
Build a Security Compliance Program
- Most organizations spend between 25 and 40 percent of their security budget on compliance-related activities.
- Despite this growing investment in compliance, only 28% of organizations believe that government regulations help them improve cybersecurity.
- The cost of complying with cybersecurity and data protection requirements has risen to the point where 58% of companies see compliance costs as barriers to entering new markets.
- However, recent reports suggest that while the costs of complying are higher, the costs of non-compliance are almost three times greater.
Our Advice
Critical Insight
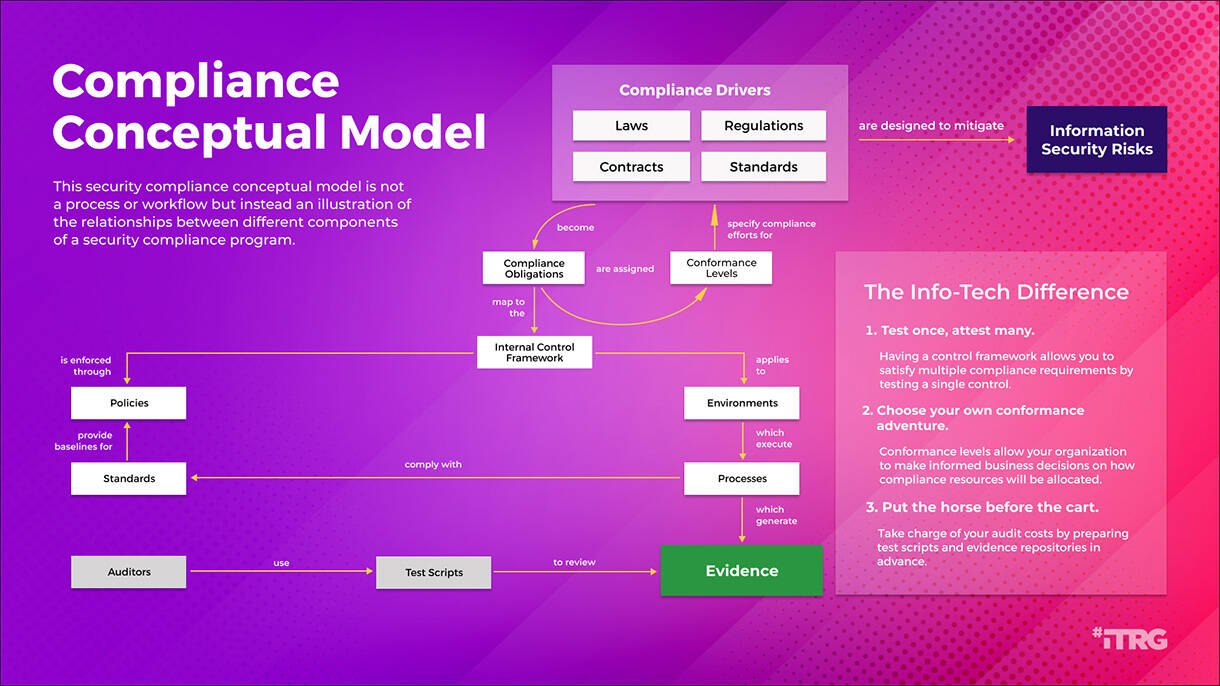
- Test once, attest many. Having a control framework allows you to satisfy multiple compliance requirements by testing a single control.
- Choose your own conformance adventure. Conformance levels allow your organization to make informed business decisions on how compliance resources will be allocated.
- Put the horse before the cart. Take charge of your audit costs by preparing test scripts and evidence repositories in advance.
Impact and Result
- Reduce complexity within the control environment by using a single framework to align multiple compliance regimes.
- Provide senior management with a structured framework for making business decisions on allocating costs and efforts related to cybersecurity and data protection compliance obligations.
- Reduces costs and efforts related to managing IT audits through planning and preparation.
- This blueprint can help you comply with NIST, ISO, CMMC, SOC2, PCI, CIS, and other cybersecurity and data protection requirements.
Build a Security Compliance Program Research & Tools
Start here – read the Executive Brief
Read our concise Executive Brief to find out why you should manage your security compliance obligations, review Info-Tech’s methodology, and understand the ways we can support you in completing this project.Besides the small introduction, subscribers and consulting clients within this management domain have access to:
- Build a Security Compliance Program – Phases 1-5
- Security Compliance Process Template
- Security Compliance Management Tool
Infographic
Workshop: Build a Security Compliance Program
Workshops offer an easy way to accelerate your project. If you are unable to do the project yourself, and a Guided Implementation isn't enough, we offer low-cost delivery of our project workshops. We take you through every phase of your project and ensure that you have a roadmap in place to complete your project successfully.
1 Establish the Program
The Purpose
Establish the security compliance management program.
Key Benefits Achieved
Reviewing and adopting an information security control framework.
Understanding and establishing roles and responsibilities for security compliance management.
Identifying and scoping operational environments for applicable compliance obligations.
Activities
1.1 Review the business context.
1.2 Review the Info-Tech security control framework.
1.3 Establish roles and responsibilities.
1.4 Define operational environments.
Outputs
RACI matrix
Environments list and definitions
2 Identify Obligations
The Purpose
Identify security and data protection compliance obligations.
Key Benefits Achieved
Identifying the security compliance obligations that apply to your organization.
Documenting obligations and obtaining direction from management on conformance levels.
Mapping compliance obligation requirements into your control framework.
Activities
2.1 Identify relevant security and data protection compliance obligations.
2.2 Develop conformance level recommendations.
2.3 Map compliance obligations into control framework.
2.4 Develop process for operationalizing identification activities.
Outputs
List of compliance obligations
Completed Conformance Level Approval forms
(Optional) Mapped compliance obligation
(Optional) Identification process diagram
3 Implement Compliance Strategy
The Purpose
Understand how to build a compliance strategy.
Key Benefits Achieved
Updating security policies and other control design documents to reflect required controls.
Aligning your compliance obligations with your information security strategy.
Activities
3.1 Review state of information security policies.
3.2 Recommend updates to policies to address control requirements.
3.3 Review information security strategy.
3.4 Identify alignment points between compliance obligations and information security strategy.
3.5 Develop compliance exception process and forms.
Outputs
Recommendations and plan for updates to information security policies
Compliance exception forms
4 Track and Report
The Purpose
Track the status of your compliance program.
Key Benefits Achieved
Tracking the status of your compliance obligations.
Managing exceptions to compliance requirements.
Reporting on the compliance management program to senior stakeholders.
Activities
4.1 Define process and forms for self-attestation.
4.2 Develop audit test scripts for selected controls.
4.3 Review process and entity control types.
4.4 Develop self-assessment process.
4.5 Integrate compliance management with risk register.
4.6 Develop metrics and reporting process.
Outputs
Self-attestation forms
Completed test scripts for selected controls
Self-assessment process
Reporting process
Recommended metrics