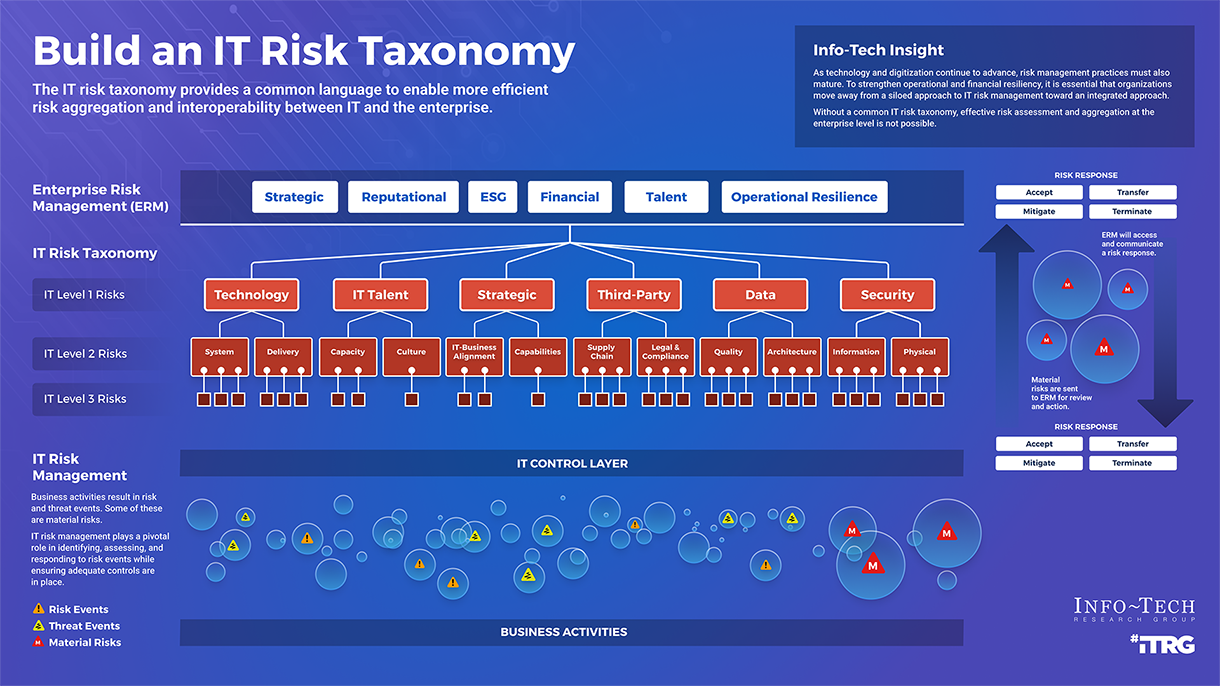
Build an IT Risk Taxonomy

- Business leaders, driven by the need to make more risk-informed decisions, are putting pressure on IT to provide more timely and consistent risk reporting.
- IT risk managers need to balance the emerging threat landscape with not losing sight of the risks of today.
- IT needs to strengthen IT controls and anticipate risks in an age of disruption.
Our Advice
Critical Insight
A common understanding of risks, threats, and opportunities gives organizations the flexibility and agility to adapt to changing business conditions and drive corporate value.
Impact and Result
- Use this blueprint as a baseline to build a customized IT risk taxonomy suitable for your organization.
- Learn about the role and drivers of integrated risk management and the benefits it brings to enterprise decision-makers.
- Discover how to set up your organization up for success by understanding how risk management links to organizational strategy and corporate performance.
Build an IT Risk Taxonomy Research & Tools
Besides the small introduction, subscribers and consulting clients within this management domain have access to:
1. Build an IT Risk Taxonomy – Develop a common approach to managing risks to enable faster, more effective decision making.
Learn how to develop an IT risk taxonomy that will remain relevant over time while providing the granularity and clarity needed to make more effective risk-based decisions.
- Build an IT Risk Taxonomy – Phases 1-3
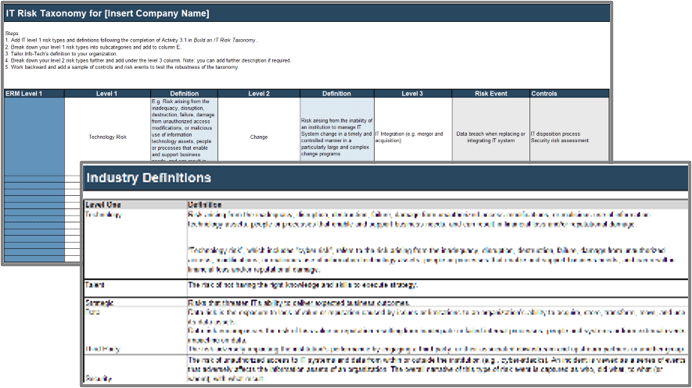
2. Build an IT Risk Taxonomy Guideline and Template – A set of tools to customize and design an IT risk taxonomy suitable for your organization.
Leverage these tools as a starting point to develop risk levels and definitions appropriate to your organization. Take a collaborative approach when developing your IT risk taxonomy to gain greater acceptance and understanding of accountability.
- IT Risk Taxonomy Committee Charter Template
- Build an IT Risk Taxonomy Guideline
- Build an IT Risk Taxonomy Definitions
- Build an IT Risk Taxonomy Design Template
3. IT Risk Taxonomy Workbook – A place to complete activities and document decisions that may need to be communicated.
Use this workbook to document outcomes of activities and brainstorming sessions.
- Build an IT Risk Taxonomy Workbook
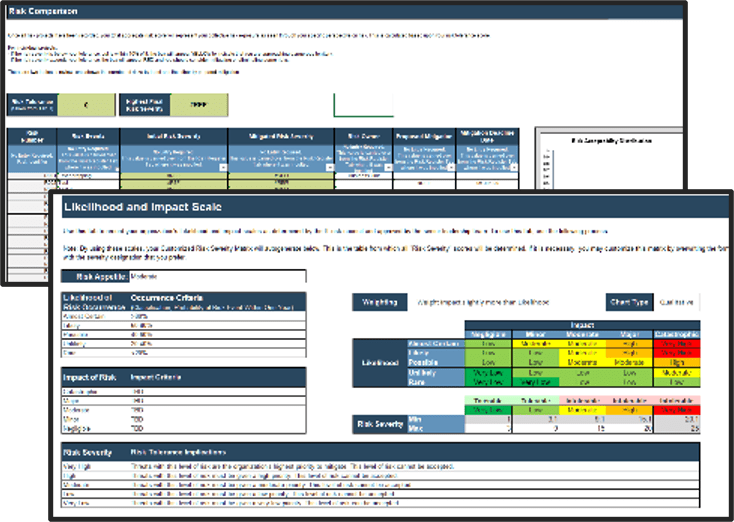
4. IT Risk Register – An internal control tool used to manage IT risks. Risk levels archived in this tool are instrumental to achieving an integrated and holistic view of risks across an organization.
Leverage this tool to document risk levels, risk events, and controls. Smaller organizations can leverage this tool for risk management while larger organizations may find this tool useful to structure and define risks prior to using a risk management software tool.
- Risk Register Tool
Infographic
Workshop: Build an IT Risk Taxonomy
Workshops offer an easy way to accelerate your project. If you are unable to do the project yourself, and a Guided Implementation isn't enough, we offer low-cost delivery of our project workshops. We take you through every phase of your project and ensure that you have a roadmap in place to complete your project successfully.
1 Review IT Risk Fundamentals and Governance
The Purpose
Review IT risk fundamentals and governance.
Key Benefits Achieved
Learn how enterprise risk management and IT risk management intersect and the role the IT taxonomy plays in integrated risk management.
Activities
1.1 Discuss risk fundamentals and the benefits of integrated risk.
1.2 Create a cross-functional IT taxonomy working group.
Outputs
IT Risk Taxonomy Committee Charter Template
Build an IT Risk Taxonomy Workbook
2 Identify Level 1 Risk Types
The Purpose
Identify suitable IT level 1 risk types.
Key Benefits Achieved
Level 1 IT risk types are determined and have been tested against ERM level one risk types.
Activities
2.1 Discuss corporate strategy, business risks, macro trends, and organizational opportunities and constraints.
2.2 Establish level 1 risk types.
2.3 Test soundness of IT level 1 types by mapping to ERM level 1 types.
Outputs
Build an IT Risk Taxonomy Workbook
3 Identify Level 2 and Level 3 Risk Types
The Purpose
Define level 2 and level 3 risk types.
Key Benefits Achieved
Level 2 and level 3 risk types have been determined.
Activities
3.1 Establish level 2 risk types.
3.2 Establish level 3 risk types (and level 4 if appropriate for your organization).
3.3 Begin to test by working backward from controls to ensure risk events will aggregate consistently.
Outputs
Build an IT Risk Taxonomy Design Template
Risk Register Tool
4 Monitor, Report, and Respond to IT Risk
The Purpose
Test the robustness of your IT risk taxonomy by populating the risk register with risk events and controls.
Key Benefits Achieved
Your IT risk taxonomy has been tested and your risk register has been updated.
Activities
4.1 Continue to test robustness of taxonomy and iterate if necessary.
4.2 Optional activity: Draft your IT risk appetite statements.
4.3 Discuss communication and continual improvement plan.
Outputs
Build an IT Risk Taxonomy Design Template
Risk Register Tool
Build an IT Risk Taxonomy Workbook
Further reading
Build an IT Risk Taxonomy
If integrated risk is your destination, your IT risk taxonomy is the road to get you there.
Analyst Perspective

|
The pace and uncertainty of the current business environment introduce new and emerging vulnerabilities that can disrupt an organization’s strategy on short notice. Having a long-term view of risk while navigating the short term requires discipline and a robust and strategic approach to risk management. Managing emerging risks such as climate risk, the impact of digital disruption on internal technology, and the greater use of third parties will require IT leaders to be more disciplined in how they manage and communicate material risks to the enterprise. Establishing a hierarchical common language of IT risks through a taxonomy will facilitate true aggregation and integration of risks, enabling more effective decision making. This holistic, disciplined approach to risk management helps to promote a more sustainable risk culture across the organization while adding greater rigor at the IT control level. Donna Bales |
Executive Summary
|
Your Challenge |
Common Obstacles |
Info-Tech’s Approach |
|---|---|---|
|
IT has several challenges when managing and responding to risk events:
|
Many IT organizations encounter obstacles in these areas:
. |
|
Info-Tech Insight
A common understanding of risks, threats, and opportunities gives organizations the flexibility and agility to adapt to changing business conditions and drive corporate value.
Increasing threat landscape
The risk landscape is continually evolving, putting greater pressure on the risk function to work collaboratively throughout the organization to strengthen operational resilience and minimize strategic, financial, and reputational impact.
|
Financial Impact |
Strategic Risk |
Reputation Risk |
|---|---|---|
|
In IBM’s 2021 Cost of a Data Breach Report, the Ponemon Institute found that data security breaches now cost companies $4.24 million per incident on average – the highest cost in the 17-year history of the report. |
58% percent of CROs who view inability to manage cyber risks as a top strategic risk. EY’s 2022 Global Bank Risk Management survey revealed that Chief Risk Officers (CROs) view the inability to manage cyber risk and the inability to manage cloud and data risk as the top strategic risks. |
Protiviti’s 2023 Executive Perspectives on Top Risks survey featured operational resilience within its top ten risks. An organization’s failure to be sufficiently resilient or agile in a crisis can significantly impact operations and reputation. |
Persistent and emerging threats
Organizations should not underestimate the long-term impact on corporate performance if emerging risks are not fully understood, controlled, and embedded into decision-making.
|
Talent Risk |
Sustainability |
Digital Disruption |
|---|---|---|
|
Protiviti’s 2023 Executive Perspectives on Top Risks survey revealed talent risk as the top risk organizations face, specifically organizations’ ability to attract and retain top talent. Of the 38 risks in the survey, it was the only risk issue rated at a “significant impact” level. |
Sustainability is at the top of the risk agenda for many organizations. In EY’s 2022 Global Bank Risk Management survey, environmental, social, and governance (ESG) risks were identified as a risk focus area, with 84% anticipating it to increase in priority over the next three years. Yet Info-Tech’s Tech Trends 2023 report revealed that only 24% of organizations could accurately report on their carbon footprint. Source: Info-Tech 2023 Tech Trends Report |
The risks related to digital disruption are vast and evolving. In the short term, risks surface in compliance and skills shortage, but Protiviti’s 2023 Executive Perspectives survey shows that in the longer term, executives are concerned that the speed of change and market forces may outpace an organization’s ability to compete. |
Blueprint benefits
|
IT Benefits |
Business Benefits |
|---|---|
|
|
Blueprint deliverables
Each step of this blueprint is accompanied by supporting deliverables to help you accomplish your goals:
|
IT Risk Taxonomy Committee Charter Template Create a cross-functional IT risk taxonomy committee. |

|
Build an IT Risk Taxonomy Guideline Use IT risk taxonomy as a baseline to build your organization’s approach. |

|
|
Build an IT Risk Taxonomy Design Template Use this template to design and test your taxonomy. |
|
Risk Register Tool Update your risk register with your IT risk taxonomy. |
|
Key deliverable:
Build an IT Risk Taxonomy Workbook
Use the tools and activities in each phase of the blueprint to customize your IT risk taxonomy to suit your organization’s needs.

Benefit from industry-leading best practices
As a part of our research process, we used the COSO, ISO 31000, and COBIT 2019 frameworks. Contextualizing IT risk management within these frameworks ensures that our project-focused approach is grounded in industry-leading best practices for managing IT risk.
|
COSO’s Enterprise Risk Management —Integrating with Strategy and Performance addresses the evolution of enterprise risk management and the need for organizations to improve their approach to managing risk to meet the demands of an evolving business environment. |
ISO 31000 – Risk Management can help organizations increase the likelihood of achieving objectives, improve the identification of opportunities and threats, and effectively allocate and use resources for risk treatment. |
COBIT 2019’s IT functions were used to develop and refine the ten IT risk categories used in our top-down risk identification methodology. |
Info-Tech offers various levels of support to best suit your needs
DIY Toolkit“Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful.” |
Guided Implementation“Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track.” |
Workshop“We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place.” |
Consulting“Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project.” |
Diagnostics and consistent frameworks used throughout all four options
Guided Implementation
| Phase 1 | Phase 2 | Phase 3 |
|---|---|---|
|
Call #1: Review risk management fundamentals. |
Call #2: Review the role of an IT risk taxonomy in risk management. Call #3: Establish a cross-functional team. |
Calls #4-5: Identify level 1 IT risk types. Test against enterprise risk management. Call #6: Identify level 2 and level 3 risk types. Call #7: Align risk events and controls to level 3 risk types and test. Call #8: Update your risk register and communicate taxonomy internally. |
A Guided Implementation (GI) is a series
of calls with an Info-Tech analyst to help implement our best practices in your organization.
A typical GI is 6 to 8 calls over the course of 3 to 6 months.
Workshop Overview
Contact your account representative for more information.
workshops@infotech.com 1-888-670-8889
| Day 1 | Day 2 | Day 3 | Day 4 | Day 5 | |
|---|---|---|---|---|---|
|
Review IT Risk Fundamentals and Governance |
Identify Level 1 IT Risk Types |
Identify Level 2 and Level 3 Risk Types |
Monitor, Report, and Respond to IT Risk |
Next Steps and |
|
| Activities |
1.1 Discuss risk fundamentals and the benefits of integrated risk. 1.2 Create a cross-functional IT taxonomy working group. |
2.1 Discuss corporate strategy, business risks, macro trends, and organizational opportunities and constraints. 2.2 Establish level 1 risk types. 2.3 Test soundness of IT level 1 types by mapping to ERM level 1 types. |
3.1 Establish level 2 risk types. 3.2 Establish level 3 risk types (and level 4 if appropriate for your organization). 3.3 Begin to test by working backward from controls to ensure risk events will aggregate consistently. |
4.1 Continue to test robustness of taxonomy and iterate if necessary. 4.2 Optional activity: Draft your IT risk appetite statements. 4.3 Discuss communication and continual improvement plan. |
5.1 Complete in-progress deliverables from previous four days. 5.2 Set up review time for workshop deliverables and to discuss next steps. |
| Deliverables |
|
|
|
|
|
Phase 1
Understand Risk Management Fundamentals
|
Phase 1 |
Phase 2 |
Phase 3 |
|---|---|---|
|
|
|
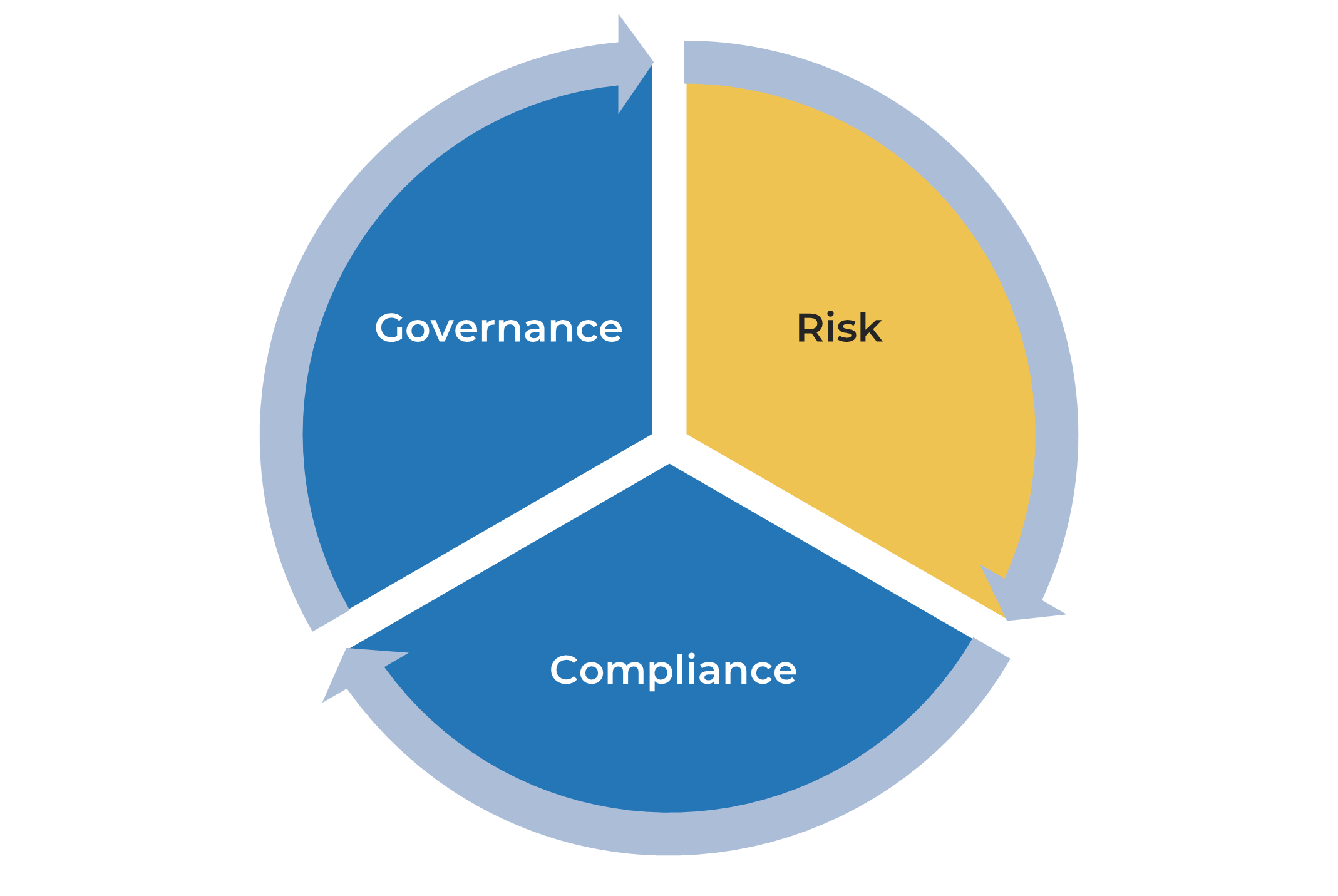
Governance, risk, and compliance (GRC)
Risk management is one component of an organization’s GRC function.
GRC principles are important tools to support enterprise management.
Governance sets the guardrails to ensure that the enterprise is in alignment with standards, regulations, and board decisions. A governance framework will communicate rules and expectations throughout the organization and monitor adherence.
Risk management is how the organization protects and creates enterprise value. It is an integral part of an organization’s processes and enables a structured decision-making approach.
Compliance is the process of adhering to a set of guidelines; these could be external regulations and guidelines or internal corporate policies.
GRC principles are tightly bound and continuous
Enterprise risk management
Regardless of size or structure, every organization makes strategic and operational decisions that expose it to uncertainties.
Enterprise risk management (ERM) is a strategic business discipline that supports the achievement of an organization’s objectives by addressing the full spectrum of its risks and managing the combined impact of those risks as an interrelated risk portfolio (RIMS).
An ERM is program is crucial because it will:
- Help shape business objectives, drive revenue growth, and execute risk-based decisions.
- Enable a deeper understanding of risks and assessment of current risk profile.
- Support forward-looking risk management and more constructive dialogue with the board and regulatory agencies.
- Provide insight on the robustness and efficacy of risk management processes, tools, and controls.
- Drive a positive risk culture.
ERM is supported by strategy, effective processes, technology, and people
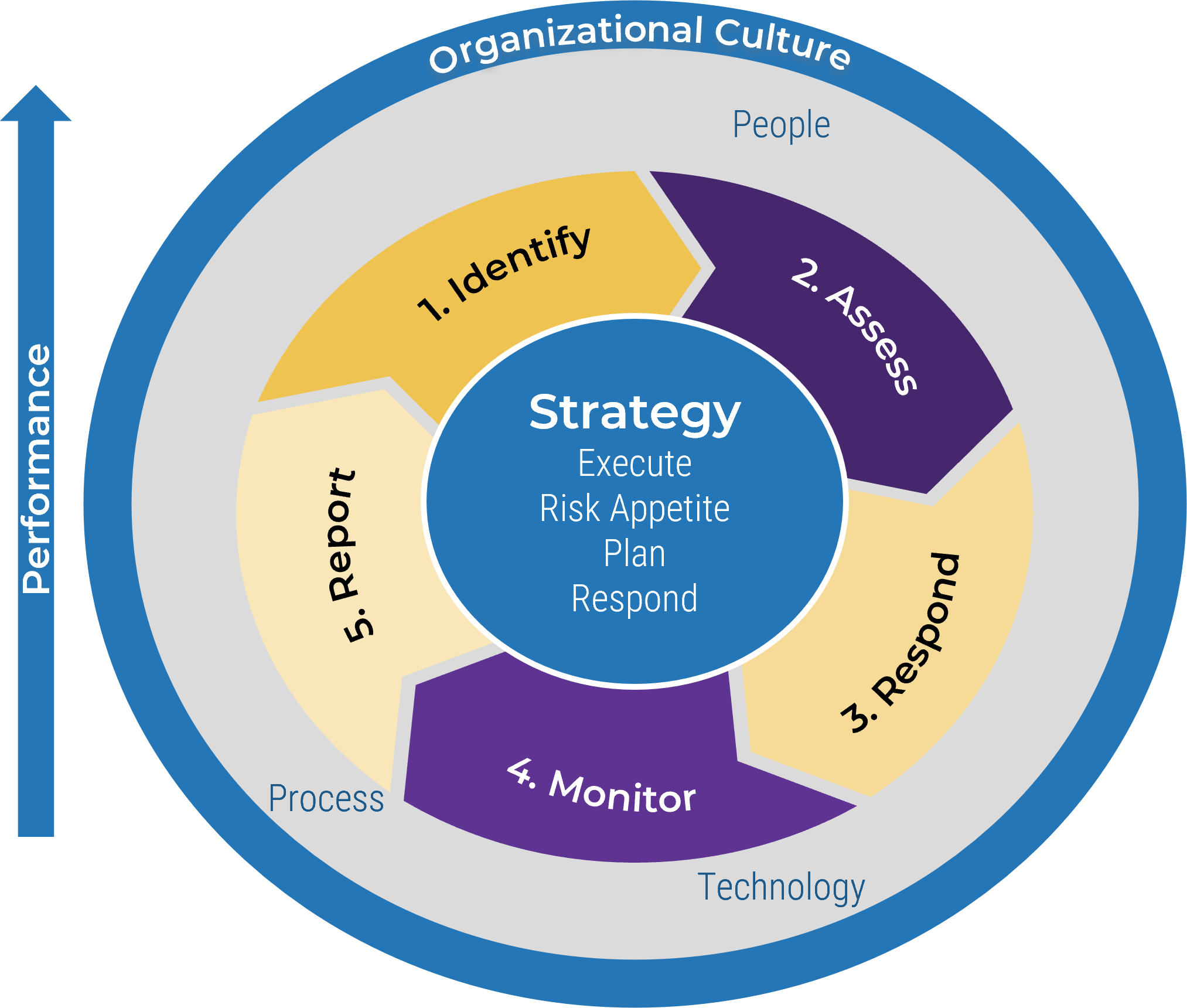
Risk frameworks
Risk frameworks are leveraged by the industry to “provide a structure and set of definitions to allow enterprises of all types and sizes to understand and better manage their risk environments.” COSO Enterprise Risk Management, 2nd edition
- Many organizations lean on the Committee of Sponsoring Organizations’ Enterprise Risk Management framework (COSO ERM) and ISO 31000 to view organizational risks from an enterprise perspective.
- Prior to the introduction of standardized risk frameworks, it was difficult to quantify the impact of a risk event on the entire enterprise, as the risk was viewed in a silo or as an individual risk component.
- Recently, the National Institute of Science and Technology (NIST) published guidance on developing an enterprise risk management approach. The guidance helps to bridge the gap between best practices in enterprise risk management and processes and control techniques that cybersecurity professionals use to meet regulatory cybersecurity risk requirements.
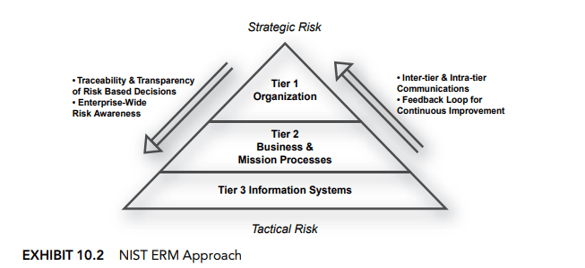
Source: National Institute of Standards and Technology
New NIST guidance (NISTIR 8286) emphasizes the complexity of risk management and the need for the risk management process to be carried out seamlessly across three tiers with the overall objective of continuous improvement.
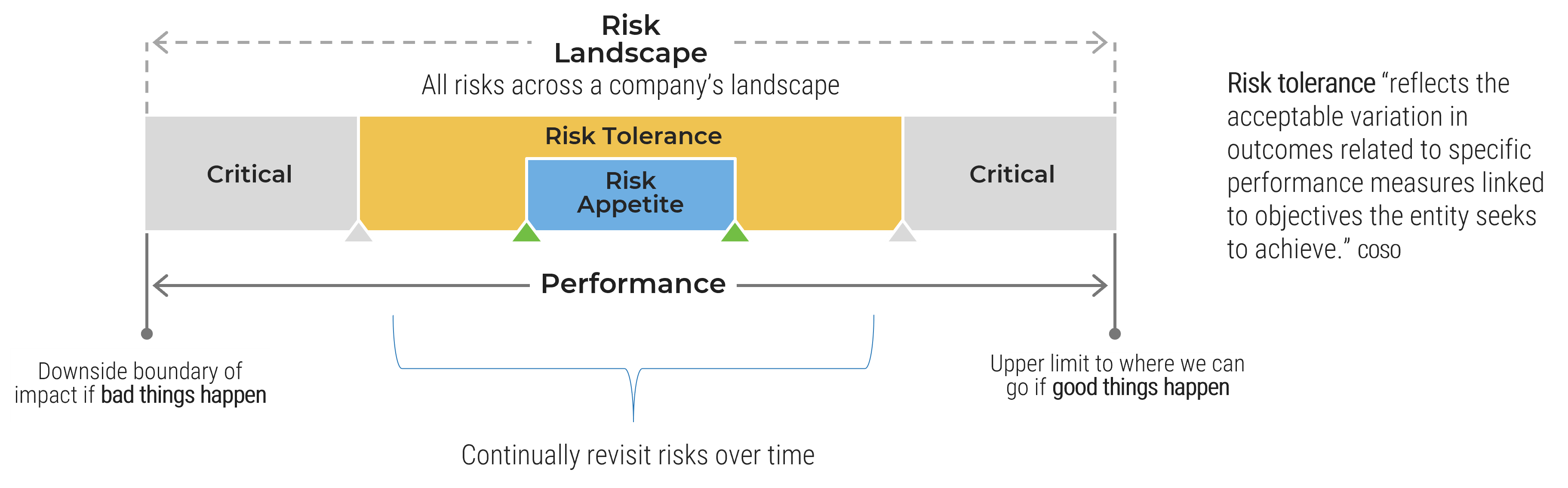
Enterprise risk appetite
“The amount of risk an organization is willing to take in pursuit of its objectives”
– Robert R. Moeller, COSO ERM Framework Model
- A primary role of the board and senior management is to balance value creation with effectively management of enterprise risks.
- As part of this role, the board will approve the enterprise’s risk appetite. Placing this responsibility with the board ensures that the risk appetite is aligned with the company’s strategic objectives.
- The risk appetite is used throughout the organization to assess and respond to individual risks, acting as a constant to make sure that risks are managed within the organization’s acceptable limits.
- Each year, or in reaction to a risk trigger, the enterprise risk appetite will be updated and approved by the board.
- Risk appetite will vary across organizations for several reasons, such as industry, company culture, competitors, the nature of the objectives pursued, and financial strength.
Change or new risks » adjust enterprise risk profile » adjust risk appetite
Risk profile vs. risk appetite
Risk profile is the broad parameters an organization considers in executing its business strategy. Risk appetite is the amount of risk an entity is willing to accept in pursuit of its strategic objectives. The risk appetite can be used to inform the risk profile or vice versa. Your organization’s risk culture informs and is used to communicate both.
|
Risk Tolerant |
Moderate |
Risk Averse |
|---|---|---|
|
|
|
Where the IT risk appetite fits into the risk program
- Your organization’s strategy and associated risk appetite cascade down to each business department. Overall strategy and risk appetite also set a strategy and risk appetite for each department.
- Both risk appetite and risk tolerances set boundaries for how much risk an organization is willing or prepared to take. However, while appetite is often broad, tolerance is tactical and focused.
- Tolerances apply to specific objectives and provide guidance to those executing on a day-to-day basis. They measure the variation around performance expectations that the organization will tolerate.
- Ideally, they are incorporated into existing governance, risk, and compliance systems and are also considered when evaluated business cases.
- IT risk appetite statements are based on IT level 1 risk types.
The risk appetite has a risk lens but is also closely linked to corporate performance.
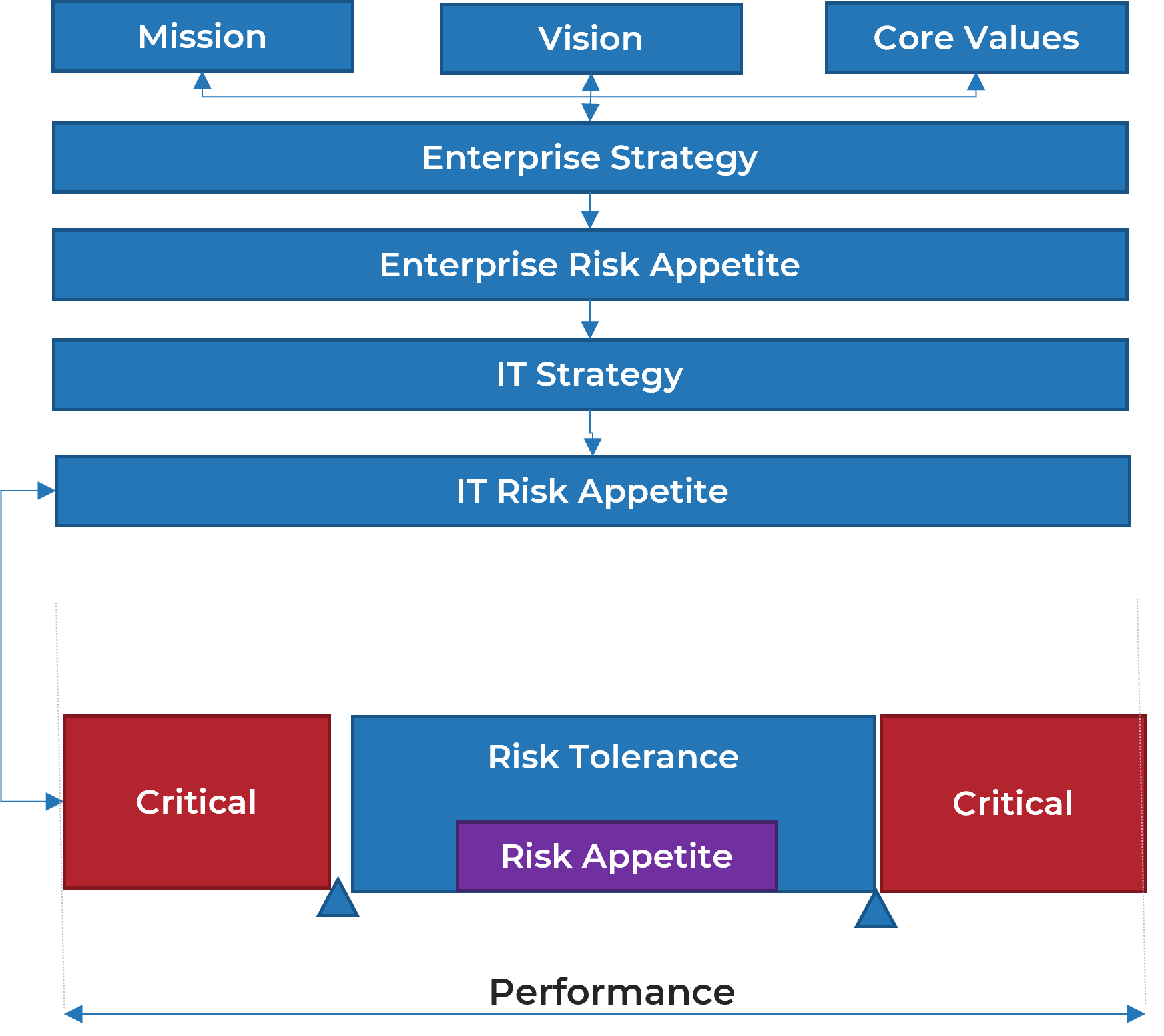
Statements of risk
|
Risk Appetite |
Risk Tolerance |
|---|---|
|
|
Risk scenarios
Risk scenarios serve two main purposes: to help decision makers understand how adverse events can affect organizational strategy and objectives and to prepare a framework for risk analysis by clearly defining and decomposing the factors contributing to the frequency and the magnitude of adverse events.
ISACA
- Organizations’ pervasive use of and dependency on technology has increased the importance of scenario analysis to identify relevant and important risks and the potential impacts of risk events on the organization if the risk event were to occur.
- Risk scenarios provide “what if” analysis through a structured approach, which can help to define controls and document assumptions.
- They form a constructive narrative and help to communicate a story by bringing in business context.
- For the best outcome, have input from business and IT stakeholders. However, in reality, risk scenarios are usually driven by IT through the asset management practice.
- Once the scenarios are developed, they are used during the risk analysis phase, in which frequency and business impacts are estimated. They are also a useful tool to help the risk team (and IT) communicate and explain risks to various business stakeholders.
Top-down approach – driven by the business by determining the business impact, i.e. what is the impact on my customers, reputation, and bottom line if the system that supports payment processing fails?
Bottom-up approach – driven by IT by identifying critical assets and what harm could happen if they were to fail.
Example risk scenario
Use level 1 IT risks to derive potential scenarios.
|
Risk Scenario Description |
Example: IT Risks |
|
|---|---|---|
|
Risk Scenario Title |
A brief description of the risk scenario |
The enterprise is unable to recruit and retain IT staff |
|
Risk Type |
The process or system that is impacted by the risk |
|
|
Risk Scenario Category |
Deeper insight into how the risk might impact business functions |
|
|
Risk Statement |
Used to communicate the potential adverse outcomes of a particular risk event and can be used to communicate to stakeholders to enable informed decisions |
The organization chronically fails to recruit sufficiently skilled IT workers, leading to a loss of efficiency in overall technology operation and an increased security exposure. |
|
Risk Owner |
The designated party responsible and accountable for ensuring that the risk is maintained in accordance with enterprise requirements |
|
|
Risk Oversight |
The person (role) who is responsible for risk assessments, monitoring, documenting risk response, and establishing key risk indicators |
CRO/COO |
Phase 2
Set Your Organization Up for Success
Phase 1 | Phase 2 | Phase 3 |
|---|---|---|
|
|
|
This phase will walk you through the following activities:
- How to set up a cross-functional IT risk taxonomy committee
This phase involves the following participants:
- CIO
- CISO
- CRO
- IT Risk Owners
- Business Leaders
- Human Resources
What is a risk taxonomy?
A risk taxonomy provides a common risk view and enables integrated risk
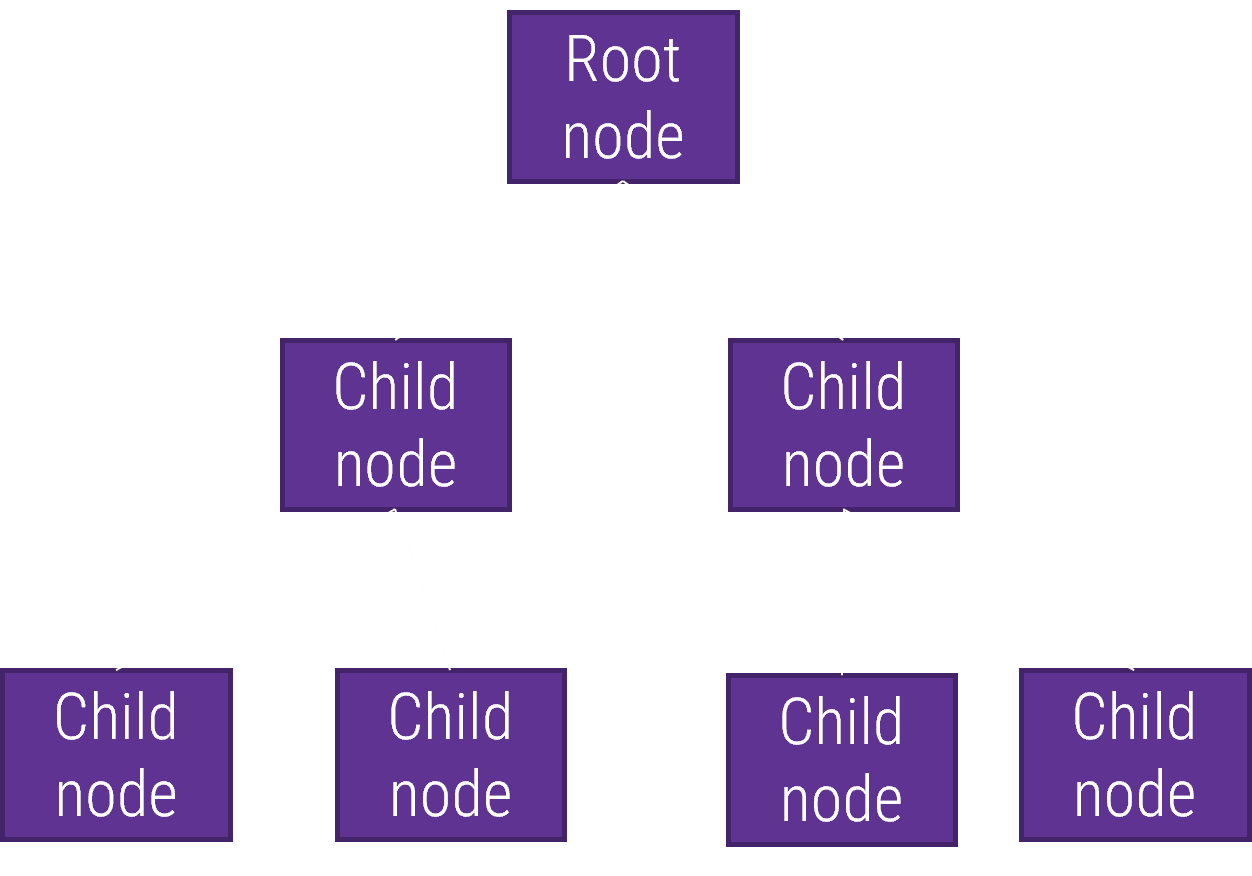
- A risk taxonomy is the (typically hierarchical) categorization of risk types. It is constructed out of a collection of risk types organized by a classification scheme.
- Its purpose is to assist with the management of an organization’s risk by arranging risks in a classification scheme.
- It provides foundational support across the risk management lifecycle in relation to each of the key risks.
- More material risk categories form the root nodes of the taxonomy, and risk types cascade into more granular manifestations (child nodes).
- From a risk management perspective, a taxonomy will:
- Enable more effective risk aggregation and interoperability.
- Provide the organization with a complete view of risks and how risks might be interconnected or concentrated.
- Help organizations form a robust control framework.
- Give risk managers a structure to manage risks proactively.
Typical Tree Structure
What is integrated risk management?
- Integrated risk management is the process of ensuring all forms of risk information, including risk related to information and technology, are considered and included in the organization’s risk management strategy.
- It removes the siloed approach of classifying risks related to specific departments or areas of the organization, recognizing that each risk is a potential threat to the overarching enterprise.
- By aggregating the different threats or uncertainty that might exist within an organization, integrated risk management enables more informed decisions to be made that align to strategic goals and continue to drive value back to the business.
- By holistically considering the different risks, the organization can make informed decisions on the best course of action that will reduce any negative impacts associated with the uncertainty and increase the overall value.
Integrated risk management: A strategic and collaborative way to manage risks across the organization. It is a forward-looking, business-specific outlook with the objective of improving risk visibility and culture.
Drivers and benefits of integrated risk
Drivers for Integrated Risk Management
- Business shift to digital experiences
- The breadth and number of risks requiring oversight
- The need for faster risk analysis and decision making
Benefits of Integrated Risk Management
- Enables better scenario planning
- Enables more proactive risk responses
- Provides more relevant risk assurance to key stakeholders
- Improves transparency and comparability of risks across organizational silos
- Supports better financial resilience
Business velocity and complexity are making real-time risk management a business necessity.
If integrated risk is the destination, your taxonomy is your road to get you there
Info-Tech’s Model for Integrated Risk
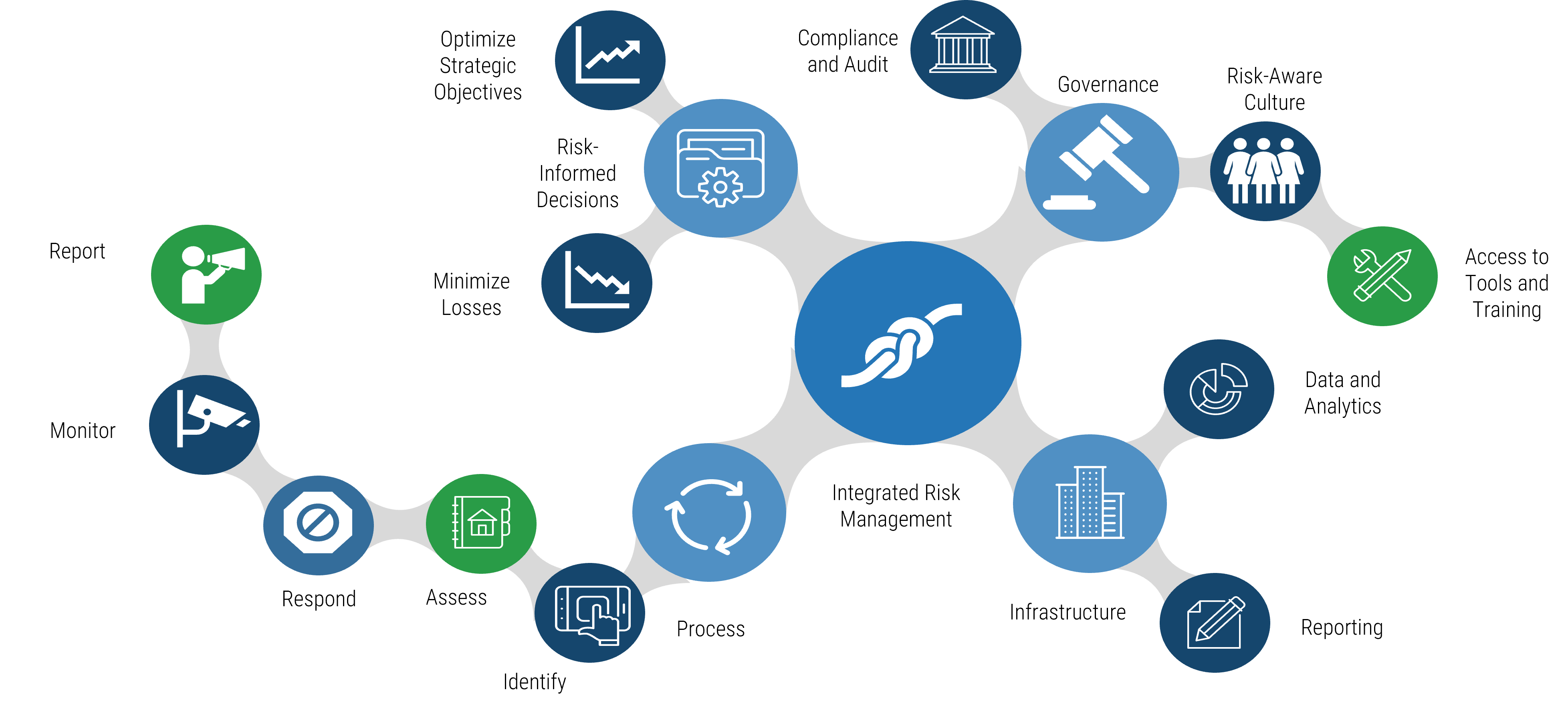
How the risk practices intersect
The risk taxonomy provides a common classification of risks that allows risks to roll up systematically to enterprise risk, enabling more effective risk responses and more informed decision making.
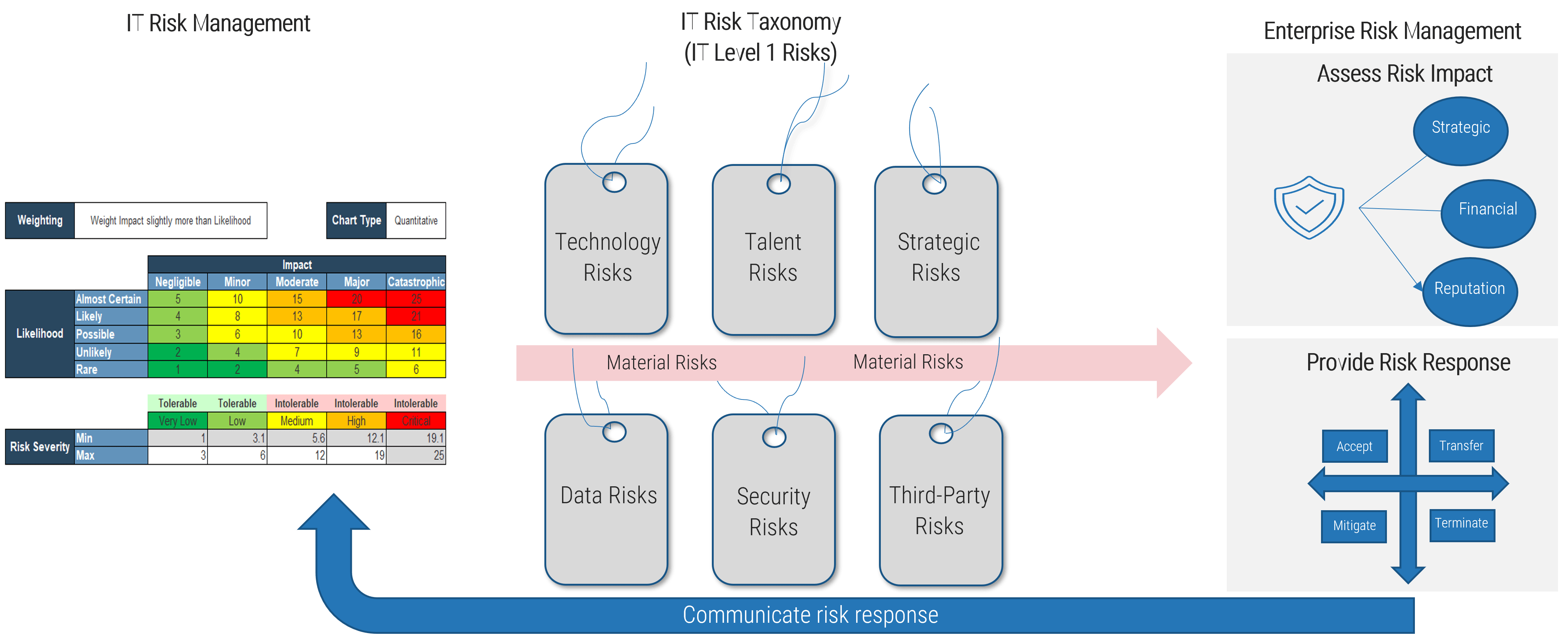
ERM taxonomy
Relative to the base event types, overall there is an increase in the number of level 1 risk types in risk taxonomies
Oliver Wyman
- The changing risk profile of organizations and regulatory focus in some industries is pushing organizations to rethink their risk taxonomies.
- Generally, the expansion of level 1 risk types is due to the increase in risk themes under the operational risk umbrella.
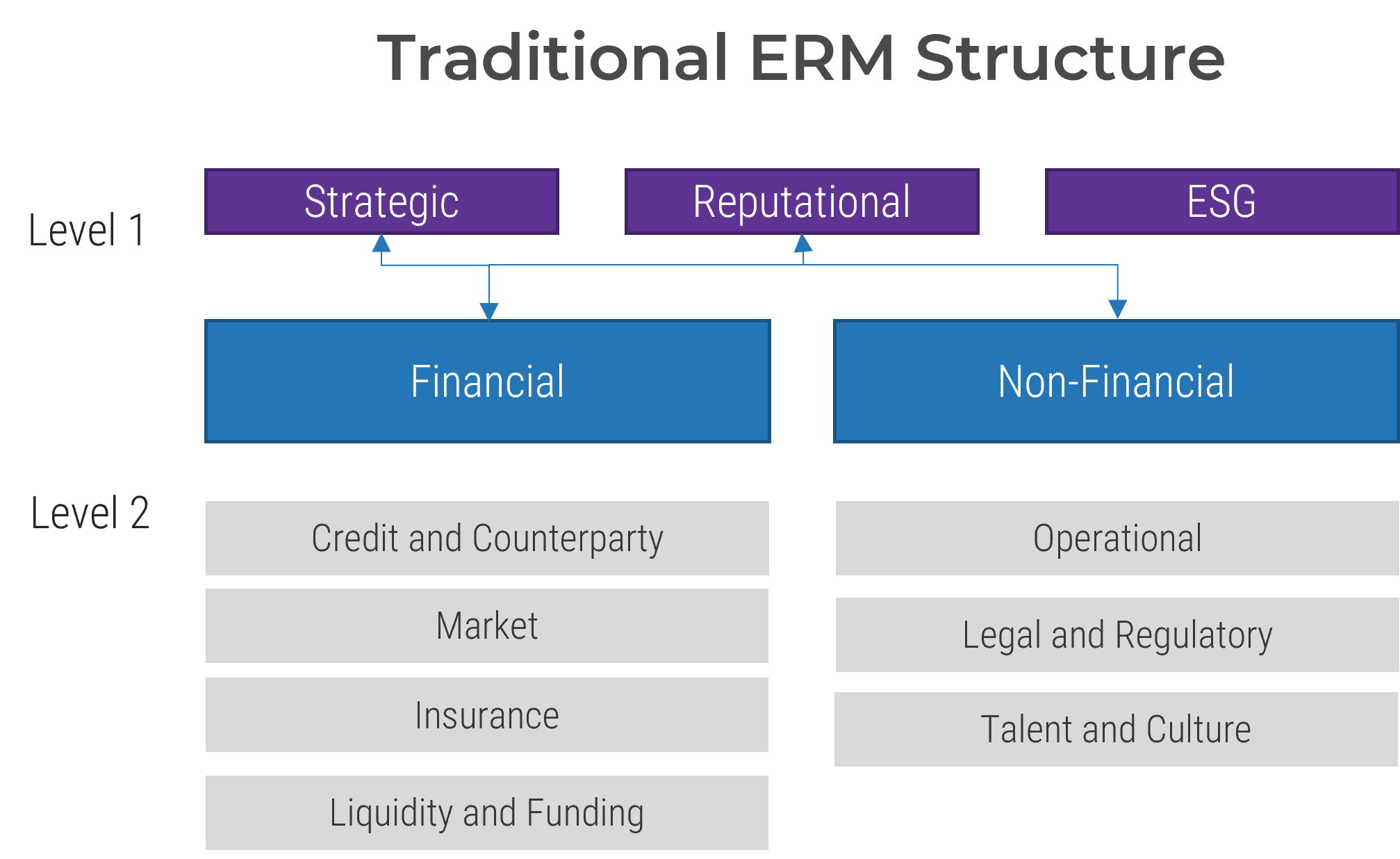
- Non-financial risks are risks that are not considered to be traditional financial risks, such as operational risk, technology risk, culture, and conduct. Environmental, social, and governance (ESG) risk is often referred to as a non-financial risk, although it can have both financial and non-financial implications.
- Certain level 1 ERM risks, such as strategic risk, reputational risk, and ESG risk, cover both financial and non-financial risks.
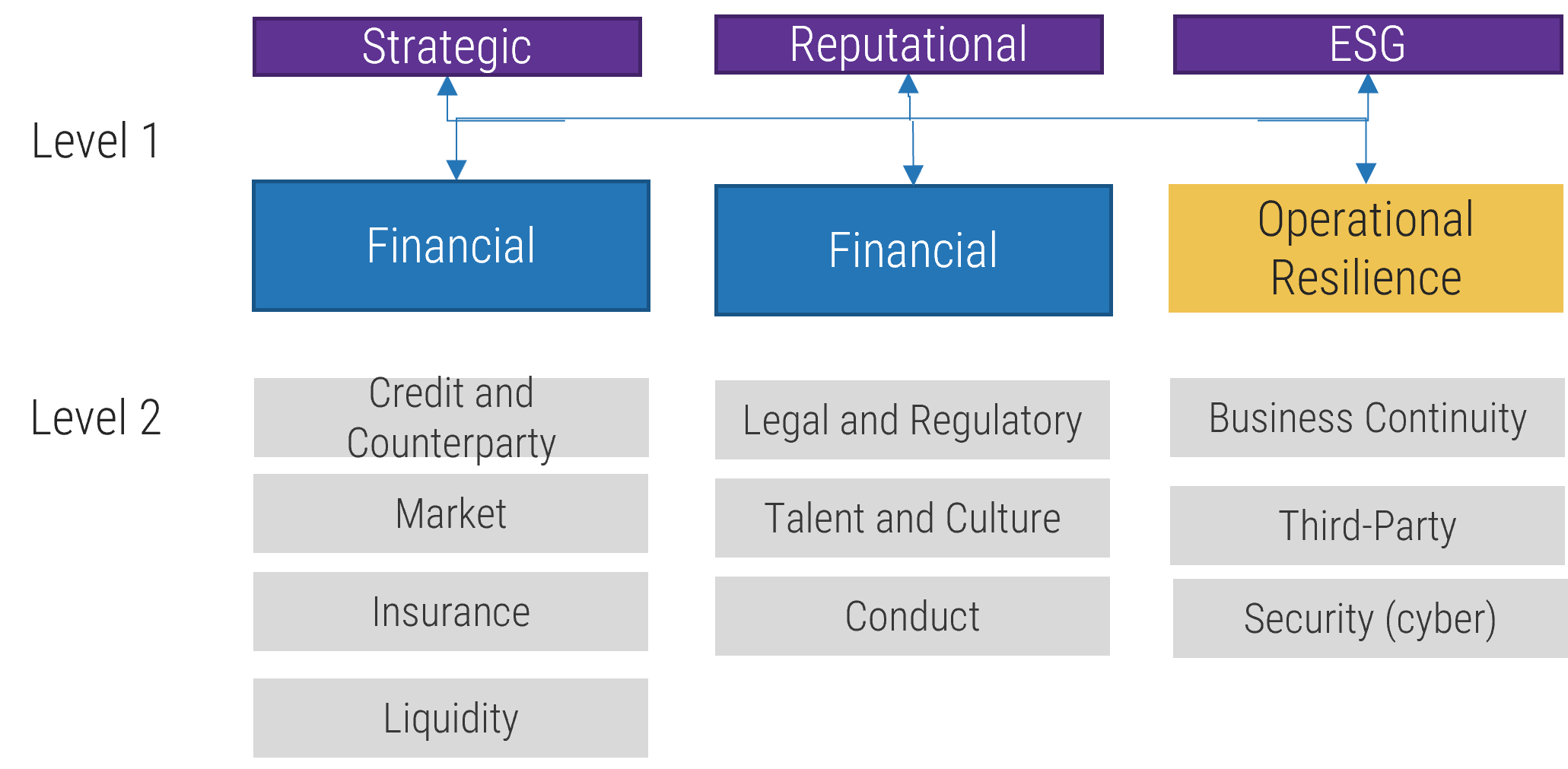
Operational resilience
- The concept of operational resiliency was first introduced by European Central Bank (ECB) in 2018 as an attempt to corral supervisory cooperation on operational resiliency in financial services.
- The necessity for stronger operational resiliency became clear during the early stages of COVID-19 when many organizations were not prepared for disruption, leading to serious concern for the safety and soundness of the financial system.
- It has gained traction and is now defined in global supervisory guidance. Canada’s prudential regulator, Office of the Superintendent of Financial Institutions (OSFI), defines it as “the ability of a financial institution to deliver its operations, including its critical operations, through disruption.”
- Practically, its purpose is to knit together several operational risk management categories such as business continuity, security, and third-party risk.
- The concept has been adopted by information and communication technology (ICT) companies, as technology and cyber risks sit neatly under this risk type.
- It is now not uncommon to see operational resiliency as a level 1 risk type in a financial institution’s ERM framework.
Operational resilience will often feature in ERM frameworks in organizations that deliver critical services, products, or functions, such as financial services
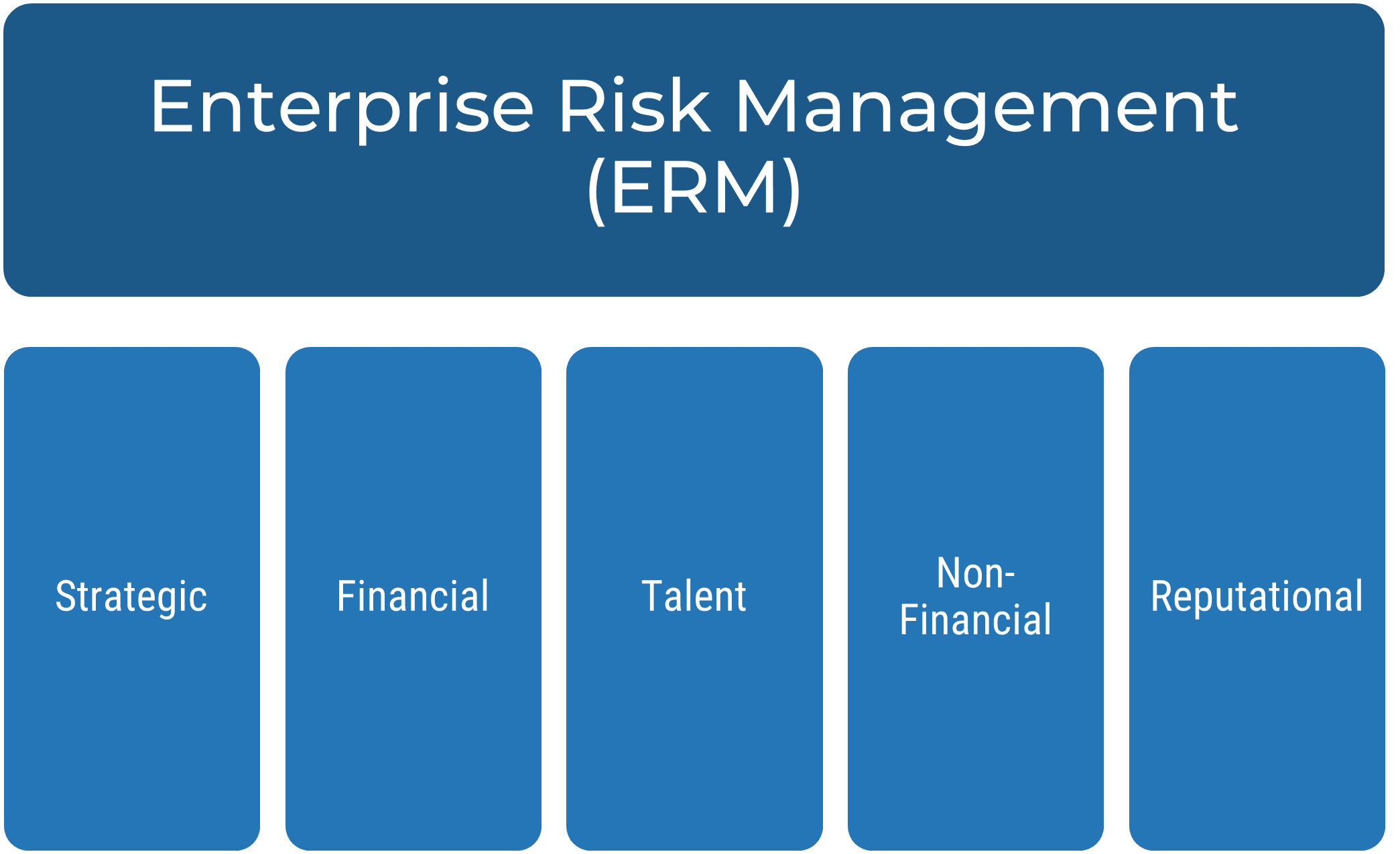
ERM level 1 risk categories
Although many organizations have expanded their enterprise risk management taxonomies to address new threats, most organizations will have the following level 1 risk types:
|
ERM Level 1 |
Definition |
Definition Source |
|---|---|---|
|
Financial |
The ability to obtain sufficient and timely funding capacity. |
Global Association of Risk Professionals (GARP) |
|
Non-Financial |
Non-financial risks are risks that are not considered to be traditional financial risks such as operational risk, technology risk, culture and conduct. |
Office of the Superintendent of Financial Institutions (OSFI) |
|
Reputational |
Potential negative publicity regarding business practices regardless of validity. |
US Federal Reserve Global Association of Risk Professionals (GARP) |
|
Strategic |
Risk of unsuccessful business performance due to internal or external uncertainties, whether the event is event or trend driven. Actions or events that adversely impact an organizations strategies and/or implementation of its strategies. |
The Risk Management Society (RIMS) |
|
Sustainability (ESG) |
This risk of any negative financial or reputational impact on an organizations stemming from current or prospective impacts of ESG factors on its counterparties or invested assets. |
Open Risk Manual Info-Tech Research Group |
|
Talent and Risk Culture |
The widespread behaviors and mindsets that can threaten sound decision-making, prudent risk-taking, and effective risk management and can weaken an institution’s financial and operational resilience. |
Info-Tech Research Group |
Different models of ERM
Some large organizations will elevate certain operational risks to level 1 organizational risks due to risk materiality.
Every organization will approach its risk management taxonomy differently; the number of level 1 risk types will vary and depend highly on perceived impact.
Some of the reasons why an organization would elevate a risk to a level 1 ERM risk are:
- The risk has significant impact on the organization's strategy, reputation, or financial performance.
- The regulator has explicitly called out board oversight within legislation.
- It is best practice in the organization’s industry or business sector.
- The organization has structured its operations around a particular risk theme due to its potential negative impact. For example, the organization may have a dedicated department for data privacy.
|
Level 1 |
Potential Rationale |
Industries |
Risk Definition |
|---|---|---|---|
|
Advanced Analytics |
Use of advanced analytics is considered material |
Large Enterprise, Marketing |
Risks involved with model risk and emerging risks posed by artificial intelligence/machine learning. |
|
Anti-Money Laundering (AML) and Fraud |
Risk is viewed as material |
Financial Services, Gaming, Real Estate |
The risk of exposure to financial crime and fraud. |
|
Conduct Risk |
Sector-specific risk type |
Financial Services |
The current or prospective risk of losses to an institution arising from inappropriate supply of financial services including cases of willful or negligent misconduct. |
|
Operational Resiliency |
Sector-specific risk type |
Financial Services, ICT |
Organizational risk resulting from an organization’s failure to deliver its operations, including its critical operations, through disruption. |
|
Privacy |
Board driven – perceived as material risk to organization |
Healthcare, Financial Services |
The potential loss of control over personal information. |
|
Information Security |
Board driven – regulatory focus |
All may consider |
The people, processes, and technology involved in protecting data (information) in any form – whether digital or on paper – through its creation, storage, transmission, exchange, and destruction. |
Risk and impact
Mapping risks to business outcomes happens within the ERM function and by enterprise fiduciaries.
- When mapping risk events to enterprise risk types, the relationship is rarely linear. Rather, risk events typically will have multiple impacts on the enterprise, including strategic, reputational, ESG, and financial impacts.
- As risk information is transmitted from lower levels, it informs the next level, providing the appropriate information to prioritize risk.
- In the final stage, the enterprise portfolio view will reflect the enterprise impacts according to risk dimensions, such as strategic, operational, reporting, and compliance.
Rolling Up Risks to a Portfolio View
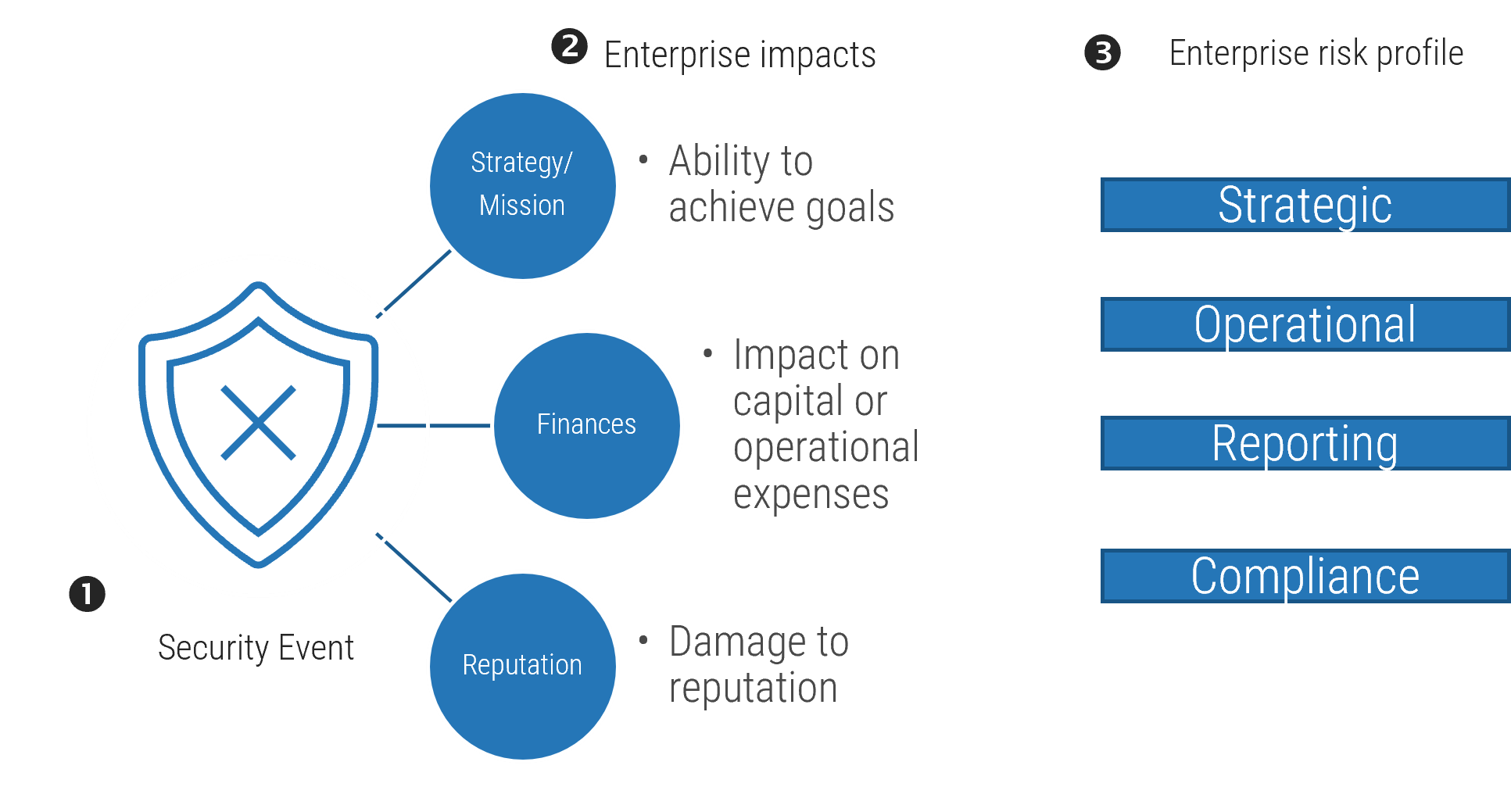
- A risk event within IT will roll up to the enterprise via the IT risk register.
- The impact of the risk on cash flow and operations will be aggregated and allocated in the enterprise risk register by enterprise fiduciaries (e.g. CFO).
- The impacts are translated into full value exposures or modified impact and likelihood assessments.
Common challenges
How to synthesize different objectives between IT risk and enterprise risk
Commingling risk data is a major challenge when developing a risk taxonomy, but one of the underlying reasons is that the enterprise and IT look at risk from different dimensions.
|
↔ |
|
Establish a team
Cross-functional collaboration is key to defining level 1 risk types.
Establish a cross-functional working group.
- Level 1 IT risk types are the most important to get right because they are the root nodes that all subtypes of risk cascade from.
- To ensure the root nodes (level 1 risk types) address the risks of your organization, it is vital to have a strong understanding or your organization’s value chain, so your organizational strategy is a key input for defining your IT level 1 risk types.
- Since the taxonomy provides the method for communicating risks to the people who need to make decisions, a wide understanding and acceptance of the taxonomy is essential. This means that multiple people across your organization should be involved in defining the taxonomy.
- Form a cross-functional tactical team to collaborate and agree on definitions. The team should include subject matter experts and leaders in key risk and business areas. In terms of governance structure, this committee might sit underneath the enterprise risk council, and members of your IT risk council may also be good candidates for this tactical working group.
- The committee would be responsible for defining the taxonomy as well as performing regular reviews.
- The importance of collaboration will become crystal clear as you begin this work, as risks should be connected to only one risk type.
|
Governance Layer |
Role/ Responsibilities |
|---|---|
|
Enterprise Defines organizational goals. Directs or regulates the performance and behavior of the enterprise, ensuring it has the structure and capabilities to achieve its goals. |
Enterprise Risk Council
|
|
Strategic Ensures business and IT initiatives, products, and services are aligned to the organization’s goals and strategy and provide expected value. Ensures adherence to key principles. |
IT Risk Council
|
|
Tactical Ensures key activities and planning are in place to execute strategic initiatives. |
Subcommittee
|
2.1 Establish a cross-functional working group
2-3 hours
- Consider your organization’s operating model and current governance framework, specifically any current risk committees.
- Consider the members of current committees and your objectives and begin defining:
- Committee mandate, goals, and success factors.
- Responsibility and membership.
- Committee procedures and policies.
- Make sure you define how this tactical working group will interact with existing committees.
Download Build an IT Risk Taxonomy Workbook
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Phase 3
Structure Your IT Risk Taxonomy
Phase 1 | Phase 2 | Phase 3 |
|---|---|---|
|
|
|
This phase will walk you through the following activities:
- Establish level 1 risk types
- Test level 1 risk types
- Define level 2 and level 3 risk types
- Test the taxonomy via your control framework
This phase involves the following participants:
- CIO
- CISO
- CRO
- IT Risk Owners
- Business Leaders
- Human Resources
Structuring your IT risk taxonomy
Do’s
- Ensure your organization’s values are embedded into the risk types.
- Design your taxonomy to be forward looking and risk based.
- Make level 1 risk types generic so they can be used across the organization.
- Ensure each risk has its own attributes and belongs to only one risk type.
- Collaborate on and communicate your taxonomy throughout organization.
Don’ts
- Don’t develop risk types based on function.
- Don’t develop your taxonomy in a silo.
A successful risk taxonomy is forward looking and codifies the most frequently used risk language across your organization.
Level 1
Parent risk types aligned to organizational values
Level 2
Subrisks to level 1 risks
Level 3
Further definition
Steps to define your IT risk taxonomy
Step 1
Leverage Info-Tech’s Build an IT Risk Taxonomy Guideline and identify IT level 1 risk types. Consider corporate inputs and macro trends.
Step 2
Test level 1 IT risk types by mapping to your enterprise's ERM level 1 risk types.
Step 3
Draft your level 2 and level 3 risk types. Be mutually exclusive to the extent possible.
Step 4
Work backward – align risk events and controls to the lowest level risk category. In our examples, we align to level 3.
Step 5
Add risk levels to your risk registry.
Step 6
Optional – Add IT risk appetite statements to risk register.
Inputs to use when defining level 1
To help you define your IT risk taxonomy, leverage your organization’s strategy and risk management artifacts, such as outputs from risk assessments, audits, and test results. Also consider macro trends and potential risks unique to your organization.
Step 1 – Define Level 1 Risk Types
Use corporate inputs to help structure your taxonomy
- Corporate Strategy
- Risk Assessment
- Audit
- Test Results
Consider macro trends that may have an impact on how you manage IT risks
- Geopolitical Risk
- Economic Downturn
- Regulation
- Competition
- Climate Risk
- Industry Disruption
Evaluate from an organizational lens
Ask risk-based questions to help define level 1 IT risks for your organization.
IT Risk Type | Example Questions |
|---|---|
Technology | How reliant is our organization on critical assets for business operations? How resilient is the organization to an unexpected crisis? How many planned integrations do we have (over the next 24 months)? |
Talent Risk | What is our need for specialized skills, like digital, AI, etc.? Does our culture support change and innovation? How susceptible is our organization to labor market changes? |
Strategy | What is the extent of digital adoption or use of emerging technologies in our organization? How aligned is IT with strategy/corporate goals? How much is our business dependent on changing customer preferences? |
| Data | How much sensitive data does our organization use? How much data is used and stored aggregately? How often is data moved? And to what locations? |
Third-party | How many third-party suppliers do we have? How reliant are we on the global supply chain? What is the maturity level of our third-party suppliers? Do we have any concentration risk? |
Security | How equipped is our organization to manage cyber threats? How many security incidents occur per year/quarter/day? Do we have regulatory obligations? Is there risk of enforcement action? |
Level 1 IT taxonomy structure
Step 2 – Consider your organization’s strategy and areas where risks may manifest and use this guidance to advance your thinking. Many factors may influence your taxonomy structure, including internal organizational structure, the size of your organization, industry trends and organizational context, etc.
Most IT organizations will include these level 1 risks in their IT risk taxonomy
IT Level 1 | Definition | Definition Source | |
|---|---|---|---|
Technology | Risk arising from the inadequacy, disruption, destruction, failure, damage from unauthorized access modifications, or malicious use of information technology assets, people or processes that enable and support business needs, and can result in financial loss and/or reputational damage. | Open Risk Manual | Note how this definition by OSFI includes cyber risk as part of technology risk. Smaller organizations and organizations that do not use large amounts of sensitive information will typically fold cyber risks under technology risks. Not all organizations will take this approach. Some organizations may elevate security risk to level 1. |
“Technology risk”, which includes “cyber risk”, refers to the risk arising from the inadequacy, disruption, destruction, failure, damage from unauthorized access, modifications, or malicious use of information technology assets, people or processes that enable and support business needs, and can result in financial loss and/or reputational damage. | Office of the Superintendent of Financial Institutions (OSFI) | ||
Talent | The risk of not having the right knowledge and skills to execute strategy. | Info-Tech Research Group/McLean & Company | Human capital challenges including succession challenges and the ability to attract and retain top talent are considered the most dominant risk to organizations’ ability to meet their value proposition (Protiviti, 2023). |
| Strategic | Risks that threaten IT’s ability to deliver expected business outcomes. | Info-Tech Research Group | IT’s role as strategic enabler to the business has never been so vital. With the speed of disruptive innovation, IT must be able to monitor alignment, support opportunities, and manage unexpected crises. |
Level 1 IT taxonomy structure cont'd
Step 2 – Large and more complex organizations may have more level 1 risk types. Variances in approaches are closely linked to the type of industry and business in which the organization operates as well as how they view and position risks within their organization.
IT Level 1 | Definition | Definition Source | |
|---|---|---|---|
Data | Data risk is the exposure to loss of value or reputation caused by issues or limitations to an organization’s ability to acquire, store, transform, move, and use its data assets. | Deloitte | |
Data risk encompasses the risk of loss value or reputation resulting from inadequate or failed internal processes, people and systems or from external events impacting on data. | Australian Prudential Regulation Authority (APRA) CPG 235 -2013) | Data is increasingly being used for strategic growth initiatives as well as for meeting regulatory requirements. Organizations that use a lot of data or specifically sensitive information will likely have data as a level 1 IT risk type. | |
Third-Party | The risk adversely impacting the institutions performance by engaging a third party, or their associated downstream and upstream partners or another group entity (intragroup outsourcing) to provide IT systems or related services. | European Banking Association (EBA) Open Risk Manual uses EBA definition | Third-party risk (supply chain risk) received heightened attention during COVID-19. If your IT organization is heavily reliant on third parties, you may want to consider elevating third-party risk to level 1. |
Security | The risk of unauthorized access to IT systems and data from within or outside the institution (e.g., cyber-attacks). An incident is viewed as a series of events that adversely affects the information assets of an organization. The overall narrative of this type of risk event is captured as who, did what, to what (or whom), with what result. | Open Risk Manual | Some organizations and industries are subject to regulatory obligations, which typically means the board has strict oversight and will elevate security risk to a level 1. |
Common challenges
Considerations when defining level 1 IT risk types
- Ultimately, the identification of a level 1 IT risk type will be driven by the potential for and materiality of vulnerabilities that may impede an organization from delivering successful business outcomes.
- Senior leaders within organizations play a central role in protecting organizations against vulnerabilities and threats.
- The size and structure of your organization will influence how you manage risk.
- The following slide shows typical roles and responsibilities for data privacy.
- Large enterprises and organizations that use a lot of personal identifiable information (PII) data, such as those in healthcare, financial services, and online retail, will typically have data as a level 1 IT risk and data privacy as a level 2 risk type.
- However, smaller organizations or organizations that do not use a lot of data will typically fold data privacy under either technology risk or security risk.
Deciding placement in taxonomy
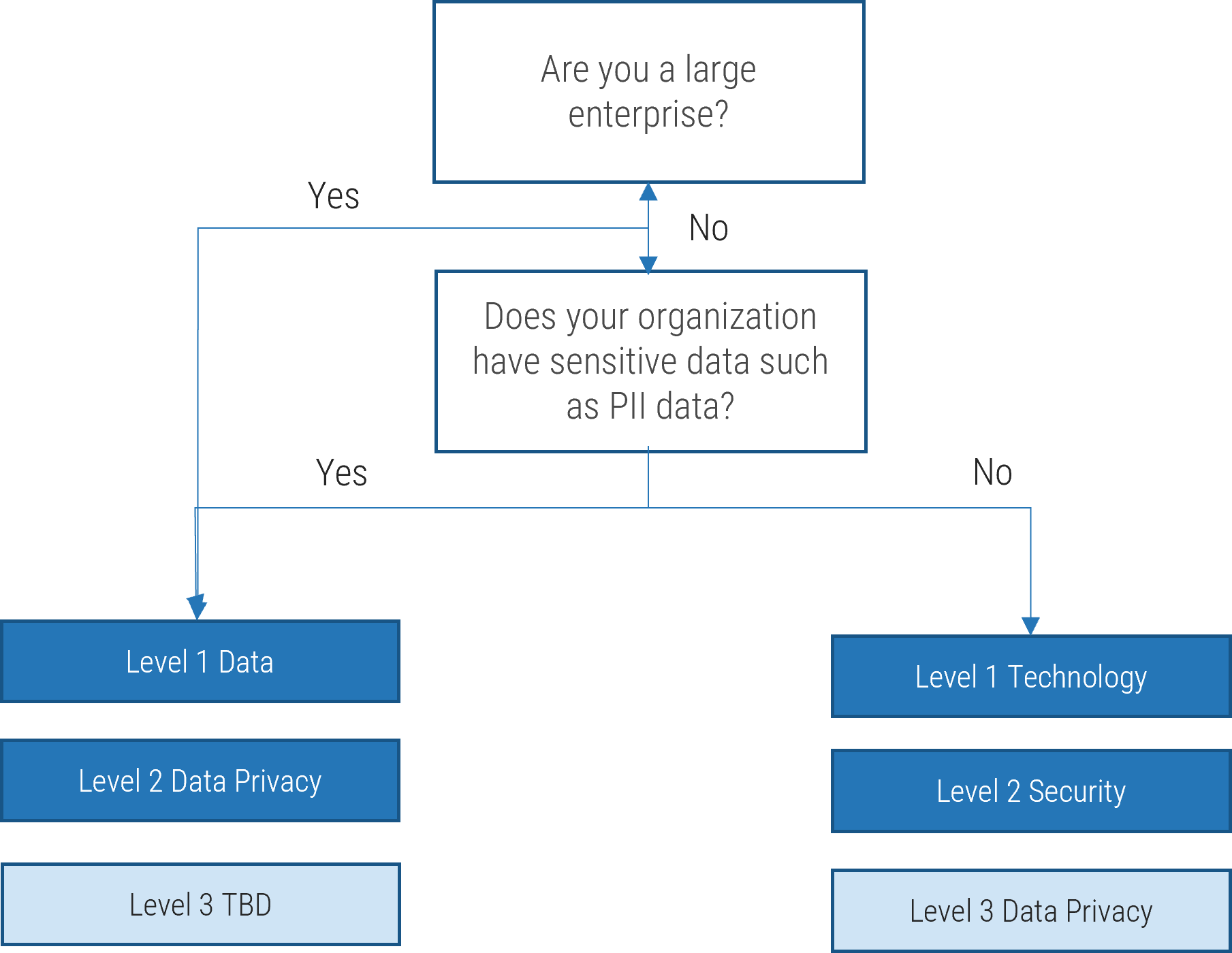
- In larger enterprises, data risks are managed within a dedicated functional department with its own governance structure. In small organizations, the CIO is typically responsible and accountable for managing data privacy risk.
|
Global Enterprise |
Midmarket |
|||
|---|---|---|---|---|
|
Privacy Requirement |
What Is Involved |
Accountable |
Responsible |
Accountable & Responsible |
|
Privacy Legal and Compliance Obligations |
|
Privacy Officer (Legal) |
Privacy Officer (Legal) |
|
|
Privacy Policy, Standards, and Governance |
|
Chief Risk Officer (Risk) |
Head of Risk Function |
|
|
Data Classification and Security Standards and Best-Practice Capabilities |
|
Chief Information Security Officer (IT) |
Chief Information Security Officer (IT) |
|
|
Technical Application of Data Classification, Management and Security Standards |
|
Chief Information Officer (IT) |
Chief Data Architect (IT) |
Chief Information Officer (IT) |
|
Data Management Standards and Best-Practice Capabilities |
|
Chief Data Officer |
Where no Head of Data Exists and IT, not the business, is seen as de facto owner of data and data quality |
|
|
Execution of Data Management |
|
L1 Business Process Owner |
L2 Business Process Owner |
|
Common challenges
Defining security risk and where it resides in the taxonomy
- For risk management to be effective, risk professionals need to speak the same language, but the terms “information security,” “cybersecurity,” and “IT security” are often used interchangeably.
- Traditionally, cyber risk was folded under technology risk and therefore resided at a lower level of a risk taxonomy. However, due to heightened attention from regulators and boards stemming from the pervasiveness of cyber threats, some organizations are elevating security risks to a level 1 IT risk.
- Furthermore, regulatory cybersecurity requirements have emphasized control frameworks. As such, many organizations have adopted NIST because it is comprehensive, regularly updated, and easily tailored.
- While NIST is prescriptive and action oriented, it start with controls and does not easily integrate with traditional ERM frameworks. To address this, NIST has published new guidance focused on an enterprise risk management approach. The guidance helps to bridge the gap between best practices in enterprise risk management and processes and control techniques that cybersecurity professionals use to meet regulatory cybersecurity risk requirements.
Definitional Nuances
“Cybersecurity” describes the technologies, processes, and practices designed to protect networks, computers, programs, and data from attack, damage, or unauthorized access.
“IT security” describes a function as well as a method of implementing policies, procedures, and systems to defend the confidentiality, integrity, and availability of any digital information used, transmitted, or stored throughout the organization’s environment.
“Information security” defines the people, processes, and technology involved in protecting data (information) in any form – whether digital or on paper – through its creation, storage, transmission, exchange, and destruction.
3.1 Establish level 1 risk types
2-3 hours
- Consider your current and future corporate goals and business initiatives, risk management artifacts, and macro industry trends.
- Ask questions to understand risks unique to your organization.
- Review Info-Tech’s IT level 1 risk types and identify the risk types that apply to your organization.
- Add any risk types that are missing and unique to your organization.
- Refine the definitions to suit your organization.
- Be mutually exclusive and collectively exhaustive to the extent possible.
Download Build an IT Risk Taxonomy Workbook
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
3.2 Map IT risk types against ERM level 1 risk types
1-2 hours
- Using the output from Activity 3.1, map your IT risk types to your ERM level 1 risk types.
- Record in the Build an IT Risk Taxonomy Workbook.
Download Build an IT Risk Taxonomy Workbook
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
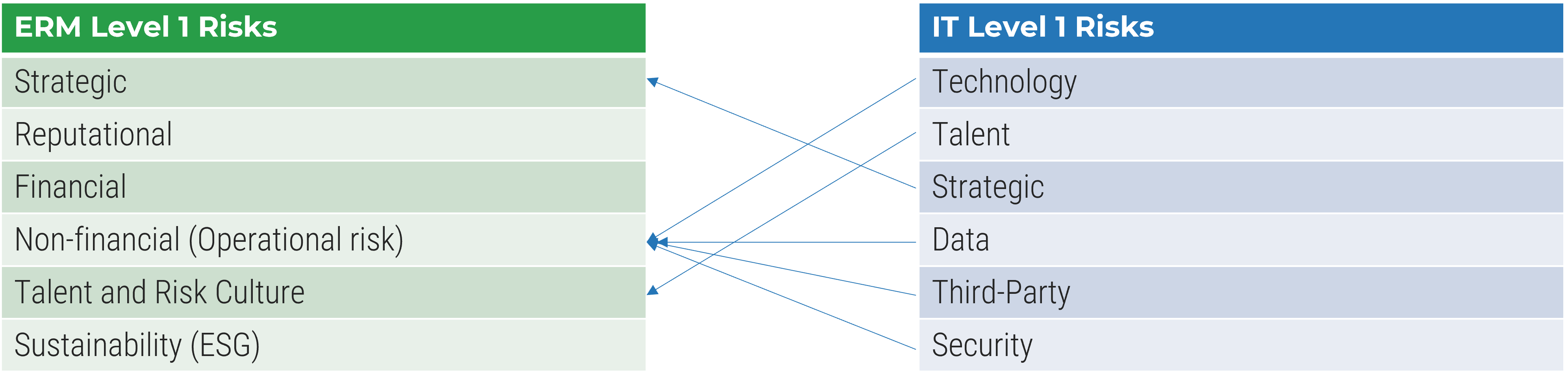
Map IT level 1 risk types to ERM
Test your level 1 IT risk types by mapping to your organization’s level 1 risk types.
Step 2 – Map IT level 1 risk types to ERM
3.3 Establishing level 2 and 3 risk types
3-4 hours
- Using the level 1 IT risk types that you have defined and using Info-Tech’s Risk Taxonomy Guideline, first begin to identify level 2 risk types for each level 1 type.
- Be mutually exclusive and collectively exhaustive to the extent possible.
- Once satisfied with your level 2 risk types, break them down further to level 3 risk types.
Note: Smaller organizations may only define two risk levels, while larger organizations may define further to level 4.
Download Build an IT Risk Taxonomy Design Template
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Level 2 IT taxonomy structure
Step 3 – Break down your level 1 risk types into subcategories. This is complicated and may take many iterations to reach a consistent and accepted approach. Try to make your definitions intuitive and easy to understand so that they will endure the test of time.

Security vulnerabilities often surface through third parties, but where and how you manage this risk is highly dependent on how you structure your taxonomy. Organizations with a lot of exposure may have a dedicated team and may manage and report security risks under a level 1 third-party risk type.
Level 3 IT taxonomy structure
Step 3 – Break down your level 2 risk types into lower-level subcategories. The number of levels of risk you have will depend on the size of and magnitude of risks within your organization. In our examples, we demonstrate three levels.

Risk taxonomies for smaller organizations may only include two risk levels. However, large enterprises or more complex organizations may extend their taxonomy to level 3 or even 4. This illustration shows just a few examples of level 3 risks.
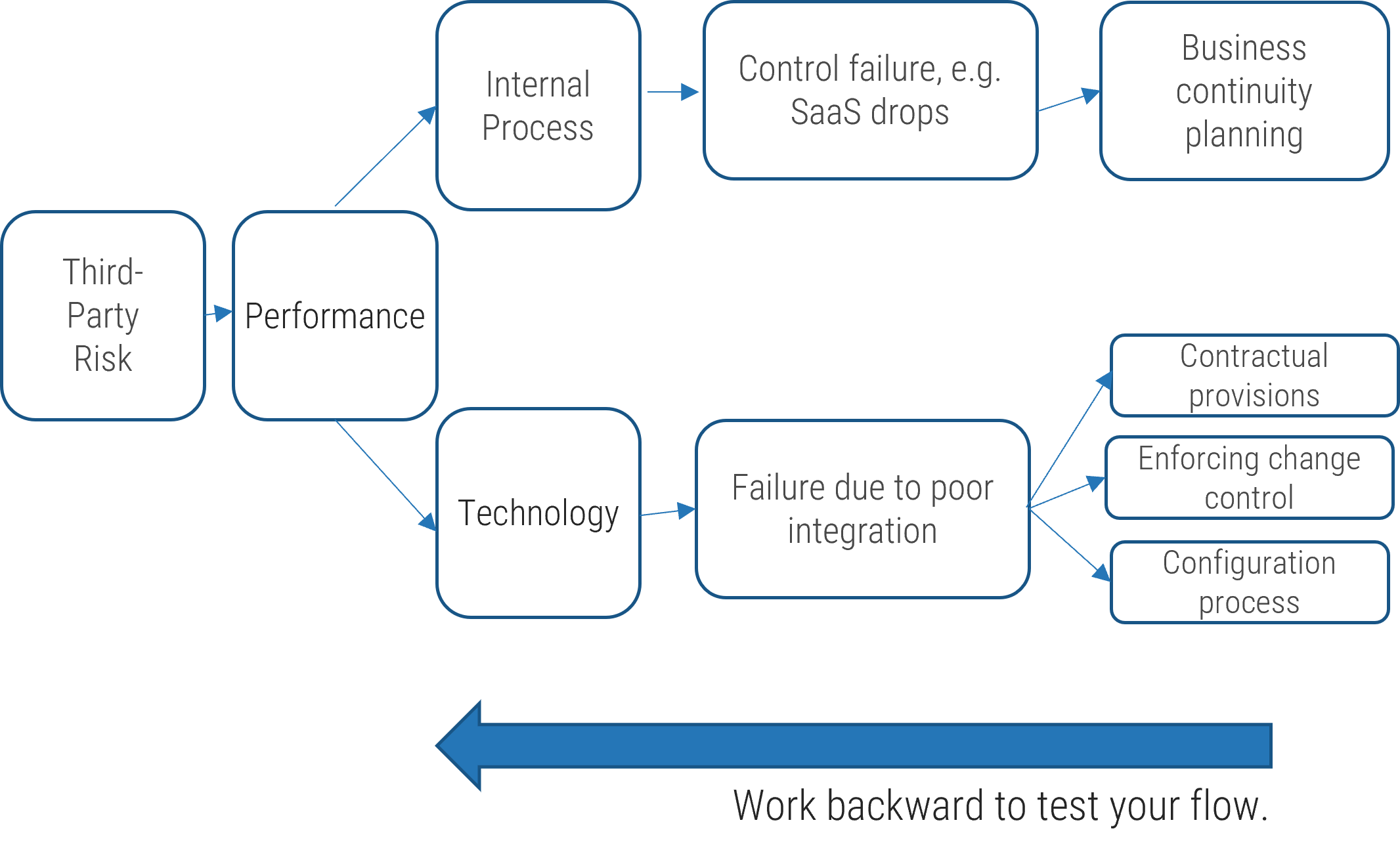
Test using risk events and controls
Ultimately risk events and controls need to roll up to level 1 risks in a consistent manner. Test the robustness of your taxonomy by working backward.
Step 4 – Work backward to test and align risk events and controls to the lowest level risk category.
- A key function of IT risk management is to monitor and maintain internal controls.
- Internal controls help to reduce the level of inherent risk to acceptable levels, known as residual risk.
- As risks evolve, new controls may be needed to upgrade protection for tech infrastructure and strengthen connections between critical assets and third-party suppliers.
Example – Third Party Risk
3.4 Test your IT taxonomy
2-3 hours
- Leveraging the output from Activities 3.1 to 3.3 and your IT Risk Taxonomy Design Template, begin to test the robustness of the taxonomy by working backward from controls to level 1 IT risks.
- The lineage should show clearly that the control will mitigate the impact of a realized risk event. Refine the control or move the control to another level 1 risk type if the control will not sufficiently reduce the impact of a realized risk event.
- Once satisfied, update your risk register or your risk management software tool.
Download Build an IT Risk Taxonomy Design Template
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
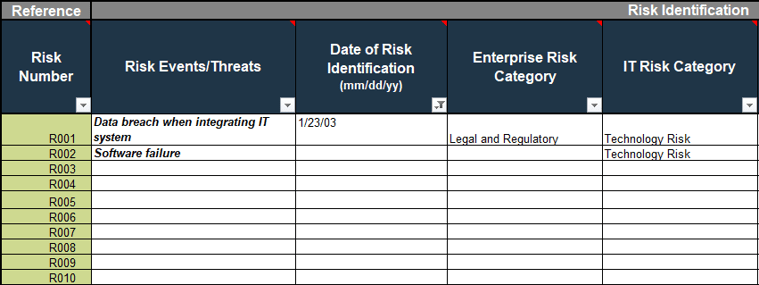
Update risk register
Step 5 – Once you are satisfied with your risk categories, update your risk registry with your IT risk taxonomy.
Use Info-Tech’s Risk Register Tool or populate your internal risk software tool.
Download Info-Tech’s Risk Register Tool
Augment the risk event list using COBIT 2019 processes (Optional)
Other industry-leading frameworks provide alternative ways of conceptualizing the functions and responsibilities of IT and may help you uncover additional risk events.
- Managed IT Management Framework
- Managed Strategy
- Managed Enterprise Architecture
- Managed Innovation
- Managed Portfolio
- Managed Budget and Costs
- Managed Human Resources
- Managed Relationships
- Managed Service Agreements
- Managed Vendors
- Managed Quality
- Managed Risk
- Managed Security
- Managed Data
- Managed Programs
- Managed Requirements Definition
- Managed Solutions Identification and Build
- Managed Availability and Capacity
- Managed Organizational Change Enablement
- Managed IT Changes
- Managed IT Change Acceptance and Transitioning
- Managed Knowledge
- Managed Assets
- Managed Configuration
- Managed Projects
- Managed Operations
- Managed Service Requests and Incidents
- Managed Problems
- Managed Continuity
- Managed Security Services
- Managed Business Process Controls
- Managed Performance and Conformance Monitoring
- Managed System of Internal Control
- Managed Compliance with External Requirements
- Managed Assurance
- Ensured Governance Framework Setting and Maintenance
- Ensured Benefits Delivery
- Ensured Risk Optimization
- Ensured Resource Optimization
- Ensured Stakeholder Engagement
Example IT risk appetite
When developing your risk appetite statements, ensure they are aligned to your organization’s risk appetite and success can be measured.
Example IT Risk Appetite Statement | ||
|---|---|---|
Risk Type | Technology Risk | IT should establish a risk appetite statement for each level 1 IT risk type. |
Appetite Statement | Our organization’s number-one priority is to provide high-quality trusted service to our customers. To meet this objective, critical systems must be highly performant and well protected from potential threats. To meet this objective, the following expectations have been established:
| The ideal risk appetite statement is qualitative and supported by quantitative measures. |
Risk Owner | Chief Information Officer | Ultimately, there is an accountable owner(s), but involve business and technology stakeholders when drafting to gain consensus. |
Risk Oversight | Enterprise Risk Committee | |
Supporting Framework(s) | Business Continuity Management, Information Security, Internal Audit | The number of supporting programs and frameworks will vary with the size of the organization. |
3.5 Draft your IT risk appetite statements
Optional Activity
2-3 hours
- Using your completed taxonomy and your organization’s risk appetite statement, draft an IT risk appetite statement for each level 1 risk in your workbook.
- Socialize the statements and gain approval.
- Add the approved risk appetite statements to your IT risk register.
Download Build an IT Risk Taxonomy Workbook
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Key takeaways and next steps
- The risk taxonomy is the backbone of a robust enterprise risk management program. A good taxonomy is frequently used and well understood.
- Not only is the risk taxonomy used to assess organizational impact, but it is also used for risk reporting, scenarios analysis and horizon scanning, and risk appetite expression.
- It is essential to capture IT risks within the ERM framework to fully understand the impact and allow for consistent risk discussions and meaningful aggregation.
- Defining an IT risk taxonomy is a team sport, and organizations should strive to set up a cross-functional working group that is tasked with defining the taxonomy, monitoring its effectiveness, and ensuring continual improvement.
- The work does not end when the taxonomy is complete. The taxonomy should be well socialized throughout the organization after inception through training and new policies and procedures. Ultimately, it should be an activity embedded into risk management practices.
- The taxonomy is a living document and should be continually improved upon.
3.6 Prepare to communicate the taxonomy internally
1-2 hours
To gain acceptance of your risk taxonomy within your organization, ensure it is well understood and used throughout the organization.
- Consider your audience and agree on the key elements you want to convey.
- Prepare your presentation.
- Test your presentation with a smaller group before communicating to senior leadership or the board.
Coming soon: Look for our upcoming research Communicate Any IT Initiative.
| Input | Output |
|---|---|
|
|
| Materials | Participants |
|
|
Related Info-Tech Research
Build an IT Risk Management Program
- Use this blueprint to transform your ad hoc risk management processes into a formalized ongoing program and increase risk management success.
- Learn how to take a proactive stance against IT threats and vulnerabilities by identifying and assessing IT’s greatest's risks before they occur.
Integrate IT Risk Into Enterprise Risk
- Use this blueprint to understand gaps in your organization’s approach to risk management.
- Learn how to integrate IT risks into the foundational risk practice
Coming Soon: Communicate Any IT initiative
- Use this blueprint to compose an easy-to-understand presentation to convey the rationale of your initiative and plan of action.
- Learn how to identify your target audience and tailor and deliver the message in an authentic and clear manner.
Risk definitions
| Term | Description |
|---|---|
| Emergent Risk | Risks that are poorly understood but expected to grow in significance. |
| Residual Risk | The amount of risk you have left after you have removed a source of risk or implemented a mitigation approach (controls, monitoring, assurance). |
| Risk Acceptance | If the risk is within the enterprise's risk tolerance or if the cost of otherwise mitigating the risk is higher than the potential loss, the enterprise can assume the risk and absorb any losses. |
| Risk Appetite | An organization’s general approach and attitude toward risk; the total exposed amount that an organization wishes to undertake on the basis of risk-return trade-offs for one or more desired and expected outcomes. |
| Risk Assessment | The process of estimating and evaluating risk. |
| Risk Avoidance | The risk response where an organization chooses not to perform a particular action or maintain an existing engagement due to the risk involved. |
| Risk Event | A risk occurrence (actual or potential) or a change of circumstances. Can consist of more than one occurrence or of something not happening. Can be referred to as an incident or accident. |
| Risk Identification | The process of finding, recognizing, describing, and documenting risks that could impact the achievement of objectives. |
| Risk Management | The capability and related activities used by an organization to identify and actively manage risks that affect its ability to achieve goals and strategic objectives. Includes principles, processes, and framework. |
| Risk Likelihood | The chance of a risk occurring. Usually measured mathematically using probability. |
| Risk Management Policy | Expresses an organization’s commitment to risk management and clarifies its use and direction. |
| Risk Mitigation | The risk response where an action is taken to reduce the impact or likelihood of a risk occurring. |
| Risk Profile | A written description of a set of risks. |
Risk definitions
| Term | Description |
|---|---|
| Risk Opportunity | A cause/trigger of a risk with a positive outcome. |
| Risk Owner | The designated party responsible and accountable for ensuring that the risk is maintained in accordance with enterprise requirements. |
| Risk Register | A tool used to identify and document potential and active risks in an organization and to track the actions in place to manage each risk. |
| Risk Response | How you choose to respond to risk (accept, mitigate, transfer, or avoid). |
| Risk Source | The element that, alone or in combination, has potential to give rise to a risk. Usually this is the root cause of the risk. |
| Risk Statement | A description of the current conditions that may lead to the loss, and a description of the loss. |
| Risk Tolerance | The amount of risk you are prepared or able to accept (in terms of volume or impact); the amount of uncertainty an organization is willing to accept in the aggregate (or more narrowly within a certain business unit or for a specific risk category). Expressed in quantitative terms that can be monitored (such as volatility or deviation measures), risk tolerance often is communicated in terms of acceptable/unacceptable outcomes or as limited levels of risk. Risk tolerance statements identify the specific minimum and maximum levels beyond which the organization is unwilling to accept variations from the expected outcome. |
| Risk Transfer | The risk response where you transfer the risk to a third party. |
Research Contributors and Experts
LynnAnn Brewer
Director
McLean & Company
Sandi Conrad
Principal Research Director
Info-Tech Research Group
Valence Howden
Principal Research Director
Info-Tech Research Group
John Kemp
Executive Counsellor – Executive Services
Info-Tech Research Group
Brittany Lutes
Research Director
Info-Tech Research Group
Carlene McCubbin
Practice Lead – CIO Practice
Info-Tech Research Group
Frank Sargent
Senior Workshop Director
Info-Tech Research Group
Frank Sewell
Advisory Director
Info-Tech Research Group
Ida Siahaan
Research Director
Info-Tech Research Group
Steve Willis
Practice Lead – Data Practice
Info-Tech Research Group
Bibliography
Andrea Tang, “Privacy Risk Management”. ISACA Journal, June 2020, Accessed January 2023
Anthony Kruizinga, “Reshaping the risk taxonomy”. PwC, April 2021, Accessed January 2023
Auditboard, "The Essentials of Integrated Risk Management (IRM)", June 2022, Accessed January 2023
Brenda Boultwood, “How to Design an ERM-Friendly Risk Data Architecture”. Global Association of Risk Professionals, February 2020, Accessed January 2023
BSI Standards Publication, "Risk Management Guidelines", ISO 31000, 2018
Dan Swinhoe, "What is Physical Security, How to keep your facilities and devices safe from onsite attackers", August 2021, Accessed January 2023
Eloise Gratton, “Data governance and privacy risk in Canada: A checklist for boards and c-suite”. Borden Ladner Gervais, November 2022 , Accessed January 2023
European Union Agency for Cyber Security Glossary
European Banking Authority, "Guidelines on ICT Risk Assessment under the Supervisory Review and Evaluation process (SREP)", September 2017, Accessed February 2023
European Banking Authority, "Regulatory Framework for Mitigating Key Resilient Risks", Sept 2018, Accessed February 2023
EY, "Seeking stability within volatility: How interdependent risks put CROs at the heart of the banking business", 12th annual EY/IFF global bank risk management survey, 2022, Accessed February 2023
Financial Stability Board, "Cyber Lexicon", November 2018, Accessed February 2023
Financial Stability Board, "Principles for Effective Risk Appetite Framework", November 2013, Accessed January 2023
Forbes Technology Council, "14 Top Data Security Risks Every Business Should Address", January 2020, Accessed January 2023
Frank Martens, Dr. Larry Rittenberg, "COSO, Risk Appetite Critical for Success, Using Risk Appetite to Thrive in a Changing World", May 2020, Accessed January 2023
Gary Stoneurmer, Alice Goguen and Alexis Feringa, "NIST, Risk Management Guide for Information Technology Systems", Special Publication, 800-30, September 2012, Accessed February 2023
Guy Pearce, "Real-World Data Resilience Demands and Integrated Approach to AI, Data Governance and the Cloud", ISACA Journal, May 2022
InfoTech Tech Trends Report, 2023
ISACA, "Getting Started with Risk Scenarios", 2022, Accessed February 2023
James Kaplan, "Creating a technology risk and cyber risk appetite framework," McKinsey & Company, August 2022, Accessed February 2023
Jean-Gregorie Manoukian, Wolters Kluwer, "Risk appetite and risk tolerance: what’s the difference?", Sept 2016, Accessed February 2023
Jennifer Bayuk, “Technology’s Role in Enterprise Risk Management”, ISACA Journal, March 2018, Accessed in February 2023
John Thackeray, "Global Association of Risk Professionals, 7 Key Elements of Effective ERM", January 2020, Accessed January 2023
KPMG, "Regulatory rigor: Managing technology and cyber risk, How FRFI’s can achieve outcomes laid out in OSFI B-13", October 2022, Accessed January 2023
Marc Chiapolino et al, “Risk and resilience priorities, as told by chief risk officers”, McKinsey and Company, December 2022, Accessed January 2023
Mike Rost, Workiva, "5 Steps to Effective Strategic Management", Updated February 2023. Accessed February 2023
NIST, "Risk Management Framework for Information Systems and Organization, The System Life Cycle Approach for Security and Privacy," December 2018, Accessed February 2023
NIST, NISTIR, "Integrating CyberSecurity and Enterprise Risk", October 2020, Accessed February 2023
Oliver Wyman, "The ORX Reference Taxonomy for operational and non-financial risk summary report", 2019, Accessed February 2023.
Office of the Superintendent of Financial Institutions, "Operational Resilience Consultation Results Summary", December 2021, Accessed January 2023
Open Risk Manual, Risk Taxonomy Definitions
Ponemon. "Cost of a Data Breach Report 2021." IBM, July 2021. Web.
Protiviti, "Executive Perspectives on Top Risks, 2023 & 2032, Key Issues being discussed in the boardroom and c-suite", February 2023, Accessed February 2023
RIMS, ISACA, "Bridging the Digital Gap, How Collaboration Between IT and Risk Management can Enhance Value Creation", September 2019, Accessed February 2023
Robert, R. Moeller, "COSO, Enterprise Risk Management, Second Edition, 2011", Accessed February 2023
Robert Putrus, "Effective Reporting to the BoD on Critical Assets, Cyberthreats and Key Controls: The Qualitative and Quantitative Model", ISACA Journal, January 2021, Accessed January 2023
Ron Brash, "Prioritizing Asset Risk Management in ICS Security", August 2020, Accessed February 2023
Ronald Van Loon, "What is Data Culture and How to Implement it?", November 2023, Accessed February 2023
SAS, "From Crisis to Opportunity, Redefining Risk Management", 2021Accessed January 2023
Satori, Cloudian, "Data Protection and Privacy: 12 Ways to Protect User Data", Accessed January 2023
Spector Information Security, "Building your Asset and Risk Register to Manage Technology Risk", November 2021, Accessed January 2023
Talend, "What is data culture", Accessed February 2023
Tom Schneider, "Managing Cyber Security Risk as Enterprise Risk", ISACA Journal, September 2022, Accessed February 2023
Tony Martin –Vegue, "How to Write Strong Risk Scenarios and Statements", ISACA Journal, September 2021, Accessed February 2023
The Wall Street Journal, "Making Data Risk a Top Priority", April 2018, Accessed February 2023
Buying Options
Build an IT Risk Taxonomy
IT Risk Management · IT Leadership & Strategy implementation · Operational Management · Service Delivery · Organizational Management · Process Improvements · ITIL, CORM, Agile · Cost Control · Business Process Analysis · Technology Development · Project Implementation · International Coordination · In & Outsourcing · Customer Care · Multilingual: Dutch, English, French, German, Japanese · Entrepreneur
Tymans Group is a brand by Gert Taeymans BV
Gert Taeymans bv
Europe: Koning Albertstraat 136, 2070 Burcht, Belgium — VAT No: BE0685.974.694 — phone: +32 (0) 468.142.754
USA: 4023 KENNETT PIKE, SUITE 751, GREENVILLE, DE 19807 — Phone: 1-917-473-8669
Copyright 2017-2022 Gert Taeymans BV
