Create a Post-Implementation Plan for Microsoft 365

M365 projects are fraught with obstacles. Common mistakes organizations make include:
- Not having a post-migration plan in place.
- Treating user training as an afterthought.
- Inadequate communication to end users.
Our Advice
Critical Insight
There are three primary areas where organizations fail in a successful implementation of M365: training, adoption, and information governance. While it is not up to IT to ensure every user is well trained, it is their initial responsibility to find champions, SMEs, and business-based trainers and manage information governance from the backup, retention, and security aspects of data management.
Impact and Result
Migrating to M365 is a disruptive move for most organizations. It poses risk to untrained IT staff, including admins, help desk, and security teams. The aim for organizations, especially in this new hybrid workspace, is to maintain efficiencies through collaboration, share information in a secure environment, and work from anywhere, any time.
Create a Post-Implementation Plan for Microsoft 365 Research & Tools
Besides the small introduction, subscribers and consulting clients within this management domain have access to:
1. Create a Post-Implementation Plan for Microsoft 365 Storyboard – A deck that guides you through the important considerations that will help you avoid common pitfalls and make the most of your investment.
There are three primary goals when deploying Microsoft 365: productivity, security and compliance, and collaborative functionality. On top of these you need to meet the business KPIs and IT’s drive for adoption and usage. This research will guide you through the important considerations that are often overlooked as this powerful suite of tools is rolled out to the organization.
Further reading
Create a Post-Implementation Plan for Microsoft 365
You’ve deployed M365. Now what? Look at your business goals and match your M365 KPIs to meet those objectives.
Analyst perspective
You’ve deployed M365. Now what?
 |
There are three primary objectives when deploying Microsoft 365: from a business perspective, the expectations are based on productivity; from an IT perspective, the expectations are based on IT efficiencies, security, and compliance; and from an organizational perspective, they are based on a digital employee experience and collaborative functionality. Of course, all these expectations are based on one primary objective, and that is user adoption of Teams, OneDrive, and SharePoint Online. A mass adoption, along with a high usage rate and a change in the way users work, is required for your investment in M365 to be considered successful. So, adoption is your first step, and that can be tracked and analyzed through analytics in M365 or other tools. But what else needs to be considered once you have released M365 on your organization? What about backup? What about security? What about sharing data outside your business? What about self-service? What about ongoing training? M365 is a powerful suite of tools, and taking advantage of all that it entails should be IT’s primary goal. How to accomplish that, efficiently and securely, is up to you! |
John Donovan |
Insight summary
Collaboration, efficiencies, and cost savings need to be earned |
Migrating to M365 is a disruptive move for most organizations. Additionally, it poses risk to untrained IT staff, including admins, help desk, and security teams. The aim for organizations, especially in this new hybrid workspace, is to maintain efficiencies through collaboration, share information in a secure environment, and work from anywhere, any time. However, organizations need to manage their licensing and storage costs and build this new way of working through post-deployment planning. By reducing their hardware and software footprint they can ensure they have earned these savings and efficiencies. |
Understand any shortcomings in M365 or pay the price |
Failing to understand any shortcomings M365 poses for your organization can ruin your chances at a successful implementation. Commonly overlooked expenses include backup and archiving, especially for regulated organizations; spending on risk mitigation through third-party tools for security; and paying a premium to Microsoft to use its Azure offerings with Microsoft Sentinel, Microsoft Defender, or any security add-on that comes at a price above your E5 license, which is expensive in itself. |
Spend time with users to understand how they will use M365 |
Understanding business processes is key to anticipating how your end users will adopt M365. By spending time with the staff and understanding their day-to-day activities and interactions, you can build better training scenarios to suit their needs and help them understand how the apps in M365 can help them do their job. On top of this you need to meet the business KPIs and IT’s drive for adoption and usage. Encourage early adopters to become trainers and champions. Success will soon follow. |
Executive summary
Your Challenge |
Common Obstacles |
Info-Tech’s Approach |
|---|---|---|
M365 is a full suite of tools for collaboration, communication, and productivity, but organizations find the platform is not used to its full advantage and fail to get full value from their license subscription. Many users are unsure which tool to use when: Do you use Teams or Viva Engage, MS Project or Planner? When do you use SharePoint versus OneDrive? From an IT perspective, finding time to help users at the outset is difficult – it’s quite the task to set up governance, security, and backup. Yet training staff must be a priority if the implementation is to succeed. |
M365 projects are fraught with obstacles. Common mistakes organizations make include:
|
To define your post-migration tasks and projects:
Failure to take meaningful action will not bode well for your M365 journey. |
Info-Tech Insight
There are three primary areas where organizations fail in a successful implementation of M365: training, adoption, and information governance. While it is not up to IT to ensure every user is well trained, it is their initial responsibility to find champions, SMEs, and business-based trainers and to manage information governance from backup, retention, and security aspects of data management.
Business priorities
What priorities is IT focusing on with M365 adoption?
What IT teams are saying
- In a 2019 SoftwareONE survey, the biggest reason IT decision makers gave for adopting M365 was to achieve a “more collaborative working style.”
- Organizations must plan and execute a strategy for mass adoption and training to ensure processes match business goals.
- Cost savings can only be achieved through rightsizing license subscriptions, retiring legacy apps, and building efficiencies within the IT organization.
- With increased mobility comes with increased cybersecurity risk. Make sure you take care of your security before prioritizing mobility. Multifactor authentication (MFA), conditional access (CA), and additional identity management will maintain a safe work-from-anywhere environment.
Top IT reasons for adopting M365
61% More collaborative working style
54% Cost savings
51% Improved cybersecurity
49% Greater mobility
Source: SoftwareONE, 2019; N=200 IT decision makers across multiple industries and organization sizes
Define & organize post-implementation projects
Key areas to success
- Using Microsoft’s M365 adoption guide, we can prioritize and focus on solutions that will bring about better use of the M365 suite.
- Most of your planning and prioritizing should be done before implementation. Many organizations, however, adopted M365 – and especially Teams, SharePoint Online, and OneDrive – in an ad hoc manner in response to the pandemic measures that forced users to work from home.
- Use a Power BI Pro license to set up dashboards for M365 usage analytics. Install GitHub from AppSource and use the templates that will give you good insight and the ability to create business reports to show adoption and usage rates on the platform.
- Reimagine your working behavior. Remember, you want to bring about a more collective and open framework for work. Take advantage of a champion SME to show the way. Every organization is different, so make sure your training is aligned to your business processes.
Process steps
Define Vision |
Build Team |
Plan Projects |
Execute |
|---|---|---|---|
Define your vision and what your priorities are for M365. Understand how to reach your vision. |
Ensure you have an executive sponsor, develop champions, and build a team of SMEs. |
List all projects in a to-be scenario. Rank and prioritize projects to understand impact and difficulty. |
Build your roadmap, create timelines, and ensure you have enough resources and time to execute and deliver to the business. |
Info-Tech’s approach
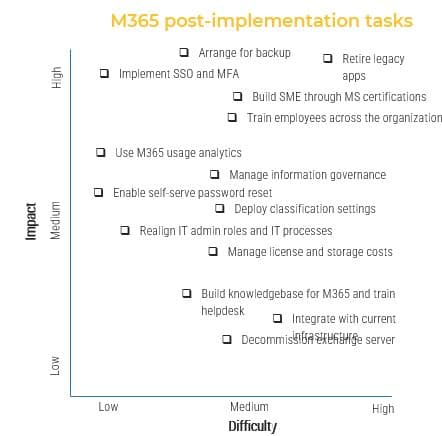
Use the out-of-the-box tools and take advantage of your subscription.
Info-Tech Insight
A clear understanding of the business purpose and processes, along with insight into the organizational culture, will help you align the right apps with the right tasks. This approach will bring about better adoption and collaboration and cancel out the shadow IT products we see in every business silo.
Leverage built-in usage analytics
Adoption of services in M365
To give organizations insight into the adoption of services in M365, Microsoft provides built-in usage analytics in Power BI, with templates for visualization and custom reports. There are third-party tools out there, but why pay more? However, the template app is not free; you do need a Power BI Pro license.
Usage Analytics pulls data from ActiveDirectory, including location, department, and organization, giving you deeper insight into how users are behaving. It can collect up to 12 months of data to analyze.
Reports that can be created include Adoption, Usage, Communication, Collaboration (how OneDrive and SharePoint are being used), Storage (cloud storage for mailboxes, OneDrive, and SharePoint), and Mobility (which clients and devices are used to connect to Teams, email, Yammer, etc.).
Source: Microsoft 365 usage analytics
Understand admin roles
Prevent intentional or unintentional internal breaches
Admin Roles |
Best Practices |
|---|---|
|
Only assign two to four global admins, depending on the size of the organization. Too many admins increases security risk. In larger organizations, segment admin roles using role-based access control. Because admins have access to sensitive data, you’ll want to assign the least permissive role so they can access only the tools and data they need to do their job. Enable MFA for all admins except one break-glass account that is stored in the cloud and not synced. Ensure a complex password, stored securely, and use only in the event of an MFA outage. Due to the large number of admin roles available and the challenges that brings with it, Microsoft has a built-in tool to compare roles in the admin portal. This can help you determine which role should be used for specific tasks. |
Secure your M365 tenant
A checklist to ensure basic security coverage post M365
- Multifactor Authentication: MFA is part of your M365 tenant, so using it should be a practical identity security. If you want additional conditional access (CA), you will require an Azure AD (AAD) Premium P1+ license. This will ensure adequate identity security protecting the business.
- Password Protection: Use the AAD portal to set this up under Security > Authentication Methods. Microsoft provides a list of over 2,000 known bad passwords and variants to block.
- Legacy Authentication: Disable legacy protocols; check to see if your legacy apps/workflows/scripts use them in the AAD portal. Once identified, update them and turn the protocols off. Use CA policies.
- Self-Service Password Reset: Enable self-service to lower the helpdesk load for password resets. Users will have to initially register and set security questions. Hybrid AD businesses must write back to AD from AAD once changes are made.
- Security Defaults: For small businesses, turn on default settings. To enable additional security settings, such as break- glass accounts, go into Manage Security Defaults in your AAD properties.
- Conditional Access (CA) Policies: Use CA policies if strong identity security and zero trust are required. To create policies in AAD go to Security > Conditional Access > New Policies.
Identity Checklist
- Enable MFA for Admins
- Enable MFA for Users
- Disable App Passwords
- Configure Trusted IPs
- Disable Text/Phone MFA
- Remember MFA on Trusted Devices for 90 Days
- Train Staff in Using MFA Correctly
- Integrate Apps Into Azure AD
Training guidelines
Identify business scenarios and training adoption KPIs
- Customize your training to meet your organizational goals, align with your business culture, and define how users will work inside the world of M365.
- Create scenario templates that align to your current day-to-day operations in each department. These can be created by individual business unit champions.
- Make sure you have covered must-have capabilities and services within M365 that need to be rolled out post-pilot.
- Phase in large transitions rather than multiple small ones to ensure collaboration between departments meets business scenarios.
- Ensure your success metrics are being measured and continue to communicate and train after deployment using tools available in M365. See Microsoft’s adoption guidelines and template for training.
Determine your training needs and align with your business processes. Choose training modalities that will give users the best chance of success. Consider one or many training methods, such as:
- Online training
- In-person classroom
- Business scenario use cases
- Mentoring
- Department champion/Early adopter
- Weekly bulletin fun facts
Don’t forget backup!
Providing 99% uptime and availability is not enough
Why is M365 backup so important?
Accidental Data Deletion.
If a user is deleted, that deletion gets replicated across the network. Backup can save you here by restoring that user.
Internal and External Security Threats.
Malicious internal deletion of data and external threats including viruses, ransomware, and malware can severely damage a business and its reputation. A clean backup can easily restore the business’ uninfected data.
Legal and Compliance Requirements.
While e-discovery and legal hold are available to retain sensitive data, a third-party backup solution can easily search and restore all data to meet regulatory requirements – without depending on someone to ensure a policy was set.
Retention Policy Gaps.
Retention policies are not a substitute for backup. While they can be used to retain or delete content, they are difficult to keep track of and manage. Backups offer greater latitude in retention and better security for that data.
Retire your legacy apps to gain adoption
Identify like for like and retire your legacy apps
Legacy |
Microsoft 365 |
|---|---|
SharePoint 2016/19 |
SharePoint Online |
Microsoft Exchange Server |
Microsoft Exchange in Azure |
Skype for Business Server |
Teams |
Trello |
Planner 2022 |
System Center Configuration Manager (SCCM) |
Endpoint Manager, Intune, Autopilot |
File servers |
OneDrive |
Access |
Power Apps |
To meet the objectives of cost reduction and rationalization, look at synergies that M365 brings to the table. Determine what you are currently using to meet collaboration, storage, and security needs and plan to use the equivalent in your Microsoft entitlement.
Managing M365’s hidden costs
Licenses and storage limits TCO
- Email security. Ninety-one percent of all cyberattacks come from phishing on email. Microsoft Defender for M365 is a bolt-on, so it is an additional cost.
- Backup. This will bring additional cost to M365. Plan to spend more to ensure data is backed up and stored.
- Email archiving. Archiving is different than backup. See our research on the subject. Archiving is needed for compliance purposes. Email archiving solutions are available through third-party software, which is an added cost.
- Email end-to-end encryption. This is a requirement for all organizations that are serious about security. The enterprise products from Microsoft come at an additional cost.
- Cybersecurity training. IT needs to ramp up on training, another expense.
- Microsoft 365 Power Platform Licencing. From low-code and no-code developer tools (Power Apps), workflow tools (Power Automate), and business intelligence (Power BI) – while the E5 license gives you Power BI Pro, there are limitations and costs. Power BI Pro has limitations for data volume, data refresh, and query response time, so your premium license comes at a considerably marked up cost.
M365 is not standalone
- While Microsoft 365 is a platform that is ”just good enough,” it is actually not good enough in today’s cyberthreat environment. Microsoft provides add-ons with Defender for 365, Purview, and Sentinel, which pose additional costs, just like a third-party solution would. See the Threat Intelligence & Incident Response research in our Security practice.
- The lack of data archiving, backup, and encryption means additional costs that may not have been budgeted for at the outset. Microsoft provides 30-60-90-day recovery, but anything else is additional cost. For more information see Understand the Difference between Backups and Archiving.
Compliance and regulations
Security and compliance features out of the box
There are plenty of preconfigured security features contained in M365, but what’s available to you depends on your license. For example, Microsoft Defender, which has many preset policies, is built-in for E5 licenses, but if you have E3 licenses Defender is an add-on.
Three elements in security policies are profiles, policies, and policy settings.
- Preset Profiles come in the shape of:
- Standard – baseline protection for most users
- Strict – aggressive protection for profiles that may be high-value targets
- Built-in Protection – turned on by default; it is not recommended to make exceptions based on users, groups, or domains
- Preset Security Policies
- Exchange Online Protection Policies – anti-spam, -malware, and -phishing policies
- Microsoft Defender Policies – safe links and safe attachments policies
- Policy Settings
- User impersonation protection for internal and external domains
- Select priorities from strict, standard, custom, and built-in
Info-Tech Insight
Check your license entitlement before you start purchasing add-ons or third-party solutions. Security and compliance are not optional in today’s cybersecurity risk world. With many organizations offering hybrid and remote work arrangements and bring-your-own-device (BYOD) policies, it is necessary to protect your data at the tenant level. Defender for Microsoft 365 is a tool that can protect both your exchange and collaboration environments.
More information: Microsoft 365 Defender
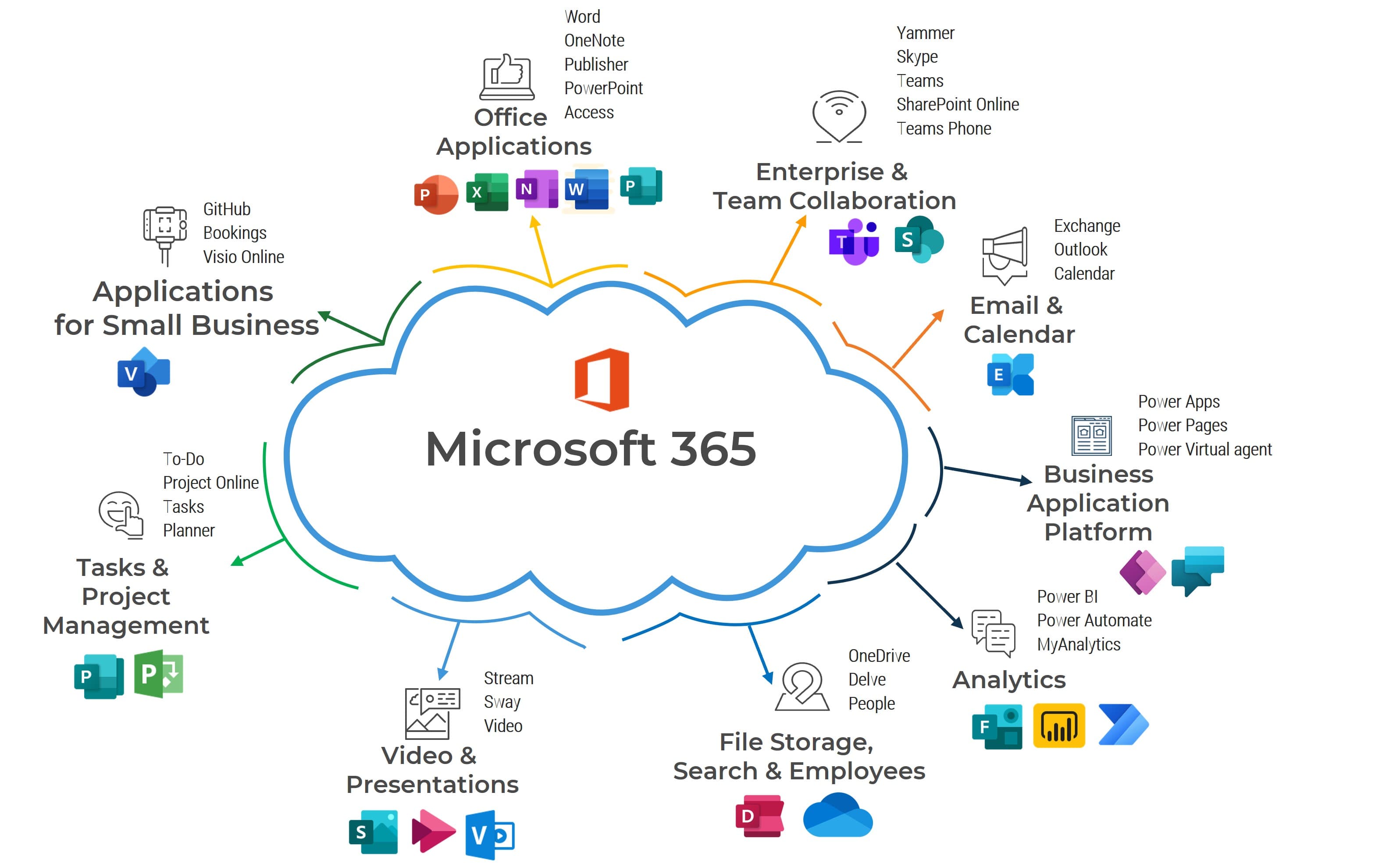
Use Intune and Autopilot
Meet the needs of your hybrid workforce
- Using the tools available in M365 can help you develop your hybrid or remote work strategy.
- This strategy will help you maintain security controls for mobile and BYOD.
- Migrating to Intune and Autopilot will give rise to the opportunity to migrate off SCCM and further reduce your on-premises infrastructure.
NOTE: You must have Azure AD Premium and Windows 10 V1703 or later as well as Intune or other MDM service to use Autopilot. There is a monthly usage fee based on volume of data transmitted. These fees can add up over time.
For more details visit the following Microsoft Learn pages:
- Overview of Windows Autopilot
- Windows Autopilot registration overview
- Microsoft Intune fundamentals
- Tutorial: Walkthrough Intune in Microsoft Endpoint Manager
Intune /Autopilot Overview
Info-Tech’s research on zero-touch provisioning goes into more detail on Intune and Autopilot:
Simplify Remote Deployment With Zero-Touch Provisioning
M365 long-term strategies
Manage your costs in an inflationary world
- Recent inflation globally, whether caused by supply chain woes or political uncertainty, will impact IT and cloud services along with everything else. Be prepared to pay more for your existing services and budget accordingly.
- Your long-term strategies must include ongoing cost management, data management, security risks, and license and storage costs.
- Continually investigate efficiencies, overlaps, and new tools in M365 that can get the job done for the business. Use as many of the applications as you can to ensure you are getting the best bang for your buck.
- Watch for upgrades in the M365 suite of tools. As Microsoft continues to improve and deliver on most business applications well after their first release, you may find that something that was previously inefficient could work in your environment today and replace a tool you currently use.
Ongoing Activities You Need to Maintain
- Be aware of increased license costs and higher storage costs.
- Keep an eye on Teams sprawl.
- Understand your total cost of ownership.
- Continue to look at legacy apps and get rid of your infrastructure debt.
Activity
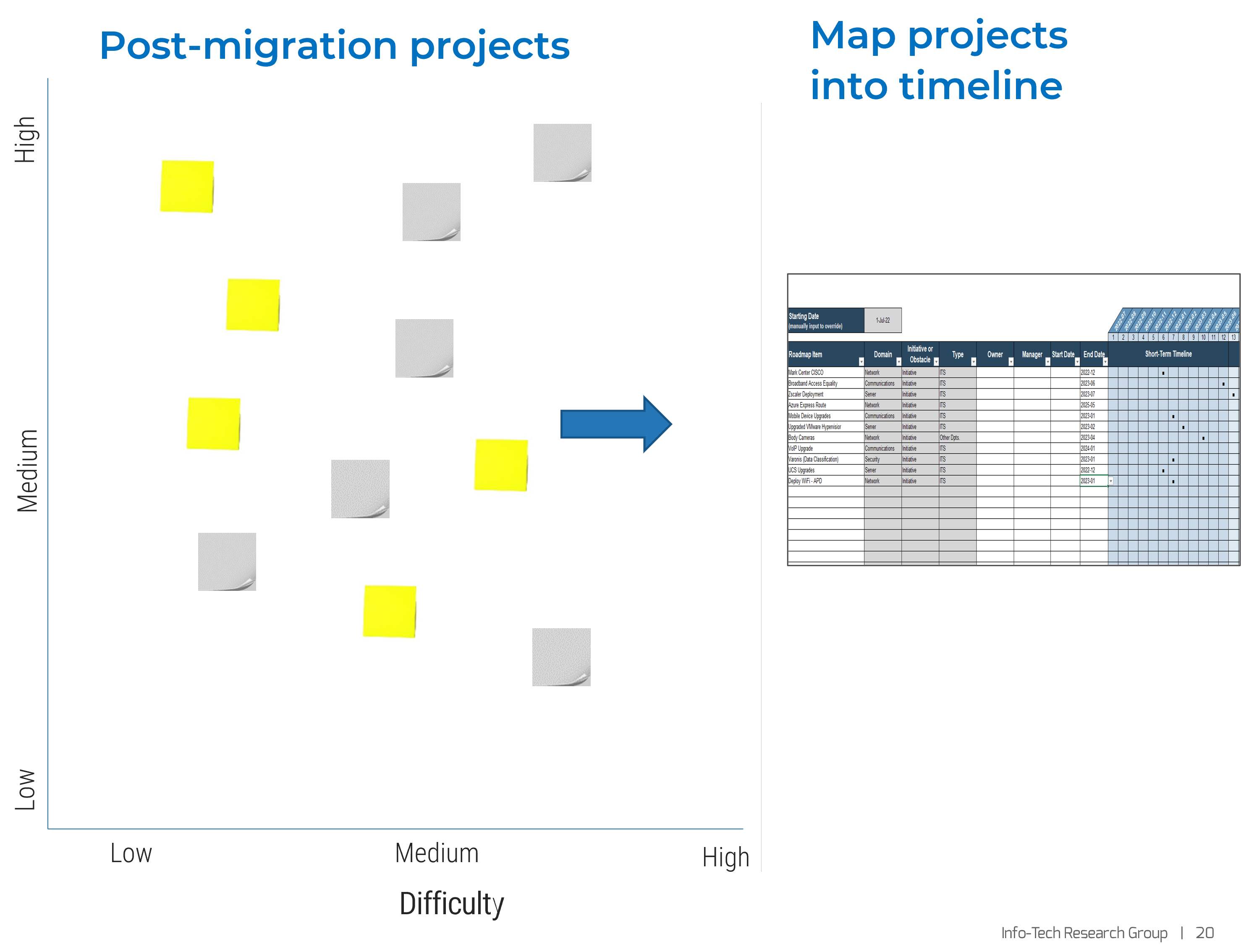
Build your own M365 post-migration plan
- Using slide 6 as your guideline, create your own project list using impact and difficulty as your weighting factors.
- Do this exercise as a whiteboard sticky note exercise to agree on impact and difficulty as a team.
- Identify easy wins that have high impact.
- Place the projects into a project plan with time lines.
- Agree on start and completion dates.
- Ensure you have the right resources to execute.
Related Info-Tech Research
- Office 365 is as difficult to wrangle as it is valuable. Leverage best practices to produce governance outcomes aligned with your goals.
Drive Ongoing Adoption With an M365 Center of Excellence
- Accelerate business processes change and get more value from your subscription by building and sharing, thanks to an effective center of excellence.
Simplify Remote Deployment With Zero-Touch Provisioning
- Adopt zero-touch provisioning to provide better services to your end users.
- Save time and resources during device deployment while providing a high-quality experience to remote end users.
Bibliography
“5 Reasons Why Microsoft Office 365 Backup Is Important.” Apps 4Rent, Dec 2021, Accessed Oct 2022 .
Chandrasekhar, Aishwarya. “Office 365 Migration Best Practices & Challenges 2022.” Saketa, 31 Mar 2022. Accessed Oct. 2022.
Chronlund, Daniel. “The Fundamental Checklist – Secure your Microsoft 365 Tenant”. Daniel Chronlund Cloud Tech Blog,1 Feb 2019. Accessed 1 Oct 2022.
Davies, Joe. “The Microsoft 365 Enterprise Deployment Guide.” Tech Community, Microsoft, 19 Sept 2018. Accessed 2 Oct 2022.
Dillaway, Kevin. “I Upgraded to Microsoft 365 E5, Now What?!.” SpyGlassMTG, 10 Jan 2022. Accessed 4 Oct. 2022.
Hartsel, Joe. “How to Make Your Office 365 Implementation Project a Success.” Centric, 20 Dec 2021. Accessed 2 Oct. 2022.
Jha, Mohit. “The Ultimate Microsoft Office 365 Migration Checklist for Pre & Post Migration.” Office365 Tips.Org, 24 June 2022. Accessed Sept. 2022.
Lang, John. “Why organizations don't realize the full value of Microsoft 365.“Business IT, 29 Nov 202I. Accessed 10 Oct 2022.
Mason, Quinn. “How to increase Office 365 / Microsoft 365 user adoption.” Sharegate, 19 Sept 2019. Accessed 3 Oct 2022.
McDermott, Matt. “6-Point Office 365 Post-Migration Checklist.” Spanning , 12 July 2019 . Accessed 4 Oct 2022.
“Microsoft 365 usage analytics.” Microsoft 365, Microsoft, 25 Oct 2022. Web.
Sharma, Megha. “Office 365 Pre & Post Migration Checklist.’” Kernel Data Recovery, 26 July 2022. Accessed 30 Sept. 2022.
Sivertsen, Per. “How to avoid a failed M365 implementation? Infotechtion, 19 Dec 2021. Accessed 2 Oct. 2022.
St. Hilaire, Dan. “Most Common Mistakes with Office 365 Deployment (and How to Avoid Them).“ KnowledgeWave, 4Mar 2019. Accessed Oct. 2022.
“Under the Hood of Microsoft 365 and Office 365 Adoption.” SoftwareONE, 2019. Web.
IT Risk Management · IT Leadership & Strategy implementation · Operational Management · Service Delivery · Organizational Management · Process Improvements · ITIL, CORM, Agile · Cost Control · Business Process Analysis · Technology Development · Project Implementation · International Coordination · In & Outsourcing · Customer Care · Multilingual: Dutch, English, French, German, Japanese · Entrepreneur
Tymans Group is a brand by Gert Taeymans BV
Gert Taeymans bv
Europe: Koning Albertstraat 136, 2070 Burcht, Belgium — VAT No: BE0685.974.694 — phone: +32 (0) 468.142.754
USA: 4023 KENNETT PIKE, SUITE 751, GREENVILLE, DE 19807 — Phone: 1-917-473-8669
Copyright 2017-2022 Gert Taeymans BV