Prevent Data Loss Across Cloud and Hybrid Environments
- Organizations are often beholden to compliance obligations that require protection of sensitive data.
- All stages of the data lifecycle exist in the cloud and all stages provide opportunity for data loss.
- Organizations must find ways to mitigate insider threats without impacting legitimate business access.
Our Advice
Critical Insight
- Data loss prevention is the outcome of a well-designed strategy that incorporates multiple, sometimes disparate, tools within your existing security program.
- The journey to data loss prevention is complex and should be taken in small and manageable steps.
Impact and Result
- Organizations will achieve data comprehension.
- Organizations will align DLP with their current security program and architecture.
- A DLP strategy will be implemented with a distinct goal in mind.
Prevent Data Loss Across Cloud and Hybrid Environments Research & Tools
Besides the small introduction, subscribers and consulting clients within this management domain have access to:
1. Prevent Data Loss Across Cloud and Hybrid Environments Storyboard – A guide to handling data loss prevention in cloud services.
This research describes an approach to strategize and implement DLP solutions for cloud services.
- Prevent Data Loss Across Cloud and Hybrid Environments Storyboard
2. Data Loss Prevention Strategy Planner – A workbook designed to guide you through identifying and prioritizing your data and planning what DLP actions should be applied to protect that data.
Use this tool to identify and prioritize your data, then use that information to make decisions on DLP strategies based on classification and data environment.
- Data Loss Prevention Strategy Planner
Further reading
Prevent Data Loss Across Cloud and Hybrid Environments
Leverage existing tools and focus on the data that matters most to your organization.
Analyst Perspective
Data loss prevention is an additional layer of protection
Driven by reduced operational costs and improved agility, the migration to cloud services continues to grow at a steady rate. A recent report by Palo Alto Networks indicates workload in the cloud increased by 13% last year, and companies are expecting to move an additional 11% of their workload to the cloud in the next 24 months1.
However, moving to the cloud poses unique challenges for cyber security practitioners. Cloud services do not offer the same level of management and control over resources as traditional IT approaches. The result can be reduced visibility of data in cloud services and reduced ability to apply controls to that data, particularly data loss prevention (DLP) controls.
It’s not unusual for organizations to approach DLP as a point solution. Many DLP solutions are marketed as such. The truth is, DLP is a complex program that uses many different parts of an organization’s security program and architecture. To successfully implement DLP for data in the cloud, an organization should leverage existing security controls and integrate DLP tools, whether newly acquired or available in cloud services, with its existing security program.

Bob Wilson
CISSP
Research Director, Security and Privacy
Info-Tech Research Group
Executive Summary
Your ChallengeOrganizations must prevent the misuse and leakage of data, especially sensitive data, regardless of where it’s stored. Organizations often have compliance obligations requiring protection of sensitive data. All stages of the data lifecycle exist in the cloud and all stages provide opportunity for data loss. Organizations must find ways to mitigate insider threats without impacting legitimate business access. |
Common ObstaclesMany organizations must handle a plethora of data in multiple varied environments. Organizations don’t know enough about the data they use or where it is located. Different systems offer differing visibility. Necessary privileges and access can be abused. |
Info-Tech’s ApproachThe path to data loss prevention is complex and should be taken in small and manageable steps. First, organizations must achieve data comprehension. Organizations must align DLP with their current security program and architecture. Organizations need to implement DLP with a distinct goal in mind. Once the components are in place it’s important to measure and improve. |
Info-Tech Insight
Data loss prevention is the outcome of a well-designed strategy that incorporates multiple, sometimes disparate, tools within your existing security program.
Your challenge
Protecting data is a critical responsibility for organizations, no matter where it is located.
45% of breaches occurred in the cloud (“Cost of a Data Breach 2022,” IBM Security, 2022).
It can take upwards of 12 weeks to identify and contain a breach (“Cost of a Data Breach 2022,” IBM Security, 2022).
- Compliance obligations will require organizations to protect certain data.
- All data states can exist in the cloud, and each state provides a unique opportunity for data loss.
- Insider threats, whether intentional or not, are especially challenging for organizations. It’s necessary to prevent illicit data use while still allowing work to happen.
Info-Tech Insight
Data loss prevention doesn’t depend on a single tool. Many of the leading cloud service providers offer DLP controls with their services and these controls should be considered.
Common obstacles
As organizations increasingly move data into the cloud, their environments become more complex and vulnerable to insider threats
- It’s not uncommon for an organization not to know what data they use, where that data exists, or how they are supposed to protect it.
- Cloud systems, especially software as a service (SaaS) applications, may not provide much visibility into how that data is stored or protected.
- Insider threats are a primary concern, but employees must be able to access data to perform their duties. It isn’t always easy to strike a balance between adequate access and being too restrictive with controls.
Insider threats are a significant concern
53%53% of a study’s respondents think it is more difficult to detect insider threats in the cloud. Source: "2023 Insider Threat Report," Cybersecurity Insiders, 2023 |
45%Only about 45% of organizations think native cloud app functionality is useful in detecting insider threats. Source: "2023 Insider Threat Report," Cybersecurity Insiders, 2023 |
Info-Tech Insight
An insider threat management (ITM) program focuses on the user. DLP programs focus on the data.
Insight summary
DLP is not just a single tool. It’s an additional layer of security that depends on different components of your security program, and it requires time and effort to mature.
Organizations should leverage existing security architecture with the DLP controls available in the cloud services they use.
Data loss prevention is not a point solution
Data loss prevention is the outcome of a well-designed strategy that incorporates multiple, sometimes disparate tools within your existing security program.
Prioritize data
Start with the data that matters most to your organization.
Define an objective
Having a clearly defined objective will make implementing a DLP program much easier.
DLP is a layer
Data loss prevention is not foundational, and it depends on many other parts of a mature information security program.
The low hanging fruit is sweet
Start your DLP implementation with a quick win in mind and build on small successes.
DLP is a work multiplier
Your organization must be prepared to investigate alerts and respond to incidents.
Prevent data loss across cloud or hybrid environments
Data loss prevention is not a point solution.
It’s the outcome of a well-designed strategy that incorporates multiple, sometimes disparate tools within your existing security program.
Info-Tech Insight
Leverage existing security tools where possible.
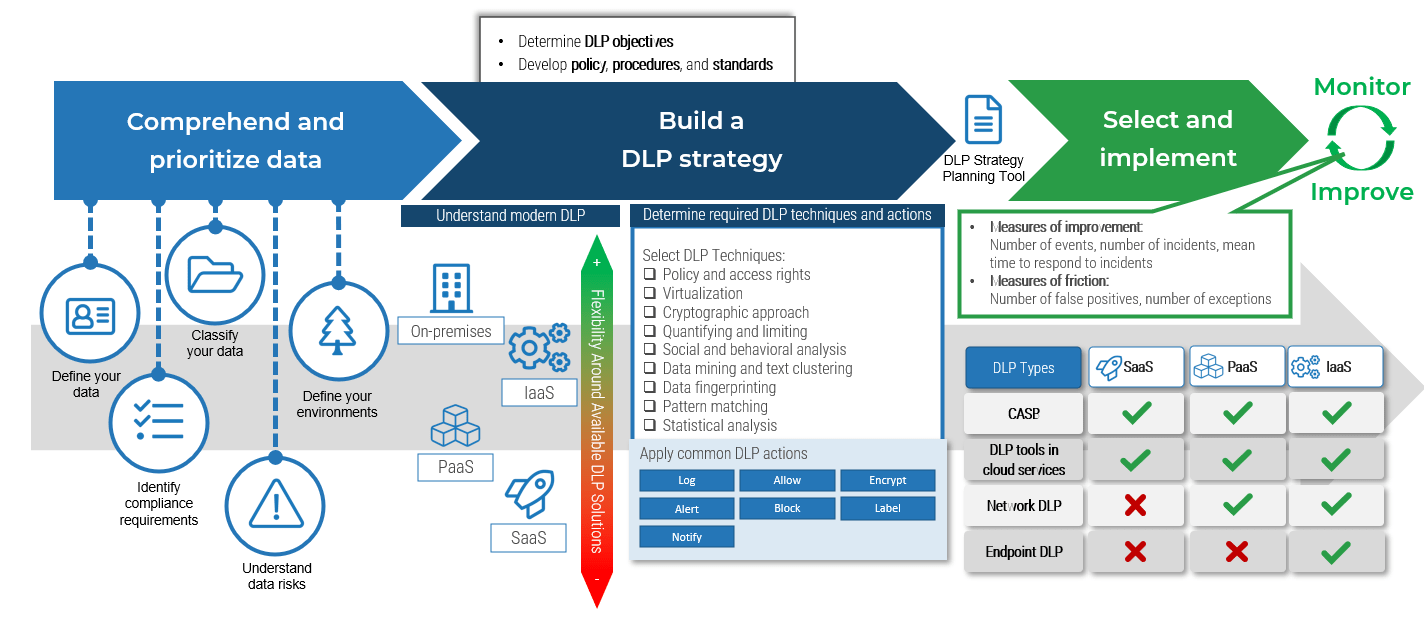
Data loss prevention (DLP) overview
DLP is an additional layer of security.
DLP is a set of technologies and processes that provides additional data protection by identifying, monitoring, and preventing data from being illicitly used or transmitted.
DLP depends on many components of a mature security program, including but not limited to:
- Acceptable use policy
- Data classification policy and data handling guidelines
- Identity and access management
DLP is achieved through some or all of the following tactics:
- Identify: Data is detected using policies, rules, and patterns.
- Monitor: Data is flagged and data activity is logged.
- Prevent: Action is taken on data once it has been detected.
Info-Tech Insight
DLP is not foundational. Your information security program needs to be moderately mature to support a DLP strategy.
DLP approaches and methods
DLP uses a handful of techniques to achieve its tactics:
- Policy and access rights: Limits access to data based on user permissions or other contextual attributes.
- Isolation or virtualization: Data is isolated in an environment with channels for data leakage made unavailable.
- Cryptographic approach: Data is encrypted.
- Quantifying and limiting: Use or transfer of data is restricted by quantity.
- Social and behavioral analysis: The DLP system detects anomalous activity, such as users accessing data outside of business hours.
- Pattern matching: Data content is analyzed for specific patterns.
- Data mining and text clustering: Large sets are analyzed, typically with machine learning (ML), to identify patterns.
- Data fingerprinting: Data files are matched against a pre-calculated hash or based on file contents.
- Statistical Analysis: Data content is analyzed for sensitive data. Usually involves machine learning.
DLP has two primary approaches for applying techniques:
- Content-based: Data is identified through inspecting its content. Fingerprinting and pattern matching are examples of content-based methods.
- Context-based: Data is identified based on its situational or contextual attributes. Some factors that may be used are source, destination, and format.
Some DLP tools use both approaches.
Info-Tech Insight
Different DLP products will support different methods. It is important to keep these in mind when choosing a DLP solution.
Start by defining your data
Define data by answering the 5 “W”s
Who? Who owns the data? Who needs access? Who would be impacted if it was lost?
What? What data do you have? What type of data is it? In what format does it exist?
When? When is the data generated? When is it used? When is it destroyed?
Where? Where is the data stored? Where is it generated? Where is it used?
Why? Why is the data needed?
Use what you discover about your data to create a data inventory!
Compliance requirements
Compliance requirements often dictate what must be done to manage and protect data and vary from industry to industry.
Some examples of compliance requirements to consider:
- Healthcare - Health Insurance Portability and Accountability Act (HIPAA)
- Financial Services - Gramm-Leach-Bliley Act (GLBA)
- Payment Card Industry Data Security Standards (PCI DSS)
Info-Tech Insight
Why is especially important. If you don’t need a specific piece of data, dispose of it to reduce risk and administrative overhead related to maintaining or protecting data.
Classify your data
Data classification facilitates making decisions about how data is treated.
Data classification is a process by which data is categorized.
- The classifications are often based on the sensitivity of the data or the impact a loss or breach of that data would have on the organization.
- Data classification facilitates decisions about data handling and how information security controls are implemented. Instead of considering many different types of data individually, decisions are based on a handful of classification levels.
- A mature data classification should include a formalized policy, handling standards, and a steering committee.
Refer to our Discover and Classify Your Data blueprint for guidance on data classification.
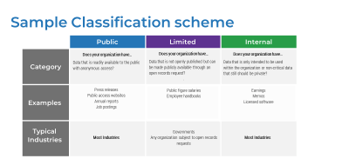
Sample data classification schema
Label |
Category |
| Top Secret | Data that is mission critical and highly likely to negatively impact the organization if breached. The “crown jewels.” Examples: Trade secrets, military secrets |
| Confidential | Data that must not be disclosed, either because of a contractual or regulatory requirement or because of its value to the organization. Examples: Payment card data, private health information, personally identifiable information, passwords |
| Internal | Data that is intended for organizational use, which should be kept private. Examples: Internal memos, sales reports |
| Limited | Data that isn’t generally intended for public consumption but may be made public. Examples: Employee handbooks, internal policies |
| Public | Data that is meant for public consumption and anonymous access. Examples: Press releases, job listings, marketing material |
Info-Tech Insight
Data classification should be implemented as a continuous program, not a one-time project.
Understand data risk
Knowing where and how your data is at risk will inform your DLP strategy.
Data exists in three states, and each state presents different opportunities for risk. Different DLP methodologies will be appropriate for different states.
Data states
In use
- End-user devices
- Mobile devices
- Servers
In motion
- Cloud services
- Web/web apps
- Instant messaging
- File transfers
At rest
- Cloud services
- Databases
- End-user devices
- Email archives
- Backups
- Servers
- Physical storage devices
Causes of Risk
The most common causes of data loss can be categorized by people, processes, and technology.
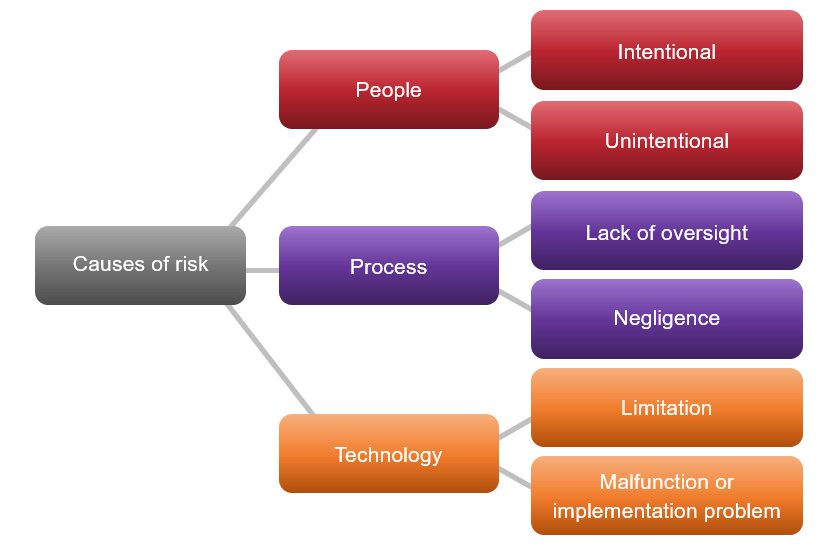
Check out our Combine Security Risk Management Components Into One Program blueprint for guidance on risk management, including how to do a full risk assessment.
Prioritize your data
Know what data matters most to your organization.
Prioritizing the data that most needs protection will help define your DLP goals.
The prioritization of your data should be a business decision based on your comprehension of the data. Drivers for prioritizing data can include:
- Compliance-driven: Noncompliance is a risk in itself and your organization may choose to prioritize data based on meeting compliance requirements.
- Audit-driven: Data can be prioritized to prepare for a specific audit objective or in response to an audit finding.
- Business-driven: Data could be prioritized based on how important it is to the organization’s business processes.
Info-Tech Insight
It’s not feasible for most organizations to apply DLP to all their data. Start with the most important data.
Activity: Prioritize your data
Input: Lists of data, data types, and data environments
Output: A list of data types with an estimated priority
Materials: Data Loss Prevention Strategy Planner worksheet
Participants: Security leader, Data owners
1-2 hours
For this activity, you will use the Data Loss Prevention Strategy Planner workbook to prioritize your data.
- Start with tab “2. Setup” and fill in the columns. Each column features a short explanation of itself, and the following slides will provide more detail about the columns.
- On tab “3. Data Prioritization,” work through the rows by selecting a data type and moving left to right. This sheet features a set of instructions at the top explaining each column, and the following slides also provide some guidance. On this tab, you may use data types and data environments multiple times.
Click to download the Data Loss Prevention Strategy Planner
Activity: Prioritize your data
In the Data Loss Prevention Strategy Planner tool, start with tab “2. Setup.”
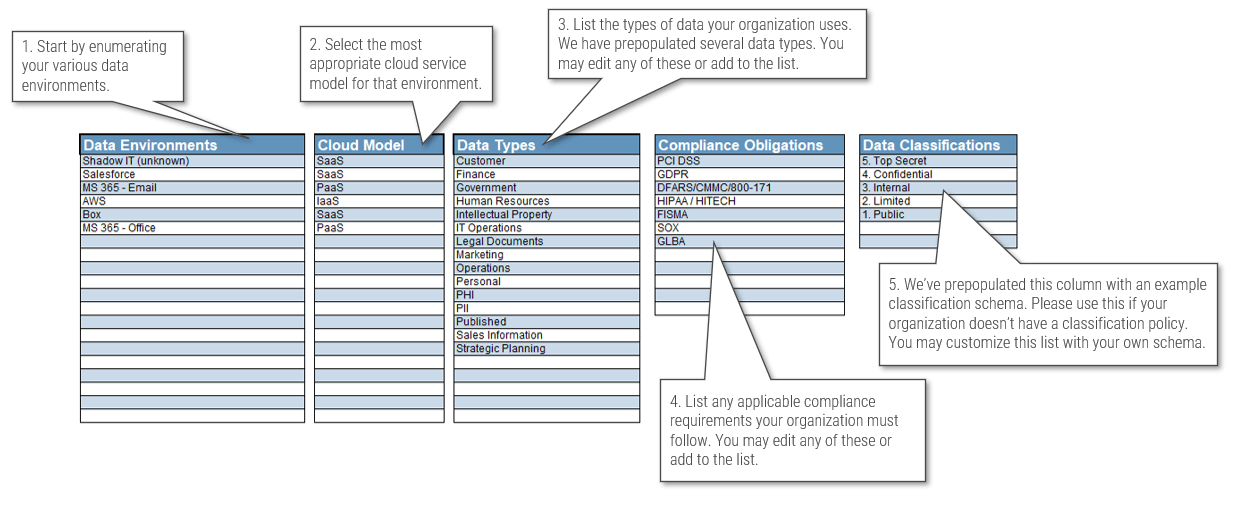
Next, move to tab “3. Data Prioritization.”
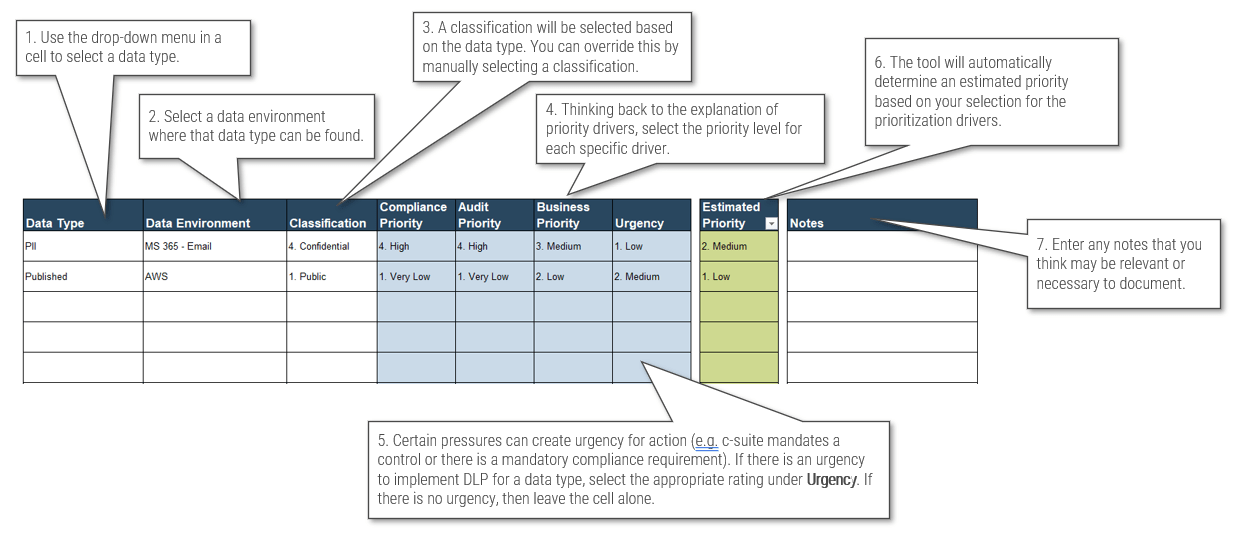
Click to download the Data Loss Prevention Strategy Planner
Determine DLP objectives
Your DLP strategy should be able to function as a business case.
DLP objectives should achieve one or more of the following:
- Prevent disclosure or unauthorized use of data, regardless of its state.
- Preserve usability while providing adequate security.
- Improve security, privacy, and compliance capabilities.
- Reduce overall risk for the enterprise.
Example objectives:
- Prevent users from emailing ePHI to addresses outside of the organization.
- Detect when a user is uploading an unusually large amount of data to a cloud drive.
Most common DLP use cases:
- Protection of data, primarily from internal threats.
- Meet compliance requirements to protect data.
- Automate the discovery and classification of data.
- Provide better data management and visibility across the enterprise.
- Manage and protect data on mobile devices.
Info-Tech Insight
Having a clear idea of your objectives will make implementing a DLP program easier.
Align DLP with your existing security program/architecture
DLP depends on many different aspects of your security program.
To the right are some components of your existing security program that will support DLP.
1. Data handling standards or guidelines: These specify how your organization will handle data, usually based on its classification. Your data handling standards will inform the development of DLP rules, and your employees will have a clear idea of data handling expectations.
2. Identity and access management (IAM): IAM will control the access users have to various resources and data and is integral to DLP processes.
3. Incident response policy or plan: Be sure to consider your existing incident handling processes when implementing DLP. Modifying your incident response processes to accommodate alerts from DLP tools will help you efficiently process and respond to incidents.
4. Existing security tools: Firewalls, email gateways, security information and event management (SIEM), and other controls should be considered or leveraged when implementing a DLP solution.
5. Acceptable use policy: An organization must set expectations for acceptable/unacceptable use of data and IT resources.
6. User education and awareness: Aside from baseline security awareness training, organizations should educate users about policies and communicate the risks of data leakage to reduce risk caused by user error.
Info-Tech Insight
Consider DLP as a secondary layer of protection; a safety net. Your existing security program should do most of the work to prevent data misuse.
Cloud service models
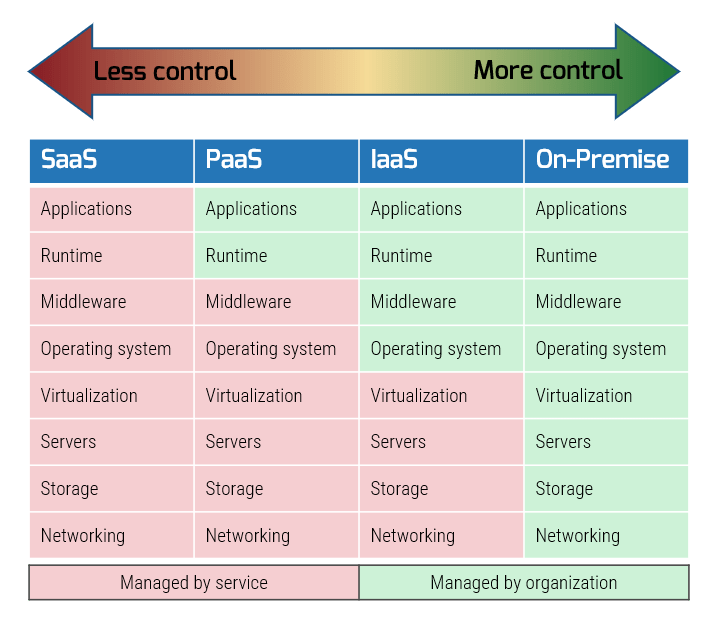
A fundamental challenge with implementing DLP with cloud services is the reduced flexibility that comes with managing less of the technology stack. Each cloud model offers varying levels of abstraction and control to the user.
Infrastructure as a service (IaaS): This service model provides customers with virtualized technology resources, such as servers and networking infrastructure. IaaS allows users to have complete control over their virtualized infrastructure without needing to purchase and maintain hardware resources or server space. Popular examples include Amazon Web Servers, Google Cloud Engine, and Microsoft Azure.
Platform as a service (PaaS): This service model provides users with an environment to develop and manage their own applications without needing to manage an underlying infrastructure. Popular examples include Google Cloud Engine, OpenShift, and SAP Cloud.
Software as a service (SaaS): This service model provides customers with access to software that is hosted and maintained by the cloud provider. SaaS offers the least flexibility and control over the environment. Popular examples include Salesforce, Microsoft Office, and Google Workspace.
Info-Tech Insight
Cloud service providers may include DLP controls and functionality for their environments with the subscription. These tools are usually well suited for DLP functions on that platform.
Different DLP tools
DLP products often fall into general categories defined by where those tools provide protection. Some tools fit into more than one category.
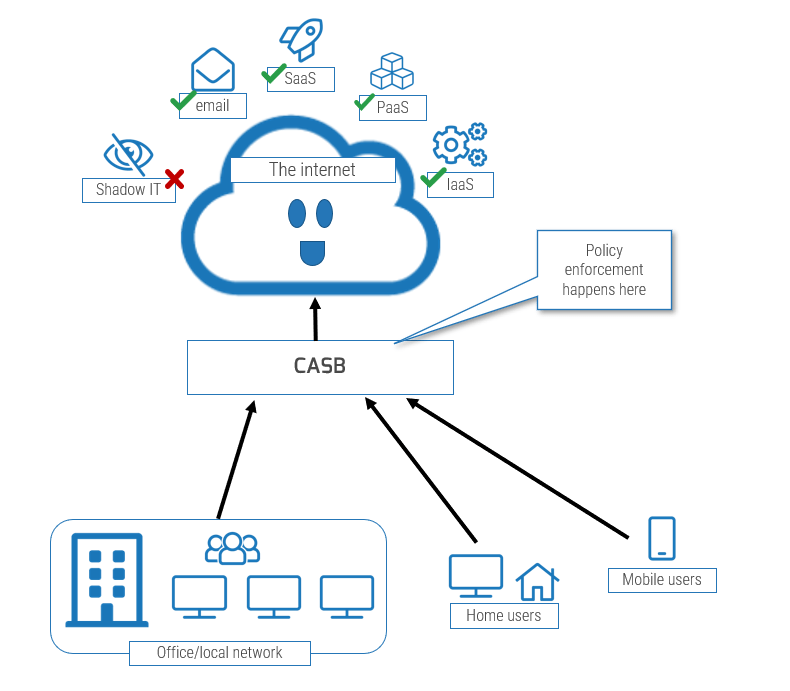
Cloud DLP refers to DLP products that are designed to protect data in cloud environments.
- Cloud access security broker (CASB): This system, either in-cloud or on-premises, sits between cloud service users and cloud service providers and acts as a point of control to enforce policies on cloud-based resources. CASBs act on data in motion, for the most part, but can detect and act on data at rest through APIs.
- Existing tools integrated within a service: Many cloud services provide DLP tools to manage data loss in their service.
Endpoint DLP: This DLP solution runs on an endpoint computing device and is suited to detecting and controlling data at rest on a computer as well as data being uploaded or downloaded. Endpoint DLP would be feasible for IaaS.
Network DLP: Network DLP, deployed on-premises or as a cloud service, enforces policies on network flows between local infrastructure and the internet.
- “Email DLP”: Detects and enforces security policies specifically on data in motion as emails.
Choosing a DLP solution
You will also find that some DLP solutions are better suited for some cloud service models than others.
DLP solution types that are better suited for SaaS: CASB and Integrated Tools
DLP solution types that are better suited for PaaS: CASB, Integrated Tools, Network DLP
DLP solution types that are better suited for IaaS: CASB, Integrated Tools, Network DLP, and Endpoint DLP
Your approach for DLP will vary depending on the data state you’ll be acting on and whether you are trying to detect or prevent.
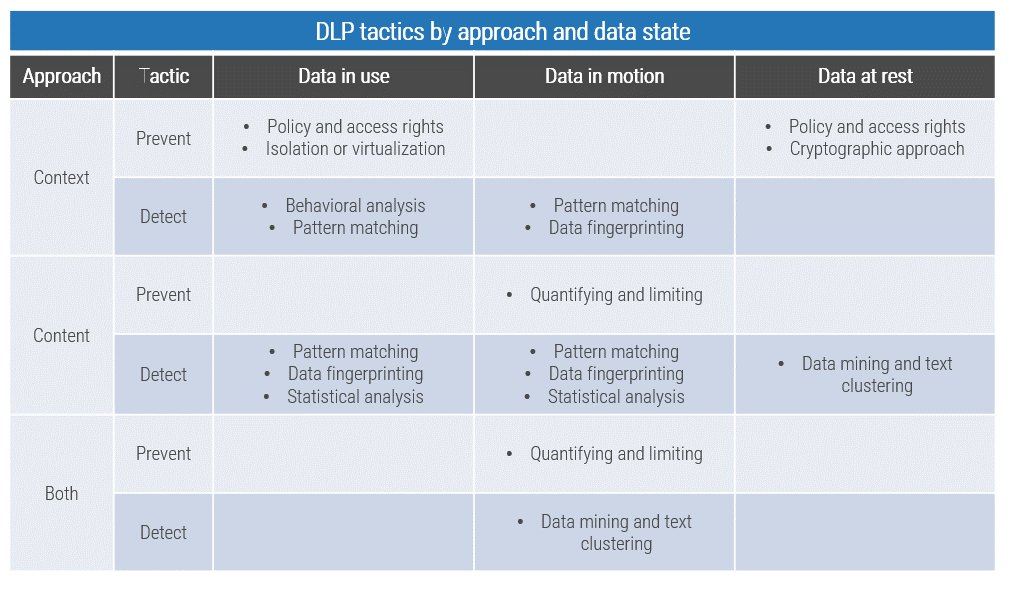
Click to download the Data Loss Prevention Strategy Planner
Check the tab labeled “6. DLP Features Reference” for a list of common DLP features.
Activity: Plan DLP methods
Input: Knowledge of data states for data types
Output: A set of technical DLP policy rules for each data type by environment
Materials: The same Data Loss Prevention Strategy Planner worksheet from the earlier activity
Participants: Security leader, Data owners
1-2 hours
Continue with the same workbook used in the previous activity.
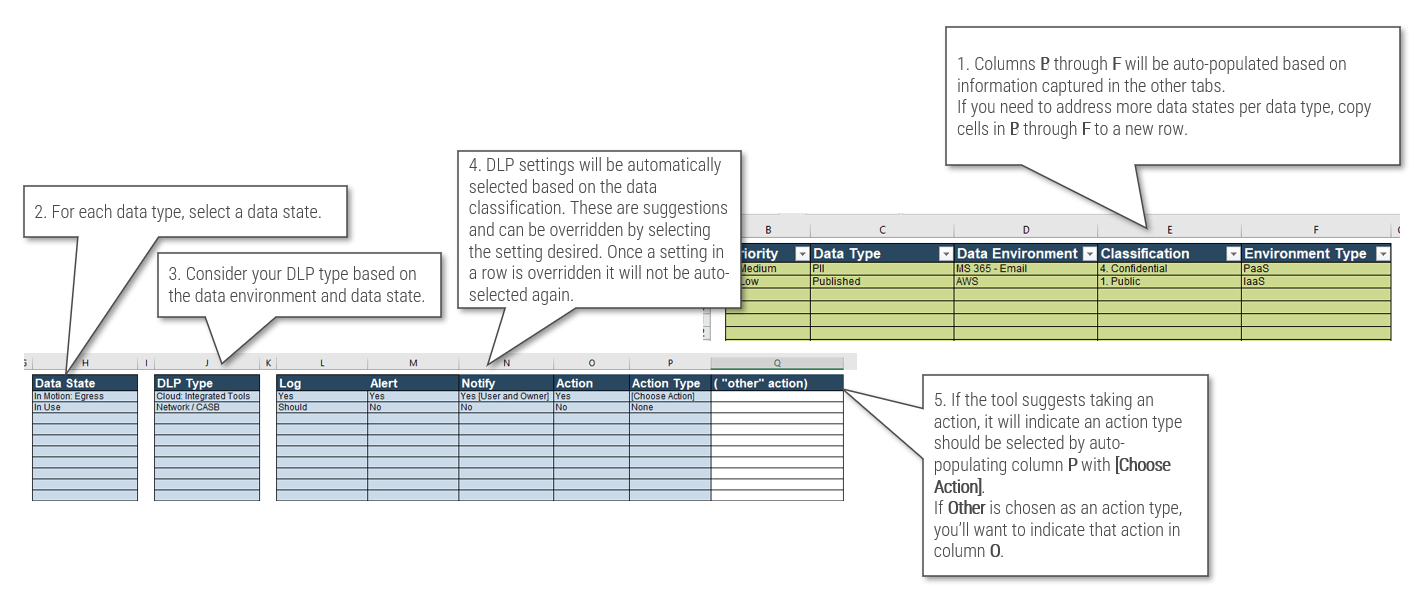
- On tab “4. DLP Methods,” indicate the expected data state the DLP control will act on. Then, select the type of DLP control your organization intends to use for that data type in that data environment.
- DLP actions are suggested based on the classification of the data type, but these may be overridden by manually selecting your preferred action.
- You will find more detail on this activity on the following slide, and you will find some additional guidance in the instructional text at the top of the worksheet.
- Once you have populated the columns on this worksheet, a summary of suggested DLP rules can be found on tab “5. Results.”
Click to download the Data Loss Prevention Strategy Planner
Activity: Plan DLP methods
Use tab “4. DLP Methods” to plan DLP rules and technical policies.
See tab “5. Results” for a summary of your DLP policies.
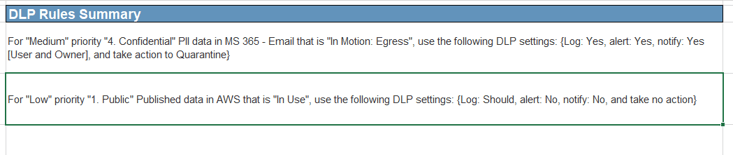
Click to download the Data Loss Prevention Strategy Planner
Implement your DLP program
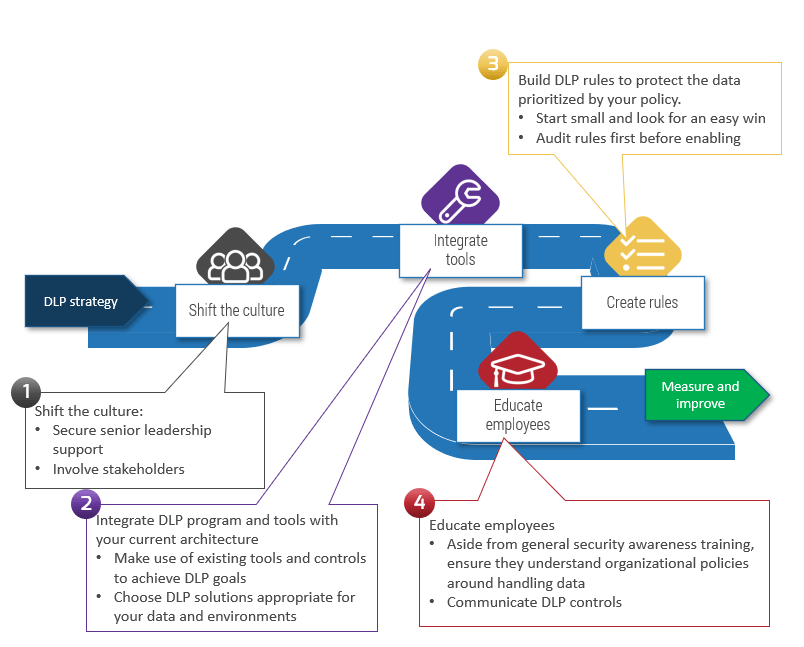
Take the steps to properly implement your DLP program
- It’s important to shift the culture. You will need leadership’s support to implement controls and you’ll need stakeholders’ participation to ensure DLP controls don’t negatively affect business processes.
- Integrate DLP tools with your security program. Most cloud service providers, like Amazon, Microsoft, and Google provide DLP controls in their native environment. Many of your other security controls, such as firewalls and mail gateways, can be used to achieve DLP objectives.
- DLP is best implemented with a crawl, walk, then run approach. Following change management processes can reduce friction.
- Communicating controls to users will also reduce friction.
Info-Tech Insight
After a DLP program is implemented, alerts will need to be investigated and incidents will need a response. Be prepared for DLP to be a work multiplier!
Measure and improve
Metrics of effectiveness
DLP attempts to tackle the challenge of promptly detecting and responding to an incident.
To measure the effectiveness of your DLP program, compare the number of events, number of incidents, and mean time to respond to incidents from before and after DLP implementation.
Metrics that indicate friction
A high number of false positives and rule exceptions may indicate that the rules are not working well and may be interfering with legitimate use.
It’s important to address these issues as the frustration felt by employees can undermine the DLP program.
Tune DLP rules
Establish a process for routinely using metrics to tune rules.
This will improve performance and reduce friction.
Info-Tech Insight
Aside from performance-based tuning, it’s important to evaluate your DLP program periodically and after major system or business changes to maintain an awareness of your data environment.
Related Info-Tech Research
|
|
Discover and Classify Your DataUnderstand where your data lives and who has access to it. This blueprint will help you develop an appropriate data classification system by conducting interviews with data owners and by incorporating vendor solutions to make the process more manageable and end-user friendly. |
|
|
Identify the Components of Your Cloud Security ArchitectureThis blueprint and associated tools are scalable for all types of organizations within various industry sectors. It allows them to know what types of risk they are facing and what security services are strongly recommended to mitigate those risks. |
|
|
Data Loss Prevention on SoftwareReviewsQuickly evaluate top vendors in the category using our comprehensive market report. Compare product features, vendor strengths, user-satisfaction, and more. Don’t settle for just any vendor – find the one you can trust. Use the Emotional Footprint report to see which vendors treat their customers right. |
Research Contributors
Andrew Amaro
CSO and Founder
Klavan Physical and Cyber Security Services
Arshad Momin
Cyber Security Architect
Unicom Engineering, Inc.
James Bishop
Information Security Officer
StructureFlow
Michael Mitchell
Information Security and Privacy Compliance Manager
Unicom Engineering, Inc.
One Anonymous Contributor
Bibliography
Alhindi, Hanan, Issa Traore, and Isaac Woungang. "Preventing Data Loss by Harnessing Semantic Similarity and Relevance." jisis.org Journal of Internet Services and Information Security, 31 May 2021. Accessed 2 March 2023. https://jisis.org/wp-content/uploads/2022/11/jisis-2021-vol11-no2-05.pdf
Cash, Lauryn. "Why Modern DLP is More Important Than Ever." Armorblox, 10 June 2022. Accessed 10 February 2023. https://www.armorblox.com/blog/modern-dlp-use-cases/
Chavali, Sai. "The Top 4 Use Cases for a Modern Approach to DLP." Proofpoint, 17 June 2021. Accessed 7 February 2023. https://www.proofpoint.com/us/blog/information-protection/top-4-use-cases-modern-approach-dlp
Crowdstrike. "What is Data Loss Prevention?" Crowdstrike, 27 Sept. 2022. Accessed 6 Feb. 2023. https://www.crowdstrike.com/cybersecurity-101/data-loss-prevention-dlp/
De Groot, Juliana. "What is Data Loss Prevention (DLP)? Definition, Types, and Tips." Digital Guardian, 8 February 2023. Accessed 9 Feb. 2023. https://digitalguardian.com/blog/what-data-loss-prevention-dlp-definition-data-loss-prevention
Denise. "Learn More About DLP Key Use Cases." CISO Platform, 28 Nov. 2019. Accessed 10 February 2023. https://www.cisoplatform.com/profiles/blogs/learn-more-about-dlp-key-use-cases
Google. "Cloud Data Loss Prevention." Google Cloud Google, n.d. Accessed 7 Feb. 2023. https://cloud.google.com/dlp#section-6
Gurucul. "2023 Insider Threat Report." Cybersecurity Insiders, 13 Jan. 2023. Accessed 23 Feb. 2023. https://gurucul.com/2023-insider-threat-report
IBM Security. "Cost of a Data Breach 2022." IBM Security, 1 Aug. 2022. Accessed 13 Feb. 2023. https://www.ibm.com/downloads/cas/3R8N1DZJ
Mell, Peter & Grance, Tim. "The NIST Definition of Cloud Computing." NIST CSRC NIST, Sept. 2011. Accessed 7 Feb. 2023. https://csrc.nist.gov/publications/detail/sp/800-145/final
Microsoft. "Plan for Data Loss Prevention (DLP)." Microsoft 365 Solutions and Architecture Microsoft, 6 Feb. 2023. Accessed 14 Feb. 2023. https://learn.microsoft.com/en-us/microsoft-365/compliance/dlp-overview-plan-for-dlp
Nanchengwa, Christopher. "The Four Questions for Successful DLP Implementation." ISACA Journal ISACA, 1 Jan. 2019. Accessed 6 Feb. 2023. https://www.isaca.org/resources/isaca-journal/issues/2019/volume-1/the-four-questions-for-successful-dlp-implementation
Palo Alto Networks. "The State of Cloud Native Security 2023." Palo Alto Networks, 2 March 2023. Accessed 23 March 2023. https://www.paloaltonetworks.com/content/dam/pan/en_US/assets/pdf/reports/state-of-cloud-native-security-2023.pdf
Pritha. "Top Six Metrics for your Data Loss Prevention Program." CISO Platform, 27 Nov. 2019. Accessed 10 Feb. 2023. https://www.cisoplatform.com/profiles/blogs/top-6-metrics-for-your-data-loss-prevention-program
Raghavarapu, Mounika. "Understand DLP Key Use Cases." Cymune, 12 June 2021. Accessed 7 Feb. 2023. https://www.cymune.com/blog-details/DLP-key-use-cases
Sheela, G. P., & Kumar, N. "Data Leakage Prevention System: A Systematic Report." International Journal of Recent Technology and Engineering BEIESP, 30 Nov. 2019. Accessed 2 March 2023. https://www.ijrte.org/wp-content/uploads/papers/v8i4/D6904118419.pdf
Sujir, Shiv. "What is Data Loss Prevention? Complete Guide [2022]." Pathlock, 15 Sep. 2022. Accessed 7 February 2023. https://pathlock.com/learn/what-is-data-loss-prevention-complete-guide-2022/
Wlosinski, Larry G. "Data Loss Prevention - Next Steps." ISACA Journal, 16 Feb. 2018. Accessed 21 Feb. 2023. https://www.isaca.org/resources/isaca-journal/issues/2018/volume-1/data-loss-preventionnext-steps