
Establish Effective Security Governance & Management
- The security team is unsure of governance needs and how to manage them.
- There is a lack of alignment between key stakeholder groups
- There are misunderstandings related to the role of policy and process.
Our Advice
Critical Insight
Good governance stems from a deep understanding of how stakeholder groups interact with each other and their respective accountabilities and responsibilities. Without these things, organizational functions tend to interfere with each other, blurring the lines between governance and management and promoting ad–hoc decision making that undermines governance.
Impact and Result
- The first phase of this project will help you establish or refine your security governance and management by determining the accountabilities, responsibilities, and key interactions of your stake holder groups.
- In phase two, the project will guide you through the implementation of essential governance processes: setting up a steering committee, determining risk appetite, and developing a policy exception-handling process.
Establish Effective Security Governance & Management Research & Tools
Besides the small introduction, subscribers and consulting clients within this management domain have access to:
1. Establish Effective Security Governance and Management Deck – A step-by-step guide to help you establish or refine the governance model for your security program.
This storyboard will take you through the steps to develop a security governance and management model and implement essential governance processes.
- Establish Effective Security Governance & Management – Phases 1-2
2. Design Your Governance Model – A security governance and management model to track accountabilities, responsibilities, stakeholder interactions, and the implementation of key governance processes.
This tool will help you determine governance and management accountabilities and responsibilities and use them to build a visual governance and management model.
- Security Governance Model Templates (Visio)
- Security Governance Model Templates (PDF)
- Security Governance Model Tool
3. Organizational Structure Template – A tool to address structural issues that may affect your new governance and management model.
This template will help you to implement or revise your organizational structure.
- Security Governance Organizational Structure Template
4. Information Security Steering Committee Charter & RACI – Templates to formalize the role of your steering committee and the oversight it will provide.
These templates will help you determine the role a steering committee will play in your governance and management model.
- Information Security Steering Committee Charter
- Information Security Steering Committee RACI Chart
5. Security Policy Lifecycle Template – A template to help you model your policy lifecycle.
Once this governing document is customized, ensure the appropriate security policies are developed as well.
- Security Policy Lifecycle Template
6. Security Policy Exception Approval Process Templates – Templates to establish an approval process for policy exceptions and bolster policy governance and risk management.
These templates will serve as the foundation of your security policy exception approval processes.
- Security Policy Exception Approval Workflow (Visio)
- Security Policy Exception Approval Workflow (PDF)
- Policy Exception Tracker
- Information Security Policy Exception Request Form
Infographic
Further reading
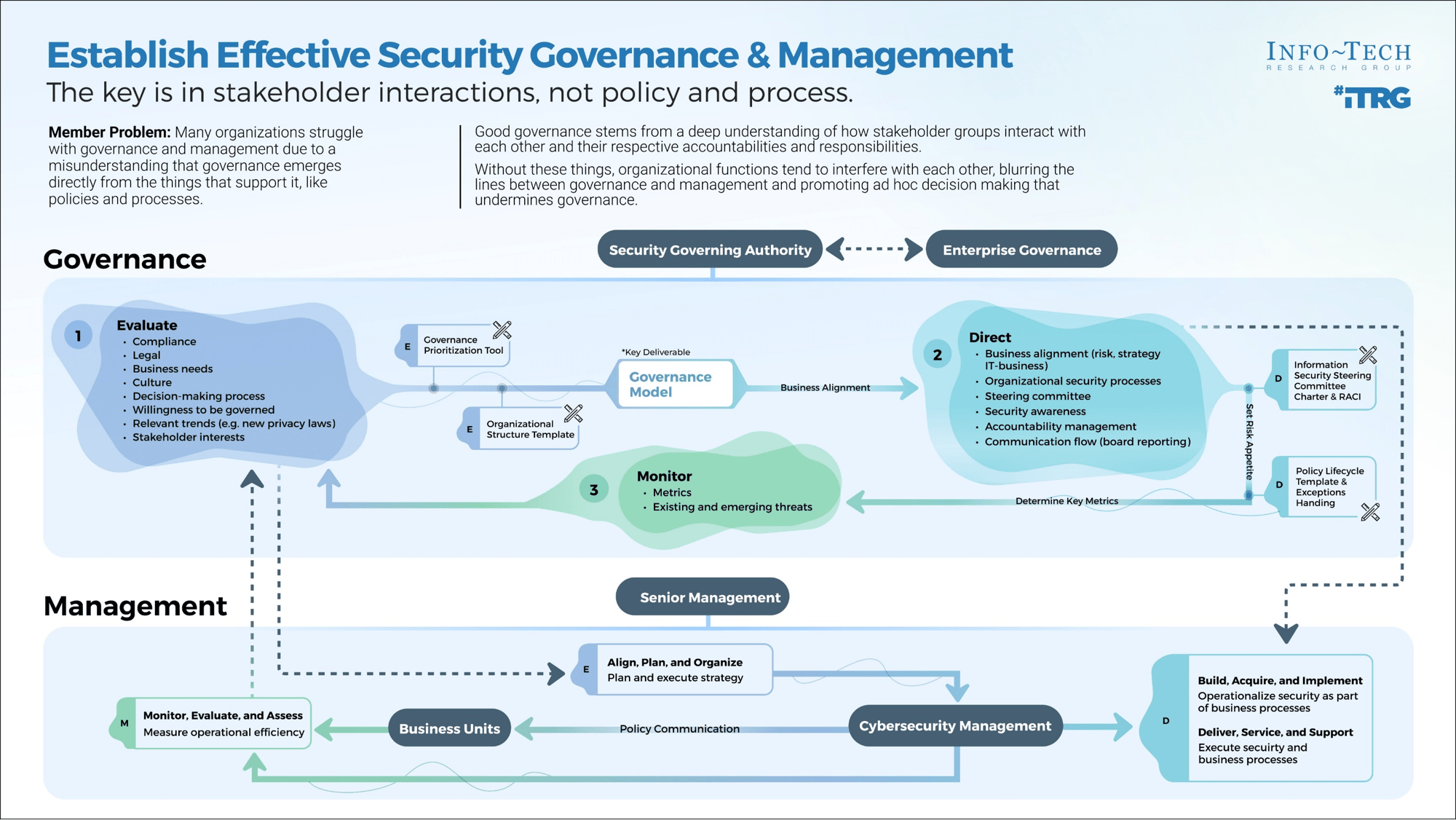
Establish Effective Security Governance & Management
The key is in stakeholder interactions, not policy and process.
Analyst Perspective
It's about stakeholder interactions, not policy and process.
Many security leaders complain about a lack of governance and management in their organizations. They have policies and processes but find neither have had the expected impact and that the organization is teetering on the edge of lawlessness, with stakeholder groups operating in ways that interfere with each other (usually due to poorly defined accountabilities).
Among the most common examples is security's relationship to the business. When these groups don't align, they tend to see each other as adversaries and make decisions in line with their respective positions: security endorses one standard, the business adopts another.
The consequences of this are vast. Such an organization is effectively opposed to itself. No wonder policy and process have not resolved the issue.
At a practical level, good governance stems from understanding how different stakeholder groups interact, providing inputs and outputs to each other and modeling who is accountable for what. But this implied accountability model needs to be formalized (perhaps even modified) before governance can help all stakeholder groups operate as strategic partners with clearly defined roles, responsibilities, and decision-making power. Only when policies and processes reflect this will they serve as effective tools to support governance.

Logan Rohde
Senior Research Analyst, Security & Privacy
Info-Tech Research Group
Executive Summary
| Your Challenge | Common Obstacles | Info-Tech's Approach |
Ineffective governance and management processes, if they are adopted at all, can lead to:
|
Most governance and management initiatives stumble because they do not address governance as a set of interactions and influences that stakeholders have with and over each other, seeing it instead as policy, process, and risk management. Challenges include:
| You will be able to establish a robust governance model to support the current and future state of your organization by accounting for these three essential parts:
|
Info-Tech Insight
Good governance stems from a deep understanding of how stakeholder groups interact with each other and their respective accountabilities and responsibilities. Without these things, organizational functions tend to interfere with each other, blurring the lines between governance and management and promoting ad hoc decision making that undermines governance.
Your challenge
This research is designed to help organizations who need to:
- Establish security governance from scratch.
- Improve security governance despite a lack of cooperation from the business.
- Determine the accountabilities and responsibilities of each stakeholder group.
This blueprint will solve the above challenges by helping you model your organization's governance structure and implement processes to support the essential governance areas: policy, risk, and performance metrics.
Percentage of organizations that have yet to fully advance to a maturity-based approach to security
70%
Source: McKinsey, 2021
Common obstacles
These barriers make this challenge difficult to address for many organizations:
- The business does not wish to be governed and does not seek to align with security on the basis of risk.
- Various stakeholder groups essentially govern themselves, causing business functions to interfere with each other.
- Security teams struggle to differentiate between governance and management and the purpose of each.
Early adopter infrastructure
63%
Security leaders not reporting to the board about risk or incident detection and prevention.
Source: LogRhythm, 2021
46%
Those who report that senior leadership is confident cybersecurity leaders understand business goals.
Source: LogRhythm, 2021
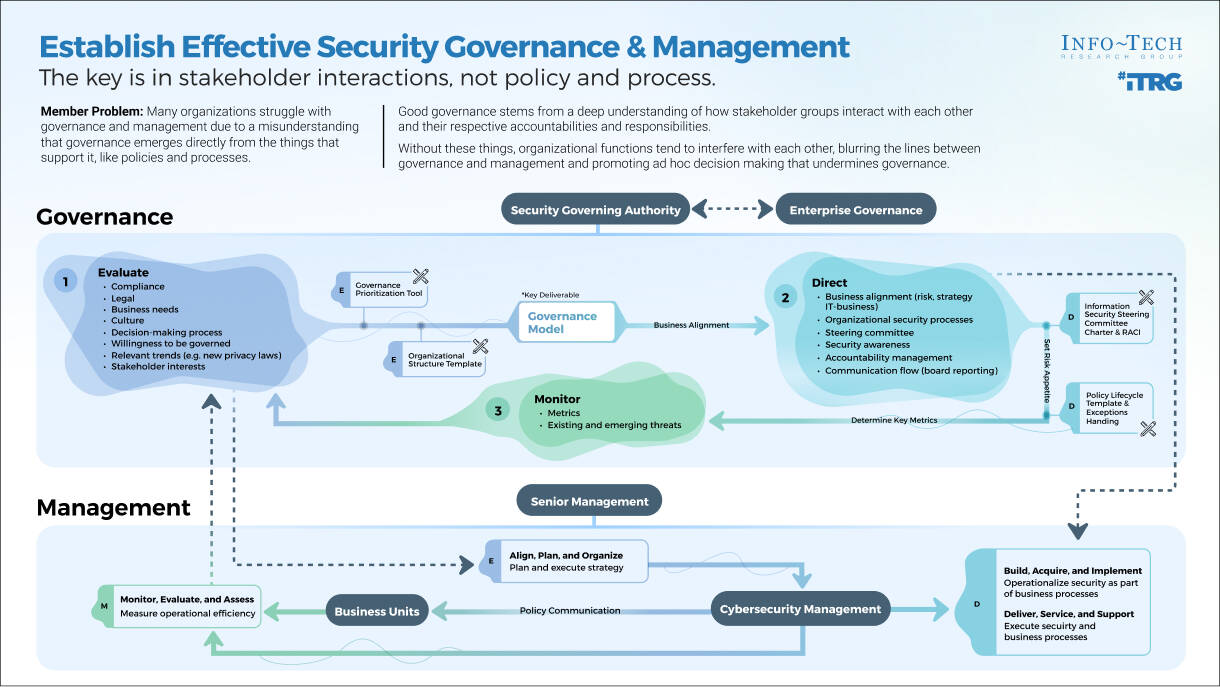
Governance isn't just policy and process
Governance is often mistaken for an organization's formalized policies and processes. While both are important governance supports, they do not provide governance in and of themselves.
For governance to work well, an organization needs to understand how stakeholder groups interact with each other. What inputs and outputs do they provide? Who is accountable? Who is responsible? These are the questions one needs to ask before designing a governance structure. Failing to account for any of these three elements tends to result in overlap, inefficiency, and a lack of accountability, creating flawed governance.
Separate governance from management
Oversight versus operations
- COBIT emphasizes the importance of separating governance from management. These are complementary functions, but they refer to different parts of organizational operation.
- Governance provides a decision-making apparatus based on predetermined requirements to ensure smooth operations. It is used to provide oversight and direction and hinges on established accountabilities
- Simply put, governance refers to what an organization is and is not willing to permit in day-to-day operations, and it tends to make its presence known via the key areas of risk appetite, formal policy and process, and exception handling.
- Note: These key areas do not provide governance in and of themselves. Rather, governance emerges in accordance with the decisions an organization has made regarding these areas. Sometimes, however, these "decisions" have not been formally or consciously made and the current state of the organization's operations becomes the default - even when it is not working well.
- Management, by contrast, is concerned with executing business processes in accordance with the governance model, essentially, governance provides guidance for how to make decisions during daily management.
"Information security governance is the guiding hand that organizes and directs risk mitigation efforts into a business-aligned strategy for the entire organization."
Steve Durbin,
Chief Executive,
Information Security Forum, Forbes, 2023
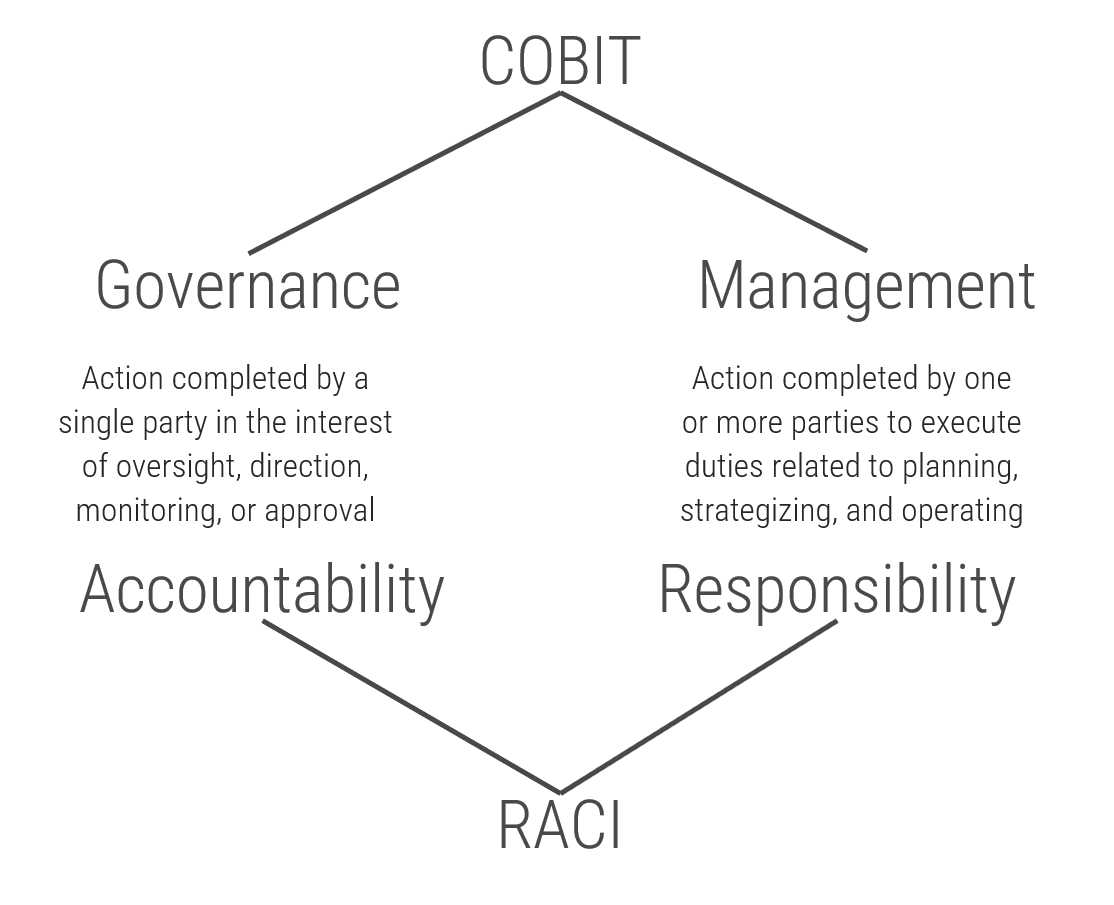
Models for governance and management
Info-Tech's Governance and Management research uses the logic of COBIT's governance and management framework but distills this guidance into a practical, easy-to-implement series of steps, moving beyond the rudimentary logic of COBIT to provide an actionable and personalized governance model.
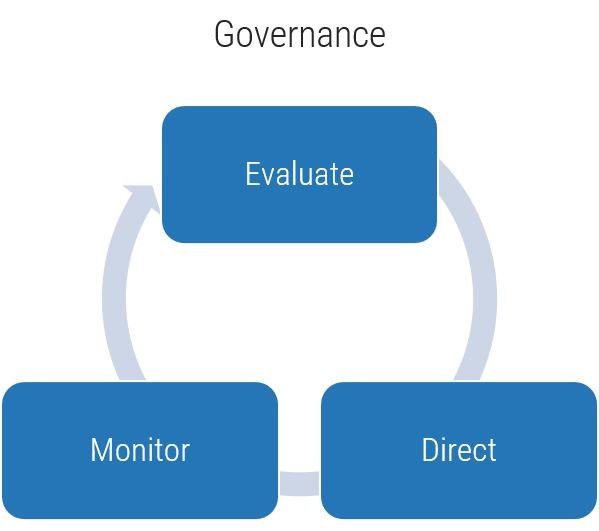
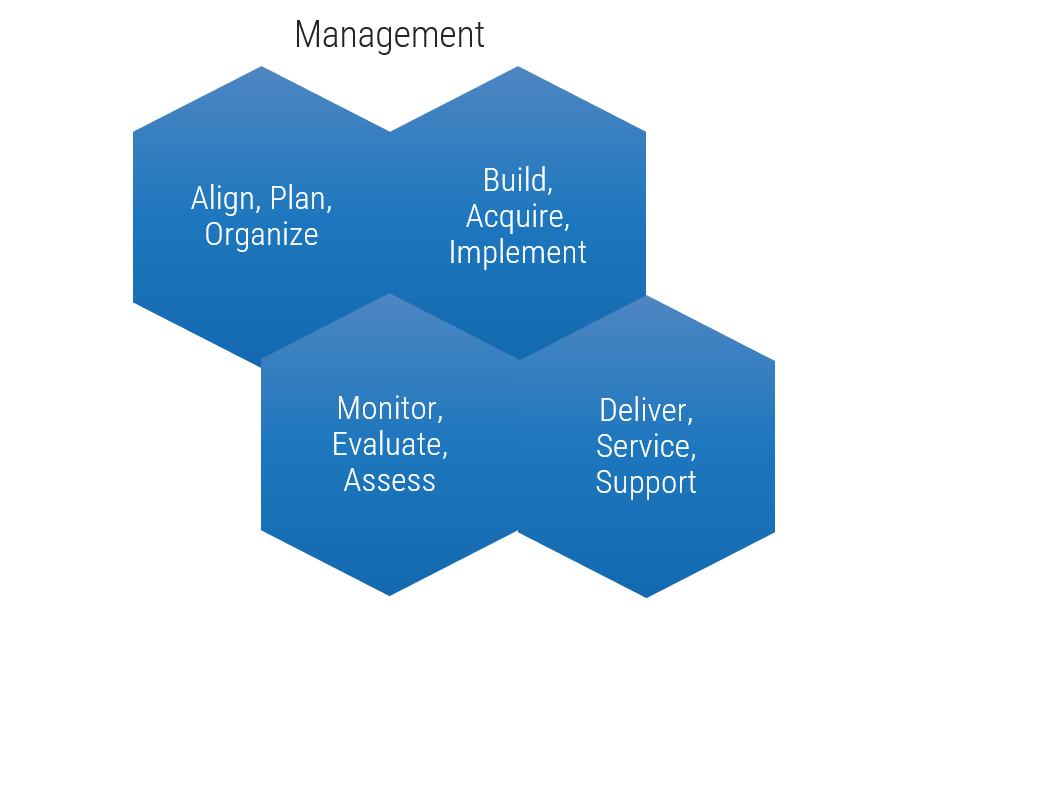
Clear accountabilities and responsibilities
Complementary frameworks to simplify governance and management
The distinction that COBIT draws between governance and management is roughly equivalent to that of accountability and responsibility, as seen in the RACI* model.
There can be several stakeholders responsible for something, but only one party can be accountable.
Use this guidance to help determine the accountabilities and responsibilities of your governance and management model.
*Responsible, Accountable, Consulted, Informed
Security governance framework
A security governance framework is a system that will design structures, processes, accountability definitions, and membership assignments that lead the security department toward optimal results for the business.
Governance is performed in three ways:
| 1 Evaluate | 2 Direct | 3 Monitor |
|---|---|---|
| For governance to be effective it must account for stakeholder interests and business needs. Determining what these are is the vital first step. | Governance is used to determine how things should be done within an organization. It sets standards and provides oversight so decisions can be made during day-to-day management. | Governance needs change and inefficiencies need to be revised. Therefore, monitoring key performance indicators is an essential step to course correct as organizational needs evolve. |
"Governance specifies the accountability framework and provides oversight to ensure that risks are adequately mitigated, while management ensures that controls are implemented to mitigate risks. Management recommends security strategies. Governance ensures that security strategies are aligned with business objectives and consistent with regulations."
- EDUCAUSE
SMART metrics
Suggested targets to measure success
Specific
Measurable
Achievable
Relevant
Time-Bound
| Examples |
| Security's risk analyses will be included as part of the business decision-making process within three months after completing the governance initiative. |
| Increase rate of security risk analysis using risk appetite within three months of project completion. |
| Have stakeholder engagement supply input into security risk-management decisions within three months of completing phase one of blueprint. |
| Reduce time to approve policy exceptions by 25%. |
| Reduce security risk related to policy non-compliance by 50% within one year. |
| Develop five KPIs to measure progress of governance and management within three months of completing blueprint. |
Info-Tech's methodology for security governance and management
| 1. Design Your Governance Model | 2. Implement Essential Governance Processes | |
|---|---|---|
| Phase Steps |
|
|
| Phase Outcomes |
|
|
Governance starts with mapping stakeholder inputs, outputs, and throughputs
The key is in stakeholder interactions, not policy and process
Good governance stems from a deep understanding of how stakeholder groups interact with each other and their respective accountabilities and responsibilities. Without these things, organizational functions tend to interfere with each other, blurring the lines between governance and management and promoting ad hoc decision making that undermines governance.
Policy, process, and org. charts support governance but do not produce it on their own
To be effective, these things need to be developed with the accountabilities and influence of the organizational functions that produce them.
A lack of business alignment does not mean you're doomed to fail
While the highest levels of governance maturity depend on strong security-business alignment, there are still tactics one can use to improve governance.
All organizations have governance
Sometimes it is poorly defined, ineffective, and occurs in the same place as management, but it exists at some level, acting as the decision-making apparatus for an organization (i.e. what can and cannot occur).
Risk tolerances are variable across lines of business
This can lead to misalignments between security and the business, as each may have their own tolerance for particular risks. The remedy is to understand the risk appetite of the business and allow this to inform security risk management decisions.
Blueprint deliverables
Each step of this blueprint is accompanied by supporting deliverables to help you accomplish your goals:
Security Governance Model Tool
Security Governance Organizational Structure Template
Information Security Steering Committee Charter & RACI
Policy Exceptions-Handling Workflow
Policy Exception Tracker and Request Form
Key deliverable:
By the end of this blueprint, you will have created a personalized governance model to map your stakeholders' accountabilities, responsibilities, and key interactions.
Blueprint benefits
| IT Benefits | Business Benefits |
|---|---|
|
|
Info-Tech offers various levels of support to best suit your needs
| DIY Toolkit | Guided Implementation | Workshop | Consulting |
|---|---|---|---|
| "Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful." | "Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track." | "We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place." | "Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project." |
Diagnostics and consistent frameworks are used throughout all four options.
Guided Implementation
What does a typical GI on this topic look like?
| Phase 1 | Phase 2 | |||
|---|---|---|---|---|
| Call #1: Scope requirements, objectives, and your specific challenges. | Call #2: Determine governance requirements. Call #3: Review governance model. |
Call #4: Determine KPIs. Call #5: Stand up steering committee. |
Call #6: Set risk appetite. Call #7: Establish policy lifecycle. |
Call #8: Revise exception-handing process. |
A Guided Implementation (GI) is a series of calls with an Info-Tech analyst to help implement our best practices in your organization.
A typical GI is 4 to 8 calls over the course of 2 to 3 months.
Workshop Overview
| Day 1 | Day 2 | Day 3 | Day 4 | Day 5 | |
|---|---|---|---|---|---|
| Activities | Evaluate | Direct | Monitor | Implement Essential Governance Processes | Next Steps and Wrap-Up (offsite) |
| 1.1 Prioritize governance accountabilities 1.2 Prioritize management responsibilities 1.3 Evaluate organizational structure |
2.1 Align with business 2.2 Build security governance and management model 2.3 Visualize security governance and management model |
3.1 Develop governance and management KPIs | 4.1 Draft steering committee charter 4.2 Complete steering committee RACI 4.3 Draft qualitative risk statements 4.4 Define policy management lifecycle 4.5 Establish policy exception approval process |
5.1 Complete in-progress deliverables from previous four days 5.2 Set up review time for workshop deliverables and to discuss next steps |
|
| Deliverables |
|
|
|
|
Contact your account representative for more information.
workshops@infotech.com 1-888-670-8889
Customize your journey
The security governance and management blueprint pairs well with security design and security strategy.
- The governance and management model you create in this blueprint will inform efforts to improve security, like revisiting security program design and your security strategy.
- Work with your member services director, executive advisor, or technical counselor to scope the journey you need. They will work with you to align the subject matter experts to support your roadmap and workshops.
Workshop Day 1 and Day 2
Security Governance and Management
Workshop Day 3 and Day 4
Security Strategy Gap Analysis or Security Program Design Factors
Phase 1
Design Your Governance Model
Phase 1
1.1 Evaluate
1.2 Direct
1.3 Monitor
Phase 2
2.1 Implement Oversight
2.2 Set Risk Appetite
2.3 Implement Policy lifecycle
Establish Security Governance & Management
This phase will walk you through the following activities:
- Prioritize governance accountabilities
- Prioritize management responsibilities
- Evaluate current organizational structure
- Align with the business
- Build security governance and management model
- Finalize governance and management model
- Develop governance and management KPIs
This phase involves the following participants:
- CISO
- CIO
- Business representative
Step 1.1
Evaluate
Activities
1.1.1 Prioritize governance accountabilities
1.1.2 Prioritize management responsibilities
1.1.3 Evaluate current organizational structure
This step involves the following participants:
- CISO
- CIO
- Business representative
Outcomes of this step
- Defined governance accountabilities
- Defined management responsibilities
Design Your Governance Model
Step 1.1 > Step 1.2 > Step 1.3
Evaluate: Getting started
| Element | Questions |
| Compliance | What voluntary or mandatory standards must be represented in my governance model? |
| Legal | What laws are the organization accountable to? Who is the accountable party? |
| Business needs | What does the business need to operate? What sort of informational or operational flows need to be accounted for? |
| Culture | How does the business operate? Are departments siloed or cooperative? Where does security fit in? |
| Decision-making process | How are decisions made? Who is involved? What information needs to be available to do so? |
| Willingness to be governed | Is the organization adverse to formal governance mechanisms? Are there any opportunities to improve alignment with the business? |
| Relevant trends | Are there recent developments (e.g. new privacy laws) that are likely to affect the organization in the future? Will this complicate or simplify governance modeling efforts? |
| Stakeholder interests | Who are the internal and external stakeholders that need to be represented in the governance model? |
The above is a summary of COBIT 2019 EDM01.01 Evaluate the governance system, along with Info-Tech-recommended questions to contextualize each element for your organization.
1.1.1 Prioritize governance accountabilities
1-2 hours
Using the example on the next slide, complete the following steps.
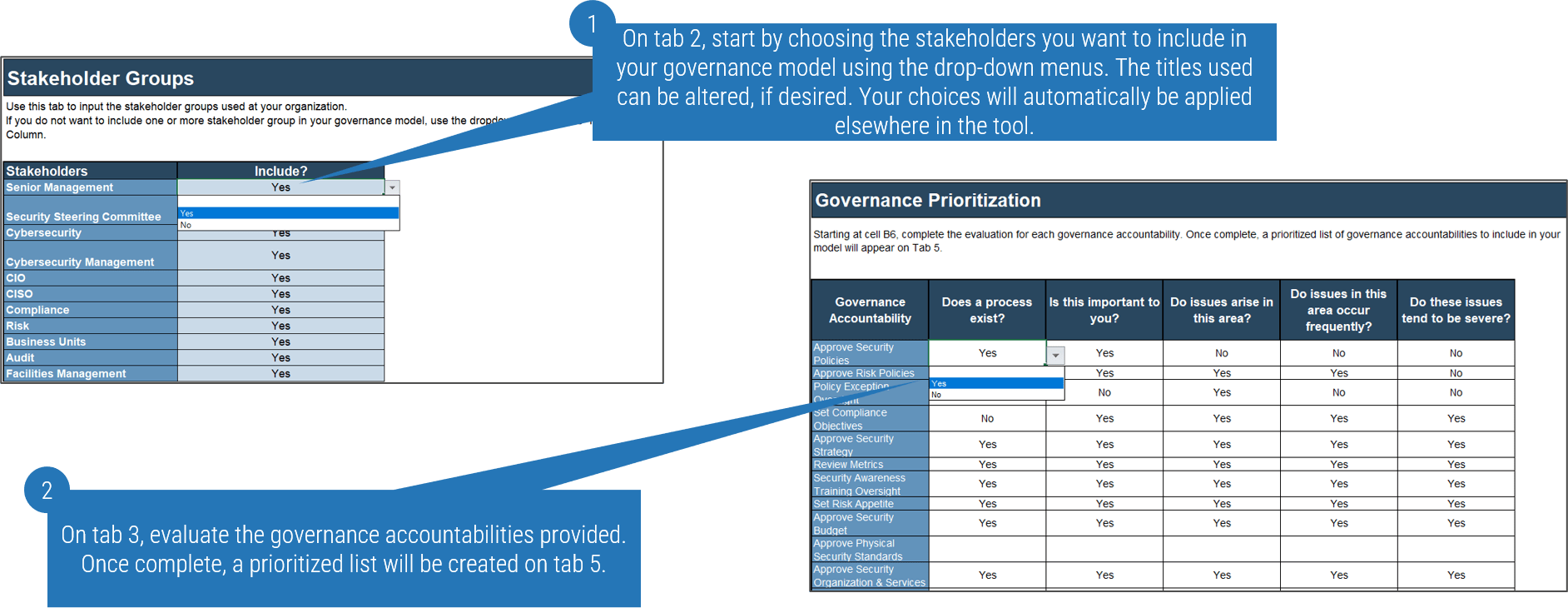
- Download Info-Tech's Security Governance Model Tool using the link below and customize the stakeholder groups on tab 1 to reflect the makeup of your organization.
- Using the previous slide as a guide, evaluate your organization's internal and external pressures and discuss their possible impacts your governance and management model.
- Complete tab 2, Governance Prioritization, indicating your response to each prompt using the drop-down menus. The tool will score your responses and provide you with a prioritized list of governance accountabilities based on greatest need on tab 4, Governance Model Builder.
- Review the list and make any desired modifications to the prompts on tab 2 and then move on to Activity 1.1.2. (We will return to tab 4 in Step 2.1.) Remember to evaluate the results against the internal/external pressure analysis to ensure these details are reflected.
Download the Security Governance Model Tool
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Security Governance and Management Model Tool
Tabs 2 and 3
1.1.2 Prioritize management responsibilities
1 hours
Using the examples on the previous slide, complete the following steps.
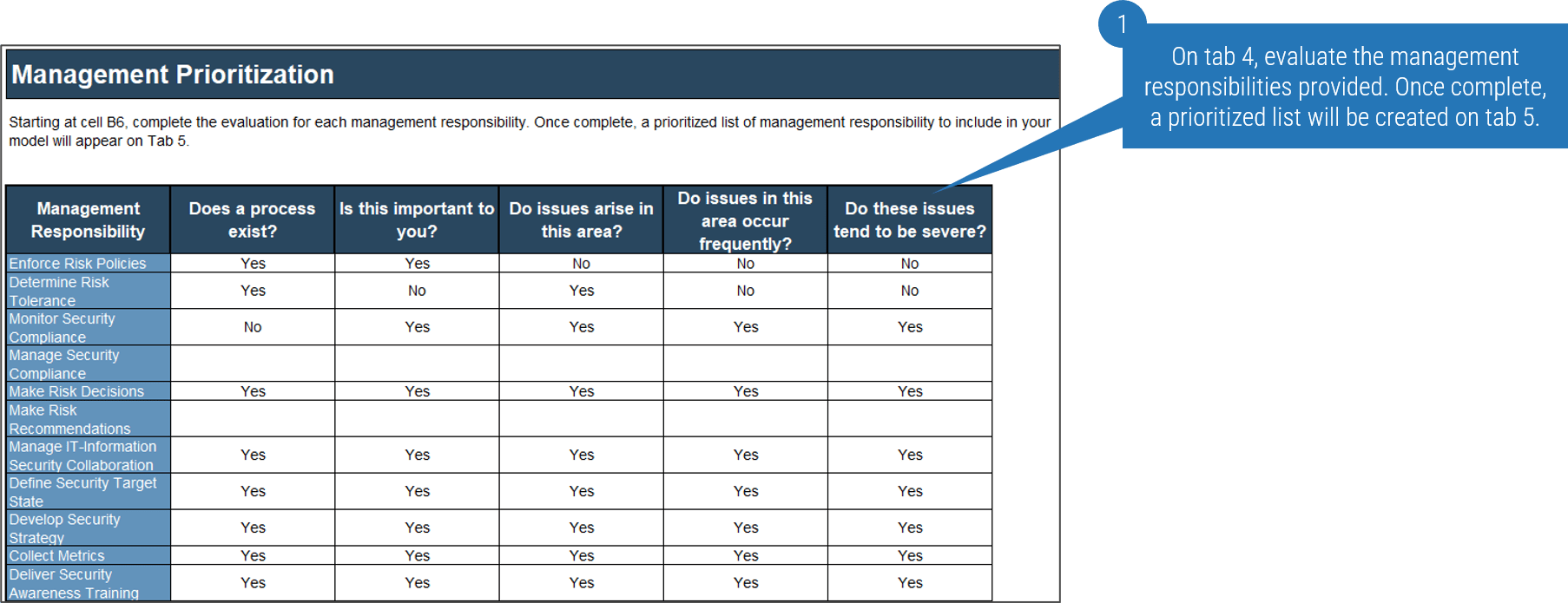
- Complete tab 3, Management Prioritization, indicating your response to each prompt using the drop-down menus. The tool will score your responses and provide you with a prioritized list of governance accountabilities based on greatest need on tab 4, Governance Model Builder.
- Review the list and make any desired modifications to the prompts on tab 3 and then move on to Activity 1.1.3. (We will return to tab 4 in Step 2.1.) Remember to evaluate the results against the internal/external pressure analysis to ensure these details are reflected.
Download Security Governance Model Tool
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Security Governance and Management Model Tool
Tab 4
1.1.3 Evaluate current organizational structure
1-3 hours
- Download and modify Info-Tech's Security Governance Organizational Structure Template to reflect the reporting structure at your organization. If such a document already exists, simply review it and move on to the next step below.
- Determine if the current organizational structure will negatively affect your ability to pursue the items in your prioritized lists from governance accountabilities and management responsibilities (e.g. conflicts of interest related to oversight or reporting), and discuss the feasibility of changing the current governance structure.
- Record these recommended changes and any other key points you'd like the business or other stakeholders to be aware of. We'll use this information in the business alignment exercise in Step 2.1
Download the Security Governance Organizational Structure Template
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Info-Tech resources
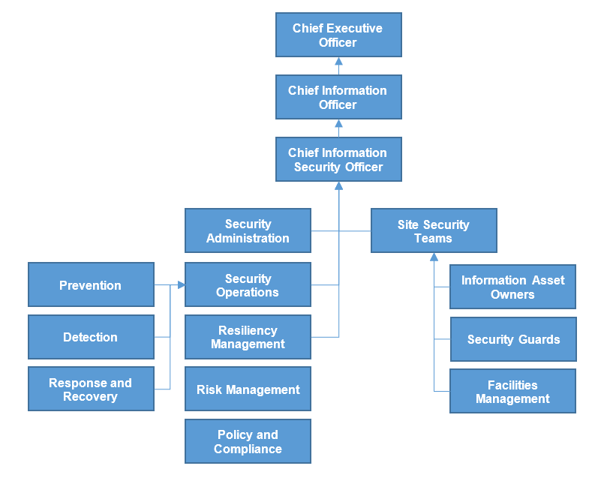
Locate structural problems in advance
- If you do not already have a diagram of your organization's reporting structure, use this template to create one. Examples are provided for high, medium, and low maturity.
- The existing reporting structure will likely affect the governance model you create, as it may not be feasible to assign certain governance accountabilities and management responsibilities to certain stakeholders.
- For example, it may make sense for the head of security to approve the security budget, but if they report to a CIO with greater authority that accountability will likely have to sit with the CIO instead.
Download the Security Governance Organizational Structure Template
Step 1.2
Direct
Activities
1.2.1 Align with the business
1.2.2 Build security governance and management model
1.2.3 Finalize governance and management model
This step involves the following participants:
CISO
CIO
Business representative
Outcomes of this step
- Record of key stakeholder interactions
- Visual governance model
Design Your Governance Model
Step 1.1 > Step 1.2 > Step 1.3
Direct: Getting started
| Element | Questions |
| Business alignment | Do we have a full understanding of the business's approach to risk and security's role to support business objectives? |
| Organizational security process | How well do our current processes work? Are we missing any key processes? |
| Steering committee | Will we use a dedicated steering committee to oversee security governance, or will another stakeholder assume this role? |
| Security awareness | Does the organization have a strong security culture? Does an effort need to be made to educate stakeholder groups on the role of security in the organization? |
| Roles and responsibilities | Does the organization use RACI charts or another system to define roles and document duties? |
| Communication flows | Do we have a good understanding of how information flows between stakeholder groups? Are there any gaps that need to be addressed (e.g. regular board reporting)? |
The above is a summary of COBIT 2019 EDM01.02 Direct the governance system, along with Info-Tech-recommended questions to contextualize each element for your organization.
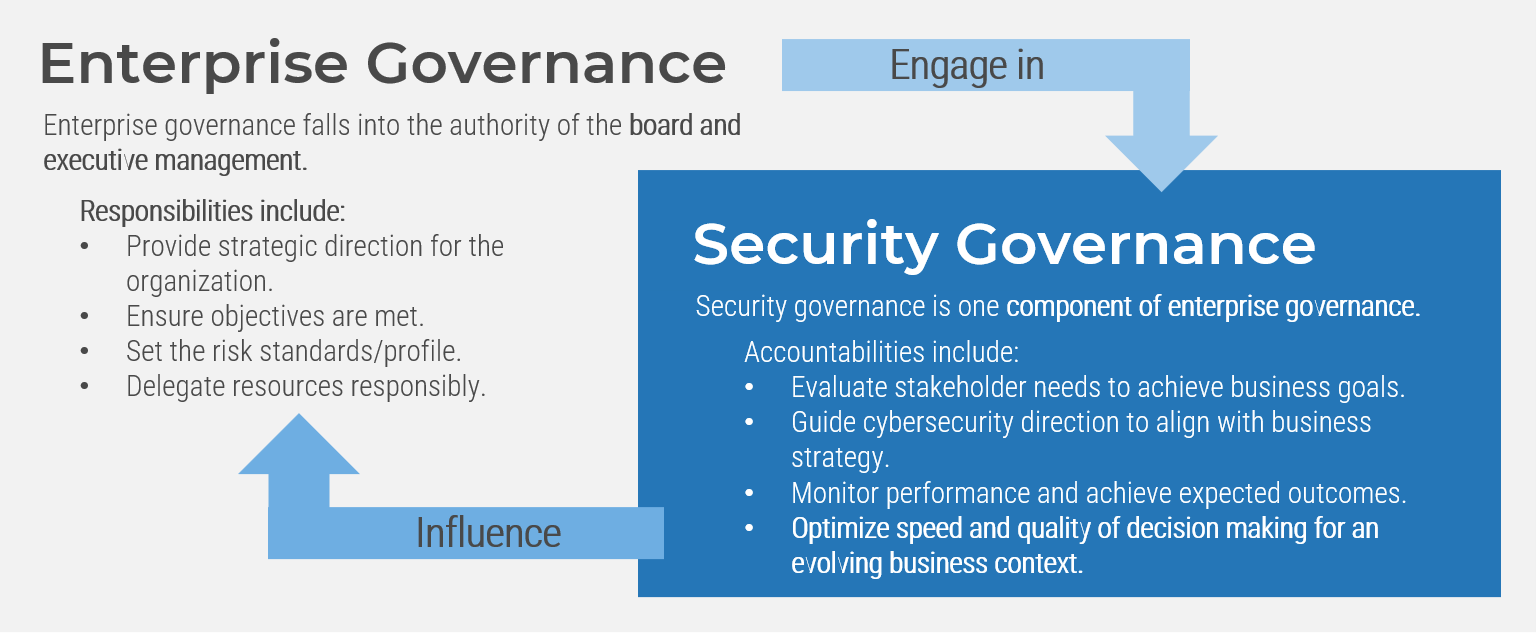
Embed security governance within enterprise governance
Design structures, processes, authority definitions, and steering committee assignments to drive optimal business results.
1.2.1 Align with the business
1-3 hours
- Request a meeting with the business to present your findings from the previous activities in Step 1.1. As you prepare for the meeting, remember to following points:
- The goal here is to align, not to command. You want the business to see the security team as a strategic ally that supports the pursuit of business goals.
- Make recommendations and explain any security risks associated with the direction the business wants to take, but the goal is not to strongarm the business into adopting your perspective.
- Above all, listen to the business to learn more about how they relate to governance and what their priorities are. This will help you adapt your governance model to better support business needs.
Info-Tech Insight
A lack of business participation does not mean your governance initiative is doomed. From this lack, we can still infer their attitudes toward security governance, and we can account for this in our governance model. This may limit the maturity your program can reach, but it doesn't prevent improvements from being made to your current security governance.
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
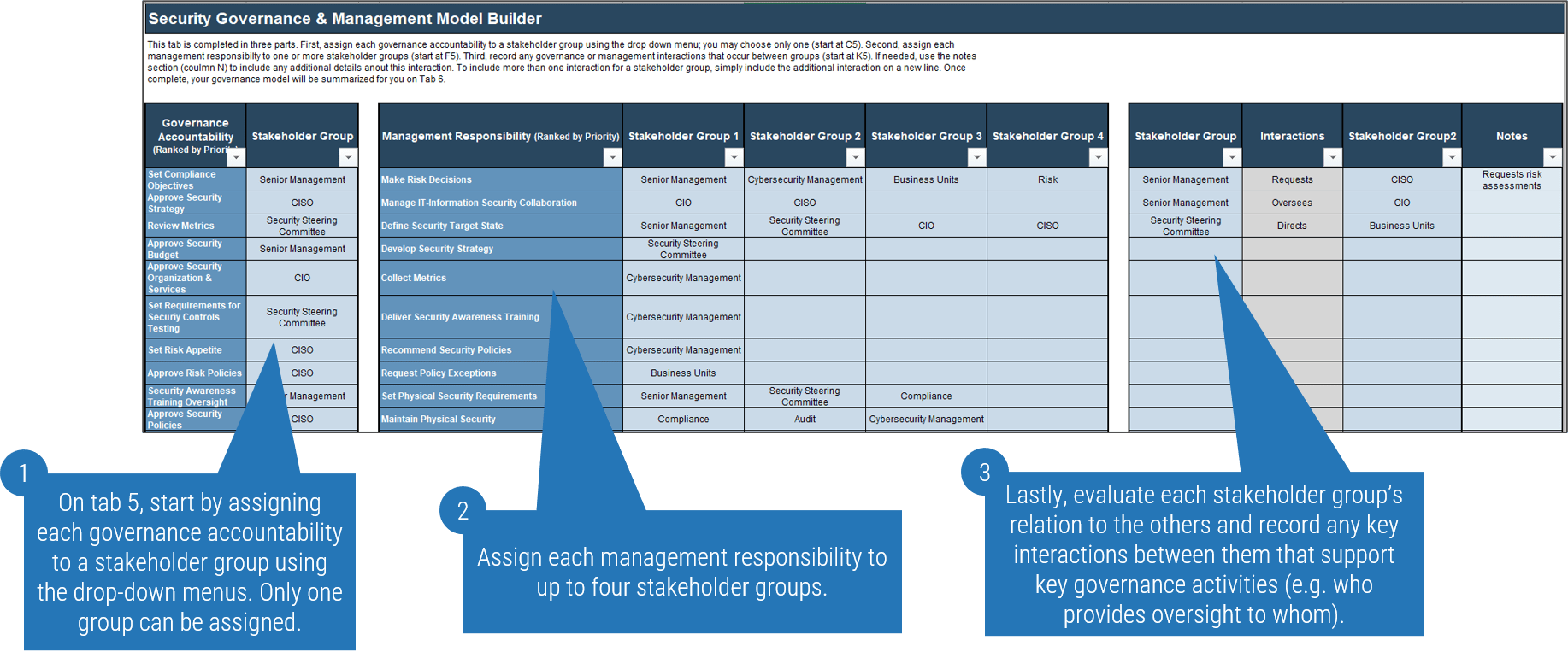
1.2.2 Build security governance and management model
1-2 hours
Using the example on the next slide, complete the following steps:
- On tab 4, review the prioritized lists for governance accountabilities and management responsibilities and begin assigning them to the appropriate stakeholder groups.
- Remember: Responsibilities can be assigned to up to four stakeholders, but there can be only one party listed as accountable.
- Documenting these interactions will help you ensure your governance program accounts for inputs and outputs that are required by, or that otherwise affect, your various stakeholder groups.
Note: You may wish to review Info-Tech's governance model templates before completing this activity to get an idea of what you'll be working toward in this step. See slides 37-38.
Download Security Governance Model Tool
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Security Governance and Management Model Tool
Tab 5
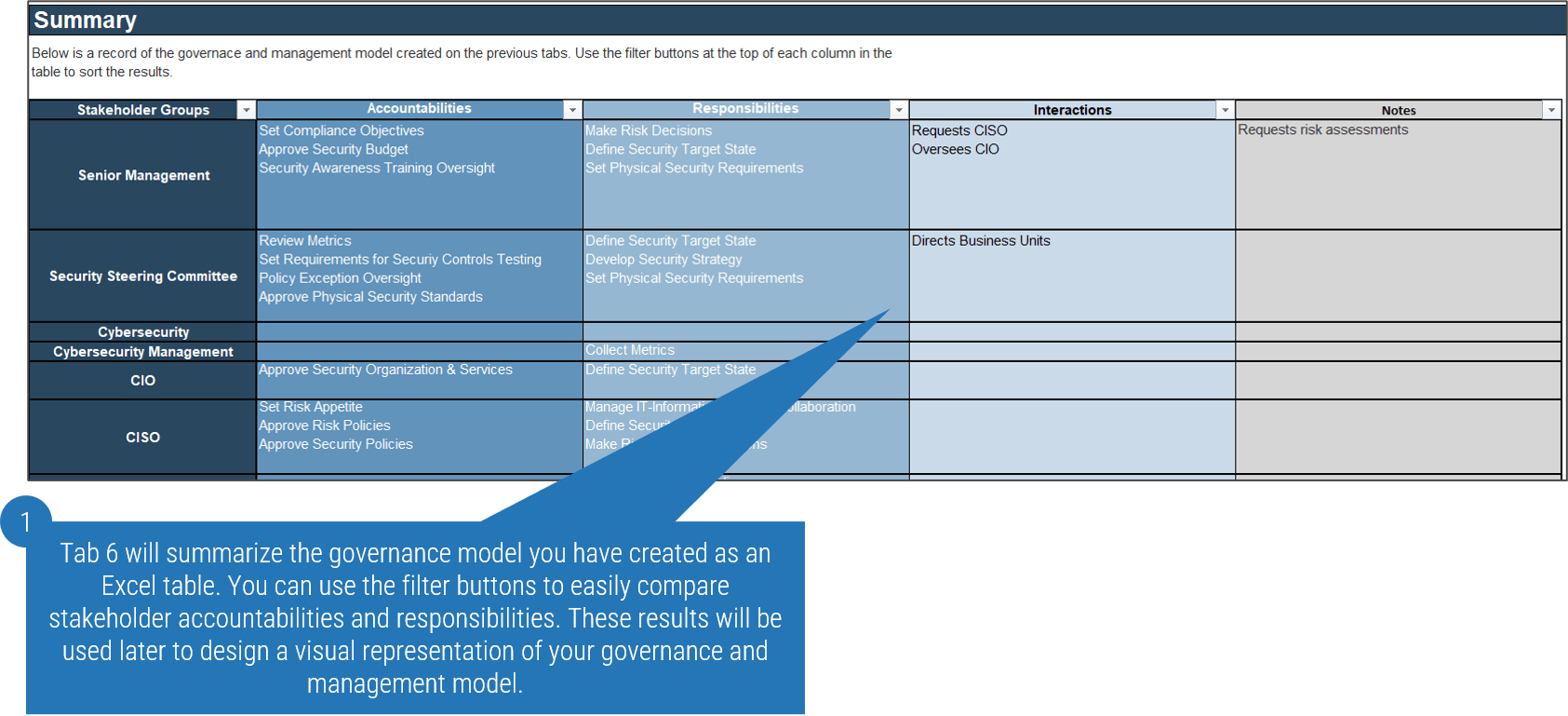
Security Governance and Management Model Tool continued
Tab 6
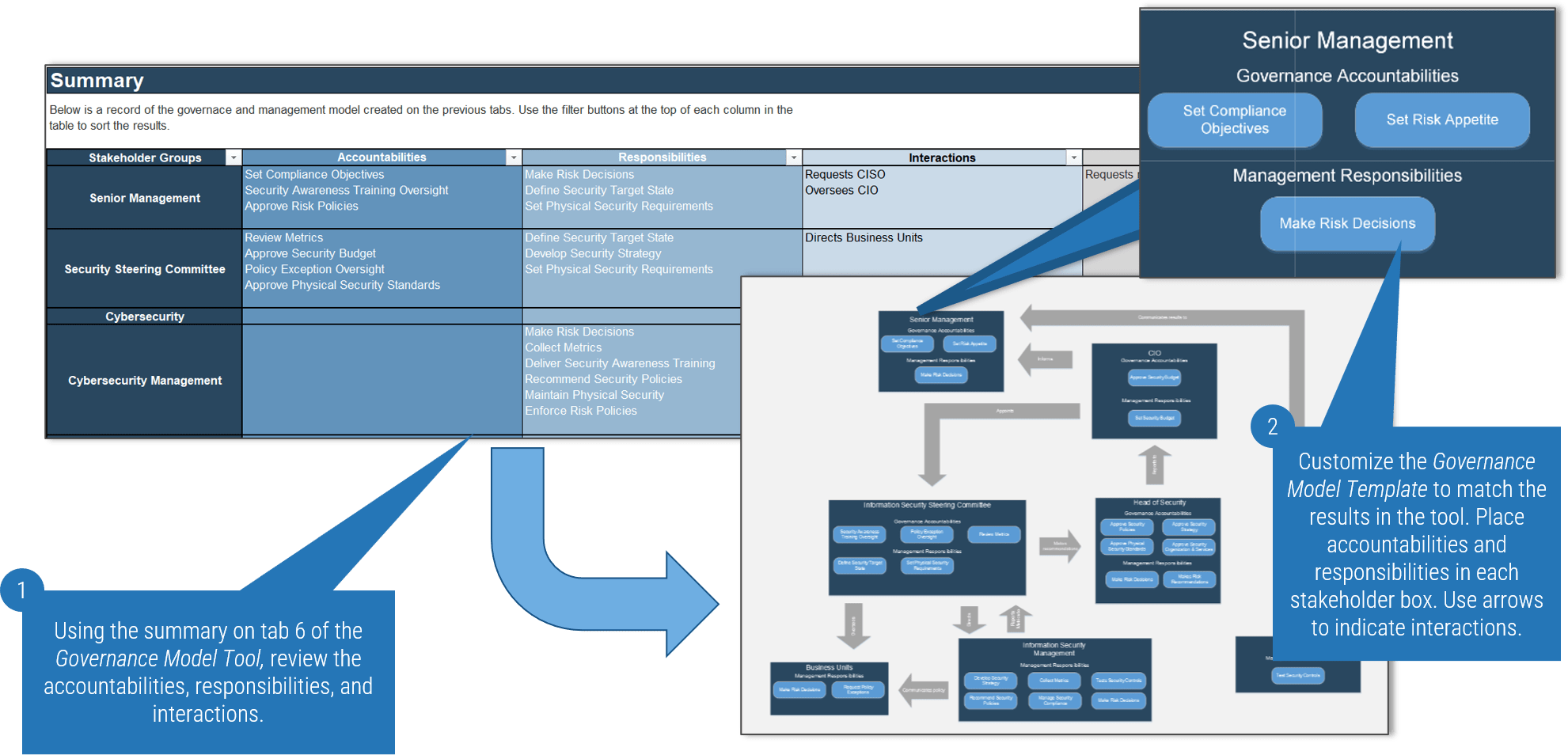
1.2.3 Visualize your security governance and management model
1-2 hours
- Download the Security Governance Model Templates using the link below and determine which of the three example models most closely resembles your own.
- Once you have chosen an example to work from, begin customizing it to reflect the governance model completed in Activity 1.2.2. See next slide for example.
Note: You do not have to use these templates. If you prefer, you can use them as inspiration and design your own model.
Download Security Governance Model Templates
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Customize the template
Step 1.3
Monitor
Activities
1.3.1 Develop governance and management KPIs
This step involves the following participants:
- CISO
- CIO
- Security team
- Business representative
Outcomes of this step
Key performance indicators
Design Your Governance Model
Step 1.1 > Step 1.2 > Step 1.3
Monitor: Getting started
| Element | Questions |
| Metrics | Does the organization have a well-developed metrics program or will this need to be taken up as a separate effort? Have we considered what outcomes we are hoping to see as a result of implementing a new governance and management model? |
| Existing and emerging threats | What has changed or is likely to change in the future that may destabilize our governance program? What do we need to do to mitigate any security risks to our organizational governance and management? |
The above is a summary of COBIT 2019 EDM01.03 Monitor the governance system, along with Info-Tech-recommended questions to contextualize each element for your organization.
1.3.1 Develop governance and management KPIs
1-2 hours
This activity is meant to provide a starting point for key governance metrics. To develop a comprehensive metrics program, see Info-Tech's Build a Security Metrics Program to Drive Maturity blueprint.
- Create a list of four to six outcomes you'd like to see as the result of your new governance model. Be as specific as you can; the better defied the outcome, the easier it will be to determine suitable KPI.
- For each desired outcome, determine what would best indicate that progress is being made toward that state.
- Desired outcome: security team is consulted before critical business decisions are made.
- Success criteria: the business evaluates Security's recommendations before starting new projects
- Possible KPI: % of critical business decisions made with security consultation
- See next slide for additional examples
Note: Try to phrase each KPI using percents, which helps to add context to the metric and will make it easier to explain when reporting metrics in the future.
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Example KPIs
| Desired Outcome | Success Criteria | Possible KPI |
| Security team is consulted before critical business decisions are made | The business evaluates Security's recommendations before starting new projects | % of critical business decisions with Security consultation |
| Greater alignment over risk appetite | The business does not take on initiatives with excessive security risks | % of incidents stemming from not following Security's risk management recommendations |
| Reduced number of policy exceptions | Policy exceptions are only granted when a clear need is present and a formal process is followed | % of incidents stemming from policy exceptions |
| Improved policy adherence | Policies are understood and followed throughout the organization | % of incidents stemming from policy violations |
Establish Baseline Metrics
Baseline metrics will be improved through:
- Improved business alignment
- Developing formal process to manage security risks
- Separating governance from management
| Metric | Current | Goal |
| % of critical business decisions with Security consultation | 20% | 100% |
| % of incidents stemming from not following Security's risk management recommendations | 65% | 0% |
| % of incidents stemming from policy exceptions | 35% | 5% |
| % of incidents stemming from policy violations | 40% | 5% |
| % of ad hoc decisions made (i.e. not accounted for by governance model | 85% | 5% |
| % of accepted security risks evaluated against risk appetite | 50% | 100% |
| % of deferred steering committee decisions (i.e. decisions not made ASAP after issue arises) | 50% | 5% |
| % of policies approved within target window (e.g. 1 month) | 20% | 100% |
Phase 2
Implement Essential Governance Processes
Phase 1
1.1 Evaluate
1.2 Direct
1.3 Monitor
Phase 2
2.1 Implement Oversight
2.2 Set Risk Appetite
2.3 Implement Policy Lifecycle
This phase will walk you through the following activities:
- Draft Steering Committee Charter
- Complete Steering Committee RACI
- Draft qualitative risk statements
- Model policy lifecycle
- Establish exceptions-handling process
This phase involves the following participants:
- CISO
- CRO
- CIO
- HR
- Internal Audit
- Business representative
- Legal
Establish Security Governance & Management
Step 2.1
Implement Oversight
Activities
2.1.1 Draft steering committee charter
2.1.2 Complete steering committee RACI
This step involves the following participants:
- CISO
- CRO
- CIO
- HR
- Internal Audit
- Business representative
- Legal
Outcomes of this step
Steering Committee Charter and RACI
Implement Essential Governance Processes
Step 2.1 > Step 2.2 > Step 2.3
2.1.1 Draft steering committee charter
1-3 hours
This activity is meant to provide a starting point for your steering committee. If a more comprehensive approach is desired, see Info-Tech's Improve Security Governance With a Security Steering Committee blueprint.
- Download the template using the link below and review the various sections of the document
- Review slides 50-51 to help determine the scope of your steering committee's role. Discuss with other stakeholder groups, as necessary, to determine the steering committee's duties, how often the group will meet, and what the regular meeting agenda will be.
- Customize the template to suit your organization's needs.
Download Information Security Steering Committee Charter
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Steering committee membership
Representation is key, but don't try to please everyone
- For your steering committee to be effective, it should include representatives from across the organization. However, it is important not to overextend committee membership, which can interfere with decision making.
- Participants should be selected based on the identified responsibilities of the security steering committee, and the number of people should be appropriate to the size and complexity of the organization.
Example steering committee
CISO
CRO
Internal Audit
CIO
Business Leaders
HR
Legal
Typical steering committee duties
| Strategic Oversight | Policy Governance |
|---|---|
|
|
Typical steering committee duties
| Risk Governance | Monitoring and Reporting |
|---|---|
|
|
2.1.2 Complete steering committee RACI
1-3 hours
- Download the RACI template and review the membership roles. Customize the template to match the makeup of your steering committee.
- Read through each task in the left-hand column and determine who will be involved:
- R - responsible: the person doing the action (can be multiple)
- A - accountable: the owner of the task, usually a department head who delegates the execution of the task (only assigned to one stakeholder)
- C - consulted: stakeholders that offer some kind of guidance, advice, or recommendation (can be multiple)
- I - Informed: stakeholders that receive status updates about the task (can be multiple)
Note: All tasks must have accountability and responsibility assigned (sometimes a single stakeholder is accountable and responsible). However, not all tasks will have someone consulted or informed.
Download Information Security Steering Committee RACI Chart
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Step 2.2
Set Risk Appetite
Activities
2.2.1 Draft qualitative risk statements
This step involves the following participants:
- CISO
- CIO
- Business representative
Outcomes of this step
Qualitative risk appetite
Implement Essential Governance Processes
Step 2.1 > Step 2.2 > Step 2.3
Know your appetite for risk
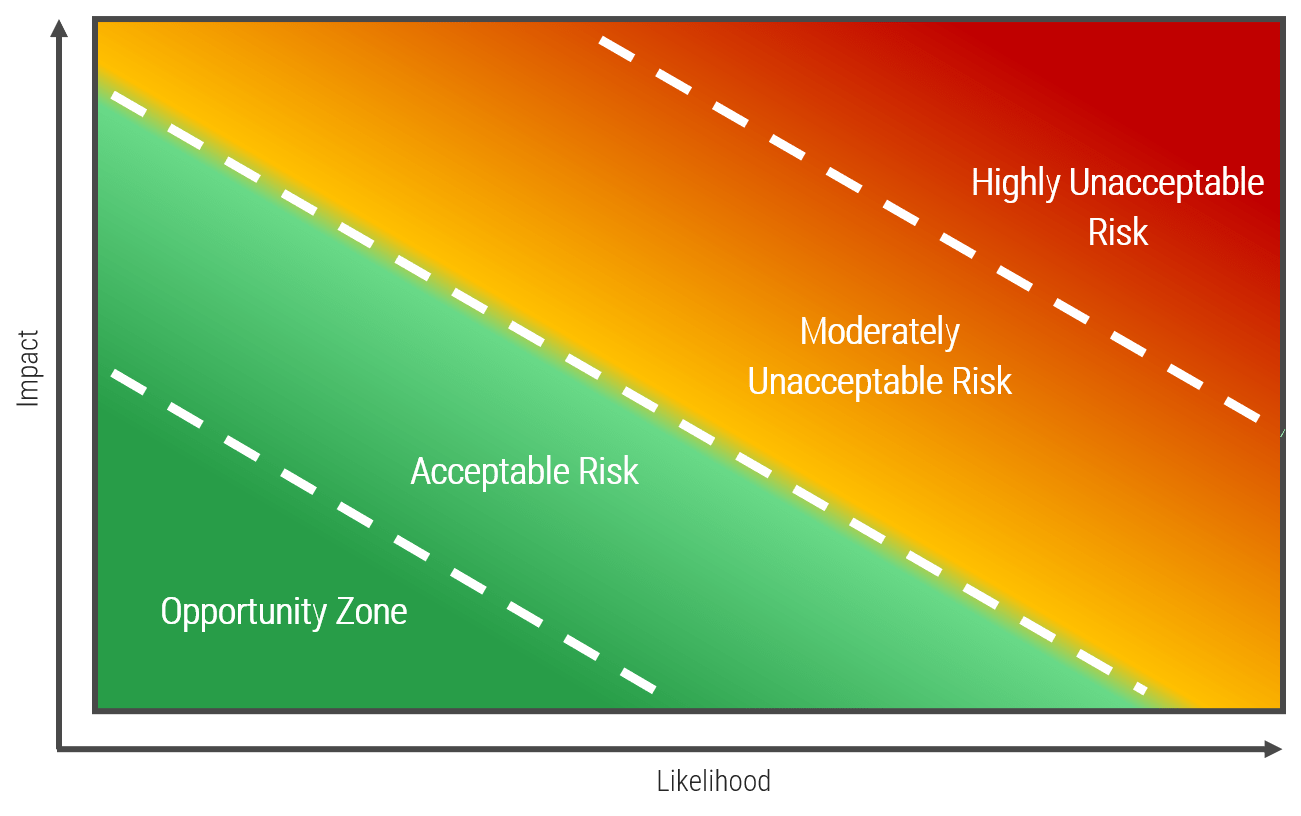
What is an organizational risk appetite?
Setting risk appetite is a key governance function, as it structures how your organization will deal with the risks it will inevitably face - when they can be accepted, when they need to be mitigated, and when they must be rejected entirely.
It is important to note that risk appetite and risk tolerance are not the same. Risk appetite refers to the amount of risk the organization is willing to accept as part of doing business, whereas risk tolerance has more to do with individual risks affecting one or more lines of business that exceed that appetite. Such risks are often tolerated as individual cases that can be mitigated to an acceptable level of risk even though it exceeds the risk-appetite threshold.
2.1.2 Draft qualitative risk-appetite statements
1-3 hours
This activity is meant to provide a starting point for risk governance. To develop a comprehensive risk-management program, see Info-Tech's Combine Security Risk Management Components Into One Program blueprint.
- Draft statements that express your attitudes toward the kinds of risks your organization faces. The point is to set boundaries to better understand when risk mitigation may be necessary. Examples:
- We will not accept risks that may cause us to violate SLAs.
- We will avoid risks that may prevent the organization from operating normally.
- We will not accept risks that may result in exposure of confidential information.
- We will not accept risks that may cause significant brand damage.
- We will not accept risks that pose undue risk to human life or safety.
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Step 2.3
Implement Policy Lifecycle
Activities
2.3.1 Model your policy lifecycle
2.3.2 Establish exception-approval process
This step involves the following participants:
- CISO
- CIO
Outcomes of this step
Policy lifecycle
Exceptions-handling process
Implement Essential Governance Processes
Step 2.1 > Step 2.2 > Step 2.3
2.3.1 Model your policy lifecycle
1-3 hours
This activity is meant to provide a starting point for policy governance. To develop a comprehensive policy-management program, see Info-Tech's Develop and Deploy Security Policies blueprint.
- Review the sections within the Security Policy Lifecycle Template and delete any sections or subsections that do not apply to your organization.
- As necessary, modify the lifecycle and receive approved sign-off by your organization's leadership.
- Solicit feedback from stakeholders, specifically, IT department management and business stakeholders.
Download the Security Policy Lifecycle Template
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Develop the security policy lifecycle
The security policy lifecycle is an integral component of the security policy program and adds value by:
- Setting out a roadmap to define needs, develop required documentation, and implement, communicate, and measure your policy program.
- Defining roles and responsibilities for the security policy suite.
- Aligning the business goals, security program goals, and policy objectives.
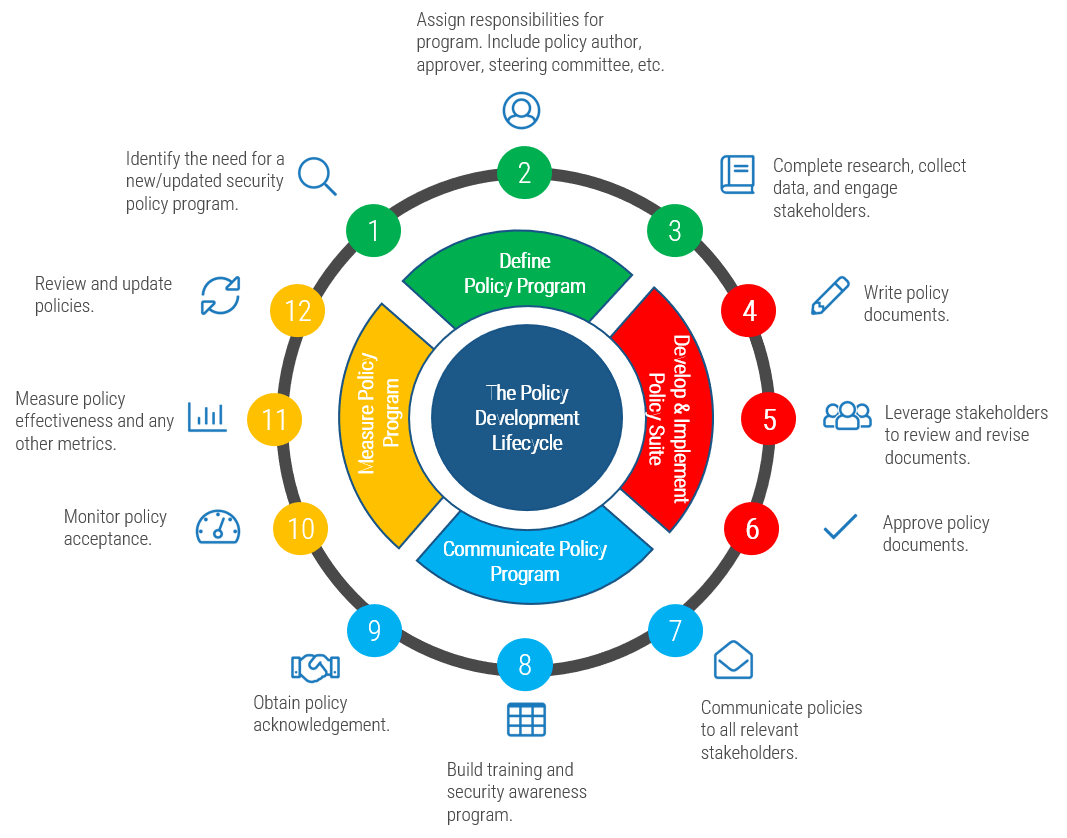
Diagram inspired by: ComplianceBridge, 2021
2.3.2 Establish exception-approval process
1-3 hours
- Download the Security Policy Exception Approval Template and customize it to match your exception-handling process. Be sure to account for the recommendations on the next slide.
- Use the Policy Exception Tracker to record and monitor granted exceptions.
Download the Security Policy Exception Approval Workflow
Download the Security Policy Exception Tracker
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Determine criteria to grant policy exception
A key part of security risk and policy governance
- Not all policies can be complied with all the time. As technology and business needs change, sometimes exceptions must be granted for operations to continue smoothly.
- Exceptions can be either short or long term.
- Short-term exceptions are often granted until a particular security gap can be closed, such as allowing staff to temporarily use new laptops that have yet to receive a required VPN for remote access.
- Long-term exceptions usually occur when closing the gap entirely is not feasible. For example, a legacy system may be unable to meet evolving security standards, but there is no room in the budget to replace it.
- Having a formal approval process for exceptions and a record of granted exceptions will help you to stay on top of security risk governance.
Before granting an exception:
- Assess security risks associated with doing so: are they acceptable?
- Look for another way to resolve the issue: is a suitable workaround possible?
- Evaluate mitigating controls: is it possible to provide an equivalent level of security via other means?
- Assign risk ownership: who will be accountable if an incident arises from the exception?
- Determine appeals process: when disagreements arise, how will the final decision be made?
Sources: University of Virginia; CIS
Summary of Accomplishment
Problem Solved
You have now established a formal governance model for your organization - congratulations! Building this model and determining stakeholders' accountabilities and responsibilities is a big step.
Remember to continue to use the evaluate-direct-monitor framework to make sure your governance model evolves as organizational governance matures and priorities shift.
If you would like additional support, have our analysts guide you through an Info-Tech workshop or Guided Implementation.
Contact your account representative for more information.
workshops@infotech.com
1-888-670-8889
Additional Support
If you would like additional support, have our analysts guide you through other phases as part of an Info-Tech Workshop.
To accelerate this project, engage your IT team in an Info-Tech workshop with an Info-Tech analyst team.
Info-Tech analysts will join you and your team at your location or welcome you to Info-Tech's historic Toronto office to participate in an innovative onsite workshop.
Contact your account representative for more information.
workshops@infotech.com 1-888-670-8889
The following are sample activities that will be conducted by Info-Tech analysts with your team:
Build Governance Model
Build a customized security governance model for your organization.
Develop policy lifecycle
Develop a policy lifecycle and exceptions-handling process.
Related Info-Tech Research
Build an Information Security Strategy
Design a Business-Focused Security Program
Combine Security Risk Management Components Into One Program
Research contributors and experts

Michelle Tran
Consulting Industry
One anonymous contributor
Bibliography
Durbin, Steve. "Achieving The Five Levels Of Information Security Governance." Forbes, 4 Apr. 2023. Accessed 4 Apr. 2023.
Eiden, Kevin, et al. "Organizational Cyber Maturity: A Survey of Industries." McKinsey & Company, 4 Aug. 2021. Accessed 25 Apr. 2023.
"Information Security Exception Policy." Center for Internet Security, 2020. Accessed 14 Apr. 2023.
"Information Security Governance." EDUCAUSE, n.d. Accessed 27 Apr. 2023.
ISACA. COBIT 2019 Framework: Governance and Management Objectives. GF Books, 2018.
Policies & Procedures Team. "Your Policy for Policies: Creating a Policy Management Framework." ComplianceBridge, 30 Apr. 2021. Accessed 27 Apr. 2023.
"Security and the C-Suite: Making Security Priorities Business Priorities." LogRhythm, Feb. 2021. Accessed 25 Apr 2023.
University of Virginia. "Policy, Standards, and Procedures Exceptions Process." Information Security at UVA, 1 Jun. 2022. Accessed 14 Apr. 2023