals in the “Goals Cascade” tab of the Integrate Physical Security and Information Security Requirements Gathering Tool. Try to limit the number of business goals to no more than ten goals. This limitation will be critical to helping focus on your integrated security goals.
- For each goal, identify one to two security alignment goals. These should be objectives for the security strategy that will support the identified organization goals.
Download the Integrate Physical Security and Information Security Requirements Gathering Tool.
Record organizational goals
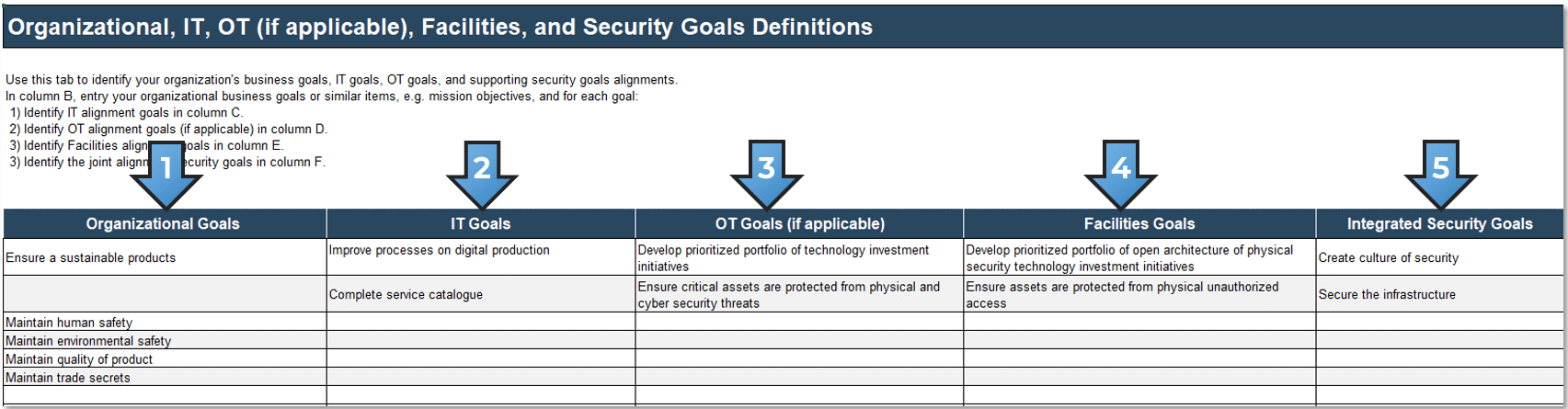
Refer to the Integration of Physical and Information Security Framework when filling in the table.
- Record your identified organizational goals in the “Goals Cascade” tab of the Integrate Physical Security and Information Security Requirements Gathering Tool.
- For each organizational goal, identify IT alignment goals.
- For each organizational goal, identify OT alignment goals (if applicable).
- For each organizational goal, identify Facilities alignment goals.
- For each organizational goal, select an integrated security goal from the drop-down menu.
Justify value for the business
Facilities in most cases have a team that is responsible for physical security installations such as access key controllers. Whenever there is an issue, they contact the provider to fix the error. However, with smart buildings and smart devices, the threat surface grows to include information security threats, and Facilities may not possess the knowledge and skills required to deal with them. At the same time, delegating physical security to IT may add more tasks to their already-too-long list of responsibilities. Consolidating security to a focused security team that covers both physical and information security can help.1 We need to develop the security integration business case beyond physical security "gates, guns, and guards" mentality.2
An example of a cost-benefit analysis for security integration:
Benefits |
Metrics |
Operational Efficiency and Cost Savings |
|
Reliability Improvements |
|
Customers & Users Benefits |
|
Cost |
Metrics |
Equipment and Infrastructure |
|
Software and Commission |
|
Support and Resources |
|
Sources: 1 Andrew Amaro, KLAVAN Security Services (contributor); 2 Baker and Benny, 2013;
Industrial Control System Modernization, Info-Tech Research Group, 2023; Lawrence Berkeley National Laboratory, 2021
Plan
Define roles and responsibilities
Input
| Output
|
Materials
| Participants
|
Many factors impact an organization’s level of effectiveness as it relates to integration of physical and information security. How the team interacts, what skill sets exist, the level of clarity around roles and responsibilities, and the degree of executive support and alignment are only a few. Thus, we need to identify stakeholders that are:
- Responsible: The person(s) who does the work to accomplish the activity; they have been tasked with completing the activity and/or getting a decision made.
- Accountable: The person(s) who is accountable for the completion of the activity. Ideally, this is a single person and is often an executive or program sponsor.
- Consulted: The person(s) who provides information. This is usually several people, typically called subject matter experts (SMEs).
- Informed: The person(s) who is updated on progress. These are resources that are affected by the outcome of the activities and need to be kept up to date.
Download the Integrate Physical Security and Information Security RACI Chart Tool
Define RACI chart
Define Responsible, Accountable, Consulted, Informed (RACI) stakeholders.
- Customize the Work Units to best reflect your operation with applicable stakeholders.
- Customize the Action rows as required.
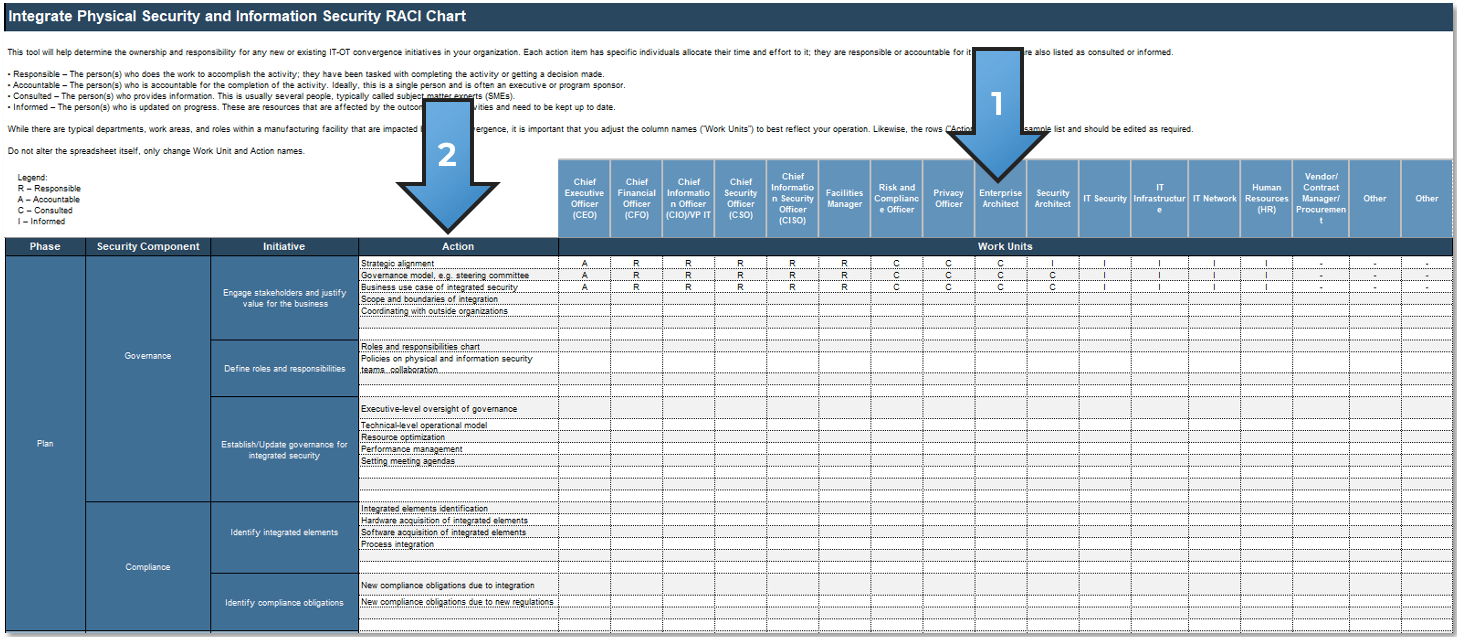
Sources: ISC, 2015; ISC, 2021
Info-Tech Insight
The roles and responsibilities should be clearly defined. For example, IT Security should be responsible for the installation and configuration of all physical access controllers and devices, and facility managers should be responsible for the physical maintenance including malfunctioning such as access device jammed or physically broken.
Plan
Establish/update governance for integrated security
HR & Finance
HR provides information such as new hires and office hours as input to the security system. Finance assists in budgeting.
Security & Privacy
The security and privacy team will need to evaluate solutions and enforce standards on various physical and information security systems and to protect data privacy.
Business Leaders
Business stakeholders will provide clarity for their strategy and provide input into how they envision security furthering those goals.
IT Executives
IT stakeholders will be a driving force, ensuring all necessary resources are available and funded.
Facilities/ Operations
Operational plans will include asset management, monitoring, and support to meet functional goals and manage throughout the asset lifecycle.
Infrastructure & Enterprise Architects
Each solution added to the environment will need to be chosen and architected to meet business goals and security functions.
Info-Tech Insight
Assemble the right team to ensure the success of your integrated security ecosystem and decide the governance model, e.g. security steering committee (SSC) or a centralized single structure.
Adapted from Create and Implement an IoT Strategy, Info-Tech Research Group, 2022
What does the SSC do?
Ensuring proper governance over your security program is a complex task that requires ongoing care and feeding from executive management to succeed.
Your SSC should aim to provide the following core governance functions for your security program:
-
Define Clarity of Intent and Direction
How does the organization’s security strategy support the attainment of the business, IT, facilities management, and physical and information security strategies? The SSC should clearly define and communicate strategic linkage and provide direction for aligning security initiatives with desired outcomes. -
Establish Clear Lines of Authority
Security programs contain many important elements that need to be coordinated. There must be clear and unambiguous authority, accountability, and responsibility defined for each element so lines of reporting/escalation are clear and conflicting objectives can be mediated. -
Provide Unbiased Oversight
The SSC should vet the organization’s systematic monitoring processes to ensure there is adherence to defined risk tolerance levels and that monitoring is appropriately independent from the personnel responsible for implementing and managing the security program. -
Optimize Security Value Delivery
Optimized value delivery occurs when strategic objectives for security are achieved and the organization’s acceptable risk posture is attained at the lowest possible cost. This requires constant attention to ensure controls are commensurate with any changes in risk level or appetite.
Adapted from Improve Security Governance With a Security Steering Committee , Info-Tech Research Group, 2018
Plan
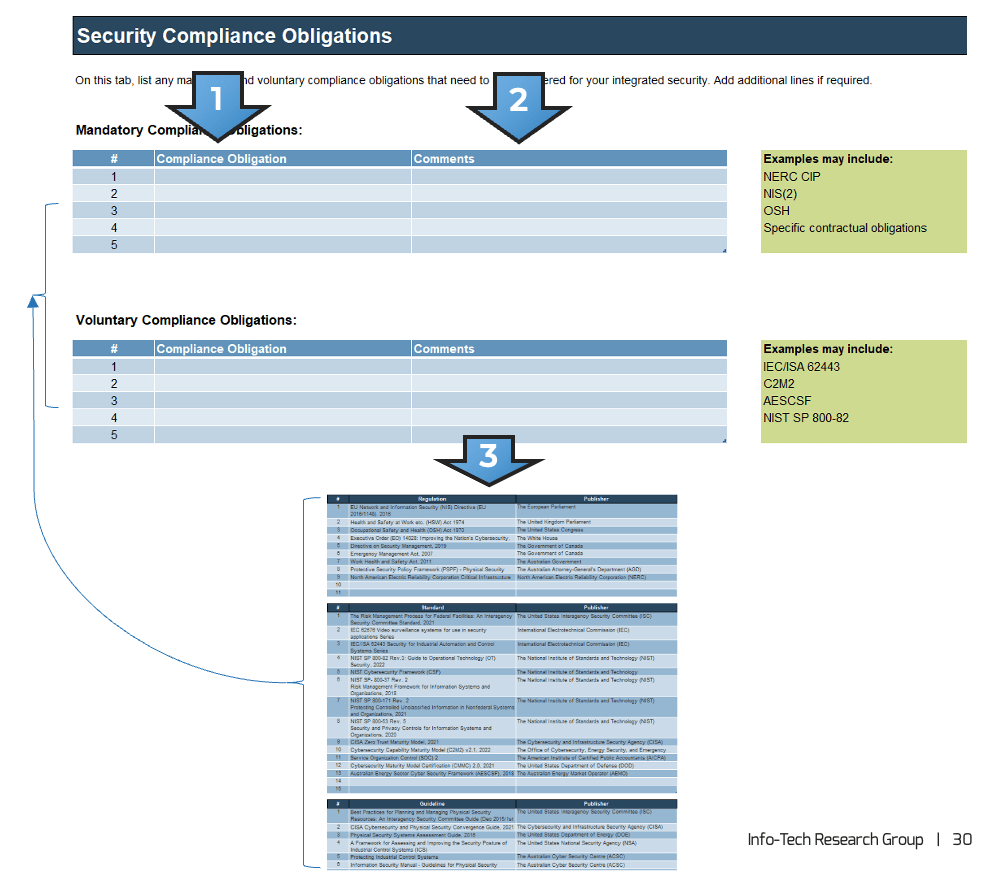
Identify integrated elements and compliance obligations
To determine what elements need to be integrated, it’s important to scope the security integration program and to identify the consequences of integration for compliance obligations.
INTEGRATED ELEMENTS
What are my concerns?
Process integrations
Determine which processes need to be integrated and how
- Examples: Security prevention, detection, and response; risk assessment
Software and data integration
Determine which software and data need to be integrated and how
- Examples: Threat management tools, SIEM, IDPS, security event logs
Hardware integration
Determine which hardware needs to be integrated and how
- Examples: Sensors, alarms, cameras, keys, locks, combinations, and card readers
Network and infrastructure
Determine which network and infrastructure components need to be integrated and how
- Example: Network segmentation for physical access controllers.
COMPLIANCE
How can I address my concerns?
Regulations
Adhere to mandatory laws, directives, industry standards, specific contractual obligations, etc.
- Examples: NERC CIP (North American Utilities), Network and Information Security (NIS) Directive (EU), Health and Safety at Work etc Act 1974 (UK), Occupational Safety and Health Act, 1970 (US), Emergency Management Act, 2007 (Canada)
Standards
Adhere to voluntary standards and obligations
- Examples: NIST Cybersecurity Framework (CSF), The Risk Management Process for Federal Facilities: An Interagency Security Committee Standard (US), Cybersecurity Maturity Model Certification (CMMC), Service Organization Control (SOC 1 and 2)
Guidelines
Adopt guidelines that can improve the integrated security program
- Examples: Best Practices for Planning and Managing Physical Security Resources (US Interagency Security Committee), Information Security Manual - Guidelines for Physical Security (Australian Cyber Security Centre), 1402-2021-Guide for Physical Security of Electric Power Substations (IEEE)
Record integrated elements
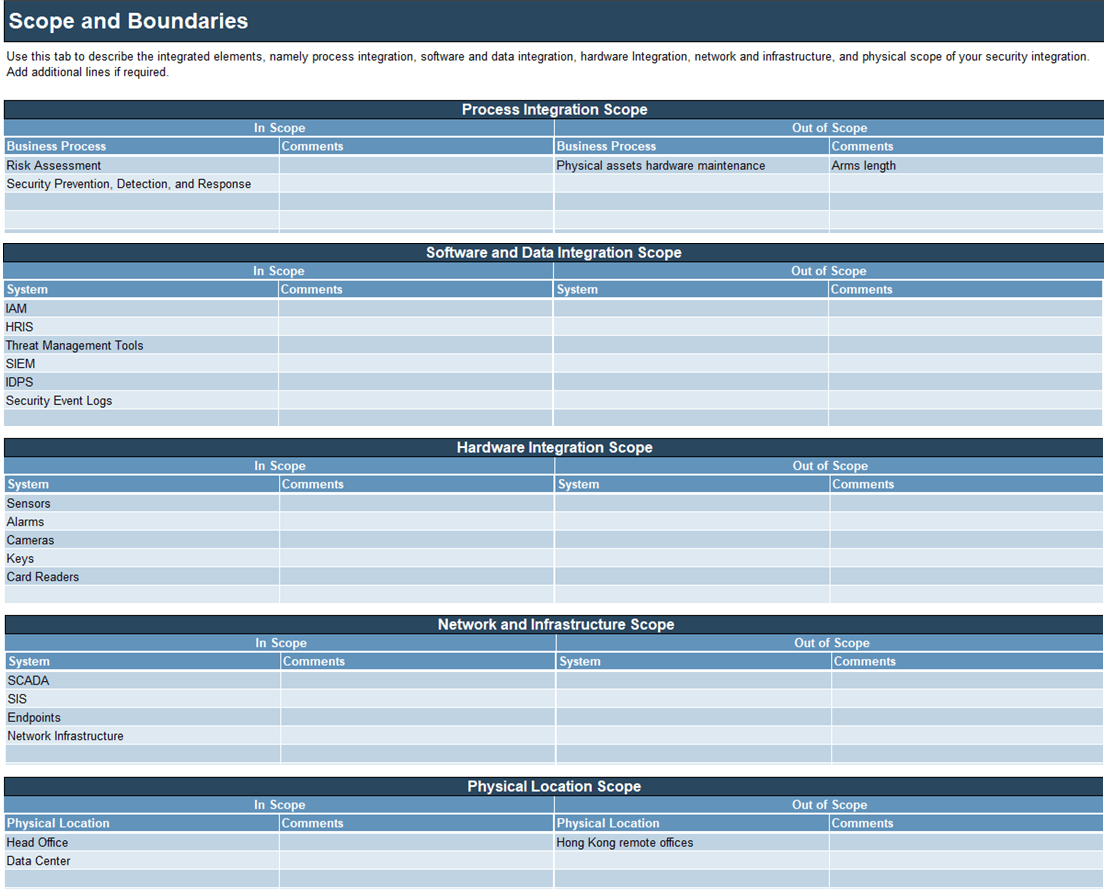
Refer to the “Scope” tab of the Integrate Physical Security and Information Security Requirements Gathering Tool when filling in the following elements.
- Record your integrated elements, i.e. process integration, software and data integration, hardware integration, network and infrastructure, and physical scope of your security integration, in the “Scope” tab of the Integrate Physical Security and Information Security Requirements Gathering Tool.
- For each of your scoping give the rationale for including them in the Comments column. Careful attention should be paid to any elements that are not in scope.
Record your compliance obligations
Refer to the “Compliance Obligations” tab of the Integrate Physical Security and Information Security Requirements Gathering Tool.
-
Identify your compliance obligations. These can include both mandatory and voluntary obligations. Mandatory obligations include:
- Laws
- Government regulations
- Industry standards
- Contractual agreements
- Record your compliance obligations, along with any notes, in your copy of the Integrate Physical Security and Information Security Requirements Gathering Tool.
- Refer to the “Compliance DB” tab for lists of standards/regulations/ guidelines.
Remediate third-party compliance gaps
If you have third-party compliance gaps, there are four primary ways to eliminate them:
-
Find a New, Compliant Partner
Terminate existing contract and find another organization to partner with. -
Bring the Capability In-House
Expense permitting, this may be the best way to protect yourself. -
Demand Compliance
Tell the third party they must become compliant. Make sure you set a deadline. -
Accept Noncompliance and Assume the Risk
Sometimes remediation just isn’t cost effective and you have no choice.
Follow Contracting Best Practices to Mitigate the Risk of Future Third-Party Compliance Gaps
- Perform Initial Due Diligence: Request proof of third-party compliance prior to entering into a contract.
- Perform Ongoing Due Diligence: Request proof of third-party contractor compliance annually.
- Contract Negotiation: Insert clauses requesting periodic assertions of compliance.
View a sample contract provided by the US Department of Health and Human Services.
Source: Take Control of Compliance Improvement to Conquer Every Audit, Info-Tech Research Group, 2015
Pitfalls to avoid when planning security integration
-
No Resources Lineups
Integration of security needs support from leadership, proper planning, and clear and consistent communication across the organization. -
Not Addressing Holistic Security
Create policies and procedures and follow standards that are holistic and based on threats and risks, e.g. consolidated access control policies. -
Lack of Governance
While the IT department is a critical partner in cybersecurity, the ownership of such a role sits squarely in the organizational C-suite, with regular reporting to the board of directors (if applicable). -
Overlooking Business Continuity Effort
IT and physical security are integral to business continuity and disaster recovery strategies. -
Not Having Relevant Training and Awareness
Provide a training and awareness program based on relevant attack vectors. Trained employees are key assets to the development of a safe and secure environment. They must form the base of your security culture. -
Overbuilding or Underbuilding
Select third-party providers that offer systems interoperability with other security tools. The intent is to promote a unified approach to security to avoid a cumbersome tooling zoo.
Sources: Real Time Networks, 2022; Andrew Amaro, KLAVAN Security Services (contributor)
Enhance
Enhancing is the development of an integrated security strategy, policies, procedures, BCP, DR, and IR based on the organization’s risks.
Enhance
Determine the level of security maturity and update the security strategy
- Before updating your security strategies, you need to understand the organization’s business strategies, IT strategies, facilities strategies, and physical and information security strategies. The goal is to align your integrated security strategies to contribute to your organization’s success.
-
The integrated security leaders need to understand the direction of the organization. For example:
- Growth expectation
- Expansions or mergers anticipation
- Product or service changes
- Regulatory requirements
- Wise security investments depend on aligning your security initiatives to the organization’s objectives by supporting operational performance and ensuring brand protection and shareholder values.
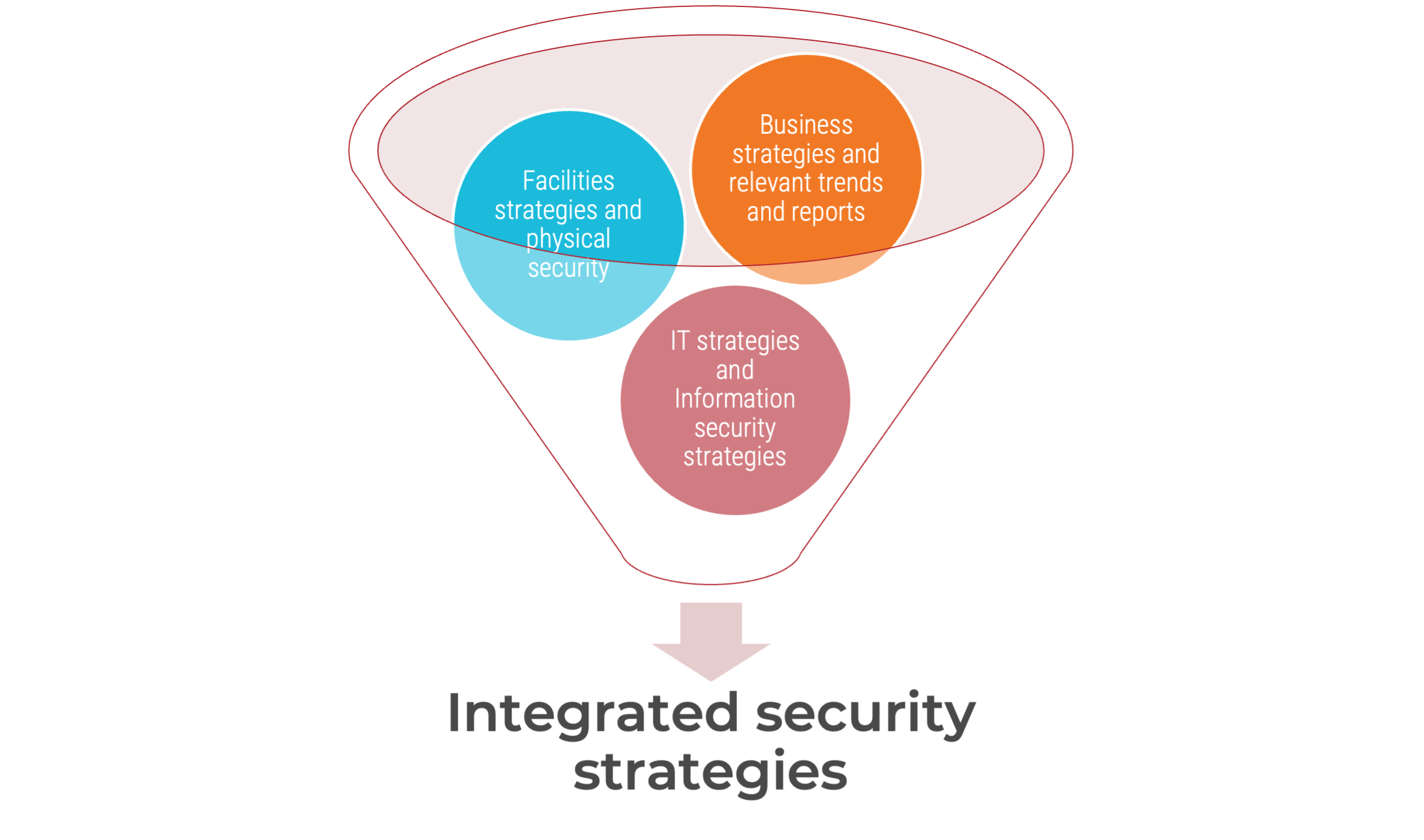
Sources: Amy L. Meger, Platte River Power Authority (contributor); Baker and Benny, 2013; IFSEC Global, 2023; Security Priorities 2023, Info-Tech Research Group, 2023; Build an Information Security Strategy, Info-Tech Research Group, 2020; ISC, n.d.
Understanding security maturity
Maturity models are very effective for determining security states. This table provides examples of general descriptions for physical and information security maturity levels.
Determine which framework is suitable and select the description that most accurately reflects the ideal state for security in your organization.
Level 1 |
Level 2 |
Level 3 |
Level 4 |
Level 5 |
|
| Minimum security with simple physical barriers. | Low-level security to prevent and detect some unauthorized external activity. | Medium security to prevent, detect, and assess most unauthorized external activity and some unauthorized internal activity. | High-level security to prevent, detect, and assess most unauthorized external and internal activity. | Maximum security to prevent, detect, assess, and neutralize all unauthorized external and internal activity. |
Physical security maturity level1 |
| Initial/Ad hoc security programs are reactive. | Developing security programs can be effective at what they do but are not holistic. | A defined security program is holistic, documented, and proactive. | Managed security programs have robust governance and metrics processes. | An optimized security program is based on strong risk management practices, including the production of key risk indicators (KRIs). |
Information security maturity level2 |
Sources: 1 Fennelly, 2013; 2 Build an Information Security Strategy, Info-Tech Research Group, 2020
Enhance
Assess and treat integrated security risks
The risk assessment conducted consists of analyzing existing inherent risks, existing pressure to the risks such as health and safety laws and codes of practice, new risks from the integration process, risk tolerance, and countermeasures.
- Some organizations already integrate security into corporate security that consists of risk management, compliance, governance, information security, personnel security, and physical security. However, some organizations are still separating security components, especially physical security and information security, which limits security visibility and the organization’s ability to complete a comprehensive risks assessment.
- Many vendors are also segregating physical security and information security solutions because their tools do well only on certain aspects. This forces organizations to combine multiple tools, creating a complex environment.
- Additionally, risks related to people such as mental health issues must be addressed properly. The prevalence of hybrid work post-pandemic makes this aspect especially important.
- Assess and treat risks based on the organization’s requirements, including its environments. For example, the US federal facility security organization is required to conduct risk assessments at least every five years for Level I (lowest risk) and Level II facilities and at least every three years for Level III, IV, and V (highest risk) facilities.
Sources: EPA, n.d.; America's Water Infrastructure Act (AWIA), 2018; ISC, 2021
“In 2022, 95% of US companies are consolidating into a single platform across physical security, cybersecurity, HR, legal and compliance.”
Source: Ontic Center for Protective Intelligence, 2022; N=359
Example risk levels
The risk assessment conducted is based on a combination of physical and information security factors such as certain facilities factors. The risk level can be used to determine the baseline level of protection (LOP). Next, the baseline LOP is customized to the achievable LOP. The following is an example for federal facilities determined by Interagency Security Committee (ISC).
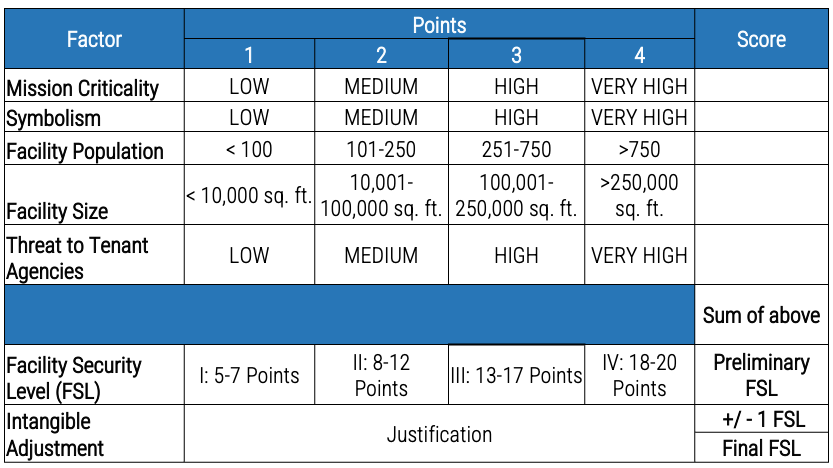
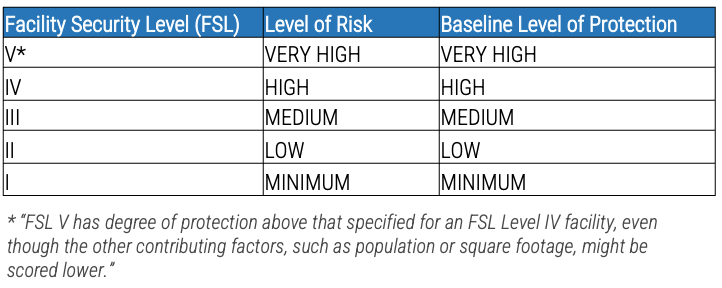
Source: ISC, 2021
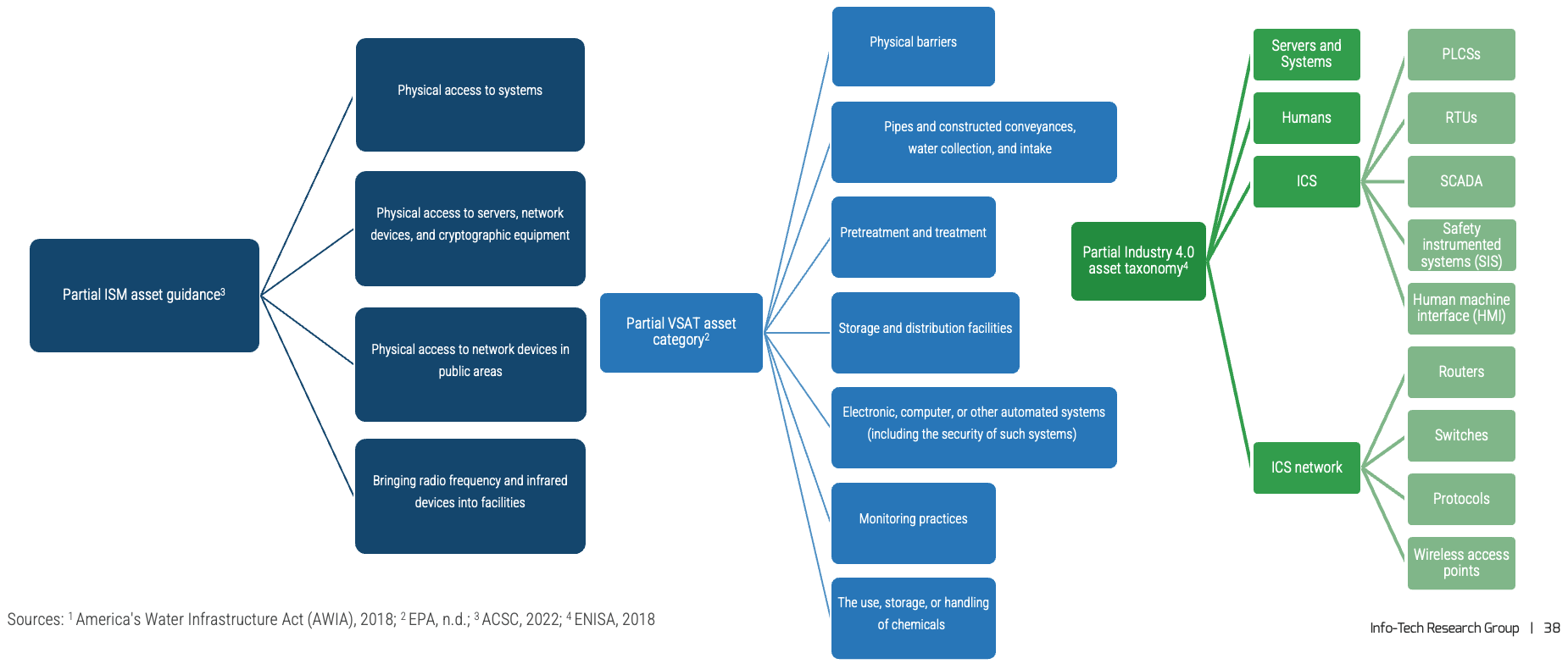
Example assets
It is important to identify the organization’s requirements, including its environments (IT, IoT, OT, facilities, etc.), and to measure and evaluate its risks and threats using an appropriate risk framework and tools with the critical step of identifying assets prior to acquiring solutions.
Info-Tech Insight
Certain exceptions must be identified in risk assessment. Usually physical barriers such as gates and intrusion detection sensors are considered as countermeasures,1 however, under certain assessment, e.g. America's Water Infrastructure Act (AWIA),2 physical barriers are also considered assets and as such must also be assessed.
Compromising a fingerprint scanner
An anecdotal example of why physical security alone is not sufficient.

Image by Rawpixel.com on Freepik
Lessons learned from using fingerprints for authentication:
- Fingerprint scanners can be physically circumvented by making a copy an authorized user’s fingerprint with 3D printing or even by forcefully amputating an authorized user’s finger.
- Authorized users may not be given access when the fingerprint cannot be recognized, e.g. if the finger is covered by bandage due to injury.
- Integration with information security may help detect unauthorized access, e.g. a fingerprint being scanned in a Canadian office when the same user was scanned at a close time interval from an IP in Europe will trigger an alert of a possible incident.
Info-Tech Insight
In an ideal world, we want a physical security system that is interoperable with all technologies, flexible with minimal customization, functional, and integrated. In the real world, we may have physical systems with proprietary configurations that are not easily customized and siloed.
Source: Robert Dang, Info-Tech Research Group
Use case: Microchip implant
Microchip implants can be used instead of physical devices such as key cards for digital identity and access management. Risks can be assessed using quantitative or qualitative approaches. In this use case a qualitative approach is applied to impact and likelihood, and a quantitative approach is applied to revenue and cost.
Asset: Microchip implant
Benefits
Impact |
|
Likelihood |
|
Revenue |
|
Risks
Impact |
|
Likelihood |
|
Cost |
|
Sources: Business Insider, 2018; BBC News, 2022; ISC, 2015
Enhance
Update integrated security policies and procedures
Global policies with local implementation
This model works for corporate groups with a parent company. In this model, global security policies are developed by a parent company and local policies are applied to the unique business that is not supported by the parent company.
Update of existing security policies
This model works for organizations with sufficient resources. In this model, integrated security policies are derived from various policies. For example, physical security in smart buildings/devices (sensors, automated meters, HVAC, etc.) and OT systems (SCADA, PLCs, RTUs, etc.) introduce unique risk exposures, necessitating updates to security policies.
Customization of information security policies
This model works for smaller organizations with limited resources. In this model, integrated security policies are derived from information security policies. The issue is when these policies are not applicable to physical security systems or other environments, e.g. OT systems.
Sources: Kris Krishan, Waymo (contributor); Isabelle Hertanto, Info-Tech Research Group (contributor); Physical and Environmental Security Policy Template, Info-Tech Research Group, 2022.
Enhance
Update BCP, DR, IR
- Physical threats such as theft of material, vandalism, loitering, and the like are also part of business continuity threats.
- These threats can be carried out by various means such as vehicles breaching perimeter security, bolt cutters used for cutting wire and cable, and ballistic attack.
- Issues may occur when security operations are owned separately by physical security or information security, thus lacking consistent application of best practices.
- To overcome this issue, organizations need to update BCP, DR, and IR holistically based on a cost-benefit analysis and the level of security maturity, which can be defined based on the suitable framework.
Sources: IEEE, 2021; ISC, 2021
“The best way to get management excited about a disaster plan is to burn down the building across the street.”
Source: Dan Erwin, Security Officer, Dow Chemical Co., in Computerworld, 2022
Optimize
Optimizing means working to make the most effective and efficient use of resources, starting with identifying skill requirements and closing skill gaps, followed by designing and deploying integrated security architecture and controls, and finally monitoring and reporting integrated security metrics.
Optimize
Identify skill requirements and close skill gaps
- The pandemic changed how people work and where they choose to work, and most people still want a hybrid work model. Our survey in July 2022 (N=516) found that 55.8% of employees have the option to work offsite 2-3 days per week, 21.0% can work offsite 1 day per week, and 17.8% can work offsite 4 days per week.
- The investment (e.g. on infrastructure and networks) to initiate remote work was huge, and the costs didn’t end there; organizations needed to maintain the secure remote work infrastructure to facilitate the hybrid work model.
- Moreover, roles are evolving due to convergence and modernization. These new roles require an integrative skill set. For example, the grid security and ops team might consist of an IT security specialist, a SCADA technician/engineer, and an OT/IIOT security specialist, where OT/IIOT security specialist is a new role.
| Identify skill gaps that hinder the successful execution of the hybrid work security strategy. | Use the identified skill gaps to define the technical skill requirements for current and future work roles. | Conduct a skills assessment on your current workforce to identify employee skill gaps. | Decide whether to train (including certification), hire, contract, or outsource to close each skill gap. |
Strategic investment in internal security team
Internal security governance and management using in-house developed tools or off-the-shelf solutions, e.g. security information and event management (SIEM).
Security management using third parties
Internal security management using third-party security services, e.g. managed security service providers (MSSPs).
Outsourcing security management
Outsourcing the entire security functions, e.g. using managed detection and response (MDR).
Sources: Info-Tech Research Group’s Security Priorities 2023, Close the InfoSec Skills Gap, Build an IT Employee Engagement Program, and Grid Modernization
Select the right certifications
What are the options?
- One issue in security certification is the complexity of relevancy in topics with respect to roles and levels.
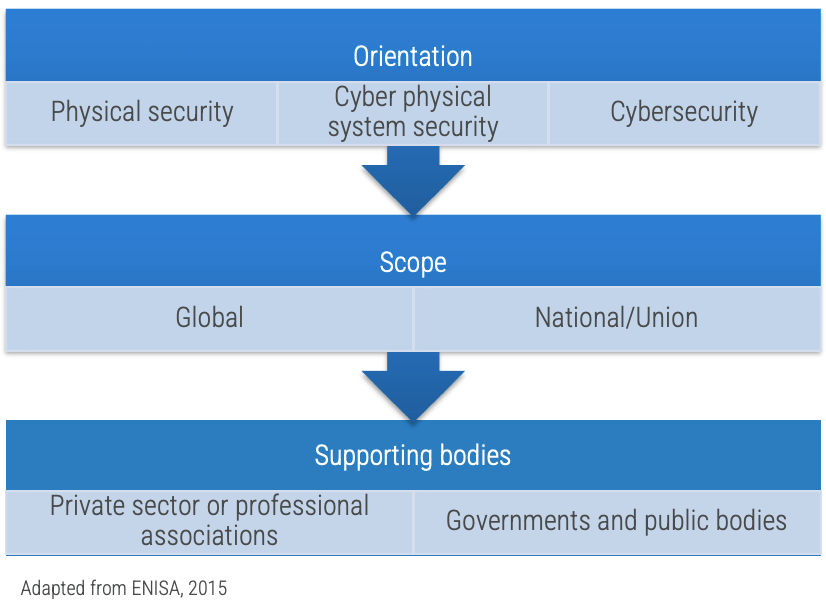
- The European Union Agency for Cybersecurity (ENISA) takes the approach of analyzing existing certifications of ICS/SCADA professionals' cybersecurity skills by orientation, scope, and supporting bodies that are grouped into specific certifications, relevant certifications, and safety certifications (ENISA, 2015).
- This approach can also be applied to integrated security certifications.
Physical security certification
- Examples: Industrial Security Professional Certification (NCMS-ISP); Physical Security Professional (ASIS-PSP); Physical Security Certification (CDSE-PSC); ISC I-100, I-200, I-300, and I-400
Cyber physical system security certification
- Examples: Certified SCADA Security Architect (CSSA), EC-Council ICS/SCADA Cybersecurity Training Course
Information security certification
- Examples: Network and Information Security (NIS) Driving License, ISA/IEC 62443 Cybersecurity Certificate Program, GIAC Global Industrial Cyber Security Professional (GICSP)
Safety Certifications
- Examples: Board of Certified Safety Professionals (BCSP), European Network of Safety and Health Professional Organizations (ENSHPO)
Optimize
Design and deploy integrated security architecture and controls
- A survey by Brivo found that 38% of respondents have partly centralized security platforms, 25% have decentralized platforms, and 36% have centralized platforms (Brivo, 2022; N=700).
- If your organization’s security program is still decentralized or partly centralized and your organization is planning to establish an integrated security program, then the recommendation is to perform a holistic risk assessment based on probability and impact assessments on threats and vulnerabilities.
- The impacted factors, for example, are customers served, criticality of services, equipment present inside the building, personnel response time for operational recovery and the mitigation of hazards, and costs.
- Frameworks such as Sherwood Applied Business Security Architecture (SABSA), Control Objectives for Information and Related Technologies (COBIT), and The Open Group Architecture Framework (TOGAF) can be used to build security architecture that aligns security goals with business goals.
- Finally, analyze the security design against the design criteria.
Sources: ISA and Honeywell Integrated Security Technology Lab, n.d.; IEEE, 2021
“As long as organizations treat their physical and cyber domains as separate, there is little hope of securing either one.”
Source: FedTech magazine, 2009
Analyze architecture design
Cloud, on-premises, or hybrid? During the pandemic, many enterprises were under tight deadlines to migrate to the cloud. Many did not refactor data and applications correctly for cloud platforms during migration, with the consequence of high cloud bills. This happened because the migrated applications cannot take advantage of on-premises capabilities such as autoscaling. Thus, in 2023, it is plausible that enterprises will bring applications and data back on-premises.
Below is an example of a security design analysis of platform architecture. Design can be assessed using quantitative or qualitative approaches. In this example, a qualitative approach is applied using high-level advantages and disadvantages.
Design criteria | Cloud | Hybrid | On-premises |
Effort | Consumer effort is within a range, e.g. < 60% | Consumer effort is within a range e.g. < 80% | 100% organization |
Reliability | High reliability | High reliability | Medium reliability that depends on data centers |
Cost | High cost when data and applications are not correctly designed for cloud | Optimized cost when data and applications are correctly designed either for cloud or native | Medium cost when data and applications take advantage of on-prem capabilities |
Info-Tech Insight
It is important for organizations to find the most optimized architecture to support them, for example, a hybrid architecture of cloud and on-premises based on operations and cost-effectiveness. To help design a security architecture that is strategic, realistic, and based on risk, see Info-Tech’s Identify the Components of Your Cloud Security Architecture research.
Sources: InfoWorld, 2023; Identify the Components of Your Cloud Security Architecture , Info-Tech Research Group, 2021
Analyze equipment design
Below is an example case of a security design analysis of electronic security systems. Design can be assessed using quantitative or qualitative approaches. In this example a qualitative approach is applied using advantages and disadvantages.
Surveillance design criteria |
Video camera |
Motion detector |
Theft of security system equipment |
Higher economic loss | Lower economic loss |
Reliability |
Positive detection of intrusion | Spurious indication and lower reliability |
Energy savings and bandwidth |
Only record when motion is detected | Detect and process all movement |
Info-Tech Insight
Once the design has been analyzed, the next step is to conduct market research to analyze the solutions landscape, e.g. to compare products or services from vendors or manufacturers.
Sources: IEEE, 202; IEC, n.d.; IEC, 2013
Analyze off-the-shelf solutions
Criteria to consider when comparing solutions:
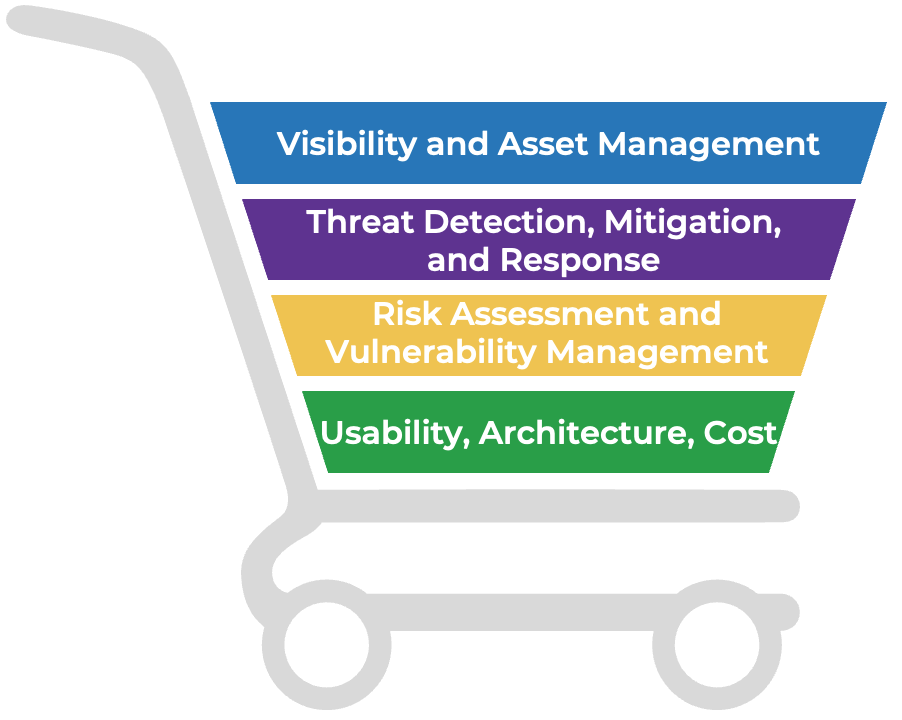
Visibility and Asset Management
Passively monitoring data using various protocol layers, actively sending queries to devices, or parsing configuration files of physical security devices, OT, IoT, and IT environments on assets, processes, and connectivity paths.
Threat Detection, Mitigation, and Response (+ Hunting)
Automation of threat analysis (signature-based, specification-based, anomaly-based, flow-based, content-based, sandboxing) not only in IT but also in relevant environments, e.g. physical, IoT, IIoT, and OT on assets, data, network, and orchestration with threat intelligence sharing and analytics.
Risk Assessment and Vulnerability Management
Risk scoring approach (qualitative, quantitative) based on variables such as behavioral patterns and geolocation. Patching and vulnerability management.
Usability, Architecture, Cost
The user and administrative experience, multiple deployment options, extensive integration capabilities, and affordability.
Source: Secure IT/OT Convergence, Info-Tech Research Group, 2022
Optimize
Establish, monitor, and report integrated security metrics
Security metrics serve various functions in a security program.1 For example:
- As audit requirements. For integrated security, the requirements are derived from mandatory or voluntary compliance, e.g. NERC CIP.
- As an indicator of maturity level. For integrated security, maturity level is used to measure the state of security, e.g. C2M2, CMMC.
- As a measurement of effectiveness and efficiency. Security metrics consist of operational metrics, financial metrics, etc.
Safety
Physical security interfaces with the physical world. Thus, metrics based on risks related to safety are crucial. These metrics motivate personnel by making clear why they should care about security.
Source: EPRI, 2017
Business Performance
The impact of security on the business can be measured with various metrics such as operational metrics, service level agreements (SLAs), and financial metrics.
Source: BMC, 2022
Technology Performance
Early detection leads to faster remediation and less damage. Metrics such as maximum tolerable downtime (MTD) and mean time to recovery (MTR) indicate system reliability.
Source: Dark Reading, 2022
Security Culture
Measure the overall quality of security culture with indicators such as compliance and audit, vulnerability management, and training and awareness.
Info-Tech Insight
Security failure can be avoided by evaluating the security systems and program. Security evaluation requires understanding what, where, when, and how to measure and to report the relevant metrics.
Related Info-Tech Research
Secure IT/OT Convergence
The previously entirely separate OT ecosystem is migrating into the IT ecosystem, primarily to improve access via connectivity and to leverage other standard IT capabilities for economic benefit.
Hence, IT and OT need to collaborate, starting with communication to build trust and to overcome their differences and followed by negotiation on components such as governance and management, security controls on OT environments, compliance with regulations and standards, and establishing metrics for OT security.
Preparing for Technology Convergence in Manufacturing
Information technology (IT) and operational technology (OT) teams have a long history of misalignment and poor communication.
Stakeholder expectations and technology convergence create the need to leave the past behind and build a culture of collaboration.
Build an Information Security Strategy
Info-Tech has developed a highly effective approach to building an information security strategy – an approach that has been successfully tested and refined for over seven years with hundreds of organizations.
This unique approach includes tools for ensuring alignment with business objectives, assessing organizational risk and stakeholder expectations, enabling a comprehensive current-state assessment, prioritizing initiatives, and building a security roadmap.
Bibliography
"1402-2021 - IEEE Guide for Physical Security of Electric Power Substations." IEEE, 2021. Accessed 25 Jan. 2023.
"2022 State of Protective Intelligence Report." Ontic Center for Protective Intelligence, 2022. Accessed 16 Jan. 2023.
"8 Staggering Statistics: Physical Security Technology Adoption." Brivo, 2022. Accessed 5 Jan. 2023.
"America's Water Infrastructure Act of 2018." The United States' Congress, 2018. Accessed 19 Jan. 2023.
Baker, Paul and Daniel Benny. The Complete Guide to Physical Security. Auerbach Publications. 2013
Bennett, Steve. "Physical Security Statistics 2022 - Everything You Need to Know." WebinarCare, 4 Dec. 2022. Accessed 30 Dec. 2022.
"Best Practices for Planning and Managing Physical Security Resources: An Interagency Security Committee Guide." Interagency Security Committee (ISC), Dec. 2015. Accessed 23 Jan. 2023.
Black, Daniel. "Improve Security Governance With a Security Steering Committee." Info-Tech Research Group, 23 Nov. 2018. Accessed 30 Jan. 2023.
Borg, Scott. "Don't Put Up Walls Between Your Security People." FedTech Magazine, 17 Feb. 2009. Accessed 15 Dec. 2022.
Burwash, John. “Preparing for Technology Convergence in Manufacturing.” Info-Tech Research Group, 12 Dec. 2018. Accessed 7 Dec. 2022.
Carney, John. "Why Integrate Physical and Logical Security?" Cisco. Accessed 19 Jan. 2023.
"Certification of Cyber Security Skills of ICS/SCADA Professionals." European Union Agency for Cybersecurity (ENISA), 2015. Accessed 27 Sep. 2022.
Cherdantseva, Yulia and Jeremy Hilton. "Information Security and Information Assurance. The Discussion about the Meaning, Scope and Goals." Organizational, Legal, and Technological Dimensions of IS Administrator, Almeida F., Portela, I. (eds.), pp. 1204-1235. IGI Global Publishing, 2013.
Cobb, Michael. "Physical security." TechTarget. Accessed 8 Dec. 2022.
“Conduct a Drinking Water or Wastewater Utility Risk Assessment.” United States Environmental Protection Agency (EPA), n.d. Web.
Conrad, Sandi. "Create and Implement an IoT Strategy." Info-Tech Research Group, 28 July 2022. Accessed 7 Dec. 2022.
Cooksley, Mark. "The IEC 62443 Series of Standards: A Product Manufacturer's Perspective." YouTube, uploaded by Plainly Explained, 27 Apr. 2021. Accessed 26 Aug. 2022.
"Cyber and physical security must validate their value in 2023." IFSEC Global, 12 Jan. 2023. Accessed 20 Jan. 2023.
"Cybersecurity Evaluation Tool (CSET®)." Cybersecurity and Infrastructure Security Agency (CISA). Accessed 23 Jan. 2023.
"Cybersecurity Maturity Model Certification (CMMC) 2.0." The United States' Department of Defense (DOD), 2021. Accessed 29 Dec. 2022.
“Cyber Security Metrics for the Electric Sector: Volume 3.” Electric Power Research Institute (EPRI), 2017.
Czachor, Emily. "Mass power outage in North Carolina caused by gunfire, repairs could take days." CBS News, 5 Dec. 2022. Accessed 20 Jan. 2023.
Dang, Robert, et al. “Secure IT/OT Convergence.” Info-Tech Research Group, 9 Dec. 2022. Web.
"Emergency Management Act (S.C. 2007, c. 15)." The Government of Canada, 2007. Accessed 19 Jan. 2023.
"Emergency management vocabulary." Translation Bureau, Government of Canada. Accessed 19 Jan. 2023.
Fennelly, Lawrence. Effective physical security. Butterworth-Heinemann, 2013.
Ghaznavi-Zadeh, Rassoul. "Enterprise Security Architecture - A Top-down Approach." The Information Systems Audit and Control Association (ISACA). Accessed 25 Jan. 2023.
"Good Practices for Security of Internet of Things." European Union Agency for Cybersecurity (ENISA), 2018. Accessed 27 Sep. 2022.
"Health and Safety at Work etc Act 1974." The United Kingdom Parliament. Accessed 23 Jan. 2023.
Hébert, Michel, et al. “Security Priorities 2023.” Info-Tech Research Group, 1 Feb. 2023. Web.
"History and Initial Formation of Physical Security and the Origin of Authority." Office of Research Services (ORS), National Institutes of Health (NIH). March 3, 2017. Accessed 19 Jan. 2023.
"IEC 62676-1-1:2013 Video surveillance systems for use in security applications - Part 1-1: System requirements - General." International Electrotechnical Commission (IEC), 2013. Accessed 9 Dec. 2022.
"Incident Command System (ICS)." ICS Canada. Accessed 17 Jan. 2023.
"Information Security Manual - Guidelines for Physical Security." The Australian Cyber Security Centre (ACSC), Dec. 2022. Accessed 13 Jan. 2023.
"Integrated Physical Security Framework." Anixter. Accessed 8 Dec. 2022.
"Integrating Risk and Security within a TOGAF® Enterprise Architecture." TOGAF 10, The Open Group. Accessed 11 Jan. 2023.
Latham, Katherine. "The microchip implants that let you pay with your hand." BBC News, 11 Apr. 2022. Accessed 12 Jan. 2023.
Linthicum, David. "2023 could be the year of public cloud repatriation." InfoWorld, 3 Jan. 2023. Accessed 10 Jan. 2023.
Ma, Alexandra. "Thousands of people in Sweden are embedding microchips under their skin to replace ID cards." Business Insider, 14 May 2018. Accessed 12 Jan. 2023.
Mendelssohn, Josh and Dana Tessler. "Take Control of Compliance Improvement to Conquer Every Audit." Info-Tech Research Group, 25 March 2015. Accessed 27 Jan. 2023.
Meredith, Sam. "All you need to know about the Nord Stream gas leaks - and why Europe suspects 'gross sabotage'." CNBC, 11 Oct. 2022. Accessed 20 Jan. 2023.
Nicaise, Vincent. "EU NIS2 Directive: what’s changing?" Stormshield, 20 Oct. 2022. Accessed 17 Nov. 2022.
"NIST SP 800-53 Rev. 5 Security and Privacy Controls for Information Systems and Organizations." The National Institute of Standards and Technology (NIST), 13 Jul. 2022. Accessed 27 Jan. 2023.
"North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) Series." NERC. Accessed 23 Jan. 2023.
"North America Physical Security Market - Global Forecast to 2026." MarketsandMarkets, June 2021. Accessed 30 Dec. 2022.
"NSTISSI No. 4011 National Training Standard For Information Systems Security (InfoSec) Professionals." The United States Committee on National Security Systems (CNSS), 20 Jun. 1994. Accessed 23 Jan. 2023.
"Occupational Safety and Health Administration (OSH) Act of 1970." The United States Department of Labor. Accessed 23 Jan. 2023.
Palter, Jay. "10 Mistakes Made in Designing a Physical Security Program." Real Time Networks, 7 Sep. 2022. Accessed 6 Jan. 2023.
Parker, Donn. Fighting Computer Crime. John Wiley & Sons, 1998.
Pathak, Parag. "What Is Threat Management? Common Challenges and Best Practices." Security Intelligence, 2020. Accessed 5 Jan. 2023.
Pender-Bey, Georgie. "The Parkerian Hexad." Lewis University, 2012. Accessed 24 Jan. 2023.
Philippou, Oliver. "2023 Trends to Watch: Physical Security Technologies." Omdia. Accessed 20 Jan. 2023.
Phinney, Tom. "IEC 62443: Industrial Network and System Security." ISA and Honeywell Integrated Security Technology Lab. Accessed 30 Jan. 2023.
"Physical Security Market, with COVID-19 Impact Analysis - Global Forecast to 2026." MarketsandMarkets, Jan. 2022. Accessed 30 Dec. 2022.
"Physical Security Professional (PSP)" ASIS International. Accessed 17 Jan. 2023.
"Physical Security Systems (PSS) Assessment Guide" The United States' Department of Energy (DOE), Dec. 2016. Accessed 23 Jan. 2023.
"Policies, Standards, Best Practices, Guidance, and White Papers." Interagency Security Committee (ISC). Accessed 23 Jan. 2023.
"Profiles, Add-ons and Specifications." ONVIF. Accessed 9 Dec. 2022.
"Protective Security Policy Framework (PSPF)." The Australian Attorney-General's Department (AGD). Accessed 13 Jan. 2023.
"Satellites detect methane plume in Nord Stream leak." The European Space Agency (ESA), 6 oct. 2022. Accessed 23 Jan. 2023.
""Satellites detect methane plume in Nord Stream leak." The European Space Agency (ESA), 6 oct. 2022. Accessed 23 Jan. 2023.
Satgunananthan, Niru. "Challenges in Security Convergence?" LinkedIn, 8 Jan. 2022. Accessed 20 Dec. 2022.
Sooknanan, Shastri and Isaac Kinsella. "Identify the Components of Your Cloud Security Architecture." Info-Tech Research Group, 12 March 2021. Accessed 26 Jan. 2023.
"TC 79 Alarm and electronic security systems." International Electrotechnical Commission (IEC), n.d. Accessed 9 Dec. 2022.
"The Risk Management Process for Federal Facilities: An Interagency Security Committee Standard." Interagency Security Committee (ISC), 2021. Accessed 26 Jan. 2023.
"The Short Guide to Why Security Programs Can Fail." CyberTalk, 23 Sep. 2021. Accessed 30 Dec. 2022.
Verton, Dan. "Companies Aim to Build Security Awareness." Computerworld, 27 Nov. 2022. Accessed 26 Jan. 2023.
"Vulnerability Assessment of Federal Facilities." The United States' Department of Justice, 28 Jun. 1995. Accessed 19 Jan. 2023.
"What is IEC 61508?" 61508 Association. Accessed 23 Jan. 2023.
Wolf, Gene. "Better Include Physical Security With Cybersecurity." T&D World 5 Jan. 2023. Accessed 19 Jan. 2023.
Wood, Kate, and Isaac Kinsella. “Build an Information Security Strategy.” Info-Tech Research Group, 9 Sept. 2020. Web.
Woolf, Tim, et al. "Benefit-Cost Analysis for Utility-Facing Grid Modernization Investments: Trends, Challenges, and Considerations." Lawrence Berkeley National Laboratory, Feb. 2021. Accessed 15 Nov. 2022.
"Work Health and Safety Act 2011." The Australian Government. Accessed 13 Jan. 2023.
Wu, Jing. “Industrial Control System Modernization: Unlock the Value of Automation in Utilities.” Info-Tech Research Group, 6 April 2023. Web.
Research Contributors and Experts
Amy L. Meger, IGP
Information and Cyber Governance Manager
Platte River Power Authority
Andrew Amaro
Chief Security Officer (CSO) & Founder
KLAVAN Security
Bilson Perez
IT Security Manager
4Wall Entertainment
Dan Adams
VP of Information Technology
4Wall Entertainment
Doery Abdou
Senior Manager
March Networks Corporate
Erich Krueger
Manager of Security Engineering
Omaha Public Power District
Kris Krishan
Head of IT
Waymo
Owen Yardley
Director, Facilities Security Preparedness
Omaha Public Power District
Buying Options
Integrate Physical Security and Information Security
IT Risk Management · IT Leadership & Strategy implementation · Operational Management · Service Delivery · Organizational Management · Process Improvements · ITIL, CORM, Agile · Cost Control · Business Process Analysis · Technology Development · Project Implementation · International Coordination · In & Outsourcing · Customer Care · Multilingual: Dutch, English, French, German, Japanese · Entrepreneur
Tymans Group is a brand by Gert Taeymans BV
Gert Taeymans bv
Europe: Koning Albertstraat 136, 2070 Burcht, Belgium — VAT No: BE0685.974.694 — phone: +32 (0) 468.142.754
USA: 4023 KENNETT PIKE, SUITE 751, GREENVILLE, DE 19807 — Phone: 1-917-473-8669
Copyright 2017-2022 Gert Taeymans BV