Implement Hardware Asset Management

- Executives are often aware of the benefits asset management offers, but many organizations lack a defined program to manage their hardware.
- Efforts to implement hardware asset management (HAM) are stalled because organizations feel overwhelmed navigating the process or under use the data, failing to deliver value.
Our Advice
Critical Insight
- Organizations often implement an asset management program as a one-off project and let it stagnate.
- Organizations often fail to dedicate adequate resources to the HAM process, leading to unfinished processes and inconsistent standards.
- Hardware asset management programs yield a large amount of useful data. Unfortunately, this data is often underutilized. Departments within IT become data siloes, preventing effective use of the data.
Impact and Result
- As the IT environment continues to change, it is important to establish consistency in the standards around IT asset management.
- A current state assessment of your HAM program will shed light on the steps needed to safeguard your processes.
- Define the assets that will need to be managed to inform the scope of the ITAM program before defining processes.
- Build and involve an ITAM team in the process from the beginning to help embed the change.
- Define standard policies, processes, and procedures for each stage of the hardware asset lifecycle, from procurement through to disposal.
Implement Hardware Asset Management Research & Tools
Start here – read the Executive Brief
Read our concise Executive Brief to find out why you should Implement Hardware Asset Management, review Info-Tech’s methodology, and understand the four ways we can support you in completing this project.Besides the small introduction, subscribers and consulting clients within this management domain have access to:
- Implement Hardware Asset Management – Phases 1-4
1. Lay foundations
Build the foundations for the program to succeed.
- Implement Hardware Asset Management – Phase 1: Lay Foundations
- HAM Standard Operating Procedures
- HAM Maturity Assessment Tool
- IT Asset Manager
- IT Asset Administrator
2. Procure & receive
Define processes for requesting, procuring, receiving, and deploying hardware.
- Implement Hardware Asset Management – Phase 2: Procure and Receive
- HAM Process Workflows (Visio)
- HAM Process Workflows (PDF)
- Non-Standard Hardware Request Form
- Purchasing Policy
3. Maintain & dispose
Define processes and policies for managing, securing, and maintaining assets then disposing or redeploying them.
- Implement Hardware Asset Management – Phase 3: Maintain and Dispose
- Asset Security Policy
- Hardware Asset Disposition Policy
4. Plan implementation
Plan the hardware budget, then build a communication plan and roadmap to implement the project.
- Implement Hardware Asset Management – Phase 4: Plan Implementation
- HAM Budgeting Tool
- HAM Communication Plan
- HAM Implementation Roadmap
Workshop: Implement Hardware Asset Management
Workshops offer an easy way to accelerate your project. If you are unable to do the project yourself, and a Guided Implementation isn't enough, we offer low-cost delivery of our project workshops. We take you through every phase of your project and ensure that you have a roadmap in place to complete your project successfully.
1 Lay Foundations
The Purpose
Build the foundations for the program to succeed.
Key Benefits Achieved
Evaluation of current challenges and maturity level
Defined scope for HAM program
Defined roles and responsibilities
Identified metrics and reporting requirements
Activities
1.1 Outline hardware asset management challenges.
1.2 Conduct HAM maturity assessment.
1.3 Classify hardware assets to define scope of the program.
1.4 Define responsibilities.
1.5 Use a RACI chart to determine roles.
1.6 Identify HAM metrics and reporting requirements.
Outputs
HAM Maturity Assessment
Classified hardware assets
Job description templates
RACI Chart
2 Procure & Receive
The Purpose
Define processes for requesting, procuring, receiving, and deploying hardware.
Key Benefits Achieved
Defined standard and non-standard requests for hardware
Documented procurement, receiving, and deployment processes
Standardized asset tagging method
Activities
2.1 Identify IT asset procurement challenges.
2.2 Define standard hardware requests.
2.3 Document standard hardware request procedure.
2.4 Build a non-standard hardware request form.
2.5 Make lease vs. buy decisions for hardware assets.
2.6 Document procurement workflow.
2.7 Select appropriate asset tagging method.
2.8 Design workflow for receiving and inventorying equipment.
2.9 Document the deployment workflow(s).
Outputs
Non-standard hardware request form
Procurement workflow
Receiving and tagging workflow
Deployment workflow
3 Maintain & Dispose
The Purpose
Define processes and policies for managing, securing, and maintaining assets then disposing or redeploying them.
Key Benefits Achieved
Policies and processes for hardware maintenance and asset security
Documented workflows for hardware disposal and recovery/redeployment
Activities
3.1 Build a MAC policy, request form, and workflow.
3.2 Design process and policies for hardware maintenance, warranty, and support documentation handling.
3.3 Revise or create an asset security policy.
3.4 Identify challenges with IT asset recovery and disposal and design hardware asset recovery and disposal workflows.
Outputs
User move workflow
Asset security policy
Asset disposition policy, recovery and disposal workflows
4 Plan Implementation
The Purpose
Select tools, plan the hardware budget, then build a communication plan and roadmap to implement the project.
Key Benefits Achieved
Shortlist of ITAM tools
Hardware asset budget plan
Communication plan and HAM implementation roadmap
Activities
4.1 Generate a shortlist of ITAM tools that will meet requirements.
4.2 Use Info-Tech’s HAM Budgeting Tool to plan your hardware asset budget.
4.3 Build HAM policies.
4.4 Develop a communication plan.
4.5 Develop a HAM implementation roadmap.
Outputs
HAM budget
Additional HAM policies
HAM communication plan
HAM roadmap tool
Further reading
Implement Hardware Asset Management
Build IT services value on the foundation of a proactive asset management program.
ANALYST PERSPECTIVE
IT asset data impacts the entire organization. It’s time to harness that potential.
"Asset management is like exercise: everyone is aware of the benefits, but many struggle to get started because the process seems daunting. Others fail to recognize the integrative potential that asset management offers once an effective program has been implemented.
A proper hardware asset management (HAM) program will allow your organization to cut spending, eliminate wasteful hardware, and improve your organizational security. More data will lead to better business decision-making across the organization.
As your program matures and your data gathering and utility improves, other areas of your organization will experience similar improvements. The true value of asset management comes from improved IT services built upon the foundation of a proactive asset management program." - Sandi Conrad, Practice Lead, Infrastructure & Operations Info-Tech Research Group
Our understanding of the problem
This Research Is Designed For:
- Asset Managers and Service Delivery Managers tasked with developing an asset management program who need a quick start.
- CIOs and CFOs who want to reduce or improve budgeting of hardware lifecycle costs.
- Information Security Officers who need to mitigate the risk of sensitive data loss due to insecure assets.
This Research Will Help You:
- Develop a hardware asset management (HAM) standard operating procedure (SOP) that documents:
- Process roles and responsibilities.
- Data classification scheme.
- Procurement standards, processes, and workflows for hardware assets.
- Hardware deployment policies, processes, and workflows.
- Processes and workflows for hardware asset security and disposal.
- Identify requirements for an IT asset management (ITAM) solution to help generate a shortlist.
- Develop a hardware asset management implementation roadmap.
- Draft a communication plan for the initiative.
Executive summary
Situation
- Executives are aware of the numerous benefits asset management offers, but many organizations lack a defined ITAM program and especially a HAM program.
- Efforts to implement HAM are stalled because organizations cannot establish and maintain defined processes and policies.
Complication
- Organizations often implement an asset management program as a one- off project and let it stagnate, but asset management needs to be a dynamic, continually involving process to succeed.
- Organizations often fail to dedicate adequate resources to the HAM process, leading to unfinished processes and inconsistent standards.
- Hardware asset management programs yield a large amount of useful data. Unfortunately, this data is often underused. Departments within IT become data siloes, preventing effective use of the data.
Resolution
- As the IT environment continues to change, it is important to establish consistency in the standards around IT asset management.
- A current state assessment of your HAM program will shed light on the steps needed to safeguard your processes.
- Define the assets that will need to be managed to inform the scope of the ITAM program before defining processes.
- Build and involve an ITAM team in the process from the beginning to help embed the change.
- Define standard policies, processes, and procedures for each stage of the hardware asset lifecycle, from procurement through to disposal.
- Pace yourself; a staged implementation will make your ITAM program a success.
Info-Tech Insight
- HAM is more than just tracking inventory. A mature asset management program provides data for proactive planning and decision making to reduce operating costs and mitigate risk.
- ITAM is not just IT. IT leaders need to collaborate with Finance, Procurement, Security, and other business units to make informed decisions and create value across the enterprise.
- Treat HAM like a process, not a project. HAM is a dynamic process that must react and adapt to the needs of the business.
Implement HAM to reduce and manage costs, gain efficiencies, and ensure regulatory compliance
Save & Manage Money
- Companies with effective HAM practices achieve cost savings through redeployment, reduction of lost or stolen equipment, power management, and on-time lease returns.
- The right HAM system will enable more accurate planning and budgeting by business units.
Improve Contract Management
- Real-time asset tracking to vendor terms and conditions allows for more effective negotiation.
Inform Technology Refresh
- HAM provides accurate information on hardware capacity and compatibility to inform upgrade and capacity planning
Gain Service Efficiencies
- Integrating the hardware lifecycle with the service desk will enable efficiencies through Install/Moves/Adds/Changes (IMAC) processes, for larger organizations.
Meet Regulatory Requirements
- You can’t secure organizational assets if you don’t know where they are! Meet governance and privacy laws by knowing asset location and that data is secure.
Prevent Risk
- Ensure data is properly destroyed through disposal processes, track lost and stolen hardware, and monitor hardware to quickly identify and isolate vulnerabilities.
HAM is more than just inventory; 92% of organizations say that it helps them provide better customer support
Hardware asset management (HAM) provides a framework for managing equipment throughout its entire lifecycle. HAM is more than just keeping an inventory; it focuses on knowing where the product is, what costs are associated with it, and how to ensure auditable disposition according to best options and local environmental laws.
Implementing a HAM practice enables integration of data and enhancement of many other IT services such as financial reporting, service management, green IT, and data and asset security.
Cost savings and efficiency gains will vary based on the organization’s starting state and what measures are implemented, but most organizations who implement HAM benefit from it. As organizations increase in size, they will find the greatest gains operationally by becoming more efficient at handling assets and identifying costs associated with them.
A 2015 survey by HDI of 342 technical support professionals found that 92% say that HAM has helped their teams provide better support to customers on hardware-related issues. Seventy-seven percent have improved customer satisfaction through managing hardware assets. (HDI, 2015)
HAM delivers cost savings beyond only the procurementstage
HAM cost savings aren’t necessarily realized through the procurement process or reduced purchase price of assets, but rather through the cost of managing the assets.
HAM delivers cost savings in several ways:
- Use a discovery tool to identify assets that may be retired, redeployed, or reused to cut or reallocate their costs.
- Enforce power management policies to reduce energy consumption as well as costs associated with wasted energy.
- Enforce policies to lock down unauthorized devices and ensure that confidential information isn’t lost (and you don’t have to waste money recovering lost data).
- Know the location of all your assets and which are connected to the network to ensure patches are up to date and avoid costly security risks and unplanned downtime.
- Scan assets to identify and remediate vulnerabilities that can cause expensive security attacks.
- Improve vendor and contract management to identify areas of hardware savings.
The ROI for HAM is significant and measurable
| Benefit | Calculation | Sample Annual Savings |
|---|---|---|
|
Reduced help desk support
|
# of hardware-related support tickets per year * cost per ticket * % reduction in average call length | 2,000 * $40 * 20% = $16,000 |
|
Greater inventory efficiency
|
Hours required to complete inventory * staff required * hourly pay rate for staff * number of times a year inventory required | 8 hours * 5 staff * $33 per hour * 2 times a year = $2,640 |
|
Improved employee productivity
|
# of employees * percentage of employees who encounter productivity loss through unauthorized software * number of hours per year spent using unauthorized software * average hourly pay rate | 500 employees * 10% * 156 hours * $18 = $140,400 |
|
Improved security
|
# of devices lost or stolen last year * average replacement value of device + # of devices stolen * value of data lost from device | (50 * $1,000) + (50 * $5,000) = $300,000 |
| Total Savings: | $459,040 | |
- Weigh the return against the annual cost of investing in an ITAM solution to calculate the ROI.
- Don’t forget about the intangible benefits that are more difficult to quantify but still significant, such as increased visibility into hardware, more accurate IT planning and budgeting, improved service delivery, and streamlined operations.
Avoid these common barriers to ITAM success
Organizations that struggle to implement ITAM successfully usually fall victim to these barriers:
Organizational resistance to change
Senior-level sponsorship, engagement, and communication is necessary to achieve the desired outcomes of ITAM; without it, ITAM implementations stall and fail or lack the necessary resources to deliver the value.
Lack of dedicated resources
ITAM often becomes an added responsibility for resources who already have other full-time responsibilities, which can quickly cause the program to lose focus. Increase the chance of success through dedicated resources.
Focus on tool over process
Many organizations buy a tool thinking it will do most of the work for them, but without supporting processes to define ITAM, the data within the tool can become unreliable.
Choosing a tool or process that doesn’t scale
Some organizations are able to track assets through manual discovery, but as their network and user base grows, this quickly becomes impossible. Choose a tool and build processes that will support the organization as it grows.
Using data only to respond to an audit without understanding root causes
Often, organizations implement ITAM only to the extent necessary to achieve compliance for audits, but without investigating the underlying causes of non-compliance and thus not solving the real problems.
To help you make quick progress, Info-Tech Research Group parses hardware asset management into essential processes
Focus on hardware asset lifecycle management essentials:
IT Asset Procurement:
- Define procurement standards for new hardware along with related warranties and support options.
- Develop processes and workflows for purchasing and work out financial implications to inform budgeting later.
IT Asset Intake and Deployment:
- Define policies, processes, and workflows for hardware and receiving, inventory, and tracking practices.
- Develop processes and workflows for managing imaging, change and moves, and large-scale rollouts.
IT Asset Security and Maintenance:
- Develop processes, policies, and workflows for asset tracking and security.
- Maintain contracts and agreements.
IT Asset Disposal or Recovery:
- Manage the employee termination and equipment recovery cycle.
- Securely wipe and dispose of assets that have reached retirement stage.
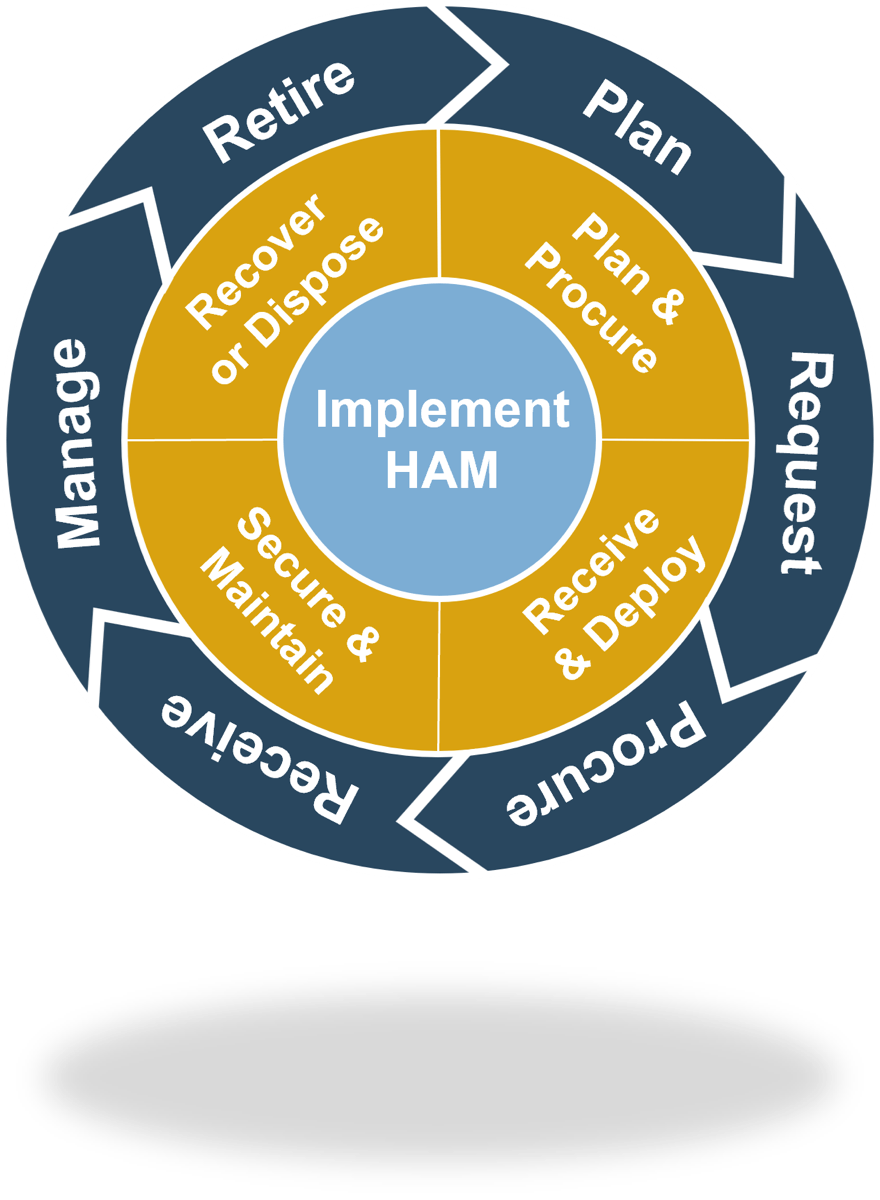
Follow Info-Tech’s methodology to build a plan to implement hardware asset management
| Phase 1: Assess & Plan | Phase 2: Procure & Receive | Phase 3: Maintain & Dispose | Phase 4: Plan Budget & Build Roadmap |
| 1.1 Assess current state & plan scope | 2.1 Request & procure | 3.1 Manage & maintain | 4.1 Plan budget |
| 1.2 Build team & define metrics | 2.2 Receive & deploy | 3.2 Redeploy or dispose | 4.2 Communicate & build roadmap |
| HAM Maturity Assessment | Procurement workflow | User move workflow | HAM Budgeting Tool |
| Classified hardware assets | Non-standard hardware request form | Asset security policy | HAM Communication Plan |
| RACI Chart | Receiving & tagging workflow | Asset disposition policy | HAM Roadmap Tool |
| Job Descriptions | Deployment workflow | Asset recovery & disposal workflows | Additional HAM policies |
Asset management is a key piece of Info-Tech's COBIT- inspired IT Management and Governance Framework
Cisco IT reduced costs by upwards of $50 million through implementing ITAM
CASE STUDY
Industry IT
Source Cisco Systems, Inc.
Cisco Systems, Inc.
Cisco Systems, Inc. is the largest networking company in the world. Headquartered in San Jose, California, the company employees over 70,000 people.
Asset Management
As is typical with technology companies, Cisco boasted a proactive work environment that encouraged individualism amongst employees. Unfortunately, this high degree of freedom combined with the rapid mobilization of PCs and other devices created numerous headaches for asset tracking. At its peak, spending on hardware alone exceeded $100 million per year.
Results
Through a comprehensive ITAM implementation, the new asset management program at Cisco has been a resounding success. While employees did have to adjust to new rules, the process as a whole has been streamlined and user-satisfaction levels have risen. Centralized purchasing and a smaller number of hardware platforms have allowed Cisco to cut its hardware spend in half, according to Mark Edmondson, manager of IT services expenses for Cisco Finance.
This case study continues in phase 1
Info-Tech delivers: Use our tools and templates to accelerate your project to completion
HAM Standard Operating Procedures (SOP)
HAM Maturity Assessment
Non-Standard Hardware Request Form
HAM Visio Process Workflows
HAM Policy Templates
HAM Budgeting Tool
HAM Communication Plan
HAM Implementation Roadmap Tool
Measured value for Guided Implementations (GIs)
Engaging in GIs doesn’t just offer valuable project advice, it also results in significant cost savings.
| GI | Measured Value |
|---|---|
| Phase 1: Lay Foundations |
|
| Phase 2: Procure & Receive |
|
| Phase 3: Maintain & Dispose |
|
| Phase 4: Plan Implementation |
|
| Total savings | $25,845 |
Info-Tech offers various levels of support to best suit your needs
DIY Toolkit
“Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful.”
Guided Implementation
“Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track.”
Workshop
“We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place.”
Consulting
“Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project.”
Diagnostics and consistent frameworks used throughout all four options
Guided Implementation overview
| 1. Lay Foundations | 2. Procure & Receive | 3. Maintain & Dispose | 4. Budget & Implementation | |
|---|---|---|---|---|
| Best-Practice Toolkit |
1.1 Assess current state & plan scope 1.2 Build team & define metrics |
2.1 Request & procure 2.2 Receive & deploy |
3.1 Manage & maintain 3.2 Redeploy or dispose |
4.1 Plan budget 4.2 Communicate & build roadmap |
| Guided Implementation |
|
|
|
|
| Results & Outcomes |
|
|
|
|
Workshop overview
Contact your account representative or email Workshops@InfoTech.comfor more information.
| Phases: | Teams, Scope & Hardware Procurement | Hardware Procurement and Receiving | Hardware Maintenance & Disposal | Budgets, Roadmap & Communications |
|---|---|---|---|---|
| Duration* | 1 day | 1 day | 1 day | 1 day |
| * Activities across phases may overlap to ensure a timely completion of the engagement | ||||
| Projected Activities |
|
|
|
|
| Projected Deliverables |
|
|
||
Phase 1
Lay Foundations
Implement Hardware Asset Management
A centralized procurement process helped cut Cisco’s hardware spend in half
CASE STUDY
Industry IT
Source Cisco Systems, Inc.
Challenge
Cisco Systems’ hardware spend was out of control. Peaking at $100 million per year, the technology giant needed to standardize procurement processes in its highly individualized work environment.
Users had a variety of demands related to hardware and network availability. As a result, data was spread out amongst multiple databases and was managed by different teams.
Solution
The IT team at Cisco set out to solve their hardware-spend problem using a phased project approach.
The first major step was to identify and use the data available within various departments and databases. The heavily siloed nature of these databases was a major roadblock for the asset management program.
This information had to be centralized, then consolidated and correlated into a meaningful format.
Results
The centralized tracking system allowed a single point of contact (POC) for the entire lifecycle of a PC. This also created a centralized source of information about all the PC assets at the company.
This reduced the number of PCs that were unaccounted for, reducing the chance that Cisco IT would overspend based on its hardware needs.
There were still a few limitations to address following the first step in the project, which will be described in more detail further on in this blueprint.
This case study continues in phase 2
Step 1.1: Assess current state and plan scope
Phase 1: Assess & Plan
1.1 Assess current state & plan scope
1.2 Build team & define metrics
This step will walk you through the following activities:
1.1.1 Complete MGD (optional)
1.1.2 Outline hardware asset management challenges
1.1.3 Conduct HAM maturity assessment
1.1.4 Classify hardware assets to define scope of the program
This step involves the following participants:
- CIO/CFO
- IT Director
- Asset Manager
- Purchasing
- Service Desk Manager
- Security (optional)
- Operations (optional)
Step Outcomes
- Understand key challenges related to hardware asset management within your organization to inform program development.
- Evaluate current maturity level of hardware asset management components and overall program to determine starting point.
- Define scope for the ITAM program including list of hardware to track as assets.
Complete the Management & Governance Diagnostic (MGD) to weigh the effectiveness of ITAM against other services
1.1.1 Optional Diagnostic
The MGD helps you get the data you need to confirm the importance of improving the effectiveness of your asset management program.
The MGD allows you to understand the landscape of all IT processes, including asset management. Evaluate all team members’ perceptions of each process’ importance and effectiveness.
Use the results to understand the urgency to change asset management and its relevant impact on the organization.
Establish process owners and hold team members accountable for process improvement initiatives to ensure successful implementation and realize the benefits from more effective processes.
To book a diagnostic, or get a copy of our questions to inform your own survey, visit Info-Tech’s Benchmarking Tools, contact your account manager, or call toll-free 1-888-670-8889 (US) or 1-844-618-3192 (CAN).
Sketch out challenges related to hardware asset management to shape the direction of the project
Common HAM Challenges
Processes and Policies:
- Existing asset management practices are labor intensive and time consuming
- Manual spreadsheets are used, making collaboration and automation difficult
- Lack of HAM policies and standard operating procedures
- Asset management data is not centralized
- Lack of clarity on roles and responsibilities for ITAM functions
- End users don’t understand the value of asset management
Tracking:
- Assets move across multiple locations and are difficult to track
- Hardware asset data comes from multiple sources, creating fragmented datasets
- No location data is available for hardware
- No data on ownership of assets
Security and Risk:
- No insight into which assets contain sensitive data
- There is no information on risks by asset type
- Rogue systems need to be identified as part of risk management best practices
- No data exists for assets that contain critical/sensitive data
Procurement:
- No centralized procurement department
- Multiple quotes from vendors are not currently part of the procurement process
- A lack of formal process can create issues surrounding employee onboarding such as long lead times
- Not all procurement standards are currently defined
- Rogue purchases create financial risk
Receiving:
- No formal process exists, resulting in no assigned receiving location and no assigned receiving role
- No automatic asset tracking system exists
Disposal:
- No insight into where disposed assets go
- Formal refresh and disposal system is needed
Contracts:
- No central repository exists for contracts
- No insight into contract lifecycle, hindering negotiation effectiveness and pricing optimization
Outline hardware asset management challenges
1.1.1 Brainstorm HAM challenges
Participants
- CIO/CFO
- IT Director
- Asset Manager
- Purchasing
- Service Desk Manager
- Security
- Operations (optional)
A. As a group, outline the hardware asset management challenges facing the organization.
Use the previous slide to help you get started. You can use the following headings as a guide or think of your own:
- Processes and Policies
- Tracking
- Procurement
- Receiving
- Security and Risk
- Disposal
- Contracts
B. If you get stuck, use the Hardware Asset Management Maturity Assessment Tool to get a quick view of your challenges and maturity targets and kick-start the conversation.
To be effective with hardware asset management, understand the drivers and potential impact to the organization
| Drivers of effective HAM | Results of effective HAM | |
|---|---|---|
| Contracts and vendor licensing programs are complex and challenging to administer without data related to assets and their environment. | → | Improved access to accurate data on contracts, licensing, warranties, installed hardware and software for new contracts, renewals, and audit requests. |
| Increased need to meet compliance requires a formal approach to tracking and managing assets, regardless of device type. | → | Encryption, hardware tracking and discovery, software application controls, and change notifications all contribute to better asset controls and data security. |
| Cost cutting is on the agenda, and management is looking to reduce overall IT spend in the organization in any possible way. | → | Reduction of hardware spend by as much as 5% of the total budget through data for better forecasting and planning. |
| Assets with sensitive data are not properly secured, go missing, or are not safely disposed of when retired. | → | Document and enforce security policies for end users and IT staff to ensure sensitive data is properly secured, preventing costs much larger than the cost of only the device. |
Each level of HAM maturity comes with its own unique challenges
| Maturity | People & Policies | Processes | Technology |
|---|---|---|---|
| Chaos |
|
|
|
| Reactive |
|
|
|
| Controlled |
|
|
|
| Proactive |
|
|
|
| Optimized |
|
|
|
Conduct a hardware maturity assessment to understand your starting point and challenges
1.1.3 Complete HAM Maturity Assessment Tool
Complete the Hardware Asset Management Maturity Assessment Tool to understand your organization’s overall maturity level in HAM, as well as the starting maturity level aligned with each step of the blueprint, in order to identify areas of strength and weakness to plan the project. Use this to track progress on the project.
An effective asset management project has four essential components, with varying levels of management required
The hardware present in your organization can be classified into four categories of ascending strategic complexity: commodity, inventory, asset, and configuration.
Commodity items are devices that are low-cost, low-risk items, where tracking is difficult and of low value.
Inventory is tracked primarily to identify location and original expense, which may be depreciated by Finance. Typically there will not be data on these devices and they’ll be replaced as they lose functionality.
Assets will need the full lifecycle managed. They are identified by cost and risk. Often there is data on these devices and they are typically replaced proactively before they become unstable.
Configuration items will generally be tracked in a configuration management database (CMDB) for the purpose of enabling the support teams to make decisions involving dependencies, configurations, and impact analysis. Some data will be duplicated between systems, but should be synchronized to improve accuracy between systems.
See Harness Configuration Management Superpowers to learn more about building a CMDB.
Classify your hardware assets to determine the scope and strategy of the program
Asset: A unique device or configuration of devices that enables a user to perform productive work tasks and has a defined location and ownership attributes.
- Hardware asset management involves tracking and managing physical components from procurement through to retirement. It provides the base for software asset management and is an important process that can lead to improved lifecycle management, service request fulfillment, security, and cost savings through harvesting and redeployment.
- When choosing your strategy, focus on those devices that are high cost and high risk/function such as desktops, laptops, servers, and mobile devices.
ASSET - Items of high importance and may contain data, such as PCs, mobile devices, and servers.
INVENTORY - Items that require significant financial investment but no tracking beyond its existence, such as a projector.
COMMODITY - Items that are often in use but are of relatively low cost, such as keyboards or mice.
Classify your hardware assets to define the scope of the program
1.1.4 Define the assets to be tracked within your organization
Participants
- Participants
- CIO/CFO
- IT Director
- Asset Manager
- Purchasing
- Service Desk Manager
- Security (optional)
- Operations (optional)
Document
Document in the Standard Operating Procedures, Section 1 – Overview & Scope
- Determine value/risk threshold at which items should be tracked (e.g. over $1,000 and holding data).
- Divide a whiteboard or flip chart into three columns: commodity, asset, and inventory.
- Divide participants into groups by functional role to brainstorm devices in use within the organization. Write them down on sticky notes.
- Place the sticky notes in the column that best describes the role of the product in your organization.
Align the scope of the program with business requirements
CASE STUDY
Industry Public Administration
Source Client Case Study
Situation
A state government designed a process to track hardware worth more than $1,000. Initially, most assets consisted of end-user computing devices.
The manual tracking process, which relied on a series of Excel documents, worked well enough to track the lifecycle of desktop and laptop assets.
However, two changes upended the organization’s program: the cost of end-user computing devices dropped dramatically and the demand for network services led to the proliferation of expensive equipment all over the state.
Complication
The existing program was no longer robust enough to meet business requirements. Networking equipment was not only more expensive than end-user computing devices, but also more critical to IT services.
What was needed was a streamlined process for procuring high-cost, high-utility equipment, tracking their location, and managing their lifecycle costs without compromising services.
Resolution
The organization decided to formalize, document, and automate hardware asset management processes to meet the new challenges and focus efforts on high-cost, high-utility end-user computing devices only.
Step 1.2: Build team and define metrics
Phase 1: Assess & Plan
1.1 Assess current state & plan scope
1.2 Build team and define metrics
This step will walk you through the following activities:
1.2.1 Define responsibilities for Asset Manager and Asset Administrator
1.2.2 Use a RACI chart to determine roles within HAM team
1.2.3 Further clarify HAM responsibilities for each role
1.2.4 Identify HAM reporting requirements
This step involves the following participants:
- CIO/CFO
- IT Director
- IT Managers
- Asset Manager
- Asset Coordinators
- ITAM Team
- Service Desk
- End-User Device Support Team
Step Outcomes:
- Defined responsibilities for Asset Manager and Asset Administrator
- Documented RACI chart assigning responsibility and accountability for core HAM processes
- Documented responsibilities for ITAM/HAM team
- Defined and documented KPIs and metrics to meet HAM reporting requirements
Form an asset management team to lead the project
Asset management is an organizational change. To gain buy-in for the new processes and workflows that will be put in place, a dedicated, passionate team needs to jump-start the project.
Delegate the following roles to team members and grow your team accordingly.
|
Asset Manager |
|
|---|---|
|
Asset Administrator |
|
| Service Desk, IT Operations, Applications |
|
- The ITAM team should visit and consult with each component of the business as well as IT.
- Engage with leaders in each department to determine what their pain points are.
- The needs of each department are different and their responses will assist the ITAM team when designing goals for asset management.
- Consultations within each department also communicates the change early, which will help with the transition to the new ITAM program.
Info-Tech Insight
Ensure that there is diversity within the ITAM team. Assets for many organizations are diverse and the composition of your team should reflect that. Have multiple departments and experience levels represented to ensure a balanced view of the current situation.
Define the responsibilities for core ITAM/HAM roles of Asset Manager and Asset Administrator
1.2.1 Use Info-Tech’s job description templates to define roles
The role of the IT Asset Manager is to oversee the daily and long-term strategic management of software and technology- related hardware within the organization. This includes:
- Planning, monitoring, and recording software licenses and/or hardware assets to ensure compliance with vendor contracts.
- Forming procurement strategies to optimize technology spend across the organization.
- Developing and implementing procedures for tracking company assets to oversee quality control throughout their lifecycles.
The role of the IT Asset Administrator is to actively manage hardware and software assets within the organization. This includes:
- Updating and maintaining accurate asset records.
- Planning, monitoring, and recording software licenses and/or hardware assets to ensure compliance with vendor contracts.
- Administrative duties within procurement and inventory management.
- Maintaining records and databases regarding warranties, service agreements, and lifecycle management.
- Product standardization and tracking.
Use Info-Tech’s job description templates to assist in defining the responsibilities for these roles.
Organize your HAM team based on where they fit within the strategic, tactical, and operational components
Typically the asset manager will answer to either the CFO or CIO. Occasionally they answer to a vendor manager executive. The hierarchy may vary based on experience and how strategic a role the asset manager will play.
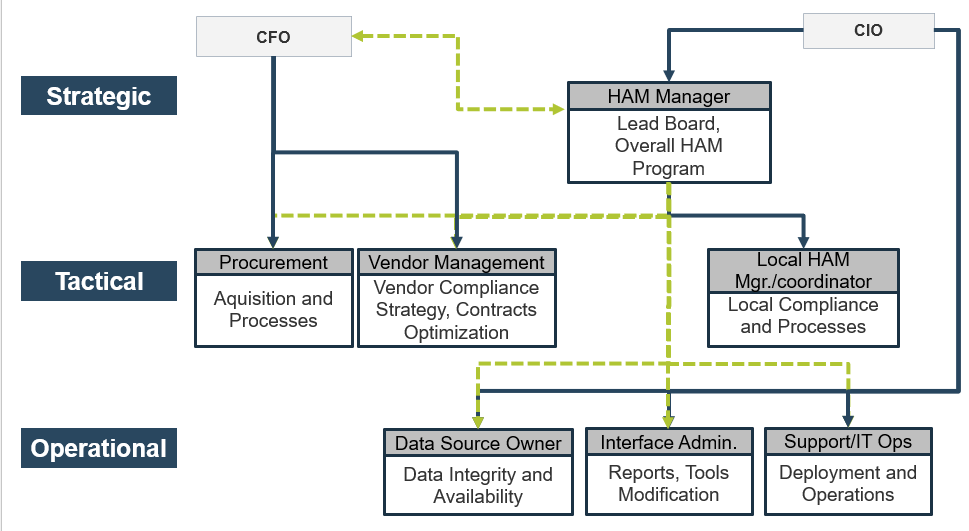
Determine the roles and responsibilities of the team who will support your HAM program
1.2.2 Complete a RACI
A RACI chart will identify who should be responsible, accountable, consulted, and informed for each key activity during the consolidation.
Participants
- Project Sponsor
- IT Director, CIO
- Project Manager
- IT Managers and Asset Manager(s)
- ITAM Team
Document
Document in the Standard Operating Procedure.
Instructions:
- Write out the list of all stakeholders along the top of a whiteboard. Write out the key initiative steps for the consolidation project along the left side (use this list as a starting point).
- For each initiative, identify each team member’s role. Are they:
- Responsible? The one responsible for getting the job done.
- Accountable? Only one person can be accountable for each task.
- Consulted? Involved through input of knowledge and information.
- Informed? Receive information about process execution and quality.
- As you proceed through the initiative, continue to add tasks and assign responsibility to this RACI chart.
A sample RACI chart is provided on the next slide
Start with a RACI chart to determine the responsibilities
1.2.2 Complete a RACI chart for your organization
| HAM Tasks | CIO | CFO | HAM Manager | HAM Administrator | Service Desk (T1,T2, T3) | IT Operations | Security | Procurement | HR | Business Unit Leaders | Compliance /Legal | Project Manager |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Policies and governance | A | I | R | I | I | C | I | C | C | I | I | |
| Strategy | A | R | R | R | R | |||||||
| Data entry and quality management | C | I | A | I | C | C | I | I | C | C | ||
| Risk management and asset security | A | R | C | C | R | C | C | |||||
| Process compliance auditing | A | R | I | I | I | I | I | |||||
| Awareness, education, and training | I | A | I | I | C | |||||||
| Printer contracts | C | A | C | C | C | R | C | C | ||||
| Hardware contract management | A | I | R | R | I | I | R | R | I | I | ||
| Workflow review and revisions | I | A | C | C | C | C | ||||||
| Budgeting | A | R | C | I | C | |||||||
| Asset acquisition | A | R | C | C | C | C | I | C | C | |||
| Asset receiving (inspection/acceptance) | I | A | R | R | I | |||||||
| Asset deployment | A | R | R | I | I | |||||||
| Asset recovery/harvesting | A | R | R | I | I | |||||||
| Asset disposal | C | A | R | R | I | I | ||||||
| Asset inventory (input/validate/maintain) | I | I | A/R | R | R | R | I | I | I |
Further clarify HAM responsibilities for each role
1.2.3 Define roles and responsibilities for the HAM team
Participants
- Participants IT Asset Managers and Coordinators
- ITAM Team
- IT Managers and IT Director
Document
- Document in the Standard Operating Procedures in section 3 – Roles and Responsibilities
- Discuss and finalize positions to be established within the ITAM/HAM office as well as additional roles that will be involved in HAM.
- Review the sample responsibilities below and revise or create responsibilities for each key position within the HAM team.
- Document in the HAM Standard Operating Procedures.
| Role | Responsibility |
|---|---|
| IT Manager |
|
| Asset Managers |
|
| Service Desk | |
| Desktop team | |
| Security | |
| Infrastructure teams |
Determine criteria for success: establish metrics to quantify and demonstrate the results and value of the HAM function
HAM metrics fall in the following categories:
HAM Metrics
- Quantity e.g. inventory levels and need
- Cost e.g. value of assets, budget for hardware
- Compliance e.g. contracts, policies
- Quality e.g. accuracy of data
- Duration e.g. time to procure or deploy hardware
Follow a process for establishing metrics:
- Identify and obtain consensus on the organization’s ITAM objectives, prioritized if possible.
- For each ITAM objective, select two or three metrics in the applicable categories (not all categories will apply to all objectives); be sure to select metrics that are achievable with reasonable effort.
- Establish a baseline measurement for each metric.
- Establish a method and accountability for ongoing measurement and analysis/reporting.
- Establish accountability for taking action on reported results.
- As ITAM expands and matures, change or expand the metrics as appropriate.
Define KPIs and associated metrics
- Identify the critical success factors (CSFs) for your hardware asset management program based on strategic goals.
- For each success factor, identify the key performance indicators (KPIs) to measure success and specific metrics that will be tracked and reported on.
- Sample metrics are below:
| CSF | KPI | Metrics |
|---|---|---|
| Improve accuracy of IT budget and forecasting |
|
|
| Identify discrepancies in IT environment |
|
|
| Avoid over purchasing equipment |
|
|
| Make more-effective purchasing decisions |
|
|
| Improve accuracy of data |
|
|
| Improved service delivery |
|
|
Identify hardware asset reporting requirements and the data you need to collect to meet them
1.2.4 Identify asset reporting requirements
Participants
- CIO/CFO
- IT Director
- Asset Manager
- Purchasing
- Service Desk Manager
- Operations (optional)
Document
Document in the Standard Operating Procedures, Section 13: Reporting
- Discuss the goals and objectives of implementing or improving hardware asset management, based on challenges identified in Step 1.2.
- From the goals, identify the critical success factors for the HAM program
- For each CSF, identify one to three key performance indicators to evaluate achievement of the success factor.
- For each KPI, identify one to three metrics that can be tracked and reported on to measure success. Ensure that the metrics are tangible and measurable and will be useful for decision making or to take action.
- Determine who needs this information and the frequency of reporting.
- If you have existing ITAM data, record the baseline metric.
| CSF | KPI | Metrics | Stakeholder/frequency |
|---|---|---|---|
Phase 1 Guided Implementation
Call 1-888-670-8889 or email GuidedImplementations@InfoTech.com for more information.
Complete these steps on your own or call us to complete a guided implementation. A guided implementation is a series of 2-3 advisory calls that help you execute each phase of a project. They are included in most advisory memberships.
Guided Implementation 1: Lay Foundations
Proposed Time to Completion: 4 weeks
Step 1.1: Assess current state and plan scope
Start with an analyst kick-off call:
- Review challenges.
- Assess current HAM maturity level.
- Define scope of HAM program.
Then complete these activities…
- Complete MGD (optional).
- Outline hardware asset management challenges.
- Conduct HAM maturity assessment.
- Classify hardware assets to define scope of the program.
With these tools & templates:
HAM Maturity Assessment
Standard Operating Procedures
Step 1.2: Build team and define metrics
Review findings with analyst:
- Define roles and responsibilities.
- Assess reporting requirements.
- Document metrics to track.
Then complete these activities…
- Define responsibilities for Asset Manager and Asset Administrator.
- Use a RACI chart to determine roles within HAM team.
- Document responsibilities for HAM roles.
- Identify HAM reporting requirements.
With these tools & templates:
RACI Chart
Asset Manager and Asset Administrator Job Descriptions
Standard Operating Procedures
Phase 1 Results & Insights:
For asset management to succeed, it needs to support the business. Engage business leaders to determine needs and build your HAM program around these goals.
If you want additional support, have our analysts guide you through this phase as part of an Info-Tech workshop
Book a workshop with our Info-Tech analysts:
- To accelerate this project, engage your IT team in an Info-Tech workshop with an Info-Tech analyst team.
- Info-Tech analysts will join you and your team onsite at your location or welcome you to Info-Tech’s historic Toronto office to participate in an innovative onsite workshop.
- Contact your account manager (www.infotech.com/account), or email Workshops@InfoTech.com for more information.
The following are sample activities that will be conducted by Info-Tech analysts with your team:
1.1.4 Classify hardware assets to define scope of the program
Determine value/risk threshold at which assets should be tracked, then divide a whiteboard into four quadrants representing four categories of assets. Participants write assets down on sticky notes and place them in the appropriate quadrant to classify assets.
1.2.2 Build a RACI chart to determine responsibilities
Identify all roles within the organization that will play a part in hardware asset management, then document all core HAM processes and tasks. For each task, assign each role to be responsible, accountable, consulted, or informed.
Phase 2
Procure and Receive
Implement Hardware Asset Management
Step 2.1: Request and Procure Hardware
Phase 2: Procure & Receive
2.1 Request & Procure
2.2 Receive & Deploy
This step will walk you through the following activities:
2.1.1 Identify IT asset procurement challenges
2.1.2 Define standard hardware requests
2.1.3 Document standard hardware request procedure
2.1.4 Build a non-standard hardware request form
2.1.5 Make lease vs. buy decisions for hardware assets
2.1.6 Document procurement workflow
2.1.7 Build a purchasing policy
This step involves the following participants:
- Asset Manager
- Purchasing
- Service Desk Manager
- Operations (optional)
- CFO or other management representative from Finance
Step Outcomes:
- Definition of standard hardware requests for roles, including core vs. optional assets
- End-user request process for standard hardware
- Non-standard hardware request form
- Lease vs. buy decisions for major hardware assets
- Defined and documented procurement workflow
- Documented purchasing policy
California saved $40 million per year using a green procurement strategy
CASE STUDY
Industry Government
Source Itassetmanagement.net
Challenge
Signed July 27, 2004, Executive order S-20-04, the “Green Building Initiative,” placed strict regulations on energy consumption, greenhouse gas emissions, and raw material usage and waste.
In compliance with S-20-04, the State of California needed to adopt a new procurement strategy. Its IT department was one of the worst offenders given the intensive energy usage by the variety of assets managed under the IT umbrella.
Solution
A green IT initiative was enacted, which involved an extensive hardware refresh based on a combination of agent-less discovery data and market data (device age, expiry dates, power consumption, etc.).
A hardware refresh of almost a quarter-million PCs, 9,500 servers, and 100 email systems was rolled out as a result.
Other changes, including improved software license compliance and data center consolidation, were also enacted.
Results
Because of the scale of this hardware refresh, the small changes meant big savings.
A reduction in power consumption equated to savings of over $40 million per year in electricity costs. Additionally, annual carbon emissions were trimmed by 200,000 tons.
Improve your hardware asset procurement process to…
Asset Procurement
- Standardization
- Aligned procurement processes
- SLAs
- TCO reduction
- Use of centralized/ single POC
Standardize processes: Using standard products throughout the enterprise lowers support costs by reducing the variety of parts that must be stocked for onsite repairs or for provisioning and supporting equipment.
Align procurement processes: Procurement processes must be aligned with customers’ business requirements, which can have unique needs.
Define SLAs: Providing accurate and timely performance metrics for all service activities allows infrastructure management based on fact rather than supposition.
Reduce TCO: Management recognizes service infrastructure activities as actual cost drivers.
Implement a single POC: A consolidated service desk is used where the contact understands both standards (products, processes, and practices) and the user’s business and technical environment.
Identify procurement challenges to identify process improvement needs
2.1.1 Identify IT asset procurement challenges
Participants
- Asset Manager
- Purchasing
- Service Desk Manager
- Operations (optional)
- As a group, brainstorm existing challenges related to IT hardware requests and procurement.
- If you get stuck, consider the common challenges listed below.
- Use the results of the discussion to focus on which problems can be resolved and integrated into your organization as operational standards.
Document hardware standards to speed time to procure and improve communications to users regarding options
The first step in your procurement workflow will be to determine what is in scope for a standard request, and how non-standard requests will be handled. Questions that should be answered by this procedure include:
- What constitutes a non-standard request?
- Who is responsible for evaluating each type of request? Will there be one individual or will each division in IT elect a representative to handle requests specific to their scope of work?
- What additional security measures need to be taken?
- Are there exceptions made for specific departments or high-ranking individuals?
If your end-user device strategy requires an overhaul, schedule time with an Info-Tech analyst to review our blueprint Build an End-User Computing Strategy.
Once you’ve answered questions like these, you can outline your hardware standards as in the example below:
| Use Case | Mobile Standard | Mac Standard | Mobile Power User |
|---|---|---|---|
| Asset | Lenovo ThinkPad T570 | iMac Pro | Lenovo ThinkPad P71 |
| Operating system | Windows 10 Pro | Mac OSX | Windows 10 Pro, 64 bit |
| Display | 15.6" | 21.5" | 17.3” |
|
Memory |
32GB | 8GB | 64GB |
| Processor | Intel i7 – 7600U Processor | 2.3GHz | Xeon E3 v6 Processor |
| Drive | 500GB | 1TB | 1TB |
| Warranty | 3 year | 1 year + 2 extended | 3 year |
Info-Tech Insight
Approach hardware standards from a continual improvement frame of mind. Asset management is a dynamic process. Hardware standards will need to adapt over time to match the needs of the business. Plan assessments at routine intervals to ensure your current hardware standards align with business needs.
Document specifications to meet environmental, security, and manageability requirements
Determine environmental requirements and constraints.
Power management
Compare equipment for power consumption and ability to remotely power down machines when not in use.
Heat and noise
Test equipment run to see how hot the device gets, where the heat is expelled, and how much noise is generated. This may be particularly important for users who are working in close quarters.
Carbon footprint
Ask what the manufacturer is doing to reduce post-consumer waste and eliminate hazardous materials and chemicals from their products.
Ensure security requirements can be met.
- Determine if network/wireless cards meet security requirements and if USB ports can be turned off to prevent removal of data.
- Understand the level of security needed for mobile devices including encryption, remote shut down or wipe of hard drives, recovery software, or GPS tracking.
- Decide if fingerprint scanners with password managers would be appropriate to enable tighter security and reduce the forgotten-password support calls.
Review features available to enhance manageability.
- Discuss manageability goals with your IT team to see if any can be solved with added features, for example:
- Remote control for troubleshooting and remote management of data security settings.
- Asset management software or tags for bar coding, radio frequency identification (RFID), or GPS, which could be used in combination with strong asset management practices to inventory, track, and manage equipment.
If choosing refurbished equipment, avoid headaches by asking the right questions and choosing the right vendor
- Is the equipment functional and for how long is it expected to last?
- How long will the vendor stand behind the product and what support can be expected?
- This is typically two to five years, but will vary from vendor to vendor.
- Will they repair or replace machines? Many will just replace the machine.
- How big is the inventory supply?
- What kind of inventory does the vendor keep and for how long can you expect the vendor to keep it?
- How does the vendor source the equipment and do they have large quantities of the same make and model for easier imaging and support?
- How complete is the refurbishment process?
- Do they test all components, replace as appropriate, and securely wipe or replace hard drives?
- Are they authorized to reload MS Windows OEM?
- Is the product Open Box or used?
- Open Box is a new product returned back to the vendor. Even if it is not used, the product cannot be resold as a new product. Open Box comes with a manufacturer’s warranty and the latest operating system.
- If used, how old is the product?
"If you are looking for a product for two or three years, you can get it for less than half the price of new. I bought refurbished equipment for my call center for years and never had a problem". – Glen Collins, President, Applied Sales Group
Info-Tech Insight
Price differences are minimal between large and small vendors when dealing with refurbished machines. The decision to purchase should be based on ability to provide and service equipment.
Define standard hardware requests, including core and optional assets
2.1.2 Identify standards for hardware procurement by role
Participants
- Asset Manager
- Purchasing
- Service Desk Manager
- Operations (optional)
- Representatives from all other areas of the business
Document
Document in the Standard Operating Procedures, Section 7: Procurement.
- Divide a whiteboard into columns representing all major areas of the business.
- List the approximate number of end users present at each tier and record these totals on the board.
- Distribute sticky notes. Use two different sizes: large sizes represent critically important hardware and small sizes represent optional hardware.
- Define core hardware assets for each division as well as optional hardware assets.
- Focus on the small sticky notes to determine if these optional purchases are necessary.
- Finalize the group decision to determine the standard hardware procurement for each role in the organization. Record results in a table similar to the example below:
| Department | Core Hardware Assets | Optional Hardware Assets |
|---|---|---|
| IT | PC, tablet, monitor | Second monitor |
| Sales | PC, monitor | Laptop |
| HR | PC, monitor | Laptop |
| Marketing | PC (iMac) | Tablet, laptop |
Document procedures for users to make standard hardware requests
2.1.3 Document standard hardware request procedure
Participants
- Asset Manager
- Purchasing
- Service Desk Manager
- Operations (optional)
- Representatives from all other areas of the business
Document
Document in the Standard Operating Procedures, Section 6: End-User Request Process.
Discuss and document the end-user request process:
- In which cases can users request a primary device?
- In which cases can users request a secondary (optional device)?
- What justification is needed to approve of a secondary device?
- E.g. The request for a secondary device should be via email to the IS Projects and Procurements Officer. This email should outline the business case for why multiple devices are required.
- Will a service catalog be available and integrated with an ITAM solution for users to make standard requests? If so, can users also configure their options?
- Document the process in the standard operating procedure. Example:
End-User Request Process
- Hardware and software will be purchased through the user-facing catalog.
- Peripherals will be ordered as needed.
- End-user devices will be routed to business managers for approval prior to fulfillment by IT.
- Requests for secondary devices must be accompanied by a business case.
- Equipment replacements due to age will be managed through IT replacement processes.
Improve the process for ordering non-standard hardware by formalizing the request process, including business needs
2.1.4 Build a non-standard hardware request form
- Although the goal should be to standardize as much as possible, this isn’t always possible. Ensure users who are requesting non-standard hardware have a streamlined process to follow that satisfies the justifications for increased costs to deliver.
- Use Info-Tech’s template to build a non-standard hardware request form that may be used by departments/users requesting non-standard hardware in order to collect all necessary information for the request to be evaluated, approved, and sent to procurement.
- Ensure that the requestor provides detailed information around the equipment requested and the reason standard equipment does not suffice and includes all required approvals.
- Include instructions for completing and submitting the form as well as expected turnaround time for the approval process.
Info-Tech Insight
Include non-standard requests in continual improvement assessment. If a large portion of requests are for non-standard equipment, it’s possible the hardware doesn’t meet the recommended requirements for specialized software in use with many of your business users. Determine if new standards need to be set for all users or just “power users.”
Identify the information you need to collect to ensure a smooth purchasing process
| Categories | Peripherals | Desktops/Laptops | Servers |
|---|---|---|---|
| Financial |
|
|
|
| Request authorization |
|
|
|
| Required approvals |
|
|
|
| Warranty requirements |
|
|
|
| Inventory requirements |
|
|
|
| Tracking requirements |
|
|
|
Info-Tech Best Practice
Take into account the possibility of encountering taxation issues based on where the equipment is being delivered as well as taxes imposed or incurred in the location from which the asset was shipped or sent. This may impact purchasing decisions and shipping instructions.
Develop a procurement plan to get everyone in the business on the same page
- Without an efficient and structured process around how IT purchases are budgeted and authorized, maverick spending and dark procurement can result, limiting IT’s control and visibility into purchases.
- The challenge many IT departments face is that there is a disconnect between meeting the needs of the business and bringing in equipment according to existing policies and procedures.
- The asset manager should demonstrate how they can bridge the gaps and improve tracking mechanisms at the same time.
Improve procurement decisions:
- Demonstrate how technology is a value-add.
- Make a clear case for the budget by using the same language as the rest of the business.
- Quantify the output of technology investments in tangible business terms to justify the cost.
- Include the refresh cycle in the procurement plan to ensure mission- critical systems will include support and appropriate warranty.
- Plan technology needs for the future and ensure IT technology will continue to meet changing needs.
- Synchronize redundant organizational procurement chains in order to lower cost.
Document the following in your procurement procedure:
- Process for purchase requests
- Roles and responsibilities, including requestors and approvers
- Hardware assets to purchase and why they are needed
- Timelines for purchase
- Process for vendors
Info-Tech Insight
IT procurement teams are often heavily siloed from ITAM teams. The procurement team is typically found in the finance department. One way to bridge the gap is to implement routine, reliable reporting between departments.
Determine if it makes sense to lease or buy your equipment; weigh the pros and cons of leasing hardware
Pros
- Keeps operational costs low in the short term by containing immediate cost.
- Easy, predictable payments makes it easier to budget for equipment over long term.
- Get the equipment you need to start doing business right away if you’re just starting out.
- After the leasing term is up, you can continue the lease and update your hardware to the latest version.
- Typical leases last 2 or 3 years, meaning your hardware can get upgrades when it needs it and your business is in a better position to keep up with technology.
- Leasing directly from the vendor provides operational flexibility.
- Focus on the business and let the vendor focus on equipment service and updates as you don’t have to pay for maintenance.
- Costs structured as OPEX.
Cons
- In the long term, leasing is almost always more expensive than buying because there’s no equity in leased equipment and there may be additional fees and interest.
- Commitment to payment through the entire lease period even if you’re not using the equipment anymore.
- Early termination fees if you need to get out of the lease.
- No option to sell equipment once you’re finished with it to make money back.
- Maintenance is up to leasing company’s specifications.
- Product availability may be limited.
Recommended for:
- Companies just starting out
- Business owners with limited capital or budget
- Organizations with equipment that needs to be upgraded relatively often
Weigh the pros and cons of purchasing hardware
Pros
- Complete control over assets.
- More flexible and straightforward procurement process.
- Tax incentives: May be able to fully deduct the cost of some newly purchased assets or write off depreciation for computers and peripherals on taxes.
- Preferable if your equipment will not be obsolete in the next two or three years.
- You can resell the asset once you don’t need it anymore to recover some of the cost.
- Customization and management of equipment is easier when not bound by terms of leasing agreement.
- No waiting on vendor when maintenance is needed; no permission needed to make changes.
Cons
- High initial cost of investment with CAPEX expense model.
- More paperwork.
- You (as opposed to vendor) are responsible for equipment disposal in accordance with environmental regulations.
- You are responsible for keeping up with upgrades, updates, and patches.
- You risk ending up with out-of-date or obsolete equipment.
- Hardware may break after terms of warranty are up.
Recommended for:
- Established businesses
- Organizations needing equipment with long-term lifecycles
Make a lease vs. buy decision for equipment purchases
2.1.4 Decide whether to purchase or lease
Participants
- Asset Manager
- Purchasing
- Service Desk Manager
- Operations (optional)
- Representatives from all other areas of the business
Document
Document policy decisions in the Standard Operating Procedures – Section 7: Procurement
- Identify hardware equipment that requires a purchase vs. lease decision.
- Discuss with Finance whether it makes sense to purchase or lease each major asset, considering the following:
- Costs of equipment through each method
- Tax deductions
- Potential resale value
- Potential revenue from using the equipment
- How quickly the equipment will be outdated or require refresh
- Size of equipment
- Maintenance and support requirements
- Overall costs
Determine appropriate warranty and service-level agreements for your organization
Determine acceptable response time, and weigh the cost of warranty against the value of service.
- Standard warranties vary by manufacturer, but are typically one or three years.
- Next-day, onsite service may be part of the standard offering or may be available as an uplift.
- Four-hour, same-day service can also be added for high availability needs.
- Extended warranties can be purchased beyond three years, although not many organizations take advantage of this offering.
- Other organizations lower or remove the warranty and have reported savings of as much as $150 per machine.
Speak to your partner to see how they can help the process of distributing machines.
- Internal components change frequently with laptops and desktops. If purchasing product over time rather than buying in bulk, ensure the model will be available for a reasonable term to reduce imaging and support challenges.
- Determine which services are important to your organization and request these services as part of the initial quote. If sending out a formal RFQ or RFP, document required services and use as the basis for negotiating SLAs.
- Document details of SLA, including expectations of services for manufacturer, vendor, and internal team.
- If partner will be providing services, request they stock an appropriate number of hot spares for frequently replaced parts.
- If self-certifying, review resource capabilities, understand skill and certification requirements; for example, A+ certification may be a pre-requisite.
- Understand DOA policy and negotiate a “lemon policy,” meaning if product dies within 15 or 30 days it can be classified as DOA. Seek clarity on return processes.
Consider negotiation strategies, including how and when to engage with different partners during acquisition
Direct Model
- Dell’s primary sales model is direct either through a sales associate or through its e-commerce site. Promotions are regularly listed on the website, or if customization is required, desktops and laptops have some flexibility in configuration. Discounts can be negotiated with a sales rep on quantity purchases, but the discount level changes based on the model and configuration.
- Other tier-one manufacturers typically sell direct only from their e-commerce sites, providing promotions based on stock they wish to move, and providing some configuration flexibility. They rely heavily on the channel for the majority of their business.
Channel Model
- Most tier one manufacturers have processes in place to manage a smaller number of partners rather than billing and shipping out to individual customers. Deviating from this process and dealing direct with end customers can create order processing issues.
- Resellers have the ability to negotiate discounts based on quantities. Discounts will vary based on model, timing (quarter or year end), and quantity commitment.
- Negotiations on large quantities should involve a manufacturer rep as well as the reseller to clearly designate roles and services, ensure processes are in place to fulfill your needs, and agree on pricing scheme. This will prevent misunderstandings and bring clarity to any commitments.
- Often the channel partners are authorized to provide repair services under warranty for the manufacturer.
- Dell also uses the channel model for distribution where customers demand additional services.
Expect discounts to reflect quantity and method of purchase
Transaction-based purchases will receive the smallest discounting.
- Understand requirements to find the most appropriate make and model of equipment.
- Prepare a forecast of expected purchases for the year and discuss discounting.
- Typically initial discounts will be 3-5% off suggested retail price.
- Once a history is in place, and the vendor is receiving regular orders, it may extend deeper discounts.
Bulk purchases will receive more aggressive discounting of 5-15% off suggested retail price, depending on quantities.
- Examine shipping options and costs to take advantage of bulk deliveries; in some cases vendors may waive shipping fees as an extension of the discounting.
- If choosing end-of-line product, ensure appropriate quantity of a single model is available to efficiently roll out equipment.
- Various pricing models can be used to obtain best price.
Larger quantities rolled out over time will require commitments to the manufacturer to obtain deepest discounts.
- Discuss all required services as part of negotiation to ensure there are no surprise charges.
- Several pricing models can be used to obtain the best price.
- Suggested retail price minus as much as 20%.
- Cost plus 3% up to 10% or more.
- Fixed price based on negotiating equipment availability with budget requirements.
If sending out to bid, determine requirements and scoring criteria
It’s nearly impossible to find two manufacturers with the exact same specifications, so comparisons between vendors is more art than science.
New or upgraded components will be introduced into configurations when it makes the most sense in a production cycle. This creates a challenge in comparing products, especially in an RFP. The best way to handle this is to:
- Define and document minimum technology requirements.
- Define and document service needs.
- Compare vendors to see if they’ve met the criteria or not; if yes, compare prices.
- If the vendors have included additional offerings, see if they make sense for your organization. If they do, include that in the scoring. If not, exclude and score based on price.
- Recognize that the complexity of the purchase will dictate the complexity of scoring.
"The hardware is the least important part of the equation. What is important is the warranty, delivery, imaging, asset tagging, and if they cannot deliver all these aspects the hardware doesn’t matter." – Doug Stevens, Assistant Manager Contract Services, Toronto District School Board
Document and analyze the hardware procurement workflow to streamline process
The procurement process should balance the need to negotiate appropriate pricing with the need to quickly approve and fulfill requests. The process should include steps to follow for approving, ordering, and tracking equipment until it is ready for receipt.
Within the process, it is particularly important to decide if this is where equipment is added into the database or if it will happen upon receipt.
A poorly designed procurement workflow:
- Includes many bottlenecks, stopping and starting points.
- May impact project and service requests and requires unrealistic lead times.
- May lead to lost productivity for users and lost credibility for the IT department.
A well-designed hardware procurement workflow:
- Provides reasonable lead times for project managers and service or hardware request fulfillment.
- Provides predictability for technical resources to plan deployments.
- Reduces bureaucracy and workload for following up on missing shipments.
- Enables improved documentation of assets to start lifecycle management.
Info-Tech Insight
Where the Hardware Asset Manager is unable to affect procurement processes to reduce time to deliver, consider bringing inventory onsite or having your hardware vendor keep stock, ready to ship on demand. Projects, replacements, and new-user requests cannot be delayed in a service-focused IT organization due to bureaucratic processes.
Document and analyze your procurement workflow to identify opportunities for improvement and communicate process
Determine if you need one workflow for all equipment or multiples for small vs. large purchases.
Occasionally large rollouts require significant changes from lower dollar purchases.
Watch for:
- Back and forth communications
- Delays in approvals
- Inability to get ETAs from vendors
- Too many requests for quotes for small purchases
- Entry into asset database
This sample can be found in the HAM Process Workflows.
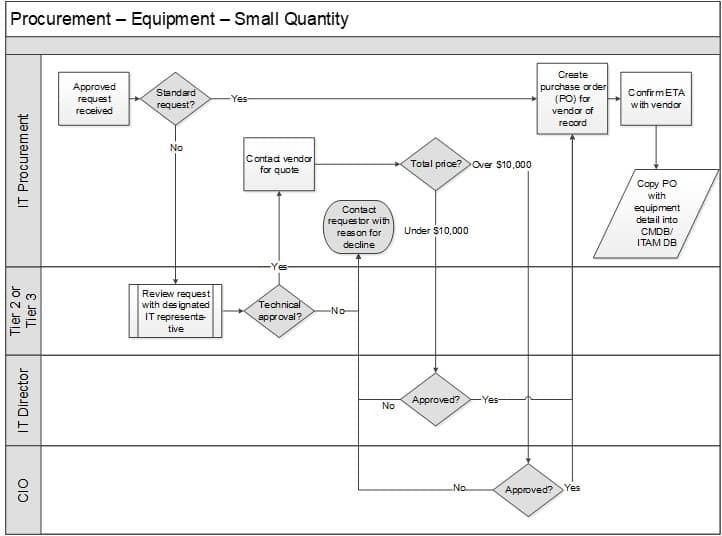
Design the process workflow for hardware procurement
2.1.6 Illustrate procurement workflow with a tabletop exercise
Participants
- Asset Manager
- Purchasing
- Service Desk Manager
- Operations (optional)
- CFO or other management representative from Finance
Document
Document in the Standard Operating Procedures, Section 7: Procurement
- In a group, distribute sticky notes or cue cards.
- Designate a space on the table/whiteboard to plot the workflow.
- Determine which individuals are responsible for handling non-standard requests. Establish any exceptions that may apply to your defined hardware standard.
- Gather input from Finance on what the threshold will be for hardware purchases that will require further approval.
- Map the procurement process for a standard hardware purchase.
- If applicable, map the procurement process for a non-standard request separately.
- Evaluate the workflow to identify any areas of inefficiency and make any changes necessary to improve the process.
- Be sure to discuss and include:
- All necessary approvals
- Time required for standard equipment process
- Time required for non-standard equipment process
- How information will be transferred to ITAM database
Document and share an organizational purchasing policy
2.1.7 Build a purchasing policy
A purchasing policy helps to establish company standards, guidelines, and procedures for the purchase of all information technology hardware, software, and computer-related components as well as the purchase of all technical services.
The policy will ensure that all purchasing processes are consistent and in alignment with company strategy. The purchasing policy is key to ensuring that corporate purchases are effective and the best value for money is obtained.
Implement a purchasing policy to prevent or reduce:
- Costly corporate conflict of interest cases.
- Unauthorized purchases of non-standard, difficult to support equipment.
- Unauthorized purchases resulting in non-traceable equipment.
- Budget overruns due to decentralized, equipment acquisition.
Download Info-Tech’s Purchasing Policytemplate to build your own purchasing policy.
Step 2.2: Receive and Deploy Hardware
Phase 2: Procure & Receive
2.1 Request & Procure
2.2 Receive & Deploy
This step will walk you through the following activities:
2.2.1 Select appropriate asset tagging method
2.2.2 Design workflow for receiving and inventorying equipment
2.2.3 Document the deployment workflow(s)
This step involves the following participants:
- Asset Manager
- Purchasing
- Receiver (optional)
- Service Desk Manager
- Operations (optional)
Step Outcomes:
- Understanding of the pros and cons of various asset tagging methods
- Defined asset tagging method, process, and location by equipment type
- Identified equipment acceptance, testing, and return procedures
- Documented equipment receiving and inventorying workflow
- Documented deployment workflows for desktop hardware and large-scale deployments
Cisco implemented automation to improve its inventory and deployment system
CASE STUDY
Industry Networking
Source Cisco IT
Challenge
Although Cisco Systems had implemented a centralized procurement location for all PCs used in the company, inventory tracking had yet to be addressed.
Inventory tracking was still a manual process. Given the volume of PCs that are purchased each year, this is an incredibly labor-intensive process.
Sharing information with management and end users also required the generation of reports – another manual task.
Solution
The team at Cisco recognized that automation was the key component holding back the success of the inventory management program.
Rolling out an automated process across multiple offices and groups, both nationally and internationally, was deemed too difficult to accomplish in the short amount of time needed, so Cisco elected to outsource its PC management needs to an experienced vendor.
Results
As a result of the PC management vendor’s industry experience, the implementation of automated tracking and management functions drastically improved the inventory management situation at Cisco.
The vendor helped determine an ideal leasing set life of 30 months for PCs, while also managing installations, maintenance, and returns.
Even though automation helped improve inventory and deployment practices, Cisco still needed to address another key facet of asset management: security.
This case study continues in phase 3.
An effective equipment intake process is critical to ensure product is correct, documented, and secured
Examine your current process for receiving assets. Typical problems include:
Receiving inventory at multiple locations can lead to inconsistent processes. This can make invoice reconciliation challenging and result in untracked or lost equipment and delays in deployment.
Equipment not received and secured quickly. Idle equipment tends to go missing if left unsupervised for too long. Missed opportunities to manage returns where equipment is incorrect or defective.
Disconnect between procurement and receiving where ETAs are unknown or incorrect. This can create an issue where no one is prepared for equipment arrival and is especially problematic on large orders.
How do you solve these problems? Create a standardized workflow that outlines clear steps for asset receiving.
A workflow will help to answer questions such as:
- How do you deal with damaged shipments? Incorrect shipments?
- Did you reach an agreement with the vendor to replace damaged/incorrect shipments within a certain timeframe?
- When does the product get tagged and entered into the system as received?
- What information needs to get captured on the asset tag?
Standardize the process for receiving your hardware assets
The first step in effective hardware asset intake is establishing proper procedures for receiving and handling of assets.
Process: Start with information from the procurement process to determine what steps need to follow to receive into appropriate systems and what processes will enable tagging to happen as soon as possible.
People: Ensure anyone who may impact this process is aware of the importance of documenting before deployment. Having everyone who may be handling equipment on board is key to success.
Security: Equipment will be secured at the loading dock or reception. It will need to be secured as inventory and be secured if delivering directly to the bench for imaging. Ensure all receiving activities are done before equipment is deployed.
Tools: A centralized ERP system may already provide a place to receive and reconcile with purchasing and invoicing, but there may still be a need to receive directly into the ITAM and/or CMDB database rather than importing directly from the ERP system.
Tagging: A variety of methods can be used to tag equipment to assist with inventory. Consider the overall lifecycle management when determining which tagging methods are best.
Info-Tech Insight
Decentralized receiving doesn’t have to mean multiple processes. Take advantage of enterprise solutions that will centralize the data and ensure everyone follows the same processes unless there is an uncompromising and compelling logistical reason to deviate.
Evaluate the pros and cons of different asset tagging methods
| Method | Cost | Strengths | Weaknesses | Recommendation |
|---|---|---|---|---|
| RFID with barcoding – asset tag with both a barcode and RFID solution | $$$$ |
|
|
|
| RFID only – small chip with significant data capacity | $$$ |
|
|
|
| Barcoding only – adding tags with unique barcodes | $$ |
|
|
|
Evaluate the pros and cons of different asset tagging methods
| Method | Cost | Strengths | Weaknesses | Recommendation |
|---|---|---|---|---|
| QR codes – two-dimensional codes that can store text, binary, image, or URL data | $$ |
|
|
|
| Manual tags – tag each asset with your own internal labels and naming system | $ |
|
|
|
| Asset serial numbers – tag assets using their serial number | $ |
|
|
|
Select the appropriate method for tagging and tracking your hardware assets
2.2.1 Select asset tagging method
Participants
- Asset Manager
- Purchasing
- Service Desk Manager
- Operations (optional)
Document
Document in the Standard Operating Procedures, Section 8
- Define your asset tagging method. For most organizations, asset tracking is done via barcoding or QR codes, either by using one method or a combination of the two. Other methods, including RFID, may be applicable based on cost or tracking complexity. Overall, barcodes embedded with RFID are the most robust and efficient method for asset tagging, but also the most expensive. Choose the best method for your organization, taking into account affordability, labor-intensiveness, data complexity needs, and ease of deployment.
- Define the process for tagging assets, including how soon they should receive the tag, whose responsibility it is, and whether the tag type varies depending on the asset type.
- Define the location of asset tags according to equipment type. Example:
| Asset Type | Asset Tag Location |
|---|---|
| PC desktop | Right upper front corner |
| Laptop | Right corner closest to user when laptop is closed |
| Server | Right upper front corner |
| Printer | Right upper front corner |
| Modems | Top side, right corner |
Inspect and test equipment before accepting it into inventory to ensure it’s working according to specifications
Upon receipt of procured hardware, validate the equipment before accepting it into inventory.
- Receive - Upon taking possession of the equipment, stage them for inspection before placing them into inventory or deploying for immediate use.
- Inspect - The inspection process should involve at minimum examining the products that have been delivered to determine conformance to purchase specifications.
- Test -Depending on the type and cost of hardware, some assets may benefit from additional testing to determine if they perform at a satisfactory level before being accepted.
- Accept - If the products conform to the requirements of the purchase order, acknowledge receipt so the supplier may be paid. Most shipments are automatically considered as accepted and approved for payment within a specific timeframe.
Assign responsibility and accountability for inspection and acceptance of equipment, verifying the following:
- The products conform to purchase order requirements.
- The quantity ordered is the same as the quantity delivered.
- There is no damage to equipment.
- Delivery documentation is acceptable.
- Products are operable and perform according to specifications.
- If required, document an acceptance testing process as a separate procedure.
Build the RMA procedure into the receiving process to handle receipt of defective equipment
The return merchandise authorization (RMA) process should be a standard part of the receiving process to handle the return of defective materials to the vendor for either repair or replacement.
If there is a standard process in place for all returns in the organization, you can follow the same process for returning hardware equipment:
- Call the vendor to receive a unique RMA number that will be attached to the equipment to be returned, then follow manufacturer specifications for returning equipment within allowable timelines according to the contract where applicable.
- Establish a lemon policy with vendors, allowing for full returns up to 30 days after equipment is deployed if the product proves defective after initial acceptance.
Info-Tech Insight
Make sure you’re well aware of the stipulations in your contract or purchase order. Sometimes acceptance is assumed after 60 days or less, and oftentimes the clock starts as soon as the equipment is shipped out rather than when it is received.
Info-Tech Best Practice
Keep in mind that the serial number on the received assed may not be the asset that ultimately ends up on the user’s desk if the RMA process is initiated. Record the serial number after the RMA process or add a correction process to the workflow to ensure the asset is properly accounted for.
Determine what equipment should be stocked for quick deployment where demand is high or speed is crucial
The most important feature of your receiving and inventory process should be categorization. A well-designed inventory system should reflect not only the type of asset, but also the usage level.
A common technique employed by asset managers is to categorize your assets using an ABC analysis. Assets are classified as either A, B, or C items. The ratings are based on the following criteria:
A
A items have the highest usage. Typically, 10-20% of total assets in your inventory account for upwards of 70-80% of the total asset requests.
A items should be tightly controlled with secure storage areas and policies. Avoiding stock depletion is a top priority.
B
B items are assets that have a moderate usage level, with around 30% of total assets accounting for 15-25% of total requests.
B items must be monitored; B items can transition to A or C items, especially during cycles of heavier business activity.
C
C items are assets that have the lowest usage, with upwards of 50% of your total inventory accounting for just 5% of total asset requests.
C items are reordered the least frequently, and present a low demand and high risk for excessive inventory (especially if they have a short lifecycle). Many organizations look to move towards an on-demand policy to mitigate risk.
Info-Tech Insight
Get your vendor to keep stock of your assets. If large quantities of a certain asset are required but you lack the space to securely store them onsite, ask your vendor to keep stock for you and release as you issue purchase orders. This speeds up delivery and delays warranty activation until the item is shipped. This does require an adherence to equipment standards and understanding of demand to be effective.
Define the process for receiving equipment into inventory
Define the following in your receiving process:
- When will equipment be opened once delivered?
- Who will open and validate equipment upon receipt?
- How will discrepancies be resolved?
- When will equipment be tagged and identified in the tracking tool?
- When will equipment be locked in secure storage?
- Where will equipment go if it needs to be immediately deployed?
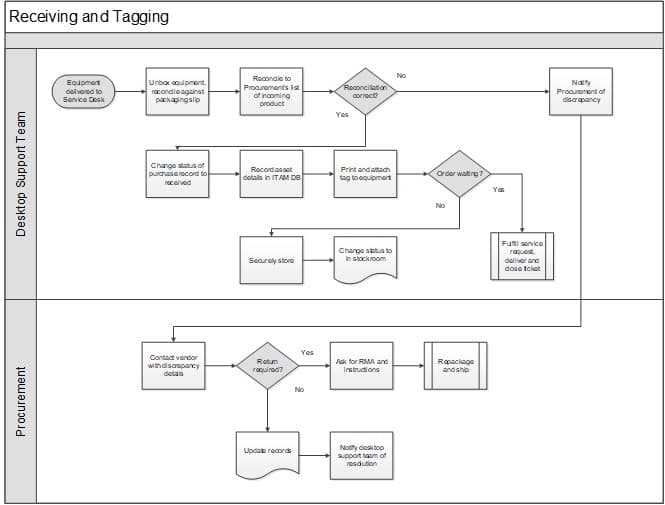
Design the workflow for receiving and inventorying equipment
2.2.2 Illustrate receiving workflow with a tabletop exercise
Participants
- Asset Manager
- Purchasing
- Service Desk Manager
- Operations (optional)
- CFO or other management representative from Finance
Document
Document in the Standard Operating Procedures, Section 8: Receiving and Equipment Inventory
Option 1: Whiteboard
- Discuss the workflow and draw it on the whiteboard.
- Assess whether you are using the best workflow. Modify it if necessary.
- Use the sample workflow from this step as a guide if starting from scratch.
- Engage the team in refining the process workflow.
- Transfer data to Visio and add to the SOP.
Option 2: Tabletop Exercise
- Distribute index cards to each member of the team.
- Have each person write a single task they perform on the index card. Be granular. Include the title or the name of the person responsible.
- Mark cards that are decision points. Use a card of a different color or use a marker to make a colored dot.
- Arrange the index cards in order, removing duplicates.
- Assess whether you are using the best workflow. Engage the team to refine it if necessary.
- Transfer data to Visio and add to the SOP.
Improve device deployment by documenting software personas for each role
- Improve the deployment process for new users by having a comprehensive list of software used by common roles within the organization. With large variations in roles, it may be impossible to build a complete list, but as you start to see patterns in requirements, you may find less distinct personas than anticipated.
- Consider a survey to business units to determine what they need if this will solve some immediate problems. If this portion of the project will be deferred, use the data uncovered in the discovery process to identify which software is used by which roles.
- Replacement equipment can have the software footprint created by what was actually utilized by the user, not necessarily what software was installed on the previous device.
A software usage snapshot for an urban planner/engineer.
- Once software needs are determined, use this information to review the appropriate device for each persona.
- Ensure hardware is appropriate for the type of work the user does and supports required software.
- If it is more appropriate for a user to have a tablet, ensure the software they use can be used on any device.
- Review deployment methods to determine if there is any opportunity to improve the imaging or software deployment process with better tools or methodologies.
- Document the device’s location if it will be static, or if the user may be more mobile, add location information for their primary location.
- Think about the best place to document – if this information can be stored in Active Directory and imported to the ITAM database, you can update once and use in multiple applications. But this process is built into your add/move/change workflows.
Maintain a lean library to simplify image management
Simplify, simplify, simplify. Use a minimal number of desktop images and automate as much as you can.
- Embrace minimalism. When it comes to managing your desktop image library, your ultimate goal should be to minimize the manual effort involved in provisioning new desktops.
- Less is more. Try to maintain as few standard desktop images as possible and consider a thin gold image, which can be patched and updated on a regular basis. A thin image with efficient application deployment will improve the provisioning process.
- Standardize and repeat. System provisioning should be a repeatable process. This means it is ripe for standardization and automation. Look at balancing the imaging process with software provisioning, using group policy and deployment tools to reduce time to provision and deliver equipment.
- Outsource where appropriate. Imaging is one of the most employed services, where the image is built in-house and deployed by the hardware vendor. As a minimum, quarterly updates should still be provided to integrate the latest patches into the operating system.
Document the process workflow for hardware deployment
Define the process for deploying hardware to users.
Include the following in your workflow:
- How will equipment be configured and imaged before deployment?
- Which images will be used for specific roles?
- Which assets are assigned to specific roles?
- How will the device status be changed in the ITAM tool once deployed?
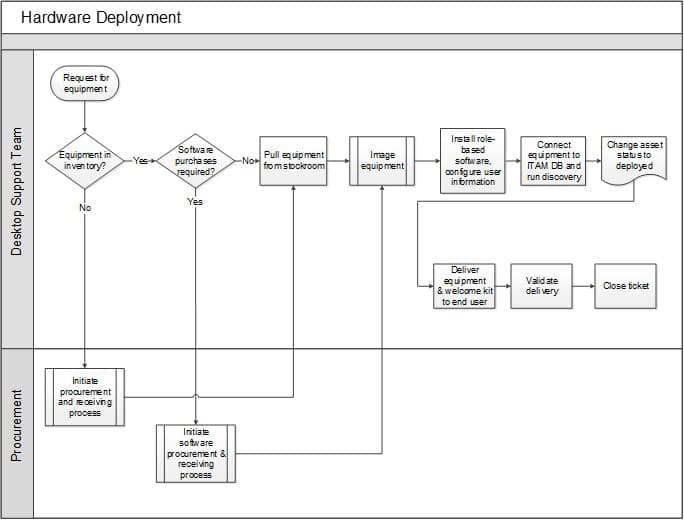
Large-scale deployments should be run as projects, benefitting from economies of scale in each step
Large-scale desktop deployments or data center upgrades will likely be managed as projects.
These projects should include project plans, including resources, timelines, and detailed procedures.
Define the process for large-scale deployment if it will differ from the regular deployment process.
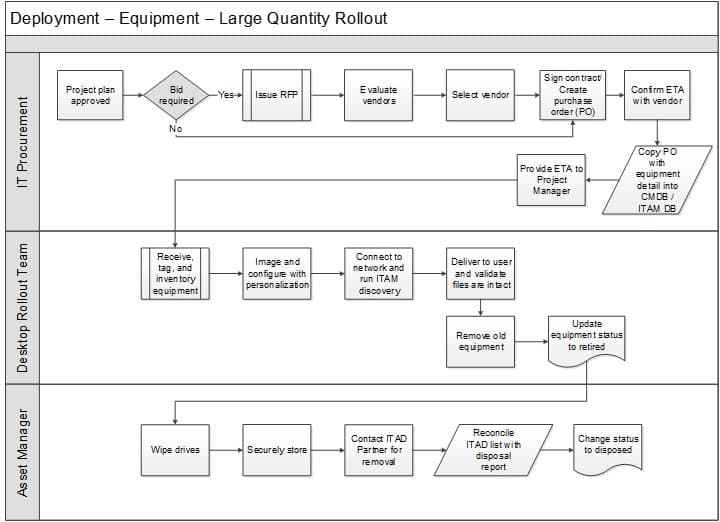
Document the deployment workflow(s)
2.2.3 Document deployment workflows for desktop and large-scale deployment
Participants
- Asset Manager
- Purchasing
- Service Desk Manager
- Operations (optional)
- CFO or other management representative from Finance
Document
Document in the Standard Operating Procedures, Section 9: Deployment
Document each step in the system deployment process with notecards or on a whiteboard. Identify the challenges faced by your organization and strategize potential solutions.
- Outline each step in the process of desktop deployment. Be as granular as possible. On each card, describe the step as well as the individual responsible for it.
- When you are satisfied that each step is accurately captured, use a second color of notecard to document any challenges, inefficiencies, or pains associated with each step. Consider further documenting the time on each task.
- Examine each challenge or pain point. Discuss whether or not there is a clear solution to the problem. If yes, document the solution and amend the workflow. If not, engage in a broader discussion of possible solutions, taking into account people, processes, and available technology.
- Document separately the process for large-scale deployment if required.
Look for opportunities to improve the request and deployment process with better communication and tools
The biggest challenge in deploying equipment is meeting expectations of the business, and without cooperation from multiple departments, this becomes significantly more difficult.
- Work with the procurement and the services team to ensure inventory is accessible, and regularly validate that inventory levels in the ITAM database are accurate.
- Work with the HR department to predict (where possible) anticipated new hires. Plan for inventory ebbs and flows to match the hiring timelines where there are large variations.
- If service catalogs will be made available for communicating options and SLAs for equipment purchases, work with the service catalog administrators to automate inventory checks and notifications. Work with the end-user device managers to set standards and reduce equipment variations to a manageable amount.
- Where deployments are part of equipment refresh, ensure data is up to date for the services team to plan the project rollouts and know which software should be redeployed with the devices.
- Infrastructure and security teams may have specific hardware assets relating to networking, data centers, and security, which may bypass the end-user device workflows but need to be tagged and entered into inventory early in the process. Work with these teams to have their equipment follow the same receiving and inventory processes. Deployment will vary based on equipment type and location.
Automate hardware deployment where users are dispersed and deployment volume is high
Self-serve kiosks (vending machines) can provide cost reductions in delivery of up to 25%. Organizations that have a high distribution rate are seeing reductions in cost of peripherals averaging 30-35% and a few extreme cases of closer to 85%.
Benefits of using vending machines:
- Secure equipment until deployed.
- Equipment can be either purchased by credit card or linked to employee ID cards, enabling secure transactions and reporting.
- Access rights can be controlled in real time, preventing terminated employees from accessing equipment or managing how many devices can be deployed to each user.
- Vending machines can be managed through a cellular or wireless network.
- Technology partners can be tasked with monitoring and refilling vending machines.
- Employees are able to access technology wherever a vending machine can be located rather than needing to travel to the help desk.
- Equipment loans and new employee packages can be managed through vending machines.
Phase 2 Guided Implementation
Call 1-888-670-8889 or email GuidedImplementations@InfoTech.com for more information.Complete these steps on your own or call us to complete a guided implementation. A guided implementation is a series of 2-3 advisory calls that help you execute each phase of a project. They are included in most advisory memberships.
Guided Implementation 2: Request, Procure, Receive, and Deploy
Proposed Time to Completion: 4 weeks
Step 2.1: Request & Procure
Start with an analyst kick-off call:
- Define standard and non-standard hardware.
- Weigh the pros and cons of leasing vs. buying.
- Build the procurement process.
Then complete these activities…
- Define standard hardware requests.
- Document standard hardware request procedure.
- Document procurement workflow.
- Build a purchasing policy.
With these tools & templates:
- Standard Operating Procedures
- Non-Standard Hardware Request Form
- Hardware Procurement Workflow
- Purchasing Policy
Step 2.2: Receive & Deploy
Review findings with analyst:
- Determine appropriate asset tagging method.
- Define equipment receiving process.
- Define equipment deployment process.
Then complete these activities…
- Select appropriate asset tagging method.
- Design workflow for receiving and inventorying equipment.
- Document the deployment workflow(s).
With these tools & templates:
- Standard Operating Procedures
- Equipment Receiving & Tagging Workflow
- Deployment Workflow
Phase 2 Insight: Bridge the gap between IT and Finance to build a smoother request and procurement process through communication and routine reporting. If you’re unable to affect procurement processes to reduce time to deliver, consider bringing inventory onsite or having your hardware vendor keep stock, ready to ship on demand.
If you want additional support, have our analysts guide you through this phase as part of an Info-Tech workshop
Book a workshop with our Info-Tech analysts:
- To accelerate this project, engage your IT team in an Info-Tech workshop with an Info-Tech analyst team.
- Info-Tech analysts will join you and your team onsite at your location or welcome you to Info-Tech’s historic Toronto office to participate in an innovative onsite workshop.
- Contact your account manager (www.infotech.com/account), or email Workshops@InfoTech.com for more information.
The following are sample activities that will be conducted by Info-Tech analysts with your team:
2.1.2 Define standard hardware requests
Divide whiteboard into columns representing core business areas. Define core hardware assets for end users in each division along with optional hardware assets. Discuss optional assets to narrow and define standard equipment requests.
2.2.1 Select appropriate method for tagging and tracking assets
Discuss the various asset tagging methods and choose the tagging method that is most appropriate for your organization. Define the process for tagging assets and document the standard asset tag location according to equipment type.
Phase 3
Maintain and Dispose
Implement Hardware Asset Management
Cisco overcame organizational resistance to change to improve asset security
CASE STUDY
Industry Networking
Source Cisco IT
Challenge
Cisco Systems had created a dynamic work environment that prized individuality. This environment created high employee satisfaction, but it also created a great deal of risk surrounding device security.
Cisco lacked an asset security policy; there were no standards for employees to follow. This created a surplus of not only hardware, but software to support the variety of needs amongst various teams at Cisco.
Solution
The ITAM team at Cisco recognized that their largest problem was the lack of standardization with respect to PCs. Variance in cost, lifecycle, and software needs/compatibility were primary issues.
Cisco introduced a PC leasing program with the help of a PC asset management vendor to correct these issues. The primary goal was to increase on-time returns of PCs. A set life of 30 months was defined by the vendor.
Results
Cisco engaged employees to help contribute to improving its asset management protocols, and the approach worked.
On-time returns increased from 60% to 80%. Costs were reduced due to active tracking and disposal of any owned assets still present.
A reduction in hardware and software platforms has cut costs and increased security thanks to improved tracking capabilities.
This case study continues in phase 4
Step 3.1: Manage, Maintain, and Secure Hardware Assets
Phase 3: Maintain & Dispose
3.1 Manage & Maintain
3.2 Dispose or Redeploy
This step will walk you through the following activities:
3.1.1 Build a MAC policy and request form
3.1.2 Build workflows to document user MAC processes
3.1.3 Design process and policies for hardware maintenance, warranty, and support documentation handling
3.1.4 Revise or create an asset security policy
This step involves the following participants:
- Asset Manager
- Service Desk Manager
- Operations (optional)
- Security Department
Step Outcomes
- Understanding of inventory management process best practices
- Templates for move/add/change request policy and form
- Documented process workflows for the user move/add/change process
- Process and policies for hardware maintenance, warranty, and support documentation handling
- Defined policies for maintaining asset security
Determine methods for performing inventory audits on equipment
Auto-discovery
- Auto-discovery tools will be crucial to the process of understanding what equipment is connected to the network and in use.
- The core functionality of discovery tools is to scan the environment and collect configuration data from all connected assets, but most tools can also be used to collect usage data, network monitoring, and software asset management data including software distribution, compliance, and license information.
- These tools may not connect to peripheral devices such as monitors and external drives, will not scan devices that are turned off or disconnected from the network, may not inventory remote users, and will rarely provide location information. This often results in a need to complete physical audits as well.
Info-Tech Insight
One of the most common mistakes we see when it comes to asset management is to assume that the discovery tool will discovery most or all of your inventory and do all the work. It is better to assume only 80-90% coverage by the discovery tool and build ownership records to uncover the unreportable assets that are not tied into the network.
Physical audit
- The physical audit can be greatly improved with barcode, RFID, or QR codes, allowing items to be scanned, records opened, then updated.
- If not everything is tagged or entered into the ITAM database, then searching closets, cabinets, and desk drawers may be required to tag and enter those devices into the database.
- Provide the inventory team with exact instructions on what needs to be collected, verified, and recorded. Depending on the experience and thoroughness of the team, spot checks early in the process may alleviate quality issues often discovered at the end of the inventory cycle.
Determine requirements for performing inventory audits on equipment
Conduct an annual hardware audit to ensure hardware is still assigned to the person and location identified in your ITAM system, and assess its condition.
Perform a quarterly review of hardware stock levels in order to ensure all equipment is relevant and usable. The table below is an example of how to organize this information.
| Item | Target Stock Levels | Estimated $ Value |
|---|---|---|
| Desktop computers | ||
| Standard issue laptops | ||
| Mice | ||
| Keyboards | ||
| Network cables | ||
| Phones |
Info-Tech Insight
Don’t forget about your remotely deployed assets. Think about how you plan to inventory remotely deployed equipment. Some tools will allow data collection through an agent that will talk to the server over the internet, and some will completely ignore those assets or provide a way to manually collect the data and email back to the asset manager. Mobile device management tools may also help with this inventory process. Determine what is most appropriate based on the volume of remote workers and devices.
Build an inventory management process to maintain an accurate view of owned hardware assets
- Your inventory should capture which assets are on hand, where they are located, and who owns them, at minimum. Maintaining an accurate, up-to-date view of owned hardware assets allows you to see at any time the actual state of the components that make up your infrastructure across the enterprise.
- Automated inventory practices save time and effort from doing physical inventories and also reduce the interruption to business users while improving accuracy of data.
- If you are just starting out, define the process for conducting an inventory of deployed assets, and then define the process for regular upkeep and audit of inventory data.
Inventory Methods
- Electronic – captures networked asset information only and can be deployed over the network with no deskside service interaction.
- Physical – captures environmental detail and must be performed manually by a service technician with possible disruption to users.
- Full inventory – both physical and electronic inventory of assets.
Internal asset information to collect electronically
- Hardware configuration
- Installed software
- Operating system
- System BIOS
- Network configuration
- Network drive mappings
- Printer setups
- System variables
External asset information that cannot be detected electronically
- Assigned user
- Associated assets
- Asset/user location
- Usage of asset
- Asset tag number
IMAC (Install, Move, Add, Change) services will form the bulk of asset management work while assets are deployed
IMAC services are usually performed at a user’s deskside by a services technician and can include:
- Installing new desktops or peripherals
- Installing or modifying software
- Physically moving an end user’s equipment
- Upgrading or adding components to a desktop
Specific activities may include:
Changes
- Add new user IDs
- Manage IDs
- Network changes
- Run auto-discovery scan
Moves
- Perform new location site survey
- Coordinate with facilities
- Disconnect old equipment
- Move to new location
- Reconnect at new location
- Test installed asset
- Obtain customer acceptance
- Close request
Installs and Adds
- Perform site survey
- Perform final configuration
- Coordinate with Facilities
- Asset tagging
- Transfer data from old desktop
- Wipe old desktop hard drive
- Test installed asset
- Initiate auto-discovery scan
- Obtain customer acceptance
- Close request
A strong IMAC request process will lessen the burden on IT asset managers
- When assets are actively in use, Asset Managers must also participate in the IMAC (Install-Move-Add-Change) process and ensure that any changes to asset characteristics or locations are updated and tracked in the asset management tool and that the value and usefulness of the asset is monitored.
- The IMAC process should not only be reactive in response to requests, but proactive to plan for moves and relocations during any organizational change events.
Recommendations:
Automate. Wherever possible, use tools to automate the IMAC process.
E-forms, help desk, ticketing, or change management software can automate the request workflow by allowing the requestor to submit a request ticket that can then be automatically assigned to a designated team member according to the established chain of command. As work is completed, the ticket can be updated, and the requestor will be able to check the status of the work at any time.
Communicate the length of any downtime associated with execution of the IMAC request to lessen the frustration and impatience among users.
Involve HR. When it comes to adding or removing user accounts, HR can be a valuable resource. As most new employees should be hired through HR, work with them to improve the onboarding process with enough advanced notice to set up accounts and equipment. Role changes with access rights and software modifications can benefit from improved communications. Review the termination process as well, to secure data and equipment.
Build a MAC request policy and form for end users
A consistent Move, Add, Change (MAC) request process is essential for lessening the burden on the IT department. MAC requests are used to address any number of tasks, including:
- Relocation of PCs and/or peripherals.
- New account setup.
- Hardware or software upgrades.
- Equipment swaps or replacements.
- User account/access changes.
- Document generation.
- User acceptance testing.
- Vendor coordination.
Create a request form.
If you are not using help desk or other ticketing software, create a request template that must be submitted for each MAC. The request should include:
- The name and department of the requester.
- The date of the request.
- Severity of the request. For example, severity can be graded on a score of high, medium, or low where high represents a mission-critical change that could compromise business continuity if not addressed immediately, and low represents a more cosmetic change that will not negatively affect operations. The severity of the request can be determined by the service-level agreement (SLA) associated with the service.
- Date the request must be completed by. Or at least, what would be the ideal date for completion. This will vary greatly depending on the severity of the request. For example, deleting the access of a terminated employee would be very time sensitive.
- Item or service to be moved, added, or changed. Include location, serial number, or other designated identifier where possible.
- If the item or service is to be moved, indicated where it is being moved.
- It is a good idea to include a comments section where the requester can add any additional questions or details.
Use Info-Tech’s templates to build your MAC policy and request form
3.1.1 Build a MAC policy and request form
Desktop Move/Add/Change Policy
This desktop move/add/change policy should be put in place to mitigate the risk associated with unauthorized changes, minimize disruption to the business, IT department, and end users, and maintain consistent expectations.
Move, Add, Change Request Form
Help end users navigate the move/add/change process. Use the Move/Add/Change Request Form to increase efficiency and organization for MAC requests.
Document the process for user equipment moves
Include the following in your process documentation:
- How and when will any changes to user or location information be made in the ITAM tool?
- Will any changes in AD automatically update in the ITAM tool?
- How should requests for equipment moves or changes be made?
- How will resources be scheduled?
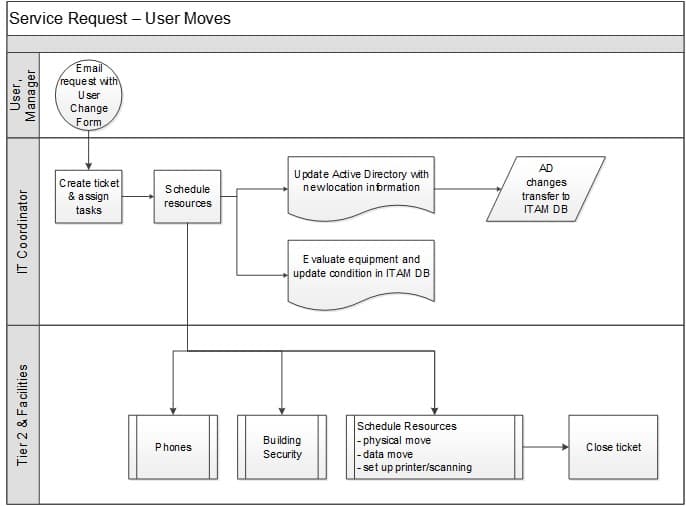
Build workflows to document user MAC processes
3.1.2 Build MAC process workflows
Participants
- Asset Manager
- Service Desk Manager
- Operations (optional)
Document
Document in the Standard Operating Procedures, Section 10: Equipment Install, Adds, Moves, and Changes
Document each step in the system deployment process using notecards or on a whiteboard. Identify the challenges faced by your organization and strategize potential solutions.
- Outline each step in the process of desktop deployment. Be as granular as possible. On each card, describe the step as well as the individual responsible for each step.
- When you are satisfied that each step is accurately captured, use a second color of notecard to document any challenges, inefficiencies, or pains associated with each step. Consider further documenting the time on each task.
- Examine each challenge or pain point. Discuss whether or not there is a clear solution to the problem. If so, document the solution and amend the workflow. If not, engage in a broader discussion of possible solutions, taking into account people, processes, and available technology.
- Document separately the process for large-scale deployment if required.
Define a policy to ensure effective maintenance of hardware assets
Effective maintenance and support of assets provides longer life, higher employee productivity, and increased user satisfaction.
- Your asset management documentation and database should store equipment maintenance contract information so that it can be consulted whenever hardware service is required.
- Record who to contact as well as how, warranty information, and any SLAs that are associated with the maintenance agreement.
- Record all maintenance that hardware equipment receives, which will be valuable for evaluating asset and supplier performance.
- In most cases, the Service Desk should be the central point of contact for maintenance calls to all suppliers.
Sample equipment maintenance policy terms:
- Maintenance and support arrangements are required for all standard and non-standard hardware.
- All onsite hardware should be covered by onsite warranty agreements with appropriate response times to meet business continuity needs.
- Defective items under warranty should be repaired in a timely fashion.
- Service, maintenance, and support shall be managed through the help desk ticketing system.
Design process and policies for hardware maintenance, warranty, and support documentation handling
3.1.3 Design process for hardware maintenance
Participants
- Asset Manager
- Purchasing
- Service Desk Manager
- Security
- Operations (optional)
Document
Document in the Standard Operating Procedures, Section 10
- Discuss and document the policy for hardware maintenance, warranty, and support.
- Key outcomes should include:
- Who signs off on policies?
- What is the timeline for documentation review?
- Where are warranty and maintenance documents stored?
- How will equipment be assessed for condition during audits?
- How often will deployed equipment be reimaged?
- How will equipment repair needs be requested?
- How will repairs for equipment outside warranty be handled?
Use your HAM program to improve security and meet regulatory requirements
ITAM complements and strengthens security tools and processes, improving the company’s ability to protect its data and systems and reduce operational risk.
It’s estimated that businesses worldwide lose more than $221 billion per year as a result of security breaches. HAM is one important factor in securing data, equipment investment, and meeting certain regulatory requirements.
How does HAM help keep your organization secure?
- Educating users on best practices for securing their devices, and providing physical security such as cable locks and tracking mechanisms.
- Best practices for reporting lost or stolen equipment for quickly removing access and remotely wiping devices.
- Accurate location and disposal records will enable accurate reporting for HIPAA and PCI DSS audits where movement of media or hardware containing data is a requirement. Best practices for disposal will include properly wiping drives, recording information, and ensuring equipment is disposed of according to environmental regulations.
- Secure access to data through end-user mobile devices. Use accurate records and MDM tools to securely track, remove access, and wipe mobile devices if compromised.
- Encrypt devices that may be difficult to track such as USB drives or secure ports to prevent data from being copied to external drives.
- Managed hardware allows software to be managed and patched on a regular basis.
Best Practices
- Educate end users about traveling with equipment. Phones and laptops are regularly stolen from cars; tablets and phones are left on planes. Encourage users to consider how they store equipment on the way home from work.
- Cable locks used at unsecured offsite or onsite work areas should be supplied to employees.
- Equipment stored in IT must be secured at all times.
Implement mobile device management (MDM) solutions
Organizations with a formal mobile management strategy have fewer problems with their mobile devices.
Develop a secure MDM to:
- Provide connection and device support when the device is fully subsidized by the organization to increase device control.
- Have loaner devices for when traveling to limit device theft or data loss.
- Personal devices not managed by MDM should be limited to internet access on a guest network.
- Limit personal device access to only internet access or a limited zone for data access and a subset of applications.
- Advanced MDM platforms provide additional capabilities including containerization.
The benefits of a deployed MDM solution:
- Central management of a variety of devices and platforms is the most important advantage of MDM. Administrators can gain visibility into device status and health, set policies to groups of users, and control who has access to what.
- Security features such as enforcing passcodes and remote wipe are also essential, given the increased risk of mobile devices.
- Remote wipe should be able to wipe either the whole device or just selected areas.
- Separation of personal data is becoming increasingly important as BYOD becomes the norm. This is a feature that vendors are approaching radically differently.
- Device lock: Be able to lock the device itself, its container, or its SIM. Even if the SIM is replaced, the device should still remain locked. Consider remote locking a device if retrieval is possible.
Mobile device management is constantly evolving to incorporate new features and expand to new control areas. This is a high-growth area that warrants constant up-to-date knowledge on the latest developments.
What can be packed into an MDM can vary and be customized in many forms for what your organization needs.
Secure endpoint devices to protect the data you cannot control
Endpoint Encryption
| Endpoints | Average | None |
|---|---|---|
| Desktop | 73% | 4% |
| Laptops | 65% | 9% |
| Smartphones | 27% | 28% |
| Netbooks | 26% | 48% |
| Tablets | 16% | 59% |
| Grand average | 41% |
Benefits from endpoint encryption:
- Reduced risk associated with mobile workers.
- Enabled sharing of data in secured workspace.
- Enhanced end-user accountability.
- Reduced number of data breach incidents.
- Reduced number of regulatory violations.
Ways to reduce endpoint encryption costs:
- Use multiple vendors (multiple platforms): 33%
- Use a single vendor (one platform): 40%
- Use a single management console: 22%
- Outsource to managed service provider: 26%
- Permit user self-recovery: 26%
Remote Wiping
- If all else fails, a device can always be erased of all its data, protecting sensitive data that may have been on it.
- Selective wipe takes it a step further by erasing only sensitive data.
Selective wipe is not perfect.
It is nearly impossible to keep the types of data separate, even with a sandbox approach. Selective wipe will miss some corporate data, and even a full remote wipe can only catch some of users’ increasingly widely distributed data.
Selective wipe can erase:
- Corporate profiles, email, and network settings.
- Data within a corporate container or other sandbox.
- Apps deployed across the enterprise.
Know when to perform a remote wipe.
Not every violation of policy warrants a wipe. Playing Candy Crush during work hours probably does not warrant a wipe, but jail breaking or removing a master data management client can open up security holes that do warrant a wipe.
Design an effective asset security policy to protect the business
Data security is not simply restricted to compromised software. In fact, 70% of all data breaches in the healthcare industry since 2010 are due to device theft or loss, not hacking. (California Data Breach Report – October, 2014) ITAM is not just about tracking a device, it is also about tracking the data on the device.
Organizations often struggle with the following with respect to IT asset security:
- IT hardware asset removal control.
- Personal IT hardware assets (BYOD).
- Data removal from IT hardware assets.
- Inventory control with respect to leased hardware and software.
- Unused software.
- Repetitive versions of software.
- Unauthorized software.
Your security policy should seek to protect IT hardware and software that:
- Have value to the business.
- Require ongoing maintenance and support.
- Create potential risk in terms of financial loss, data loss, or exposure.
These assets should be documented and controlled in order to meet security requirements.
The asset security policy should encompass the following:
- Involved parties.
- Hardware removal policy/documentation procedure.
- End-user asset security responsibilities.
- Theft/loss reporting procedure.
- BYOD standards, procedures, and documentation requirements.
- Data removal.
- Software usage.
- Software installation.
Info-Tech Insight
Hardware can be pricey; data is priceless. The cost of losing a device is minimal compared to the cost of losing data contained on a device.
Revise or create an asset security policy
3.1.4 Develop IT asset security policy
Participants
- CIO or IT Director
- Asset Manager
- Service Desk Manager
- Security
- Operations (optional)
Document
Document in the Asset Security Policy.
- Identify asset security challenges within your organization. Record them in a table like the one below.
| Challenge | Current Security Risk | Target Policy |
|---|---|---|
| Hardware removal | Secure access and storage, data loss | Designated and secure storage area |
| BYOD | No BYOD policy in place | N/A → phasing out BYOD as an option |
| Hardware data removal | Secure data disposal | Data disposal, disposal vendor |
| Unused software | Lack of support/patching makes software vulnerable | Discovery and retirement of unused software |
| Unauthorized software | Harder to track, less secure | Stricter stance on pirated software |
- Brainstorm the reasons for why these challenges exist.
- Identify target policy details that pertain to each challenge. Record the outcomes in section(s) 5.1, 5.2, or 5.3 of the Asset Security Policy.
Poor asset security and data protection had costly consequences for UK Ministry of Justice
CASE STUDY
Industry Legal
Source ICO
Challenge
The Ministry of Justice (MoJ) in the UK had a security problem: hard drives that contained sensitive prisoner data were unencrypted and largely unprotected for theft.
These hard drives contained information related to health, history of drug use, and past links to organized crime.
After two separate incidents of hard drive theft that resulted in data breaches, the Information Commissioner’s Office (ICO), stepped in.
Solution
It was determined that after the first hard drive theft in October 2011, replacement hard drives with encryption software were provisioned to prisons managed by the MoJ.
Unfortunately, the IT security personnel employed by the MoJ were unaware that the encryption software required manual activation.
When the second hard drive theft occurred, the digital encryption could not act as a backup to poor physical security (the hard drive was not secured in a locker as per protocol).
Results
The perpetrators were never found and the stolen hard drives were never recovered.
As a result of the two data breaches, the MoJ had to implement costly security upgrades to its data protection system.
The ICO fined the MoJ £180,000 for its repeated security breaches. This costly fine could have been avoided if more diligence was present in the MoJ’s asset management program.
Step 3.2: Dispose or Redeploy Assets
3.1 Manage & Maintain
3.2 Dispose or Redeploy
This step will walk you through the following activities:
3.2.1 Identify challenges with IT asset recovery and disposal
3.2.2 Design hardware asset recovery and disposal workflows
3.2.3 Build a hardware asset disposition policy
This step involves the following participants:
- Infrastructure Director/Manager
- Asset Manager
- Service Desk Manager
- Operations (optional)
Step Outcomes:
- Defined process to determine when to redeploy vs. dispose of hardware assets
- Process for recovering and redeploying hardware equipment
- Process for safely disposing of assets that cannot be redeployed
- Comprehensive asset disposition policy
Balance the effort to roll out new equipment against the cost to maintain equipment when building your lifecycle strategy
 $500MM); and orange is Overall.">
$500MM); and orange is Overall.">
(Info-Tech Research Group; N=96)
Determining the optimal length of time to continue to use equipment will depend on use case and equipment type
| Budget profiles | Refresh methods |
|---|---|
|
Stretched Average equipment age: 7+ years |
To save money, some organizations will take a cascading approach, using the most powerful machines for engineers or scientists to ensure processing power, video requirements and drives will meet the needs of their applications and storage needs; then passing systems down to departments who will require standard-use machines. The oldest and least powerful machines are either used as terminals or disposed. |
|
Generous Average equipment age: 3 years |
Organizations that do not want to risk user dissatisfaction or potential compatibility or reliability issues will take a more aggressive replacement approach. These organizations often have less people assigned to end-user device maintenance and will not repair equipment outside of warranty. There is little variation in processing power among devices, with major differences determined by mobility and operating system. |
|
Cautious Average equipment age: 4 to 5 years |
Organizations that fit between the other two profiles will look to stretch the budget beyond warranty years, but will keep a close eye on maintenance requirements. Repairs needed outside of warranty will require an eye to costs, efforts, and subsequent administrative work of loaning equipment to keep the end user productive while waiting on service. Recommendations to keep users happy and equipment in prime form is to check condition at the 2-3 year mark, reimage at least once to improve performance, and have backup machines, if equipment starts to become problematic. |
Build a process to determine when and how to redeploy or dispose of hardware assets at end of use
- When equipment is no longer needed for the function or individual to whom it was assigned, the Hardware Asset Manager needs to use data to ensure the right decision is made as to what to do with the asset.
- End of use involves evaluating options for either continuing to use the equipment in another capacity or by another individual or determining that the asset has no remaining value to the organization in any capacity and it is time to retire it.
- If the asset is retired, it may still have capacity for continued use outside of the organization or it may be disposed.
Redeployment
- Deliver the asset to a new user if it is no longer needed by the original user but still has value and usability.
- Redeployment saves money and prevents unnecessary purchases.
- Common when employees leave the company or a merge or acquisition changes the asset pool.
VS.
Disposal
- When an asset is no longer of use to the organization, it may be disposed of.
- Need to consider potential financial and public relations considerations if disposal is not done according to environmental legislation.
- Need to ensure proper documentation and data removal is built into disposition policy.
Use persistent documentation and communication to improve hardware disposal and recovery
Warning! Poor hardware disposal and recovery practices can be caused by the following:
- Your IT team is too busy and stretched thin. Data disposal is one of many services your IT team is likely to have to deal with, but this service requires undivided attention. By standardizing hardware refreshes, you can instill more predictability with your hardware life cycles and better manage disposal.
- Poor inventory management. Outdated data and poor tracking practices can result in lost assets during the disposal phase. It only takes a single lost asset to cause a disastrous data breach in your supply chain.
- Obliviousness to disposal regulations. Electronic disposal and electronically stored data are governed by strict regulation.
How do you improve your hardware disposal and recovery process?
- A specific, controlled process needs to be in place to wipe all equipment and verify that it’s been wiped properly. Otherwise, companies will continue to spend money to protect data while equipment is in use, but overlook the dangerous implications of careless IT asset disposal. Create a detailed documentation process to track your assets every step of the way to ensure that data and applications are properly disposed of. Detailed documentation can also help bolster sustainability reporting for organizations wishing to track such data.
- Better communication should be required. Most decommissioning or refresh processes use multiple partners for manufacturing, warehousing, data destruction, product resale, and logistics. Setting up and vetting these networks can take years, and even then, managing them can be like playing a game of telephone; transparency is key.
Address three core challenges of asset disposal and recovery
Asset Disposal
Data Security
Sixty-five percent of organizations cite data security as their top concern. Many data breaches are a result of hardware theft or poor data destruction practices.
Choosing a reputable IT disposal company or data removal software is crucial to ensuring data security with asset disposal.
Environmental
Electronics contain harmful heavy metals such as mercury, arsenic, and cadmium.
Disposal of e-waste is heavily regulated, and improper disposal can result in hefty fines and bad publicity for organizations.
Residual value
Many obsolete IT assets are simply confined to storage at their end of life.
This often imposes additional costs with maintenance or storage fees and leaves a lot of value on the table through assets that could be sold or re-purposed within the organization.
Identify challenges with IT asset recovery and disposal with a triple bottom line scorecard
3.2.1 Identify challenges with IT asset recovery and disposal
Participants
- Infrastructure Director/Manager
- Asset Manager
- Service Desk Manager
- Operations (optional)
- Divide the whiteboard into three boxes: Social, Economic, and Environmental.
- Divide each box into columns like the one shown below:
| Economic | |||
|---|---|---|---|
| Challenge | Objectives | Targets | Initiatives |
| No data capture during disposal | Develop reporting standards | 80% disposed assets recorded | Work with Finance to develop reporting procedure |
| Idle assets | Find resale market/dispose of idle assets | 50% of idle assets disposed of within the year | Locate resale vendor and disposal service |
- Ask participants to list challenges associated with each area.
- Once challenges facing recovery and disposal have been exhausted from the group, assign a significance of 1-5 (1 being the lowest and 5 being the highest) to each challenge.
- Discuss the most significant challenges and how they might be addressed through the next steps of building recovery & disposal processes.
Build a process for recovery and redeployment of hardware
- Having hardware standards in place makes redeploying easier by creating a larger pool of possible users for a standardized asset.
- Most redeployment activities will be carried out by the Help Desk as a service request ticket, so it is important to have clear communication and guidelines with the Help Desk as to which tasks need to be carried out as part of the request.
Ensure the following are addressed:
- Where will equipment be stored before being redeployed?
- Will shipping be required and are shipping costs factored into analysis?
- Ensure equipment is cleaned before it is redeployed.
- Do repairs and reconfigurations need to be made?
- How will software be removed and licenses harvested and reported to Software Asset Manager?
- How will data be securely wiped and protected?
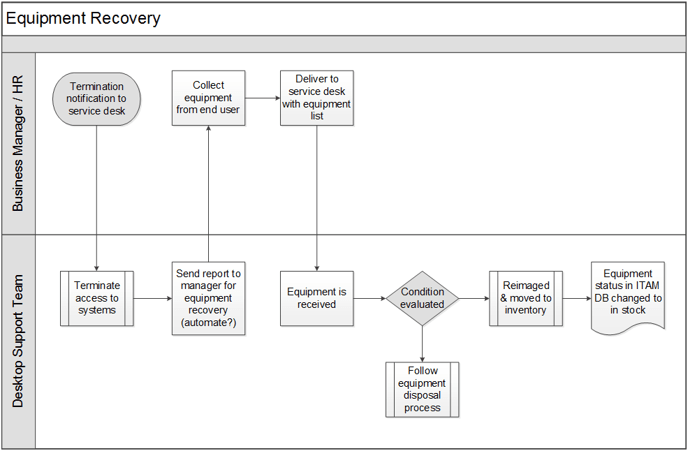
Define the process for safely disposing of assets that cannot be redeployed
Asset Disposal Checklist
- Review the data stored on the device.
- Determine if there has been any sensitive or confidential information stored.
- Remove all sensitive/confidential information.
- Determine if software licenses are transferable.
- Remove any non- transferable software prior to reassignment.
- Update the department’s inventory record to indicate new individual assigned custody.
- In the event of a transfer to another department, remove data and licensed software.
- If sensitive data has been stored, physically destroy the storage device.
- Define the process for retiring and disposing of equipment that has reached replacement age or no longer meets minimum conditions or standards.
- Clearly define the steps that need to be taken both before and after the involvement of an ITAD partner.
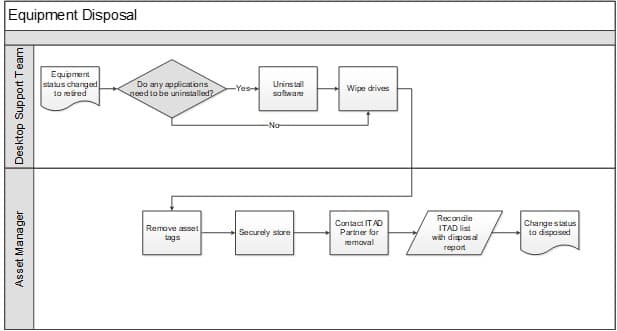
Design hardware asset recovery and disposal workflows
3.2.2 Design hardware asset recovery and disposal policies and workflows
Participants
- Infrastructure Director/Manager
- Asset Manager
- Service Desk Manager
- Operations (optional)
Document
Document in the Standard Operating Procedures, Sections 11 and 12
Document each step in the recovery and disposal process in two separate workflows using notecards or on a whiteboard. Identify the challenges faced by your organization and strategize potential solutions.
- Keeping in mind current challenges around hardware asset recovery and disposal, design the target state for both the asset recovery and disposal processes.
- Outline each step of the process and be as granular as possible.
- When you are satisfied that each step is accurately captured, use a second color of notecard to document any challenges, inefficiencies, or pains associated with each step. Consider further documenting the time on each task.
- Examine each challenge or pain point. Discuss whether or not there is a clear solution to the problem. If so, document the solution and amend the workflow. If not, engage in a broader discussion of possible solutions, taking into account people, processes, and available technology.
- Review the checklists on the previous slides to ensure all critical tasks are accounted for in your process workflows.
Add equipment disposition to asset lifecycle decisions to meet environmental regulations and mitigate risk
Although traditionally an afterthought in asset management, IT asset disposition (ITAD) needs to be front and center. Increase focus on data security and concern surrounding environmental sustainability and develop an awareness of the cost efficiencies possible through best-practices disposition.
Optimized ITAD solutions:
- Protect sensitive or valuable data
- Support sustainability
- Focus on asset value recovery
Info-Tech Insight
A well-thought-out asset management program mitigates risk and is typically less costly than dealing with a large-scale data loss incident or an inappropriate disposal suit. Also, it protects your company’s reputation – which is difficult to put a price on.
Partner with an ITAD vendor to support your disposition strategy
Maximizing returns on assets requires knowledge and skills in asset valuation, upgrading to optimize market return, supply chain management, and packaging and shipping. It’s unlikely that the return will be adequate to justify that level of investment, so partnering with a full-service ITAD vendor is a no-brainer.
- An ITAD vendor knows the repurpose and resale space better than your organization. They know the industry and have access to more potential buyers.
- ITAD vendors can help your organization navigate costly environmental regulations for improper disposal of IT assets.
Disposal doesn’t mean your equipment has to go to waste.
Additionally, your ITAD vendor can assist with a large donation of hardware to a charitable organization or a school.
Donating equipment to schools or non-profits may provide charitable receipts that can be used as taxable benefits.
Before donating:
- Ensure equipment is needed and useful to the organization.
- Be prepared for an appraisal requirement. Receipts can only be issued for fair market value.
- Prevent compromised data by thoroughly wiping or completely replacing drives.
- Ensure official transfer of ownership to prevent liability if improper disposal practices follow.
Info-Tech Insight
Government assistance grants may be available to help keep your organization’s hardware up to date, thereby providing incentives to upgrade equipment while older equipment still has a useful life.
Protect the organization by sufficiently researching potential ITAD partners
Research ITAD vendors as diligently as you would primary hardware vendors.
Failure to thoroughly investigate a vendor could result in a massive data breach, fines for disposal standards violations, or a poor resale price for your disposed assets. Evaluate vendors using questions such as the following:
- Are you a full-service vendor or are you connected to a wholesaler?
- Who are your collectors and processors?
- How do you handle data wiping? If you erase the data, how many passes do you perform?
- What do you do with the e-waste? How much is reused? How much is recycled?
- Do you have errors and omissions insurance in case data is compromised?
- How much will it cost to recycle or dispose of worthless equipment?
- How much will I receive for assets that still have useful life?
ITAD vendors that focus on recycling will bundle assets to ship to an e-waste plant – leaving money on the table.
ITAD vendors with a focus on reuse will individually package salable assets for resale – which will yield top dollars.
Info-Tech Insight
To judge the success of a HAM overhaul, you need to establish a baseline with which to compare final results. Be sure to take HAM “snapshots” before ITAD partnering so it’s easy to illustrate the savings later.
Work with ITAD partner or equipment supplier to determine most cost-effective method and appropriate time for disposal
2-4 Two-to-four year hardware refresh cycle
- Consider selling equipment to an ITAD partner who specializes in sales of refurbished equipment.
- Consider donating equipment to schools or non-profits, possibly using an ITAD partner who specializes in refurbishing equipment and managing the donation process.
5-7 Five-to-seven year hardware refresh cycle
- At this stage equipment may still have a viable life, but would not be appropriate for school or non-profit donations, due to a potentially shorter lifespan. Consider selling equipment to an ITAD partner who has customers interested in older, refurbished equipment.
7+ Seven or more years hardware refresh cycle
- If keeping computers until they reach end of life, harvest parts for replacement on existing machines and budget for disposal fees.
- Ask new computer supplier about disposal services or seek out ITAD partner who will disassemble and dispose of equipment in an environmentally responsible manner.
Info-Tech Insight
- In all cases, ensure hard drives are cleansed of data with no option for data recovery. Many ITAD partners will provide a drive erasure at DoD levels as part of their disposal service.
- Many ITAD partners will provide analysts to help determine the most advantageous time to refresh.
Ensure data security and compliance by engaging in reliable data wiping before disposition
Failure to properly dispose of data can not only result in costly data breaches, but also fines and other regulatory repercussions. Choosing an ITAD vendor or a vendor that specializes in data erasure is crucial. Depending on your needs, there are a variety of data wiping methods available.
Certified data erasure is the only method that leaves the asset’s hard drive intact for resale or donation. Three swipes is the bare minimum, but seven is recommended for more sensitive data (and required by the US Department of Defense). Data erasure applications may be destructive or non-destructive – both methods overwrite data to make it irretrievable.
Physical destruction must be done thoroughly, and rigorous testing must be done to verify data irretrievability. Methods such as hand drilling are proven to be unreliable.
Degaussing uses high-powered magnets to erase hard drives and makes them unusable. This is the most expensive option; degaussing devices can be purchased or rented.
Info-Tech Best Practice
Data wiping can be done onsite or can be contracted to an ITAD partner. Using an ITAD partner can ensure greater security at a more affordable price.
Make data security a primary driver of asset disposition practices
It is estimated that 10-15% of data loss cases result from insecure asset disposal. Protect yourself by following some simple disposition rules.
- Reconcile your data onsite
- Verify that bills of landing and inventory records match before assets leave. Otherwise, you must take the receiver’s word on shipment contents.
- Do at least one in-house data wipe before the assets leave the site for greater data security.
- Prompt shipment will minimize involvement with the assets, and therefore, cost. Also, the chance of missing assets will drop dramatically.
- Reputable ITAD companies maintain strict chain of custody control over assets. Using a third party introduces unnecessary risk.
- Records will protect you in the event of an audit, a data loss incident, or an environmental degradation claim. They could save you millions.
- Don’t forget cell phones, fax machines, USB drives, scanners, and printers – they can carry sensitive information that can put the organization at risk.
- You are never completely out of danger with regards to liability, but partnering with an insured vendor is potent risk mitigation.
Work these rules into your disposition policy to mitigate data loss risk.
Support your HAM efforts with a comprehensive disposition policy
3.2.3 Build a Hardware Asset Disposition Policy
Implementation of a HAM program is a waste of time if you aren’t going to maintain it. Maintenance requires the implementation of detailed policies, training, and an ongoing commitment to proper management.
Use Info-Tech’s Hardware Asset Disposition Policy to:
- Establish and define clear standards, procedures, and restrictions surrounding disposition.
- Ensure continual compliance with applicable data security and environmental legislation.
- Assign specific responsibilities to individuals or groups to ensure ongoing adherence to policy standards and that costs or benefits are in line with expectations.
Phase 3 Guided Implementation
Call 1-888-670-8889 or email GuidedImplementations@InfoTech.com for more information.
Complete these steps on your own or call us to complete a guided implementation. A guided implementation is a series of 2-3 advisory calls that help you execute each phase of a project. They are included in most advisory memberships.
Guided Implementation 3: Maintain & Dispose
Proposed Time to Completion: 4 weeks
Start with an analyst kick-off call:
- Discuss inventory management best practices.
- Build process for moves, adds, and changes.
- Build process for hardware maintenance.
- Define policies for maintaining asset security.
Then complete these activities…
- Build a MAC policy and request form.
- Build workflows to document user MAC processes.
- Design processes and policies for hardware maintenance, warranty, and support documentation handling.
- Build an asset security policy.
With these tools & templates:
- Standard Operating Procedures
- Asset Security Policy
Step 3.2: Dispose or Redeploy Assets
Review findings with analyst:
- Discuss when to dispose vs. redeploy assets.
- Build process for redeploying vs. disposing of assets.
- Review ITAD vendors.
Then complete these activities…
- Identify challenges with IT asset recovery and disposal.
- Design hardware asset recovery and disposal workflows.
- Build a hardware asset disposition policy.
With these tools & templates:
- Standard Operating Procedures
- Asset Recovery Workflow
- Asset Disposal Workflow
- Hardware Asset Disposition Policy
Phase 3 Insight: Not all assets are created equal. Taking a blanket approach to asset maintenance and security is time consuming and costly. Focus on the high-cost, high-use, and data-sensitive assets first.
If you want additional support, have our analysts guide you through this phase as part of an Info-Tech workshop
Book a workshop with our Info-Tech analysts:
- To accelerate this project, engage your IT team in an Info-Tech workshop with an Info-Tech analyst team.
- Info-Tech analysts will join you and your team onsite at your location or welcome you to Info-Tech’s historic Toronto office to participate in an innovative onsite workshop.
- Contact your account manager (www.infotech.com/account), or email Workshops@InfoTech.com for more information.
The following are sample activities that will be conducted by Info-Tech analysts with your team:
3.1.4 Revise or create an asset security policy
Discuss asset security challenges within the organization; brainstorm reasons the challenges exist and process changes to address them. Document a new asset security policy.
3.2.2 Design hardware asset recovery and disposal workflows
Document each step in the hardware asset recovery and disposal process, including all decision points. Examine challenges and amend the workflow to address them.
Phase 4
Plan Budget Process and Build Roadmap
Implement Hardware Asset Management
Cisco deployed an enterprise-wide re-education program to implement asset management
CASE STUDY
Industry Networking
Source Cisco IT
Challenge
Even though Cisco Systems had designed a comprehensive asset management program, implementing it across the enterprise was another story.
An effective solution, complete with a process that could be adopted by everyone within the organization, would require extensive internal promotion of cost savings, efficiencies, and other benefits to the enterprise and end users.
Cisco’s asset management problem was as much a cultural challenge as it was a process challenge.
Solution
The ITAM team at Cisco began discussions with departments that had been tracking and managing their own assets.
These sessions were used as an educational tool, but also as opportunities to gather internal best practices to deploy across the enterprise.
Eventually, Cisco introduced weekly meetings with global representation to encourage company-wide communication and collaboration.
Results
“By establishing a process for managing PC assets, we have cut our hardware costs in half.” – Mark Edmonson, Manager – IT Services Expenses
Cisco reports that although change was difficult to adopt, end-user satisfaction has never been higher. The centralized asset management approach has resulted in better contract negotiations through better data access.
A reduced number of hardware and software platforms has streamlined tracking and support, and will only drive down costs as time goes on.
Step 4.1: Plan Hardware Asset Budget
Phase 4: Plan Budget & Build Roadmap
4.1 Plan Budget
4.2 Communicate & Build Roadmap
This step will walk you through the following activities:
4.1 Use Info-Tech’s HAM Budgeting Tool to plan your hardware asset budget
This step involves the following participants:
- IT Director
- Asset Manager
- Finance Department
Step Outcomes
- Know where to find data to budget for hardware needs accurately
- Learn how to manage a hardware budget
- Plan hardware asset budget with a budgeting tool
Gain control of the budget to increase the success of HAM
A sophisticated hardware asset management program will be able to uncover hidden costs, identify targets for downsizing, save money through redistributing equipment, and improve forecasting of equipment to help control IT spending.
While some asset managers may not have experience managing budgets, there are several advantages to ITAM owning the hardware budget:
- Be more involved in negotiating pricing with suppliers.
- Build better relationships with stakeholders across the business.
- Forecast requirements more accurately.
- Inform benchmarks for hardware performance.
- Gain more responsibility and have a greater influence on purchasing decisions.
- Directly impact the reduction in IT spend.
- Manage the asset database more easily and have a greater understanding of hardware needs.
- Build a continuous rolling refresh.
Use ITAM data to forecast hardware needs accurately and realistically
Your IT budget should be realistic, accounting for business needs, routine maintenance, hardware replacement costs, unexpected equipment failures, and associated support and warranty costs. Know where to find the data you need and who to work with to forecast hardware needs as accurately as possible.
What type of data should I take into account?
Plan for:
- New hardware purchases required
- Planned refreshes based on equipment lifecycle
- Inventory for break and fix
- Standard equipment for new hires
- Non-standard equipment required
- Hardware for planned projects
- Implementation and setup costs
- Routine hardware implementation
- Large hardware implementation for projects
- Support and warranty costs
Take into account:
- Standard refresh cycle for each hardware asset
- Amount of inventory to keep on hand
- Length of time from procurement to inventory
- Current equipment costs and equipment price increases
- Equipment depreciation rates and resale profits
Where do I find the information I need to budget accurately?
- Work with HR to forecast equipment needs for new hires.
- Work with the Infrastructure Manager to forecast devices and equipment needed for approved and planned projects.
- Use the asset management database to forecast hardware refresh and replacement needs based on age and lifecycle.
- Work with business stakeholders to ensure all new equipment needs are accounted for in the budget.
Use Info-Tech’s HAM Budgeting Tool to plan your hardware asset budget
4.1.1 Build HAM budget
This tool is designed to assist in developing and justifying the budget for hardware assets for the upcoming year. The tool will allow you to budget for projects requiring hardware asset purchases as well as equipment requiring refresh and to adjust the budget as needed to accommodate both projects and refreshes. Follow the instructions on each tab to complete the tool.
The hardware budget should serve as a planning and communications tool for the organization
The most successful relationships have a common vocabulary. Thus, it is important to translate “tech speak” into everyday language and business goals and initiatives as you plan your budget.
One of the biggest barriers that infrastructure and operations team face with regards to equipment budgeting is the lack of understanding of IT infrastructure and how it impacts the rest of the organization. The biggest challenge is to help the rest of the organization overcome this barrier.
There are several things you can do to overcome this barrier:
- Avoid using technical terms or jargon. Terms many would consider common knowledge, such as “WLAN,” are foreign to many.
- Don’t assume the business knows how the technology you’re referring to will impact their day-to-day work. You will need to demonstrate it to them.
- Help the audience understand the business impact of not implementing each initiative. What does this mean for them?
- Discuss the options on the table in terms of the business value that the hardware can enable. Review how deferring refresh projects can impact user-facing applications, systems, and business unit operations.
- Present options. If you can’t implement everything on the project list, present what you can do at different levels of funding.
Info-Tech Insight
Err on the side of inviting more discussion. Your budgeting process relies on business decision makers and receiving actionable feedback requires an ongoing exchange of information.
Help users understand the importance of regular infrastructure refreshes
Getting business users to support regular investments in maintenance relies on understanding and trust. Present the facts in plain language. Provide options, and clearly state the impact of each option.
Example: Your storage environment is nearing capacity.
Don’t:
Explain the project exclusively in technical terms or slang.
“We’re exploring deduping technology as well as cheap solid state, SATA, and tape storage to address capacity.”
Do:
- Explain impact in terms that the business can understand.
“Deduplication technology can reduce our storage needs by up to 50%, allowing us to defer a new storage purchase.”
- Be ready to present project alternatives and impacts.
“Without implementing deduplication technology, we will need to purchase additional storage by the end of the year at an estimated cost of $25,000.”
- Connect the project to business initiatives and strategic priorities.
“This is a cost-effective technique to increase storage capacity to manage annual average data growth at around 20% per year.”
Step 4.2: Build Communication Plan and Roadmap
Phase 4: Plan Budget & Build Roadmap
4.1 Plan Budget
4.2 Communicate & Build Roadmap
This step will walk you through the following activities:
4.2 Develop a HAM implementation roadmap
This step involves the following participants:
- CIO
- IT Director
- Asset Manager
- Service Desk Manager
Step Outcomes
- Documented end-user hardware asset management policies
- Communications plan to achieve support from end users and other business units
- HAM implementation roadmap
Educate end users through ITAM training to increase program success
As part of your communication plan and overall HAM implementation, training should be provided to end users within the organization.
All facets of the business, from management to new hires, should be provided with ITAM training to help them understand their role in the project’s success.
ITAM solutions are complex by nature with both business process and technical knowledge required to use them correctly. Keep the message appropriate to the audience – end users don’t need to know the complete process, but will need to know policy and how to request.
Management may have priorities that appear to clash with new processes. Engage management by making them aware of the benefits and importance of ITAM. Include the benefits and consequences of not implementing ITAM in your education approach. Encourage them to support efforts by reinforcing your messages to end users.
New hires should have ITAM training bundled into their onboarding process. Fresh minds are easier to train and the ITAM program will be seen as an organizational standard, not merely a change.
Policy documents can help summarize end users’ obligations and clarify processes. Consider an IT Resources Acceptable UsePolicy.
"The lowest user is the most important user in your asset management program. New employees are your most important resource. The life cycle of the assets will go much smoother if new employees are brought on board." – Tyrell Hall, ITAM Program Coordinator
Info-Tech Insight
During training, you should present the material through the lens of “what’s in it for me?” Otherwise, you risk alienating end users through implementing organizational change viewed as low value.
Include policy design and enforcement in your communication plan
- Hardware asset management policies should define the actions to be taken to protect and preserve technology assets from failure, loss, destruction, theft, or damage.
- Implementing asset management policies enforces the notion that the organization takes its IT assets and the management of them seriously, and will help ensure the benefits of ITAM are achieved.
- Designing, approving, documenting, and adopting one set of standard ITAM policies for each department to follow will ensure the processes are enforced equally across the organization.
- Good ITAM policies answer the “what, how, and why” of IT asset management, provide the means for ITAM governance, and provide a basis for strategy and decision making.
Info-Tech Insight
Use policy templates to jumpstart your policy development and ensure policies are comprehensive, but be sure to modify and adapt policies to suit your corporate culture or they will not gain buy-in from employees. For a policy to be successful, it must be a living document and have participation and involvement from the committees and departments to whom it will pertain.
Use Info-Tech’s policy templates to build HAM policies
4.2.1 Build HAM policies
Use these HAM policy templates to get started:
Information Technology Standards Policy
This policy establishes standards and guidelines for a company’s information technology environment to ensure the confidentiality, integrity, and availability of company computing resources.
Desktop Move/Add/Change Policy
This desktop move/add/change policy is put in place for users to request to change their desktop computing environments. This policy applies configuration changes within a company.
The purchasing policy helps to establish company standards, guidelines, and procedures for the purchase of all information technology hardware, software, and computer-related components as well as the purchase of all technical services.
Hardware Asset Disposition Policy
This policy assists in creating guidelines around disposition in the last stage of the asset lifecycle.
Additional policy templates
- End-User Devices Acceptable Use Policy
- Software Asset Management Policy
- Software Development Policy
- Laptop Loan Policy
- Personnel Security Policy Template
- Application Security Policy
- Mobile Device Acceptable Use Policy
- Systems Monitoring and Auditing Policy
- Data Center Contract Management Policy
Info-Tech Insight
Use policy templates to jumpstart your policy development and ensure policies are comprehensive, but modify and adapt them to suit your corporate culture or they will not gain buy-in from employees. For a policy to be successful, it must be a living document and have participation from the committees and departments to whom it will pertain.
Create a communication plan to achieve end-user support and adherence to policies
Communication is crucial to the integration and overall implementation of your ITAM program. An effective communication plan will:
- Gain support from management at the project proposal phase.
- Create end-user buy-in once the program is set to launch.
- Maintain the presence of the program throughout the business.
- Instill ownership throughout the business from top-level management to new hires.
Use the variety of components as part of your communication plan in order to reach the organization.
- Advertise successes.
- Regularly demonstrate the value of the ITAM program with descriptive statistics focused on key financial benefits.
- Share data with the appropriate personnel; promote success to obtain further support from senior management.
- Sharing detailed asset-related reports frequently gives decision makers useful data to aid in their strategy.
- These reports can help your organization prepare for audits, adjust asset budgeting, and detect unauthorized assets.
- Educate management and end users about how they fit into the bigger picture.
- Individuals need to know that their behaviors can adversely affect data quality and, ultimately, lead to better decision making.
Develop a communication plan to convey the right messages
4.2.2 Develop a communication plan to convey the right messages
Participants
- CIO
- IT Director
- Asset Manager
- Service Desk Manager
Document
Document in the HAM Communication Plan
- Identify the groups that will be affected by the HAM program as those who will require communication.
- For each group requiring a communication plan, identify the following:
- Benefits of HAM for that group of individuals (e.g. better data, security).
- The impact the change will have on them (e.g. change in the way a certain process will work).
- Communication method (i.e. how you will communicate).
- Timeframe (i.e. when and how often you will communicate the changes).
| Group | Benefits | Impact | Method | Timeline |
|---|---|---|---|---|
| Service Desk | Improve end-user device support | Follow new processes | Email campaign | 3 months |
| Executives | Mitigate risks, better security, more data for reporting | Review and sign off on policies | ||
| End Users | Smoother request process | Adhere to device security and use policies | ||
| Infrastructure | Faster access to data and one source of truth | Modified processes for centralized procurement and inventory |
Implement ITAM in a phased, constructive approach
- One of the most difficult decisions to make when implementing ITAM is: “where do we start?”
- The pyramid to the right mirrors Maslow’s hierarchy of needs. The base is the absolute bare minimum that should be in place, and each level builds upon the previous one.
- As you track up the pyramid, your ITAM program will become more and more mature.
Now that your asset lifecycle environment has been constructed in full, it’s time to study it. Gather data about your assets and use the results to create reports and new solutions to continually improve the business.
- Asset Data
- Asset Protection: safely protect and dispose of assets once they are mass distributed throughout your organization.
- Asset Distribution: determine standards for asset provisioning and asset inventory strategy.
- Asset Gathering: define what assets you will procure, distribute, and track. Classifying your assets by tier will allow you to make decisions as you progress up the pyramid.
↑ ITAM Program Maturity
Integrate your HAM program into the organization to assist its implementation
The HAM program cannot perform on its own – it must be integrated with other functional areas of the organization in order to maintain its stability and support.
- Effective IT asset management is supported by a comprehensive set of processes as part of its implementation.
- For example, integration with the purchasing/procurement team is required to gather hardware and software purchase data to control asset costs and mitigate software license compliance risk.
- Integration with Finance is required to support internal cost allocations and charge backs.
To integrate your ITAM program into your organization effectively, a clear implementation roadmap needs to be designed. Prioritize “quick wins” in order to demonstrate success to the business early and gain buy-in from your team. Long-term goals should be designed that will be supported by the outcomes of the short-term gains of your ITAM program.
| Short-term goal | Long-term goal |
|---|---|
| Identify inventory classification and tool (hardware first) | Hardware contract data integration (warranty, maintenance, lease) |
| Create basic ITAM policies and processes | Continual improvement through policy impact review and revision |
| Implement ITAM auto-discovery tools | Software compliance reports, internal audits |
Info-Tech Insight
Installing an ITAM tool does not mean you have an effective asset management program. A complete solution needs to be built around your tool, but the strength of ITAM comes from processes embedded in the organization that are shaped and supported by your ITAM data.
Develop an IT hardware asset management implementation roadmap
4.2.3 Develop a HAM implementation roadmap
Participants
- CIO
- IT Director
- Asset Manager
- Service Desk Manager
Document
Document in the IT Hardware Asset Management Implementation Roadmap
- Identify up to five streams to work on initiatives for the hardware asset management project.
- Fill out key tasks and objectives for each process. Assign responsibility for each task.
- Select a start date and end date for each task. See tab 1 of the tool for instructions on which letters to input for each stage of the process.
- Once your list is complete, open tab 3 of the tool to see your completed sunshine diagram.
- Keep this diagram visible for your team and use it as a guide to task completion as you work towards your future-state value stream.
Focus on continual improvement to sustain your ITAM program
Periodically review the ITAM program in order to achieve defined goals, objectives, and benefits.
Act → Plan → Do → Check
Once ITAM is in place in your organization, a focus on continual improvement creates the following benefits:
- Remain in sync with the business: your asset management program reflects the current and desired future states of your organization at the time of its creation. But the needs of the business change. As mentioned previously, asset management is a dynamic process, so in order for your program to keep pace, a focus on continual improvement is needed.
- For example, imagine if your organization had designed your ITAM program before cloud-based solutions were an option. What if your asset classification scheme did not include personal devices or tablets or your asset security policy lacked a section on BYOD?
- Create funding for new projects through ITAM continual improvement: one of the goals is to save money through more efficient use of your assets by “sweating” out underused hardware and software.
- It may be tempting to simply present the results to Finance as savings, but instead, describe the results as “available funds for other projects.” Otherwise, Finance may view the savings as a nod to restrict IT’s budget and allocate funds elsewhere. Make it clear that any saved funds are still required, albeit in a different capacity.
Info-Tech Best Practice
Look for new uses for ITAM data. Ask management what their goals are for the next 12-18 months. Analyze the data you are gathering and determine how your ITAM data can assist with achieving these goals.
Phase 4 outline
Call 1-888-670-8889 or email GuidedImplementations@InfoTech.com for more information.
Complete these steps on your own or call us to complete a guided implementation. A guided implementation is a series of 2-3 advisory calls that help you execute each phase of a project. They are included in most advisory memberships.
Step 4.1: Plan Budget
Start with an analyst kick-off call:
- Know where to find data to budget for hardware needs accurately.
- Learn how to manage a hardware budget.
Then complete these activities…
- Plan hardware asset budget.
With these tools & templates:
HAM Budgeting Tool
Step 4.2: Communicate & Roadmap
Review findings with analyst:
- Develop policies for end users.
- Build communications plan.
- Build an implementation roadmap.
Then complete these activities…
- Build HAM policies.
- Develop a communication plan.
- Develop a HAM implementation roadmap.
With these tools & templates:
HAM policy templates
HAM Communication Plan
HAM Implementation Roadmap
If you want additional support, have our analysts guide you through this phase as part of an Info-Tech workshop
Book a workshop with our Info-Tech analysts:
- To accelerate this project, engage your IT team in an Info-Tech workshop with an Info-Tech analyst team.
- Info-Tech analysts will join you and your team onsite at your location or welcome you to Info-Tech’s historic Toronto office to participate in an innovative onsite workshop.
- Contact your account manager (www.infotech.com/account), or email Workshops@InfoTech.com for more information.
The following are sample activities that will be conducted by Info-Tech analysts with your team:
4.1.1 Build a hardware asset budget
Review upcoming hardware refresh needs and projects requiring hardware purchases. Use this data to forecast and budget equipment for the upcoming year.
4.2.2 Develop a communication plan
Identify groups that will be affected by the new HAM program and for each group, document a communications plan.
Insight breakdown
Overarching Insights
HAM is more than just tracking inventory. A mature asset management program provides data for proactive planning and decision making to reduce operating costs and mitigate risk.
ITAM is not just IT. IT leaders need to collaborate with Finance, Procurement, Security, and other business units to make informed decisions and create value across the enterprise.
Treat HAM like a process, not a project. HAM is a dynamic process that must react and adapt to the needs of the business.
Phase 1 Insight
For asset management to succeed, it needs to support the business. Engage business leaders to determine needs and build your HAM program around these goals.
Phase 2 Insight
Bridge the gap between IT and Finance to build a smoother request and procurement process through communication and routine reporting. If you’re unable to affect procurement processes to reduce time to deliver, consider bringing inventory onsite or having your hardware vendor keep stock, ready to ship on demand.
Phase 3 Insight
Not all assets are created equal. Taking a blanket approach to asset maintenance and security is time consuming and costly. Focus on the high-cost, high-use, and data-sensitive assets first.
Phase 4 Insight
Deploying a fancy ITAM tool will not make hardware asset management implementation easier. Implementation is a project that requires you focus on people and process first – the technology comes after.
Related Info-Tech research
Implement Software Asset Management
Build an End-User Computing Strategy
Find the Value – and Remain Valuable – With Cloud Asset Management
Consolidate IT Asset Management
Bibliography
Chalkley, Martin. “Should ITAM Own Budget?” The ITAM Review. 19 May 2011. Web.
“CHAMP: Certified Hardware Asset Management Professional Manual.” International Association of Information Technology Asset Managers, Inc. 2008. Web.
Foxen, David. “The Importance of Effective HAM (Hardware Asset Management).” The ITAM Review. 19 Feb. 2015. Web.
Foxen, David. “Quick Guide to Hardware Asset Tagging.” The ITAM Review. 5 Sep. 2014. Web.
Galecki, Daniel. “ITAM Lifecycle and Savings Opportunities – Mapping out the Journey.” International Association of IT Asset Managers, Inc. 16 Nov. 2014. Web.
“How Cisco IT Reduced Costs Through PC Asset Management.” Cisco IT Case Study. 2007. Web.
Irwin, Sherry. “ITAM Metrics.” The ITAM Review. 14 Dec. 2009. Web.
“IT Asset and Software Management.” ECP Media LLC, 2006. Web.
Rains, Jenny. “IT Hardware Asset Management.” HDI Research Brief. May 2015. Web.
Riley, Nathan. “IT Asset Management and Tagging Hardware: Best Practices.” Samanage Blog. 5 March 2015. Web.
“The IAITAM Practitioner Survey Results for 2016 – Lean Toward Ongoing Value.” International Association of IT Asset Managers, Inc. 24 May 2016. Web.
Buying Options
Implement Hardware Asset Management
Client rating
Cost Savings
Days Saved
IT Risk Management · IT Leadership & Strategy implementation · Operational Management · Service Delivery · Organizational Management · Process Improvements · ITIL, CORM, Agile · Cost Control · Business Process Analysis · Technology Development · Project Implementation · International Coordination · In & Outsourcing · Customer Care · Multilingual: Dutch, English, French, German, Japanese · Entrepreneur
Tymans Group is a brand by Gert Taeymans BV
Gert Taeymans bv
Europe: Koning Albertstraat 136, 2070 Burcht, Belgium — VAT No: BE0685.974.694 — phone: +32 (0) 468.142.754
USA: 4023 KENNETT PIKE, SUITE 751, GREENVILLE, DE 19807 — Phone: 1-917-473-8669
Copyright 2017-2022 Gert Taeymans BV