Enterprise Network Design Considerations

Security, risk, and trust models play into how networks are designed and deployed. If these models are not considered during network design, band-aids and workarounds will be deployed to achieve the needed goals, potentially bypassing network controls.
Our Advice
Critical Insight
The cloud “gold rush” has made it attractive for many enterprises to migrate services off the traditional network and into the cloud. These services are now outside of the traditional network and associated controls. This shifts the split of east-west vs. north-south traffic patterns, as well as extending the network to encompass services outside of enterprise IT’s locus of control.
Impact and Result
Where users access enterprise data or services and from which devices dictate the connectivity needed. With the increasing shift of work that the business is completing remotely, not all devices and data paths will be under the control of IT. This shift does not allow IT to abdicate from the responsibility to provide a secure network.
Enterprise Network Design Considerations Research & Tools
Besides the small introduction, subscribers and consulting clients within this management domain have access to:
1. Enterprise Network Design Considerations Deck – A brief deck that outlines key trusts and archetypes when considering enterprise network designs.
This blueprint will help you:
- Enterprise Network Design Considerations Storyboard
2. Enterprise Network Roadmap Technology Assessment Tool – Build an infrastructure assessment in an hour.
Dispense with detailed analysis and customizations to present a quick snapshot of the road ahead.
- Enterprise Network Roadmap Technology Assessment Tool
Further reading
Enterprise Network Design Considerations
It is not just about connectivity.
Executive Summary
Info-Tech Insight
Connectivity and security are tightly coupled
Security, risk, and trust models play into how networks are designed and deployed. If these models are not considered during network design, band-aids and workarounds will be deployed to achieve the needed goals, potentially bypassing network controls.
Many services are no longer within the network
The cloud “gold rush” has made it attractive for many enterprises to migrate services off the traditional network and into the cloud. These services are now outside of the traditional network and associated controls. This shifts the split of east-west vs. north-south traffic patterns, as well as extending the network to encompass services outside of enterprise IT’s locus of control.
Users are demanding an anywhere, any device access model
Where users access enterprise data or services and from which devices dictate the connectivity needed. With the increasing shift of work that the business is completing remotely, not all devices and data paths will be under the control of IT. This shift does not allow IT to abdicate from the responsibility to provide a secure network.
Enterprise networks are changing
The new network reality
The enterprise network of 2020 and beyond is changing:
- Services are becoming more distributed.
- The number of services provided “off network” is growing.
- Users are more often remote.
- Security threats are rapidly escalating.
The above statements are all accurate for enterprise networks, though each potentially to differing levels depending on the business being supported by the network. Depending on how affected the network in question currently is and will be in the near future, there are different common network archetypes that are best able to address these concerns while delivering business value at an appropriate price point.
High-Level Design Considerations
- Understand Business Needs
- Define Your Trust Model
- Align With an Archetype
- Understand Available Tooling
Understand what the business needs are and where users and resources are located.
Trust is a spectrum and tied tightly to security.
How will the network be deployed?
What tools are in the market to help achieve design principles?
Understand business needs
Mission
Never ignore the basics. Start with revisiting the mission and vision of the business to address relevant needs.
Users
Identify where users will be accessing services from. Remote vs. “on net” is a design consideration now more than ever.
Resources
Identify required resources and their locations, on net vs. cloud.
Controls
Identify required controls in order to define control points and solutions.
Define a trust model
Trust is a spectrum
- There is a spectrum of trust, from fully trusted to not trusted at all. Each organization must decide for their network (or each area thereof) the appropriate level of trust to assign.
- The ease of network design and deployment is directly proportional to the trust spectrum.
- When resources and users are outside of direct IT control, the level of appropriate trust should be examined closely.
Implicit
Trust everything within the network. Security is perimeter based and designed to stop external actors from entering the large trusted zone.
Controlled
Multiple zones of trust within the network. Segmentation is a standard practice to separate areas of higher and lower trust.
Zero
Verify trust. The network is set up to recognize and support the principle of least privilege where only required access is supported.
Align with an archetype
Archetypes are a good guide
- Using a defined archetype as a guiding principle in network design can help clarify appropriate tools or network structures.
- Different aspects of a network can have different archetypes where appropriate (e.g. IT vs. OT [operational technology] networks).
Traditional
Services are provided from within the traditional network boundaries and security is provided at the network edge.
Hybrid
Services are provided both externally and from within the traditional network boundaries, and security is primarily at the network edge.
Inverted
Services are provided primarily externally, and security is cloud centric.
Traditional networks
Resources within network boundaries
Moat and castle security perimeter
Abstract
A traditional network is one in which there are clear boundaries defined by a security perimeter. Trust can be applied within the network boundaries as appropriate, and traffic is generally routed through internally deployed control points that may be centralized. Traditional networks commonly include large firewalls and other “big iron” security and control devices.
Network Design Tenets
- The full network path from resource to user is designed, deployed, and controlled by IT.
- Users external to the network must first connect to the network to gain access to resources.
- Security, risk, and trust controls will be implemented by internal enterprise hardware/software devices.
Control
In the traditional network, it is assumed that all required control points can be adequately deployed across hardware/software that is “on prem” and under the control of central IT.
Info-Tech Insight
With increased cloud services provided to end users, this network is now more commonly used in data centers or OT networks.
Traditional networks
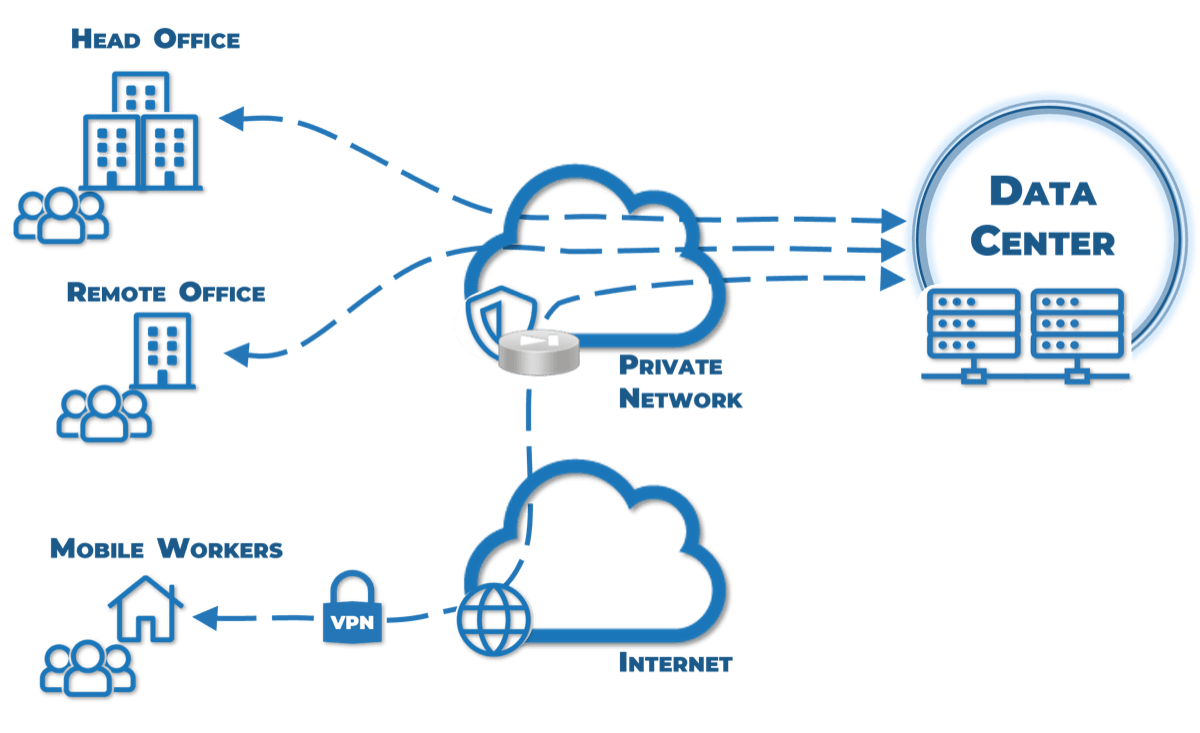
Defining Characteristics
- Traffic flows in a defined path under the control of IT to and from central IT resources.
- Due to visibility into, and the control of, the traffic between the end user and resources, IT can relatively simply implement the required security controls on owned hardware.
Common Components
- Traditional offices
- Remote users/road warriors
- Private data center/colocation space
Hybrid networks
Resources internal and external to network
Network security perimeter combined with cloud protection
Abstract
A hybrid network is one that combines elements of a traditional network with cloud resources. As some of these resources are not fully under the control of IT and may be completely “offnet” or loosely coupled to the on-premises network, the security boundaries and control points are less likely to be centralized. Hybrid networks allow the flexibility and speed of cloud deployment without leaving behind traditional network constructs. This generally makes them expensive to secure and maintain.
Network Design Tenets
- The network path from resource to user may not be in IT’s locus of control.
- Users external to the network must first connect to the network to gain access to internal resources but may directly access publicly hosted ones.
- Security, risk, and trust controls may potentially be implemented by a mixture of internal enterprise hardware/software devices and external control points.
Control
The hallmark of a hybrid network is the blending of public and private resources. This blending tends to necessitate both public and private points of control that may not be homogenous.
Info-Tech Insight
With multiple control points to address, take care in simplifying designs while addressing all concerns to ease operational load.
Hybrid networks
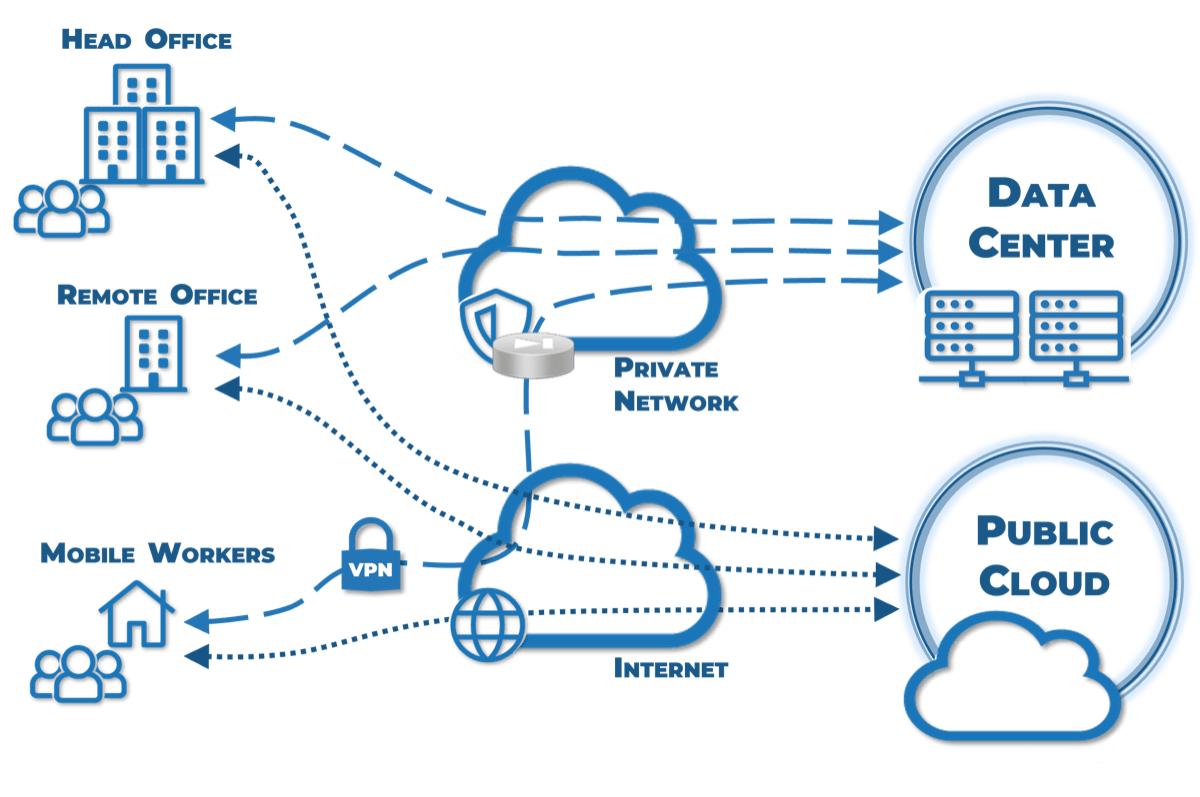
Defining Characteristics
- Traffic flows to central resources across a defined path under the control of IT.
- Traffic to cloud assets may be partially under the control of IT.
- For central resources, the traffic to and from the end user can have the required security controls relatively simply implemented on owned hardware.
- For public cloud assets, IT may or may not have some control over part of the path.
Common Components
- Traditional offices
- Remote users/road warriors
- Private data center/colocation space
- Public cloud assets (IaaS/PaaS/SaaS)
Inverted perimeter
Resources primarily external to the network
Security control points are cloud centric
Abstract
An inverted perimeter network is one in which security and control points cover the entire workflow, on or off net, from the consumer of services through to the services themselves with zero trust. Since the control plane is designed to encompass the workflow in a secure manner, much of the underlying connectivity can be abstracted. In an extreme version of this deployment, IT would abstract end-user access, and any cloud-based or on-premises resources would be securely published through the control plane with context-aware precision access.
Network Design Tenets
- The network path from resource to user is abstracted and controlled by IT through services like secure access service edge (SASE).
- Users only need internet access and appropriate credentials to gain access to resources.
- Security, risk, and trust controls will be implemented through external cloud based services.
Control
An inverted network abstracts the lower-layer connectivity away and focuses on implementing a cloud-based zero trust control plane.
Info-Tech Insight
This model is extremely attractive for organizations that consume primarily cloud services and have a large remote work force.
Inverted networks
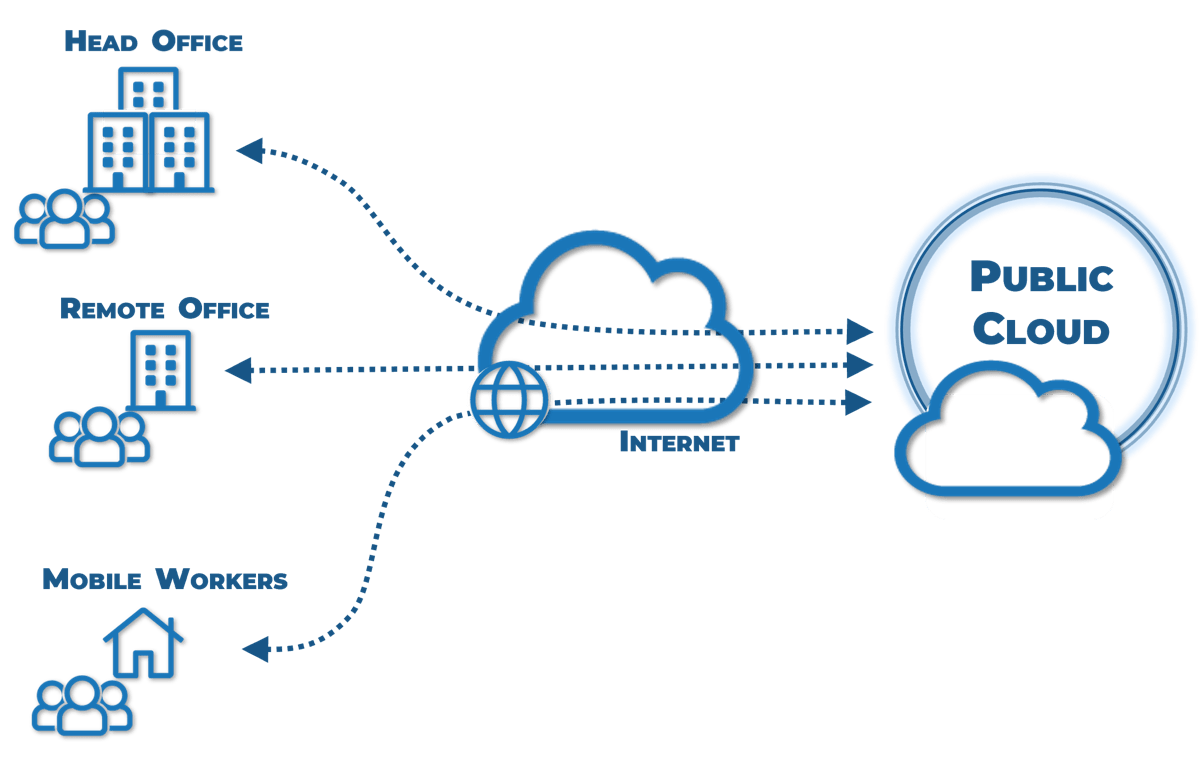
Defining Characteristics
- The end user does not have to be in a defined location.
- All central resources that are to be accessed are hosted on cloud resources.
- IT has little to no control of the path between the end user and central resources.
Common Components
- Traditional offices
- Regent offices/shared workspaces
- Remote users/road warriors
- Public cloud assets (IaaS/PaaS/SaaS)
Understand available tooling
Don’t buy a hammer and go looking for nails
- A network archetype must be defined in order to understand what tools (hardware or software) are appropriate for consideration in a network build or refresh.
- Tools are purpose built and generally designed to solve specific problems if implemented and operated correctly. Choose the tools to align with the challenges that you are solving as opposed to choosing tools and then trying to use those purchases to overcome challenges.
- The purchase of a tool does not allow for abdication of proper design. Tools must be chosen appropriately and integrated properly to orchestrate the best solutions. Purchasing a tool and expecting the tool to solve all your issues rarely succeeds.
“It is essential to have good tools, but it is also essential that the tools should be used in the right way.” — Wallace D. Wattles
Software-defined WAN (SD-WAN)
Simplified branch office connectivity
Archetype Value: Traditional Networks
What It Is Not
SD-WAN is generally not a way to slash spending by lowering WAN circuit costs. Though it is traditionally deployed across lower cost access, to minimize risk and realize the most benefits from the platform many organizations install multiple circuits with greater bandwidths at each endpoint when replacing the more costly traditional circuits. Though this maximizes the value of the technology investment, it will result in the end cost being similar to the traditional cost plus or minus a small percentage.
What It Is
SD-WAN is a subset of software-defined networking (SDN) designed specifically to deploy a secure, centrally managed, connectivity agnostic, overlay network connecting multiple office locations. This technology can be used to replace, work in concert with, or augment more traditional costly connectivity such as MPLS or private point to point (PtP) circuits. In addition to the secure overlay, SD-WAN usually also enables policy-based, intelligent controls, based on traffic and circuit intelligence.
Why Use It
You have multiple endpoint locations connected by expensive lower bandwidth traditional circuits. Your target is to increase visibility and control while controlling costs if and where possible. Ease of centralized management and the ability to more rapidly turn up new locations are attractive.
Cloud access security broker (CASB)
Inline policy enforcement placed between users and cloud services
Archetype Value: Hybrid Networks
What It Is Not
CASBs do not provide network protection; they are designed to provide compliance and enforcement of rules. Though CASBs are designed to give visibility and control into cloud traffic, they have limits to the data that they generally ingest and utilize. A CASB does not gather or report on cloud usage details, licencing information, financial costing, or whether the cloud resource usage is aligned with the deployment purpose.
What It Is
A CASB is designed to establish security controls beyond a company’s environment. It is commonly deployed to augment traditional solutions to extend visibility and control into the cloud. To protect assets in the cloud, CASBs are designed to provide central policy control and apply services primarily in the areas of visibility, data security, threat protection, and compliance.
Why Use It
You a mixture of on-premises and cloud assets. In moving assets out to the cloud, you have lost the traditional controls that were implemented in the data center. You now need to have visibility and apply controls to the usage of these cloud assets.
Secure access service edge (SASE)
Convergence of security and service access in the cloud
Archetype Value: Inverted Networks
What It Is Not
Though the service will consist of many service offerings, SASE is not multiple services strung together. To present the value proposed by this platform, all functionality proposed must be provided by a single platform under a “single pane of glass.” SASE is not a mature and well-established service. The market is still solidifying, and the full-service definition remains somewhat fluid.
What It Is
SASE exists at the intersection of network-as-a-service and network-security-as-a-service. It is a superset of many network and security cloud offerings such as CASB, secure web gateway, SD-WAN, and WAN optimization. Any services offered by a SASE provider will be cloud hosted, presented in a single stack, and controlled through a single pane of glass.
Why Use It
Your network is inverting, and services are provided primarily as cloud assets. In a full realization of this deployment’s value, you would abstract how and where users gain initial network access yet remain in control of the communications and data flow.
Activity
Understand your enterprise network options
Activity: Network assessment in an hour
- Learn about the Enterprise Network Roadmap Technology Assessment Tool
- Complete the Enterprise Network Roadmap Technology Assessment Tool
This activity involves the following participants:
- IT strategic direction decision makers.
- IT managers responsible for network.
- Organizations evaluating platforms for mission critical applications.
Outcomes of this step:
- Completed Enterprise Network Roadmap Technology Assessment Tool
Info-Tech Insight
Review your design options with security and compliance in mind. Infrastructure is no longer a standalone entity and now tightly integrates with software-defined networks and security solutions.
Build an assessment in an hour
Learn about the Enterprise Network Roadmap Technology Assessment Tool.
This workbook provides a high-level analysis of a technology’s readiness for adoption based on your organization’s needs.
- The workbook then places the technology on a graph that measures both the readiness and fit for your organization. In addition, it provides warnings for specific issues and lets you know if you have considerable uncertainty in your answers.
- At a glance you can now communicate what you are doing to help the company:
- Grow
- Save money
- Reduce risk
- Regardless of your specific audience, these are important stories to be able to tell.
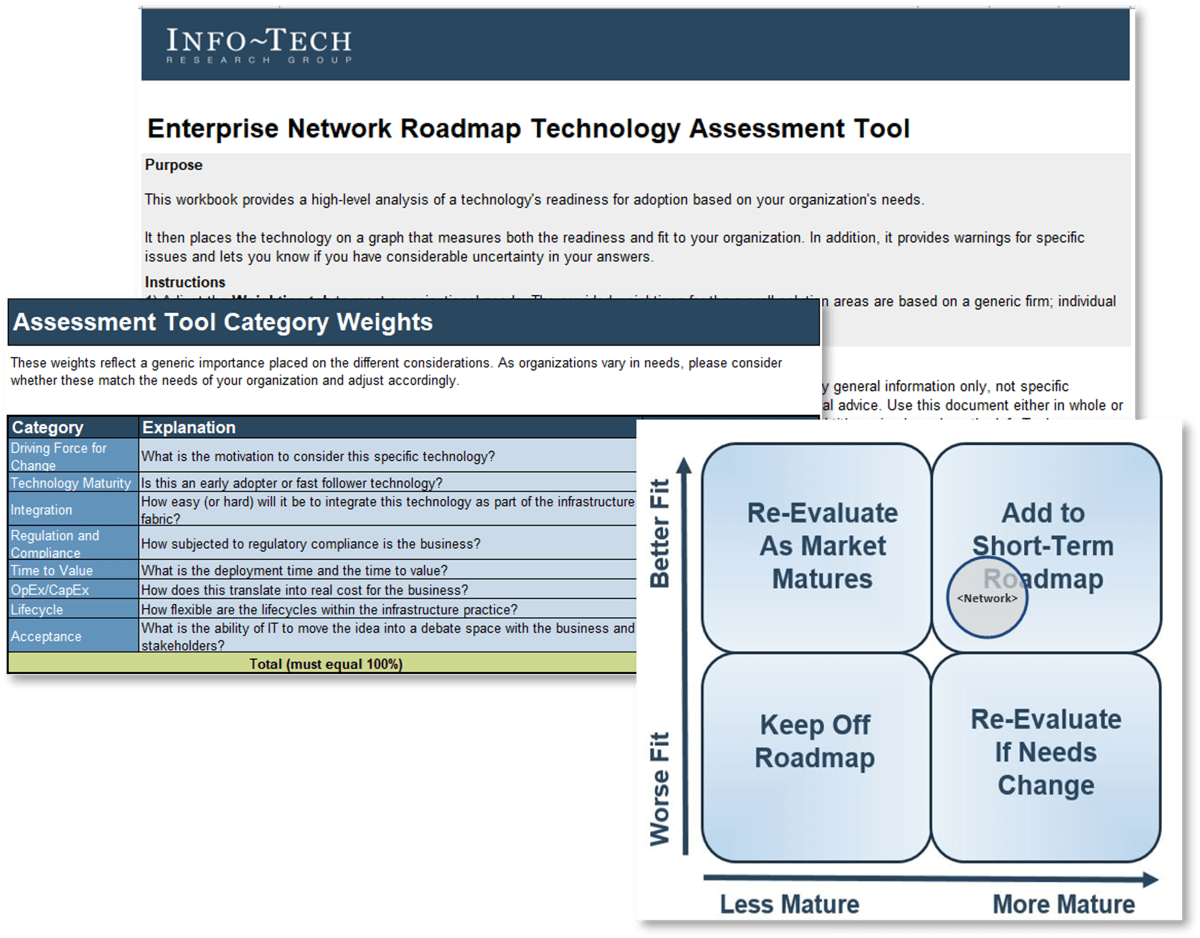
Build an assessment in an hour
Complete the Enterprise Network Roadmap Technology Assessment Tool.
Dispense with detailed analysis and customizations to present a quick snapshot of the road ahead.
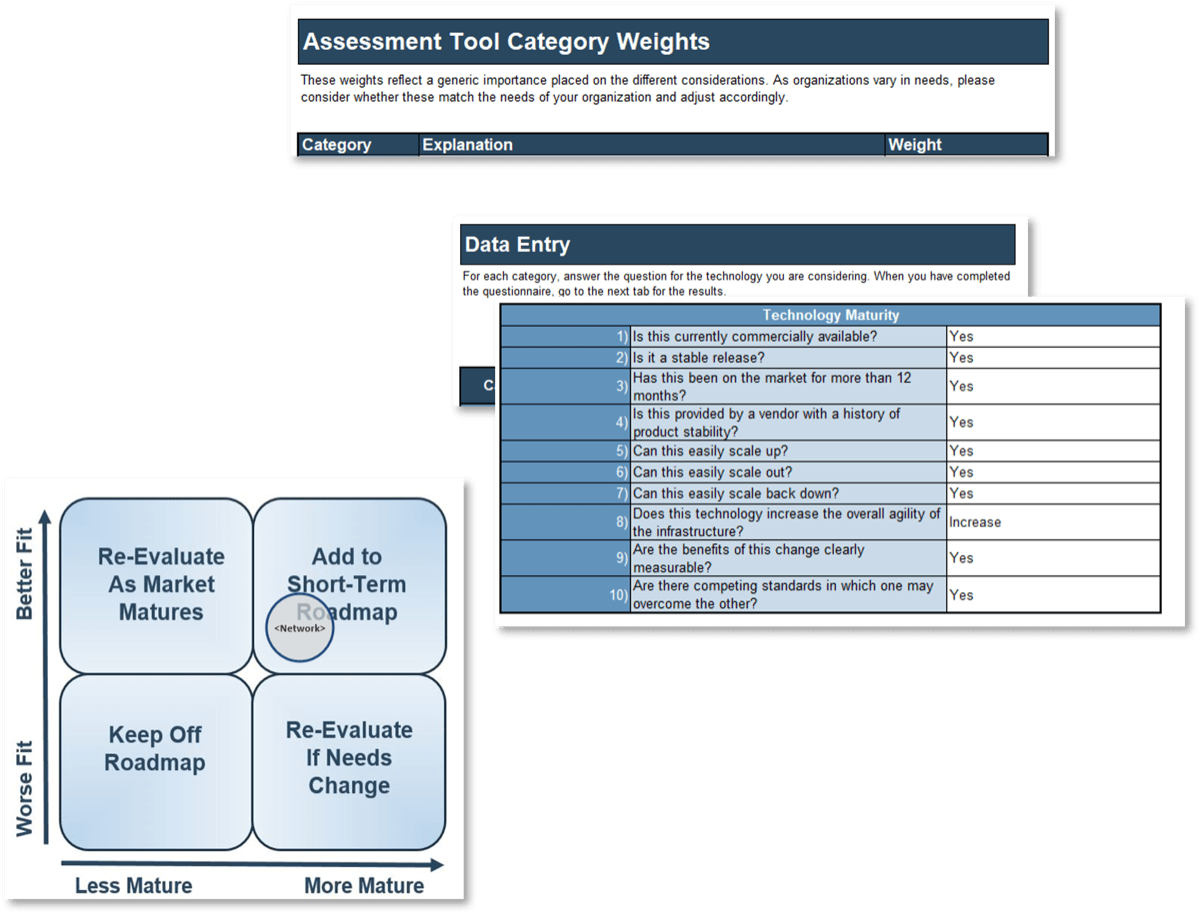
- Weightings: Adjust the Weighting tab to meet organizational needs. The provided weightings for the overall solution areas are based on a generic firm; individual firms will have different needs.
- Data Entry: For each category, answer the questions for the technology you are considering. When you have completed the questionnaire, go to the next tab for the results.
- Results: The Enterprise Network Roadmap Technology Assessment Tool provides a value versus readiness assessment of your chosen technology customized to your organization.
Related Info-Tech Research
Effectively Acquire Infrastructure Services
Acquiring a service is like buying an experience. Don’t confuse the simplicity of buying hardware with buying an experience.
Outsource IT Infrastructure to Improve System Availability, Reliability, and Recovery
There are very few IT infrastructure components you should be housing internally – outsource everything else.
Build Your Infrastructure Roadmap
Move beyond alignment: Put yourself in the driver’s seat for true business value.
Drive Successful Sourcing Outcomes With a Robust RFP Process
Leverage your vendor sourcing process to get better results.
Research Authors

Scott Young, Principal Research Advisor, Info-Tech Research Group
Scott Young is a Director of Infrastructure Research at Info-Tech Research Group. Scott has worked in the technology field for over 17 years, with a strong focus on telecommunications and enterprise infrastructure architecture. He brings extensive practical experience in these areas of specialization, including IP networks, server hardware and OS, storage, and virtualization.

Troy Cheeseman, Practice Lead, Info-Tech Research Group
Troy has over 24 years of experience and has championed large enterprise-wide technology transformation programs, remote/home office collaboration and remote work strategies, BCP, IT DRP, IT operations and expense management programs, international right placement initiatives, and large technology transformation initiatives (M&A). Additionally, he has deep experience working with IT solution providers and technology (cloud) startups.
Bibliography
Ahlgren, Bengt. “Design considerations for a network of information.” ACM Digital Library, 21 Dec. 2008.
Cox Business. “Digital transformation is here. Is your business ready to upgrade your mobile work equation?” BizJournals, 1 April 2022. Accessed April 2022.
Elmore, Ed. “Benefits of integrating security and networking with SASE.” Tech Radar, 1 April 2022. Web.
Greenfield, Dave. “From SD-WAN to SASE: How the WAN Evolution is Progressing.” Cato Networks, 19 May 2020. Web
Korolov, Maria. “What is SASE? A cloud service that marries SD-WAN with security.” Network World, 7 Sept. 2020. Web.
Korzeniowski, Paul, “CASB tools evolve to meet broader set of cloud security needs.” TechTarget, 26 July 2019. Accessed March 2022.
Buying Options
Enterprise Network Design Considerations
IT Risk Management · IT Leadership & Strategy implementation · Operational Management · Service Delivery · Organizational Management · Process Improvements · ITIL, CORM, Agile · Cost Control · Business Process Analysis · Technology Development · Project Implementation · International Coordination · In & Outsourcing · Customer Care · Multilingual: Dutch, English, French, German, Japanese · Entrepreneur
Tymans Group is a brand by Gert Taeymans BV
Gert Taeymans bv
Europe: Koning Albertstraat 136, 2070 Burcht, Belgium — VAT No: BE0685.974.694 — phone: +32 (0) 468.142.754
USA: 4023 KENNETT PIKE, SUITE 751, GREENVILLE, DE 19807 — Phone: 1-917-473-8669
Copyright 2017-2022 Gert Taeymans BV