
Develop Infrastructure & Operations Policies and Procedures
- Time and money are wasted dealing with mistakes or missteps that should have been addressed by procedures or policies.
- Standard operating procedures are less effective without a policy to provide a clear mandate and direction.
- Adhering to policies is rarely a priority, as compliance often feels like an impediment to getting work done.
- Processes aren’t measured or audited to assess policy compliance, which makes enforcing the policies next to impossible.
Our Advice
Critical Insight
- Document what you need to document and forget the rest. Always check to see if you can use a previously approved policy before you create a new one. You may only need to create new guidelines or standards rather than approve a new policy.
Impact and Result
- Start with a comprehensive policy framework to help you identify policy gaps. Prioritize and address those policy gaps.
- Create effective policies that are reasonable, measurable, auditable, and enforceable.
- Create and document procedures to support policy changes.
Develop Infrastructure & Operations Policies and Procedures Research & Tools
Start here – read the Executive Brief
Read our concise Executive Brief to find out why you should change your approach to developing Infrastructure & Operations policies and procedures, review Info-Tech’s methodology, and understand the four ways we can support you in completing this project.Besides the small introduction, subscribers and consulting clients within this management domain have access to:
- Develop Infrastructure & Operations Policies and Procedures – Phases 1-3
1. Identify policy and procedure gaps
Create a prioritized action plan for documentation based on business need.
- Develop Infrastructure & Operations Policies and Procedures – Phase 1: Identify Policy and Procedure Gaps
2. Develop policies
Adapt policy templates to meet your business requirements.
- Develop Infrastructure & Operations Policies and Procedures – Phase 2: Develop Policies
- Availability and Capacity Management Policy
- Business Continuity Management Policy
- Change Control – Freezes & Risk Evaluation Policy
- Change Management Policy
- Configuration Management Policy
- Firewall Policy
- Hardware Asset Management Policy
- IT Triage and Support Policy
- Release Management Policy
- Software Asset Management Policy
- System Maintenance Policy – NIST
- Internet Acceptable Use Policy
3. Document effective procedures
Improve policy adherence and service effectiveness through procedure standardization and documentation.
- Develop Infrastructure & Operations Policies and Procedures – Phase 3: Document Effective Procedures
- Capacity Plan Template
- Change Management Standard Operating Procedure
- Configuration Management Standard Operation Procedures
- Incident Management and Service Desk SOP
- DRP Summary Template
- Service Desk Standard Operating Procedure
- HAM Standard Operating Procedures
- SAM Standard Operating Procedures
Further reading
Develop Infrastructure & Operations Policies and Procedures
Document what you need to document and forget the rest.
Table of contents
Project Rationale
Project Outlines
- Phase 1: Identify Policy and Procedure Gaps
- Phase 2: Develop Policies
- Phase 3: Document Effective Procedures
Bibliography
ANALYST PERSPECTIVE
Document what you need to document now and forget the rest.
"Most IT organizations struggle to create and maintain effective policies and procedures, despite known improvements to consistency, compliance, knowledge transfer, and transparency.
The numbers are staggering. Fully three-quarters of IT professionals believe their policies need improvement, and the same proportion of organizations don’t update procedures as required.
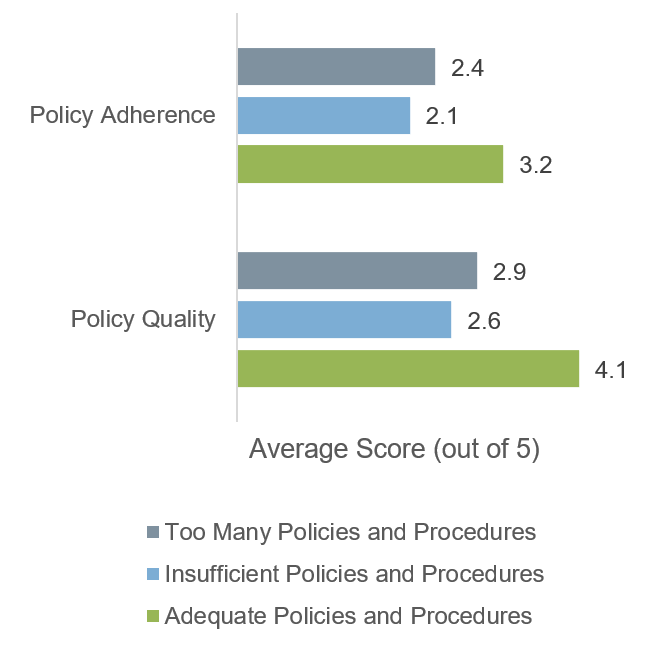
At the same time, organizations that over-document and under-document perform equally poorly on key measures such as policy quality and policy adherence. Take a practical, step-by-step approach that prioritizes the documentation you need now. Leave the rest for later."
(Andrew Sharp, Research Manager, Infrastructure & Operations Practice, Info-Tech Research Group)Our understanding of the problem
This Research Is Designed For:
- Infrastructure Managers
- Chief Technology Officers
- IT Security Managers
This Research Will Help You:
- Address policy gaps
- Develop effective procedures and procedure documentation to support policy compliance
This Research Will Also Assist:
- Chief Information Officers
- Enterprise Risk and Compliance Officers
- Chief Human Resources Officers
- Systems Administrators and Engineers
This Research Will Help Them:
- Understand the importance of a coherent approach to policy development
- Understand the importance of Infrastructure & Operations policies
- Support Infrastructure & Operations policy development and enforcement
Info-Tech Best Practice
This blueprint supports templates for key policies and procedures that help Infrastructure & Operations teams to govern and manage internal operations. For security policies, see the NIST SP 800-171 aligned Info-Tech blueprint, Develop and Deploy Security Policies.
Executive Summary
Situation
- Time and money are wasted dealing with mistakes or missteps that should have been addressed by procedures or policies.
- Standard operating procedures are less effective without a policy to provide a clear mandate and direction.
Complication
- Existing policies were written, approved, signed – and forgotten for years because no one has time to maintain them.
- Adhering to policies is rarely a priority, as compliance often feels like an impediment to getting work done.
- Processes aren’t measured or audited to assess policy compliance, which makes enforcing the policies next to impossible.
Resolution
- Start with a comprehensive policy framework to help you identify policy gaps. Prioritize and address those policy gaps.
- Create effective policies that are reasonable, measurable, auditable, and enforceable.
- Create and document procedures to support policy changes.
Info-Tech Insight
- Document what you need to document and forget the rest.
Always check if a previously approved policy exists before you create a new one. You may only need to create new guidelines or standards rather than approve a new policy. - Support policies with documented procedures.
Build procedures that embed policy adherence in daily operations. Find opportunities to automate policy adherence (e.g. removing local admin rights from user computers).
What are policies, procedures, and processes?
A policy is a governing document that states the long-term goals of the organization and in broad strokes outlines how they will be achieved (e.g. a Data Protection Policy).
In the context of policies, a procedure is composed of the steps required to complete a task (e.g. a Backup and Restore Procedure). Procedures are informed by required standards and recommended guidelines. Processes, guidelines, and standards are three pillars that support the achievement of policy goals.
A process is higher level than a procedure – a set of tasks that deliver on an organizational goal.
Better policies and procedures reduce organizational risk and, by strengthening the ability to execute processes, enhance the organization’s ability to execute on its goals.
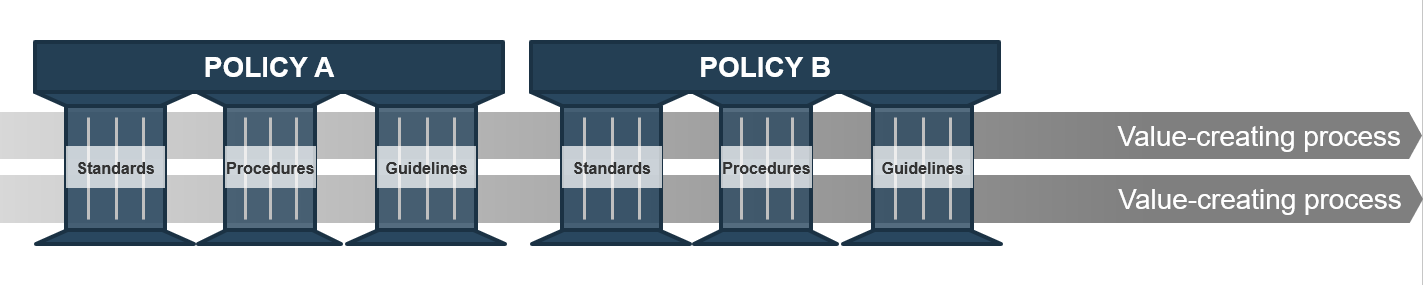
Document to improve governance and operational processes
Deliver value
Build, deliver, and support Infrastructure assets in a consistent way, which ultimately reduces costs associated with downtime, errors, and rework. A good manual process is the foundation for a good automated process.
Simplify Training
Use documentation for knowledge transfer. Routine tasks can be delegated to less-experienced staff.
Maintain compliance
Comply with laws and regulations. Policies are often required for compliance, and formally documented and enforced policies help the organization maintain compliance by mandating required due diligence, risk reduction, and reporting activities.
Provide transparency
Build an open kitchen. Other areas of the organization may not understand how Infra & Ops works. Your documentation can provide the answer to the perennial question: “Why does that take so long?”
Info-Tech Best Practice
Governance goals must be supported with effective, well-aligned procedures and processes. Use Info-Tech’s research to support the key Infrastructure & Operations processes that enable your business to create value.
Document what you need to document – and forget the rest
Half of all organizations believe their policy suite is insufficient. (Info-Tech myPolicies Survey Data (N=59))
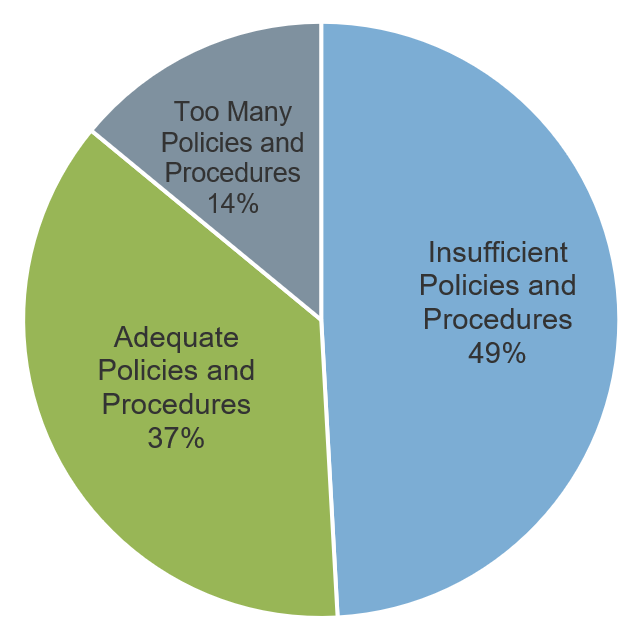
Too much documentation and a lack of documentation are both ineffective. (Info-Tech myPolicies Survey Data (N=59))
77% of IT professionals believe their policies require improvement. (Kaspersky Lab)
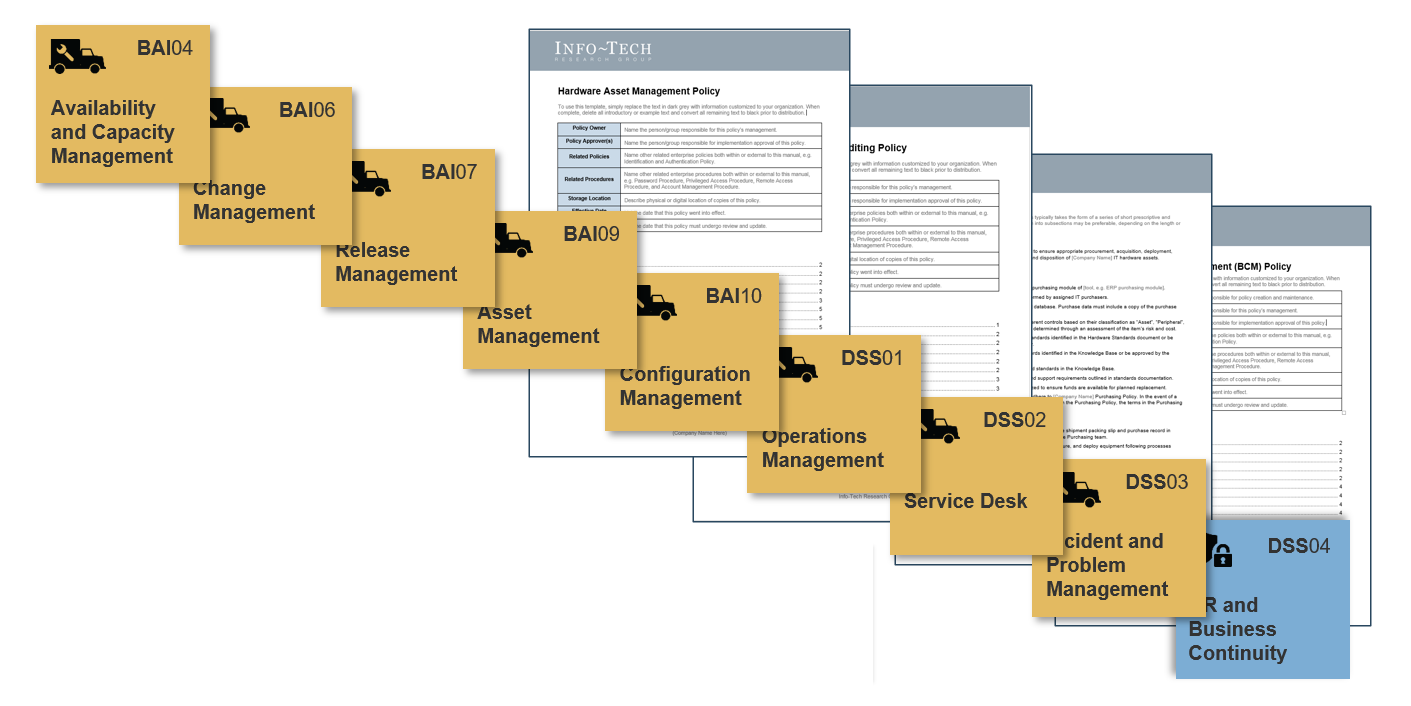
Presenting: A COBIT-aligned policy suite
We’ve developed a suite of effective policy templates for every Infra & Ops manager based on Info-Tech’s IT Management & Governance Framework.
Info-Tech Best Practice
Look for these symbols as you work through the deck. Prioritize and focus on the policies you work on first based on the value of the policy to the enterprise and the existing gaps in your governance structure.
Phases |
1. Identify policy and procedure gaps | 2. Develop policies | 3. Document effective procedures |
Steps |
|
|
|
Outcomes |
Action list of policy and procedure gaps | New or updated Infrastructure & Operations policies | Procedure documentation |
Use these icons to help direct you as you navigate this research
Use these icons to help guide you through each step of the blueprint and direct you to content related to the recommended activities.

This icon denotes a slide where a supporting Info-Tech tool or template will help you perform the activity or step associated with the slide. Refer to the supporting tool or template to get the best results and proceed to the next step of the project.

This icon denotes a slide with an associated activity. The activity can be performed either as part of your project or with the support of Info-Tech team members, who will come onsite to facilitate a workshop for your organization.
Info-Tech offers various levels of support to best suit your needs
DIY Toolkit |
Guided Implementation |
Workshop |
Consulting |
| "Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful." | "Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track." | "We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place." | "Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project." |
Diagnostics and consistent frameworks used throughout all four options
Accelerate policy development with a Guided Implementation
Your trusted advisor is just a call away.
- Identify Policy and Procedure Gaps (Calls 1-2)
Assess current policies, operational challenges, and gaps. Mitigate significant risks first. - Create and Review Policies (Calls 2-4)
Modify and review policy templates with an Info-Tech analyst. - Create and Review Procedures (Calls 4-6)
Workflow procedures, using templates wherever possible. Review documentation best practices.
Contact Info-Tech to set up a Guided Implementation with a dedicated advisor who will walk you through every stage of your policy development project.
Develop Infrastructure & Operations Policies and Procedures
Phase 1
Identify Policy and Procedure Gaps
PHASE 1: Identify Policy and Procedure Gaps
Step 1.1: Review and right-size the existing policy set
This step will walk you through the following activities:
- Identify gaps in your existing policy suite
- Document challenges to core Infrastructure & Operations processes
- Identify documentation that can close gaps
- Prioritize your documentation effort
This step involves the following participants:
- Infrastructure & Operations Manager
- Infrastructure Supervisors
Results & Insights
- Results: A review of the existing policy suite and identification of opportunities for improvement.
- Insights: Not all gaps necessarily require a fresh policy. Repurpose, refresh, or supplement existing documentation wherever appropriate.
Conduct a policy review
You’ve got time to review your policy suite. Make the most of it.
- Start with organizational requirements.
- What initiatives are on the go? What policies or procedures do you have a mandate to create?
- Weed out expired and dated policies.
- Gather your existing policies. Identify when each one was published or last reviewed.
- Decide whether to retire, merge, or update expired or obviously dated policy.
- Review policy statements.
- Check that the organization is adequately supporting policy statements with SOPs, standards, and guidelines. Ensure role-related information is up to date.
- Document and bring any gaps forward to the next activity. If no action is required, indicate that you have completed a review and submit the findings for approval.
But they just want one policy...
A review of your policy suite is good practice, especially when it hasn’t been done for a while. Why?- Existing policies may address what you’re trying to do with a new policy. Using or modifying an existing policy avoids overlap and contradiction and saves you the effort required to create, communicate, approve, and maintain a new policy.
- Review the suite to validate that you’re addressing the most important challenges first.
Brainstorm improvements for core Infrastructure & Operations processes
Supplement the list of gaps from your policy review with process challenges.
- Write out key Infra & Ops–related processes – one piece of flipchart paper per process. You can work through all of these processes or cherry-pick the processes you want to improve first.
- With participants, write out in point form how you currently execute on these processes (e.g. for Asset Management, you might be tagging hardware, tracking licenses, etc.)
- Work through a “Start – Stop – Continue” exercise. Ask participants: What should we start doing? What must we stop doing? What do we do currently that’s valuable and must continue? Write ideas on sticky notes.
- Once you’ve worked through the “Start – Stop – Continue” exercise for all processes, group similar suggestions for improvements.
Asset Management: Manage hardware and software assets across their lifecycle to protect assets and manage costs.
Availability and Capacity Management: Balance current and future availability, capacity, and performance needs with cost-to-serve.
Business Continuity Management: Continue operation of critical business processes and IT services.
Change Management: Deliver technical changes in a controlled manner.
Configuration Management: Define and maintain relationships between technical components.
Problem Management: Identify incident root cause.
Operations Management: Coordinate operations.
Release and Patch Management: Deliver updates and manage vulnerabilities in a controlled manner.
Service Desk: Respond to user requests and all incidents.
PHASE 1: Identify Policy and Procedure Gaps
Step 1.2: Create an action plan to address policy gaps
This step will walk you through the following activities:
- Identify challenges and gaps that can be addressed via documentation
- Prioritize high-value, high-risk gaps
This step involves the following participants:
- Infrastructure & Operations Manager
- Infrastructure Supervisors
Results & Insights
- Results: An action plan to tackle policy and procedures gaps, aligned with business requirements and business value.
- Insights: Not all documentation is equally valuable. Prioritize documentation that delivers value and mitigates risk.
Support policies with procedures, standards, and guidelines
Use a working definition for each type of document.
Policy: Directives, rules, and mandates that support the overarching, long-term goals of the organization.
- Standards: Prescriptive, uniform requirements.
- Procedures: Specific, detailed, step-by-step instructions for completing a task.
- Guidelines: Non-enforceable, recommended best practices.
Info-Tech Best Practice
Take advantage of your Info-Tech advisory membership by scheduling review sessions with an analyst. We provide high-level feedback to ensure your documentation is clear, concise, and consistent and aligns with the governance objectives you’ve identified.
Answer the following questions to decide if governance documentation can help close gaps
![]() 1(c) 30 minutes
1(c) 30 minutes
Documentation supports knowledge sharing, process consistency, compliance, and transparency. Ask the following questions:
- What is the purpose of the documentation?
Procedures support task completion. Policies set direction and manage organizational risk. - Should it be enforceable?
Policies and standards are enforceable; guidelines are not. Procedures are enforceable in that they should support policy enforcement. - What is the scope?
To document a task, create a procedure. Set overarching rules with policies. Use standards and guidelines to set detailed rules and best practices. - What’s the expected cadence for updates?
Policies should be revisited and revised less frequently than procedures.
Info-Tech Best Practice
Reinvent the wheel? I don’t think so!
Always check to see if a gap can be addressed with existing tools before drafting a new policy
- Is there an existing policy that could be supported with new or updated procedures, technical standards, or guidelines?
- Is there a technical control you can deploy that would enforce the terms of an existing, approved policy?
- It may be simpler to amend an existing policy instead of creating a new one.
Some problems can’t be solved by better documentation (or by documentation alone). Consider additional strategies that address people, process, and technology.
Tackle high-value, high-risk gaps first
![]() 1(d) 30 minutes
1(d) 30 minutes
Prioritize your documentation effort.
- List each proposed piece of documentation on the board.
- Assign a score to the risk posed to the business by the lack of documentation and to the expected benefit of completing the documentation. Use a scoring scale between 1 and 3 such as the one on the right.
- Prioritize documentation that mitigates risks and maximizes benefits.
- If you need to break ties, consider effort required to develop, implement, and enforce policies or procedures.
Example Scoring Scale
| Score | Business risk of missing documentation | Business benefit of value of documentation |
1 |
Low: Affects ad hoc activities or non-critical data. | Low: Minimal impact. |
2 |
Moderate: Impacts productivity or internal goodwill. | Moderate: Required periodically; some cross-training opportunities. |
3 |
High: Impacts revenue, safety, or external goodwill. | High: Save time for common or ongoing processes; extensive improvement to training/knowledge transfer. |
Info-Tech Insight
Documentation pulls resources away from other important programs and projects, so ultimately it must be a demonstrably higher priority than other work. This exercise is designed to align documentation efforts with business goals.
Phase 1: Review accomplishments
Policy pillars: Standards, Procedures, Guidelines
Summary of Accomplishments
- Identified gaps in the existing policy suite and identified pain points in existing Infra & Ops processes.
- Developed a list of policies and procedures that can address existing gaps and prioritized the documentation effort.
Develop Infrastructure & Operations Policies and Procedures
Phase 2
Develop Policies
PHASE 2: Develop Policies
Step 2.1: Modify policy templates and gather feedback
This step will walk you through the following activities:
- Modify policy templates
This step involves the following participants:
- Infrastructure & Operations Manager
- Technical Writer
Results & Insights
- Results: Your own COBIT-aligned policies built by modifying Info-Tech templates.
- Insights: Effective policies are easy to read and navigate.
Write Good-er: Be Clear, Consistent, and Concise
Effective policies adhere to the three Cs of documentation.
- Be clear. Make it as easy as possible for a user to learn how to comply with your policy.
- Be consistent. Write policies that complement each other, not contradict each other.
- Be concise. Make it as quick and easy as possible to read and understand your policy.
Info-Tech Best Practice
To download the full suite of templates all at once, click the “Download Research” button on the research landing page on the website.
Use the three Cs: Be Clear
Understanding makes compliance possible. Create policy with the goal of making compliance as easy as possible. Use positive, simple language to convey your intentions and rationale to your audience. Staff will make an effort adhere to your policy when they understand the need and are able to comply with the terms.
- Choose a skilled writer. Select a writer who can write clearly and succinctly.
- Default to simple language and define key terms. Define scope and key terms upfront. Avoid using technical terms outside of technical documentation; if they’re necessary be sure to define them as well.
- Use active, positive language. Where possible, tell people what they can do, not what they can’t.
- Keep the structure simple. Complicated documents are less likely to be understood and read. Use short sentences and paragraphs. Lists are a helpful way to summarize important information. Guide your reader through the document with appropriately named section headers, tables of contents, and numeration.
- Add a process for handling exceptions. Refer to procedures, standards, and guidelines documentation. Try to keep these links as static as possible. Also, refer to a process for handling exceptions.
- Manage the integrity of electronic documents. When published electronically, the policy should have restricted editing access or should be published in a non-editable format. Access to the procedure and policy storage database for employees should be read-only.
Info-Tech Insight
Highly effective policies are easy to navigate. Your policies should be “skimmable.” Very few people will fully read a policy before accepting it. Make it easy to navigate so the reader can easily find the policy statements that apply to them.
Use the three Cs: Be Consistent
Ensure that policies are aligned with other organizational policies and procedures. It detracts from compliance if different policies prescribe different behavior in the same situation. Moreover, your policies should reflect the corporate culture and other company standards. Use your policies to communicate rules and get employees aligned with how your company works.
- Use standard sentences and paragraphs. Policies are usually expressed in short, standard sentences. Lists should also be used when necessary or appropriate.
- Remember the three Ws. When writing a policy, always be sure to clearly state what the rule is, when it should be applied, and who needs to follow it. Policies should clearly define their scope of application and whether directives are mandatory or recommended.
- Use an outline format. Using a numbered or outline format will make a document easier to read and will make content easier to look up when referring back to the document at a later time.
- Avoid amendments. Avoid the use of information that is quickly outdated and requires regular amendment (e.g. names of people).
- Reference a set of supplementary documents. Codify your tactics outside of the policy document, but make reference to them within the text. This makes it easier to ensure consistency in the behavior prescribed by your policies.
"One of the issues is the perception that policies are rules and regulations. Instead, your policies should be used to say ‘this is the way we do things around here.’" (Mike Hughes CISA CGEIT CRISC, Principal Director, Haines-Watts GRC)
Use the three Cs: Be Concise
Reading and understanding policies shouldn’t be challenging, and it shouldn’t significantly detract from productive time. Long policies are more difficult to read and understand, increasing the work required for employees to comply with them. Put it this way: How often do you read the Terms and Conditions of software you’ve installed before accepting them?
- Be direct. The quicker you get to the point, the easier it is for the reader to interpret and comply with your policy.
- Your policy is a rule, not a recipe. Your policy should outline what needs to be accomplished and why – your standards, guidelines, and SOPs address the how.
- Keep policies short. Nobody wants to read a huge policy book, so keep your policies short.
- Use additional documentation where needed. In addition to making consistency easier, this shortens the length of your policies, making them easier to read.
- Policy still too large? Modularize it. If you have an extremely large policy, it’s likely that it’s too widely scoped or that you’re including statements that should be part of procedure documentation. Consider breaking your policy into smaller, focused, more digestible documents.
"If the policy’s too large, people aren’t going to read it. Why read something that doesn’t apply to me?" (Carole Fennelly, Owner and Principal, cFennelly Consulting)
"I always try to strike a good balance between length and prescriptiveness when writing policy. Your policies … should be short and describe the problem and your approach to solving it. Below policies, you write standards, guidelines, and SOPs." (Michael Deskin, Policy and Technical Writer, Canadian Nuclear Safety Commission)
Customize policy documents
Use the policies templates to support key Infrastructure & Operations programs.
INPUT: List of prioritized policies
OUTPUT: Written policy drafts ready for review
Materials: Policy templates
Participants: Policy writer, Signing authority
No policy template will be a perfect fit for your organization. Use Info-Tech’s research to develop your organization’s program requirements. Customize the policy templates to support those requirements.
- Work through policies from highest to lowest priority as defined in Phase 1.
- Follow the instructions written in grey text to customize the policy. Follow the three Cs when you write your policy.
- When your draft is finished, prepare to request signoff from your signing authority by reviewing the draft with an Info-Tech analyst.
- Complete the highest ranked three or four draft policies. Review all these policies with relevant stakeholders and include all relevant signing authorities in the signoff process.
- Rinse and repeat. Iterate until all relevant polices are complete.
Request, Incident, and Problem Management
An effective, timely service desk correlates with higher overall end-user satisfaction across all other IT services. (Info-Tech Research Group, 2016 (N=25,998))
Use the following template to create a policy that outlines the goals and mandate for your service and support organization:
- IT Triage and Support Policy
Support the program and associated policy statements using Info-Tech’s research:
- Standardize the Service Desk
- Incident and Problem Management
- Design & Build a User-Facing Service Catalog
Embrace Standardization
- Outline the support and service mandate with the policy. Support the policy with the methodology in Info-Tech’s research.
- Over time, organizations without standardized processes face confusion, redundancies, and cost overruns. Standardization avoids wasting energy and effort building new solutions to solved issues.
- Standard processes for IT services define repeatable approaches to work and sandbox creative activities.
- Create tickets for every task and categorize them using a standard classification system. Use the resulting data to support root-cause analysis and long-term trend management.
- Create a single point of contact for users for all incidents and requests. Escalate and resolve tickets faster.
- Empower end users and technicians with knowledge bases that help them solve problems without intervention.
Change, Release, and Patch Management
Slow turnaround, unauthorized changes, and change-related incidents are all too familiar to many managers.
Use the following templates to create policies that define effective patch, release, and change management:
- Change Management Policy
- Release and Patch Management Policy
- Change Control – Freezes & Risk Evaluation Policy
Ensure the policy is supported by using the following Info-Tech research:
- Optimize Change Management
Embrace Change
- IT system owners resist change management when they see it as slow and bureaucratic.
- At the same time, an increasingly interlinked technical environment may cause issues to appear in unexpected places. Configuration management systems are often not kept up to date, so preventable conflicts get missed.
- No process exists to support the identification and deployment of critical security patches. Tracking down users to find a maintenance window takes significant, dedicated effort and intervention from the management team.
- Create a unified change management process that reduces risk and is balanced in its approach toward deploying changes, while also maintaining throughput of patches, fixes, enhancements, and innovation.
IT Asset Management (ITAM)
A proactive, dynamic ITAM program will pay dividends in support, contract management, appropriate provisioning, and more.
Start by outlining the requirements for effective asset management:
- Hardware Asset Management Policy
- Software Asset Management Policy
Support ITAM policies with the following Info-Tech research:
- Implement IT Asset Management
Leverage Asset Data
- Create effective, directional policies for your asset management program that provide a mandate for action. Support the policies with robust procedures, capable staff, and right-fit technology solutions.
- Poor management of assets generally leads to higher costs due to duplicated purchases, early replacement, loss, and so on.
- Visibility into asset location and ownership improves security and accountability.
- A centralized repository of asset data supports request fulfilment and incident management.
- Asset management is an ongoing program, not a one-off project, and must be resourced accordingly. Organizations often implement an asset management program and let it stagnate.
"Many of the large data breaches you hear about… nobody told the sysadmin the client data was on that server. So they weren’t protecting and monitoring it." (Carole Fennelly, Owner and Principal, cFennelly Consulting)
Business Continuity Management (BCM)
Streamline the traditional approach to make BCM practical and repeatable.
![]()
Set the direction and requirements for effective BCM:
- Business Continuity Management Policy
Support the BCM policy with the following Info-Tech research:
- Create a Right-Sized Disaster Recovery Plan
- Develop a Business Continuity Plan
Build Organizational Resilience
- Evidence of disaster recovery and business continuity planning is increasingly required to comply with regulations, mitigate business risk, and meet customer demands.
- IT leaders are often asked to take the lead on business continuity, but overall accountability for business continuity rests with the board of directors, and each business unit must create and maintain its business continuity plan.
- Set an organizational mandate for BCM with the policy.
- Divide the business continuity mandate into manageable parcels of work. Follow Info-Tech’s practical methodology to tackle key disaster recovery and business continuity planning activities one at a time.
Info-Tech Best Practice
Governance goals must be supported with effective, well-aligned procedures and processes. Use Info-Tech’s research to support the key Infrastructure & Operations processes that enable your business to create value.
Availability, Capacity, and Operations Management
What was old is new again. Use time-tested techniques to manage and plan cloud capacity and costs.
Set the direction and requirements for effective availability and capacity management:
- Availability and Capacity Management Policy
- System Maintenance Policy – NIST
Support the policy with the following Info-Tech research:
- Develop an Availability and Capacity Management Plan
- Improve IT Operations Management
- Develop an IT Infrastructure Services Playbook
Mature Service Delivery
- Hybrid IT deployments – managing multiple locations, delivery models, and service providers – are the future of IT. Hybrid deployments significantly complicate capacity planning and operations management.
- Effective operations management practices develop structured processes to automate activities and increase process consistency across the IT organization, ultimately improving IT efficiency.
- Trying to add mature service delivery can feel like playing whack-a-mole. Systematically improve your service capabilities using the tactical, iterative approach outlined in Improve IT Operations Management.
Enhance your overall security posture with a defensible, prescriptive policy suite
Align your security policy suite with NIST Special Publication 800-171.
Security policies support the organization’s larger security program. We’ve created a dedicated research blueprint and a set of templates that will help you build security policies around a robust framework.
- Start with a security charter that aligns the security program with organizational objectives.
- Prioritize security policies that address significant risks.
- Work with technical and business stakeholders to adapt Info-Tech’s NIST SP 800-171–aligned policy templates (at right) to reflect your organizational objectives.
Review and download Info-Tech's blueprint Develop and Deploy Security Policies.
Info-Tech Best Practice
Customize Info-Tech’s policy framework to align your policy suite to NIST SP 800-171. Given NIST’s requirements for the control of confidential information, organizations that align their policies to NIST standards will be in a strong governance position.
PHASE 2: Develop Policies
Step 2.2: Implement, enforce, measure, and maintain new policies
This step will walk you through the following activities:
- Gather stakeholder feedback
- Identify preventive and detective controls
- Identify required supports
- Seek policy approval
- Establish roles and responsibilities for policy maintenance
This step involves the following participants:
- Infrastructure & Operations Manager
- Infrastructure Supervisors
- Technical Writer
- Policy Stakeholders
Results & Insights
- Results: Well-supported policies that have received signoff.
- Insights: If you’re not prepared to enforce the policy, you might not actually need a policy. Use the policy statements as guidelines or standards, create and implement procedures, and build a culture of compliance. Once you can confidently execute on required controls, seek signoff.
Gather feedback from users to assess the feasibility of the new policies
![]() 2(b) Review period: 1-2 weeks
2(b) Review period: 1-2 weeks
Once the policies are drafted, roundtable the drafts with stakeholders.
INPUT: Draft policies
OUTPUT: Reviewed policy drafts ready for approval
Materials: Policy drafts
Participants: Policy stakeholders
- Form a test group of users who will be affected by the policy in different ways. Keep the group to around five staff.
- Present new policies to the testers. Allow them to read the documents and attempt to comply with the new policies in their daily routines.
- Collect feedback from the group.
- Consider using interviews, email surveys, chat channels, or group discussions.
- Solicit ideas on how policy statements could be improved or streamlined.
- Make reasonable changes to the first draft of the policies before submitting them for approval. Policies will only be followed if they’re realistic and user friendly.
Info-Tech Best Practice
Allow staff the opportunity to provide input on policy development. Giving employees a say in policy development helps avoid obstacles down the road. This is especially true if you’re trying to change behavior rather than lock it in.
Develop mechanisms for monitoring and enforcement
Brainstorm preventive and detective controls.
INPUT: Draft policies
OUTPUT: Reviewed policy drafts ready for approval
Materials: Policy drafts
Participants: Policy stakeholders
Preventive controls are designed to discourage or pre-empt policy breaches before they occur. Training, approvals processes, and segregation of duties are examples of preventive controls. (Ohio University)
Detective controls help enforce the policy by identifying breaches after they occur. Forensic analysis and event log auditing are examples of detective controls. (Ohio University)
Not all policies require the same level of enforcement. Policies that are required by law or regulation generally require stricter enforcement than policies that outline best practices or organizational values.
Identify controls and enforcement mechanisms that are in line with policy requirements. Build control and enforcement into procedure documentation as needed.
Suggestions:
- Have staff sign off on policies. Disclose any monitoring/surveillance.
- Ensure consequences match the severity of the infraction. Document infractions and ensure that enforcement is applied consistently across all infractions.
- Automatic controls shouldn’t get in the way of people’s ability to do their jobs. Test controls with users before you roll them out widely.
Support the policy before seeking approval
A policy is only as strong as its supporting pillars.
Create Standards
Standards are requirements that support policy adherence. Server builds and images, purchase approval criteria, and vulnerability severity definitions can all be examples of standards that improve policy adherence.
Where reasonable, use automated controls to enforce standards. If you automate the control, consider how you’ll handle exceptions.
Create Guidelines
If no standards exist – or best practices can’t be monitored and enforced, as standards require – write guidelines to help users remain in compliance with the policy.
Create Procedures: We’ll cover procedure development and documentation in Phase 3.
Info-Tech Insight
In general, failing to follow or strictly enforce a policy creates a risk for the business. If you’re not confident a policy will be followed or enforced, consider using policy statements as guidelines or standards as an interim measure as you update procedures and communicate and roll out changes that support adherence and enforcement.
Seek approval and communicate the policy
Policies ultimately need to be accepted by the business.
- Once the drafts are completed, identify who is in charge of approving the policies.
- Ensure all stakeholders understand the importance, context, and repercussions of the policies.
- The approvals process is about appropriate oversight of the drafted policies. For example:
- Do the policies satisfy compliance and regulatory requirements?
- Do the policies work with the corporate culture?
- Do the policies address the underlying need?
If the draft is rejected:
- Acquire feedback and make revisions.
- Resubmit for approval.
If the draft is approved:
- Set the effective date and a review date.
- Begin communication, training, and implementation.
- Employees must know that there are new policies and understand the steps they must take to comply with the policies in their work.
- Employees must be able to interpret, understand, and know how to act upon the information they find in the policies.
- Employees must be informed on where to get help or ask questions and from whom to request policy exceptions.
"A lot of board members and executive management teams… don’t understand the technology and the risks posed by it." (Carole Fennelly, Owner and Principal, cFennelly Consulting)
Identify policy management roles and responsibilities
Discuss and assign roles and responsibilities for ongoing policy management.
Role |
Responsibilities |
Executive sponsor |
|
Program lead |
|
Policy writer |
|
IT infrastructure SMEs |
|
Legal expert |
|
"Whether at the level of a government, a department, or a sub-organization: technology and policy expertise complement one another and must be part of the conversation." (Peter Sheingold, Portfolio Manager, Cybersecurity, MITRE Corporation)
Phase 2: Review accomplishments
Effective Policies: Clear, Consistent, and Concise
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Summary of Accomplishments
- Built priority policies based on templates aligned with the IT Management & Governance Framework and COBIT 5.
- Reviewed controls and policy supports.
- Assigned roles and responsibilities for ongoing policy maintenance.
Develop Infrastructure & Operations Policies and Procedures
Phase 3
Document Effective Procedures
PHASE 3: Document Effective Procedures
Step 3.1: Scope and outline procedures
This step will walk you through the following activities:
- Prioritize SOP documentation
- Draft workflows using a tabletop exercise
- Modify templates, as applicable
This step involves the following participants:
- Infrastructure & Operations Manager
- Technical Writer
- Infrastructure Supervisors
Results & Insights
- Results: An action plan for SOP documentation and an outline of procedure workflows.
- Insights: Don’t let tools get in the way of documentation – low-tech solutions are often the most effective way to build and analyze workflows.
Prioritize your SOP documentation effort
Build SOP documentation that gets used and doesn’t just check a box.
- Review the list of procedure gaps from Phase 1. Are any other procedures needed? Are some of the procedures now redundant?
- Establish the scope of the proposed procedures. Who are the stakeholders? What policies do they support?
- Run a basic prioritization exercise using a three-point scale. Higher scores mean greater risks or greater benefits. Score the risk of the undocumented procedure to the business (e.g. potential effect on data, productivity, goodwill, health and safety, or compliance). Score the benefit to the business of documenting the procedure (e.g. throughput improvements or knowledge transfer).
- Different procedures require different formats. Decide on one or more formats that can help you effectively document the procedure:
- Flowcharts: Depict workflows and decision points. Provide an at-a-glance view that is easy to follow. Can be supported by checklists and diagrams where more detail is required.
- Checklists: A reminder of what to do, rather than how to do it. Keep instructions brief.
- Diagrams: Visualize objects, topologies, and connections for reference purposes.
- Tables: Establish relationships between related categories.
- Prose: Use full-text instructions where other documentation strategies are insufficient.
Modify the following Info-Tech templates for larger SOPs
Support these processes... |
...with these blueprints... |
...to create SOPs using these templates. |
| Create a Right-Sized Disaster Recovery Plan | DRP Summary | |
| Implement IT Asset Management | HAM SOP and SAM SOP | |
| Optimize Change Management | Change Management SOP | |
| Standardize the Service Desk | Service Desk SOP |
Use tabletop planning or whiteboards to draft workflows
![]() 3(b) 30 minutes
3(b) 30 minutes
Tabletop planning is a paper-based exercise in which your team walks through a particular process and maps out what happens at each stage.
OUTPUT: Steps in the current process for one SOP
Materials: Tabletop, pen, and cue cards
Participants: Process owners, SMEs
- For this exercise, choose one particular process to document.
- Document each step of the process on cue cards, which can be arranged on the table in sequence.
- Be sure to include task ownership in your steps.
- Map out the process as it currently happens – we’ll think about how to improve it later.
- Keep focused. Stay on task and on time.
Example:
- Step 3: PM reviews new defects daily
- Step 4: PM assigns defects to tech leads
- Step 5: Assigned resource updates status – frequency is based on ticket priority
Info-Tech Insight
Don’t get weighed down by tools. Relying on software or other technological tools can detract from the exercise. Use simple tools such as cue cards to record steps so that you can easily rearrange steps or insert steps based on input from the group.
Collaborate to optimize the SOP
Review the tabletop exercise. What gaps exist in current processes?
How can the processes be made better? What are the outputs and checkpoints?
OUTPUT: Identify steps to optimize the SOP
Materials: Tabletop, pen, and cue cards
Participants: Process owners, SMEs
Example:
- Step 3: PM reviews new defects daily
- NEW STEP: Schedule 10-minute daily defect reviews with PM and tech leads to evaluate ticket priority
- Step 4: PM assigns defects to tech leads
- Step 5: Assigned resource updates status – frequency is based on ticket priority
- Step 5 Subprocess: Ticket status update
- Step 5 Output: Ticket status moved to OPEN by assigned resource – acknowledges receipt by assigned resource
A note on colors: Use white cards to record steps. Record gaps on yellow cards (e.g. a process step not documented) and risks on red cards (e.g. only one person knows how to execute a step) to highlight your gaps/to-dos and risks to be mitigated or accepted.
If it’s necessary to clarify complex process flows during the exercise, you can also use green cards for decision diamonds, purple for document/report outputs, and blue for subprocesses.
PHASE 3: Document Effective Procedures
Step 3.2: Document effective procedures
This step will walk you through the following activities:
- Document workflows, checklists, and diagrams
- Establish a cadence for document review and updates
This step involves the following participants:
- Infrastructure Manager
- Technical Writer
Results & Insights
- Results: Improved SOP documentation and document management practices.
- Insights: It’s possible to keep up with changes if you put the right cues and accountabilities in place. Include document review in project and change management procedures and hold staff accountable for completion.
Document workflows with flowcharting software
Suggestions for workflow documentation
- Whether you draft the workflow on a whiteboard or using cue cards, the first iteration is usually messy. Clean up the flow as you document the results of the exercise.
- Make the workflow as simple as possible and no simpler. Eliminate any decision points that aren’t strictly necessary to complete the procedure.
- Use standard flowchart shapes (see next slide).
- Use links to connect to related documentation.
- Review the documented workflow with participants.
Download the following workflow examples:
Establish flowcharting standards
If you don’t have existing flowchart standards, then keep it simple and stick to basic flowcharting conventions as described below.

|
Start, End, and Connector: Traditional flowcharting standards reserve this shape for connectors to other flowcharts or other points in the existing flowchart. Unified Modeling Language (UML) also uses the circle for start and end points. |

|
Start and End: Traditional flowcharting standards use this for start and end. However, Info-Tech recommends using the circle shape to reduce the number of shapes and avoid confusion with other similar shapes. |

|
Process Step: Individual process steps or activities (e.g. create ticket or escalate ticket). If it’s a series of steps, then use the subprocess symbol and flowchart the subprocess separately. |

|
Subprocess: A series of steps. For example, a critical incident SOP might reference a recovery process as one of the possible actions. Marking it as a subprocess, rather than listing each step within the critical incident SOP, streamlines the flowchart and avoids overlap with other flowcharts (e.g. the recovery process). |

|
Decision: Represents decision points, typically with Yes/No branches, but you could have other branches depending on the question (e.g. a “Priority?” question could branch into separate streams for Priority 1, 2, 3, 4, and 5 issues). |

|
Document/Report Output: For example, the output from a backup process might include an error log. |
Support workflows with checklists and diagrams
Diagrams
- Diagrams are a visual representation of real-world phenomena and the connections between them.
- Be sure to use standard shapes. Clearly label elements of the diagram. Use standard practices, including titles, dates, authorship, and versioning.
- IT systems and interconnections are layered. Include physical, logical, protocol, and data flow connections.
Examples:
- XMPL Recovery Workflows
- Workflow Library
Checklists
- Checklists are best used as short-form reminders on how to complete a particular task.
- Remember the audience. If the process will be carried out by technical staff, there’s technical background material you won’t need to spell out in detail.
Examples:
- Employee Termination Process Checklist
- XMPL Systems Recovery Playbook
Establish a cadence for documentation review and maintenance
Lock-in the work with strong document management practices.
- Identify documentation requirements as part of project planning.
- Require a manager or supervisor to review and approve SOPs.
- Check documentation status as part of change management.
- Hold staff accountable for documentation.
"It isn’t unusual for us to see infrastructure or operations documentation that is wildly out of date. We’re talking months, even years. Often it was produced as one big effort and then not reliably maintained." (Gary Patterson, Consultant, Quorum Resources)
Only a quarter of organizations update SOPs as needed
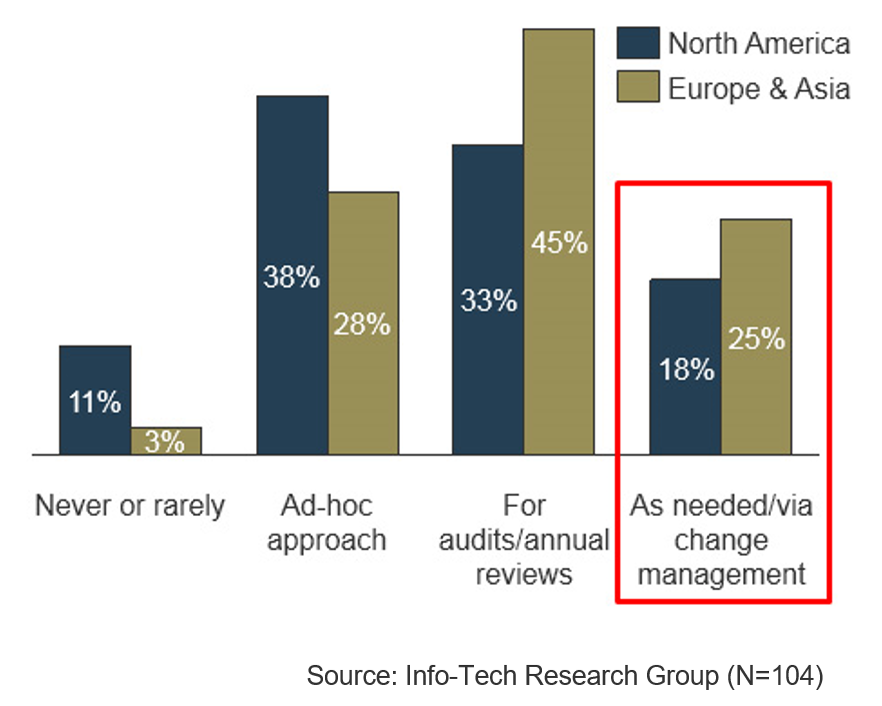
Info-Tech Best Practice
Use Info-Tech’s research Create Visual SOP Documents to further evaluate document management practices and toolsets.
Phase 3: Review accomplishments
Workflow documentation: Cue cards into flowcharts
Summary of Accomplishments
- Identified priority procedures for documentation activities.
- Created procedure documentation in the appropriate format and level of granularity to support Infra & Ops policies.
- Published and maintained procedure documentation.
Research contributors and experts
Carole Fennelly, Owner
cFennelly Consulting

Carole Fennelly provides pragmatic cyber security expertise to help organizations bridge the gap between technical and business requirements. She authored the Center for Internet Security (CIS) Solaris and Red Hat benchmarks, which are used globally as configuration standards to secure IT systems. As a consultant, Carole has defined security strategies, and developed policies and procedures to implement them, at numerous Fortune 500 clients. Carole is a Certified Information Security Manager (CISM), Certified Security Compliance Specialist (CSCS), and Certified HIPAA Professional (CHP).
Marko Diepold, IT Audit Manager
audit2advise

Marko is an IT Audit Manager at audit2advise, where he delivers audit, risk advisory, and project management services. He has worked as a Security Officer, Quality Manager, and Consultant at some of Germany’s largest companies. He is a CISA and is ITIL v3 Intermediate and ITGCP certified.
Research contributors and experts
Martin Andenmatten, Founder & Managing Director
Glenfis AG

Martin is a digital transformation enabler who has been involved in various fields of IT for more than 30 years. At Glenfis, he leads large Governance and Service Management projects for various customers. Since 2002, he has been the course manager for ITIL® Foundation, ITIL® Service Management, and COBIT training. He has published two books on ISO 20000 and ITIL.
Myles F. Suer, CIO Chat Facilitator
CIO.com/Dell Boomi

Myles Suer, according to LeadTails, is the number 9 influencer of CIOs. He is also the facilitator for the CIOChat, which has executive-level participants from around the world in such industries as banking, insurance, education, and government. Myles is also the Industry Solutions Marketing Manager at Dell Boomi.
Research contributors and experts
Peter Sheingold, Portfolio Manager
Cybersecurity, Homeland Security Center, The MITRE Corporation

Peter leads tasks that involve collaboration with the Department of Homeland Security (DHS) sponsors and MITRE colleagues and connect strategy, policy, organization, and technology. He brings a deep background in homeland security and strategic analysis to his work with DHS in the immigration, border security, and cyber mission spaces. Peter came to MITRE in 2005 but has worked with DHS from its inception.
Robert D. Austin, Professor
Ivey Business School

Dr. Austin is a professor of Information Systems at Ivey Business School and an affiliated faculty member at Harvard Medical School. Before his appointment at Ivey, he was a professor of Innovation and Digital Transformation at Copenhagen Business School, and, before that, a professor of Technology and Operations Management at the Harvard Business School.
Research contributors and experts
Ron Jones, Director of IT Infrastructure and Service Management
DATA Communications

Ron is a senior IT leader with over 20 years of management experiences from engineering to IT Service Management and operations support. He is known for joining organizations and leading enhanced process efficiency and has improved software, hardware, infrastructure, and operations solution delivery and support. Ron has worked for global and Canadian firms including BlackBerry, DoubleClick, Cogeco, Infusion, Info-Tech Research Group, and Data Communications Management.
Scott Genung, Executive Director of Networking, Infrastructure, and Service Operations
University of Chicago

Scott is an accomplished IT executive with 26 years of experience in technical and leadership roles. In his current role, Scott provides strategic leadership, vision, and oversight for an IT portfolio supporting 31,000 users consisting of services utilized by campuses located in North America, Asia, and Europe; oversees the University’s Command Center; and chairs the UC Cyberinfrastructure Alliance (UCCA), a group of research IT providers that collectively deliver services to the campus and partners.
Research contributors and experts
Steve Weil, CISSP, CISM, CRISC, Information Security Director, Cybersecurity Principal Consultant
Point B

Steve has 20 years of experience in information security design, implementation, and assessment. He has provided information security services to a wide variety of organizations, including government agencies, hospitals, universities, small businesses, and large enterprises. With his background as a systems administrator, security consultant, security architect, and information security director, Steve has a strong understanding of both the strategic and tactical aspects of information security. Steve has significant hands-on experience with security controls, operating systems, and applications. Steve has a master's degree in Information Science from the University of Washington.
Tony J. Read, Senior Program/Project Lead & Interim IT Executive
Read & Associates

Tony has over 25 years of international IT leadership experience, within high tech, computing, telecommunications, finance, banking, government, and retail industries. Throughout his career, Tony has led and successfully implemented key corporate initiatives, contributing millions of dollars to the top and bottom line. He established Read & Associates in 2002, an international IT management and program/project delivery consultancy practice whose aim is to provide IT value-based solutions, realizing stakeholder economic value and network advantage. These key concepts are presented in his new book: The IT Value Network: From IT Investment to Stakeholder Value, published by J. Wiley, NJ.
Related Info-Tech research
- Develop and Deploy Security Policies
- Develop an Availability and Capacity Management Plan
- Improve IT Operations Management
- Develop an IT Infrastructure Services Playbook
- Create a Right-Sized Disaster Recovery Plan
- Develop a Business Continuity Plan
- Implement IT Asset Management
- Optimize Change Management
- Standardize the Service Desk
- Incident and Problem Management
- Design & Build a User-Facing Service Catalog
Bibliography
“About Controls.” Ohio University, ND. Web. 2 Feb 2018.
England, Rob. “How to implement ITIL for a client?” The IT Skeptic. Two Hills Ltd, 4 Feb. 2010. Web. 2018.
“Global Corporate IT Security Risks: 2013.” Kaspersky Lab, May 2013. Web. 2018.
“Information Security and Technology Policies.” City of Chicago, Department of Innovation and Technology, Oct. 2014. Web. 2018.
ISACA. COBIT 5: Enabling Processes. International Systems Audit and Control Association. Rolling Meadows, IL.: 2012.
“IT Policy & Governance.” NYC Information Technology & Telecommunications, ND. Web. 2018.
King, Paula and Kent Wada. “IT Policy: An Essential Element of IT Infrastructure”. EDUCAUSE Review. May-June 2001. Web. 2018.
Luebbe, Max. “Simplicity.” Site Reliability Engineering. O’Reilly Media. 2017. Web. 2018.
Swartout, Shawn. “Risk assessment, acceptance, and exception with a process view.” ISACA Charlotte Chapter September Event, 2013. Web. 2018.
“User Guide to Writing Policies.” Office of Policy and Efficiency, University of Colorado, ND. Web. 2018.
“The Value of Policies and Procedures.” New Mexico Municipal League, ND. Web. 2018.