Implement Software Asset Management

- Organizations are aware of the savings that result from implementing software asset management (SAM), but are unsure of where to start the process.
- Poor data capture procedures and lack of a centralized repository produce an incomplete picture of software assets and licenses, preventing accurate forecasting and license optimization.
- Audit protocols are ad hoc, resulting in sloppy reporting and time-consuming work and lack of preparedness for external software audits.
Our Advice
Critical Insight
- A strong SAM program will benefit all aspects of the business. Data and reports gained through SAM will enable data-driven decision making for all areas of the business.
- Don’t just track licenses; manage them to create value from data. Gathering and monitoring license data is just the beginning. What you do with that data is the real test.
- Win the audit battle without fighting. Conduct internal audits to minimize surprises when external audits are requested.
Impact and Result
- Conduct a current state assessment of existing SAM processes to form an appropriate plan for implementing or improving your SAM program.
- Define standard policies, processes, and procedures for each stage of the software asset lifecycle, from procurement through to retirement.
- Develop an internal audit policy to mitigate the risk of costly external audits.
Implement Software Asset Management Research & Tools
Start here – read the Executive Brief
Read our concise Executive Brief to find out why you should implement software asset management, review Info-Tech’s methodology, and understand the four ways we can support you in completing this project.Besides the small introduction, subscribers and consulting clients within this management domain have access to:
- Implement Software Asset Management – Phases 1-4
1. Assess & plan
Assess current state and plan the scope of the SAM program, team, and budget.
- Implement Software Asset Management – Phase 1: Assess & Plan
- SAM Maturity Assessment
- SAM Standard Operating Procedures
- SAM Budget Workbook
2. Procure, receive & deploy
Define processes for software requests, procurement, receiving, and deployment.
- Implement Software Asset Management – Phase 2: Procure, Receive & Deploy
- SAM Process Workflows (Visio)
- SAM Process Workflows (PDF)
3. Manage, redeploy & retire
Define processes for software inventory, maintenance, harvest and redeployment, and retirement.
- Implement Software Asset Management – Phase 3: Manage, Redeploy & Retire
- Patch Management Policy
4. Build supporting processes
Build processes for audits and plan the implementation.
- Implement Software Asset Management – Phase 4: Build Supporting Processes & Tools
- Software Audit Scoping Email Template
- Software Audit Launch Email Template
- SAM Communication Plan
- SAM FAQ Template
- Software Asset Management Policy
Workshop: Implement Software Asset Management
Workshops offer an easy way to accelerate your project. If you are unable to do the project yourself, and a Guided Implementation isn't enough, we offer low-cost delivery of our project workshops. We take you through every phase of your project and ensure that you have a roadmap in place to complete your project successfully.
1 Assess & Plan
The Purpose
Assess current state and plan the scope of the SAM program, team, and budget.
Key Benefits Achieved
Current state assessment
Defined roles and responsibilities
SAM budget plan
Activities
1.1 Outline SAM challenges and objectives.
1.2 Assess current state.
1.3 Identify roles and responsibilities for SAM team.
1.4 Identify metrics and reports.
1.5 Identify SAM functions to centralize vs. decentralize.
1.6 Plan SAM budget process.
Outputs
Current State Assessment
RACI Chart
Defined metrics and reports
SAM Budget Workbook
2 Procure, Receive & Deploy
The Purpose
Define processes for software requests, procurement, receiving, and deployment.
Key Benefits Achieved
Defined standards for software procurement
Documented processes for software receiving and deployment
Activities
2.1 Determine software standards.
2.2 Define procurement process for new contracts.
2.3 Define process for contract renewals and additional procurement scenarios.
2.4 Design process for receiving software.
2.5 Design deployment workflow.
2.6 Define process for non-standard software requests.
Outputs
Software standards
Standard Operating Procedures
SAM Process Workflows
3 Manage, Redeploy & Retire
The Purpose
Define processes for software inventory, maintenance, harvest and redeployment, and retirement.
Key Benefits Achieved
Defined process for conducting software inventory
Maintenance and patch policy
Documented workflows for software harvest and redeployment as well as retirement
Activities
3.1 Define process for conducting software inventory.
3.2 Define policies for software maintenance and patches.
3.3 Map software license harvest and reallocation process.
3.4 Define policy for retiring software.
Outputs
Standard Operating Procedures
Patch management policy
SAM Process Workflows
4 Build Supporting Processes & Tools
The Purpose
Build processes for audits, identify tool requirements, and plan the implementation.
Key Benefits Achieved
Defined process for internal and external audits
Tool requirements
Communication and implementation plan
Activities
4.1 Define and document the internal audit process.
4.2 Define and document the external audit process.
4.3 Document tool requirements.
4.4 Develop a communication plan.
4.5 Prepare an FAQ list.
4.6 Identify SAM policies.
4.7 Develop a SAM roadmap to plan your implementation.
Outputs
Audit response templates
Tool requirements
Communication plan
End-user FAQ list
Software Asset Management Policy
Implementation roadmap
Further reading
Implement Software Asset Management
Go beyond tracking licenses to proactively managing software throughout its lifecycle.
Table of contents
- Title
- Executive Brief
- Execute the Project/DIY Guide
- Next Steps
- Appendix
Analyst Perspective
“Organizations often conflate software asset management (SAM) with license tracking. SAM is not merely knowing how many licenses you require to be in compliance; it’s asking the deeper budgetary questions to right-size your software spend.
Software audits are a growing concern for businesses, but proactive reporting and decision making supported by quality data will mitigate audit risks. Value is left on the table through underused or poor-quality data, so active data management must be in play. A dedicated ITAM tool can assist with extracting value from your license data.
Achieving an optimized SAM program is a transformative effort, but the people, processes, and technology need to be in place before that can happen.” (Sandi Conrad, Senior Director, Infrastructure & Operations Practice, Info-Tech Research Group)
Software license complexity and audit frequency are increasing: are you prepared to manage the risk?
This Research Is Designed For:
- CIOs that want to improve IT’s reputation with the business.
- CIOs that want to eliminate the threat of a software audit.
- Organizations that want proactive reporting that benefits the entire business.
- IT managers who want visibility into their software usage.
This Research Will Help You:
- Establish a standardized software management process.
- Track and manage software throughout its lifecycle, from procurement through to retirement or redeployment.
- Rationalize your software license estate.
- Improve your negotiations with software vendors.
- Improve the quality of your SAM data gathering and reporting.
Executive summary
Situation
- Organizations are aware of the savings that result from implementing software asset management (SAM), but are unsure of where to start the process. With no formal standards in place for managing licenses, organizations are constantly at risk for costly software audits and poorly executed software spends.
Complication
- Poor data-capture procedures produce an incomplete picture of software lifecycles.
- No centralized repository exists, resulting in fragmented reporting.
- Audit protocols are ad hoc, resulting in sloppy reporting and time-consuming work.
Resolution
- Conduct a current state assessment of existing SAM processes to form an appropriate plan for implementing or improving your SAM program.
- Build and involve a SAM team in the process from the beginning to help embed the change.
- Define standard policies, processes, and procedures for each stage of the software asset lifecycle, from procurement through to retirement. Pace yourself; a staged implementation will make your ITAM program a success.
- Develop an internal audit program to mitigate the risk of costly audits.
- Once a standardized SAM program and data are in place, you will be able to use the data to optimize and rationalize your software licenses.
Info-Tech Insight
A strong SAM program will benefit all aspects of the business.
Data and reports gained through SAM will enable data-driven decision making for all areas of the business.
Don’t just track licenses; manage them to create value from data.
Gathering and monitoring license data is just the beginning. What you do with that data is the real test.
Win the audit battle without fighting.
Conduct internal audits to minimize surprises when external audits are requested.
Build the business case for SAM on cost and risk avoidance
You can estimate the return even without tools or data.
| Benefit | Calculate the return |
|---|---|
| Compliance
How many audits did you have in the past three years? How much time did you spend in audit response? |
Suppose you had two audits each year for the last three years, each with an average $250,000 in settlements.
A team of four with an average salary of $75,000 each took six months to respond each year, allocating 20% of their work time to the audit. You could argue annual audits cost on average $530,000. Increasing ITAM maturity stands to reduce that cost significantly. |
| Efficiency
How much do you spend on software and maintenance by supplier? |
Suppose you spent $1M on software last year. What if you could reduce the spend by just 10% through better practices?
SAM can help reduce the annual spend by simplifying support, renegotiating contracts based on asset data, reducing redundancy, and reducing spend. |
The Business Benefits of SAM
- Compliance: Managing audits and meeting legal, contractual, and regulatory obligations.
- Efficiency: Reducing costs and making the best use of assets while maintaining service.
- Agility: Anticipate requirements using asset data for business intelligence and analytics.
Poor software asset management practices increase costs and risks
Failure to implement SAM can lead to:
High cost of undiscovered IT assets
- Needless procurement of software for new hires can be costly.
Licensing, liability, and legal violations
- Legal actions and penalties that result from ineffective SAM processes and license incompliance can severely impact an organization’s financial performance and corporate brand image.
Compromised security
- Not knowing what assets you have, who is using them and how, can compromise the security of sensitive information.
Increased management costs
- Not having up-to-date software license information impacts decision making, with many management teams failing to respond quickly and efficiently to operational demands.
Increased disruptions
- Vendors seek out organizations who don’t manage their software assets effectively; it is likely that you could be subject to major operational disruptions as a result of an audit.
Poor supplier/vendor relationship
- Most organizations fear communicating with vendors and are anxious about negotiating new licenses.
54% — A study by 1E found that only 54% of organizations believe they can identify all unused software in their organization.
28% — On average, 28% of deployed software is unused, with a wasted cost of $224 per PC on unused software (1E, 2014).
53% — Express Metrix found that 53% of organizations had been audited within the past two years. Of those, 72% had been audited within the last 12 months.
SAM delivers cost savings beyond the procurement stage
SAM delivers cost savings in several ways:
- Improved negotiating position
- Certainty around software needs and licensing terms can put the organization in a better negotiating position for new contracts or contract renewals.
- Improved purchasing position
- Centralized procurement can allow for improved purchasing agreements with better pricing.
- More accurate forecasting and spend
- With accurate data on what software is installed vs. used, more accurate decisions can be made around software purchasing needs and budgeting.
- Prevention of over deployment
- Deploy software only where it is needed based on what end users actively use.
- Software rationalization
- SAM data may reveal multiple applications performing similar functions that can be rationalized into a single standard software that is used across the enterprise.
- License harvesting
- Identify unused licenses that can be harvested and redeployed to other users rather than purchasing new licenses.
SAM delivers many benefits beyond cost savings
Manage risk. If licensing terms are not properly observed, the organization is at risk of legal and financial exposure, including illegal software installation, loss of proof of licenses purchased, or breached terms and conditions.
Control and predict spend. Unexpected problems related to software assets and licenses can significantly impact cash flow.
Less operational interruptions. Poor software asset management processes could lead to failed deployments, software update interruptions, viruses, or a shutdown of unlicensed applications.
Avoid security breaches. If data is not secure through software patches and security, confidential information may be disclosed.
More informed decisions. More accurate data on software assets improves transparency and informs decision making.
Improved contract management. Automated tools can alert you to when contracts are up for renewal to allow time to plan and negotiate, then purchase the right amount of licenses.
Avoid penalties. Conduct internal audits and track compliance to avoid fees or penalties if an external audit occurs.
Reduced IT support. Employees should require less support from the service desk with proper, up to date, licensed software, freeing up time for IT Operations to focus on other work.
Enhanced productivity. By rationalizing and standardizing software offerings, more staff should be using the same software with the same versioning, allowing for better communication and collaboration.
Asset management is especially correlated with the following processes
Being highly effective at asset management means that you are more likely to be highly effective at almost all IT processes, especially:

|
Configuration Management
76% more effective |

|
Service Catalog
74% more effective |

|
Quality Management
63% more effective |

|
Data Quality
62% more effective |

|
Performance Measurement
61% more effective |

|
Organizational Change Management
60% more effective |

|
Portfolio Management
59% more effective |

|
Enterprise Architecture
58% more effective |
Why? Good SAM processes are integral to both service management and configuration management
(Source: Info-Tech Research Group, IT Management and Governance Diagnostic; N=972 organizations) (High asset management effectiveness was defined as those organizations with an effectiveness score of 8 or above.)To accelerate progress, Info-Tech Research Group parses software asset management into its essential processes
Focus on software asset management essentials
Software Procurement:
- Define procurement standards for software and related warranties and support options.
- Develop processes and workflows for purchasing and work out financial implications to inform budgeting later.
Software Deployment and Maintenance:
- Define policies, processes, and workflows for software receiving, deployment, and maintenance practices.
- Develop processes and workflows for managing imaging, harvests and redeployments, service requests, and large-scale rollouts.
Software Harvest and Retirement:
- Manage the employee termination and software harvest cycle.
- Develop processes, policies, and workflows for software security and retirement.
Software Contract and Audit Management:
- Develop processes for data collection and validation to prepare for an audit.
- Define metrics and reporting processes to keep asset management processes on track.
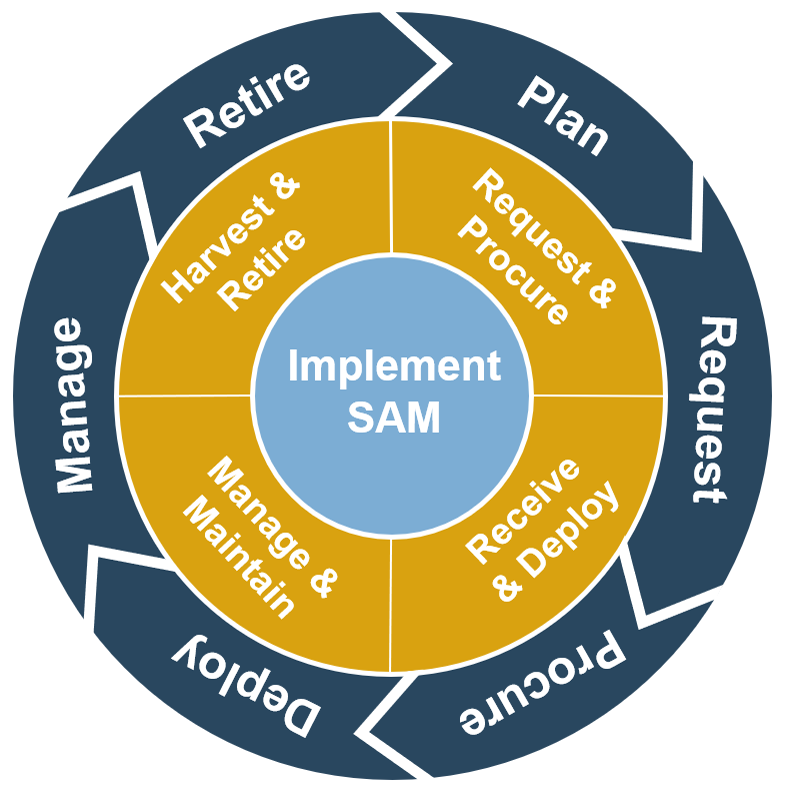
Asset management is a key piece of Info-Tech’s COBIT-based IT Management and Governance Framework
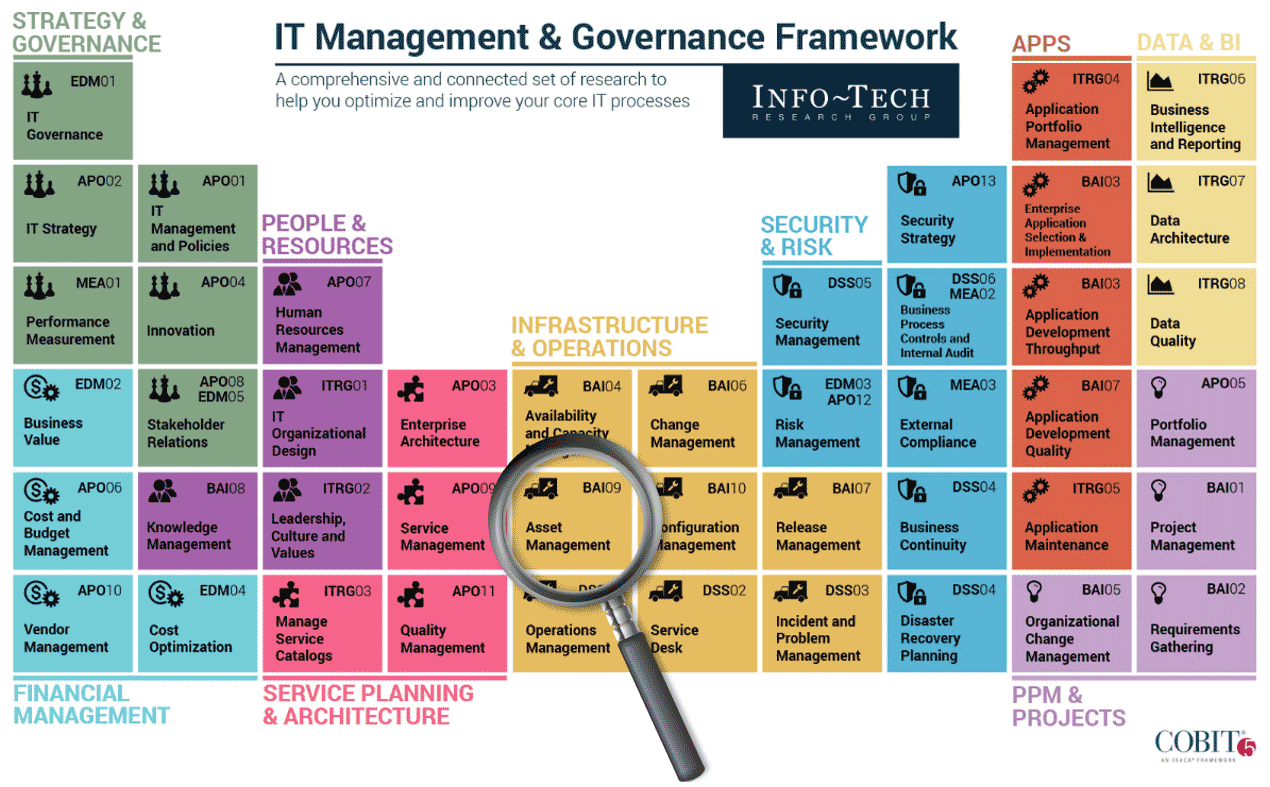
Follow Info-Tech's methodology to build a plan to implement software asset management
| Phase 1 Assess & Plan |
Phase 2 Procure, Receive & Deploy |
Phase 3 Manage, Redeploy & Retire |
Phase 4 Build supporting processes |
||||
1.1 |
Assess current state |
2.1 |
Request & procure |
3.1 |
Manage & maintain contracts |
4.1 |
Compliance & audits |
1.2 |
Build team and define metrics |
2.2 |
Receive & deploy |
3.2 |
Harvest or retire |
4.2 |
Communicate & build roadmap |
1.3 |
Plan & budget | ||||||
| Deliverables | |||||||
| Standard Operating Procedures (SOP) | |||||||
| SAM maturity assessment | Process workflows | Process workflows | Audit response templates | ||||
| RACI chart | Software standards | Patch management policy | Communication plan & FAQ template | ||||
| SAM metrics | SAM policies | ||||||
| SAM budget workbook | |||||||
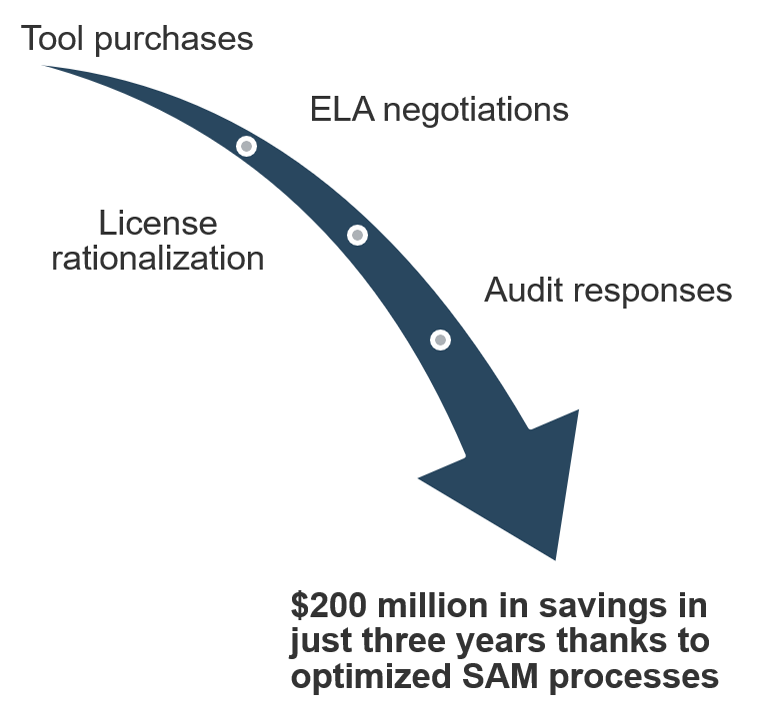
Thanks to SAM, Visa saved $200 million in three years

Case Study
Industry: Financial Services
Source: International Business Software Managers Association
Visa, Inc.
Visa, Inc. is the largest payment processing company in the world, with a network that can handle over 40,000 transactions every minute.
Software Asset Management Program
In 2006, Visa launched a formal IT asset management program, but it was not until 2011 that it initiated a focus on SAM. Joe Birdsong, the SAM director, first addressed four major enterprise license agreements (ELAs) and compliance issues. The SAM team implemented a few dedicated SAM tools in conjunction with an aggressive approach to training.
Results
The proactive approach taken by Visa used a three-pronged strategy: people, process, and tools. The process included ELA negotiations, audit responses, and software license rationalization exercises.
According to Birdsong, “In the past three years, SAM has been credited with saving Visa over $200 million.”
Info-Tech delivers: Use our tools and templates to accelerate your project to completion
 SAM Standard Operating Procedures (SOP) |
 SAM Maturity Assessment |
 SAM Visio Process Workflows |
 SAM Budget Workbook |
 Additional SAM Policy Templates |
 Software Asset Management Policy |
 SAM Communication Plan |
 SAM FAQ Template |
Use these insights to help guide your understanding of the project
- SAM provides value to other processes in IT.
Data, reports, and savings gained through SAM will enable data-driven decision making for all areas of the business. - Don’t just track licenses; manage them to create value from data.
Gathering and monitoring license data is just the beginning. What you do with that data is the real test. - SAM isn’t about managing costs; it’s about understanding your environment to make better decisions.
Capital tied up in software can impact the progress of other projects. - Managing licenses can impact the entire organization.
Gain project buy-in from stakeholders by articulating the impact that managing licenses can have on other projects and the prevalence of shadow IT.
Measure the value of a guided implementation (GI)
Engaging in GIs doesn’t just offer valuable project advice, it also results in significant cost savings.
| GI | Measured Value (Assuming 260 workdays in a year) |
|---|---|
| Phase 1: Assess & Plan |
|
| Phase 2: Procure, Receive & Deploy |
|
| Phase 3: Manage, Redeploy & Retire |
|
| Phase 4: Build Supporting Processes and Tools |
|
| Total savings | $330,325 |
Info-Tech offers various levels of support to best suit your needs
DIY Toolkit |
Guided Implementation |
Workshop |
Consulting |
| "Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful." | "Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track." | "We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place." | "Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project." |
Diagnostics and consistent frameworks used throughout all four options
Implement Software Asset Management – project overview
| Phase 1: Assess & plan | Phase 2: Procure, receive & deploy | Phase 3: Manage, redeploy & retire | Phase 4: Build supporting processes | |
|---|---|---|---|---|
 Best-Practice Toolkit
Best-Practice Toolkit
|
Step 1.1: Assess current state Step 1.2: Build team and define metrics Step 1.3: Plan and budget |
Step 2.1: Request and procure Step 2.2: Receive and deploy |
Step 3.1: Manage and maintain contracts Step 3.2: Harvest, redeploy, or retire |
Step 4.1: Compliance and audits Step 4.2: Communicate and build roadmap |
| Guided Implementations |
|
|
|
|
 Onsite Workshop
Onsite Workshop
|
Module 1:
Assess & Plan |
Module 2:
Map Core Processes: Procure, Receive & Deploy |
Module 3:
Map Core Processes: Manage, Redeploy & Retire |
Module 4:
Prepare for audit, build roadmap and communications |
Workshop Overview
Contact your account representative or email Workshops@InfoTech.com for more information.
| Workshop Day 1 | Workshop Day 2 | Workshop Day 3 | Workshop Day 4 | |
|---|---|---|---|---|
| Activities |
Assess & Plan1.1 Outline SAM challenges and objectives 1.2 Assess current state 1.3 Identify roles and responsibilities for SAM team 1.4 Identify metrics and reports 1.5 Identify SAM functions to centralize vs. decentralize 1.6 Plan SAM budget process |
Map Core Processes: Procure, Receive & Deploy2.1 Determine software standards 2.2 Define procurement process for new contracts 2.3 Define process for contract renewals and additional procurement scenarios 2.4 Design process for receiving software 2.5 Design deployment workflow 2.6 Define process for non-standard software requests |
Map Core Processes: Manage, Redeploy & Retire3.1 Define process for conducting software inventory 3.2 Define policies for software maintenance and patches 3.3 Map software license harvest and reallocation process 3.4 Define policy for retiring software |
Build Supporting Processes4.1 Define and document the internal audit process 4.2 Define and document the external audit process 4.3 Develop a communication plan 4.4 Prepare an FAQ list 4.5 Identify SAM policies 4.6 Develop a SAM roadmap to plan your implementation |
| Deliverables |
|
|
|
|
Use these icons to help direct you as you navigate this research
Use these icons to help guide you through each step of the blueprint and direct you to content related to the recommended activities.

This icon denotes a slide where a supporting Info-Tech tool or template will help you perform the activity or step associated with the slide. Refer to the supporting tool or template to get the best results and proceed to the next step of the project.

This icon denotes a slide with an associated activity. The activity can be performed either as part of your project or with the support of Info-Tech team members, who will come onsite to facilitate a workshop for your organization.
Phase 1: Assess Current State
VISA fought fire with fire to combat costly software audits

Case Study
Industry: Financial Services
Source: SAM Summit 2014
Challenge
Visa implemented an IT asset management program in 2006. After years of software audit teams from large firms visiting and leaving expensive software compliance bills, the world’s leading payment processing company decided it was time for a change.
Upper management recognized that it needed to combat audits. It had the infrastructure in place and the budget to purchase SAM tools that could run discovery and tracking functions, but it was lacking the people and processes necessary for a mature SAM program.
Solution
Visa decided to fight fire with fire. It initially contracted the same third-party audit teams to help build out its SAM processes. Eventually, Visa formed a new SAM team that was led by a group of former auditors.
The former auditors recognized that their role was not technology based, so a group of technical individuals were hired to help roll out various SAM tools.
The team rolled out tools like BDNA Discover and Normalize, Flexera FlexNet Manager, and Microsoft SCCM.
Results
To establish an effective SAM team, diverse talent is key. Visa focused on employees that were consultative but also technical. Their team needed to build relationships with teams within the organization and externally with vendors.
Most importantly, the leaders of the team needed to think like auditors to better prepare for audits. According to Joe Birdsong, SAM Director at Visa, “we want to be viewed as a team that can go in and help right-size their environment and better understand licensing to help teams make better decisions.”
The SAM team was only the beginning.
Step 1.1 Assess current state and plan scope
| Phase 1: Assess & Plan | This step will walk you through the following activities: | This step involves the following participants: | |
1.1 | Assess current state |
|
|
1.2 | Build team and define metrics | ||
1.3 | Plan & budget | ||
Step Outcomes
- An outline of the challenges related to SAM
- A clear direction for the program based on drivers, anticipated benefits, and goals
- A completed maturity assessment of current SAM processes
Sketch out challenges related to software asset management to shape the direction of the project
Common SAM challenges
- Audits are disruptive, time-consuming, and costly
- No audit strategy and response in place
- Software non-compliance risk is too high
- Lacking data to forecast software needs
- No central repository of software licenses
- Untracked or unused software licenses results in wasted spend
- Software license and maintenance costs account for a large percentage of the budget
- Lacking data to know what software is purchased and deployed across the organization
- Lack of software standards make it difficult to collect consistent information about software products
- New software licenses are purchased when existing licenses remain on the shelf or multiple similar software products are purchased
- Employees or departments make ad hoc purchases, resulting in overspending and reduced purchasing power
- License renewal dates come up unexpectedly without time for adequate decision making
- No communication between departments to coordinate software purchasing
- Difficult to stay up to date with software licensing rule changes to remain in compliance
- Processes and policies are unstandardized and undocumented
Outline the organization’s SAM challenges
Participants: CIO/CFO, IT Director, Asset Manager, Purchasing, Service Desk Manager, Security (optional), Operations (optional)
- Distribute sticky notes to participants. Have everyone start by identifying challenges they face as a result of poor software asset management.
- As group, discuss and outline the software asset management challenges facing the organization. These may be challenges caused by poor SAM processes or simply by a lack of process. Group the challenges into key pain points to inform the current state discussion and assessment to follow.
To be effective with software asset management, understand the drivers and potential impact to the organization
| Drivers of effective SAM | Results of effective SAM | |
| Contracts and vendor licensing programs are complex and challenging to administer without data related to assets and their environment. | → | Improved access to accurate data on contracts, licensing, warranties, installed software for new contracts, renewals, and audit requests. |
| Increased need to meet compliance requires a formal approach to tracking and managing assets. | → | Encryption, software application controls, and change notifications all contribute to better asset controls and data security. |
| Cost cutting is on the agenda, and management is looking to reduce overall IT spend in the organization in any possible way. | → | Reduction of software spend through data for better forecasting, planning, and licensing rationalization and harvesting. |
| Audits are time consuming, disruptive to project timelines and productivity, and costly. | → | Respond to audits with a formalized process, accurate data, and minimal disruption using always-available reporting. |
Determine goals to focus the direction of your SAM program
Participants: CIO/CFO, IT Director, Asset Manager, Service Manager (optional)
Document: Document in the Standard Operating Procedures.
- Identify the drivers behind the software asset management implementation or improvement project. List on a whiteboard or flip chart.
- Using the project drivers as input, brainstorm the goals of the SAM project. Discuss the goals as a group and finalize into a list of objectives for the SAM program.
- Record the objectives in the SOP and keep them in mind as you work through the rest of the project.
Sample Objectives:
- A single data repository to efficiently manage assets for their entire lifecycle.
- Formalizing a methodology for documenting assets to make data retrieval easy and accurate.
- Defining and documenting processes to determine where improvements can be made.
- Improving customer experience in accessing, using, and maintaining assets.
- Centralizing contract information.
- Providing access to information for all technical teams as needed.
Implementing SAM processes will support other IT functions
By improving how you manage your licenses and audit requests, you will not only provide benefits through a mature SAM program, you will also improve your service desk and disaster recovery functions.
Each level of SAM maturity comes with its own unique challenges
| Maturity | People & Policies | Processes | Technology |
|---|---|---|---|
| Chaos |
|
|
|
| Reactive |
|
|
|
| Controlled |
|
|
|
| Proactive |
|
|
|
| Optimized |
|
|
|
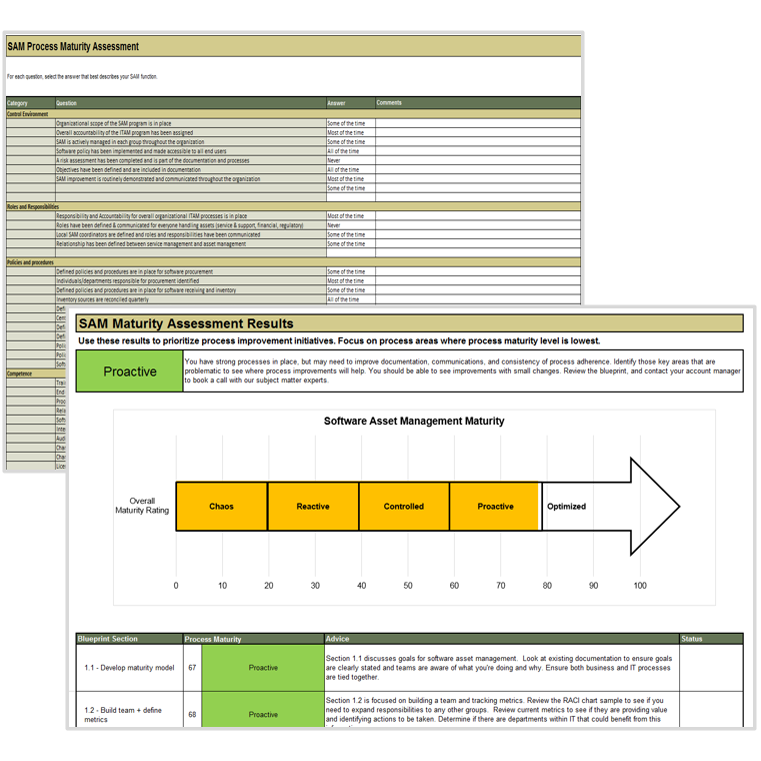
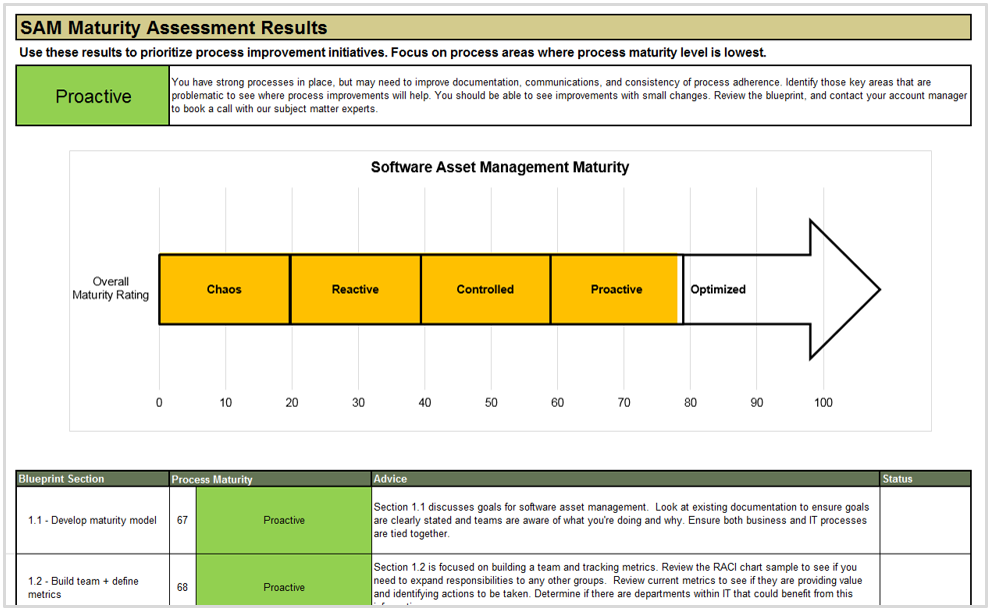
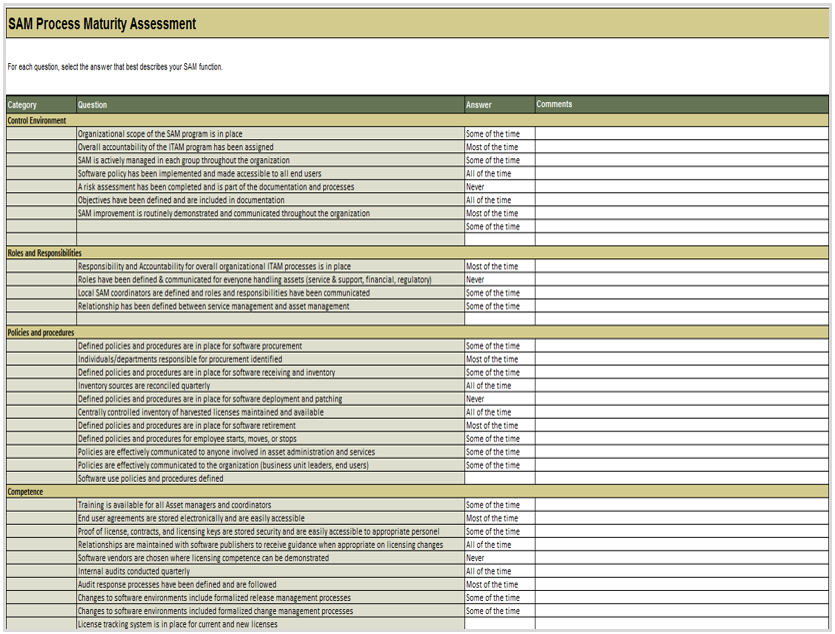
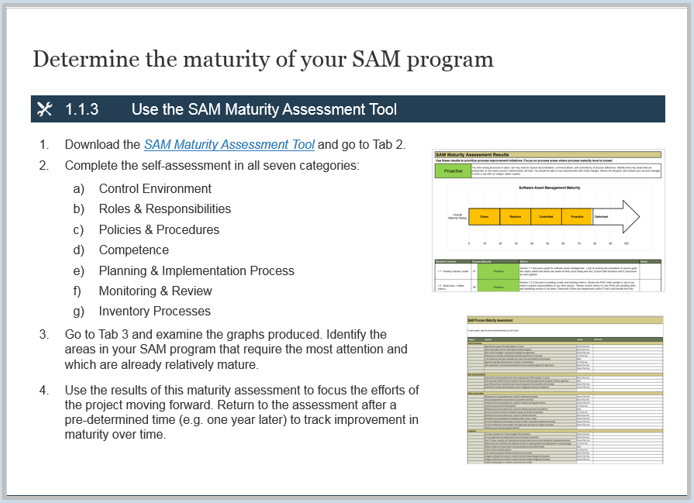
Determine the maturity of your SAM program
- Download the SAM Maturity Assessment Tool and go to tab 2.
- Complete the self-assessment in all seven categories:
- Control Environment
- Roles & Responsibilities
- Policies & Procedures
- Competence
- Planning & Implementation Process
- Monitoring & Review
- Inventory Processes
- Go to tab 3 and examine the graphs produced. Identify the areas in your SAM program that require the most attention and which are already relatively mature.
- Use the results of this maturity assessment to focus the efforts of the project moving forward. Return to the assessment after a pre-determined time (e.g. one year later) to track improvement in maturity over time.
Step 1.2 Build team and define metrics
| Phase 1: Assess & Plan | This step will walk you through the following activities: | This step involves the following participants: | |
1.1 | Assess current state |
|
|
1.2 | Build team and define metrics | ||
1.3 | Plan & budget | ||
Step Outcomes
- A description of the roles and responsibilities of IT staff involved in SAM
- A list of metrics and reports to track to measure the success of the software asset management program
Define roles and responsibilities for the SAM program
Roles and responsibilities should be adapted to fit specific organizational requirements based on its size, structure, and distribution and the scope of the program. Not all roles are necessary and in small organizations, one or two people may fulfill multiple roles.
Senior Management Sponsor – Ensures visibility and support for the program.
IT Asset Manager – Responsible for management of all assets and maintaining asset database.
Software Asset Manager – Responsible for management of all software assets (a subset of the overall responsibility of the IT Asset Manager).
SAM Process Owner – Responsible for overall effectiveness and efficiency of SAM processes.
Asset Analyst – Maintains up-to-date records of all IT assets, including software version control.
Additional roles that interact with SAM:
- Security Manager
- Auditors
- Procurement Manager
- Legal Council
- Change Manager
- Configuration Manager
- Release and Deployment Manager
- Service Desk Manager
Form a software asset management team to drive project success
Many organizations simply do not have a large enough staff to hire a full-time software asset manager. The role will need to be championed by an internal employee.
Avoid filling this position with a temporary contract; one of the most difficult operational factors in SAM implementation and continuity is constant turnover and organizational shifts. Hiring a software asset manager on contract might get the project going faster, but without the knowledge gained by doing the processes, the program won’t have enough momentum to sustain itself.
Software Asset Manager Duties
- Gather proof of license.
- Record and track all assets within the SAM repository.
- Produce compliance reports.
- Preparation of budget requests.
- Administration of software renewal process.
- Contract and support analysis.
- Document procedures.
- Ensure project is on track.
SAM Team Member Duties
- Record license and contract data in SAM tool.
- Assist in production of SAM reports.
- Data analysis.
- Match tickets to SAM data.
- Assist in documentation.
- Assist in compliance reports.
- Gather feedback from end users.
Info-Tech Best Practice
Make sure your SAM team is diverse. The SAM team will need to be skilled at achieving compliance, but there is also a need for technically skilled individuals to maximize the function of the SAM tool(s) at your organization.
Identify roles and responsibilities for SAM
![]() 1.2.1 Complete a RACI chart for your organization
1.2.1 Complete a RACI chart for your organization
Participants: CIO/CFO, IT Director, SAM Manager, SAM Team, Service Desk Manager
Document: Document in the Standard Operating Procedures.
Determine the roles and responsibilities for your SAM program. Record the results in a RACI (responsible, accountable, consulted, informed) chart such as the example below.
| SAM Processes and Tasks | CIO | CFO | SAM Manager | IT Director | Service Management Team | IT Ops | Security | Finance | Legal | Project Manager |
|---|---|---|---|---|---|---|---|---|---|---|
| Policies/Governance | A | C | R | R | I | I | C | I | R | I |
| Strategy | A | C | R | R | I | I | I | I | C | |
| Risk Management/Asset Security | A | C | R | R | C | R | C | C | C | |
| Data Entry/Quality | I | I | A | R | R | |||||
| Compliance Auditing | R | C | A | R | I | I | I | I | ||
| Education & Training | R | I | A | C | I | I | ||||
| Contract Lifecycle Management | R | R | A | R | C | C | C | C | R | C |
| Workflows | R | C | A | R | I | I | I | R | I | C/I |
| Budgeting | R | R | R | A | C | R | ||||
| Software Acquisition | R | I | A | R | I | C | R | C | C | |
| Controls/Reporting | R | I | A | R | I | I | C | I | ||
| Optimize License Harvesting | I | I | A | R | I | C | C |
Identify metrics to form the framework of the project
Trying to achieve goals without metrics is like trying to cook without measuring your ingredients. You might succeed, but you’ll have no idea how to replicate it.
SAM metrics should measure one of five categories:
- Quantity → How many do we have? How many do we want?
- Compliance → What is the level of compliance in a specific area?
- Duration → How long does it take to achieve the desired result?
- Financial → What is the cost/value? What is our comparative spend?
- Quality → How good was the end result? E.g. Completeness, accuracy, timeliness
The metrics you track depend on your maturity level. As your organization shifts in maturity, the metrics you prioritize for tracking will shift to reflect that change. Example:
| Metric category | Low maturity metric | High maturity metric |
|---|---|---|
| Compliance | % of software installed that is unauthorized | % of vendors in effective licensing position (ELP) report |
| Quantity | % of licenses documented in ITAM tool | % of requests made through unauthorized channels |
Associate KPIs and metrics with SAM goals
- Identify the critical success factors (CSFs) for your software asset management program based on strategic goals.
- For each success factor, identify the key performance indicators (KPIs) to measure success, as well as specific metrics that will be tracked and reported on.
- Sample metrics are below:
CSF = Goal, or what success looks like
KPI = How achievement of goal will be defined
Metric = Numerical measure to determine if KPI has been achieved
| CSF/Goal | KPI | Metrics |
|---|---|---|
| Improve accuracy of software budget and forecasting |
|
|
| Avoid over purchasing software licenses and optimize use of existing licenses |
|
|
| Improve accuracy of data |
|
|
| Improved service delivery |
|
|
Identify metrics and KPIs to track the success of your SAM program
![]() 1.2.2 Brainstorm metrics and KPIs
1.2.2 Brainstorm metrics and KPIs
Participants: CIO, IT Director, SAM Manager, SAM Team
Document: Document in the Standard Operating Procedures.
- Discuss the goals and objectives of implementing or improving software asset management, based on challenges identified earlier.
- From the goals, identify the critical success factors for the SAM program.
- For each CSF, identify one to three key performance indicators (KPIs) to evaluate achievement of the success factor.
- For each KPI, identify one to three metrics that can be tracked and reported on to measure success. Ensure that the metrics are tangible and measurable.
Use the table below as an example.
| Goal/CSF | KPI | Metric |
|---|---|---|
| Improve license visibility | Increase accuracy and completeness of SAM data |
|
| Reduce software costs | Reduce number of unused software licenses by 20% |
|
| Reduce shadow IT | Reduce number of unauthorized software purchases and installations by 10% |
|
Tailor metrics and reports to specific stakeholders
Asset Managers
Asset managers require data to manage how licenses are distributed throughout the organization. Are there multiple versions of the same application deployed? What proportion of licenses deployed are assigned to employees who are no longer at the organization? What are the usage patterns for applications?
Service Desk Technicians
Service desk technicians need real-time data on licenses currently available to deploy to machines that need to be imaged/updated, otherwise there is a risk of breaching a vendor agreement.
Business Managers and Executives
Business managers and executives need reports to make strategic decisions. The reports created for business stakeholders need to help them align business projects or business processes with SAM metrics. To determine which reports will provide the most value, start by looking at business goals and determining the tactical data that will help inform and support these goals and their progress.
Additional reporting guidelines:
- Dashboards should provide quick-glance information for daily maintenance.
- Alerts should be set for all contract renewals to provide enough advanced notice (e.g. 90 days).
- Reports should be automated to provide actionable information to appropriate stakeholders as needed.
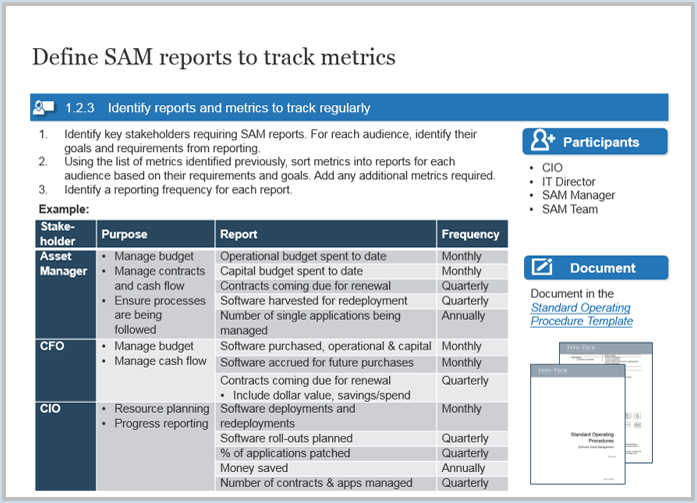
Define SAM reports to track metrics
![]() 1.2.3 Identify reports and metrics to track regularly
1.2.3 Identify reports and metrics to track regularly
Participants: CIO, IT Director, SAM Manager, SAM Team
Document: Document in the Standard Operating Procedures.
- Identify key stakeholders requiring SAM reports. For each audience, identify their goals and requirements from reporting.
- Using the list of metrics identified previously, sort metrics into reports for each audience based on their requirements and goals. Add any additional metrics required.
- Identify a reporting frequency for each report.
Example:
| Stakeholder | Purpose | Report | Frequency |
|---|---|---|---|
| Asset Manager |
|
Operational budget spent to date | Monthly |
| Capital budget spent to date | Monthly | ||
| Contracts coming due for renewal | Quarterly | ||
| Software harvested for redeployment | Quarterly | ||
| Number of single applications being managed | Annually | ||
| CFO |
|
Software purchased, operational & capital | Monthly |
| Software accrued for future purchases | Monthly | ||
Contracts coming due for renewal
|
Quarterly | ||
| CIO |
|
Software deployments and redeployments | Monthly |
| Software rollouts planned | Quarterly | ||
| % of applications patched | Quarterly | ||
| Money saved | Annually | ||
| Number of contracts & apps managed | Quarterly |
Step 1.3 Plan the SAM program and budget
| Phase 1: Assess & Plan | This step will walk you through the following activities: | This step involves the following participants: | |
1.1 | Assess current state |
|
|
1.2 | Build team and define metrics | ||
1.3 | Plan & budget | ||
Step Outcomes
- Defined scope for the SAM program in terms of the degree of centralization of core functions and contracts
- A clearer picture of software spend through the use of a SAM budgeting tool.
Asset managers need to be involved in infrastructure projects at the decision-making stage
Ensure that your software asset manager is at the table when making key IT decisions.
Many infrastructure managers and business managers are unaware of how software licensing can impact projects. For example, changes in core infrastructure configuration can have big impacts from a software licensing perspective.
Mini Case Study
- When a large healthcare organization’s core infrastructure team decided to make changes to their environment, they failed to involve their asset manager in the decision-making process.
- When the healthcare organization decided to make changes to their servers, they were running Oracle software on their servers, but the licenses were not being tracked.
- When the change was being made to the servers, the business contacted Oracle to notify them of the change. What began as a tech services call quickly devolved into a licensing error; the vendor determined that the licenses deployed in the server environment were unauthorized.
- For breaching the licensing agreement, Oracle fined the healthcare organization $250,000.
- Had the asset manager been involved in the process, they would have understood the implications that altering the hardware configuration would have on the licensing agreement and a very expensive mistake could have been avoided.
Decide on the degree of centralization for core SAM functions
- Larger organizations with multiple divisions or business units will need to decide which SAM functions will be centralized and which, if any, will be decentralized as they plan the scope of their SAM program. Generally, certain core functions should be centralized for the SAM program to deliver the greatest benefits.
- The degree of centralization may also be broken down by contract, with some contracts centralized and some decentralized.
- A centralized SAM database gives needed visibility into software assets and licenses across the organization, but operation of the database may also be done locally.
Centralization
- Allows for more strategic planning
- Visibility into software licenses across the organization promotes rationalization and cost savings
- Ensure common products are used
- More strategic sourcing of vendors and resellers
- Centrally negotiate pricing for better deals
- Easier to manage risk and prepare for audits
- Greater coordination of resources
Decentralization
- May allow for more innovation
- May be easier to demonstrate local compliance if the organization is geographically decentralized
- May be easier to procure software if offices are in different countries
- Deployment and installation of software on user devices may be easier
Identify SAM functions to centralize vs. decentralize
![]() 1.3.1 Identify functions for centralization
1.3.1 Identify functions for centralization
Participants: CIO, IT Director, SAM Manager, SAM Team
Document: Document in the Standard Operating Procedures.
- If applicable, identify SAM functions that will need to be centralized and evaluate the implications of centralization to ensure it is feasible.
- If applicable, identify SAM functions that will be decentralized, if resources are available to manage those functions locally.
Example:
Centralized Functions
|
Decentralized functions
|
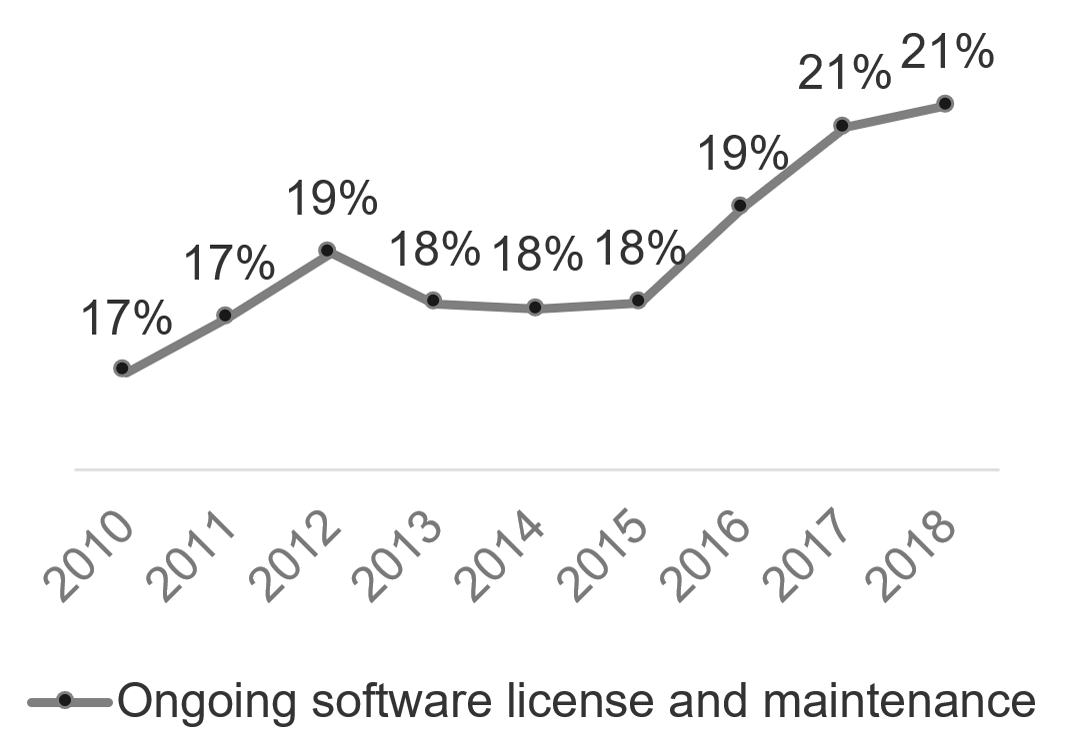
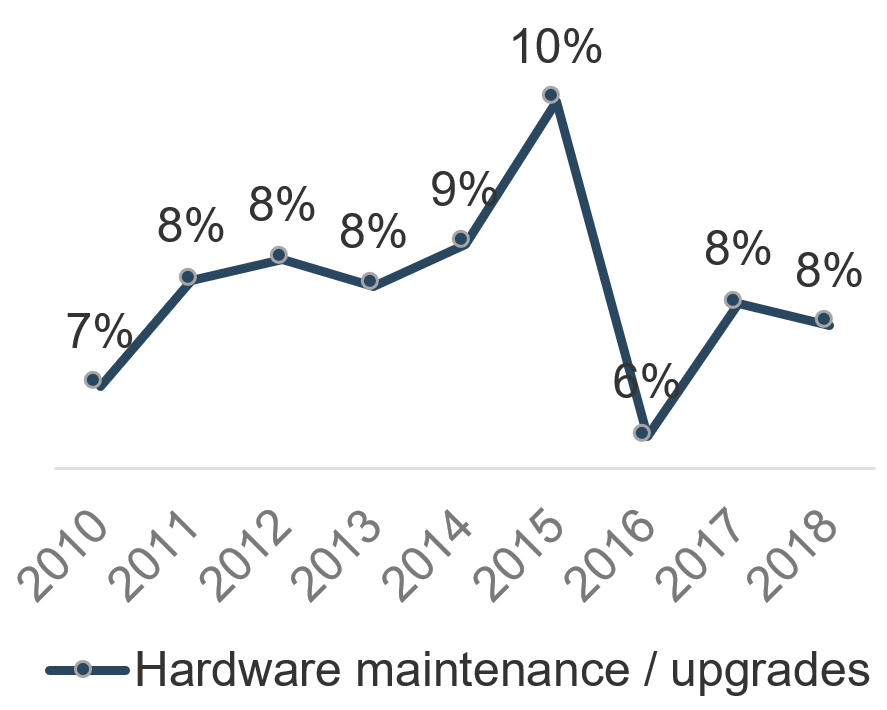
Software comprises the largest part of the infrastructure and operations budget
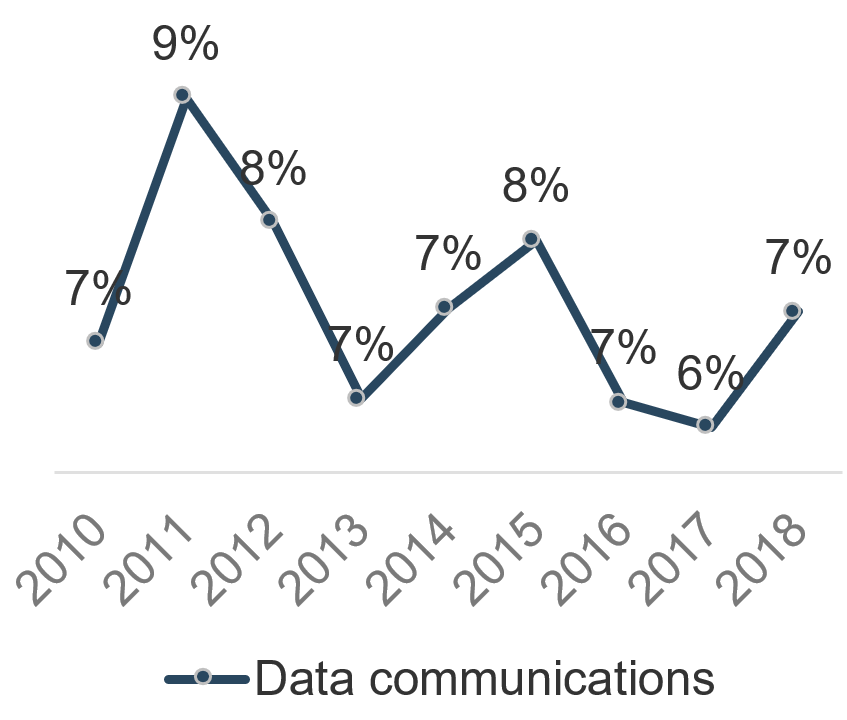
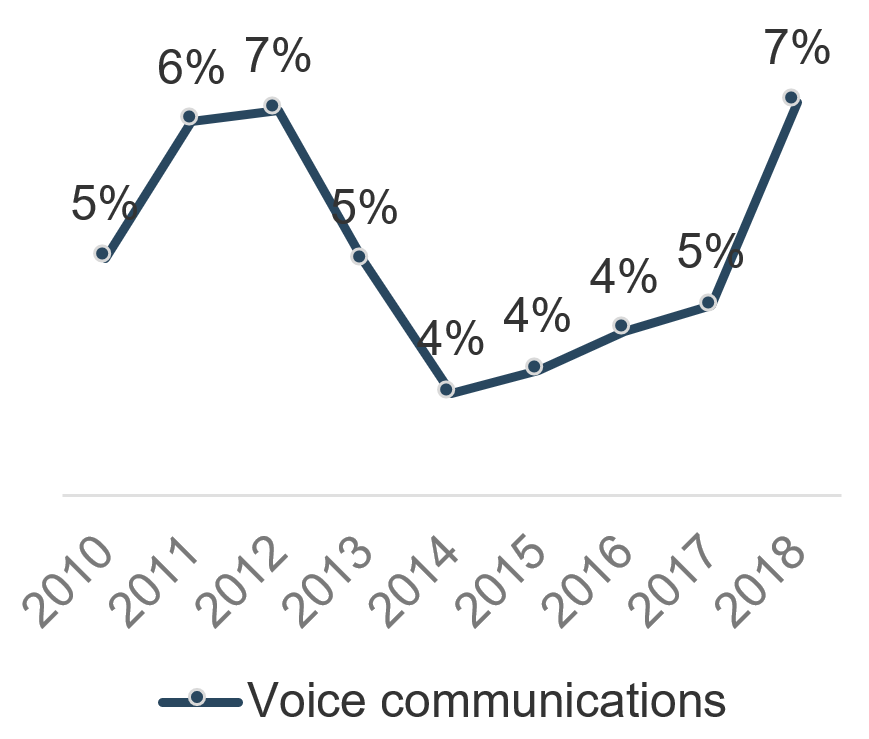
After employee salaries (38%), the four next largest spend buckets have historically been infrastructure related. Adding salaries and external services, the average annual infrastructure and operations spend is over 50% of all IT spend.
The largest portion of that spend is on software license and maintenance. As of 2016, software accounted for the roughly the same budget total as voice communications, data communications, and hardware combined. Managing software contracts is a crucial part of any mature budgeting process.
Gain control of the budget to increase the success of SAM
A sophisticated software asset management program will be able to uncover hidden costs, identify opportunities for rationalization, save money through reharvesting unused licenses, and improve forecasting of software usage to help control IT spending.
While some asset managers may not have experience managing budgets, there are several advantages to the ITAM function owning the budget:
- Be more involved in negotiating pricing with vendors.
- Build better relationships with stakeholders across the business.
- Gain greater purchasing power and have a greater influence on purchasing decisions.
- Forecast software requirements more accurately.
- Inform benchmarks and metrics with more data.
- Directly impact the reduction in IT spend.
- Manage the asset database more easily and have a greater understanding of software needs.
- Identify opportunities for cost savings through rationalization.
Examine your budget from a SAM perspective to optimize software spend
How does examining your budget from a SAM perspective benefit the business?
- It provides a chance to examine vendor contracts as they break down contracts by projects and services, which gives a clearer picture of where software fits into the budget.
- It also gives organizations a chance to review vendor agreements and identify any redundancies present in software supporting services.
Review the budget:
- When reviewing your budget, implement a contingency fund to mitigate risk from a possible breach of compliance.
- If your organization incurs compliance issues that relate to specific services, these fines may be relayed back to the departments that own those services, affecting how much money each department has.
- The more sure you are of your compliance position, the less likely you are to need a contingency fund, and vice versa.
Info-Tech Best Practice
Finance needs to be involved. Their questions may cover:
- Where are the monthly expenditures? Where are our financial obligations? Do we have different spending amounts based on what time of year it is?
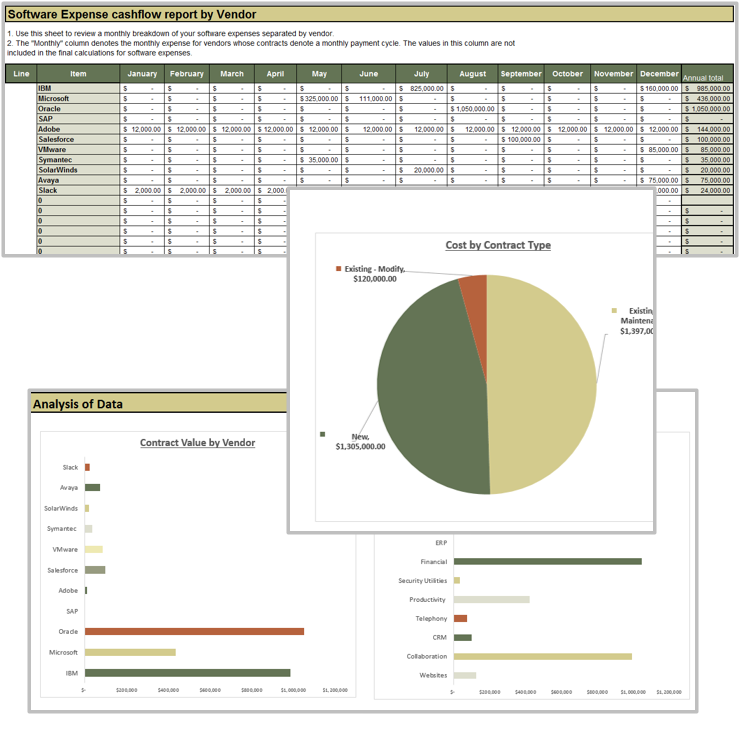
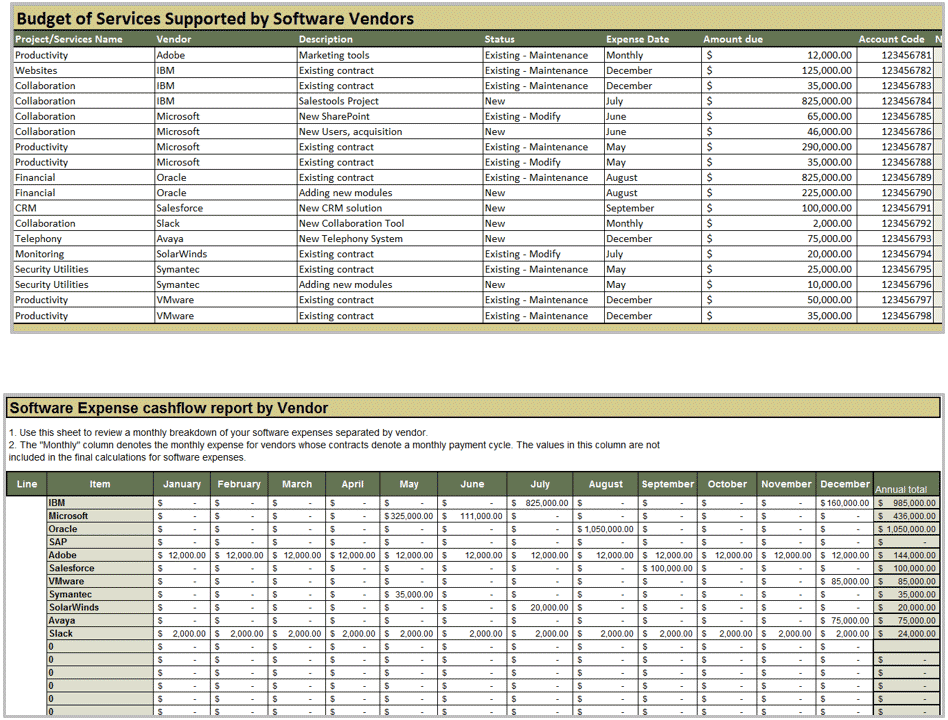
Use the SAM Budget Workbook to uncover insights about your software spend
The SAM Budget Workbook is designed to assist in developing and justifying the budget for software assets for the upcoming year.
Instructions
- Work through tabs 2-6, following the instructions as you go.
- Tab 2 involves selecting software vendors and services provided by software.
- Tab 3 involves classifying services by vendor and assigning a cost to them. Tab 3 also allows you to classify the contract status.
- Tab 4 is a cost variance tracking sheet for software contracts.
- Tabs 5 and 6 are monthly budget sheets that break down software costs by vendor and service, respectively.
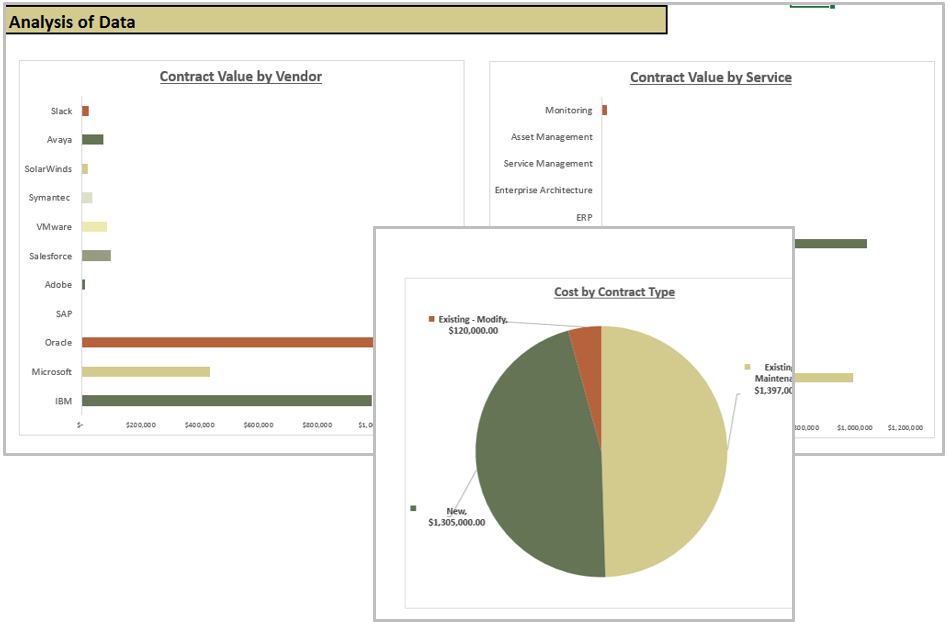
- Tab 7 provides graphs to analyze the data generated by the tool.
- Use the results found on tab 7 to analyze your budget: are you spending too much with one service? Is there vendor overlap based on what project or service that software is reporting?
If you want additional support, have our analysts guide you through this phase as part of an Info-Tech Workshop 
Book a workshop with our Info-Tech analysts:

|
|
The following are sample activities that will be conducted by Info-Tech analysts with your team:
1.1.3 |
|
Determine the maturity of your SAM program
Using the SAM Maturity Assessment Tool, fill out a series of questions in a survey to assess the maturity of your current SAM program. The survey assesses seven categories that will allow you to align your strategy to your results. |
1.2.3 |
|
Define SAM reports to track metrics
Identify key stakeholders with reporting needs, metrics to track to fulfill reporting requirements, and a frequency for producing reports. |
Phase 1 outline
Complete these steps on your own, or call us to complete a guided implementation. A guided implementation is a series of 2-3 advisory calls that help you execute each phase of a project. They are included in most advisory memberships.
Guided Implementation 1: Assess and Plan
Proposed Time to Completion (in weeks): 4
| Step 1.1: Assess current state | Step 1.2: Build team and define metrics | Step 1.3: Plan and budget |
Start with an analyst kick-off call:
|
Review findings with analyst:
|
Review findings with analyst:
|
Then complete these activities…
|
Then complete these activities…
|
Then complete these activities…
|
With these tools & templates:
|
With these tools & templates:
|
With these tools & templates:
|
Phase 2: Procure, Receive, and Deploy
VISA used high-quality SAM data to optimize its software licensing

Case Study
Industry: Financial Services
Source: SAM Summit 2014
Challenge
Visa formed a SAM team in 2011 to combat costly software audits.
The team’s first task was to use the available SAM data and reconcile licenses deployed throughout the organization.
Organizations as large as Visa constantly run into issues where they are grossly over or under licensed, causing huge financial risk.
Solution
Data collection and analysis were used as part of the license rationalization process. Using a variety of tools combined with a strong team allowed Visa to perform the necessary steps to gather license data and analyze usage.
One of the key exercises was uniting procurement and deployment data and the teams responsible for each.
End-to-end visibility allowed the data to be uniform. As a result, better decisions about license rationalization can be made.
Results
By improving its measurement of SAM data, Visa was able to dedicate more time to analyze and reconcile its licenses. This led to improved license management and negotiations that reflected actual usage.
By improving license usage through rationalization, Visa reduced the cost of supporting additional titles.
The SAM team also performed license reclamation to harvest and redistribute licenses to further improve usage. The team’s final task was to optimize audit responses.
Step 2.1 Request and procure software
| Phase 2: Procure, Receive & Deploy | This step will walk you through the following activities: | This step involves the following participants: | |
2.1 | Request & Procure |
|
|
2.2 | Receive & Deploy | ||
Step Outcomes
- Defined standards for software requests
- A documented policy for software procurement including authorization thresholds
- Documented process workflows for new contracts and contract renewals
Procurement and SAM teams must work together to optimize purchasing
Procurement and SAM must collaborate on software purchases to ensure software purchases meet business requirements and take into account all data on existing software and licenses to optimize the purchase and contract. Failure to work together can lead to unnecessary software purchases, overspending on purchases, and undesirable contract terms.
SAM managers must collaborate with Procurement when purchasing software.
SAM managers should:
|

|
Procurement must commit to be involved in the asset management process.
Procurement should:
|
Centralize procurement to decrease the likelihood of overspending
Centralized negotiation and purchasing of software can ensure that the SAM team has visibility and control over the procurement process to help prevent overspending and uncontrolled agreements.
Benefits of centralized procurement
- Ability to easily manage software demand.
- Provides capability to effectively manage your relationships with suppliers.
- Allows for decreased contract processing times.
- Provides easy access to data with a single consolidated system for tracking assets at an early stage.
- Reduces number of rogue purchases by individual departments.
- Efficiency through automation and coordinated effort to examine organization’s compliance and license position.
- Higher degree of visibility and transparency into asset usage in the organization.
Info-Tech Insights
It may be necessary to procure some software locally if organizations have multiple locations, but try to centrally procure and manage the biggest contracts from vendors that are likely to audit the organization. Even with a decentralized model, ensure all teams communicate and that contracts remain visible centrally even if managed locally.
Standards for software procurement help prevent overspending
Software procurement is often more difficult for organizations than hardware procurement because:
- Key departments that need to be involved in the purchasing process do not communicate or interact enough.
- A fear of software auditing causes organizations to overspend to mitigate risk.
- Standards are often not in place, with most purchases being made outside of the gold imaging standard.
- A lack of discovery results in gross overspending on software licenses that are already present and underused.
Info-Tech Insight
One of the major challenges involved in implementing SAM is uniting multiple datasets and data sources across the enterprise. A conversation with each major business unit will help with the creation of software procurement standards that are acceptable to all.
Determine which software contracts should be centralized vs. localized (optional)
![]() 2.1.1 Identify central standard enterprise offerings
2.1.1 Identify central standard enterprise offerings
Participants: CIO, IT Director, SAM Manager, SAM Team
Document: Document in the Standard Operating Procedures.
- As a group, list as many software contracts that are in place across the organization as can easily be identified, focusing on top vendors.
- Identify which existing software contracts are standard enterprise offerings that are procured and managed centrally and which are non-standard or localized applications.
- Looking at the list of non-standard software, identify if any can or should be rationalized or replaced with a standard offering.
Standard enterprise offerings
|
Localized or non-standard software |
Classify your approved software into tiers to improve workflow efficiency
Not all titles are created equal; classifying your pre-approved and approved software titles into a tiered system will provide numerous benefits for your SAM program.
The more prestigious the asset tier, the higher the degree of data capture, support, and maintenance required.
- Mission-critical, high-priority applications are classified as gold standard.
- Secondary applications or high priority are silver standard.
- Low-usage applications or normal priority are bronze standard.
E.g. An enterprise application that needs to be available 24/7, such as a learning management system, should be classified as a gold tier to ensure it has 24/7 support.
Creating tiers assists stakeholders in justifying the following set of decision points:
- Which assets will require added maintenance (e.g. software assurance for Microsoft)
- Technical support requirements to meet business requirements
- Lifecycle and upgrade cycle of the software assets.
- Monitoring usage to determine whether licenses can be harvested
- Authorizations required for purchase requests
Determine your software standards
![]() 2.1.2 Identify standard software images for your organization
2.1.2 Identify standard software images for your organization
Participants: Asset Manager, Purchasing, Service Desk Manager, Operations (optional)
Document: Document in the Standard Operating Procedures.
- As a group, discuss and identify the relevant software asset tiers and number of tiers.
- For each tier, define:
- Support requirements (hours and payments)
- Maintenance requirements (mandatory or optional)
- Lifecycle (when to upgrade, when to patch)
- Financial requirements (CapEx/OpEx expenses)
- Request authorizations (requestors and approvers)
- Sort the software contracts identified in the previous category into tiers, for example:
- Mission-critical software (gold tier)
- High-priority software (silver tier)
- Normal-priority software (bronze tier)
- Use the SOP as an example.
Determine which licensing options and methodologies fit into future IT strategy
Not everyone is ready to embrace the cloud for all solutions; make sure to align cloud strategy to business requirements. Work closely with IT executives to determine appropriate contract terms, licensing options, and tracking processes.
Vendors make changes to bundles and online services terms on a regular basis. Ensure you document your agreed upon terms to save your required functionality as vendor standard offerings change.
- Any contracts getting moved to the cloud will need to undergo a contract comparison first.
- The contract you signed last month could be completely different this month. Many cloud contracts are dynamic in nature.
- Keep a copy of the electronic contract that you signed in a secure, accessible location.
- Consider reaching a separate agreement with the vendor that they will ensure you maintain the results of the original agreement to prevent scope creep.
Not all on-premises to cloud options transition linearly:
- Features of perpetual licenses may not map to subscriptions
- Product terms may differ from online services terms
- Licensing may change from per device to per user
- Vendor migrations may be more complex than anticipated
Download the Own the Cloud: Strategy and Action Plan blueprint for more guidance
Understand the three primary models of software usage agreements
| Licensed | Open Source | Shareware | |
|---|---|---|---|
| License Structure | A software supplier is paid for the permission to use their software. | The software is provided free of charge, but is still licensed. | The software is provided free of charge, but is still licensed. Usage may be on a trial basis, with full usage granted after purchase. |
| Source Code | The source code is still owned by the supplier. | Source code is provided, allowing users to change and share the software to suit their needs. | Source code is property of the original developer/supplier. |
| Technical Support | Technical support is included in the price of the contract. | Technical support may be provided, often in a community-based format from other developers of the open-source software in question. | Support may be limited during trial of software, but upgraded once a purchase is made. |
Info-Tech Insight
Open-source software should be managed in the same manner as commercial software to understand licensing requirements and be aware of any changes to these agreements, such as commercialization of such products, as well as any rules surrounding source code.
Coordinate with purchasing department to define software procurement policy
![]() 2.1.3 Define procurement policy
2.1.3 Define procurement policy
Participants: Asset Manager, Purchasing, Service Desk Manager, Operations (optional)
Document: Document in the Standard Operating Procedures.
Define and document policies that will apply to IT software purchases, including policies around:
- Software purchase approvals
- Licenses for short-term contractors
- On-premises vs. SaaS purchases
- Shareware and freeware fees
- Open-source software
Use the example below as guidance and document in the SOP.
- Software will not be acquired through user corporate credit cards, office supply, petty cash, or personal expense budgets. Purchases made outside of the acceptable processes will not be reimbursed and will be removed from company computers.
- Contractors who are short term and paid through vendor contracts and invoices will supply their own licenses.
- Software may be purchased as on-premises or as-a-service solutions as IT deems appropriate for the solution.
- Shareware and freeware authors will be paid the fee they specify for use of their products.
- Open-source software will be managed in the same manner as commercial software to understand licensing requirements and be aware of any changes to these agreements, such as commercialization of such products.
Identify approvals and requests for authorization thresholds
![]() 2.1.4 Identify financial thresholds for approvals and requests
2.1.4 Identify financial thresholds for approvals and requests
Participants: Asset Manager, Purchasing, CIO, CFO, IT Director
Document: Document in the Standard Operating Procedures.
Identify and classify financial thresholds for contracts requiring approval. For each category of contract value, identify who needs to authorize the request. Discuss and document any other approvals necessary. An example is provided below.
Example:
Requests for authorization will need to be directed based on the following financial thresholds:
| Contract value | Authorization |
|---|---|
| <$50,000 | IT Director |
| $50,000 to $250,000 | CIO |
| $250,000 to $500,000 | CIO and CFO |
| >$500,000 | Legal review |
Develop a defined process for software procurement
A poorly defined software procurement workflow can result in overspending on unnecessary software licensing throughout the year. This can impact budgeting and any potential software refreshes, as businesses will often rely on purchasing what they can afford, not what they need.
Benefits of a defined workflow
- Standardized understanding of the authorization processes results in reduced susceptibility to errors and quicker processing times.
- Compliance with legal regulations.
- Protection from compliance violations.
- Transparency with the end user by communicating the process of software procurement to the business.
Elements to include in procurement workflows:
- RFP
- Authorizations and approvals
- Contract review
- Internal references to numbers, cost centers, locations, POs, etc.
Four types of procurement workflows:
- New contract – Purchasing brand new software
- Add to contract – Adding new POs or line items to an existing contract
- Contract renewal – Renewing an existing contract
- No contract required – Smaller purchases that don’t require a signed contract
Outline the procurement process for new contracts
The procurement workflow may involve the Service Desk, procurement team, and asset manager.
The following elements should be accounted for:
- Assignee
- Requestor
- Category
- Type
- Model or version
- Requisition number
- Purchase order number
- Unit price
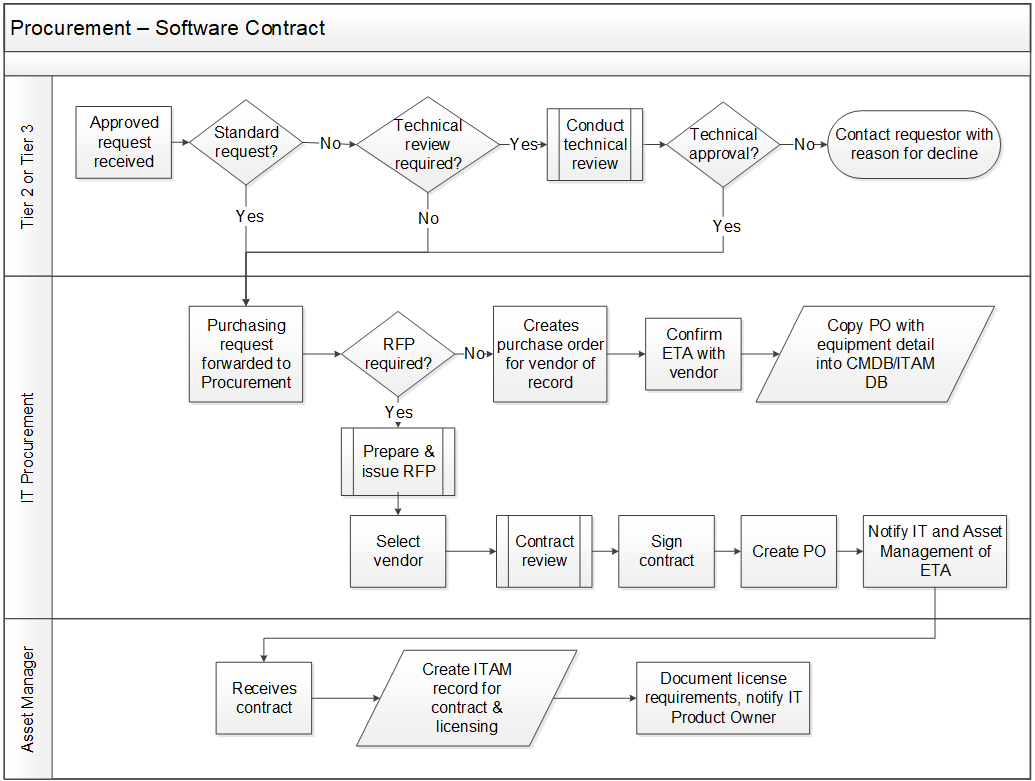
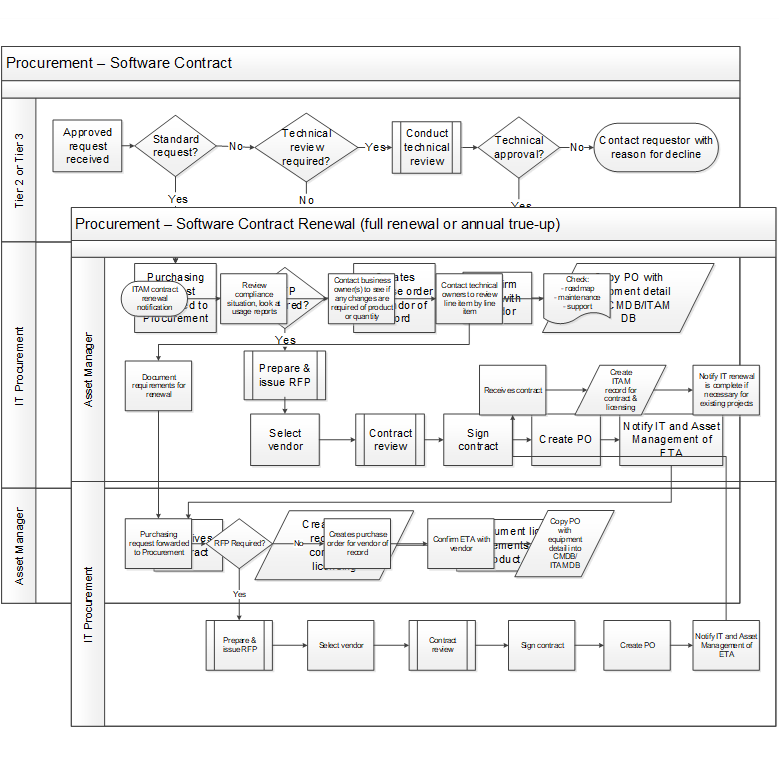
Build software procurement workflow for new contracts
![]() 2.1.5 Build new contract procurement workflow
2.1.5 Build new contract procurement workflow
Participants: Asset Manager, Purchasing, Service Desk Manager, Operations (optional)
Document: Document in the Standard Operating Procedures.
- As a team, outline each of the tasks in the process of procuring a new software asset using cue cards, sticky notes, or a whiteboard.
- Use the sample procurement workflow on the previous slide as an example if needed.
- Ensure the following elements required for the asset procurement process have been accounted for:
- Assignee
- Requestor
- Category
- Type
- Model or version
- Requisition number
- Purchase order number
- Unit price
- Review the workflow and make any adjustments necessary to improve the process. Document using Visio and add to the SOP.
Review vendor contracts to right-size licensing procurement
Many of your applications come from the same vendor, and a view into the business services provided by each software vendor contract will prove beneficial to the business.
- You may uncover overlaps in services provided by software across departments.
- The same service may be purchased from different vendors simply because two departments never compared notes!
- This leaves a lot of money on the table from a lack of volume discounts.
- Be cautious about approaching license budgeting strictly from a cost perspective. SAM is designed to right-size your licenses to properly support your organization.
- One trap organizations often fall into is bundling discounts. Vendors will offer steep discounts if clients purchase multiple titles. On the surface, this might seem like a great offer.
- However, what often happens is that organizations will bundle titles to get a steep discount on their prize title of the group.
- The other titles become shelfware, and when the time comes to renew the contract, the maintenance fees on the shelfware titles will often make the contract more expensive than if only the prize title was purchased.
Additionally, information regarding what licenses are being used for certain services may yield insight into potential redundancies. For example, two separate departments may have each have a different application deployed that supports the same service. This presents an opportunity for savings based on bulk licensing agreements, not to mention a simplified support environment by reducing the number of titles deployed in your environment.
Define a procedure for tracking and negotiating contract renewals
Participants: IT Director/CIO, Asset Manager, Purchasing, Service Desk Manager, Operations (optional)
Document: Document in the Standard Operating Procedures.
Discuss and document a policy for tracking and negotiating contract renewals. Answer the following questions as guides:
- How will renewal dates be tracked and monitored?
- How soon should contracts be reviewed prior to renewal to determine appropriateness for use and compliance?
- What criteria will be used to determine if the product should be renewed?
- Who will be consulted for contract renewal decisions for major contracts?
- How will licensing and support decisions be made?
Optional contract review:
- Take a sample contract to renew. Create a list of services that are supported by the software. Look for overlaps, redundancies, shelfware, and potential bundling opportunities. Recall the issues outlined when purchasing bundled software.
- Create a list of action items to bring into the next round of contract negotiations with that vendor and identify a start date to begin reviewing these items.
Define process for contract renewals and additional procurement scenarios
![]() 2.1.6 Build additional procurement workflows
2.1.6 Build additional procurement workflows
Participants: Asset Manager, Purchasing, Service Desk Manager, Operations (optional)
Document: Document in the Standard Operating Procedures.
Build procurement workflows and define policies and procedures for additional purchasing scenarios beyond new contracts.
This may include:
- Contract renewals
- Single purchase, non-contract procurement
- Adding to contracts
Use the sample workflows in the Standard Operating Procedures as a guide.
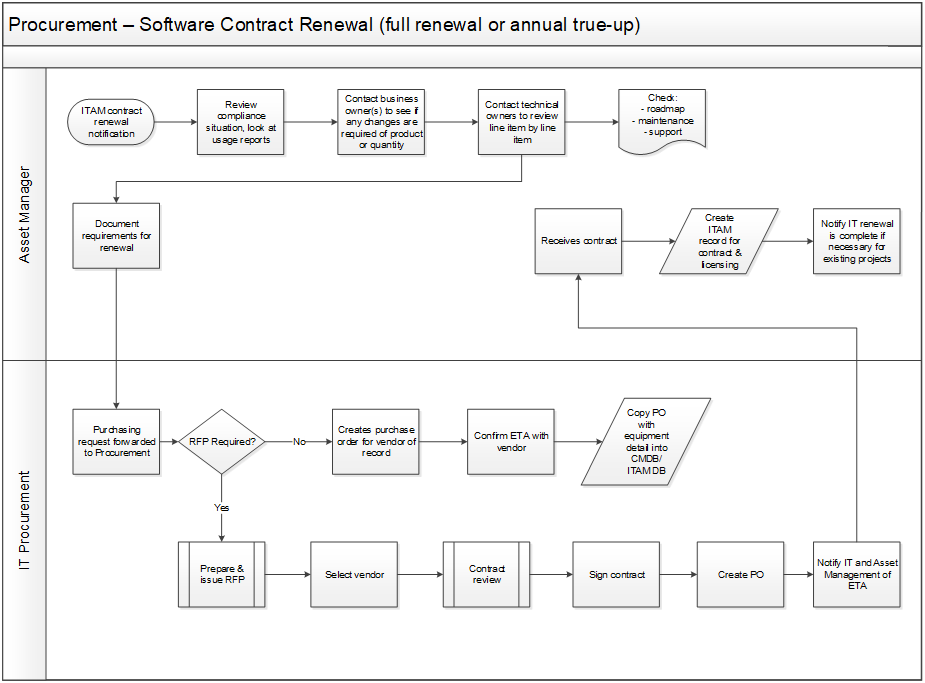
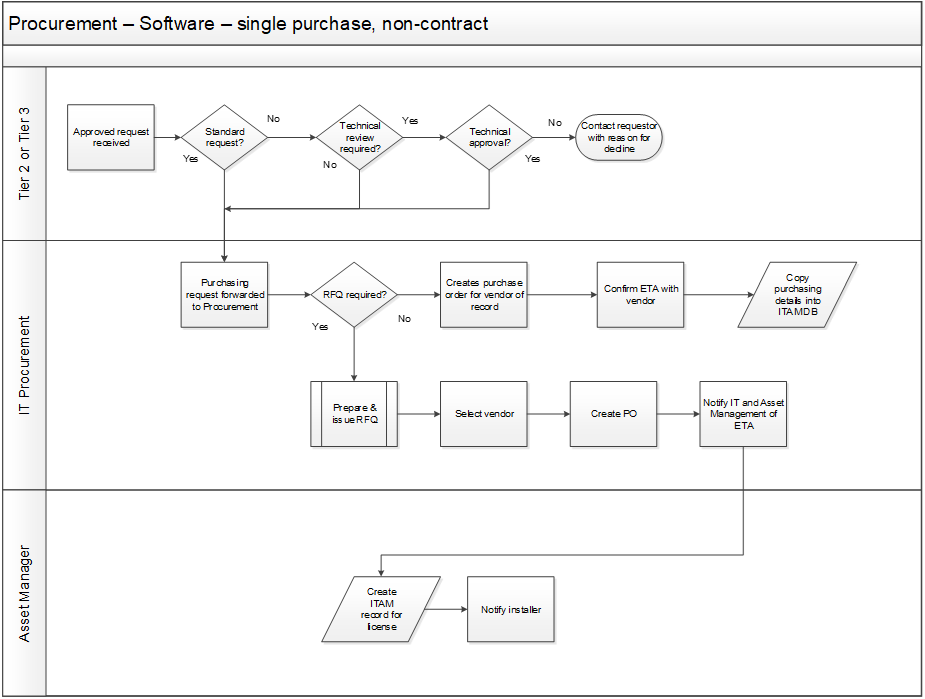
Negotiate for value to ensure quality license agreements
Approach negotiating from a value-first, price-second perspective.
Contract negotiations too often come down to a question of price. While you want to avoid overpaying for licenses, a worse offense is getting a steep discount for a bundle of applications where the majority will go unused.
| Vendors will try to sell a full stack of software at a steep discount to give the illusion of value. Often organizations bite off more than they can chew. | → | When auditors come knocking, the business may be in compliance, but being over-licensed is a dangerous state to be in. | → | Organizations end up over-licensed and in possession of numerous “shelfware” apps that sit on the proverbial shelf collecting dust while drawing expensive maintenance and licensing fees from the business. |
- Pressure from the business is also an issue. Negotiations can be rushed in an effort to fulfill an immediate need.
- Make sure you clearly outline the level of compliance expected from the vendor.
- Negotiate reduced-fee software support services. Your Service Desk can already handle the bulk of requests, and investing in a mature Service Desk will provide more lasting value than paying for expensive maintenance and support services that largely go unused.
Learn to negotiate effectively to optimize contract renewals
Leverage Info-Tech’s research, Master Contract Review and Negotiation for Software Agreements, to review your software contracts to leverage your unique position during negotiations and find substantial cost savings.
This blueprint includes the following tools and templates:
- RASCI Chart
- Vendor Communication Management Plan
- Software Business Use Case Template
- SaaS TCO Calculator
- Software Terms & Conditions Evaluation Tool
- Software Buyer’s Checklist
- Controlled Vendor Communications Letter
- Key Vendor Fiscal Year End Calendar
- Contract Negotiation Tactics Playbook
Step 2.2 Receive and deploy software
| Phase 2: Procure, Receive & Deploy | This step will walk you through the following activities: | This step involves the following participants: | |
2.1 | Request & Procure |
|
|
2.2 | Receive & Deploy | ||
Step Outcomes
- A strategy for storing software information and media in the ITAM database and DML
- A documented workflow for the software receiving process
- Documented process workflows for software requests and deployment, including for large quantities of software
- A list of pre-approved, approved, and unapproved software titles for deployment
- A process for responding to non-standard software requests
Verify product and information upon receipt
Upon receipt of procured software:
- Verify that the product is correct
- Reconcile with purchase record to ensure the order has been completed
- Verify that the invoice is correct
- Update financial information such as budget and accounting records
- Update ITAM database to show status as received
- Record/attach license keys and software codes in ITAM database
- Attach relevant documents to record in the ITAM database (license reports, invoices, end-user agreement, etc.)
- Download and store any installation files, DVDs, and CDs
- Once software has been installed, verify license is matched to discovered installed software within the ITAM database
Info-Tech Best Practice
While most software will be received through email and download, in some cases physical software may be received through courier or mail. Ensure processes and procedures are defined for both cases.
Establish a secure repository for licenses and documentation
All licenses, documentation, and digital media for authorized and supported software should be collected and stored in a central, secure location to minimize risk of theft, loss, or unauthorized installation or duplication of software.
Where to store software data?
The ITAM database should contain an up-to-date record of all software assets, including their associated:
- Serial numbers
- License keys and codes
- Contracts and agreements
The database allows you to view software that is installed and associated licenses.
A definitive media library (DML) is a single logical storage area, which may consist of one or more locations in which definitive authorized versions of all software configuration items are securely stored and protected.
The DML consists of file storage as well as physical storage of CDs and DVDs and must be continually updated to contain the latest information about each configuration item.
The DML is used to organize content and link to automated deployment to easily install software.
Use a definitive media library (DML) to assist in storage of software packages for deployment
The DML will usually contain the most up-to-date versions to minimize errors created by having unauthorized, old, or problematic software releases being deployed into the live IT environment. The DML can be used for both full-packed product (FPP) software and in-house developed software, providing formalized data around releases of in-house software.
The DML should consist of two main storage areas:
- Secure file storage
- Secure physical storage for any master CD/DVDs
Additional Recommendations:
- The process of building, testing, adapting, and final pre-production testing should provide your IT department with a solid final deployment package, but the archive will enable you to quickly pull in a previous version if necessary.
- When upgrading software packages to include new patches or configurations, use the DML to ensure you're referencing a problem-free version.
- Include the DML in your disaster recovery plan (DRP) and include testing of the DML as part of your DRP testing. If you need to rebuild servers from these files, offsite, you'll want to know your backup DML is sound.
Ensure you have a strategy to create and update your DML
Your DML should have a way to separate archived, new, and current software to allow for optimal organization of files and code, to ensure the correct software is installed, and to prepare for automated deployment through the service catalog.
New software hasn’t been tested yet. Make it available for testing, but not widely available.
Keep a record for archived software, but do not make it available for install.
Current software is regularly used and should be available for install.
Deployment
- Are you using tools to integrate with the DML for deployment?
- Store files that are ready for automated deployment in a separate location.
Identify storage locations for software information and media
![]() 2.2.1 Identify software storage locations
2.2.1 Identify software storage locations
Participants: Asset Manager, IT Director
Document: Document in the Standard Operating Procedures.
- Identify storage locations for asset data that is received (i.e. ITAM database, DML).
- Identify information that should be stored with each asset (i.e. license, serial number, invoice, end-user license agreement) and where this information should be stored.
- Identify fields that should be populated in the DML for each record:
- Product name
- Version
- Description
- Authorized by
- Received by/date
- Configuration item on which asset is installed
- Media
- Physical and backup locations
- Verified by/date
Define the standard process for receiving software
Define the following in your receiving process:
- Process for software received by email/download
- Process for physical material received at Service Desk
- Information to be recorded and where
- Process following discrepancy of received software
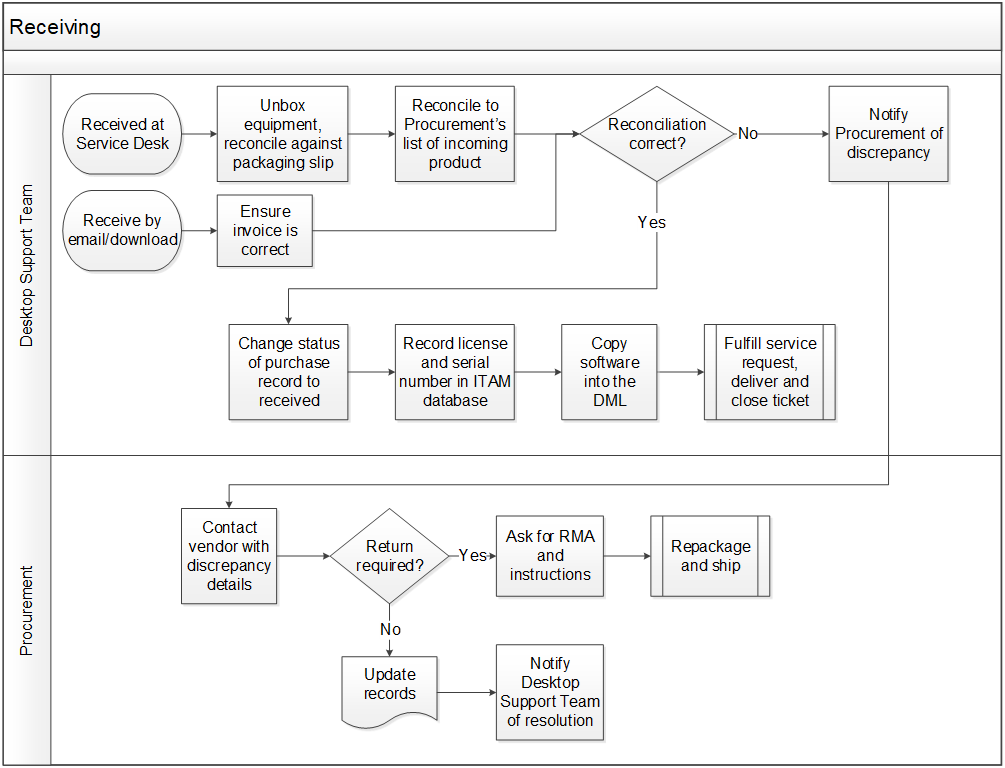
Design the workflow for receiving software
![]() 2.2.2 Design the workflow for receiving software
2.2.2 Design the workflow for receiving software
Participants: Asset Manager, Purchasing, Service Desk Manager, Operations (optional)
Document: Document in the Standard Operating Procedures.
Option 1: Whiteboard
- Discuss the workflow and draw it on the whiteboard.
- Assess whether you are using the best workflow. Modify it if necessary.
- Use the sample workflow from this step as a guide if starting from scratch.
- Engage the team in refining the process workflow.
- Transfer data to Visio and add to the SOP.
Option 2: Tabletop Exercise
- Distribute index cards to each member of the team.
- Have each person write a single task they perform on the index card. Be granular. Include the title or the name of the person responsible.
- Mark cards that are decision points. Use a card of a different color or use a marker to make a colored dot.
- Arrange the index cards in order, removing duplicates.
- Assess whether you are using the best workflow. Engage the team to refine it if necessary.
- Transfer data to Visio and add to the SOP.
Build release management into your software deployment process
A sound software deployment process is tied to sound release management practices.
Releases: A collection of authorized changes to an IT service. Releases are divided into:
- Major software releases/upgrades: Normally containing large areas of new functionality, some of which may make intervening fixes to redundant problems.
- Minor software releases/upgrades: Normally containing small enhancements and fixes, some of which may have already been issued as emergency fixes.
- Emergency software fixes: Contain the corrections to a small number of known problems.
Ensure that release management processes work with SAM processes:
- If a release will impact licensing, the SAM manager must be made aware to make any necessary adjustments.
- Deployment models should be in line with SAM strategy (i.e. is software rolled out to everyone or individually when upgrades are needed?).
- How will user requests for upgrades be managed?
- Users should be on the same software version to ensure file compatibility and smooth patch management.
- Ideally, software should be no more than two versions back.
Document the process workflow for software deployment
Define the process for deploying software to users.
Include the following in your workflow:
- All necessary approvals
- Source of software
- Process for standard vs. non-standard software requests
- Update ITAM database once software has been installed with license data and install information
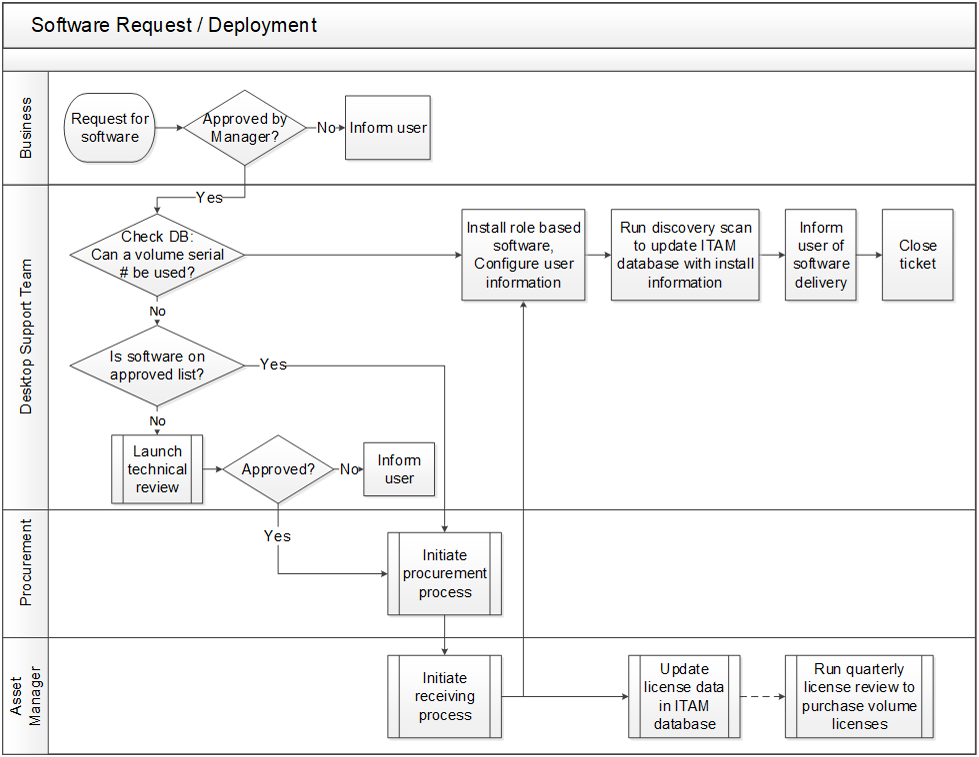
Large-scale software rollouts should be run as projects
Rollouts or upgrades of large quantities of software will likely be managed as projects.
These projects should include project plans, including resources, timelines, and detailed procedures.
Define the process for large-scale deployment if it will differ from the regular deployment process.
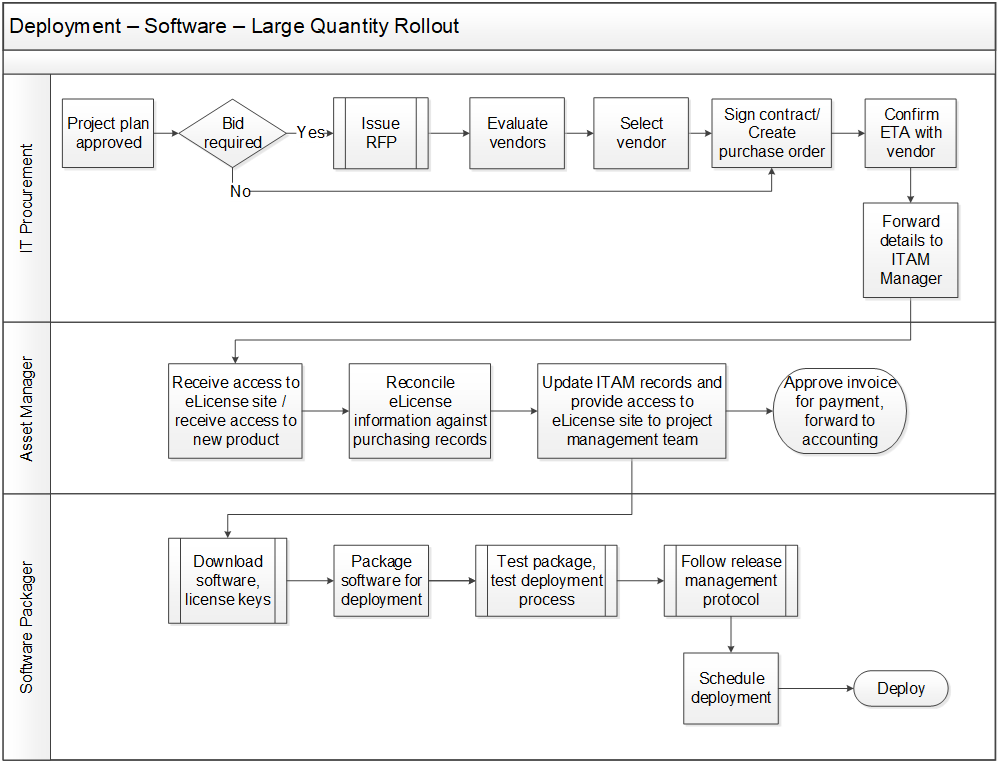
Design and document the deployment workflow(s)
![]() 2.2.3 Document deployment workflows for desktop and large-scale deployment
2.2.3 Document deployment workflows for desktop and large-scale deployment
Participants: Asset Manager, Service Desk Manager, Release & Deployment Manager
Document: Document in the Standard Operating Procedures.
- Outline each step in the process of software deployment using notecards or on a whiteboard. Be as granular as possible. On each card, describe the step and the individual responsible for each step.
- Be sure to identify the type of release for standard software releases and patches.
- Additionally, identify how additional software outside the scope of the base image will be addressed.
- When you are satisfied that each step is accurately captured, use a second color of notecard to document any challenges, inefficiencies, or pains associated with each step. Consider further documenting the time on each task.
- Examine each challenge or pain point. Discuss whether there is a clear solution to the problem. If so, document the solution and amend the workflow. If not, engage in a broader discussion of possible solutions, considering people, processes, and available technology.
- Document separately the process for large-scale software deployment if required.
Develop standards to streamline your software estate
Software should be approved and deployed based on approved standards to minimize over-deployed software and manage costs appropriately. A list of standard software improves the efficiency of the software approval process.
- Pre-approved titles include basic platforms like Office or Adobe Reader that are often available in enterprise-wide license packages.
- Approved titles include popular titles with license numbers that need to be managed on a role-by-role basis. For example, if most of your marketing team uses the Adobe Creative Suite, a user still needs to get approval before they can get a license.
- Unapproved titles are managed on a case-by-case basis and are up to the discretion of the asset manager and other involved parties.
Additionally, create a list of unauthorized software including titles not to be installed under any circumstances. This list should be designed with feedback from your end users and technical support staff. Front-line knowledge is crucial to identifying which titles are causing major problems.
Create a list of pre-approved, approved, and unapproved software titles
![]() 2.2.4 Determine software categories for deployment
2.2.4 Determine software categories for deployment
Participants: IT Director, Asset Manager, Purchasing (optional), Service Desk Manager (optional), Release & Deployment Manager (optional)
Document: Document in the Standard Operating Procedures.
- Define software categories that will be used to build software standards.
- Include definitions of each category.
- Add examples of software to each category to begin building list of approved software titles for deployment.
Use the following example as a guide.
| Category | Definition | Software titles |
|---|---|---|
| Pre-approved/standard |
|
|
| Approved by role |
|
|
| Unapproved/requires review |
|
|
| Unauthorized |
|
|
Define the review and approval process for non-standard software
Software requiring review will need to be managed on a case-by-case basis, with approval dependent on software evaluation and business need.
The evaluation and approval process may require input from several parties, including business analysts, Security, technical team, Finance, Procurement, and the manager of the requestor’s department.
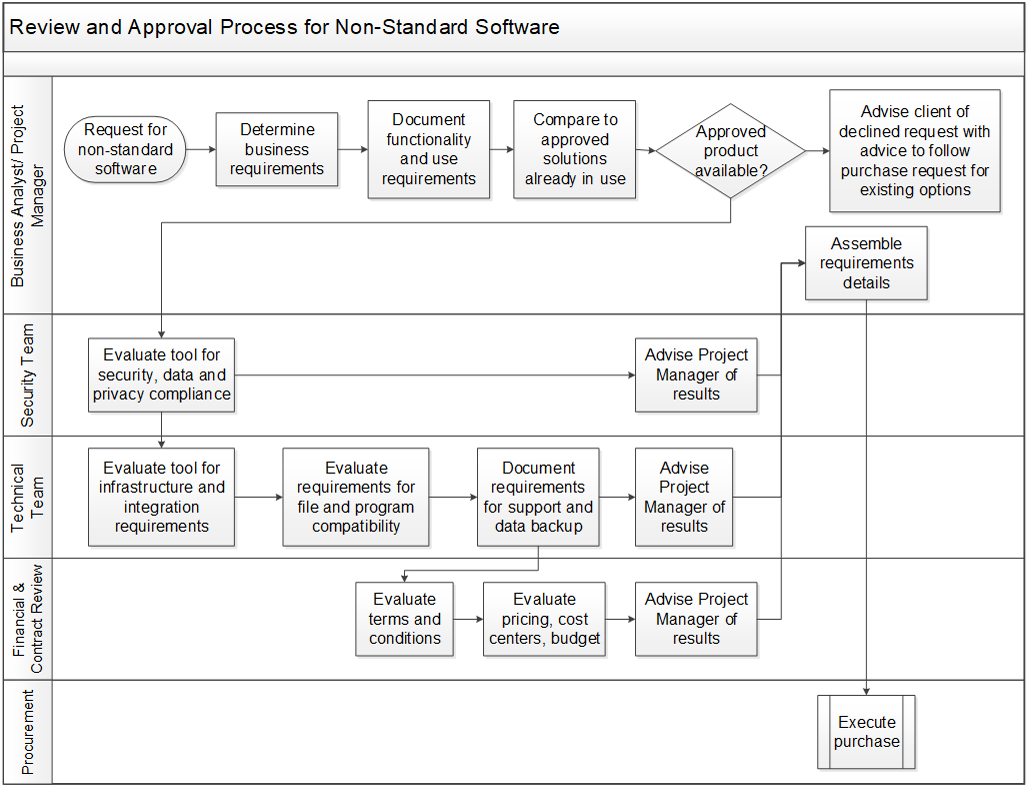
Document the request and deployment process for non-standard software
![]() 2.2.5 Document process for non-standard software requests
2.2.5 Document process for non-standard software requests
Participants: Asset Manager, Service Desk Manager, Release & Deployment Manager
Document: Document in the Standard Operating Procedures.
Define the review and approval process for non-standard software requests.
Use the workflow on the previous slide as a guide to map your own workflow process and document the steps in the Standard Operating Procedures.
The following assessments may need to be included in the process:
- Functionality and use requirements: May include suggestion back to the business before proceeding any further to see if similar, already approved software could be used in its place.
- Technical specifications: Cloud, data center, hardware, backups, integrations (Active Directory, others), file, and program compatibility.
- Security: Security team may need to assess to ensure nothing will install that will compromise data or systems security.
- Privacy policy: Security and compliance team may need to evaluate the solution to ensure data will be secured and accessed only by authorized users.
- Terms and conditions: The contracts team may evaluate terms and conditions to ensure contracts and end-user agreements do not violate existing standards.
- Accessibility and compliance: Software may be required to meet accessibility requirements in accordance with company policies.
BMW deployed a global data centralization program to achieve 100% license visibility

Case Study
Industry: Financial Services
Source: SAM Summit 2014
Challenge
BMW is a large German automotive manufacturer that employs over 100,000 people. It has over 7,000 software products deployed across 106,000 clients and servers in over 150 countries.
When the global recession hit in 2008, the threat of costly audits increased, so BMW decided to boost its SAM program to cut licensing costs. It sought to centralize inventory data from operations across the globe.
Solution
A new SAM office was established in 2009 in Germany. The SAM team at BMW began by processing all the accumulated license and installation data from operations in Germany, Austria, and the UK. Within six months, the team had full visibility of all licenses and software assets.
Compliance was also a priority. The team successfully identified where they could make substantial reductions in support and maintenance costs as well as remove surplus costs associated with duplicate licensing.
Results
BMW overcame a massive data centralization project to achieve 100% visibility of its global licensing estate, an incredible achievement given the scope of the operation.
BMW experienced efficiency gains due to transparency and centralized management of licenses through the new SAM office.
Additionally, internal investment in training and technical knowledge has helped BMW continuously improve the program. This has resulted in ongoing cost reductions for the manufacturer.
If you want additional support, have our analysts guide you through this phase as part of an Info-Tech Workshop 
Book a workshop with our Info-Tech analysts:

|
|
The following are sample activities that will be conducted by Info-Tech analysts with your team:
2.1.5 |
|
Build software procurement workflow for new contracts
Use the sample workflow to document your own process for procurement of new software contracts. |
2.2.4 |
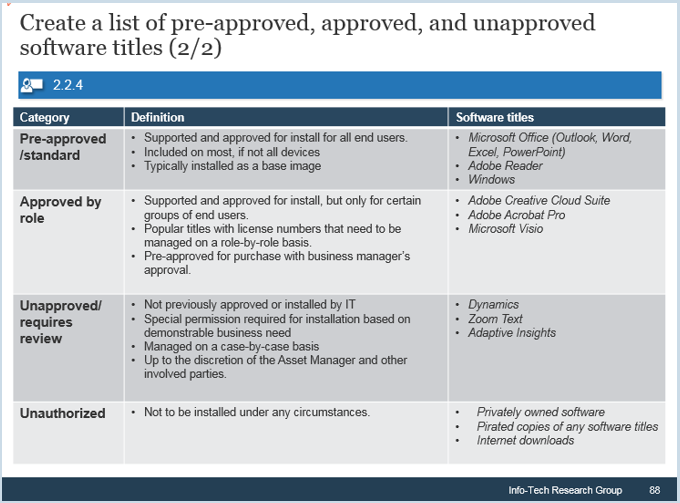
|
Create a list of pre-approved, approved, and unapproved software titles
Build definitions of software categories to inform software standards and brainstorm examples of each category. |
Phase 2 outline
![]() Call 1-888-670-8889 or email GuidedImplementations@InfoTech.com for more information.
Call 1-888-670-8889 or email GuidedImplementations@InfoTech.com for more information.
Complete these steps on your own, or call us to complete a guided implementation. A guided implementation is a series of 2-3 advisory calls that help you execute each phase of a project. They are included in most advisory memberships.
Guided Implementation 2: Procure, receive, and deploy
Proposed Time to Completion (in weeks): 6
| Step 2.1: Request and procure | Step 2.2: Receive and deploy |
Start with an analyst kick-off call:
| Review findings with analyst:
|
Then complete these activities…
| Then complete these activities…
|
With these tools & templates:
| With these tools & templates:
|
Phase 3: Manage, Redeploy, and Retire
Step 3.1 Manage and maintain software contracts
| Phase 3: Manage, Redeploy & Retire | This step will walk you through the following activities: | This step involves the following participants: | |
3.1 | Manage & Maintain Software |
|
|
3.2 | Harvest, Redeploy, or Retire | ||
Step Outcomes
- A process for conducting regular software inventory checks and analyzing the data to continually manage software assets and license compliance.
- An understanding of software maintenance requirements
- A policy for conducting regular software maintenance and patching
- A documented patch management policy
Manage your software licenses to decrease your risk of overspending
Many organizations fail to track their software inventory effectively; the focus often remains on hardware due to its more tangible nature. However, annual software purchases often account for a higher IT spend than annual hardware purchases, so it’s important to track both.
Benefits of managing software licenses
- Better control of the IT footprint. Many companies already employ hardware asset management, but when they employ SAM, there is potential to save millions of dollars through optimal use of all technology assets.
- Better purchasing decisions and negotiating leverage. Enhanced visibility into actual software needs means not only can companies procure and deploy the right increments of software in the right areas, but they can also do so more cost-effectively through tools such as volume purchase agreements or bundled services.
- No refund policy combined with shelfware (software that sits unused “on the shelf”) is where software companies make their money.
- Managing licenses will help prevent costly audit penalties. Special attention should be paid to software purchased from large vendors such as Microsoft, Oracle, Adobe, SAP, or IBM.
Maintain a comprehensive, up-to-date software inventory to manage licenses effectively
A clearly defined process for inventory management will reduce the risk of over buying licenses and falling out of compliance.
- A detailed software inventory and tracking system should act as a single point of contact for all your license data.
- Maintain a comprehensive inventory of installed software through complete and accurate records of all licenses, certifications, and software purchase transactions, storing these in a secure repository.
- Periodically review installed software and accompanying licenses to ensure only legal and supported software is in use and to ensure ongoing compliance with the software management policy.
Info-Tech Best Practice
Have and maintain a list of supported software to guide what new software will be approved for purchase and what current software should be retained on the desktops, servers, and other processing devices.
Conduct a baseline inventory of deployed software to know what you have
You have to know what you have before you can manage it.
A baseline inventory tells you exactly what software you have deployed and where it is being used. This can help to determine how to best optimize software and license usage.
A software inventory will allow you to:
- Identify all software residing on computers.
- Compare existing software to the list of supported software.
- Identify and delete illegal or unsupported software.
- Identify and stop software use that violates license agreements, copyright law, or organizational policies.
Two methods for conducting a software inventory:
- If you have several computers to analyze, use automated tools to conduct inventory for greater accuracy and efficiency. Software inventory or discovery tools scan installed software and generate inventory reports, while asset management tools will help you manage that data.
- Manual inventory may be possible if your organization has few computers.
How to conduct a manual software inventory:
- Record serial number of device being analyzed.
- Record department and employee to whom the computer is assigned.
- Inspect contents of hard drive and/or server to identify software as well as hidden files and directories.
- Record licensing information for software found on workstation and server.
- Compare findings with list of supported software and licenses stored in repository.
Keep the momentum going through regular inventory and licensing checks
Take preventive action to avoid unauthorized software usage through regular software inventory and license management:
- Regularly update the list of supported software and authorized use.
- Monitor and optimize software license usage.
- Continually communicate with and train employees around software needs and policies.
- Maintain a regular inventory schedule to keep data up to date and remain compliant with licensing requirements – your specific schedule will depend on the size of the company and procurement schedule.
- Conduct random spot inventories – even if you are using a tool, periodic spot checks should still be performed to ensure accuracy of inventory.
- Periodically review software procurement records and ensure procurement process is being followed.
- Continuously monitor software installations on networked computers through automated tools.
- Ensure software licensing documentation and data is secure.
Define process for conducting software inventory
![]() 3.1.1 Define process for regular software inventory
3.1.1 Define process for regular software inventory
Participants: IT Director, Asset Manager
Document: Document in the Standard Operating Procedures.
- If a baseline software inventory has not been conducted, discuss and document a plan for completing the inventory.
- Will the inventory be conducted manually or through automated tools?
- If manually, what information will be collected and recorded? Which devices will be analyzed? Where will data be stored?
- If automatically, which tools will be used? Will any additional information need to be collected? Who will have access to the inventory?
- When will the inventory be conducted and by whom?
- Monthly inventory may be required if there is a lot of change and movement, otherwise quarterly is usually sufficient.
- Document how inventory data will be analyzed.
- How will data be compared against supported software?
- How will software violations be addressed?
- Develop a plan for continual inventory spot checks and maintenance.
- How often will inventory be conducted and/or analyzed?
- How often will spot checks be performed?
Don’t forget that software requires maintenance
While maintenance efforts are typically focused around hardware, software maintenance – including upgrades and patches – must be built into the software asset management process to ensure software remains compliant with security and regulatory requirements.
Software maintenance guidelines:
- Maintenance agreements should be stored in the ITAM database.
- Software should be kept as current as possible. It is recommended that software remain no more than two versions off.
- Unsupported software should be uninstalled or upgraded as required.
- Upgrades should be tested, especially for high-priority or critical applications or if integrated with other applications.
- Change and release management best practices should be applied for all software upgrades and patches.
- A process should be defined for how often patches will be applied to end-user devices.
Integrate patch management with your SAM practice to improve security and reduce downtime
The integration between patch management and asset management is incredibly valuable from a technology point of view. IT asset management (ITAM) tools create reports on the characteristics of deployed software. By combining these reports with a generalized software updater, you can automate most simple patches to save your team’s efforts for more-critical incidents. Usage reports can also help determine which applications should be reviewed and removed from the environment.
- In recent years, patch management has grown in popularity due to widespread security threats, the resultant downtime, and expenses associated with them.
- The main objective of patch management is to create a consistently configured environment that is secure against known vulnerabilities in operating systems and application software.
Assessing new patches should include questions such as:
- What’s the risk of releasing the patch? What is the criticality of the system? What end users will be affected?
- How will we manage business disruption during an incident caused by a failed patch deployment?
- In the event of service outage as a result of a failed patch deployment, how will we recover services effectively in business priority order?
- What’s the risk of expediting the patch? Of not releasing the patch at all?
Define policies for software maintenance and patches
![]() 3.1.2 Define software maintenance and patching policies
3.1.2 Define software maintenance and patching policies
Participants: IT Director, Asset Manager, Release Manager (optional), Security (optional)
Document: Document in the Standard Operating Procedures.
Software maintenance:
Review the software maintenance guidelines in this section and in the SOP template. Discuss each policy and revise and document in accordance with your policies.
Patch management:
Discuss and document patch management policies:
- How often will end-user devices receive patches?
- How often will servers be patched?
- How will patches be prioritized? See example below.
- Critical patches will be applied within two days of release, with testing prioritized to meet this schedule.
- High-priority patches will be applied within 30 days of release, with testing scheduled to meet this requirement.
- Normal-priority patches will be evaluated for appropriateness and will be installed as needed.
Document your patch management policy
The patch management policy helps to ensure company computers are properly patched with the latest appropriate updates to reduce system vulnerability and to enhance repair application functionality. The policy aids in establishing procedures for the identification of vulnerabilities and potential areas of functionality enhancements, as well as the safe and timely installation of patches. The patch management policy is key to identifying and mitigating any system vulnerabilities and establishing standard patch management practices.
Use Info-Tech’s Patch Management Policy template to get started.

Step 3.2 Harvest, Redeploy, or Retire Software
| Phase 3: Manage, Redeploy & Retire | This step will walk you through the following activities: | This step involves the following participants: | |
3.1 | Manage & Maintain Software |
|
|
3.2 | Harvest, Redeploy, or Retire | ||
Step Outcomes
- A defined process for harvesting and reallocating unused software licenses
- A defined policy for how and when to retire unused or outdated software
Harvest and reallocate software to optimize license usage
Using a defined process for harvesting licenses will yield a crop of savings throughout the organization.
Unused software licenses are present in nearly every organization and result in wasted resources and software spend. Recycling and reharvesting licenses is a critical process within software asset management to save your organization money.
Licensing Recycling
When computers are no longer in use and retired, the software licenses installed on the machines may be able to be reused.
License recycling involves reusing these licenses on machines that are still in use or for new employees.
License Harvesting
License harvesting involves more actively identifying machines with licenses that are either not in use or under utilized, and recovering them to be used elsewhere, thus reducing overall software spend on new licenses.
Use software monitoring data to identify licenses for reallocation in alignment with policies and agreements
- Monitor software usage
Monitor and track software license usage to gain a clear picture of where and how existing software licenses are being used and identify any unused or underused licenses. - Identify licenses for reharvesting
Identify software licenses that can be reharvested and reallocated according to your policy. - Uninstall software
Notify user, schedule a removal time if approved, uninstall software, and confirm it has been removed. - Reallocate license when needed
Sources of surplus licenses for harvest:
- Projects that required a license during a particular time period, but now do not require a license (i.e. the free version of the software will suffice)
- Licenses assigned to users no longer with the organization
- Software installed on decommissioned hardware
- Installed software that hasn’t been used by the user in the last 90 days (or other defined period)
- Over-purchased software due to poorly controlled software request, approval, or provisioning processes
Info-Tech Insight
Know the stipulations of your end-user license agreement (EULA) before harvesting and reallocating licenses. There may be restrictions on how often a license can be recycled in your agreement.
Create a defined process for software license harvesting
Define a standard reharvest timeline. For example, every 90 days, your SAM team can perform an internal audit using your SAM tool to gather data on software usage. If a user has not used a title in that time period, your team can remove that title from that user’s machine. Depending on the terms and conditions of the contract, the license can either be retired or harvested and reallocated.
Ensure you have exception rules built in for software that’s cyclical in its usage. For example, Finance may only use tax software during tax season, so there’s no reason to lump it under the same process as other titles.
It’s important to note that in addition to this process, you will need a software usage policy that supports your license harvest process.
The value of license harvesting
- Let’s say you paid for 1,000 licenses of a software title at a price of $200 per license.
- Of this total, 950 have been deployed, and of that total, 800 are currently being used.
- This means that 16% of deployed licenses are not in use – at a cost of $30,000.
- With a defined license harvest process, this situation would have been prevented.
Build a workflow to document the software harvest process
Include the following in your process:
- How will unused software be identified?
- How often will usage reports be reviewed?
- How will the user be notified of software to be removed?
- How will the software be removed?
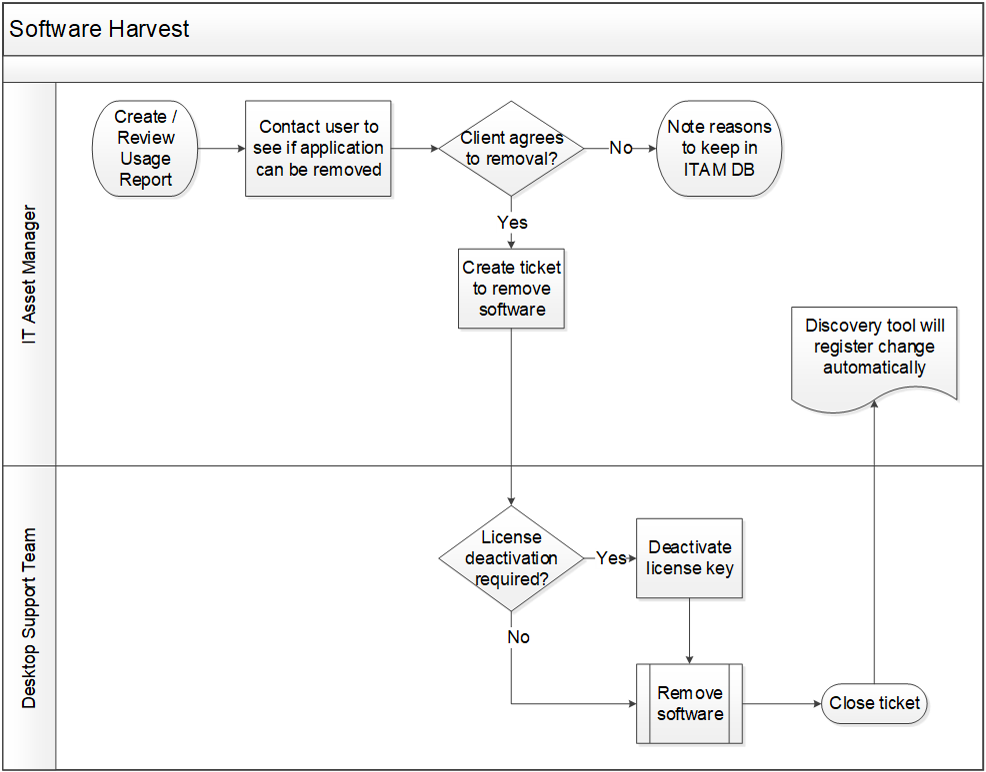
Map your software license harvest and reallocation process
![]() 3.2.1 Build license harvest and reallocation workflow
3.2.1 Build license harvest and reallocation workflow
Participants: IT Director, Asset Manager, Service Desk Manager
Document: Document in the Standard Operating Procedures.
- Outline each step in the process of software harvest and reallocation using notecards or a whiteboard. Be as granular as possible. On each card, describe the step and the individual responsible for each step.
- When you are satisfied that each step is accurately captured, use a second color of notecard to document any challenges, inefficiencies, or pains associated with each step. Consider further documenting the time on each task.
- Examine each challenge or pain point. Discuss whether there is a clear solution to the problem. If so, document the solution and amend the workflow. If not, engage in a broader discussion of possible solutions, considering people, processes, and available technology.
- Use the sample workflow on the previous slide as a guide if needed.

Improve your software retirement process to drive savings for the whole business
Business Drivers for Software Disposal
- Cost Reduction
- Application retirement allows the application and the supporting hardware stack to be decommissioned.
- This eliminates recurring costs such as licensing, maintenance, and application administration costs, representing potentially significant savings
- Consolidation
- Many legacy applications are redundant systems. For example, many companies have ten or more legacy financial systems from mergers/acquisitions.
- Systems can be siloed, running incompatible software. Moving data to a common accessible repository streamlines research, audits, and reporting.
- Compliance
- An increased focus on regulations places renewed emphasis on e-discovery policies. Keeping legacy applications active just to retain data is an expensive proposition.
- During application retirement, data is classified, assigned retention policies, and disposed of according to data/governance initiatives.
- Risk Mitigation
- Relying on IT to manage legacy systems is problematic. The lack of IT staff familiar with the application increases the potential risk of delayed responses to audits and e-discovery.
- Retiring application data to a common platform lets you leverage skills you have current investments in. This enables you to be responsive to audit or litigation results.
Retire your outdated software to decrease IT spend on redundant applications
Benefits of software retirement:
- Assists the service desk in not having to support every release, version, or edition of software that your company might have used in the past.
- Stay current with product releases so your company is better placed to take advantage of improvements built-in to such products, rather than being limited by the lack of a newly introduced function.
- Removing software that is no longer of commercial benefit can offer a residual value through assets.
Consequences of continuing to support outdated software:
- Budgets are tied up to support existing applications and infrastructure, which leaves little room to invest in new technologies that would otherwise help grow business.
- Much of this software includes legacy systems that were acquired or replaced when new applications were deployed. The value of these outdated systems decreases with every passing year, yet organizations often continue to support these applications.
- Fear of compliance and data access are the most common reasons.
- Unfortunately, the cost of doing so can consume over 50% of an overall IT budget.
The solution to this situation is to retire outdated software.
“Time and time again, I keep hearing stories from schools on how IT budgets are constantly being squeezed, but when I dig a little deeper, little or no effort is being made on accounting for software that might be on the kit we are taking away.” (Phil Goldsmith, Managing Director – ScrumpyMacs)
Define the policy for retiring software
![]() 3.2.2 Document process for software retirement
3.2.2 Document process for software retirement
Participants: IT Director, Asset Manager, Operations
Document: Document in the Standard Operating Procedures.
- Discuss and document the process for retiring software that has been deemed redundant due to changing business needs or an improvement in competitive options.
- Consider the following:
- What criteria will determine when software is suited for retirement?
- The contract should always be reviewed before making a decision to ensure proper notice is given to the vendor.
- Notice should be provided as soon as possible to ensure no additional billing arrives for renewals.
- How will software be removed from all devices? How soon must the software be replaced, if applicable?
- How long will records be archived in the ITAM database?
- Document decisions in the Standard Operating Procedures.
If you want additional support, have our analysts guide you through this phase as part of an Info-Tech Workshop 
Book a workshop with our Info-Tech analysts:
 |
|
The following are sample activities that will be conducted by Info-Tech analysts with your team:
3.1.2 |
|
Define policies for software maintenance and patches
Discuss best practices and define policies for conducting regular software maintenance and patching. |
3.2.1 |
|
Map your software license harvest and reallocation process
Build a process workflow for harvesting and reallocating unused software licenses. |
Phase 3 outline
![]() Call 1-888-670-8889 or email GuidedImplementations@InfoTech.com for more information.
Call 1-888-670-8889 or email GuidedImplementations@InfoTech.com for more information.
Complete these steps on your own, or call us to complete a guided implementation. A guided implementation is a series of 2-3 advisory calls that help you execute each phase of a project. They are included in most advisory memberships.
Guided Implementation 3: Manage, redeploy, and retire
Proposed Time to Completion (in weeks): 4
| Step 3.1: Manage and maintain software | Step 3.2: Harvest, redeploy, or retire |
Start with an analyst kick-off call:
| Review findings with analyst:
|
Then complete these activities…
| Then complete these activities…
|
With these tools & templates:
| With these tools & templates:
|
Phase 4: Build Supporting Processes & Tools
Visa used an internal SAM strategy to win the audit battle

Case Study
Industry: Financial Services
Source: SAM Summit 2014
Challenge
The overarching goal of any SAM program is compliance to prevent costly audit fines. The SAM team at Visa was made up of many individuals who were former auditors.
To deal with audit requests from vendors, “understand how auditors do things and understand their approach,” states Joe Birdsong, SAM Director at Visa.
Vendors are always on the lookout for telltale signs of a lucrative audit. For Visa, the key was to understand these processes and learn how to prepare for them.
Solution
Vendors typically look for the following when evaluating an organization for audit:
- A recent decrease in customer spend
- How easy the licensed software is to audit
- Organizational health
Ultimately, an audit is an attack on the relationship between the vendor and organization. According to Birdsong: “Maybe they haven’t really touched base with your teams and had good contact and relationship with them, and they don’t really know what’s going on in your enterprise.”
Results
By understanding the motivations behind potential audits, Visa was able to form a strategy to increase transparency with the vendor.
Regular data collection, almost real-time reporting, and open, quick communication with the vendor surrounding audits made Visa a low-risk client for vendors.
Buy-in from management is also important, and the creation of an official SAM strategy helps maintain support. Thanks to its proactive SAM program, Visa saved $200 million in just three years.
Step 4.1 Ensure compliance for audits
| Phase 4: Build supporting processes & tools | This step will walk you through the following activities: | This step involves the following participants: | |
4.1 | Compliance & audits |
|
|
4.2 | Communicate & build roadmap | ||
Step Outcomes
- An understanding of the audit process and importance of audit preparation
- A defined process for conducting regular internal audits to prepare for and defend against external audits
- A strategy and documented process for responding to external audit requests
Take a lifecycle approach to your software compliance process
Internal audits are an effective way for organizations to regularly assess their licensing position in preparation for an audit.
- Gather License Data
Use your SAM tool to run a discovery check to determine the current state of your software estate. - Improve Data Quality
Scan the data for red flags. Improve its completeness, consistency, and quality. - Identify Audit Risks
Using corrected license data, examine your reports and identify areas of risk within the organization. - Identify priority titles
Determine which titles need attention first by using the output of the license rationalization step. - Reconcile to eliminate gaps
Ensure that the correct number of licenses are deployed for each title. - Draft Vendor Response
Prepare response to vendor for when an audit has been requested.
Improve audit response maturity by leveraging technology and contract data
By improving your software asset management program’s maturity, you will drive savings for the business that go beyond the negotiating table.
Recognize the classic signs of each stage of audit response maturity to identify where your organization currently stands and where it can go.
- Optimized: Automated tools generate compliance, usage, and savings reports. Product usage reports and alerts in place to harvest and reuse licenses. Detailed savings reports provided to executive team.
- Proactive: Best practices enforced. Compliance positions are checked quarterly, and compliance reports are used to negotiate software contracts.
- Reactive: Best practices identified but unused. Manual tools still primarily in use. Compliance reports are time-consuming and often inaccurate.
- Chaotic: Purchases are ad hoc and transaction based. Minimal tracking in place, leading to time-consuming manual processes.
Implement a proactive internal audit strategy to defend against external audits
Audits – particularly those related to software – have been on the rise as vendors attempt to recapture revenue.
Being prepared for an audit is critical. Internal preparation will not only help your organization reduce the risk associated with an audit but will also improve daily operations through focusing on diligent documentation and data collection.
Conducting routine internal audits will help prepare your organization for the real deal and may even prevent the audit from happening altogether. Hundreds of thousands of dollars can be saved through a proactive audit strategy with routine documentation in place.
In addition to the fines incurred from a failed audit, numerous other negative consequences can arise:
- Multiple audits: Failing an audit makes the organization more likely to be audited again.
- Poor perception of IT: Unless non-compliance was previously disclosed to the business, IT can be deemed responsible.
- Punitive injunctions: If a settlement is not reached, vendors will apply for an injunction, inhibiting use of their software.
- Inability to justify purchases: IT can have difficulty justifying the purchase of additional resources after a failed audit.
- Disruption to business: Precious time and resources will be spent dealing with the results of the audit.
Perform routine internal compliance reports to decrease audit risk
The intent of an internal audit is to stop the battle from happening before it starts. Waiting for a knock at the door from a vendor can be stressful, and it can do harm beyond a costly fine.
- Internal audits help to ensure you’re keeping track of any software changes to keep your data and licensing up to date and avoid costly surprises if an external audit is requested.
- Identify areas where processes are breaking down and address them before there’s a potential negative impact.
- Identify control points in processes ahead of time to more easily identify access points where information should be verified.
“You want to get [the] environment to a level where you’re comfortable sharing information with [a] vendor. Inviting them in to have a chat and exposing numbers means there’s no relationship there where they’re coming to audit you. They only come to audit you when they know there’s a gain to be had, otherwise what’s the point of auditing?
I want customers to get comfortable with licensing and what they’re spending, and then there’s no problem exposing that to vendors. Vendors actually appreciate that.” (Ben Brand, SAM Practice Manager, Insight)
Info-Tech Insight
“The supreme art of war is to subdue the enemy without fighting.” – Sun Tzu
Performing routine checks on your license compliance will drastically reduce the risk that your organization gets hit with a costly fine. Maintaining transparency and demonstrating compliance will fend off audit-hungry vendors.
Define and document the internal audit process
![]() 4.1.1 Document process and procedures for internal audits
4.1.1 Document process and procedures for internal audits
Participants: CIO and/or IT Director, Asset Manager, IT Managers
Document: Document in the Standard Operating Procedures.
Define and document a process for conducting internal software audits.
Include the following:
- How often will audits be completed for each software published?
- When will audits be conducted?
- Who will conduct the audit? Who will be consulted?
- What will be included in the scope of the audit?
Example:
- Annual audits will be completed for each software publisher, scheduled as part of the license or maintenance agreement renewals.
- Where annual purchases are not required, vendor audits for compliance will be conducted annually, with a date predetermined based on minimizing scheduling conflicts with larger audits.
- Audit will be completed with input from product managers.
- Audit will include:
- Software compliance review: Licenses owned compared to product installed.
- Version review: Determine if installed versions match company standards. If there is a need for upgrades, does the license permit upgrading?
- Maintenance review: Does the maintenance match requirements for the next year’s plans and licenses in use?
- Support review: Is the support contract appropriate for use?
- Budget: Has budget been allocated; is there an adjustment required due to increases?
Identify organizational warning signs to decrease audit risk
Being prepared for an audit is critical. Internal preparation will not only help your organization reduce the risk associated with an audit but will also improve daily operations through focusing on diligent documentation and data collection.
Certain triggers exist that indicate a higher risk of an audit occurring. It is important to recognize these warning signs so you can prepare accordingly.
Health of organization
If your organization is putting out fires and a vendor can sense it, they’ll see an audit as a highly lucrative exercise.
Decrease in customer spend
A decrease in spend means that an organization has a high chance of being under-licensed.
License complexity
The more complex the license, the harder it is to remain in compliance. Some vendors are infamous for their complex licensing agreements.
Audit Strategy
- Audits should neither be feared nor embraced.
- An audit is an attack on your relationship with your vendor; your vendor needs to defend its best interests, but it would also rather maintain a satisfied relationship with its client.
- A proactive approach to audits through routine reporting and transparency with vendors will alleviate all fear surrounding the audit process. It provides your vendor with compliance assurance and communicates that an audit won’t net the vendor enough revenue to justify the effort.
Focus on three key tactics for success before responding to an audit
Taking these due diligence steps will pay dividends downstream, reducing the risk of negative results such as release of confidential information.
Form an Audit Team
- Once an audit letter is received from a vendor or third party, a virtual team needs to be formed.
- The team should be cross-functional, representing various core areas of the business.
- Don’t forget legal counsel: they will assist in the review of audit provision(s) to determine your contractual rights and obligations with respect to the audit.
Sign an NDA
- An NDA should be signed by all parties, the organization, the vendor, and the auditor.
- Don’t wait on a vendor to provide its NDA. The organization should have its own and provide it to both parties.
- If the auditor is a third party, negotiate a three-way NDA. This will prevent data being shared with other third parties.
Examine Contract History
- Vendors will attempt to alter terms of contracts when new products are purchased.
- Maintain your current agreement if they are more favorable by “grandfathering” your original agreement.
- Oracle master level agreements are an example: master level agreements offer more favorable terms than more recent versions.
Info-Tech Insight
Even if you cannot get a third-party NDA signed, the negotiation process should delay the overall audit process by at least a month, buying your organization valuable time to gather license data.
Be prepared for external audit requests with a defined process for responding
- Vendor-initiated audit request received and brought to attention of IT Asset Manager and CIO.
- Acknowledge receipt of audit notice.
- Negotiate timing and scope of the audit (including software titles, geographic locations, entities, and completion date).
- Notify staff not to remove or acquire licenses for software under audit.
- Gather documentation and create report of all licensed software within audit scope.
- Include original contract, most recent contract, and any addendums, purchase receipts, or reseller invoices, and publisher documentation such as manuals or electronic media.
- Compare documentation to installed software according to ITAM database.
- Validate any unusual or non-compliant software.
- Complete documentation requested by auditor and review results.
Define and document the external audit process
![]() 4.1.2 Define external audit process
4.1.2 Define external audit process
Participants: CIO and/or IT Director, Asset Manager, IT Managers
Document: Document in the Standard Operating Procedures.
Define and document a process for responding to external software audit requests.
Include the following:
- Who must be notified of the audit request when it is received?
- When must acknowledgement of the notice be sent and by whom?
- What must be defined under the scope of the audit (e.g. software titles, geographic locations, entities, completion date)?
- What communications must be sent to IT staff and end users to ensure compliance?
- What documentation should be gathered to review?
- How will documentation be verified against data?
- How will unusual or non-compliant software be identified and validated?
- Who needs to be informed of the results?
Control audit scope with an audit response template
Use the Software Audit Scoping Email Template to create an email directed at your external (or internal) auditors. Send the audit scoping email several weeks before an audit to determine the audit’s scope and objectives. The email should include:
- Detailed questions about audit scope and objectives.
- Critical background information on your organization/program.
The email will help focus your preparation efforts and initiate your relationship with the auditors.
Control scope by addressing the following:
- Products covered by a properly executed agreement
- Geographic regions
- User groups
- Time periods
- Specific locations
- A subset of users’ computers
Keep leadership informed with an audit launch email
Approximately a week before the audit, you should email the internal leadership to communicate information about the start of the audit. Use the Software Audit Launch Email Template to create this email, including:
- Staffing
- Functional requirements
- Audit contact person information
- Scheduling details
- Audit report estimated delivery time
For more guidance on preparing for a software audit, see Info-Tech’s blueprint: Prepare and Defend Against a Software Audit.
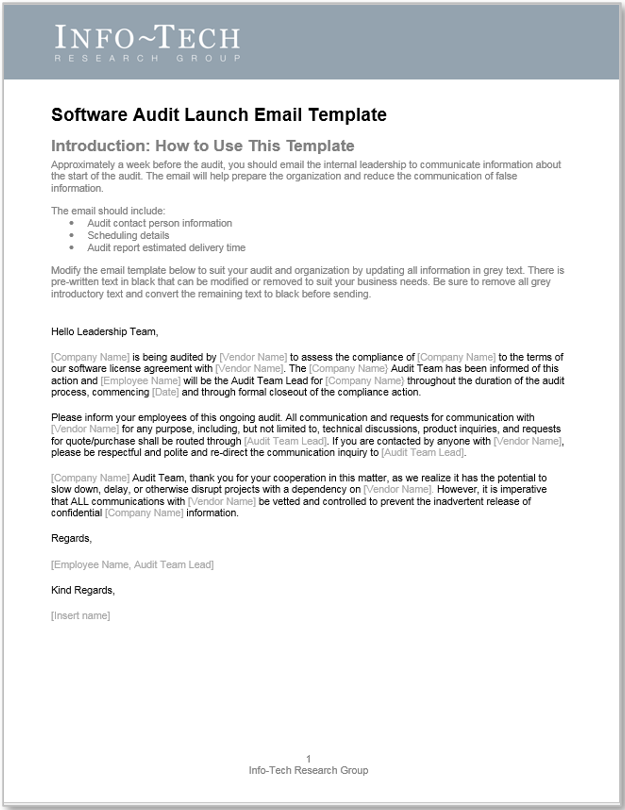
A large bank employed proactive, internal audits to experience big savings
Case Study
Industry: Banking
Source: Pomeroy
Challenge
A large American financial institution with 1,300 banking centers in 12 states, 28,000 end users, and 108,000 assets needed to improve its asset management program.
The bank had employed numerous ITAM tools, but IT staff identified that its asset data was still fragmented. There was still incomplete insight into what assets the banked owned, the precise value of those assets, their location, and what they’re being used for.
The bank decided to establish an asset management program that involved internal audits to gather more-complete data sets.
Solution
With the help of a vendor, the bank implemented cradle-to-grave asset tracking and lifecycle management, which provided discovery of almost $80 million in assets.
The bank also assembled an ITAM team and a dedicated ITAM manager to ensure that routine internal audits were performed.
The team was instrumental in establishing standardization of IT policies, hardware configuration, and service requirements.
Results
- The bank identified and now tracks over 108,000 assets.
- The previous level of 80% accuracy in inventory tracking was raised to 96%.
- Nearly $500,000 was saved through asset recovery and repurposing of 600 idle assets.
- There are hundreds of thousands of dollars in estimated savings as the result of avoiding costly penalties from failed audits thanks to proactive internal audits.
Step 4.2 Build communication plan and roadmap
| Phase 4: Build supporting processes & tools | This step will walk you through the following activities: | This step involves the following participants: | |
4.1 | Compliance & audits |
|
|
4.2 | Communicate & build roadmap | ||
Step Outcomes
- A documented communications plan for relevant stakeholders to understand the benefits and changes the SAM program will bring
- A list of anticipated end-user questions with responses
- Documented software asset management policies
- An implementation roadmap
Communicate SAM processes to gain acceptance and support
Communication is crucial to the integration and overall implementation of your SAM program. If staff and users do not understand the purpose of processes and policies, they will fail to provide the desired value.
An effective communication plan will:
- Gain support from management at the project proposal phase.
- Create end-user buy-in once the program is set to launch.
- Maintain the presence of the program throughout the business.
- Instill ownership throughout the business from top-level management to new hires.
Communicate the following:
-
Advertise successes
- Regularly demonstrate the value of the SAM program with descriptive statistics focused on key financial benefits.
- Share data with the appropriate personnel; promote success to obtain further support from senior management.
-
Report and share asset data
- Sharing detailed asset-related reports frequently gives decision makers useful data to aid in their strategy.
- These reports can help your organization prepare for audits, adjust budgeting, and detect unauthorized software.
-
Communicate the value of SAM
- Educate management and end users about how they fit into the bigger picture.
- Individuals need to know which behaviors may put the organization at risk or adversely affect data quality.
Educate staff and end users through SAM training to increase program success
As part of your communication plan and overall SAM implementation, training should be provided to both staff and end users within the organization.
- ITAM solutions are complex by nature with both business process and technical knowledge required to use them correctly.
- All facets of the business, from management to new hires, should be provided with training to help them understand their role in the program’s success.
- Keep the message appropriate to the audience – end users don’t need to know the complete process, but will need to know policy and how to request.
- Even after the SAM program has been fully implemented, keep employees up to date with policies and processes through ongoing training sessions for both new hires and existing employees:
- New hires: Provide new hires with all relevant SAM policies and ensure they understand the importance of software asset management.
- Existing employees: Continually remind them of how SAM is involved in their daily operations and inform them of any changes to policies.
Create your communications plan to anticipate challenges, remove obstacles, and ensure buy-in
Provide separate communications to key stakeholder groups
Why:
|
|
When:
|
Develop a communication plan to convey the right messages
Participants: CIO, IT Director, Asset Manager, Service Desk Manager
Document: Document in the SAM Communication Plan.
- Identify the groups that will be affected by the SAM program.
- For each group requiring a communication plan, identify the following:
- Benefits of SAM for that group of individuals (e.g. more efficient software requests).
- The impact the change will have on them (e.g. change in the way a certain process will work).
- Communication method (i.e. how you will communicate).
- Timeframe (i.e. when and how often you will communicate the changes).
- Complete this information in a table like the one below and document in the Communication Plan.
| Group | Benefits | Impact | Method | Timeline |
|---|---|---|---|---|
| Executives |
|
|
||
| End Users |
|
|
||
| IT |
|
|
Anticipate end-user questions by preparing an FAQ list
Document: Document FAQ questions and answers in the SAM FAQ Template.
ITAM imposes changes to end users throughout the business and it’s normal to expect questions about the new program. Prepare your team ahead of time by creating a list of FAQs.
Some common questions include:
- Why are you changing from the old processes?
- Why now?
- What are you going to ask me to do differently?
- Will I lose any of my software?
The benefits of preparing a list of answers to FAQs include:
- A reduction in time spent creating answers to questions. If you focus on the most common questions, you will make efficient use of your team’s time.
- Consistency in your team’s responses. By socializing the answers to FAQs, you ensure that no one on your team is out of the loop and the message remains consistent across the board.
Include policy design and enforcement in your communication plan
- Software asset management policies should define the actions to be taken to support software asset management processes and ensure the effective and efficient management of IT software assets across the asset lifecycle.
- Implementing asset management policies enforces the notion that the organization takes its IT assets and the management of them seriously and will help ensure the benefits of SAM are achieved.
- Designing, approving, documenting, and adopting one set of standard SAM policies for each department to follow will ensure the processes are enforced equally across the organization.
Info-Tech Insight
Use policy templates to jumpstart your policy development and ensure policies are comprehensive, but be sure to modify and adapt policies to suit your corporate culture or they will not gain buy-in from employees. For a policy to be successful, it must be a living document and have participation and involvement from the committees and departments to whom it will pertain.
Build a software asset management policy
Use Info-Tech’s Software Asset Management Policy template to define and document the purpose, scope, objectives, and roles and responsibilities for your organization's software asset management program.
The template allows you to customize policy requirements for:
- Procurement
- Installation and Removal
- Maintenance
- Mergers and Acquisitions
- Company Divestitures
- Audits
…as well as consequences for non-compliance.

Use Info-Tech’s policy templates to build additional policies
|
Asset Security Policy
End-User Devices Acceptable Use Policy
Purchasing Policy
Release Management Policy
Internet Acceptable Use Policy
|
|
Implement SAM in a phased, constructive approach
One of the most difficult decisions to make when implementing a SAM program is: “where do we start?”
It’s not necessary to deploy a comprehensive SAM program to start. Build on the essentials to become more mature as you grow.
SAM Program Maturity (highest to lowest)
- Audits and reporting
Gather and analyze data about software assets to ensure compliance for audits and to continually improve the business. - Contracts and budget
Analyze contracts and licenses for software across the enterprise and optimize planning to enable cost reduction. - Lifecycle standardization
Define standards and processes for all asset lifecycle phases from request and procurement through to retirement and redistribution. - Inventory and tracking
Define assets you will procure, distribute, and track. Know what you have, where it is deployed, and keep track of contracts and all relevant data.
Integrate your SAM program with the organization to assist its implementation
SAM cannot perform on its own – it must be integrated with other functional areas of the organization to maintain its stability and support.
- Effective SAM is supported by a comprehensive set of processes as part of its implementation.
- For example, integration with the procurement team’s processes and tools is required to track software purchases to mitigate software license compliance risk.
- Integration with Finance is required to support internal cost allocations and chargebacks.
- Integration with the service desk is required to track and deploy software requests.
Info-Tech Best Practice
To integrate SAM effectively, a clear implementation roadmap needs to be designed. Prioritize “quick wins” to demonstrate success to the business early and to gain buy-in from your team. Short-term gains should be designed to support long-term goals of your SAM program.
Sample short-term goals
- Identify inventory classification and tool
- Create basic SAM policies and processes
- Implement SAM auto-discovery tools
Sample long-term goals
- Software contract data integration
- Continual improvement through review and revision
- Software compliance reports, internal audits
Develop a SAM roadmap to plan your implementation
- Identify and review all initiatives that will be taken to implement or improve the software asset management program. These may fall under people, process, or technology-related tasks.
- Assign a priority level to each task (Quick Win, Low, Medium, High).
- Use the priority to sort tasks into start dates, breaking down by:
- Short, medium, or long-term
- 1 month, 3 months, 6 months, 12+ months
- Q1, Q2, Q3, Q4
- Review tasks and adjust start dates for some, if needed to set realistic and achievable timelines.
- Transfer tasks to a project plan or Gantt chart to formalize.
| Q1 | Q2 | Q3 | Q4 |
|
|
|
|
Review and maintain the SAM program to reach optimal maturity
- SAM is a dynamic process. It must adapt to keep pace with the direction of the organization. New applications, different licensing needs, and a constant stream of new end users all contribute to complicating the licensing process.
- As part of your organization’s journey to an optimized SAM program, put in place continual improvement practices to maintain momentum.
Info-Tech Insight
Advertising the increased revenue that is gained from good SAM practices is a powerful way to gain project buy-in.
Keep the momentum going:
- Clearly define ongoing responsibilities for each role.
- Develop a training and awareness program for new employees to be introduced to SAM processes and policies.
- Continually review and revise existing processes as necessary.
- Measure the success of the program to identify areas for improvement and demonstrate successes.
- Measure adherence to process and policies and enforce as needed.
Reflect on the outcomes of implementing SAM to target areas for improvement and share knowledge gained within and beyond the SAM team. Some questions to consider include:
- How did the data compare to our expectations? Was the project a success?
- What obstacles were present that impacted the project?
- How can we apply lessons learned through this project to others in the future?
If you want additional support, have our analysts guide you through this phase as part of an Info-Tech Workshop 
Book a workshop with our Info-Tech analysts:

|
|
The following are sample activities that will be conducted by Info-Tech analysts with your team:
4.2.1 |
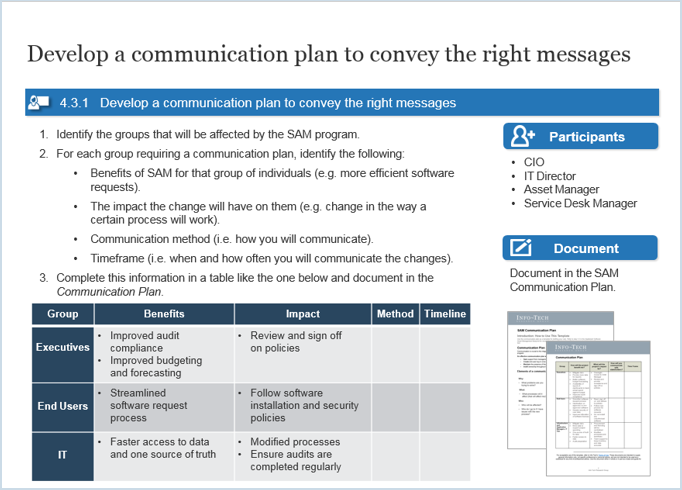
|
Develop a communication plan to convey the right messages
Identify stakeholders requiring communication and formulate a message and delivery method for each. |
4.2.5 |
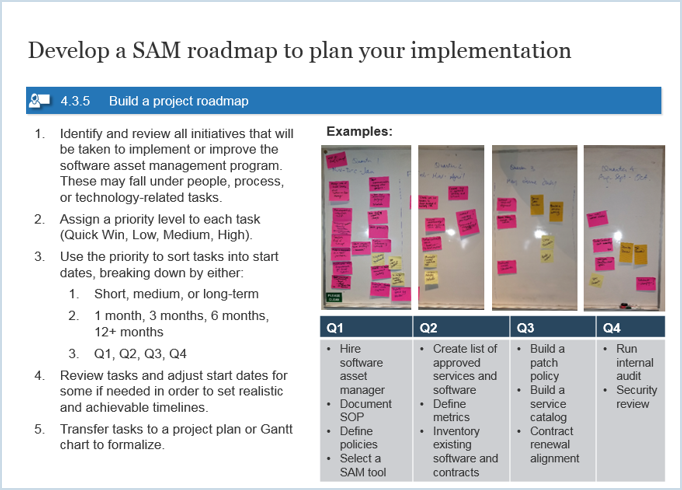
|
Develop a SAM roadmap to plan your implementation
Outline the tasks necessary for the implementation of this project and prioritize to build a project roadmap. |
Phase 4 outline
![]() Call 1-888-670-8889 or email GuidedImplementations@InfoTech.com for more information.
Call 1-888-670-8889 or email GuidedImplementations@InfoTech.com for more information.
Complete these steps on your own, or call us to complete a guided implementation. A guided implementation is a series of 2-3 advisory calls that help you execute each phase of a project. They are included in most advisory memberships.
Guided Implementation 4: Build supporting processes & tools
Proposed Time to Completion (in weeks): 4
| Step 4.1: Compliance & audits | Step 4.2: Communicate & build roadmap |
Start with an analyst kick-off call:
|
Review findings with analyst:
|
Then complete these activities…
|
Then complete these activities…
|
With these tools & templates:
|
With these tools & templates:
|
Related Info-Tech research
Implement Hardware Asset Management
Prepare and Defend Against a Software Audit
IT Asset Management (ITAM) Market Overview
Master Contract Review and Negotiation for Software Agreements
Bibliography
2013 Software Audit Industry Report.” Express Metrix, 2013. Web.
7 Vital Trends Disrupting Today’s Workplace: Results and Data from 2013 TINYpulse Employee Engagement Survey.” TINYpulse, 2013. Web.
Beaupoil, Christof. “How to measure data quality and protect against software audits.” Network World, 6 June 2011.
Begg, Daniel. “Effective Licence Position (ELP) – What is it really worth?” LinkedIn, 19 January 2016.
Boehler, Bernhard. “Advanced License Optimization: Go Beyond Compliance for Maximum Cost Savings.” The ITAM Review, 24 November 2014.
Bruce, Warren. “SAM Baseline – process & best practice.” Microsoft. 2013 Australia Partner Conference.
Case Study Top 20 U.S. Bank Tackles Asset Management.” Pomeroy, 2012. Web.
Cherwell Software Software Audit Industry Report.” Cherwell Software, 2015. Web.
Conrad, Sandi. “SAM starter kit: everything you need to get started with software asset management. Conrad & Associates, 2010.
Corstens, Jan, and Diederik Van der Sijpe. “Contract risk & compliance software asset management (SAM).” Deloitte, 2012.
Deas, A., T. Markowitzm and E. Black. “Software asset management: high risk, high reward.” Deloitte, 2014.
Doig, Chris. “Why you should always estimate ROI before buying enterprise software” CIO, 13 August 2015.
Fried, Chuck. “America Needs An Education On Software Asset Management (SAM).” LinkedIn. 16 June 2015.
Lyons, Gwen. “Understanding the Drivers Behind Application Rationalization Critical to Success.” Flexera Software Blog, 31 October 2012.
Bibliography
Metrics to Measure SAM Success: eight ways to prove your SAM program is delivering business benefits.” Snow Software White Paper, 2015.
Microsoft. “The SAM Optimization Model.” Microsoft Corporation White Paper, 2010.
Miller, D. and M. Oliver. “Engaging Stakeholders for Project Success.” Project Management Institute White Paper, 2015.
Morrison, Dan. “5 Common Misconceptions of Software Asset Management.” SoftwareOne. 12 May 2015.
O’Neill, Leslie T. “Visa Case Study: SAM in the 21st Century.” International Business Software Managers Association (IBSMA), 30 July 2014.
Reducing Hidden Operating Costs Through IT Asset Discovery.” NetSupport Inc., 2011.
SAM Summit 2014, 23-25 June 2014, University of Chicago Gleacher Center Conference Facilities, Chicago, MI.
Saxby, Heather. “20 Things Every CIO Needs to Know about Software Asset Management.” Crayon Software Experts, 13 May 2015.
The 2016 State of IT: Managing the money monsters for the coming year.” Spiceworks, 2016.
The Hidden Cost of Unused Software.” A 1E Report, 1E.com: 2014. Web.
What does it take to achieve software license optimization?” Flexera White Paper, 2013.
Research contributors and experts

|
Michael Dean
Director, User Support Services Des Moines University |
Simon Leuty
Co-Founder Livingstone Tech |

|

|
Clare Walsh
PR Consultant Adesso Tech Ltd. |
Alex Monaghan
Director, Presales EMEA Product Support Solutions |

|
Research contributors and experts

|
Ben Brand
SAM Practice Manager Insight |
Michael Swanson
President ISAM |

|

|
Bruce Aboudara
SVP, Marketing & Business Development Scalable Software |
Will Degener
Senior Solutions Consultant Scalable Software |

|
Research contributors and experts

|
Peter Gregorowicz
Associate Director, Network & Client Services Vancouver Community College |
Peter Schnitzler
Operations Team Lead Toyota Canada |

|

|
David Maughan
Head of Service Transition Mott MacDonald Ltd. |
Brian Bernard
Infrastructure & Operations Manager Lee County Clerk of Court |

|
Research contributors and experts

|
Leticia Sobrado
IT Data Governance & Compliance Manager Intercept Pharmaceuticals |
Buying Options
Implement Software Asset Management
Client rating
Cost Savings
Days Saved
IT Risk Management · IT Leadership & Strategy implementation · Operational Management · Service Delivery · Organizational Management · Process Improvements · ITIL, CORM, Agile · Cost Control · Business Process Analysis · Technology Development · Project Implementation · International Coordination · In & Outsourcing · Customer Care · Multilingual: Dutch, English, French, German, Japanese · Entrepreneur
Tymans Group is a brand by Gert Taeymans BV
Gert Taeymans bv
Europe: Koning Albertstraat 136, 2070 Burcht, Belgium — VAT No: BE0685.974.694 — phone: +32 (0) 468.142.754
USA: 4023 KENNETT PIKE, SUITE 751, GREENVILLE, DE 19807 — Phone: 1-917-473-8669
Copyright 2017-2022 Gert Taeymans BV