Create and Implement an IoT Strategy

While the Internet of Things (IoT) or smart devices have the potential to transform businesses, they have to be implemented strategically to drive value. The business often engages directly with vendors, and many IoT solutions are implemented as point solutions with IT being brought in very late in the process.
This leads to challenges with integration, communication, and data aggregation and storage. IT is often also left grappling with many new devices that need to be inventoried, added to lifecycle management practices, and secured.
Unlock the true potential of IoT with early IT involvement
As IoT solutions become more common, IT leaders must work closely with business stakeholders early in the process to ensure that IoT solutions make the most of opportunities and mitigate risks.
- Ensure that IoT solutions meet business needs: Assess IoT solutions to ensure that they meet business requirements and align with business strategy.
- Make integration and management smooth: Build and execute plans so IoT devices integrate with existing infrastructure and multiple devices can be managed efficiently.
- Ensure privacy and security: IoT solutions should meet clearly outlined privacy and security requirements and comply with regulations such as GDPR and CCPA.
- Collect and store data systematically: Manage what data will be collected and aggregated and how it will be stored so that the business can recognize value from the data with minimal risk.
Create and Implement an IoT Strategy Research & Tools
Besides the small introduction, subscribers and consulting clients within this management domain have access to:
1. Create and Implement an IoT Strategy Deck – A framework to assess and onboard IoT devices into your environment.
The storyboard will help to create a steering committee and a playbook to quickly assess IoT ideas to determine the best way to support these ideas, test them in Proof of concepts, when appropriate, and give the business the confidence they need to get the right solution for the job and to know that IT can support them long term.
- Create and Implement an IoT Strategy – Phases 1-3
2. Steering Committee Charter Template – Improve governance starting with a steering committee charter to help you clearly define the role of the steering committee to improve outcomes.
Create a steering committee to improve success of IoT implementations.
- IoT Steering Committee Charter Template
3. IoT Solution Playbook – Create an IoT playbook to define a framework to quickly assess new solutions and determine the best time and method for onboarding into your operational environment.
Create a framework to quickly evaluate IoT solutions to mitigate risks and increase success.
- IoT Solution Playbook
Infographic
Further reading
Create and Implement an IoT Strategy
Gain control of your IoT environment
Create and Implement an IoT Strategy
Gain control of your IoT environment
EXECUTIVE BRIEF
Table of Contents
Analyst perspective
IoT is an extremely efficient automated data collection system which produces millions of pieces of data. Many organizations will purchase point solutions to help with their primary business function to increase efficiency, increase profitability, and most importantly provide scalable services that cannot exist without automated data collection and analytical tools.
Most of the solutions available are designed to perform a specific function within the parameters of the devices and applications designed by vendors. As these specific use cases proliferate within any organization, the data collected can end up housed in many places, owned by each specific business unit and used only for the originally designed purpose. Imagine though, if you could take the health information of many patients, anonymize it, and compare overall health of specific regions, rather than focusing only on the patient record as a correlated point; or many data points within cities to look at pedestrian, bike, and vehicle traffic to better plan infrastructure changes, improve city plans, and monitor pollution, then compared to other cities for additional modeling.
In order to make these dramatic shifts to using many IoT solutions, it’s time to look at creating an IoT strategy that will ensure all systems meet strategic goals and will enable disparate data to be aggregated for greater insights. The act of aggregation of systems and data will require additional scrutiny to mitigate the potential perils for privacy, management, security, and auditability
The strategy identifies who stewards use of the data, who manages devices, and how IT enables broader use of this technology. But with the increased volume of devices and data, operational efficiency as part of the strategy will also be critical to success.
This project takes you through the process of defining vision and governance, creating a process for evaluating proposed solutions for proof of value, and implementing operational effectiveness.

|
Sandi Conrad
|
Executive Summary
| Your Challenge
The business needs to move quickly to adopt new ways to collect and analyze data or automate actions. IoT may be the right answer, but it can be complex and create new challenges for IT teams. Many of these solutions are implemented by vendors as point solutions, but more organizations are recognizing they need to bring the data in-house to start driving insights. As IoT solutions become more prolific, the need to get more involved in securing and managing these solutions has become evident. |
Common Obstacles
The business is often engaging directly with the vendors to better understand how they can benefit from these solutions, and IT is often brought in when the solution is ready to go live. When IT isn’t involved early, there may be challenges around integrations, communications, and getting access to data. Management becomes challenging as many devices are suddenly entering the environment, which need to be inventoried, added to lifecycle management practices, and secured. |
Info-Tech’s Approach
Info-Tech’s approach starts with assessing the proposed solutions to:
|
Early intervention will improve results. IoT is one of the biggest challenges for IT departments to manage today. The large volume of devices and lack of insight into vendor solutions is making it significantly harder to plan for upgrades and contract renewals, and to guarantee security protocols are being met. Create a multistep onboarding process, starting with an initial assessment process to increase success for the business, then look to derive additional benefits to the business and mitigate risks.
Your challenge
Scaling up and out from an IoT point solution is complicated and requires collaboration from stakeholders that may not have worked well together before
IoT solutions may be chosen by the business, but to be successful and meet their requirements, a partnership with IT will ensure better communications with the service provider for a less stressful implementation with governance over security needs and protection of the organization’s data, and it will ensure that continual value is enabled through effective operations. |
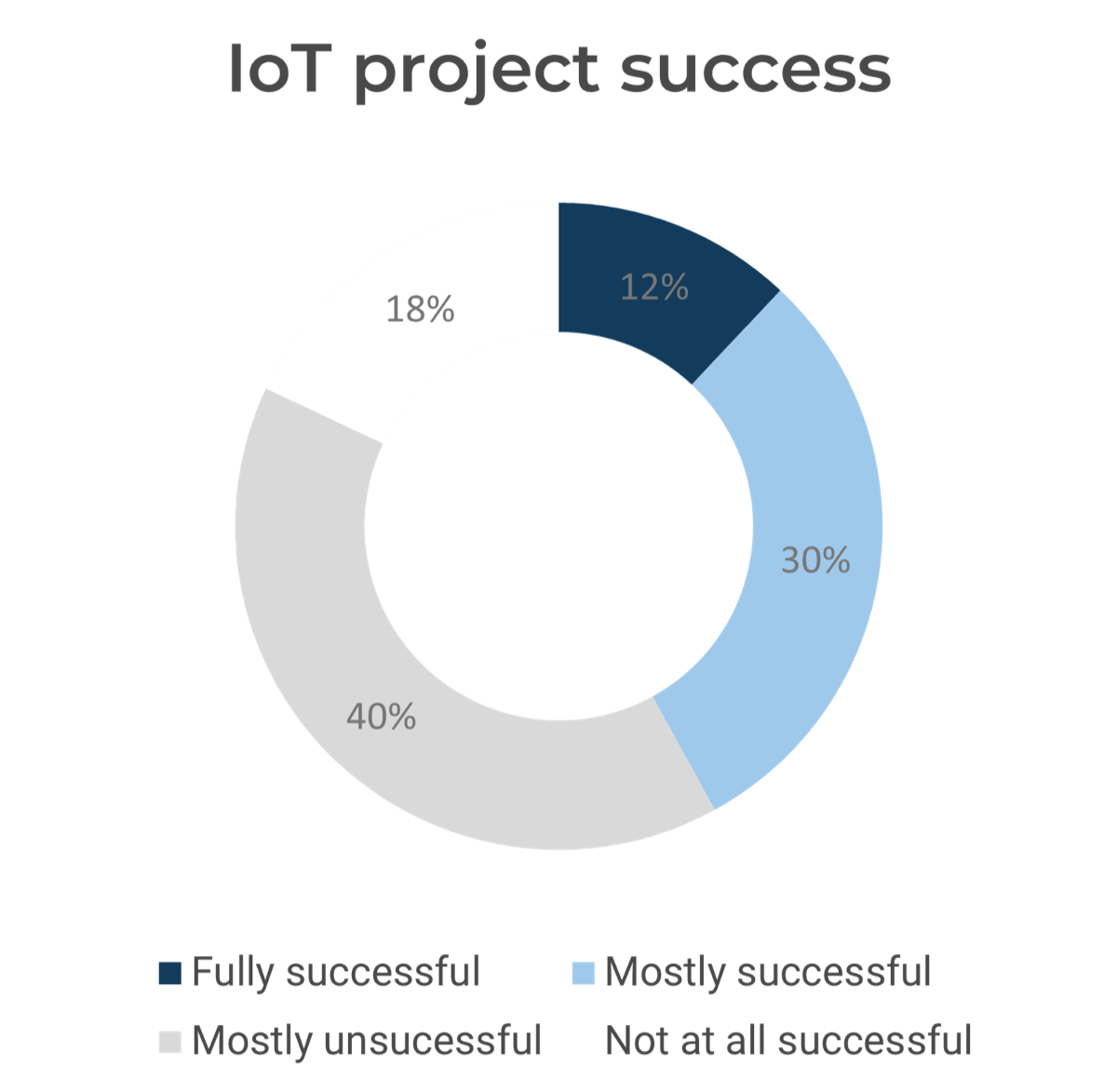 (Source: Beecham Research qtd. in Software AG) |
Common obstacles
These barriers make IoT challenging to implement for many organizations:
|
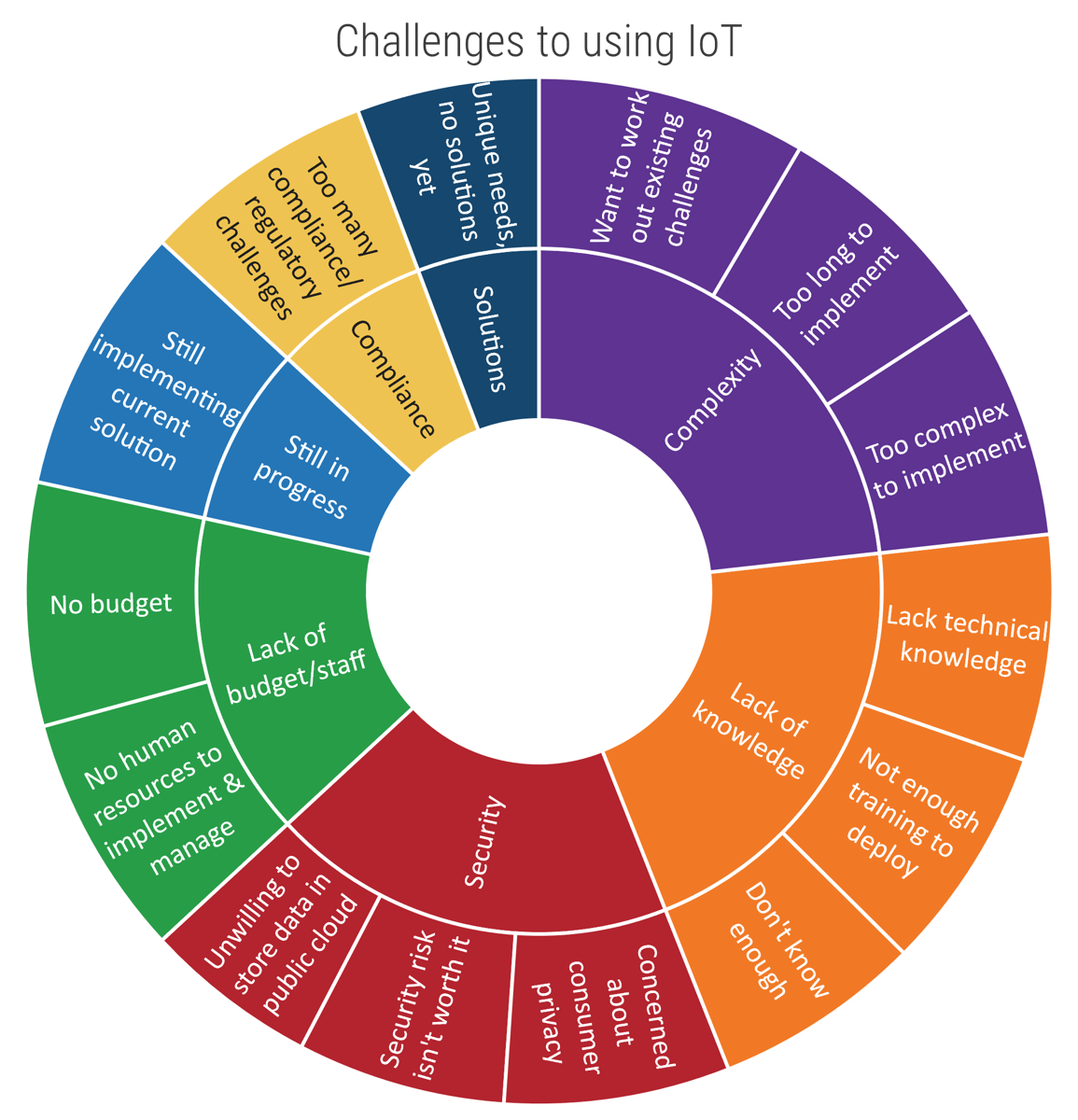
(Source: Microsoft IoT Signals, Edition 2, October 2020 n=3,000) |
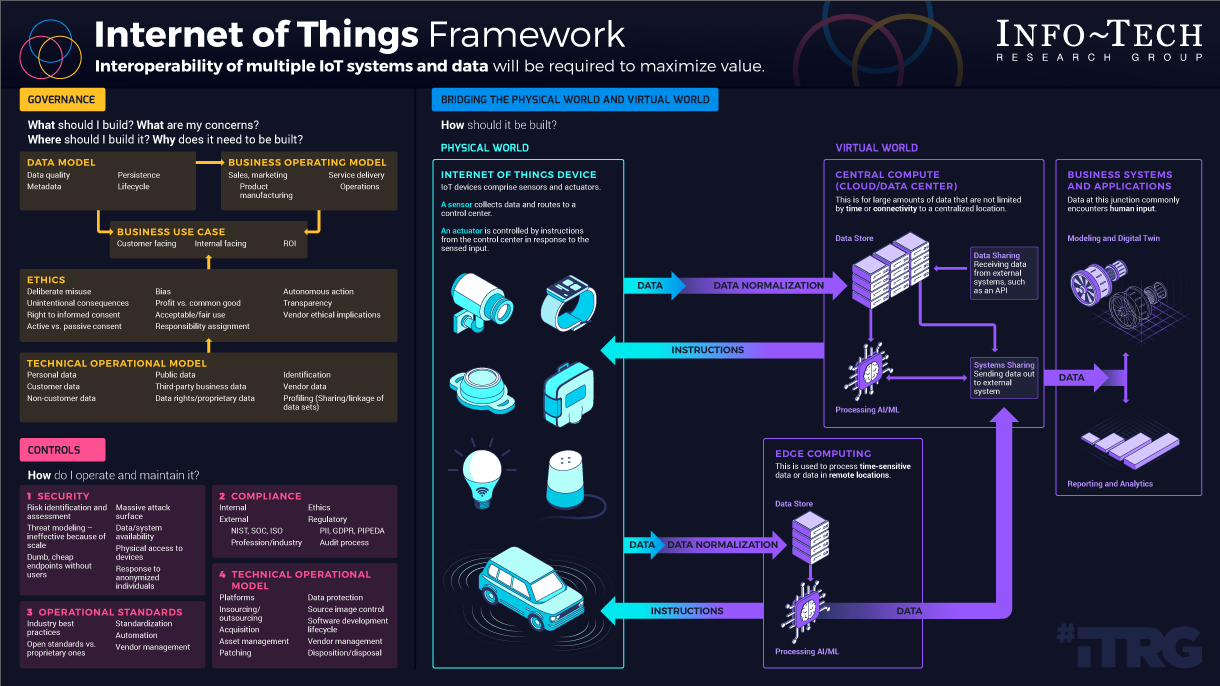
Internet of Things Framework
Interoperability of multiple IoT systems and data will be required to maximize value.GOVERNANCE
What should I build? What are my concerns?
Where should I build it? Why does it need to be built?
| DATA MODEL | ——› | BUSINESS OPERATING MODEL | ||
| Data quality Metadata |
Persistence Lifecycle |
Sales, marketing Product manufacturing |
Service delivery Operations |
|
|—› |
BUSINESS USE CASE |
‹—| |
||
| Customer facing | Internal facing | ROI | ||
| ˆ | |
||
| ETHICS | ||
| Deliberate misuse Unintentional consequences Right to informed consent Active vs. passive consent |
Bias Profit vs. common good Acceptable/fair use Responsibility assignment |
Autonomous action Transparency Vendor ethical implications |
| ˆ | |
||
| TECHNICAL OPERATIONAL MODEL | ||
| Personal data Customer data Non-customer data |
Public data Third-party business data Data rights/proprietary data |
Identification Vendor data Profiling (Sharing/linkage of data sets) |
CONTROLS
How do I operate and maintain it?
|
|
BRIDGING THE PHYSICAL WORLD AND THE VIRTUAL WORLD
How should it be built?
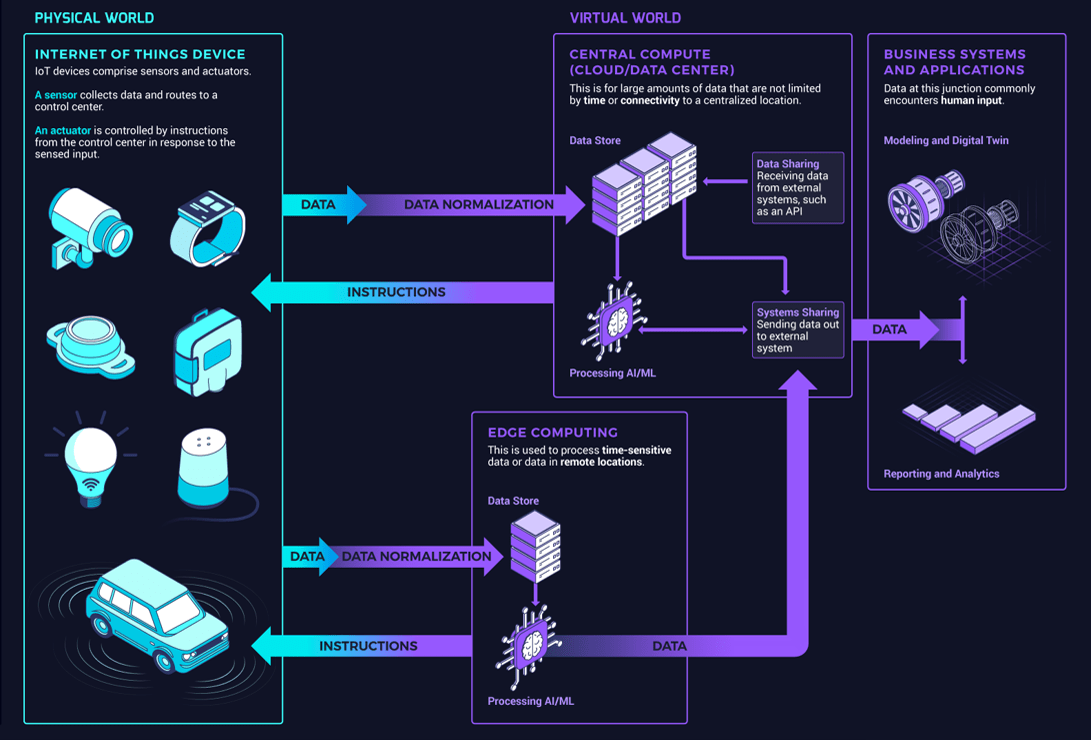 Data Normalization' from physical to virtual and 'Instructions' from virtual to physical.">
Data Normalization' from physical to virtual and 'Instructions' from virtual to physical.">
Insight summary
Real value to the business will come from insights derived from data
Many point solutions will solve many business issues and produce many data sets. Ensure your strategy includes plans on how to leverage data to further your organizational goals. A data specialist will make a significant difference in helping you determine how best to aggregate and analyze data to meet those needs.
Provide the right level of oversight to help the business adopt IoT
Regardless of who is initiating the request or installing the solution, it’s critical to have a framework that protects the organization and their data and a plan for managing the devices.
The business doesn’t always know what questions to ask, so it’s important for IT to enable them if moving to a business-led innovation model, and it’s critical to helping them achieve business value early.
Do a pre-implementation assessment to engage early and at the right level
Many IoT solutions are business- and vendor-led and are hosted outside of the organization or managed inside the business unit.
Having IT engage early allows the business to determine what level of support is appropriate for them, allows IT to ensure data integrity, and allows IT to ensure that security, privacy, and long-term operational needs are managed appropriately.
Blueprint deliverables
IoT Steering Committee CharterCreate a steering committee to improve success of IoT implementations
|
IoT Solution PlaybookCreate a framework to quickly evaluate IoT solutions to mitigate risks and increase success
|
Blueprint benefits
IT Benefits
|
Business Benefits
|
Evaluate digital transformation opportunities with these guiding principles for smart solutions
Problem & opportunity focus
|
Piece by piece
|
User buy-in
|
| Recommendations:
Focus on real problems • Be a fast follower • Build a technology ecosystem |
||
Info-Tech Insight
When looking for a quick win, consider customer journey mapping exercises to find out what it takes to do the work today, for example, map the journey to apply for a building permit, renew a license, or register a patient.
Measure the value of IoT
There is a broad range of solutions for IoT all designed to collect information and execute actions in a way designed to increase profitability and/or improve services. McKinsey estimates value created through interoperability will account for 40% to 60% of the potential value of IoT applications.
Revenue Generating
|
Improved outcomes
|
Increased access to data, especially if aggregating with other data sources, will increase opportunities for data analysis leading to more informed decision making. |
Cost Avoidance
|
Operational Metrics
|
Info-Tech offers various levels of support to best suit your needs
DIY Toolkit |
Guided Implementation |
Workshop |
Consulting |
| "Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful." | "Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track." | "We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place." | "Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project." |
Diagnostics and consistent frameworks used throughout all four options |
|||
Guided Implementation
A Guided Implementation (GI) is a series of calls with an Info-Tech analyst to help implement our best practices in your organization.
A typical GI is between 4 to 8 calls over the course of 2 to 4 months.
What does a typical GI on this topic look like?
| Phase 1 | Phase 2 | Phase 3 | |
| Call #1: Determine steering committee members and mandates.
Call #2: Define process for meeting and assessing requests. |
Call #3: Define the intake process.
Call #4: Define the role of the BRM & assessment criteria. |
Call #5: Define the process to secure funding.
Call #6: Define assessment requirements for other IT groups. |
Call #7: Define proof of value process. |
Create and Implement an IoT Strategy
Phase 1
Define your governance process
Steering Committee1.1 Define the committee’s roles and responsibilities in the IoT Steering Committee Charter 1.2 Define the IoT steering committee’s vision statement and mandates 1.3 Define procedures for reviewing proposals and roles and responsibilities |
Intake Process2.1 Define requirements for requesting new IoT solutions 2.2 Define procedures for reviewing proposals and projects – BA/BRM 2.3 Define procedures for reviewing proposals and projects – Data specialists 2.4 Define procedures for reviewing proposals and projects – Privacy & Security 2.5 Define procedures for reviewing proposals and projects – Infrastructure & Operations 2.6 Define service objectives and evaluation process |
Proof of Value3.1 Determine the criteria for running a proof of value 3.2 Define the template and process for running a proof of value |
This phase will provide the following activities
- Create the steering committee project charter
| If a steering committee exists, it may be appropriate to define IoT governance under their mandate. If a committee doesn’t already exist or their mandate will not include IoT, consider creating a committee to set standards and processes and quickly evaluate solutions for feasibility and implementation. |
Create an IoT steering committee to ensure value will be realized and operational needs will be metThe goals of the steering committee should be:
|
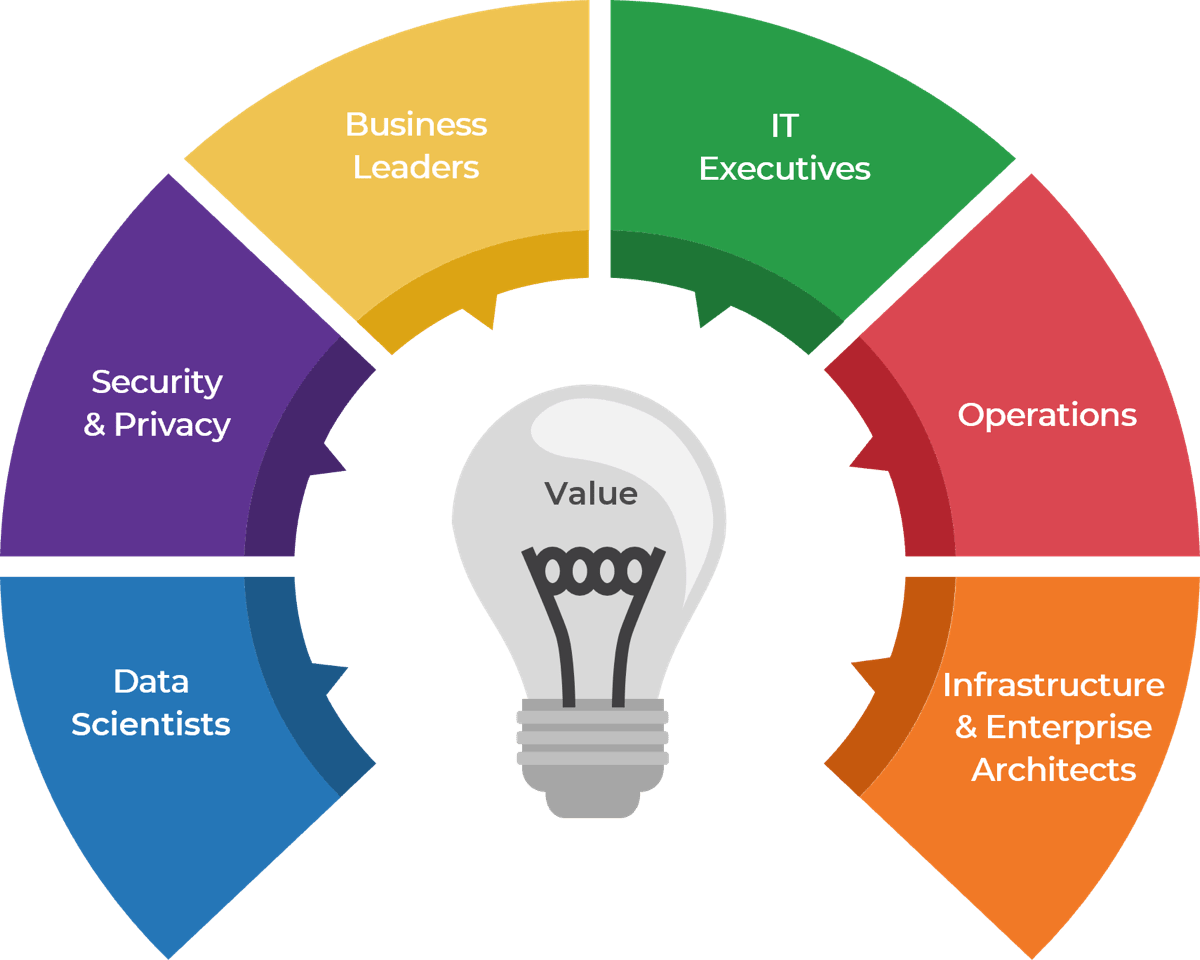
Assemble the right team to ensure the success of your IoT ecosystem
| Business stakeholders will provide clarity for their strategy and provide input into how they envision IoT solutions furthering those goals and how they may gain relevant insights from secondary data.
As IoT solutions move beyond their primary goals, it will be critical to evaluate the continually increasing data to mitigate risks of unintended consequences as new data sets converge. The security team will need to evaluate solutions and enforce standards. CDO and analysts will assess opportunities for data convergence to create new insights into how your services are used. |
|
IT stakeholders will be driving these projects forward and ensuring all necessary resources are available and funded.
Operational plans will include asset management, monitoring, and support to meet functional goals and manage throughout the asset lifecycle. Each solution added to the environment will need to be chosen and architected to meet primary functions and secondary data collection. |
Identify IoT steering committee participants to ensure broad assessment capabilities are available
|
|
Determine responsibilities of the committee to gain consensus and universal understanding
| STRATEGIC ALIGNMENT |
|
|
| VALUE DELIVERY |
|
|
| RISK OPTIMIZATION |
|
|
| RESOURCE OPTIMIZATION |
|
|
| PERFORMANCE MANAGEMENT |
|
1.1 Exercise:
Define the committee’s roles & responsibilities in the IoT steering committee charter
1-3 hours
Input: Current policies and assessment tools for security and privacy, Current IT strategy for introducing new solutions and setting standards
Output: List of roles and responsibilities, High-level discussion points
Materials: Whiteboard/flip charts, Steering committee workbook
Participants: IT executive, Privacy & Security senior staff, Infrastructure & Operations senior staff, Senior data specialist, Senior business executive(s)
- Identify and document core and auxiliary members of the committee, ensuring all important facets of the IoT environment can be assessed.
- Identify and document the committee chair.
- Gain consensus on responsibilities of the steering committee.
Download the IoT Steering Committee Charter
Define the vision statement for the IoT committee to clarify mandate and communicate to stakeholdersThe vision statement will define what you’re trying to achieve and how. You may have the statement already solidified, but if not, start with brainstorming several outcomes and narrow to less than 5 focus areas.A vision statement should be concise and should be in support of the overall IT strategy and organizational mission. The vision statement will be used as a high-level guide for defining and assessing proposed solutions and evaluating potential outcomes. It can be used as a limiter to quickly weed out ideas that don’t fit within the mandate, but it can also inspire new ideas.
|
New York City has a broad plan for implementing IoT to meet several aspects of their overall strategy and subsequently their IT strategy. Their strategic plan includes several focus areas that will benefit from IoT:
In order to accomplish this overall mission, they’ve created a specific IT vision statement: “Improve digital infrastructure to meet the needs of the 21st century.” This may seem broad, and it includes not just IoT, but also the need to upgrade infrastructure to be able to enable IoT as a tool to meet the needs to collect data, take action, and better understand how people move and live within the city. You can read more of their strategy at this |
1.2 Exercise:
Define the IoT steering committee’s vision statement and mandate
1 hour
Input: Organizational vision and IT strategy
Output: Vision statement
Materials: Whiteboard/flip charts, Steering committee workbook
Participants: Steering committee, which may include: IT executive, Privacy & Security senior staff, Infrastructure & Operations senior staff, Senior data specialist, Senior business executive(s)
- Starting with the organizational mission statement, brainstorm areas of focus with the steering committee and narrow down the statement.
- Make sure it’s broad enough to encompass your goals, but succinct enough to allow you to identify projects that don’t meet the vision.
- Test with a few existing ideas.
- Document in your steering committee charter.
Download the IoT Steering Committee Charter
Use the COPIS methodology to define your project review process
COPIS is a customer-focused methodology used to focus on the areas around the process, ensuring a holistic view starting with who the customer is and what they need, then building out the process and defining what will be required to be successful and who will be involved in fulfilling the work.
Customer
|
Outputs
|
Process
|
Inputs
|
Suppliers
|
| Agenda & process flow | Determine where people will access request form | Ending point | ||
|
||||
Create a committee charter to ensure roles are clarified and mandates can be met
| The purpose of the committee is to quickly assess and protect organizational interests while furthering the needs of the business
The committee needs to be seen as an enabler to the business, not as a gatekeeper, so it must be thorough but responsive. The charter should include:
|

|
1.3 Exercise:
Define procedures for reviewing proposals and projects
2-3 hours
Input: Schedules of committee members, Process documentation for evaluating new technology
Output: Procedures for reviewing proposals, Reference documentation for evaluating proposals
Materials: Whiteboard/flip charts, Steering committee workbook
Participants: Steering committee, which may include: IT executive, Privacy & Security senior staff, Infrastructure & Operations senior staff, Senior data specialist, Senior business executive(s)
- Discuss as a group how often you will meet for reviews and project updates. Which roles will have veto rights on project approvals?
- Define the intake process and requirements for scheduling based on average lead time to get the group together and preview documentation.
- Identify where process documentation already exists to use for evaluation of proposals and projects, and what needs to be created to quickly move from evaluation to action phases.
- Define basic rules of engagement.
- Define process flow using COPIS methodology as a framework. Note the different stages that may be part of the intake flow. Some business partners may bring solutions to IT, and others may just have an idea that needs to be solutioned.
Download the IoT Steering Committee Charter
Create and Implement an IoT Strategy
Phase 2
Define the intake and assessment process
Steering Committee1.1 Define the committee’s roles and responsibilities in the IoT Steering Committee Charter 1.2 Define the IoT steering committee’s vision statement and mandates 1.3 Define procedures for reviewing proposals and roles and responsibilities | Intake Process2.1 Define requirements for requesting new IoT solutions 2.2 Define procedures for reviewing proposals and projects – BA/BRM 2.3 Define procedures for reviewing proposals and projects – Data specialists 2.4 Define procedures for reviewing proposals and projects – Privacy & Security 2.5 Define procedures for reviewing proposals and projects – Infrastructure & Operations 2.6 Define service objectives and evaluation process | Proof of Value3.1 Determine the criteria for running a proof of value 3.2 Define the template and process for running a proof of value |
This phase will provide the following activities
- Define requirements for requesting new IoT solutions
- Define procedures for review proposals and projects
- Define service objectives and evaluation process for reviewing proposals and projects
Determine what information is necessary to start the intake process
To encourage your business leaders to engage IT in evaluating and appropriately supporting the solution, start with an intake process that is simple and easily populated with business information.
|
Business goals and benefits are important to ensure the completed solution meets the intended purpose and enables appropriate collection, analysis, and use of data in the larger business context. Ongoing operational support and service need to be considered to ensure ongoing value, and adherence to security and privacy policies is critical. |
2.1 Exercise:
Define requirements for requesting new IoT solutions
1 hour
Input: Business requirements for requesting IT solutions
Output: Request form for business users, Section 1 of the IoT Solution Playbook
Materials: Whiteboard/flip charts, IoT Solution Playbook
Participants: Steering committee, which may include: IT executive, Privacy & Security senior staff, Infrastructure & Operations senior staff, Senior data specialist, Senior business executive(s)
- Review template for the IoT Solution Playbook to ensure it meets your needs; modify as necessary.
- Determine requirements for initiating an assessment.
- Will a business case be necessary to start, or can the assessment feed into the business case?
- How can you best access the work already done by the requester to not start over?
- Determine the right questions to understand how they will define success to ensure this solution will do what they need.
- Do you need a breakdown of the way they do the job today?
- What level of authorization needs to be on the request to move forward?
- Try to balance the effort of the requester against their role. Don’t expect them to investigate solutions beyond the business value.
- Provide them with a means to provide you any information they have gathered, especially if they have already spoken to vendors.
Download the IoT Solution Playbook
Define what role the BA or BRM will play to support the request process
Identify questions that will need to be answered in order to assess if the solution will be fit for purpose, to help build out business cases, and to enable the appropriate assessments and engagement with project managers and technical teams.
Download the blueprint Embed Business Relationship Management in IT if you need help to support the business in a more strategic manner. | Info-Tech InsightUnderstanding the business issue more deeply can help the business analyst determine if the solution needs a review of business process as well as helping to build out the requirements well enough to improve chances of success. The BA should be able to determine initial workload and involvement of project managers and evaluators. |
Clearly articulate the business benefits to secure funding and resources
If the business users need to build a business case, the information being collected will help to define the value, estimate costs, and evaluate risk
IoT point solutions can be straightforward to articulate the business benefits as they will have very specific benefits which will likely fit into one of these categories:
As you start to look at the bigger picture of how these different systems can bring together disparate data sets, the benefits will be harder to define, and the costs to implement this next level of data analysis can be daunting and expensive. This doesn’t necessitate a complete alignment of data collection purposes; there may be benefits to improving operations in secondary areas such as updating HVAC systems to reduce energy costs in a hospital, though the updated systems may also include sensors to monitor air quality and further improve patient outcomes. In these cases, there may be future opportunities to use this data in unexpected ways, but even where there aren’t, applying the same standards for security, privacy, and operations should apply. |
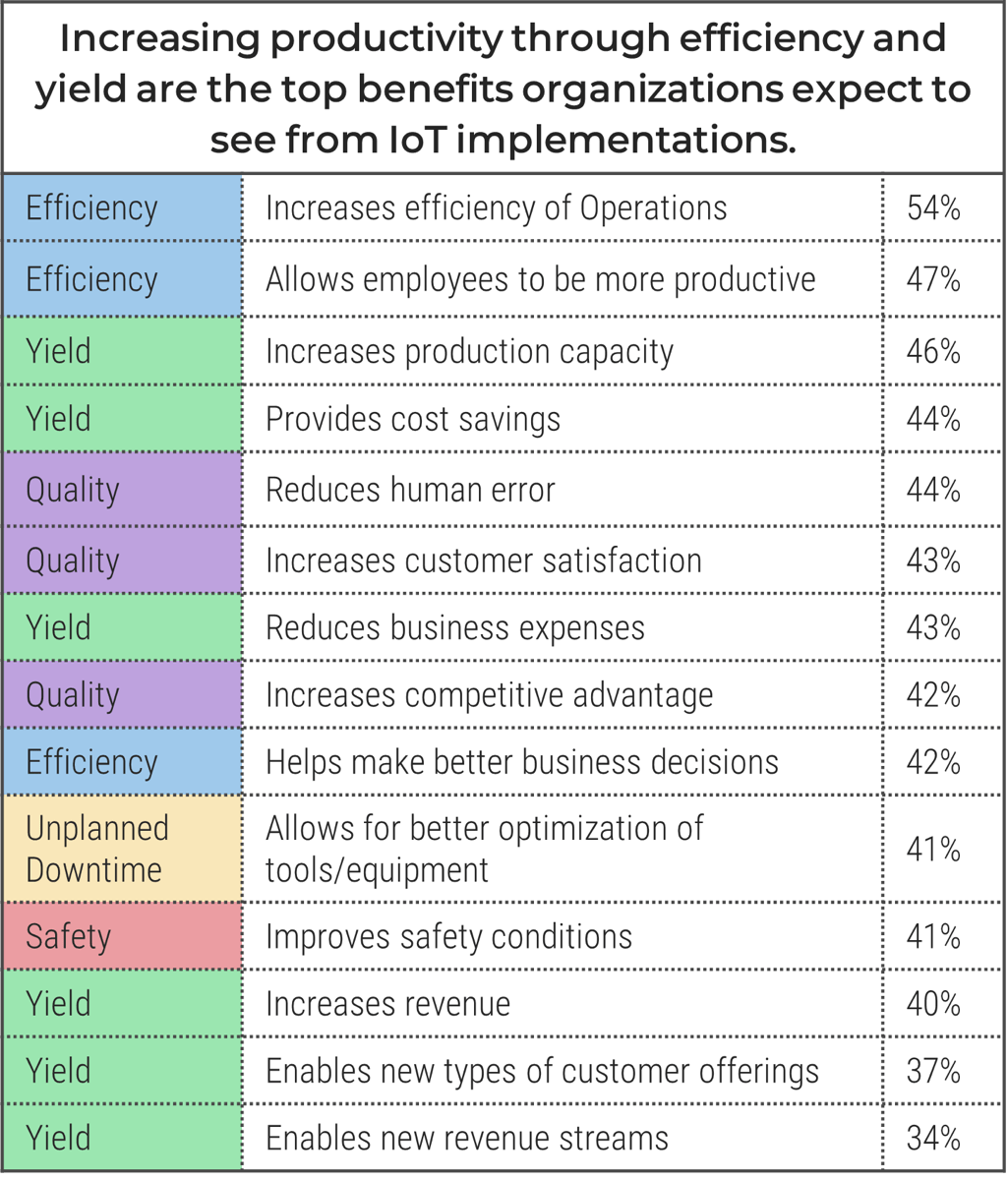
(Microsoft IoT Signals Report 2020, n= 3,000 IT Professionals) |
2.2 Exercise – BA/BRM: Define procedures for reviewing proposals and projects
1 hour
Input: Process documentation for evaluating new technology, Business case requirements
Output: Interview questions and assessment criteria for BA/BRM
Materials: Whiteboard/flip charts, IoT Solution Playbook
Participants: Steering committee, which may include: Business analyst or business relationship manager, IT executive(s), Senior data specialist, Senior business executive(s)
- Review template for the IoT Solution Playbook to ensure it meets your needs; modify as necessary.
- Identify the questions that will need to be asked of the business to determine whether the request will be fit for purpose.
- Additional questions may help to:
- Identify project sponsors to determine if requirements are defined or need to be, and who will champion this project through to implementation.
- Identify what additional work will be needed for you to shepherd the project through the various stage gates.
- Identify any prioritization criteria including business-specific milestones and outcomes.
- Document when a formal business case needs to be created.
Download the IoT Solution Playbook
Assess the vendor’s solution for accessibility to ensure data will be available and useable
| Data governance, including stewardship and ownership; lineage; and the ability to scale, deduplicate, normalize, validate, and aggregate disparate data will be critical to being able to analyze data to execute on strategic goals. |
If your organization isn’t poised to manage and make the best use of the data, see Info-Tech’s related blueprints: Relevant Research: Diagnostic: |
|
Data ownership is important to establish early on, as the owner(s) will be accountable for how data is used and accessed. Data needs to be owned by the organization (not the vendor) and needs to be accessible for:
|
Data validation will have different levels of importance depending on the use case. Where data validation is critical, there may be a need to double up sensors in key areas, validate against adjacent sensors, better understand how and where data will be collected.
|
|
Determine how often you need to access and download data
Requirements will vary depending on whether sensors are collecting data for later analysis or if they are actuators that need to process data at the source.
| Determine where the data will reside and how it will be structured. If it will be open and controlled within your own environment, confer with your data team to ensure the solution is integrated into your data systems. If, however, the solution is a point solution which will be hosted by the vendor, understand who will be normalizing the data and how frequently you can export or transfer it into your own data repository. If APIs will need to be installed to enable data transfer, work with the vendor to test them.
Self-contained or closed solutions may be quick to install and configure and may require minimal technical support from within your own IT team, but they will not provide visibility to the inner workings of the solution. This may create issues around integration and interoperability which could limit the functionality and usability beyond the point solution. If the solution chosen is a closed system, determine how you will need to interact with the vendor to gain access to the data. Interoperability may not be an option, so work with the vendor to set up a regular cadence for accessing the data. Questions for the vendor could include:
|

|
Identify whether digital twins are needed
Create a virtual world to safely test and fail without impacting the real-world applications.
| As actuators are processing information and executing actions, there may be a benefit to assess the effectiveness and impact of various scenarios in a safe environment. Digital twins enable the creation of a virtual world to test these new use cases using real world scenarios.
These virtual replicas will not be necessary for every IoT application as many solutions will be very straightforward in their application. But for those complex systems, such as smart buildings, smart cities and mechanically complex projects, digital twins can be created to run multiple simulations to aid in business continuity planning, performance assessments, R&D and more. Due to the expense and complexity of creating a full digital twin, carefully weighing the benefits, and identifying how it will be used, can help to build the business case to invest in the technology. Without the skills in house, reliance on a vendor to create the model and test scenarios will likely be part of the overall solution. The assessment will also include understanding what data will be transferred into the model, how often it will be updated, how it will be protected and who will need to be involved in the modeling process. Download the blueprint: Double Your Organization’s Effectiveness With a Digital Twin. if you need more information on how to leverage digital twin technology. |

|
To fully realize value in IoT, think beyond single use case solutions to leverage the data collected
Expertise in data analysis will be key to moving forward with an enterprise approach to IoT and the data it produces.- A single IoT solution can add hundreds of sensors, collecting a wide variety of data for specific purposes. If multiple solutions are in place, there may be divergent data sets that may never be seen by anyone other than their specific data stewards.
- Many organizations have started out with one or two solutions that support their primary business and may include some more mature offerings such as HVAC systems, which have used sensors for years. However, not all data is used today. In many cases, data is used for anomaly detection to improve operations, and only the non-standard information is used for alerting. McKinsey estimates less than 1% of data is used in these applications, with the remaining data stored or deleted, rather than used for optimization and predictive analysis.
- Thinking beyond the initial use cases, there may be opportunities to create new services, improve services for existing products, or improve insights through analysis of juxtaposed data.
- McKinsey reports up to $11.1 trillion a year in economic value may be possible by 2025 through the linking of the physical and digital worlds. Personal devices and all industries are potential growth areas – though factories and anywhere that could use predictive maintenance, cities, retail, and transportation will see the largest probable increases. Interoperability was identified as being required to maximize value, accounting for 40% to 60% of the potential value of IT applications.
- Where data is used to correct and control anomalies, very little data is retained and used for optimization or predictive analysis. By taking a deliberate approach to normalize, correlate, and analyze data, organizations can gain insight into the way their products are used, benefit from predictive maintenance, improve health care, reduce costs, and more.
By 2025 an estimated data volume of 79.4 zettabytes will be attributed to connected IoT devices. (Statistia)
Build data governance and analysis into your strategy to find new insights from correlating new and existing data
As a point solution, IoT provides a means to collect large amounts of data quickly and act. When determining the use case for IoT and best fit solutions, it’s important to think about what data needs to be collected and what actions will need to be coordinated. As the need for more than just a few IoT solutions surfaces, the complexity and potential usefulness of data increases. This can lead to significant changes to the scope of data collection, storage, and analysis and may lead to unintended consequences.- Some industries, such as governments looking to build smart cities, will have a very broad range of opportunities for IoT devices, as well as high levels of difficulty managing very disparate systems; other industries, such as healthcare, will have very focused prospects for data collection and analysis.
- In any case, the introduction of new IoT solutions can create very large amounts of data quickly, and if used only for a single purpose, there may be lost opportunity for expanding use of data to better understand your product, customers, or environment.
- Don’t limit analysis to only IoT-collected data, as this can be consolidated with other sources for validation, enhancement, and insights. For example, fleet transponders can be connected to travel logs and dispatch records for validation and evaluation of fuel and resource consumption.
- Determine the best time and methods for consolidation and normalization; consider using data consolidation vendors if the expertise is not available in-house.
- As data combines, there may be unintended consequences of unique anonymous identifiers combining to identify employees or customers, and the potential for privacy breeches will need to be evaluated as all new systems come on-line.
“We find very little IoT data in real life flows through analytics solutions, regardless of customer size. Even in the large organizations, they tend to build at-purpose applications, rather than creating those analytical scenarios or think of consolidating the IoT data in a data lake like environment.” (Rajesh Parab, Info-Tech Research Group)
2.3 Exercise – data specialists: Define criteria for assessing proposals and projects
1-2 hours
Input: Process documentation for evaluating new technology, Data governance documents
Output: Interview questions and assessment criteria for data specialists
Materials: Whiteboard/flip charts, IoT Solution Playbook
Participants: Steering committee, which may include: Business analyst or business relationship manager, IT executive, Senior data specialist, Senior business executive(s), Privacy & Security senior staff, Infrastructure & Operations senior staff
- Review template for the IoT Solution Playbook to ensure it meets your needs; modify as necessary.
- Identify the questions that will need to be asked of the solution to ensure data governance and accessibility needs will be met.
- Additional questions may help to:
- Identify data owners or stewards to determine who will have authority over data and ensure their needs will be met.
- Identify what additional work will be needed for the data team to access, validate, normalize, and centralize data.
- Identify any concerns that will identify the solution as unviable.
- Identify any risks to data accessibility which will require mitigation.
This initial review is designed to identify risks to data ownership or integrity and ensure data is available for additional uses as deemed appropriate to the organizational goals. This assessment is designed to find major flaws and to mitigate and integrate should the project be approved as viable.
Download the IoT Solution Playbook
Security assessments will need to include risk reviews specific to IoT
The increase of data collectors and actuators creates a large attack surface that could easily provide an entry point for hackers to connect into an organization’s network. Assess existing protocols and risk registry to ensure all IoT systems are reviewed for security threats.|
The significant increase in devices and applications will require a review of security practices related to IoT to understand and mitigate risks. Even if the data collected is not considered integral to the business, such as with automated HVAC systems or an aquarium monitoring system, the devices can provide an entry point to access the network. IoT and ICS devices are functionally diverse and may include more mature solutions that have been acquired many times over. There are a wide variety of protocols that may not be recognized by vulnerability scanners as safe to operate in your environment. Many of these solutions will be agentless and may not be picked up by scanners on the network. Without knowing these devices exist or understanding the data traffic patterns, protecting the devices, data, and systems they’re attached to becomes challenging. Discovery and vulnerability scanners tuned specifically for IoT to look for and allow unusual protocols and traffic patterns will enable these devices to operate as designed without being shut down by vulnerability scanners protecting more traditional devices and traffic on an IT network. Orphaned devices can be found and removed. Solutions that will provide detailed asset inventories and network topologies will improve vulnerability detection. Systems that are air gapped or completely segregated may provide a layer of protection between IoT devices and the corporate network, but this may create additional difficulties in vulnerability assessment, identifying and responding to active threats, or managing the operational side. Additionally, if there are still functional connections between these systems for traffic to flow back to central repositories, operational systems, or remote connections, there are still potential threats. |
If security controls are not yet documented, see Info-Tech’s related blueprints: Relevant Research: Diagnostic: |
Align risk assessments to your existing risk registry, to quickly approve low-risk solutions and mitigate high risk
Work with the business owner to understand how these systems are designed to work. Tracking normal patterns of behavior and traffic flow may be key to fine-tuning security settings to accommodate these solutions and prevent false positive shutdowns, especially if using automated remediation. Is the business owner identified, and will they be accessible throughout the lifecycle of the solution?Physical security: Will these systems be accessible to the public, and can they be secured in a way to minimize theft and vandalism? Will they require additional housing or waterproofing? Could access be completely secured? For example, could anyone access and install malware on a disconnected camera’s SD card?
Security settings: For ease of service and installation, a vendor may use default security settings and passwords. This can create easy access for hackers to access the network and access sensitive data. Is there a possibility of IP theft though access by sensors? Determine who will have remote access to the system, and if the vendor will be supporting the system, will they be using least privilege or zero trust models? Determine their adherence to your security policy.
Internet and network access and monitoring: Review connectivity and data transmission requirements and whether these can be accommodated in a way that balances security with operational needs. Will there be a need for air gapping, firewalls, or secure tunnelling, and will these solutions allow for discovery and monitoring? Can the vendor guarantee there are no back doors built into the code? Will the system be monitored for unauthorized access and activity, and what is the response process? Can it be integrated into your security operations center?
Failover state: IoT devices with actuators or that may impact health and safety will need to be examined. Can you ensure actions in event of a failure will not be negatively impactful? For example, a door that locks on failover and cannot be opened from the inside will create safety risks; however, a door that opens on failover could result in theft of property or IP. Who controls and can access these settings?
Firmware updates: Assess the history of updates released by the vendor and determine how these updates are sent to the devices and validated. Ensure the product has been developed using trusted platforms with security lifecycle models. Many devices will have embedded security solutions. Ensure these can be integrated into organizational security solutions and risk mitigation strategies.
Enterprise IoT strategy will require a focus on privacy and risk
Data aggregation creates new privacy concerns as data may be used outside of the original project parameters. The change of scope will need to be evaluated to determine personally identifiable information and what new issues it can create for the program, organization, and your audience.|
As a point solution, IoT provides a means to collect large amounts of data and, if actuators are completing tasks, act quickly. When determining the use case for IoT and best fit solutions, it’s important to think about what data needs to be collected and what actions will need to be coordinated. As the need for more than just a few IoT solutions surfaces, the complexity and potential usefulness of data increases. This can lead to significant changes to the scope of data collection, storage, and analysis, and may lead to unintended consequences. Questions to ask your vendors:
|
If data classification, privacy, and security controls are not yet documented, see Info-Tech’s related blueprints: Relevant Research: |
Don’t make assumptions about the type of data gathered with devices – ask the vendor to clearly state how and what is collected
| Carefully review how this information can be used by machine learning, in combination with other solutions, and if there is a possibility of unintended consequences that will create issues for your customers and therefore your own data sets.
Look for ways of capturing information that will meet your business requirements while mitigating risk of capturing personally identifiable information. Examples would be LiDAR to capture movement instead of video, or AI to blur faces or license plate numbers at time of image capture. This chart identifies data collected by smartphone accelerometers which could be used to identify and profile an individual and understand their behaviors. |
Mobile device accelerometer data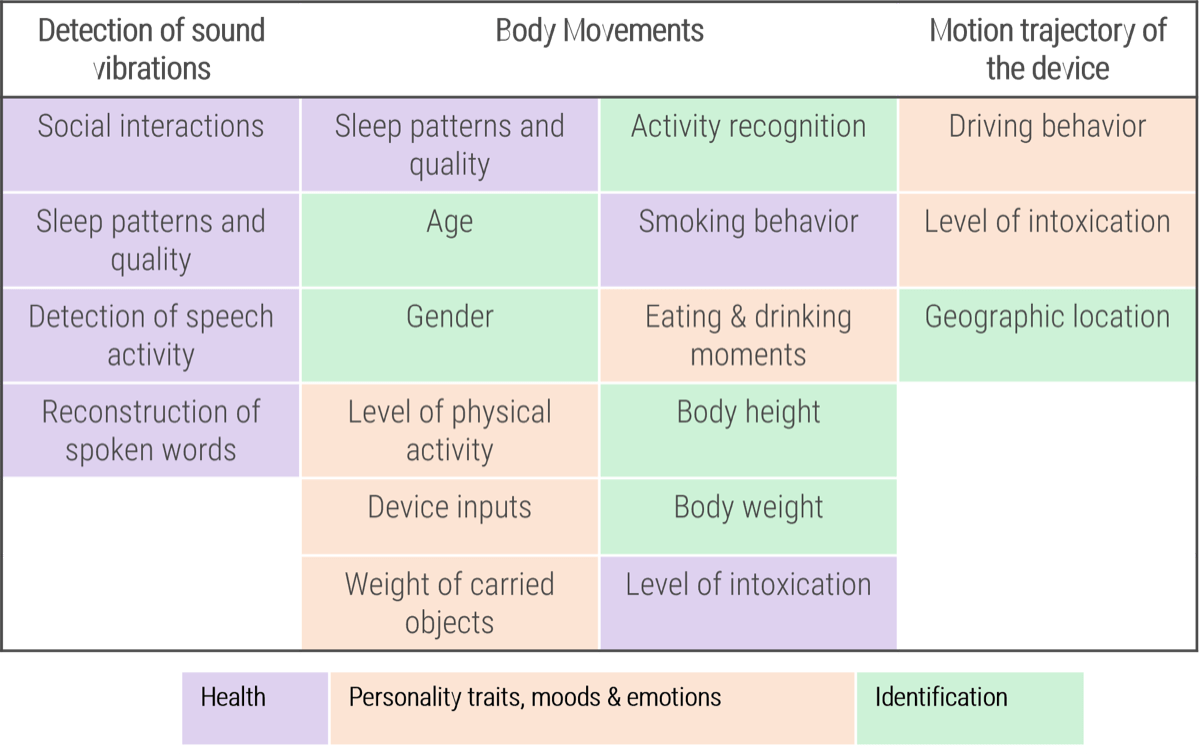
Overview of sensitive inferences that can be drawn from accelerometer data. (Source: Association for Computing Machinery, 2019.) |
2.4 Exercise – Privacy & Security specialists: Define criteria for assessing proposals and projects
1-2 hours
Input: Process documentation for evaluating new technology, Data governance documents
Output: Interview questions and assessment criteria for Privacy & Security specialists
Materials: Whiteboard/flip charts, IoT Solution Playbook
Participants: Steering committee, which may include: Business analyst or business relationship manager, IT executive, Senior data specialist, Senior business executive(s), Privacy & Security senior staff, Infrastructure & Operations senior staff
- Review template for the IoT Solution Playbook to ensure it meets your needs; modify as necessary.
- Identify the questions that will need to be asked of the solution to ensure security and privacy needs will be met.
- Additional questions may help to:
- Identify biggest risks created by a large influx of sensors and additional vendors.
- Identify options for mitigating risks for privacy and regulatory requirements.
This initial review is designed to identify risks to data ownership or integrity and ensure data is available for additional uses as deemed appropriate to the organizational goals. This assessment is designed to find major flaws and to mitigate and integrate should the project be approved as viable.
Download the IoT Solution Playbook
Review infrastructure requirements to proactively engage with vendors
A modernized architecture will provide needed flexibility for onboarding new IoT solutions as well as providing the structure to collect, transport, and house data; however, not everything will be on the network. Knowing requirements for integrations, communications, and support will eliminate surprises during implementation.|
The supporting applications will be collecting and analyzing data for each of these solutions, with most being hosted on public clouds or privately by the vendor. Access to the applications for data collection may require APIs or other middleware to transfer data outside of their application. Data transfer may be unimportant if the data collected will stand alone and never be integrated to other systems, but it will be critical if IoT plans include retrieving, aggregating, and analyzing data from most systems. If these systems are closed, determine the process to get this information, whether it’s through scheduled exports or batch transfers. Determine if data will be backed up by the vendor or if backups are the responsibility of your team. Work with the business owner to better understand business continuity requirements to plan appropriately for data transmission, storage, and archiving. Network and communications will vary dramatically depending on where sensors and actuators are located. On-premises solutions may rely on Wi-Fi on your network or may require an air-gapped or segregated network. External sensors may rely on public Wi-Fi, cellular, or satellite, and this may impact reliability and serviceability. If manual data collection is required, such as collecting SD cards on trail cams, who will be responsible, and will they have the tools and data repository they need to upload data manually? Are you able to work with the vendor to estimate traffic on these networks, and how will that impact costs for cellular or satellite service? Investigate power requirements. On-premises solutions may require additional wiring, but if using wind or solar, what is the backup? If using batteries, what is the expected lifespan? Who will be monitoring, and who will be changing the batteries? Determine monitoring requirements. Who should be responsible for performance monitoring, outages, data transmission, and validation? Is this a vendor premium service or a process to manage in-house? If managed by the vendor, discuss required SLAs and their ability to meet them. |
If your organization is dealing with technical debt and older architecture which could prevent progress, see Info-Tech’s related blueprints to build out the foundation. Relevant Research: |
Determine operational readiness to support and secure IoT solutions
Availability and capacity planning, business continuity planning, and management of all operational and support requirements will need to be put in place. Execution of controls, maintenance plans, and operational support will be required to mitigate risks and reduce value of the solutions.|
One of the biggest challenges organizations that have already adopted IoT face is management of these systems. Without an accurate inventory, it’s impossible to know how secure the IoT systems are. Abandoned sensors, stolen cameras, and old and unpatched firmware all contribute to security risks. Existing asset management solutions may provide the right solution, but they are limited in many cases by the discovery tools in place. Many discovery tools are designed to scan the network and may not have access to segregated or air-gapped networks or a means to access anything in the cloud or requiring remote access. Evaluate the effectiveness of current tools, and if they prove to be inadequate, look for solutions that are geared specifically to IoT as they may provide additional useful management capabilities. IoT management tools will provide more than just inventory. They can discover IoT devices in a variety of environments, possibly adding micro-agents to access device attributes such as name, type, and date of build, and allowing metadata and tags to be added. Additionally, these solutions will provide the means to deploy firmware updates, change configuration settings, send notifications if devices are taken offline, and run vulnerability assessments. Some may even have diagnostics tools for troubleshooting and remediation. |
If operational processes aren’t in place, see Info-Tech’s related blueprints to build out the foundation. Relevant Research: Diagnostic: |
Identify what needs to happen to onboard these solutions into your support portfolio
| Evaluate support options to determine the best way to support the business. Even if support is completely outsourced, a support plan will be critical for holding vendors to account, bringing support in-house if support doesn’t meet your needs, and understanding dependencies while navigating through incidents and problem- and change-enablement processes.
Regular maintenance for your team may include battery swaps, troubleshooting camera outages or intermittent sensors, or deploying patches. Understand the support requirements for the product lifecycle and who will be responsible for that work. If the vendor will be applying patches and upgrading firmware, get clarity on how often and how they’ll be deployed and validated. Ask the vendor about support documentation and offerings. Determine the best ways of collecting inventory on the solution. Determine what the solution offers to help with this process; however, if the project plan requires specific location details to add sensors, the project list may be the best way to initially onboard the sensors into inventory. Determine if warranty offerings are an appropriate solution for devices in each project, to schedule and record appropriate maintenance details and plan replacements as sensors reach end of life. Document dependencies for future planning. |

|
2.5 Exercise – Infrastructure & Operations specialists: Define criteria for assessing proposals and projects
1-2 hours
Input: Process documentation for evaluating new technology, Data governance documents
Output: Interview questions and assessment criteria for Infrastructure & Operations specialists
Materials: Whiteboard/flip charts, IoT Solution Playbook
Participants: Steering committee, which may include: Business analyst or business relationship manager, IT executive, Senior data specialist, Senior business executive(s), Privacy & Security senior staff, Infrastructure & Operations senior staff
- Review template for the IoT Solution Playbook to ensure it meets your needs; modify as necessary.
- Identify the questions that will need to be asked of the solutions to ensure the solutions can be integrated into the existing environment and operational processes.
- Additional questions may help to:
- Reduce risks and project failures from solutions that will be difficult to integrate or secure.
- Improve project planning for projects that are often driven by the vendor and the business.
- Reduce operational risks due to lack of integration with asset and operational processes.
This initial review is designed to identify risks to data ownership or integrity and ensure data is available for additional uses as deemed appropriate to the organizational goals. This assessment is designed to find major flaws and to mitigate and integrate should the project be approved as viable.
Download the IoT Solution Playbook
2.6 Exercise: Define service objectives and evaluation process
1 hour
Input: List of criteria in the playbook, Understanding of resource availability of solution evaluators
Output: Steering committee criteria for progressing projects through the process
Materials: Whiteboard/flip charts, IoT Steering Committee Charter workbook
Participants: Steering committee, which may include: Business analyst or business relationship manager, IT executive, Senior data specialist, Senior business executive(s), Privacy & Security senior staff, Infrastructure & Operations senior staff
Now that you’ve defined the initial review requirements, meet as a group once more to finalize the process for reviewing requests. Look for ways to speed the process, including asynchronous communications and reviews. Consider meeting as a group for any solutions that may be deemed high risk or highly complex.
- Agree on what can be identified as a reasonable SLA to respond to the business on these requests.
- Agree on methods of communication between committee members and the business.
- Determine the criteria for determining when a proof of value should be initiated, and who will lead the process.
Download the IoT Steering Committee Charter
Create and Implement an IoT Strategy
Phase 3
Prepare for a Proof of Value
Steering Committee1.1 Define the committee’s roles and responsibilities in the IoT Steering Committee Charter 1.2 Define the IoT steering committee’s vision statement and mandates 1.3 Define procedures for reviewing proposals and roles and responsibilities | Intake Process2.1 Define requirements for requesting new IoT solutions 2.2 Define procedures for reviewing proposals and projects – BA/BRM 2.3 Define procedures for reviewing proposals and projects – Data specialists 2.4 Define procedures for reviewing proposals and projects – Privacy & Security 2.5 Define procedures for reviewing proposals and projects – Infrastructure & Operations 2.6 Define service objectives and evaluation process | Proof of Value3.1 Determine the criteria for running a proof of value 3.2 Define the template and process for running a proof of value |
This phase will provide the following activities
- Create proof of value criteria
- Create proof of value template
A proof of value can quickly help you prove value or fail fast
Investing a small amount of time and money up front will validate the possibility of your proposed solution.
| A proof of value will require a vision and definition of your criteria for success, which will be necessary to determine if the project should go ahead. It should take no longer than three months and may be as short as a week.
When should you run a proof of value?
Info-Tech Insight
|
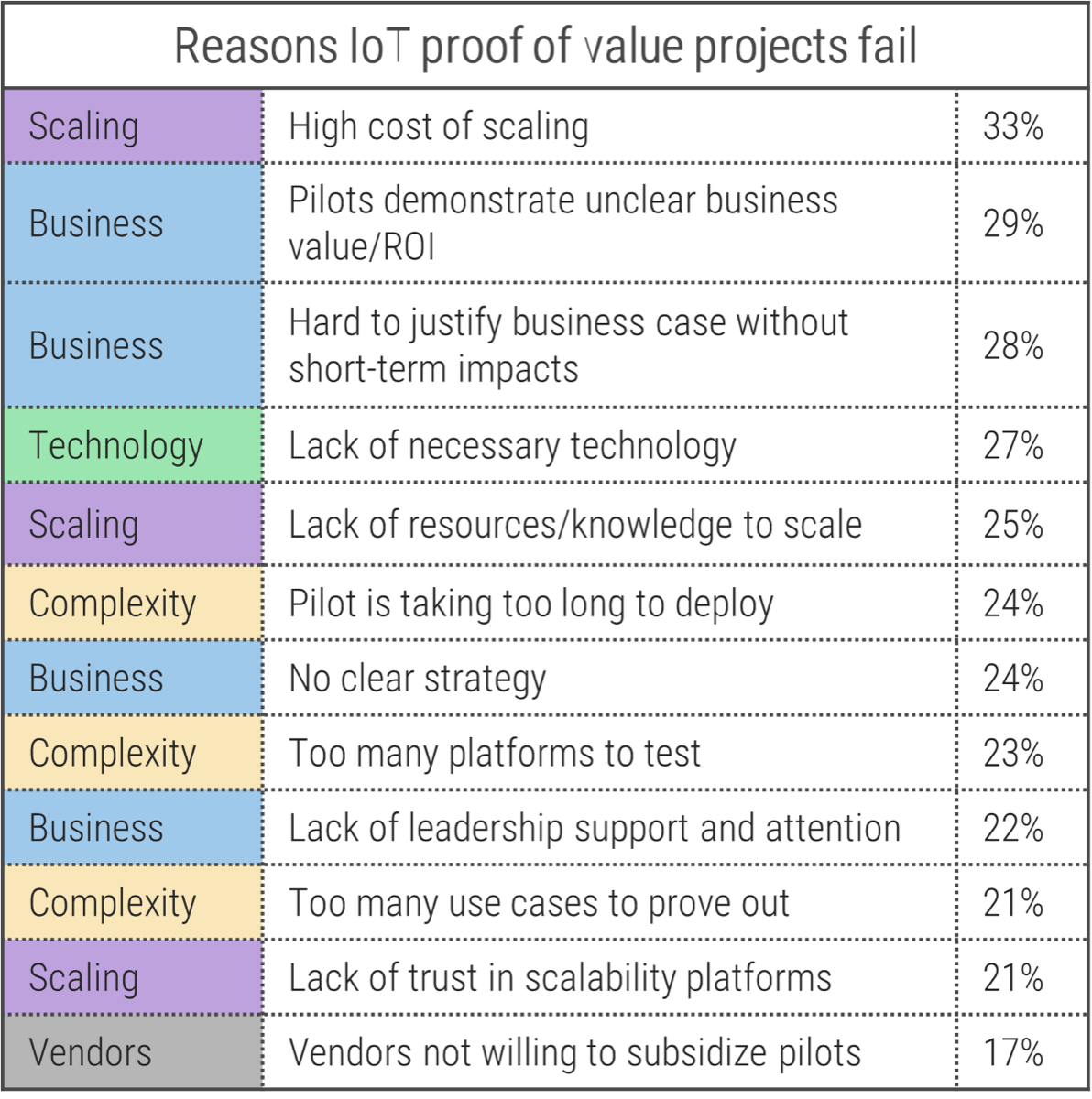
(Microsoft IoT Signals Report 2020, n= 3,000 IT Professionals) |
3.1 Exercise: Define the criteria for running a proof of value
1 hourInput: Agreement of steering committee members to create a process to mitigate risk for complex solutions.
Output: Proof of value template for use as appropriate to evaluate IoT solutions.
Materials: IoT Solution Playbook
Participants: Steering committee, which may include: Business analyst or business relationship manager, IT executive, Senior data specialist, Senior business executive(s), Privacy & Security senior staff, Infrastructure & Operations senior staff
- As a group, review the circumstances for when to run a proof of value.
- Determine who will help to build the proof of value plan.
- Determine requirements for participation in the proof of value process. Consider project size, complexity and risk and visibility.
Download IoT Solution Playbook
Design your proof of value to test the viability of the solution
Engage the right stakeholders early to gather feedback and analysis and determine suitability
Determine the proof of value methodology to ensure plan allows for fast testing
| Info-Tech InsightAdditional information on building out a process for testing new technology can be found in the blueprint: Exploit Disruptive Infrastructure Technology. “Although scope creep is not the only nemesis a project can have, it does tend to have the farthest reach. Without a properly defined project and/or allowing numerous changes along the way, a project can easily go over budget, miss the deadline, and wreak havoc on project success.” (University Alliance, Villanova University) |
Define your objectives for the proof of value
Referencing documents submitted to the committee, continue to refine the problem statement.
Objectives are a key first step to show the solution will meet your needs.
Info-Tech InsightKnow your metrics going into the proof of value. Document performance, quality, and time to do the work and compare to metrics in the proof of value. Agree on what success looks like, to ensure that improvements are substantial enough to justify the expense and effort of implementing the solution. | Questions to consider:
Info-Tech InsightBe sure to avoid scope creep! Remember: the goal of the proof of value project is to produce a minimum case for viability in a carefully defined area. Reserve a detailed accounting of costs and benefits for after the proof of value stage. |
Define use cases to test against current methods
Outline the solution to the problem
Determine how the solution should perform in completing tasks. Be careful not to focus too heavily on how things are done today: You’re looking for dramatic improvements, not going back to existing workarounds.
|
Define steps to reach these goals today:
|
Determine the appropriate project team
Bring in team members from the business and technical sides to test for those functions that matter most to each team. This effort will enable them to quickly identify risks and mitigate them as part of the product rollout or start the process to look at alternative solutions.
|
Leverage the insights of the diverse working group
|
Estimate the resources required for the pilot
Time, money, technology, resources
The benefit of running a proof of value is to make a decision on viability of a solution without the expense of implementing a full solution. This isn’t necessary for low-risk, highly proven solutions, which could be validated with references instead.
Estimate |
Estimate the number of hours needed to implement the proof of value. |
Estimate |
Estimate the hours needed for business users to test. |
Estimate |
Estimate the costs of technology. If the solution can be run in a vendor sandbox or in a test/dev instance in the cloud, you may be able to keep these costs very low. |
Determine |
Determine the appropriate number of devices to test in multiple locations and environments; work with the vendor to see if they have evaluation devices or discounts for proof of value purposes. |
Conduct a post-proof of value review to finalize the decision to move forward
Gather evaluators together to ensure the pilot team completed their assessments. A common failure of pilots is making assumptions around the level of participation that has taken place.- The core working group is responsible for producing a vision of the future and outlining new technology’s disruptive potential. The actual implementation of the proof of value (purchasing the hardware, negotiating the SLA with the vendor) is beyond the committee’s responsibilities.
- If the proof of value goes ahead, the facilitator should block some time to evaluate the completed project against the key performance indicators identified in the initial plan.
- Use the Proof of Value Template section of the IoT Solution Playbook to document POV requirements as well as finalizing the feedback loop.
- Determine ratings for the proof of value to identify which solutions are not viable and which levels of viability are worth moving forward. Some viable solutions may need a different vendor, and some may need customization or multiple integrations. This is important for the project team to move ahead with the implementation.
- Encourage everyone to provide enough feedback on the various processes to be confident in their declarations of worthiness and to confirm the proof of value was thorough.
- Communicate your working group’s findings and success to a wide audience to gain interest in IoT solutions as well as to encourage the business to work with the committee to integrate solutions into the governance and operational structure.
3.2 Exercise: Create a template for designing a proof of value
1-3 hours
Input: Agreement of steering committee members to create a process to mitigate risk for complex solutions
Output: Proof of value template for use as appropriate to evaluate IoT solutions
Materials: Whiteboard/flip charts, IoT Solution Playbook
Participants: Steering committee, which may include: Business analyst or business relationship manager, IT executive, Senior data specialist, Senior business executive(s), Privacy & Security senior staff, Infrastructure & Operations senior staff
- As a group, review the Proof of Value Template section of the IoT Solution Playbook to determine if it will meet the needs of your business and technical groups.
- Determine who will work with the business to create the proof of value plan.
- Modify the template to suit your needs, keeping in mind a need for clarity of purpose, communications throughout the POV, and clearly stated goals and definitions of success.
- Set a target timeframe to run the POV, preferably no longer than 90 days.
- Determine appropriate steps to take for POVs that do not garner the expected participation to qualify a solution to move forward.
- Determine appropriate reporting for the evaluation process.
Download IoT Solution Playbook
Communications
As with any new product, marketing and communications will be an important first step in letting the business know how to engage IT in its assessments of IoT innovations. As these solutions prove themselves, or even as you help the business to find better solutions, share your successes with the rest of the organization.
Business units are already being courted by the vendors, so it’s up to IT to insert themselves in the process in a way that helps improve the success of the business team while still meeting IT’s objectives.
Your customers will not willingly engage in highly bureaucratic processes and need to see a reason to engage.
- Keep the intake process simple.
- Provide support to answer the tough questions.
- Be clear on the benefits to the organization and the business unit by engaging with your group, and be clear about how you will help within a reasonable time frame.
- IT will help navigate the vendor prerequisites, contracts, and product setup.
- IT will assume some of the responsibility for the solution, especially around security and privacy.
- The business unit will reap the rewards of the solution with minimal operational effort.
Info-Tech Insight
Consider building your playbook into your service catalog to make it easy for business users to start the request process. From there, you can create workflows and notifications, track progress, set and meet SLAs, and enable efficient asynchronous communications.
Research Contributors and Experts

|
John Burwash
|
INFO~TECH RESEARCH GROUPInfo-Tech Research Group is an IT research and advisory firm with over 23 years of experience helping enterprises around the world with managing and improving core IT processes. They write highly relevant and unbiased research to help leaders make strategic, timely, and well-informed decisions.External contributors
|
||

|
Jennifer Jones
|

|
Aaron Shum
|
|

|
Rajesh Parab
|

|
Frank Sargent
|
|

|
Scott Young
|

|
Rocco Rao
|
Related Info-Tech Research

|
Understand and apply Internet-of-Things Use Cases to Drive Organizational Success
A concise guide to understanding how IoT applications will create value in your firm. |
Industry Coverage
Access industry-specific publications focused on IoT by adding Industry Coverage to your subscription. Contact your account manager for details.
Bibliography
Ayyaswamy, Regu, et al. “IoT Is Enabling Enterprise Strategies for New Beginnings.” Tata Consulting Services, 2020. Web.
“Data Volume of Internet of Things (IoT) Connections Worldwide in 2019 and 2025.” Statistia, 2020.
Dos Santos, Daniel, et al. “Cybersecurity in Building Automation Systems (BAS).” Forescout, 2020. Web.
Earle, Nick. “Overcoming the Barriers to Global IoT Connectivity: How Regional Operators Can Reap Rewards From IoT.” IoTNow, 30 June 2021. Web.
Faludi, Rob. “How Do IoT Devices Communicate?” Digi, 26 Mar. 2021. Web.
Halper, Fern, and Philip Russom. “TDWI IoT Data Readiness Guide, Interpreting Your Assessment Score.” Cloudera, 2018. Web.
Horwitz, Lauren. “IoT Enterprise Deployments Continue Apace, Despite COVID-19.” IoT World Today, 22 Apr. 2021.
“How Does IoT Data Collection Work?” Digiteum, 13 Feb. 2020. Web.
“IoT Data: How to Collect, Process, and Analyze Them.” Spiceworks, 26 Mar. 2019. Web.
IoT Signals Report: Edition 2, Hypothesis Group for Microsoft, Oct. 2020. Web.
King, Stacey. “4 Key Considerations for Consistent IoT Manageability and Security.” Forescout, 22 Aug. 2019. Web.
Krämer, Jurgen. “Why IoT Projects Fail and How to Beat the Odds.” Software AG, 2020. Web.
Kröger, Jacob Leon, et al. “Privacy Implications of Accelerometer Data: A Review of Possible Inferences” ICCSP, Jan. 2019, pp. 81-7. Web.
Manyika, James, et al. “Unlocking the Potential of the Internet of Things.” McKinsey Global Institute, 1 June 2015. Web.
Ricco, Emily. “How To Run a Successful Proof of Concept – Lessons From Hubspot.” Filtered. Web.
Rodela, Jimmy. “The Blueprint, Your Complete Guide to Proof of Concept.” Motley Fool, 2 Jan 2021. Web.
Sánchez, Julia, et al. “An Integral Pedagogical Strategy for Teaching and Learning IoT Cybersecurity.” Sensors, vol. 20, no. 14, July 2020, p. 3970.
The IoT Generation of Vulnerabilities. SC Media, 2020. E-book.
Woods, James P., Jr. “How Consumer IoT Devices Can Break Your Security.” HPE, 2 Nov. 2021.
Buying Options
Create and Implement an IoT Strategy
IT Risk Management · IT Leadership & Strategy implementation · Operational Management · Service Delivery · Organizational Management · Process Improvements · ITIL, CORM, Agile · Cost Control · Business Process Analysis · Technology Development · Project Implementation · International Coordination · In & Outsourcing · Customer Care · Multilingual: Dutch, English, French, German, Japanese · Entrepreneur
Tymans Group is a brand by Gert Taeymans BV
Gert Taeymans bv
Europe: Koning Albertstraat 136, 2070 Burcht, Belgium — VAT No: BE0685.974.694 — phone: +32 (0) 468.142.754
USA: 4023 KENNETT PIKE, SUITE 751, GREENVILLE, DE 19807 — Phone: 1-917-473-8669
Copyright 2017-2022 Gert Taeymans BV


