
Security Priorities 2022
- Ransomware activities and the cost of breaches are on the rise.
- Cybersecurity talent is hard to find, and an increasing number of cybersecurity professionals are considering leaving their jobs.
- Moving to the digital world increases the risk of a breach.
Our Advice
Critical Insight
- The pandemic has fundamentally changed the technology landscape. Security programs must understand how their threat surface is now different and adapt their controls to meet the challenge.
- The upside to the upheaval in 2021 is new opportunities to modernize your security program.
Impact and Result
- Use the report to ensure your plan in 2022 addresses what’s important in cybersecurity.
- Understand the current situation in the cybersecurity space.
Security Priorities 2022 Research & Tools
Besides the small introduction, subscribers and consulting clients within this management domain have access to:
1. Security Priorities 2022 – A report that describes priorities and recommendations for CISOs in 2022.
Use this report to understand the current situation in the cybersecurity space and inform your plan for 2022. This report includes sections on protecting against and responding to ransomware, acquiring and retaining talent, securing a remote workforce, securing digital transformation, and adopting zero trust.
- Security Priorities for 2022 Report
Infographic
Further reading
Security Priorities 2022
The pandemic has changed how we work
disruptions to the way we work caused by the pandemic are here to stay.
The pandemic has introduced a lot of changes to our lives over the past two years, and this is also true for various aspects of how we work. In particular, a large workforce moved online overnight, which shifted the work environment rapidly.
People changed how they communicate, how they access company information, and how they connect to the company network. These changes make cybersecurity a more important focus than ever.
Although changes like the shift to remote work occurred in response to the pandemic, they are largely expected to remain, regardless of the progression of the pandemic itself. This report will look into important security trends and the priorities that stemmed from these trends.
30% more professionals expect transformative permanent change compared to one year ago.
47% of professionals expect a lot of permanent change; this remains the same as last year. (Source: Info-Tech Tech Trends 2022 Survey; N=475)
The cost of a security breach is rising steeply
The shift to remote work exposes organizations to more costly cyber incidents than ever before.
$4.24 millionAverage cost of a data breach in 2021 |
The cost of a data breach rose by nearly 10% in the past year, the highest rate in over seven years. |
$1.07 millionMore costly when remote work involved in the breach |
The average cost of breaches where remote work is involved is $1.07 million higher than breaches where remote work is not involved. The ubiquitous remote work that we saw in 2021 and continue to see in 2022 can lead to more costly security events. (Source: IBM, 2021) |
Remote work is here to stay, and the cost of a breach is higher when remote work is involved.
The cost comes not only directly from payments but also indirectly from reputational loss. (Source: IBM, 2021)
Security teams can participate in the solution
The numbers are clear: in 2022, when we face a threat environment like WE’VE never EXPERIENCED before, good security is worth the investment
$1.76 millionSaved when zero trust is deployed facing a breach |
Zero trust controls are realistic and effective controls. Organizations that implement zero trust dramatically reduce the cost of an adverse security event. |
35%More costly if it takes more than 200 days to identify and contain a breach |
With increased BYOD and remote work, detection and response is more challenging than ever before – but it is also highly effective. Organizations that detect and respond to incidents quickly will significantly reduce the impact. (Source: IBM, 2021) |
Breaches are 34% less costly when mature zero trust is implemented.
A fully staffed and well-prepared security team could save the cost through quick responses. (Source: IBM, 2021)
Top security priorities and constraints in 2022
Survey results
As part of its research process for the 2022 Security Priorities Report, Info-Tech Research Group surveyed security and IT leaders (N=97) to ask their top security priorities as well as their main obstacles to security success in 2022:
Top Priorities
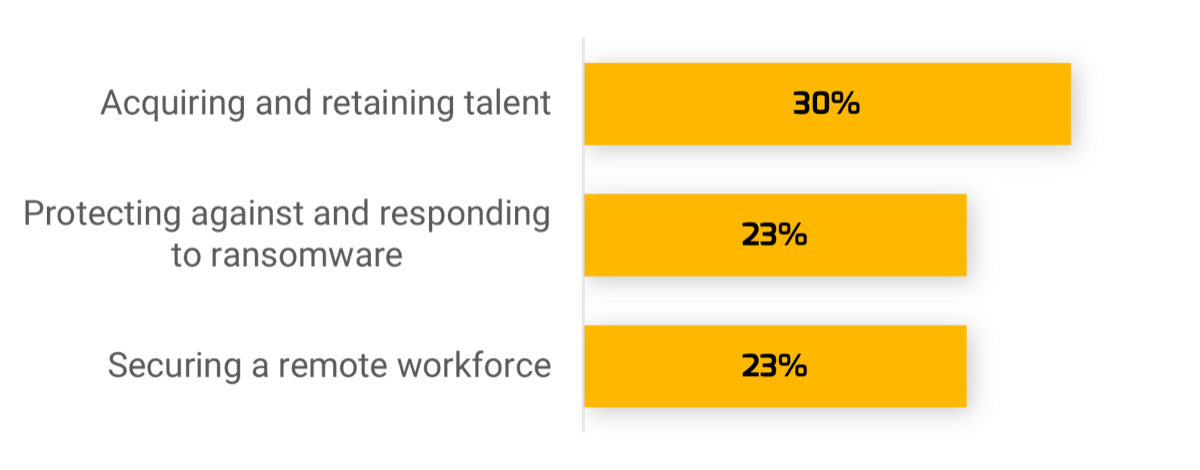
Survey respondents were asked to force-rank their security priorities. Among the priorities chosen most frequently as #1 were talent management, addressing ransomware threats, and securing hybrid/remote work. |
Top Obstacles
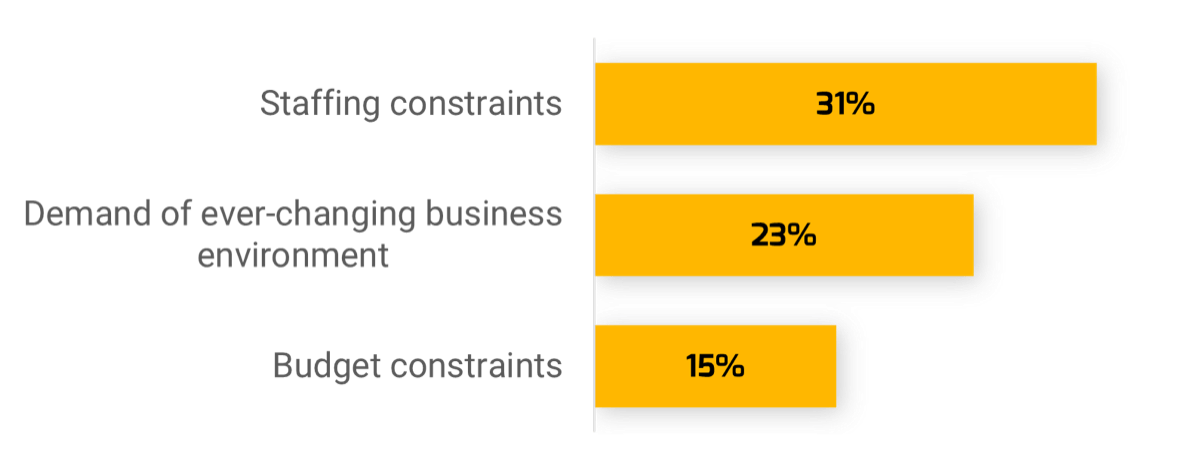
Talent management is both the #1 priority and the top obstacle facing security leaders in 2022. Unsurprisingly, the ever-changing environment in a world emerging from a pandemic and budget constraints are also top obstacles. |
We know the priorities…
But what are security leaders actually working on?
This report details what we see the world demanding of security leaders in the coming year.
Setting aside the demands – what are security leaders actually working on?
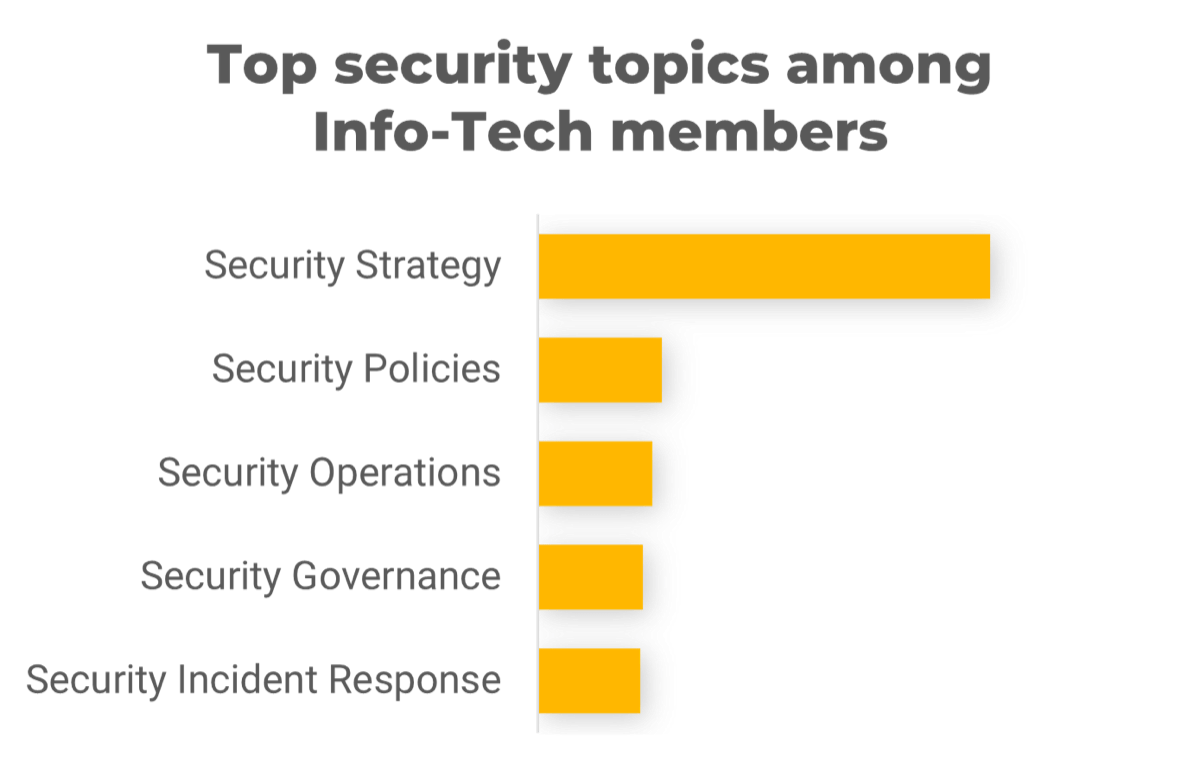 |
Many organizations are still mastering the foundations of a mature cybersecurity program. This is a good idea! Most breaches are still due to gaps in foundational security, not lack of advanced controls. |
We know the priorities…
But what are security leaders actually working on?
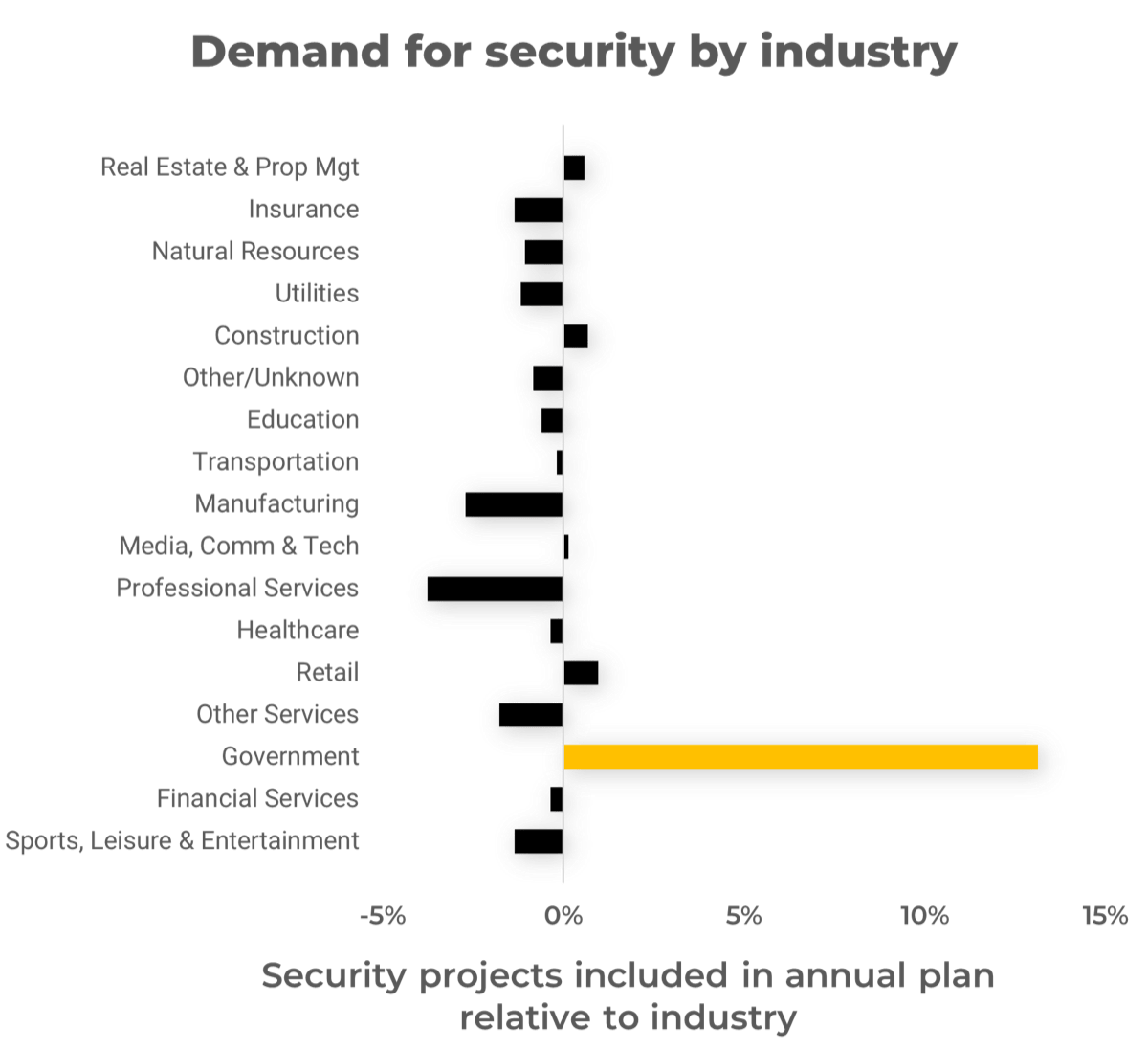 |
One industry plainly stands out from the rest. Government organizations are proportionally much more active in security than other industries, and for good reason: they are common targets. Manufacturing and professional services are proportionally less interested in security. This is concerning, given the recent targeting of supply chain and personal data holders by ransomware gangs. |
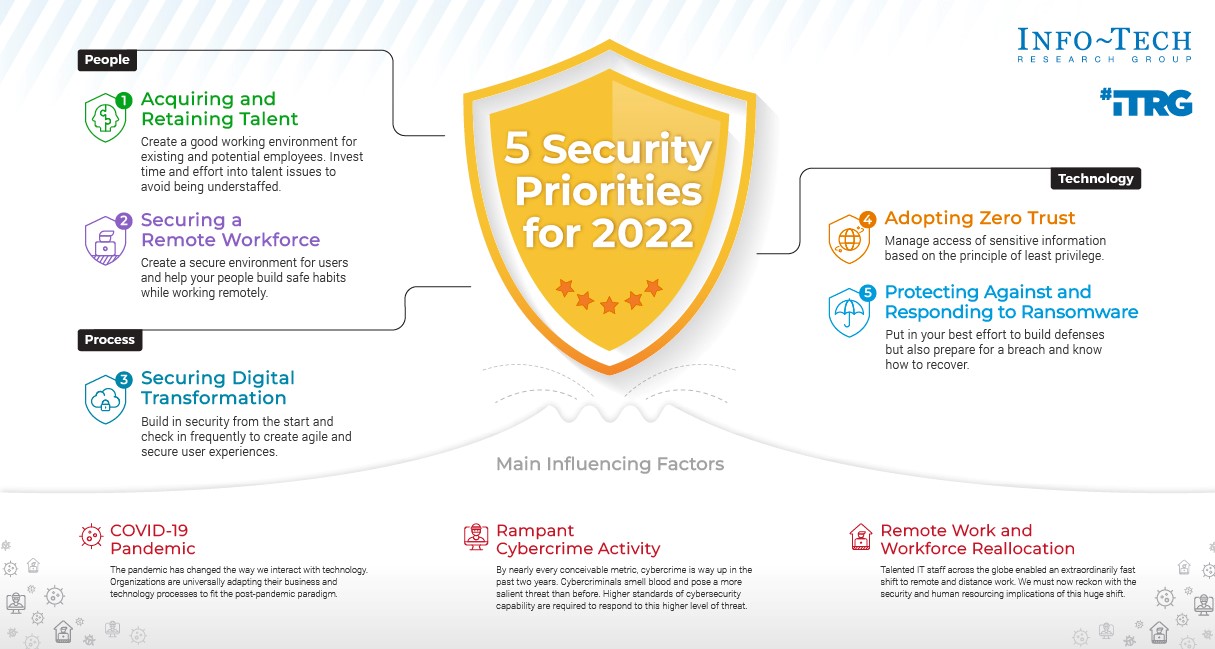
5 Security Priorities for 2022 

People
- Acquiring and Retaining Talent
Create a good working environment for existing and potential employees. Invest time and effort into talent issues to avoid being understaffed. - Securing a Remote Workforce
Create a secure environment for users and help your people build safe habits while working remotely.
Process
- Securing Digital Transformation
Build in security from the start and check in frequently to create agile and secure user experiences.
Technology
- Adopting Zero Trust
Manage access of sensitive information based on the principle of least privilege. - Protecting Against and Responding to Ransomware
Put in your best effort to build defenses but also prepare for a breach and know how to recover.
Main Influencing Factors |
||
| COVID-19 Pandemic
The pandemic has changed the way we interact with technology. Organizations are universally adapting their business and technology processes to fit the post-pandemic paradigm. |
Rampant Cybercrime Activity
By nearly every conceivable metric, cybercrime is way up in the past two years. Cybercriminals smell blood and pose a more salient threat than before. Higher standards of cybersecurity capability are required to respond to this higher level of threat. |
Remote Work and Workforce Reallocation
Talented IT staff across the globe enabled an extraordinarily fast shift to remote and distance work. We must now reckon with the security and human resourcing implications of this huge shift. |
Acquire and Retain Talent
Priority 01
Security talent was in short supply before the pandemic, and it's even worse now.
Executive summary
Background
Cybersecurity talent has been in short supply for years, but this shortage has inflected upward since the pandemic.
The Great Resignation contributed to the existing talent gap. The pandemic has changed how people work as well as how and where they choose work. More and more senior workers are retiring early or opting for remote working opportunities.
The cost to acquire cybersecurity talent is huge, and the challenge doesn’t end there. Retaining top talent can be equally difficult.
Current situation
- A 2021 survey by ESG shows that 76% of security professional agree it’s difficult to recruit talent, and 57% said their organization is affected by this talent shortage.
- (ISC)2 reports there are 2.72 million unfilled job openings and an increasing workforce gap (2021).
2.72 million unfilled cybersecurity openings (Source: (ISC)2, 2021)
IT leaders must do more to attract and retain talent in 2022
- Over 70% of IT professionals are considering quitting their jobs (TalentLMS, 2021). Meanwhile, 51% of surveyed cybersecurity professionals report extreme burnout during the last 12 months and many of them have considered quitting because of it (VMWare, 2021).
- Working remotely makes it easier for people to look elsewhere, lowering the barrier to leaving.
- This is a big problem for security leaders, as cybersecurity talent is in very short supply. The cost of acquiring and retaining quality cybersecurity staff in 2022 is significant, and many organizations are unwilling or unable to pay the premium.
- Top talent will demand flexible working conditions – even though remote work comes with security risk.
- Most smart, talented new hires in 2022 are demanding to work remotely most of the time.
| Burnout | 30% |
| Other remote opportunities | 20% |
| Lack of growth opportunities | 20% |
| Poor culture | 20% |
| Acquisition concerns | 10% |
Talent will be 2022’s #1 strength and #1 weakness
| Staffing obstacles in 2022:
“Attracting and retaining talent is always challenging. We don’t pay as well and my org wants staff in the office at least half of the time. Most young, smart, talented new hires want to work remotely 100 percent of the time.“ “Trying to grow internal resources into security roles.” “Remote work expectations by employees and refusal by business to accommodate.” “Biggest obstacle: payscales that are out of touch with cybersecurity market.” “Request additional staff. Obtaining funding for additional position is most significant obstacle.” (Info-Tech Tech Security Priorities Survey 2022) |
Top obstacles in 2022:
As you can see, respondents to our security priorities survey have strong feelings on the challenges of staffing a cybersecurity team. The growth of remote work means local talent can now be hired by anybody, vastly increasing your competition as an employer. Hiring local will get tougher – but so will hiring abroad. People who don’t want to relocate for a new job now have plenty of alternatives. Without a compelling remote work option, you will find non-local prospects unwilling to move for a new job. Lastly, many organizations are still reeling at the cost of experienced cybersecurity talent. Focused internal training and development will be the answer for many organizations. |
Recommended Actions
| Provide career development opportunities
Many security professionals are dissatisfied with their unclear career development paths. To improve retention, organizations should provide their staff with opportunities and clear paths for career and skills advancement. |
Be open-minded when hiring
To broaden the candidate pool, organizations should be open-minded when considering who to hire.
|
| Facilitate work-life balance
Many security professionals say they experience burnout. Promoting work-life balance in your organization can help retain critical skills. |
Create inclusive environment
Hire a diverse team and create an inclusive environment where they can thrive. |
Talent acquisition and retention plan
Use this template to explain the priorities you need your stakeholders to know about.
Provide a brief value statement for the initiative.
Address a top priority and a top obstacle with a plan to attract and retain top organizational and cybersecurity talent.
Initiative Description:
|
Description must include what IT will undertake to complete the initiative. | |||
Primary Business Benefits:
Reduction in costs due to turnover and talent loss |
Other Expected Business Benefits:
|
Align initiative benefits back to business benefits or benefits for the stakeholder groups that it impacts. | ||
Risks:
|
Related Info-Tech Research: |
|||
Secure a Remote Workforce
Priority 02
Trends suggest remote work is here to stay. Addressing the risk of insecure endpoints can no longer be deferred.
Executive summary
Remote work poses unique challenges to cybersecurity teams. The personal home environment may introduce unauthorized people and unknown network vulnerabilities, and the organization loses nearly all power and influence over the daily cyber hygiene of its users.
In addition, the software used for enabling remote work itself can be a target of cybersecurity criminals.
Current situation
- 70% of workers in technical services work from home.
- Employees of larger firms and highly paid individuals are more likely to be working outside the office.
- 80% of security and business leaders find that remote work has increased the risk of a breach. (Source: StatCan, 2021)
70% of tech workers work from home (Source: Statcan, 2021)
Remote work demands new security solutions
The security perimeter is finally goneThe data is outside the datacenter.
Organizations that did not implement digital transformation changes following COVID-19 experience higher costs following a breach, likely because it is taking nearly two months longer, on average, to detect and contain a breach when more than 50% of staff are working remotely (IBM, 2021). In 2022 the cumulative risk of so many remote connections means we need to rethink how we secure the remote/hybrid workforce. |
Security
|
 |
Network
|
Recommended Actions
| Mature your identity management
Compromised identity is the main vector to breaches in recent years. Stale accounts, contractor accounts, misalignment between HR and IT – the lack of foundational practices leads to headline-making breaches every week.
|
Get a handle on your endpoints
Work-from-home (WFH) often means unknown endpoints on unknown networks full of other unknown devices…and others in the home potentially using the workstation for non-work purposes. Gaining visibility into your endpoints can help to keep detection and resolution times short. |
| Educate users
Educate everyone on security best practices when working remotely:
|
Ease of use
Many workers complain that the corporate technology solution makes it difficult to get their work done. Employees will take productivity over security if we force them to choose, so IT needs to listen to end users’ needs and provide a solution that is nimble and secure. |
Roadmap to securing remote/hybrid workforce
Use this template to explain the priorities you need your stakeholders to know about.
Provide a brief value statement for the initiative.
The corporate network now extends to the internet – ensure your security plan has you covered.
Initiative Description:
| Description must include what IT will undertake to complete the initiative. | |||
Primary Business Benefits: | Other Expected Business Benefits:
| Align initiative benefits back to business benefits or benefits for the stakeholder groups that it impacts. | ||
Risks:
| Related Info-Tech Research: | |||
Secure Digital Transformation
Priority 03
Digital transformation could be a competitive advantage…or the cause of your next data breach.
Executive summary
Background
Digital transformation is occurring at an ever-increasing rate these days. As Microsoft CEO Satya Nadella said early in the pandemic, “We’ve seen two years’ worth of digital transformation in two months.”
We have heard similar stories from Info-Tech members who deployed rollouts that were scheduled to take months over a weekend instead.
Microsoft’s own shift to rapidly expand its Teams product is a prime example of how quickly the digital landscape has changed. The global adaption to a digital world has largely been a success story, but rapid change comes with risk, and there is a parallel story of rampant cyberattacks like we have never seen before.
Insight
There is an adage that “slow is smooth, and smooth is fast” – the implication being that fast is sloppy. In 2022 we’ll see a pattern of organizations working to catch up their cybersecurity with the transformations we all made in 2020.
$1.78 trillion expected in digital transformation investments (Source: World Economic Forum, 2021)
An ounce of security prevention versus a pound of cure
The journey of digital transformation is a risky one.
| Digital transformations often rely heavily on third-party cloud service providers, which increases exposure of corporate data.
Further, adoption of new technology creates a new threat surface that must be assessed, mitigations implemented, and visibility established to measure performance. However, digital transformations are often run on slim budgets and without expert guidance. Survey respondents report as much: rushed deployments, increased cloud migration, and shadow IT are the top vulnerabilities reported by security leaders and executives. |
In a 2020 Ponemon survey, 82% of IT security and C-level executives reported experiencing at least one data breach directly resulting from a digital transformation they had undergone. Scope creep is inevitable on any large project like a digital transformation. A small security shortcut early in the project can have dire consequences when it grows to affect personal data and critical systems down the road. |
Recommended Actions
| Engage the business early and often
Despite the risks, organizations engage in digital transformations because they also have huge business value. Security leaders should not be seeking to slow or stop digital transformations; rather, we should be engaging with the business early to get ahead of risks and enable successful transformation. |
Establish a vendor security program
Data is moving out of datacenters and onto third-party environments. Without security requirements built into agreements, and clear visibility into vendor security capabilities, that data is a major source of risk. A robust vendor security program will create assurance early in the process and help to reinforce the responsibility of securing data with other parts of the organization. |
| Build/revisit your security strategy
The threat surface has changed since before your transformation. This is the right time to revisit or rebuild your security strategy to ensure that your control set is present throughout the new environment – and also a great opportunity to show how your current security investments are helping secure your new digital lines of business! |
Educate your key players
Only 16% of security leaders and executives report alignment between security and business processes during digital transformation. If security is too low a priority, then key players in your transformation efforts are likely unaware of how security risks impact their own success. It will be incumbent upon the CISO to start that conversation. |
Securing digital transformation
Use this template to explain the priorities you need your stakeholders to know about.
Provide a brief value statement for the initiative.
Ensure your investment in digital transformation is appropriately secured.
Initiative Description:
| Description must include what IT will undertake to complete the initiative. | |||
Primary Business Benefits: | Other Expected Business Benefits:
| Align initiative benefits back to business benefits or benefits for the stakeholder groups that it impacts. | ||
Risks:
| Related Info-Tech Research: | |||
Adopt Zero Trust
Priority 04
Governments are recognizing the importance of zero trust strategies. So should your organization.
Why now for zero trust?
John Kindervag modernized the concept of zero trust back in 2010, and in the intervening years there has been enormous interest in cybersecurity circles, yet in 2022 only 30% of organizations report even beginning to roll out zero trust capabilities (Statista, 2022).
Why such little action on a revolutionary and compelling model?
Zero trust is not a technology; it is a principle. Zero trust adoption takes concerted planning, effort, and expense, for which the business value has been unclear throughout most of the last 10 years. However, several recent developments are changing that:
- Securing technology has become very hard! The size, complexity, and attack surface of IT environments has grown significantly – especially since the pandemic.
- Cyberattacks have become rampant as the cost to deploy harmful ransomware has become lower and the impact has become higher.
- The shift away from on-premises datacenters and offices created an opening for zero trust investment, and zero trust technology is more mature than ever before.
The time has come for zero trust adoption to begin in earnest.
97% will maintain or increase zero trust budget (Source: Statista, 2022)
Traditional perimeter security is not working
Zero trust directly addresses the most prevalent attack vectors today
A hybrid workforce using traditional VPN creates an environment where we are exposed to all the risks in the wild (unknown devices at any location on any network), but at a stripped-down security level that still provides the trust afforded to on-premises workers using known devices.
What’s more, threats such as ransomware are known to exploit identity and remote access vulnerabilities before moving laterally within a network – vectors that are addressed directly by zero trust identity and networking. Ninety-three percent of surveyed zero trust adopters state that the benefits have matched or exceeded their expectations (iSMG, 2022).
Top reasons for building a zero trust program in 2022
(Source: iSMG, 2022)44%Enforce least privilege access to critical resources |
44%Reduce attacker ability to move laterally |
41%Reduce enterprise attack surface |
The business case for zero trust is clearer than ever
Prior obstacles to Zero Trust are disappearing
A major obstacle to zero trust adoption has been the sheer cost, along with the lack of business case for that investment. Two factors are changing that paradigm in 2022:
The May 2021 US White House Executive Order for federal agencies to adopt zero trust architecture finally placed zero trust on the radar of many CEOs and board members, creating the business interest and willingness to consider investing in zero trust.
In addition, the cost of adopting zero trust is quickly being surpassed by the cost of not adopting zero trust, as cyberattacks become rampant and successful zero trust deployments create a case study to support investment.
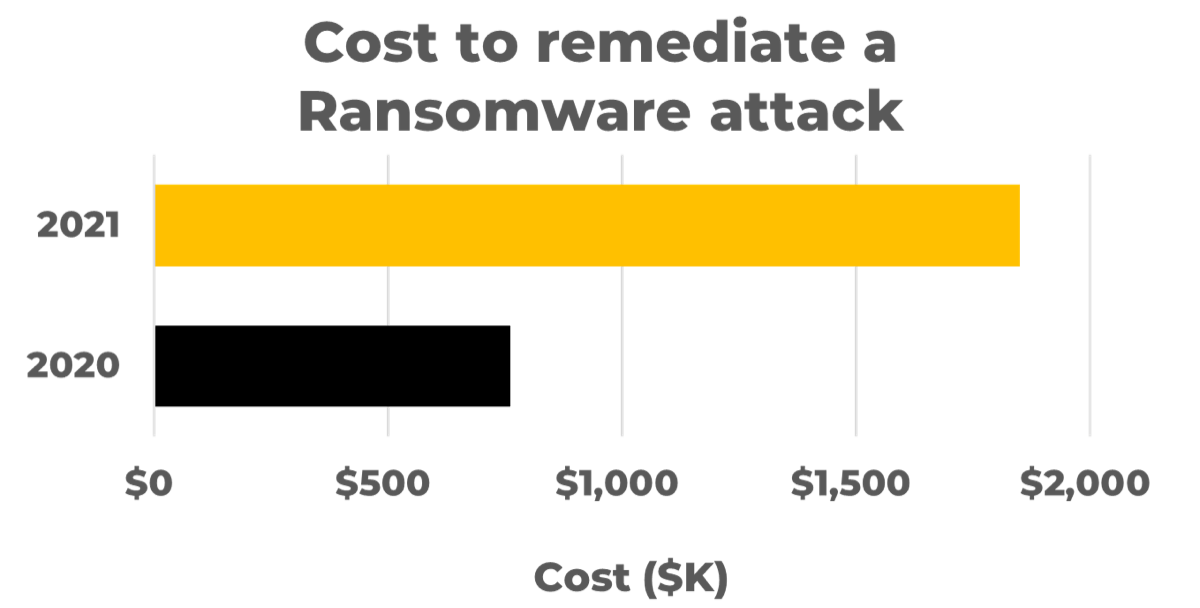 |
The cost to remediate a ransomware attack more than doubled from 2020 to 2021. Widespread adoption of zero trust capabilities could keep that number from doubling again in 2022. (Source: Sophos, 2021) |
The cost of a data breach is on average $1.76 million less for organizations with mature zero trust deployments.
That is, the cost of a data breach is 35% reduced compared to organizations without zero trust controls. (Source: IBM, 2021)
Recommended Actions
| Start small
Don’t put all your eggs in one basket by deploying zero trust in a wide swath. Rather, start as small as possible to allow for growing pains without creating business friction (or sinking your project altogether). |
Build a sensible roadmap
Zero trust principles can be applied in a myriad of ways, so where should you start? Between identities, devices, networking, and data, decide on a use case to do pilot testing and then refine your approach. |
| Beware too-good-to-be-true products
Zero trust is a powerful buzzword, and vendors know it. Be skeptical and do your due diligence to ensure your new security partners in zero trust are delivering what you need. |
Zero trust roadmap
Use this template to explain the priorities you need your stakeholders to know about.
Provide a brief value statement for the initiative.
Develop a practical roadmap that shows the business value of security investment.
Initiative Description:
| Description must include what IT will undertake to complete the initiative. | ||||
Primary Business Benefits: | Other Expected Business Benefits:
| Align initiative benefits back to business benefits or benefits for the stakeholder groups that it impacts. | |||
Risks:
| Related Info-Tech Research: | ||||
Protect Against and Respond to Ransomware
Priority 05
Ransomware is still the #1 threat to the safety of your data.
Executive summary
Background
- Ransomware attacks have transformed in 2021 and show no sign of slowing in 2022. There is a new major security breach every week, despite organizations spending over $150 billion in a year on cybersecurity (Nasdaq, 2021).
- Ransomware as a service (RaaS) is commonplace, and attackers are doubling down by holding encrypted data ransom and also demanding payment under threat to disclose exfiltrated data – and they are making good on their threats.
- The global cost of ransomware is expected to rise to $265 billion by 2031 (Cybersecurity Ventures, 2021).
- We expect to see an increase in ransomware incidents in 2022, both in severity and volume – multiple attacks and double extortion are now the norm.
- High staff turnover increases risk because new employees are unfamiliar with security protocols.
150% increase ransomware attacks in 2020 (Source: ENISA)
This is a new golden age of ransomware
| What is the same in 2022
Unbridled ransomware attacks make it seem like attackers must be using complex new techniques, but prevalent ransomware attack vectors are actually well understood. Nearly all modern variants are breaching victim systems in one of three ways:
|
What is new in 2022
The sophistication of victim targetingVictims often find themselves asking, “How did the attackers know to phish the most security-oblivious person in my staff?” Bad actors have refined their social engineering and phishing to exploit high-risk individuals, meaning your chain is only as strong as the weakest link. Ability of malware to evade detectionModern ransomware is getting better at bypassing anti-malware technology, for example, through creative techniques such as those seen in the MedusaLocker variant and in Ghost Control attacks. Effective anti-malware is still a must-have control, but a single layer of defense is no longer enough. Any organization that hopes to avoid paying a ransom must prepare to detect, respond, and recover from an attack. |
Many leaders still don’t know what a ransomware recovery would look like
| Do you know what it would take to recover from a ransomware incident?
…and does your executive leadership know what it would take to recover? The organizations that are most likely to pay a ransom are unprepared for the reality of recovering their systems. If you have not done a tabletop or live exercise to simulate a true recovery effort, you may be exposed to more risk than you realize. |
Are your defenses sufficiently hardened against ransomware?
Organizations with effective security prevention are often breached by ransomware – but they are prepared to contain, detect, and eradicate the infection. Ask yourself whether you have identified potential points of entry for ransomware. Assume that your security controls will fail. How well are your security controls layered, and how difficult would it be for an attacker to move east/west within your systems? |
Recommended Actions
| Be prepared for a breach
There is no guarantee that an organization will not fall victim to ransomware, so instead of putting all their effort into prevention, organizations should also put effort into planning to respond to a breach. |
Security awareness training/phishing detection
Phishing continues to be the main point of entry for ransomware. Investing in phishing awareness and detection among your end users may be the most impactful countermeasure you can implement. |
| Zero trust adoption
Always verify at every step of interaction, even when access is requested by internal users. Manage access of sensitive information based on the principle of least privilege access. |
Encrypt and back up your data
Encrypt your data so that even if there is a breach, the attackers don’t have a copy of your data. Also, keep regular backups of data at a separate location so that you still have data to work with after a breach occurs. You never want to pay a ransom. Being prepared to deal with an incident is your best chance to avoid paying! |
Prevent and respond to ransomware
Use this template to explain the priorities you need your stakeholders to know about.
Provide a brief value statement for the initiative.
Determine your current readiness, response plan, and projects to close gaps.
Initiative Description:
| Description must include what IT will undertake to complete the initiative. | |||
Primary Business Benefits: | Other Expected Business Benefits:
| Align initiative benefits back to business benefits or benefits for the stakeholder groups that it impacts. | ||
Risks:
| Related Info-Tech Research: | |||
Deepfakes: Dark-horse threat for 2022
Deepfake video
How long has it been since you’ve gone a full workday without having a videoconference with someone?
We have become inherently trustful that the face we see on the screen is real, but the technology required to falsify that video is widely available and runs on commercially available hardware, ushering in a genuinely post-truth online era.
Criminals can use deepfakes to enhance social engineering, to spread misinformation, and to commit fraud and blackmail.
Deepfake audio
Many financial institutions have recently deployed voiceprint authentication. TD describes its VoicePrint as “voice recognition technology that allows us to use your voiceprint – as unique to you as your fingerprint – to validate your identity” over the phone.
However, hackers have been defeating voice recognition for years already. There is ripe potential for voice fakes to fool both modern voice recognition technology and the accounts payable staff.
Bibliography
“2021 Ransomware Statistics, Data, & Trends.” PurpleSec, 2021. Web.
Bayern, Macy. “Why 60% of IT security pros want to quit their jobs right now.” TechRepublic, 10 Oct. 2018. Web.
Bresnahan, Ethan. “How Digital Transformation Impacts IT And Cyber Risk Programs.” CyberSaint Security, 25 Feb. 2021. Web.
Clancy, Molly. “The True Cost of Ransomware.” Backblaze, 9 Sept. 2021.Web.
“Cost of a Data Breach Report 2021.” IBM, 2021. Web.
Cybersecurity Ventures. “Global Ransomware Damage Costs To Exceed $265 Billion By 2031.” Newswires, 4 June 2021. Web.
“Digital Transformation & Cyber Risk: What You Need to Know to Stay Safe.” Ponemon Institute, June 2020. Web.
“Global Incident Response Threat Report: Manipulating Reality.” VMware, 2021.
Granger, Diana. “Karmen Ransomware Variant Introduced by Russian Hacker.” Recorded Future, 18 April 2017. Web.
“Is adopting a zero trust model a priority for your organization?” Statista, 2022. Web.
“(ISC)2 Cybersecurity Workforce Study, 2021: A Resilient Cybersecurity Profession Charts the Path Forward.” (ISC)2, 2021. Web.
Kobialka, Dan. “What Are the Top Zero Trust Strategies for 2022?” MSSP Alert, 10 Feb. 2022. Web.
Kost, Edward. “What is Ransomware as a Service (RaaS)? The Dangerous Threat to World Security.” UpGuard, 1 Nov. 2021. Web.
Lella, Ifigeneia, et al., editors. “ENISA Threat Landscape 2021.” ENISA, Oct. 2021. Web.
Mello, John P., Jr. “700K more cybersecurity workers, but still a talent shortage.” TechBeacon, 7 Dec. 2021. Web.
Naraine, Ryan. “Is the ‘Great Resignation’ Impacting Cybersecurity?” SecurityWeek, 11 Jan. 2022. Web.
Oltsik, Jon. “ESG Research Report: The Life and Times of Cybersecurity Professionals 2021 Volume V.” Enterprise Security Group, 28 July 2021. Web.
Osborne, Charlie. “Ransomware as a service: Negotiators are now in high demand.” ZDNet, 8 July 2021. Web.
Osborne, Charlie. “Ransomware in 2022: We’re all screwed.” ZDNet, 22 Dec. 2021. Web.
“Retaining Tech Employees in the Era of The Great Resignation.” TalentLMS, 19 Oct. 2021. Web.
Rubin, Andrew. “Ransomware Is the Greatest Business Threat in 2022.” Nasdaq, 7 Dec. 2021. Web.
Samartsev, Dmitry, and Daniel Dobrygowski. “5 ways Digital Transformation Officers can make cybersecurity a top priority.“ World Economic Forum, 15 Sept. 2021. Web.
Seymour, John, and Azeem Aqil. “Your Voice is My Passport.” Presented at black hat USA 2018.
Solomon, Howard. “Ransomware attacks will be more targeted in 2022: Trend Micro.” IT World Canada, 6 Jan. 2022. Web.
“The State of Ransomware 2021.” Sophos, April 2021. Web.
Tarun, Renee. “How The Great Resignation Could Benefit Cybersecurity.” Forbes Technology Council, Forbes, 21 Dec. 2021. Web.
“TD VoicePrint.” TD Bank, n.d. Web.
“Working from home during the COVID-19 pandemic, April 202 to June 2021.” Statistics Canada, 4 Aug. 2021. Web.
“Zero Trust Strategies for 2022.” iSMG, Palo Alto Networks, and Optiv, 28 Jan. 2022. Web.
