Bibliography
360Solutions, LLC. “The High Cost of Poor Communication: How to Improve Productivity and Empower Employees Through Effective Communication.” 360Solutions, 2009. Web.
Ali, M., B. Raza, W. Ali, and N. Imtaiz. Linking Managerial Coaching with Employees’ Innovative Work Behaviors through Affective Supervisory Commitment: Evidence from Pakistan. International Review of Management and Marketing, vol. 10, no. 4, 2020, pp. 11-16.
Allen, Frederick E. “The Terrible Management Technique That Cost Microsoft Its Creativity.” Forbes.com, 3 July 2012. Web.
Allen, Renee. “Generational Differences Chart.” West Midland Family Center, n.d. Web.
American Management Association. “Leading the Four Generations at Work.” American Management Association, Sept. 2014. Web.
Aminov, Iskandar, Aaron De Smet, Gregor Jost, and David Mendelsohn. “Decision making in the age of urgency.” McKinsey & Company, 30 April 2019. Web.
AON Hewitt. “Aon Hewitt Study Reveals Strong Link Between Employee Engagement and Employee Perceptions of Total Rewards. Honest Leader Communication Also Influences Engagement.” PR Newswire, 8 April 2015. Web.
Armstrong, Brad. “How to Fail as a New Engineering Manager.” Noteworthy - The Journal Blog, 19 Feb. 2018. Web.
Asmus, Mary Jo. “Coaching vs. Feedback.” Aspire-CS, 9 Dec. 2009. Web.
Baldwin, Timothy T., et al. “The State of Transfer of Training Research: Moving Toward More Consumer-Centric Inquiry.” Human Resource Development Quarterly, vol. 28, no. 1, March 2017, pp. 17-28. Crossref, doi:10.1002/hrdq.21278.
Batista, Ed. “Building a Feedback-Rich Culture from the Middle.” Ed Batista, April 2015. Web.
Bilalic, Merim, Peter McLeod, and Fernand Gobet. Specialization Effect and Its Influence on Memory and Problem Solving in Expert Chess Players. Wiley Online Journal, 23 July 2009, doi: https://doi.org/10.1111/j.1551-6709.2009.01030.x
Blume, Brian D., et al. “Transfer of Training: A Meta-Analytic Review.” Journal of Management, vol. 36, no. 4, July 2010, pp. 1065-105. Crossref, doi:10.1177/0149206309352880.
BOH Training Guide. Wild Wing, Jan. 2017. Web.
Bosler, Shana. “9 Strategies to Create Psychological Safety at Work.” Quantum Workplace, 3 June 2021. Web.
Building Communication Skills. ACQUIRE Project/EngenderHealth, n.d. Web.
Bucaro, Frank C. “The real issue in conflict is never about things…” Frank Bucaro blog, 7 March 2014. Web.
Burke, Lisa A., and Holly M. Hutchins. “Training Transfer: An Integrative Literature Review.” Human Resource Development Review, vol. 6, no. 3, Sept. 2007, pp. 263-96. Crossref, doi:10.1177/1534484307303035.
Caprino, Kathy. “Separating Performance Management from Compensation: New Trend for Thriving Organizations.” Forbes, 13 Dec. 2016. Web.
Caprino, Kathy. “Why the Annual Review Process Damages Employee Engagement.” Forbes, 1 March 2016. Web.
Carpineanu, Silvana. “7 Mistakes You Might Be Making When Writing A Meeting Agenda.” Time Doctor, 12 January 2021. Web.
Cecchi-Dimeglio, Paola. “How Gender Bias Corrupts Performance Reviews, and What to Do About It.” Harvard Business Review, 12 April 2017. Web.
Chartered Institute of Personnel and Development (CIPD). “PESTLE Analysis.” Chartered Institute of Personnel and Development, 2010. Web.
Chiaburu, Dan S., et al. “Social Support in the Workplace and Training Transfer: A Longitudinal Analysis: Social Support and Training Transfer.” International Journal of Selection and Assessment, vol. 18, no. 2, June 2010, pp. 187-200. Crossref, doi:10.1111/j.1468-2389.2010.00500.x.
Christensen, Ulrik Juul. “How to Teach Employees Skills They Don’t Know They Lack.” Harvard Business Review, 29 Sept. 2017. Web.
CIPD. “Rapid evidence assessment of the research literature on the effect of goal setting on workplace performance.” Charted Institute of Personnel and Development, Dec. 2016. Web.
CIPD. Annual Survey Report: Learning & Development 2015. Charted Institute of Personnel and Development, 2015. Web.
Communication and Organizational Skills: NPHW Training Manual. Population Health Research Institute (PHRI), 17 Sept. 2015. Web.
Cookson, Phil. “It’s time to see performance management as a benefit, not a burden.” CIPD. 17 March 2017. Web.
Communication Statistics 2021. Project.co, 2021. Web.
Connors, Roger. “Why Accountability?” The Oz Principle, Partners In Leadership, 2014.
Coutifaris, Constantinos G. V., and Adam M. Grant “Taking Your Team Behind the Curtain: The Effects of Leader Feedback-Sharing and Feedback-Seeking on Team Psychological Safety.” Organization Science, vol. 33,
no. 4, 2021, pp. 1574-1598. https://doi.org/10.1287/orsc.2021.1498
Coy, Charles. “Peer Feedback: 6 Tips for Successful Crowdsourcing.” Rework, 25 June 2014. Web.
“CQ Learn What Really Matters.” CQ Evidence-Based Management Learning Platform, n.d. Web.
Darwant, Sarah. Coaching Training Course Book. Elite Training, 2012. Web.
De Smet, Aaron, et al. How Companies Manage the Front Line Today: McKinsey Survey Results. McKinsey, Feb. 2010. Web.
DeNault, Charles. “Employee Coaching Survey Results: Important and Engaging.” Saba, 22 April 2015. Web.
Dermol, Valerij, and Tomaž Čater. “The Influence of Training and Training Transfer Factors on Organisational Learning and Performance.” Personnel Review, vol. 42, no. 3, April 2013, pp. 324–48. Crossref, doi:10.1108/00483481311320435.
dgdotto. “Fail to Plan, Plan to Fail.” visual.ly, 30 April 2013. Web.
Duggan, Kris. “Why the Annual Performance Review is Going Extinct.” Fast Company, 20 Oct. 2015. Web.
Duhigg, Charles. “What Google Learned From Its Quest to Build the Perfect Team.” The New York Times, 25 Feb. 2016. Web.
Earley, P. Christopher, and Randall S. Peterson. “The Elusive Cultural Chameleon: Cultural Intelligence as a New Approach to Intercultural Training for the Global Manager.” Academy of Management Learning & Education, vol. 3, no. 1, March 2004, pp. 100-15. Crossref, doi:10.5465/amle.2004.12436826.
Edmondson, Amy. “Psychological Safety and Learning Behavior in Work Teams.” Administrative Science Quarterly, vol. 44, no. 2, June 1999, pp. 350-383. Web.
“Effective Employee Communications Fosters Corporate Reputation.” The Harris Poll, 10 June 2015. Web.
Eichenwald, Kurt. “How Microsoft Lost its Mojo: Steve Ballmer and Corporate American’s Most Spectacular Decline.” Vanity Fair, 24 July 2012. Web.
Essential Supervisory Skills. University of Washington, 2016. Web.
“Estimating the Costs of Workplace Conflict.” Acas, 11 May 2021. Web.
Falcone, Paul. “Viewpoint: How to Redesign Your Performance Appraisal Template.” Society for Human Resource Management, 7 June 2017. Web.
Fermin, Jeff. “Statistics On The Importance Of Employee Feedback.” Officevibe, 7 Oct. 2014. Web.
Filipkowski, Jenna, et al. Building a Coaching Culture with Millennial Leaders. Human Capital Institute, 18 Sept. 2017. Web.
First Time Manager Training to Help New Managers Develop Essential Skills. The Ken Blanchard Companies, n.d. Web.
Fisher, Dan. Feedback vs. Coaching, What’s the Difference? Menemsha Group, 28 June 2018. Web.
Freedman, Erica. “How to Build an Internal Leadership Development Program.” Chief Executive, 2016. Web.
"Futureproof Your Organization with These 8 Manager Effectiveness Metrics.” Visier Inc., 8 Aug. 2017. Web.
Gallo, Amy. “How to Manage Your Former Peers.” Harvard Business Review, Dec. 2012. Web.
Gandhi, Vipula. “Want to Improve Productivity? Hire Better Managers.” Gallup, 3 Aug. 2018. Web.
Gallup. State of the Global Workplace. 1st edition, Gallup Press, 2017. Web.
Global Workplace Analytics. “Latest Telecommuting Statistics.” Global Workplace Analytics. Sept. 2013. Web.
Goldsmith, Marshall. “Try Feedforward Instead of Feedback.” Leader to Leader Institute, 5 April 2011. Web.
Goldsmith, Marshall. "11 Guidelines for Influencing Top Decision Makers." Marshall Goldsmith, n.d. Web.
Goldsmith, Marshall. "I Know Less Than You Do – and It’s Okay!" Marshall Goldsmith, n.d. Web.
Goldsmith, Marshall. "Is It Worth It to Add Value? Not Always." Marshall Goldsmith, n.d. Web.
Goler, L., J. Gale, and A. Grant. “Let’s Not Kill Performance Evaluations Yet.” Harvard Business Review, Nov. 2016. Web.
Good Manager, Bad Manager. Grovo, 2016. Web.
Google People Operations. “Guide: Understand Team Effectiveness.” Google, n.d. Web.
Google’s New Manager Student Workbook. re:Work with Google, n.d. Web.
Google’s New Manager Training Facilitator Guide. re:Work with Google, n.d. Web.
Gossen, Paul. A Coaching Culture Transformation ~ Case Study. Athena Training and Consulting, 1 April 2011. Web.
Goudreau, Jenna. “How to Communicate in the New Multi-Generational Office.” Forbes Magazine, Feb. 2013. Web.
Govaerts, Natalie, and Filip Dochy. “Disentangling the Role of the Supervisor in Transfer of Training.” Educational Research Review, vol. 12, June 2014, pp. 77-93. Crossref, doi:10.1016/j.edurev.2014.05.002.
Grenchus, Gabrielle. “Keep employees engaged with clear priorities and crowdsourced recognition.” IBM thinkLeaders. 8 June 2015. Web.
Grossman, Rebecca, and Eduardo Salas. “The Transfer of Training: What Really Matters: The Transfer of Training.” International Journal of Training and Development, vol. 15, no. 2, June 2011, pp. 103-20. Crossref, doi:10.1111/j.1468-2419.2011.00373.x.
Grote, Dick. “3 Popular Goal-Setting Techniques Managers Should Avoid.” Harvard Business Review. 2 Jan. 2017. Web.
Hall, John. “Why Accountability Is Vital To Your Company.” Forbes, 6 Oct. 2019. Web.
Hancock, Bryan, et al. “The Fairness Factor in Performance Management.” McKinsey, 5 April 2018. Web.
Harkins, Phil. “10 Leadership Techniques for Building High-Performing Teams.” Linkage Inc., 2014. Web.
HCI. Building a Coaching Culture with Managers and Leaders. Human Capital Institute, 2016. Web.
Heathfield, Susan M. “Tips to Create Successful Performance Appraisal Goals.” The Balance, Aug. 2016. Web.
Hills, Jan. Brain-Savvy Business: 8 Principles From Neuroscience and How to Apply Them. Head Heart + Brain, 2016. Print.
Hoffman, Mitchell, and Steven Tadelis. People Management Skills, Employee Attrition, and Manager Rewards: An Empirical Analysis. p. 96.
“How to Create an Effective Feedback Culture.” eXplorance Inc. Feb. 2013. Web.
“Importance of Performance Management Process & Best Practices To Optimize Monitoring Performance Work Reviews/Feedback and Goal Management.” SAP Success Factors, n.d. Web.
Jacobson, Darcy. “How Bad Performance Management Killed Microsoft’s Edge.” Globoforce Blog, 5 July 2012. Web.
Jaidev, Uma Pricilda, and Susan Chirayath. Pre-Training, During-Training and Post-Training Activities as Predictors of Transfer of Training. no. 4, 2012, p. 18.
Jensen, Michael C. “Paying People to Lie: The Truth about the Budgeting Process.” European Financial Management, vol. 9, no. 3, 2003, pp. 379-406. Print.
Kahneman, Daniel, and Ram Charan. HBR's 10 Must Reads on Making Smart Decisions. Harvard Business Review, 26 March 2013. Ebook.
Kirkpatrick, J., and W. Kirkpatrick. “The Kirkpatrick Four Levels: A Fresh Look After 50 Years 1959-2009.” Kirkpatrickpartners.com, 2009. Web.
Kirwan, Cyril. Improving Learning Transfer. Routledge, 2016.
Kline, Theresa J.B., and Lorne M. Sulsky. “Measurement and Assessment Issues in Performance Appraisal.” Canadian Psychology, vol. 50, no. 3, 2009, pp. 161-171. Proquest. Web.
Kowalski, Kyle. “Create a Daily Routine with Calendar Time Blocking (+ 7 Pro Tips).” Sloww, 29 May 2018. Web.
Krentz, Susanna E., et al. ”Staying on Course with Strategic Metrics.” Healthcare Financial Management, vol. 60, no. 5, 2006, pp. 86-94. Proquest. Web.
Kuligowski, Kiely. Tips for First-Time Managers. 15 Feb. 2019. Web.
Laker, Dennis R., and Jimmy L. Powell. “The Differences between Hard and Soft Skills and Their Relative Impact on Training Transfer.” Human Resource Development Quarterly, vol. 22, no. 1, March 2011, pp. 111-22. Crossref, doi:10.1002/hrdq.20063.
Lawrence, Paul. “Managerial coaching – A literature review.” International Journal of Evidence Based Coaching and Mentoring, vol. 15, no. 2, 2017, pp. 43-66. Web.
Ledford, Gerald E. Jr., George Benson, and Edward E. Lawler III. “Cutting-Edge Performance Management.” WorldatWork Research, Aug. 2016. Web.
Lee, W.R.; Choi, S.B.; Kang, S.-W. How Leaders’ Positive Feedback Influences Employees’ Innovative Behavior: The Mediating Role of Voice Behavior and Job Autonomy. Sustainability, vol. 13, no. 4, 2021, pp. 1901. https://doi.org/10.3390/su13041901
Leopold, Till Alexander, Vesselina Ratcheva, and Saadia Zahidi. The Future of Jobs. World Economic Forum, 2016. Web.
Levy, Dan. “How to Build a Culture That Embraces Feedback.” Inc. Magazine, March 2014. Web.
Lighthouse Research & Advisory. “Insights from the CHRO Panel at Workhuman 2017.” Lighthouse Research & Advisory, June 2017. Web.
Lipman, Victor. “For New Managers, Boundaries Matter (A Lot).” Forbes, 19 March 2018. Web.
Lipman, Victor. “The Hardest Thing For New Managers.” Forbes, 1 June 2016. Web.
Lipman, Victor. “The Move To New Manager May Be The Hardest Transition In Business.” Forbes, 2 Jan. 2018. Web.
Lyons, Rich. “Feedback: You Need To Lead It.” Forbes, 10 July 2017. Web.
“Managing Email Effectively.” MindTools, n.d. Web.
Managing Performance Workbook. Trainer Bubble, 16 Feb. 2013. Web.
Mayfield, Clifton, et al. “Psychological Collectivism and Team Effectiveness: Moderating Effects of Trust and Psychological Safety.” Journal of Organizational Culture, Communications and Conflict, vol. 20, no. 1, Jan. 2016, pp. 78-94. Web.
McAlpin, Kevin and Hans Vaagenes. “Critical Decision Making.” Performance Coaching International. 17 Nov. 2017. Web.
McCoy, Jim. “How to Align Employee Performance with Business Strategy.” Workforce Management, vol. 86, no. 12, 2007, pp. S5. Proquest. Web.
“Measuring Time-To-Full Productivity.” FeverBee, n.d. Web.
Meister, Jeanne. The 2020 Workplace: How Innovative Companies Attract, Develop, and Keep Tomorrow's Employees Today. HarperBusiness, 2010. Print.
Meyer, Erin. “The Four Keys To Success With Virtual Teams.” Forbes Magazine, 19 Aug. 2010. Web.
Morris, Donna. “Death to the Performance Review: How Adobe Reinvented Performance Management and Transformed Its Business.” WorldatWork, 2016, p. 10. Web.
Myers-Briggs Company. “New Research: Time Spent on Workplace Conflict Has Doubled Since 2008.” Yahoo! Finance, 18 Oct. 2022. Web.
Murdoch, Elisabeth. “Elisabeth Murdoch's MacTaggart lecture: full text.” The Guardian, 23 Aug. 2012. Web.
NASA Governance and Strategic Management Handbook (NPD 1000.0B). NASA, June 2014. Web.
NASA Space Flight Program and Project Management Handbook (NASA/SP-2014-3705). NASA, Sept. 2014. Web.
New Manager Training: Management & Leadership Skills. Schulich School of Business, n.d. Web.
O’Hanlon, Margaret. “It’s a Scandal! Manager Training Exposed! [Implementation Part 4].” Compensation Cafe, 16 Feb. 2012. Web.
Ordonez, Lisa D., et al. “Goals Gone Wild: The Systematic Side Effects of Over-Prescribing Goal Setting.” Social Science Research Network. Harvard Business School, 11 Feb. 2009. Web.
Paczka, Nina. “Meeting in the Workplace | 2023 Statistics.” LiveCareer, 25 July 2022. Web.
Pavlou, Christina. “How to Calculate Employee Turnover Rate | Workable.” Recruiting Resources: How to Recruit and Hire Better, 13 July 2016. Web.
Performance Management 101 Workbook. Halogen Software, 2015. Web.
Personal Development and Review. Oxford Learning Institute, n.d. Web.
Personal Development Plan. MindTools, 2014. Web.
Porath, Christine, et al. “The Effects of Civility on Advice, Leadership, and Performance.” Journal of Applied Psychology, vol. 44, no. 5, Sept. 2015, pp. 1527-1541. Web.
Project Management Institute. “PMI’s Pulse of The Profession: In-Depth Report.” PMI, May 2013. Web. June 2015.
Quay, C. C., and A. Yusof. “The influence of employee participation, rewards and recognition, job security, and performance feedback on employee engagement.” Issues and Perspectives in Business and Social Sciences, vol. 2, no. 1, 2022, pp. 20. https://doi.org/10.33093/ipbss.2022.2.1.3
Quinn, R. E., and J. Rohrbaugh. “A spatial model of effectiveness criteria: Towards a competing values approach to organizational analysis.” Management Science, vol. 29, 1983, pp. 363–377.
Re:Work Guide: Develop and Support Managers. re:Work with Google, n.d. Web.
Reardon, Kathleen Kelley. “7 Things to Say When a Conversation Turns Negative.” Harvard Business Review, 11 May 2016. Web.
Reh, F. John. “Here Is a List of Mistakes New Managers Make and How to Avoid Them.” The Balance Careers, 30 Dec. 2018. Web.
Richards, Leigh. “Why Is Employee Empowerment a Common Cornerstone of Organizational Development & Change Programs?” Houston Chronicle, Hearts Newspapers, LLC. 5 July 2013. Web.
Robson, Fiona. Southwood School – A Case Study: Performance Management Systems. Society for Human Resource Management, 2009. Crossref, doi:10.4135/9781473959552.
Rock, David, and Beth Jones. “Why More and More Companies are Ditching Performance Ratings.” Harvard Business Review, 8 Sept. 2015. Web.
Rock, David. “SCARF: A Brain-Based Model for Collaborating With and Influencing Others.” NeuroLeadership Journal, 2008. Web..
Romão, Soraia, Neuza Ribeiro, Daniel Roque Gomes, and Sharda Singh. “The Impact of Leaders’ Coaching Skills on Employees’ Happiness and Turnover Intention.” Administrative Sciences, vol. 12, no. 84, 2022. https://doi.org/10.3390/ admsci12030084
Romero, Joseluis. “Yes - you can build a feedback culture.” Skills 2 Lead, Aug. 2014. Web.
Runde, Craig E., and Tim A. Flanagan. “Conflict Competent Leadership.” Leader to Leader, Executive Forum, Winter 2008. PDF.
Saks, Alan M., and Lisa A. Burke-Smalley. “Is Transfer of Training Related to Firm Performance?: Transfer and Firm Performance.” International Journal of Training and Development, vol. 18, no. 2, June 2014, pp. 104–15. Crossref, doi:10.1111/ijtd.12029.
Saks, Alan M., et al. “The Transfer of Training: The Transfer of Training.” International Journal of Training and Development, vol. 18, no. 2, June 2014, pp. 81–83. Crossref, doi:10.1111/ijtd.12032.
Salomonsen, Summer. Grovo’s First-Time Manager Microlearning® Program Will Help Your New Managers Thrive in 2018. Grovo, 2018. Web.
Schwartz, Dan. “3 Topics Every New Manager Training Should Include.” Training Industry, 12 April 2017. Web.
Scott, Dow, Tom McMullen, and Mark Royal. “Retention of Key Talent and the Role of Rewards.” WorldatWork, June 2012. Web.
“Seeking Agility in Performance Management.” Human Resource Executive, 2016. Web.
“Should You Always Involve Your Team in Decision Making?” Upskillist, 25 April 2022. Web.
“SHRM Workplace Forecast.” The Top Workplace Trends According to HR Professionals, May 2013. Web.
Singhal, Nikhyl. “Eight Tips for First Time Managers.” Medium, 20 Aug. 2017. Web.
Singhania, Prakriti, et al. “2020 Global Marketing Trends.” Deloitte, 2019. Web.
SMART Goals: A How to Guide. University of California, n.d. Web.
Smith, Benson, and Tony Rutigliano. “Scrap Your Performance Appraisal System.” Gallup, 2002. Article.
“State of the Modern Meeting 2015.” BlueJeans, Aug. 2015. Web.
Sternberg, Larry, and Kim Turnage. “Why Make Managers A Strategic Priority?” Great Leadership, 12 Oct. 2017. Web.
Sullivan, Dr. John. “Facebook’s Difference: A Unique Approach For Managing Employees.”TLNT, Sept. 2013. Web.
Tal, David. “A 'Culture of Coaching' Is Your Company's Most Important Ingredient for Success.” Entrepreneur, 27 Sept. 2017. Web.
Tenut, Jeff. “How Management Development Training Reduces Turnover.” DiscoverLink, 3 July 2018. Web.
“The 5 Biggest Biases That Affect Decision-Making.” NeuroLeadership Institute, 2 August 2022. Web.
“The Different Impact of Good and Bad Leadership.” Barna Group, 2015. Web.
“The Engaged Workplace.” Gallup, 2017. Web.
“The Individual Development Plan Guide.” Wildland Fire Leadership Development Program, April 2010, p. 15.
The State of Business Communication. Grammarly, 2022. Web.
Thomas, Kenneth. “Conflict and Conflict Management.” The Handbook of Industrial and Organizational Psychology, Rand McNally, 1976. In “The Five Conflict-Handling Modes.” The Myers Briggs Company, n.d. PDF.
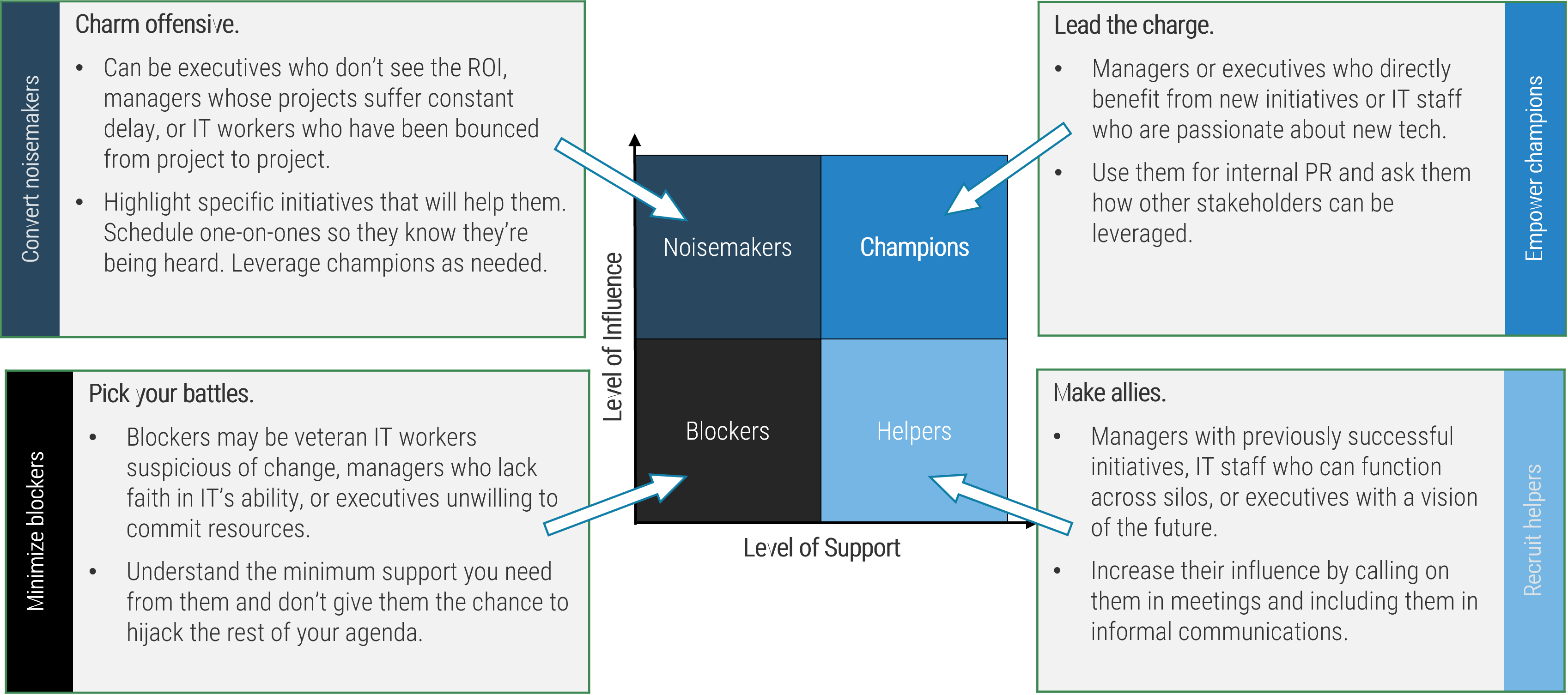
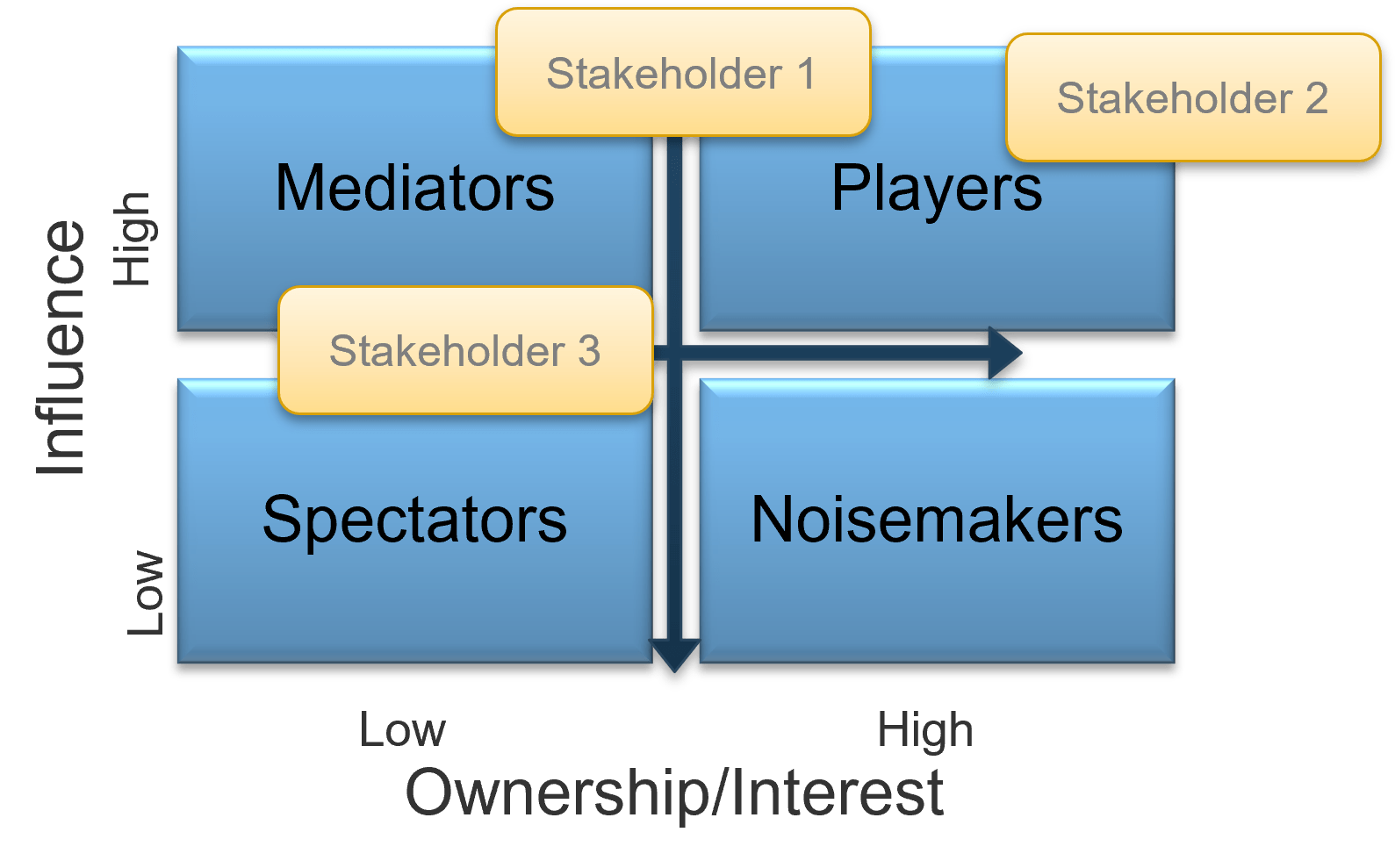
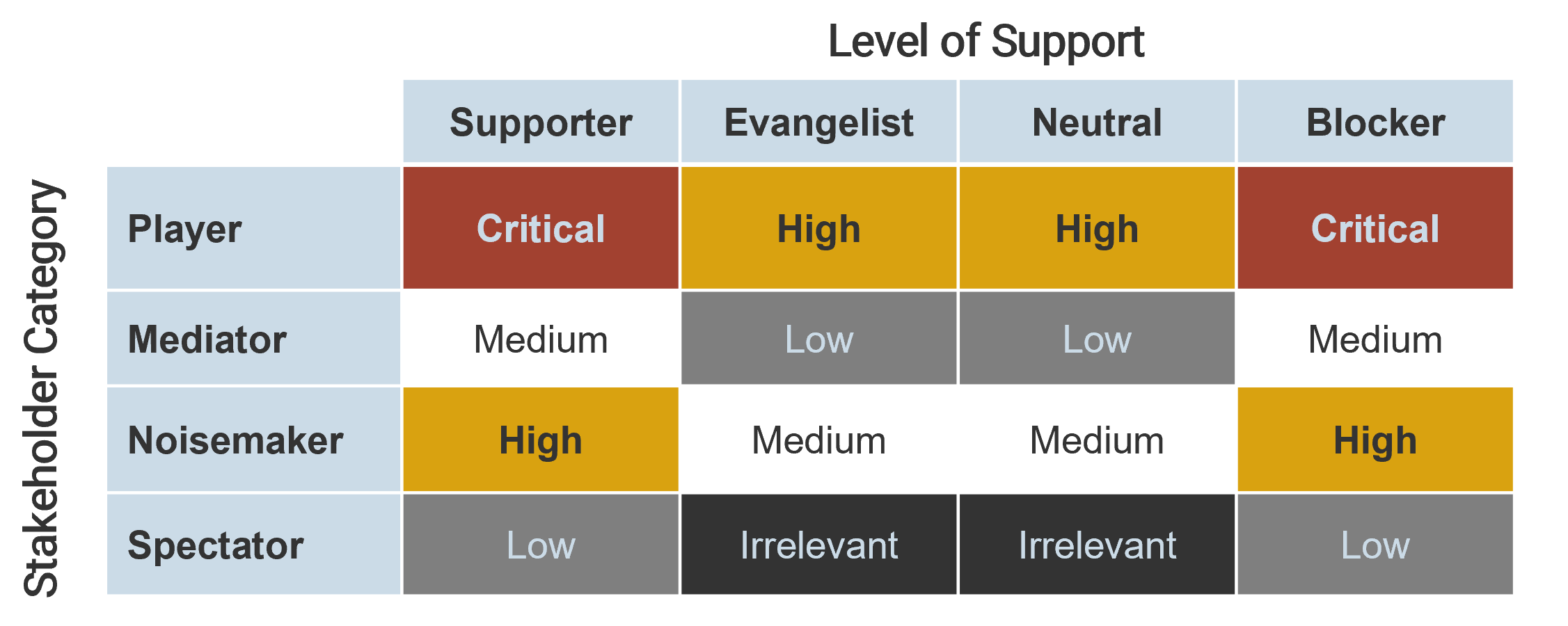
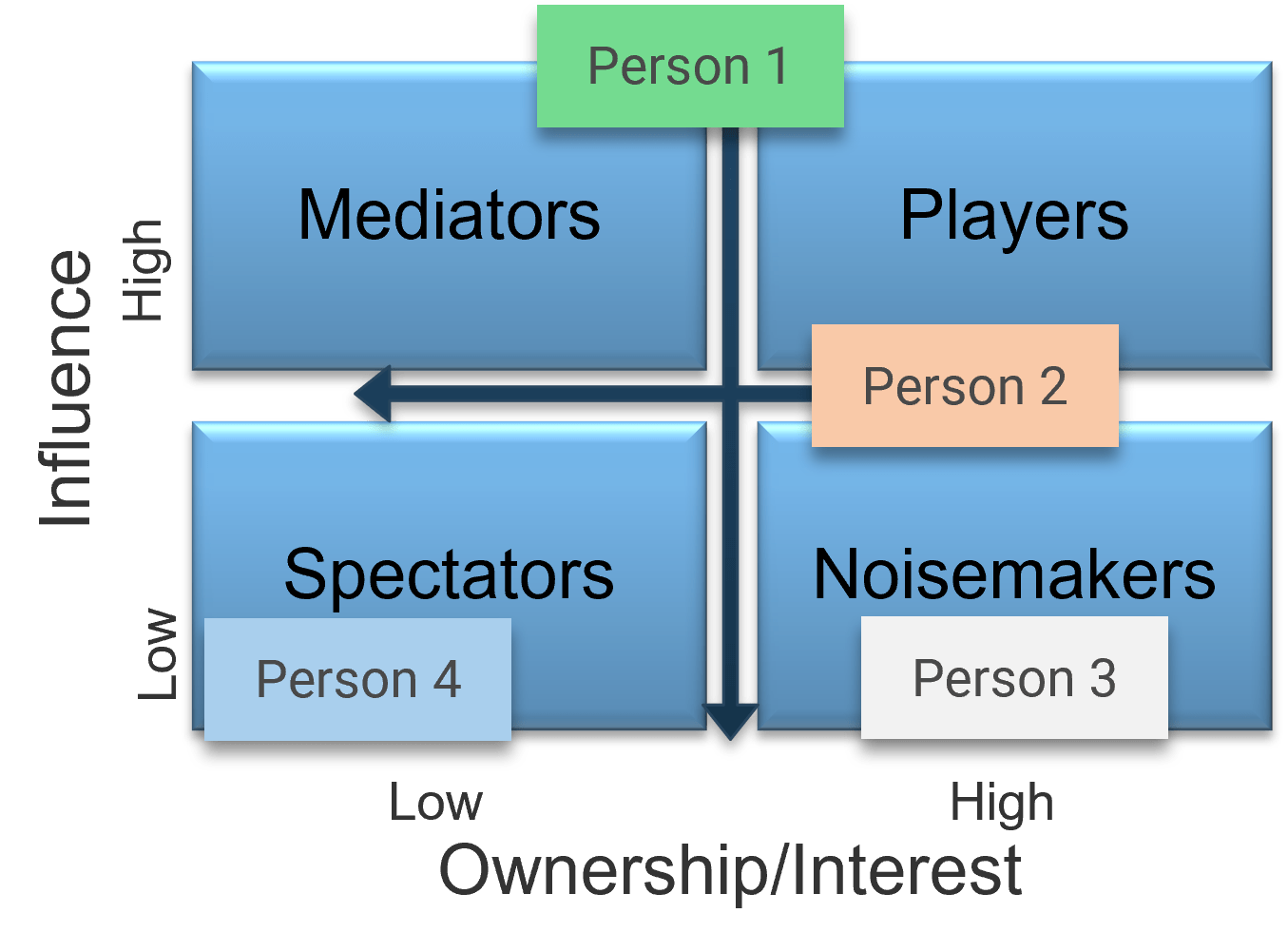
Thompson, Rachel. “What Is Stakeholder Management?” MindTools, n.d. Web.
Tollet, Francoise. “Distracted? Learn how to (re)focus.” Business Digest, 12 July 2021. Podcast.
Tonhauser, Cornelia, and Laura Buker. Determinants of Transfer of Training: A Comprehensive Literature Review, p. 40.
Towers Watson. “Clear Direction in a Complex World: How Top Companies Create Clarity, Confidence and Community to Build Sustainable Performance.” Change and Communication ROI Study Report, 2011-2012. Web.
Trudel, Natalie. “Improve Your Coaching Skills by Understanding the Psychology of Feedback.” TLNT, 12 July 2017. Web.
“Understanding When to Give Feedback.” Harvard Business Review, Dec. 2014. Web.
Vacassin, Daniel. “There are no 'good' performance management systems – there are just good line managers.” LinkedIn, 4 Oct. 2016. Web.
van der Locht, Martijn, et al. “Getting the Most of Management Training: The Role of Identical Elements for Training Transfer.” Personnel Review, vol. 42, no. 4, May 2013, pp. 422–39. Crossref, doi:10.1108/PR-05-2011-0072.
Vaughan, Liam. “Banks Find New Ways to Measure Staff.” Financial News, 10 Jan. 2011. Web.
Watkins, Michael, et al. “Hit the Ground Running:Transitioning to New Leadership Roles.” IMD Business School, May 2014. Web.
Whitney, Kelley. “Kimberly-Clark Corp.: Redesigning Performance Management.” Talent Management Magazine, vol. 2, no. 1, 2006. Web.
“Whole Foods 2015 Report.” The Predictive Index, n.d. Web.
“Whole Foods Market Reports Fourth Quarter and Fiscal Year 2016 Results.” Whole Foods, 2 Feb. 2016. Web.
Wisniewski, Dan. “Here's why everybody hates meetings.” HR Morning, 14 Dec. 2012. Web.
Woolum, Janet, and Brent Stockwell. Aligning Performance Measurement to Mission, Goals, and Strategy Workbook. Arizona State University, Jan. 2016. Web.
Worall, Les, et al. The Quality of Working Life. Chartered Management Institute, 2016. Web.
“Workplace Conflict Statistics: How We Approach Conflict at Work.” Niagara Institute, 11 Aug. 2022. Web.
“You Waste a Lot of Time at Work Infographic.” Atlassian, 23 August 2012. Web.
Zenger, Jack, and Joe Folkman. “Feedback: The Leadership Conundrum.” Talent Quarterly: The Feedback Issue, 2015. Web.
Zuberbühler, P., et al. “Development and validation of the coaching-based leadership scale and its relationship with psychological capital, work engagement, and performance.” Current Psychology, vol. 42, no. 10, 2021, pp. 1-22.


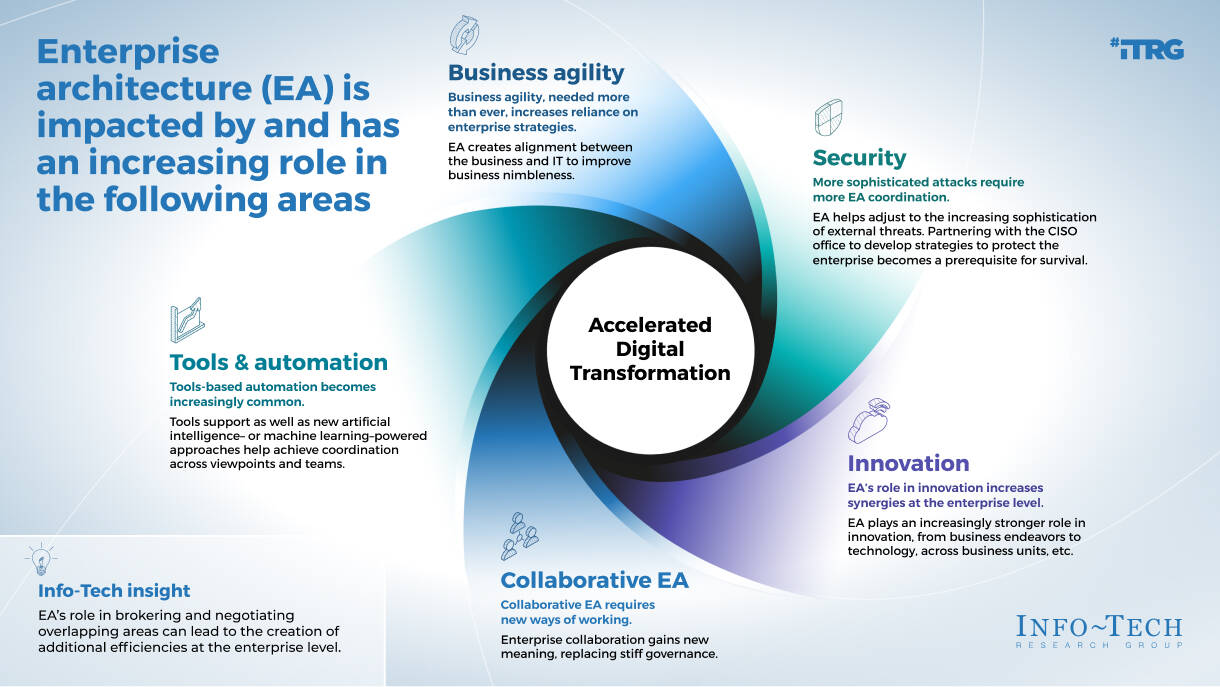



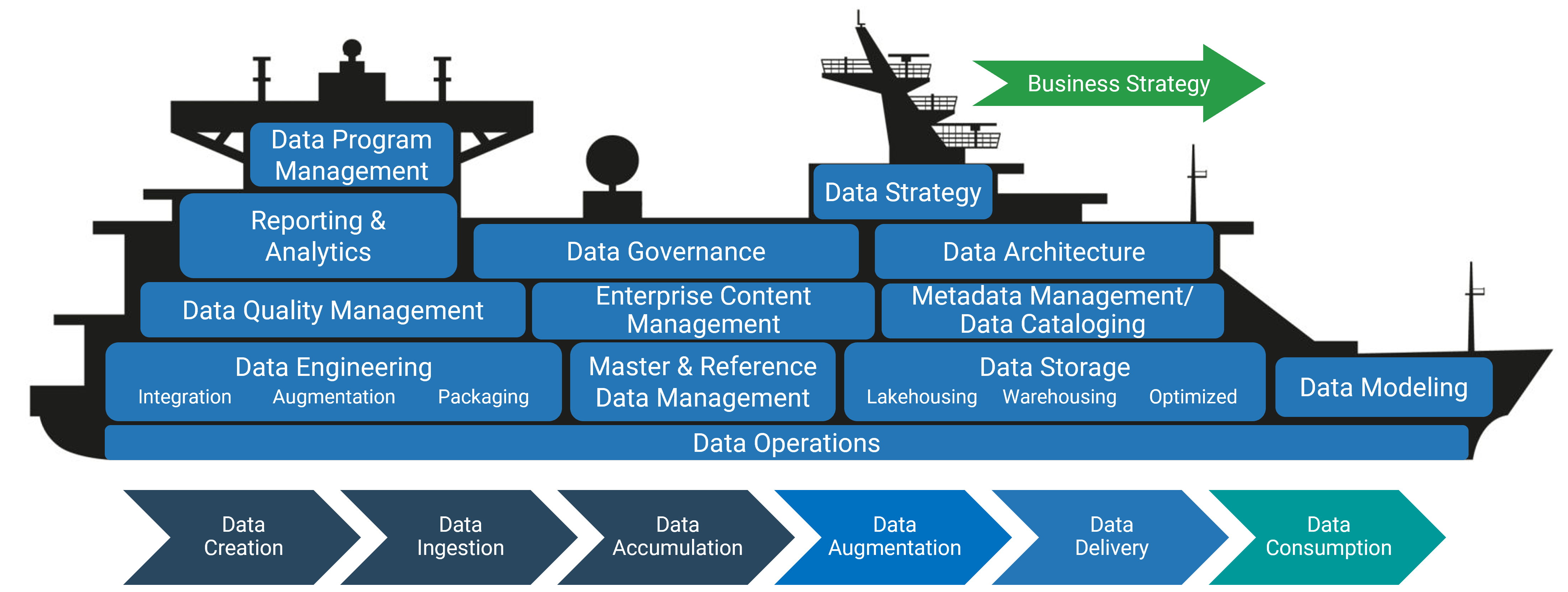


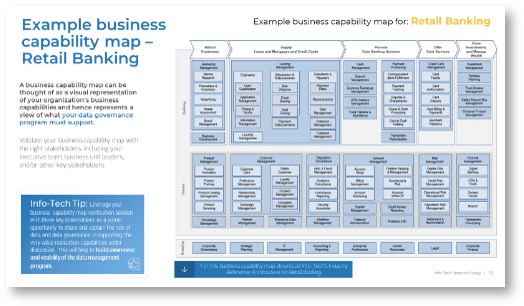
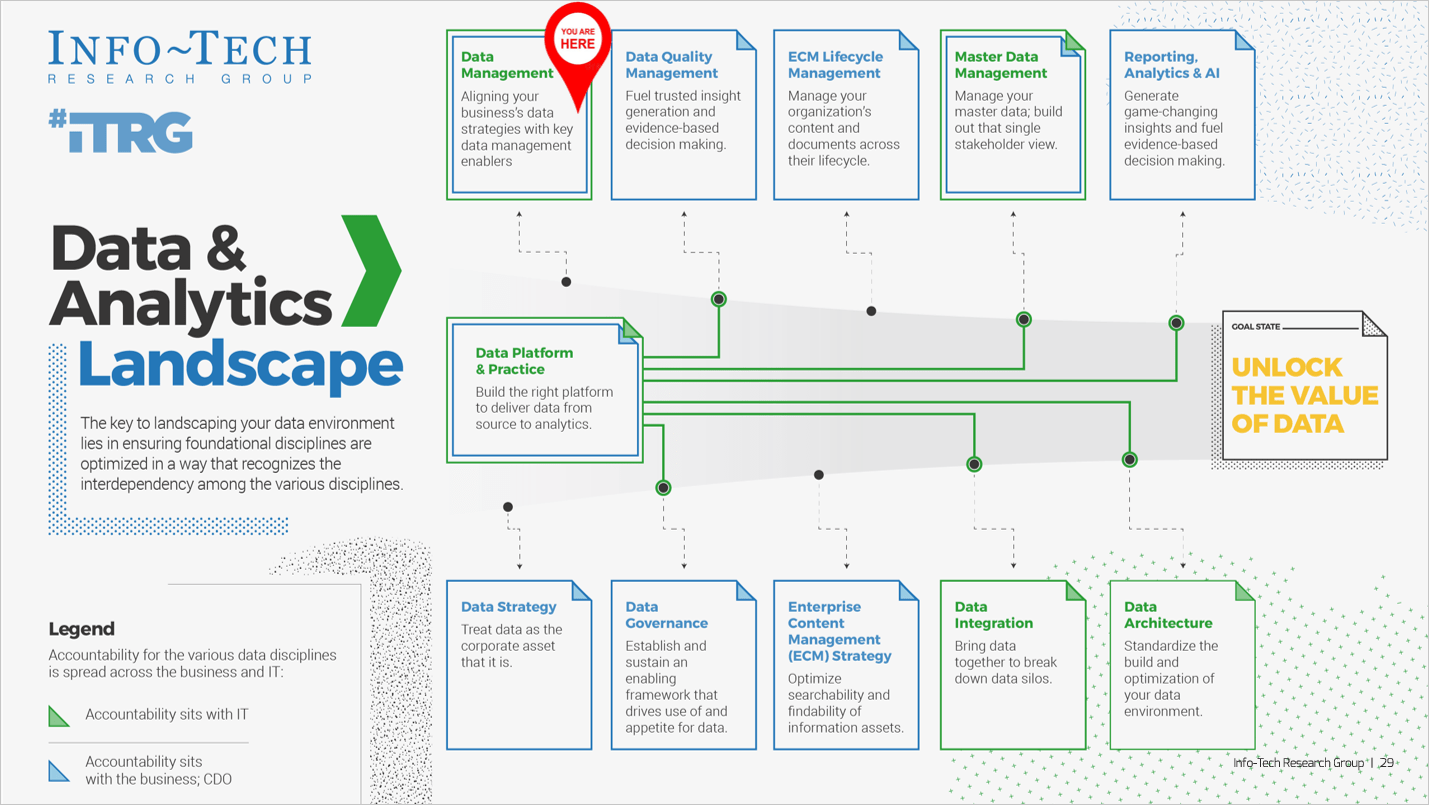
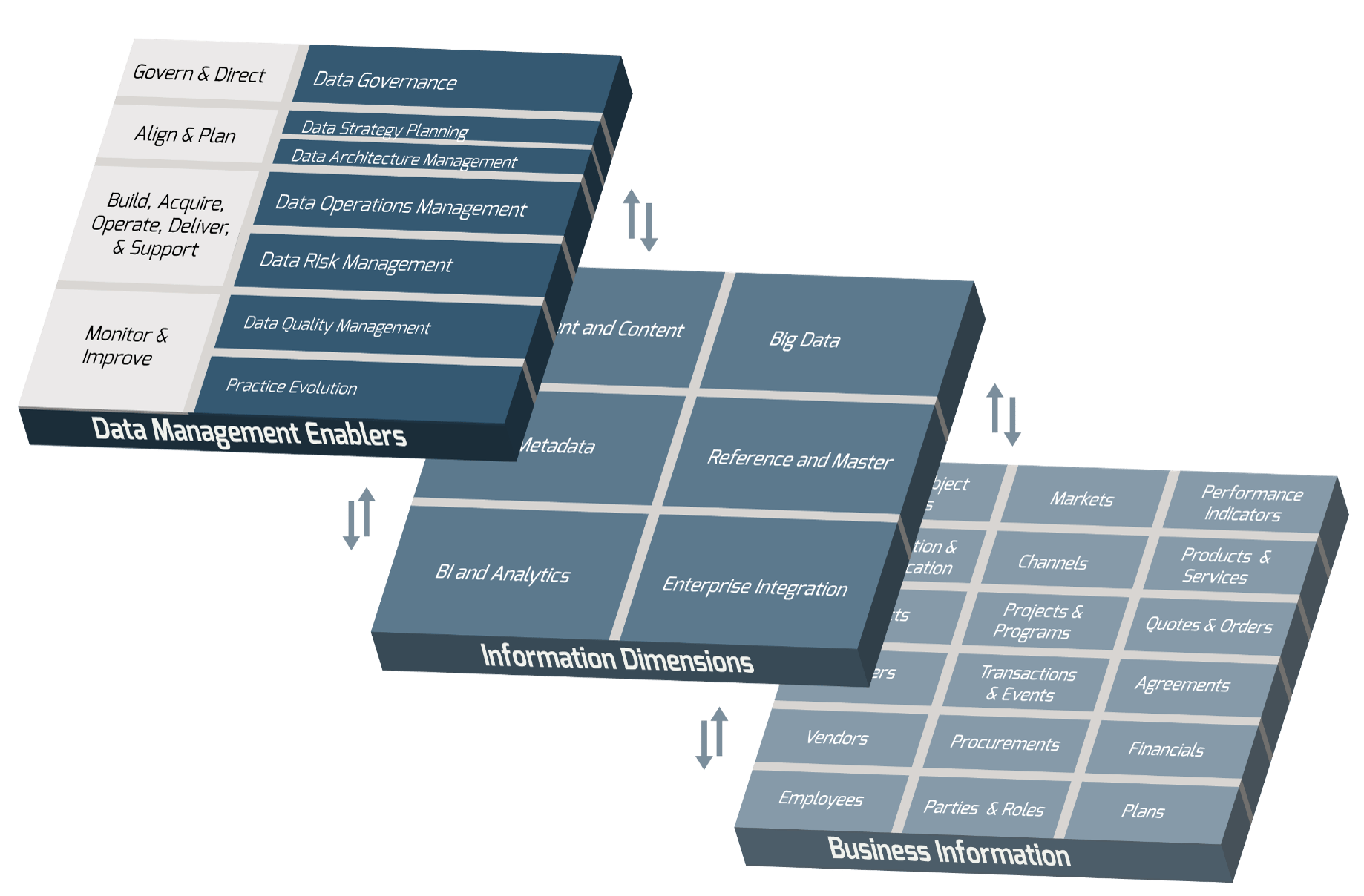

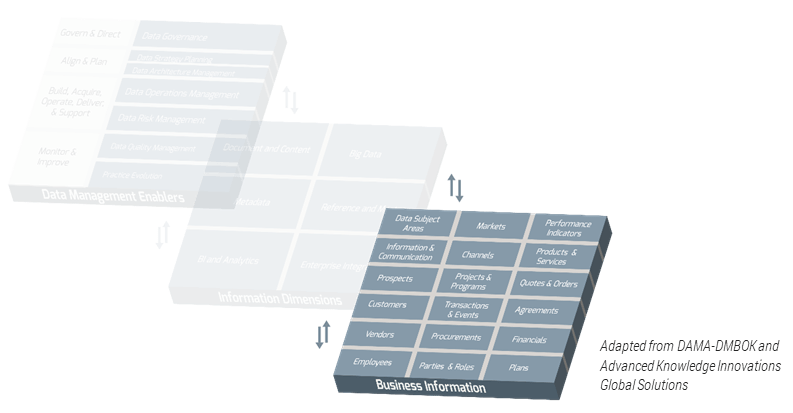
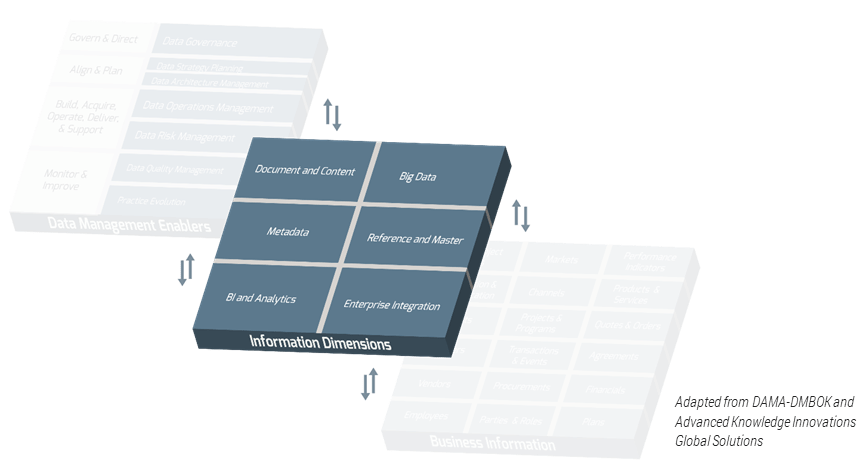
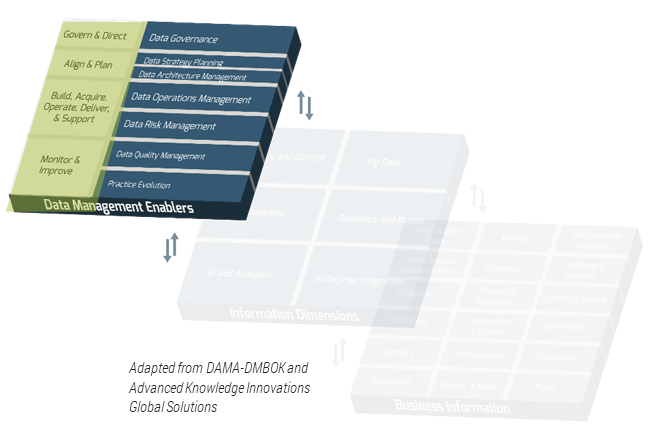

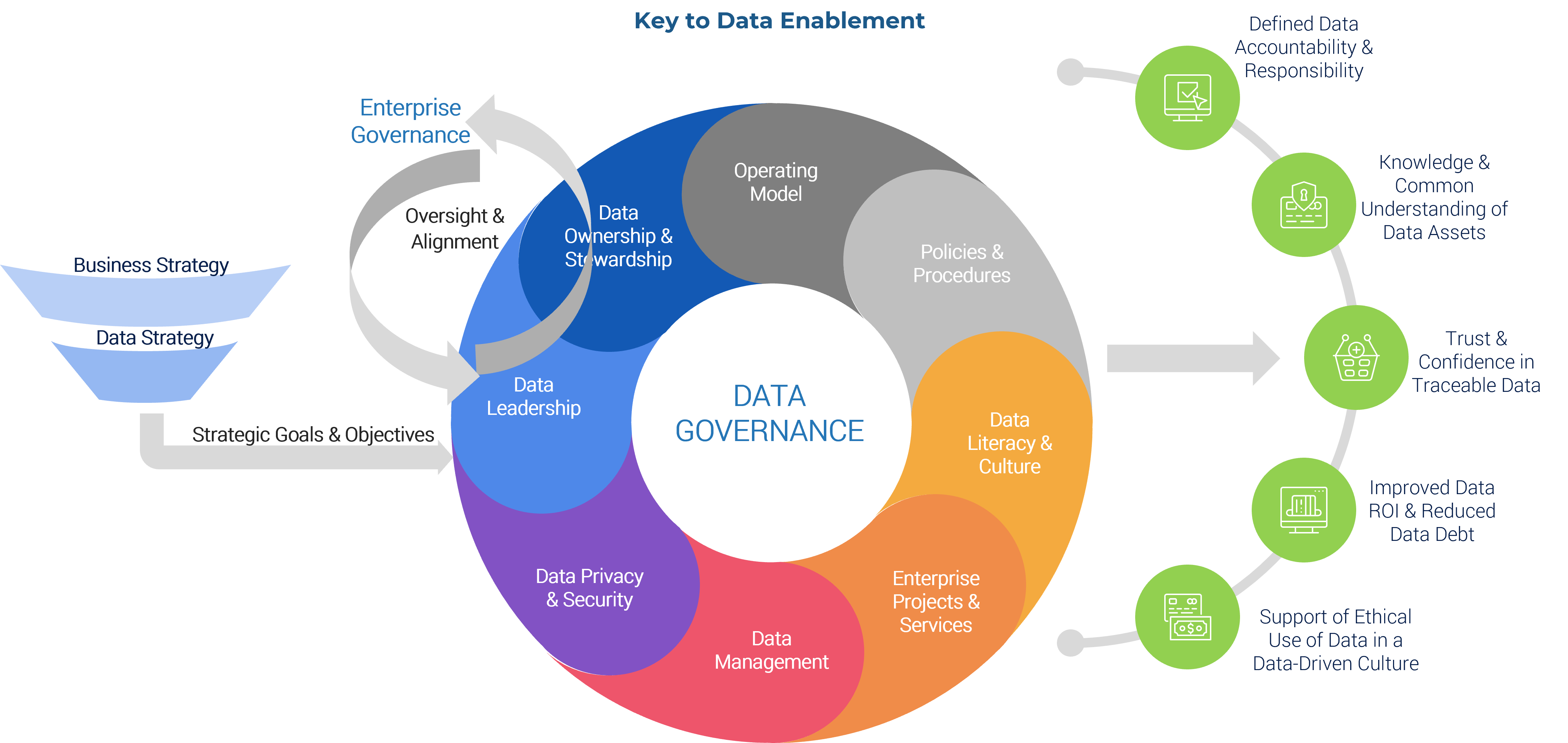
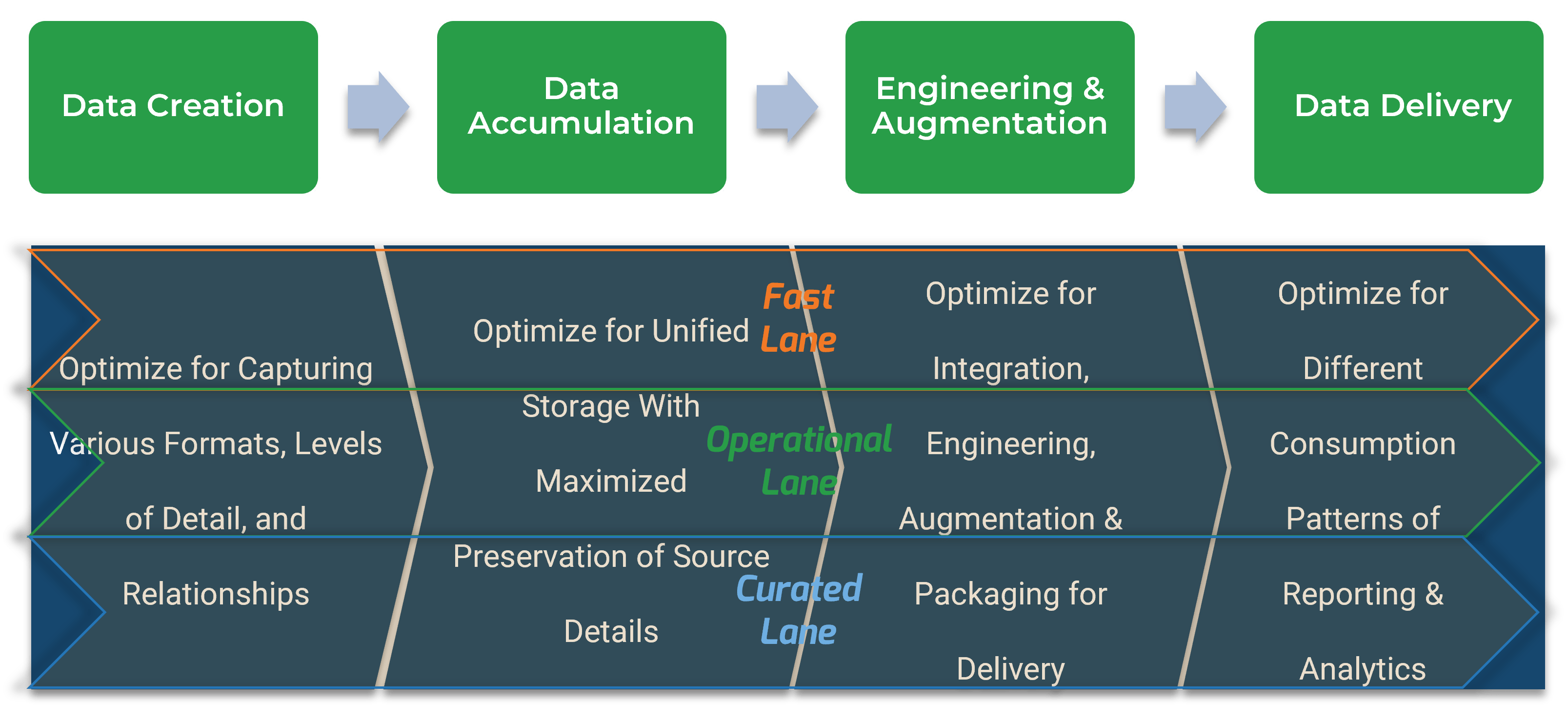
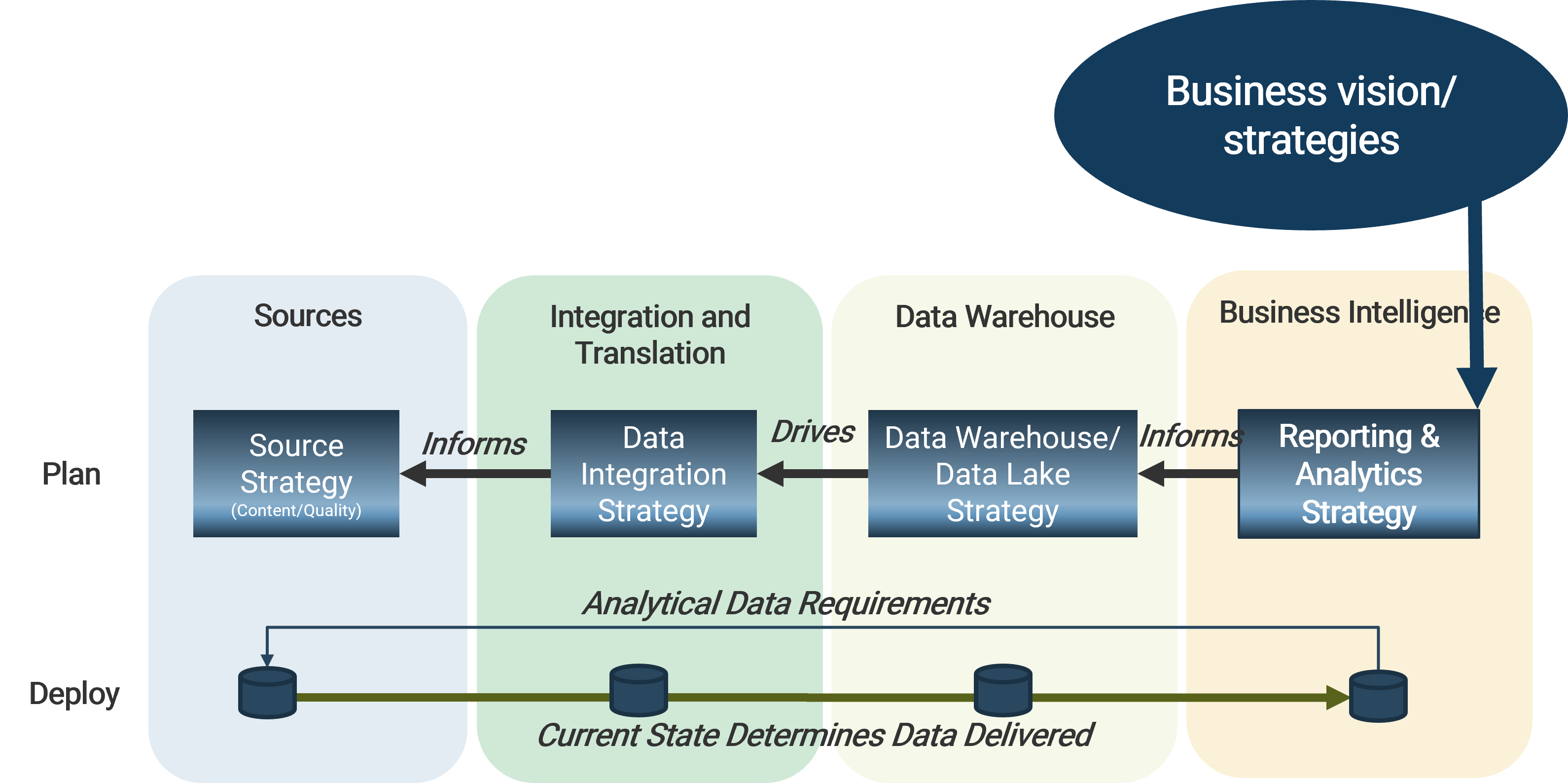
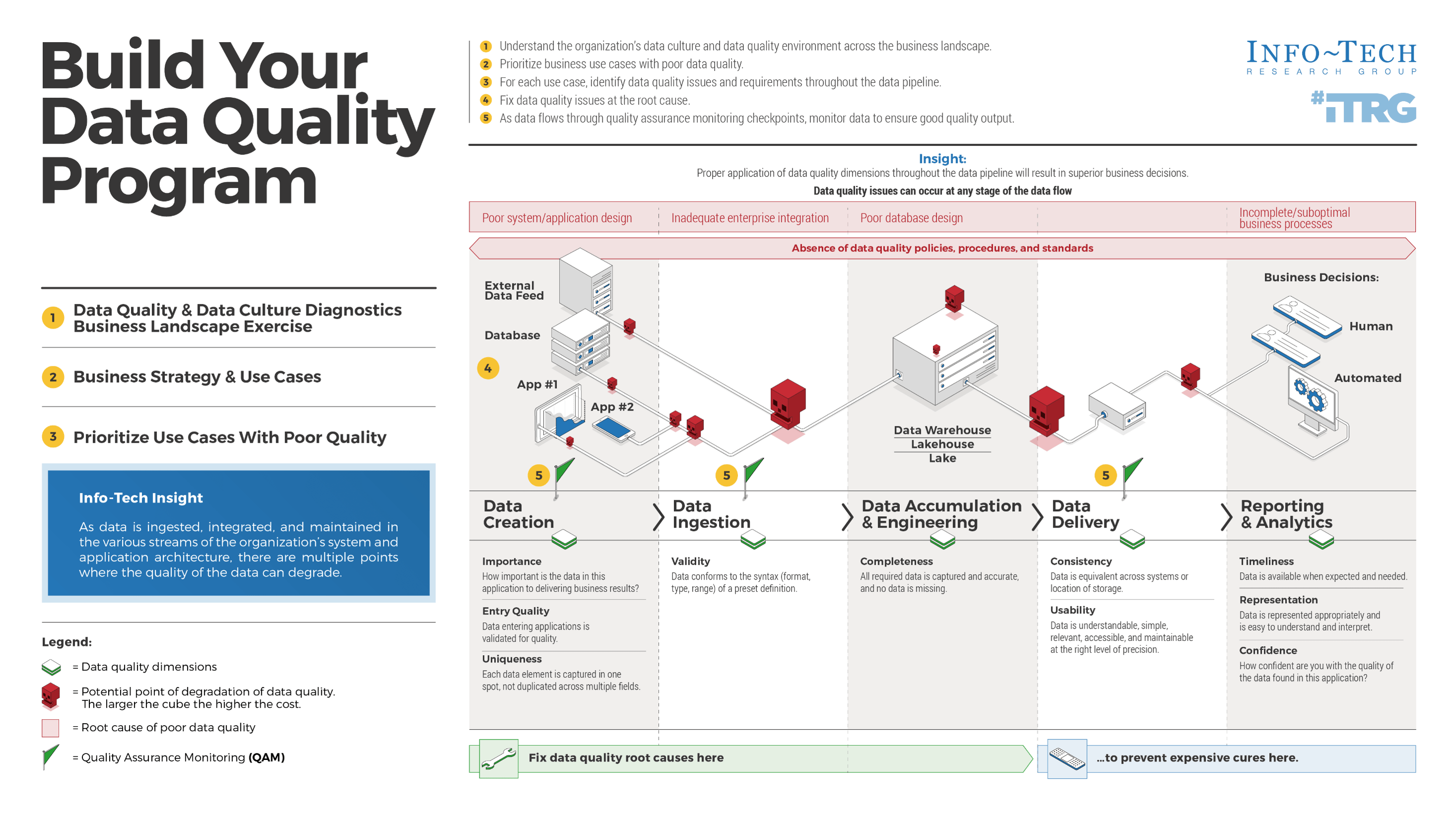
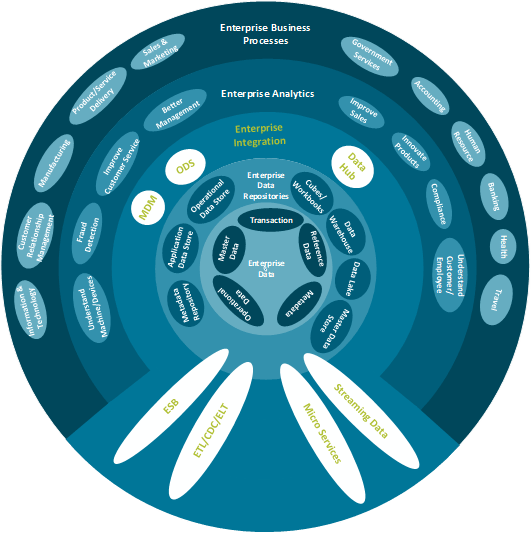
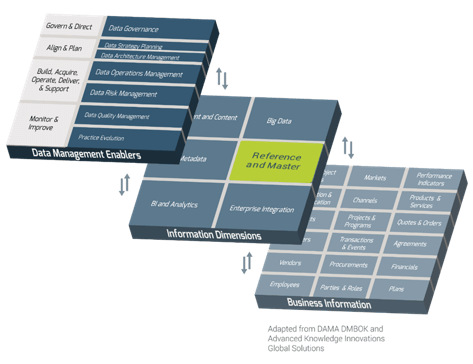
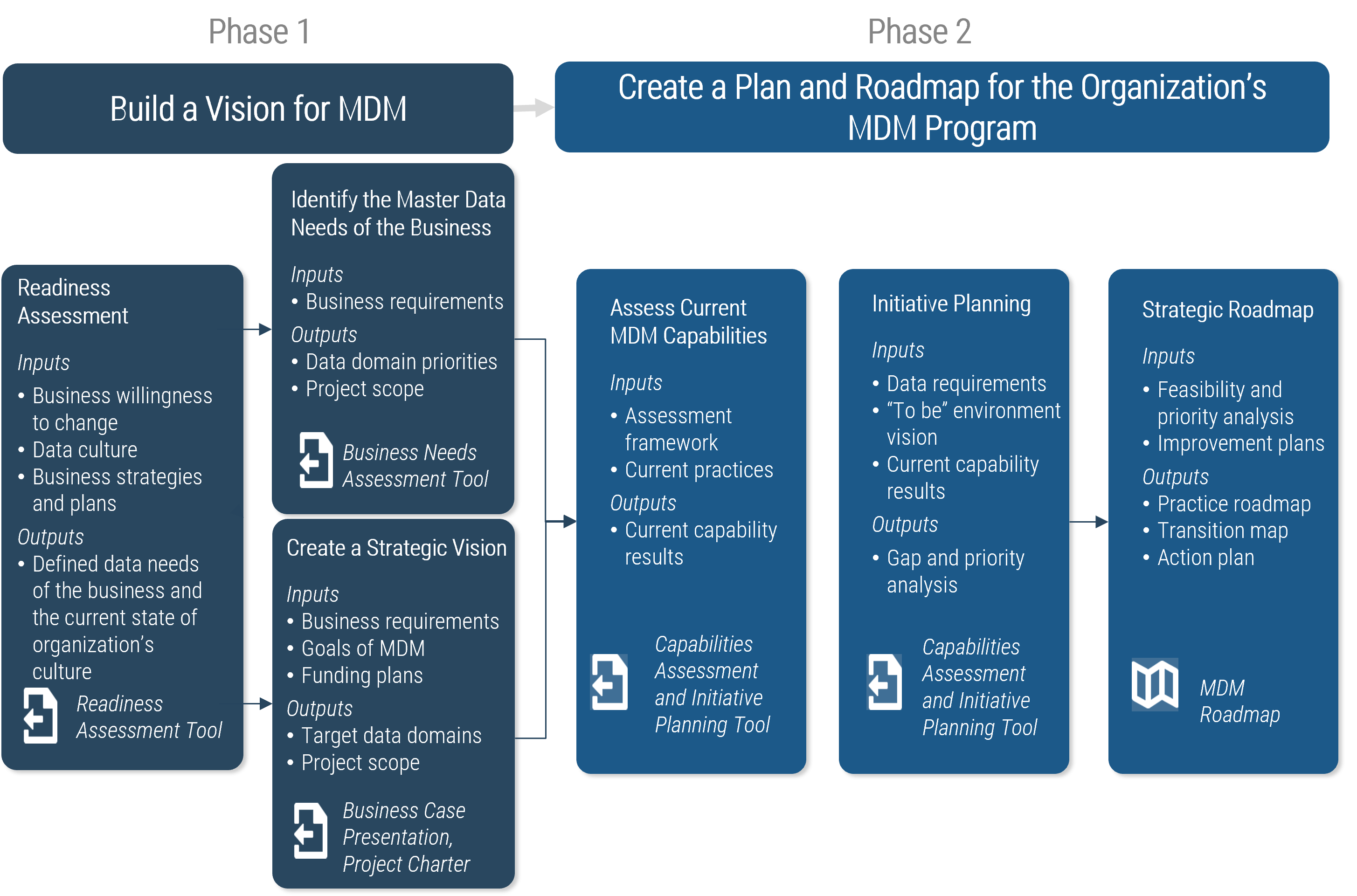
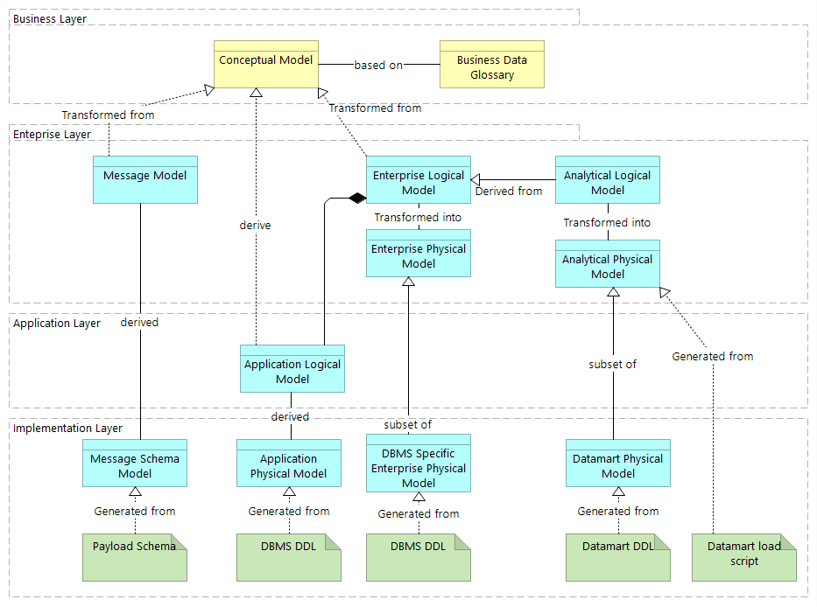
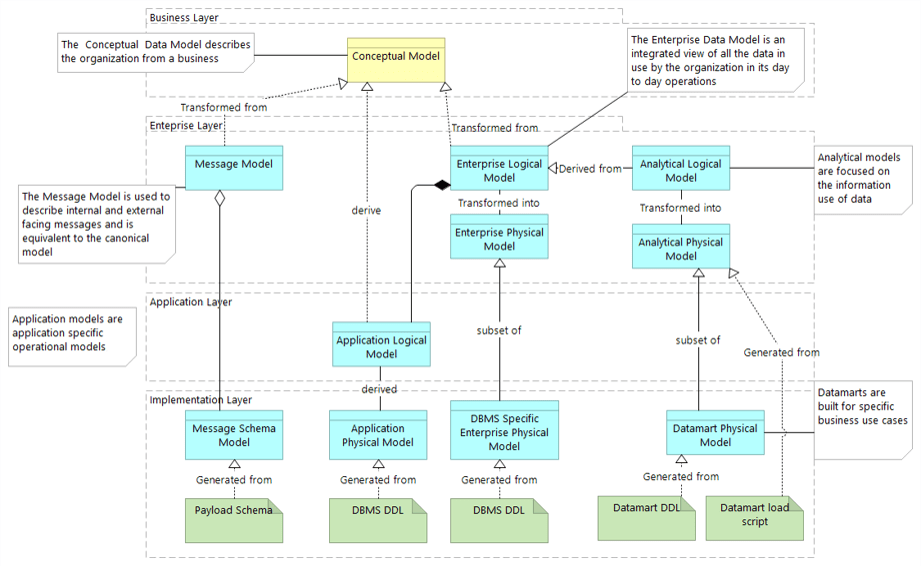
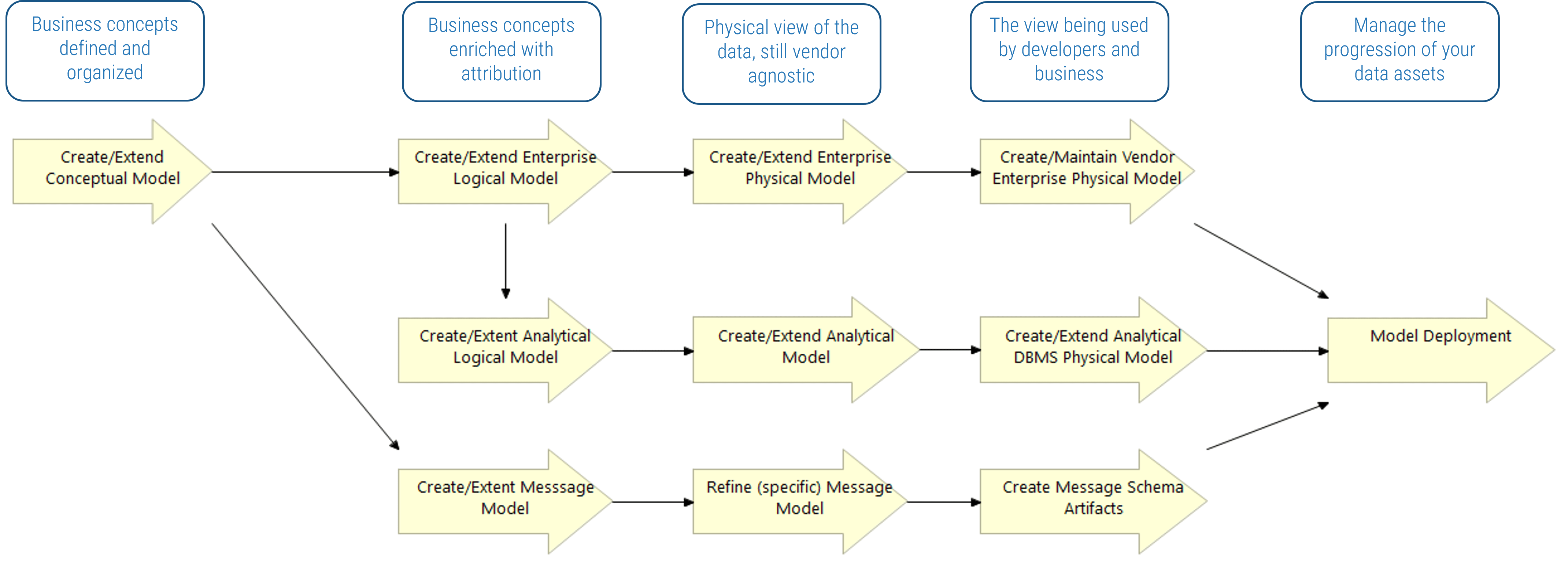
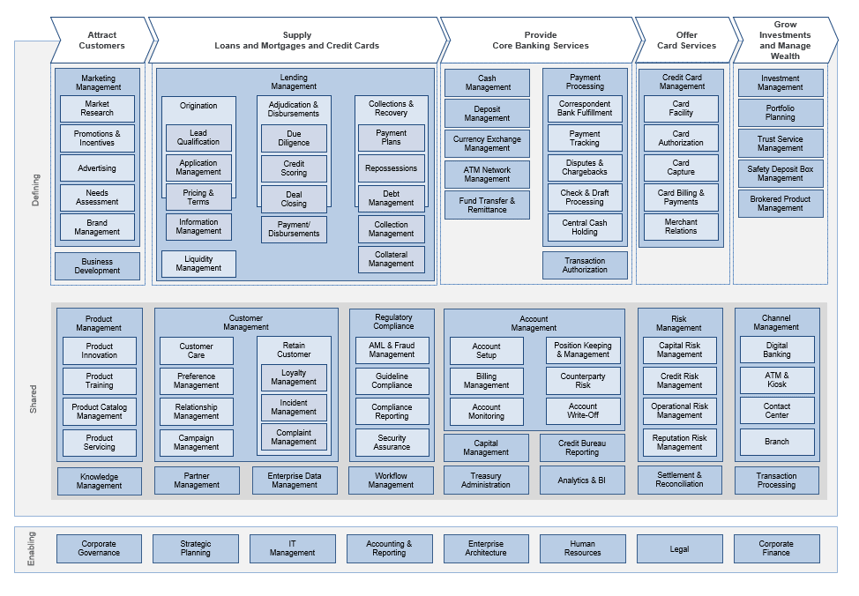
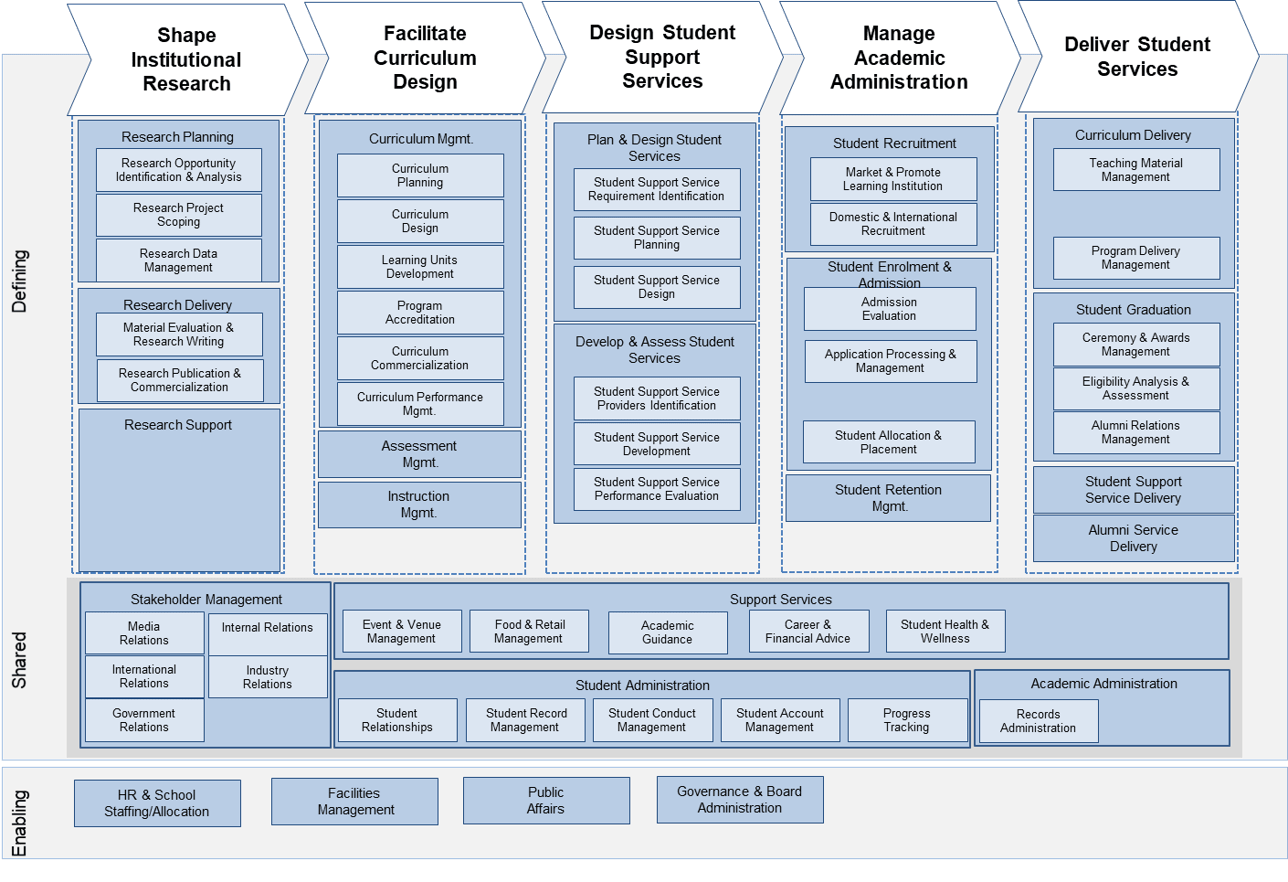
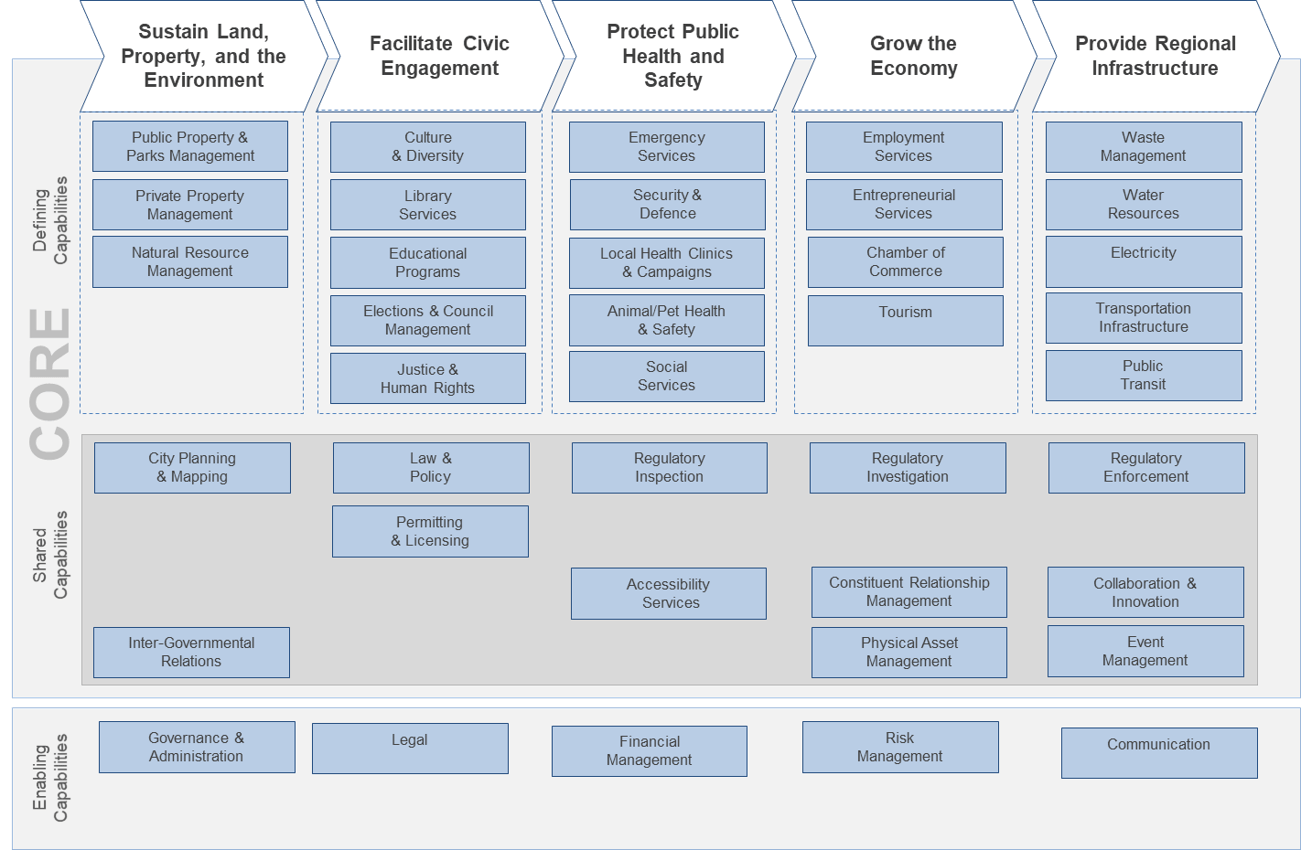
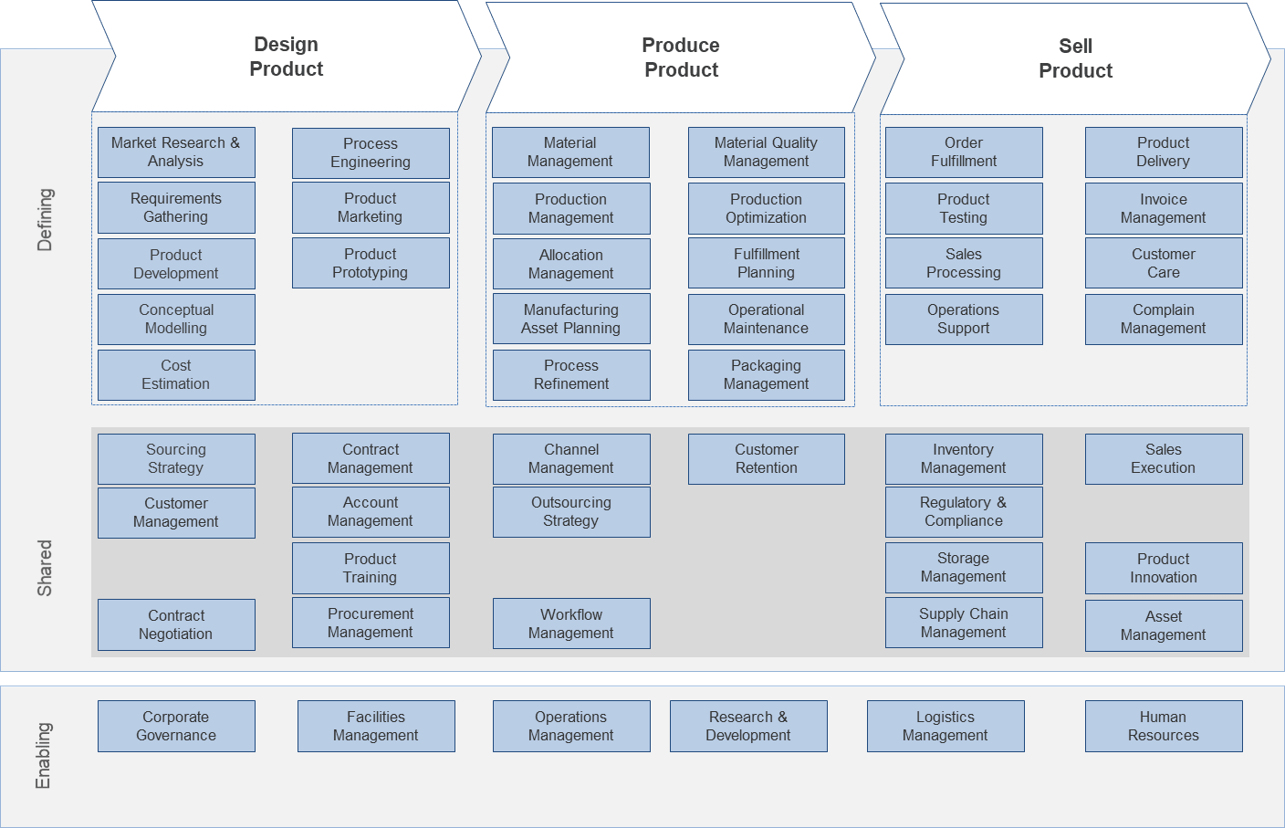
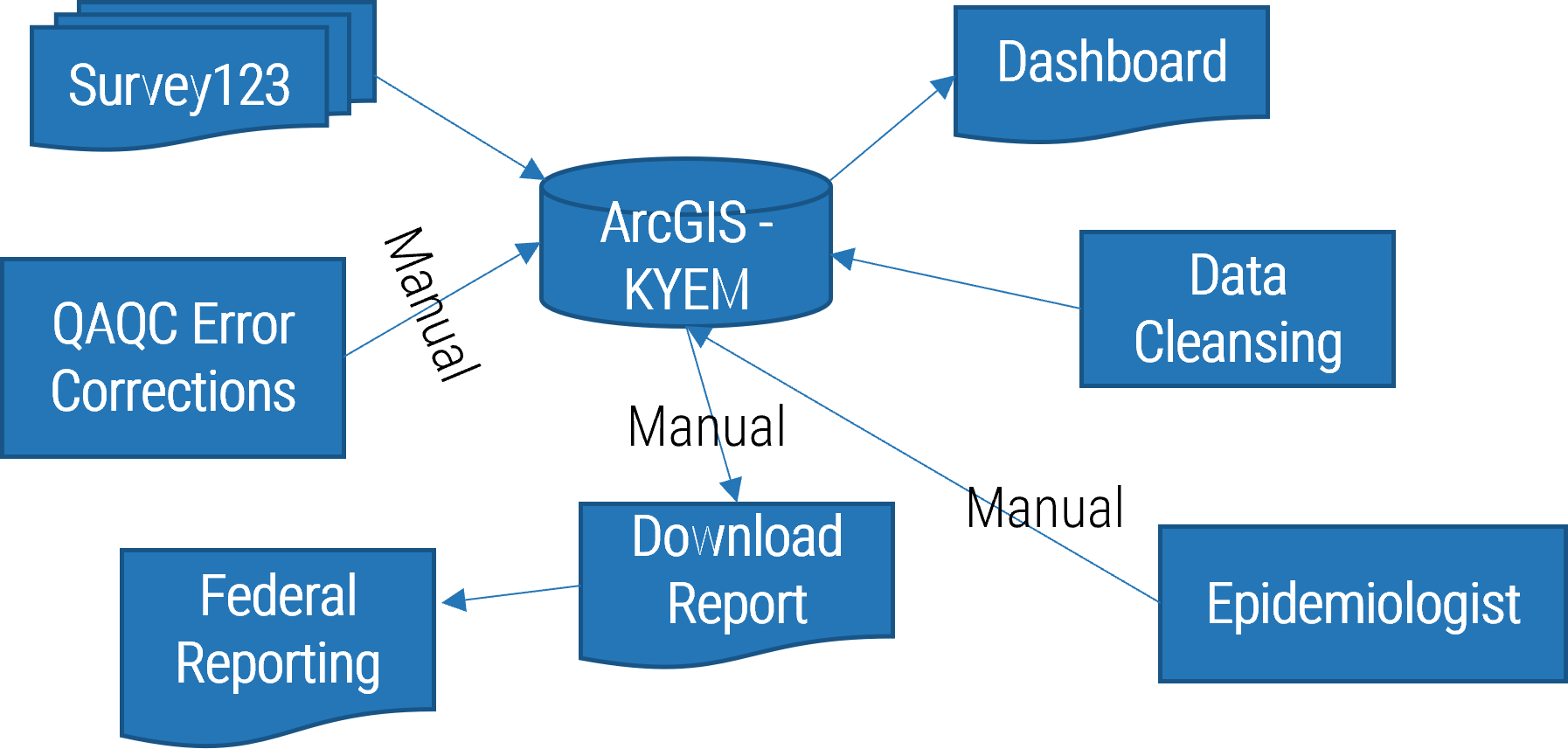
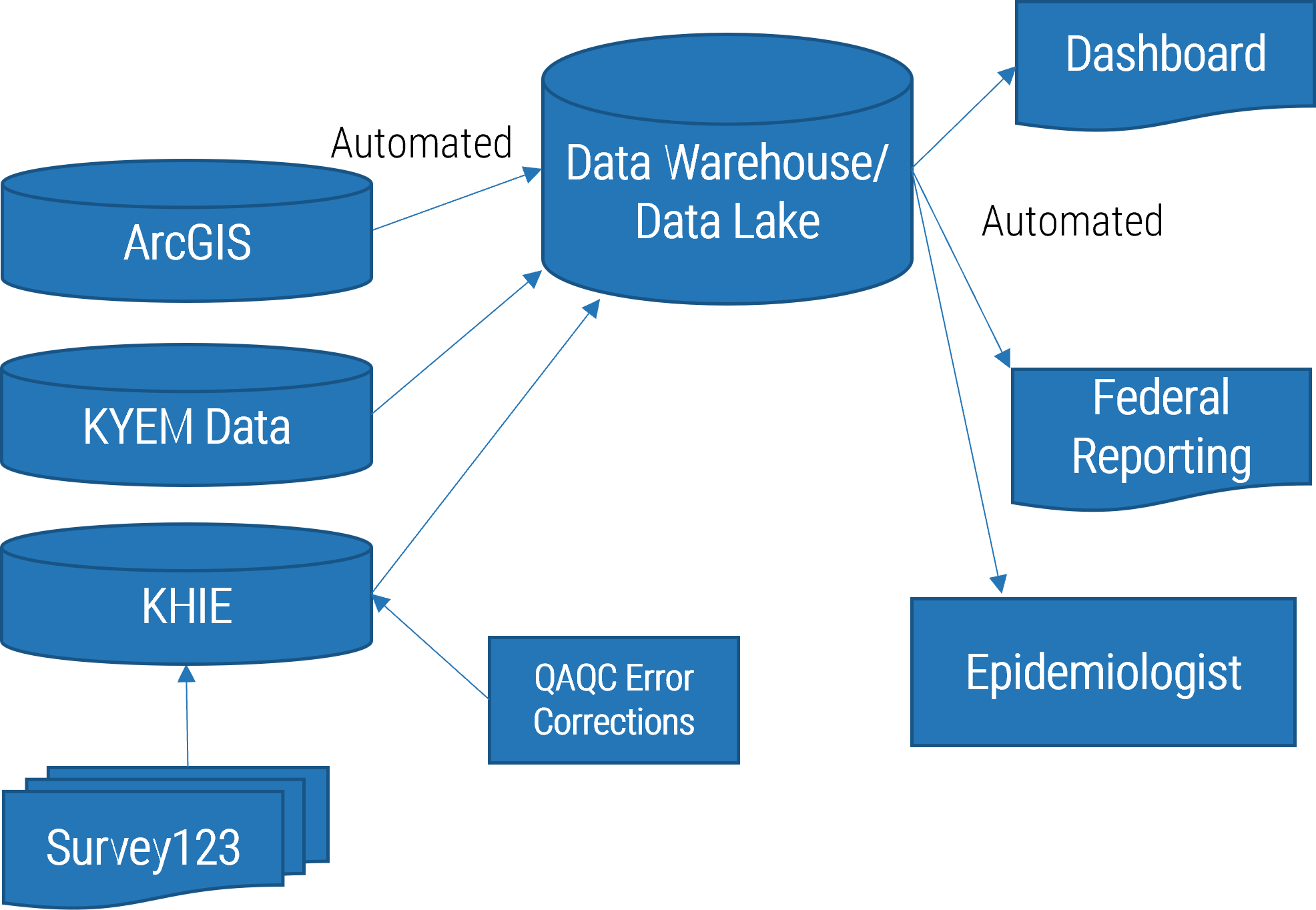

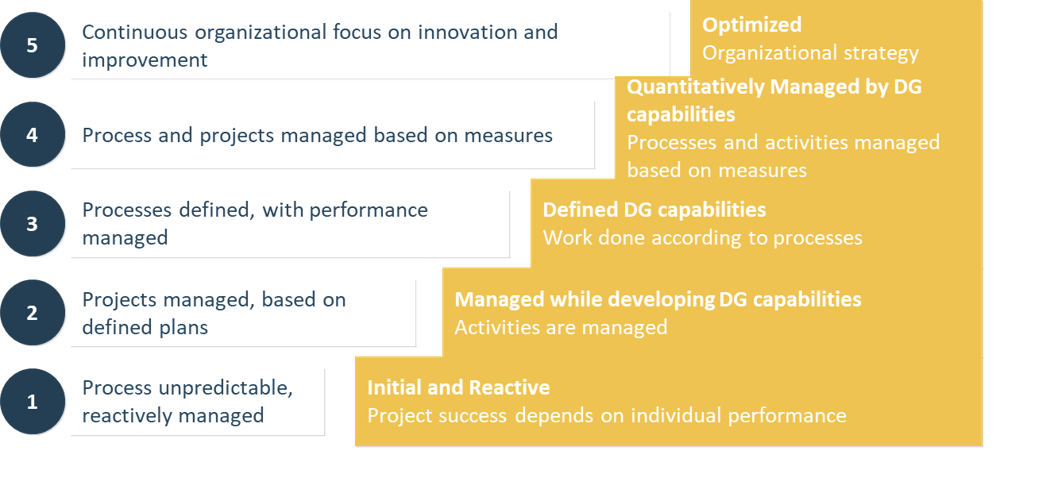

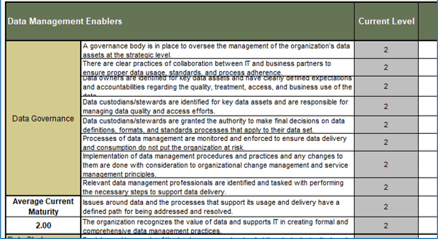










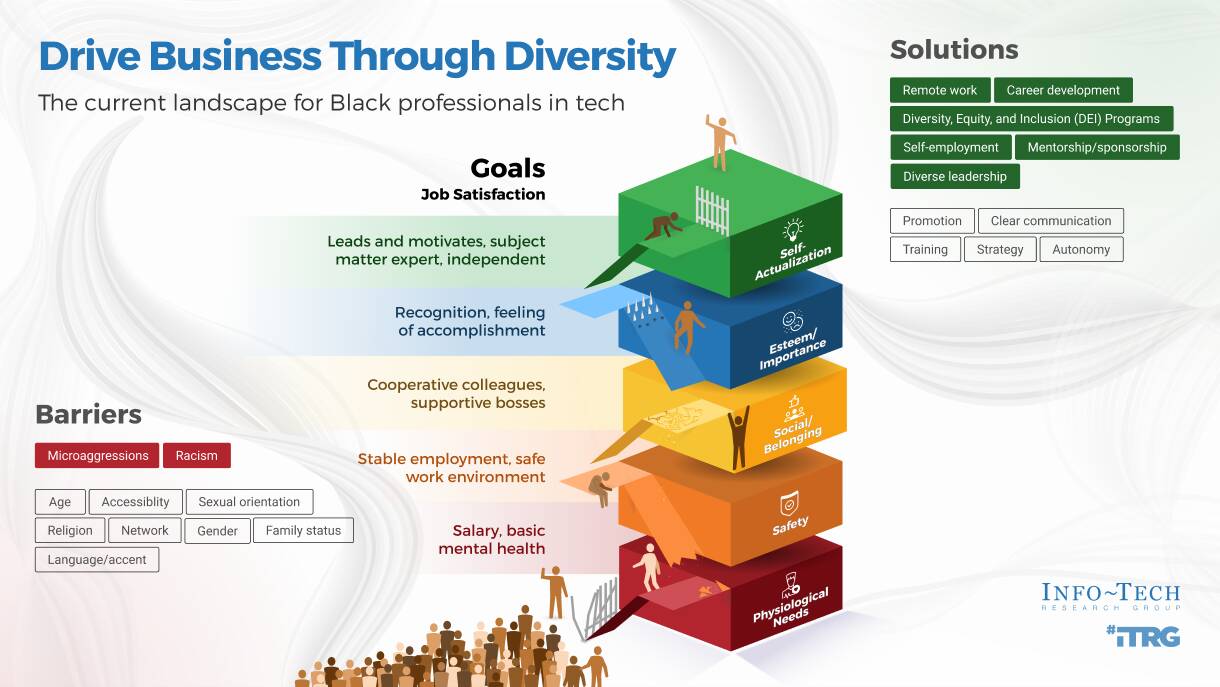











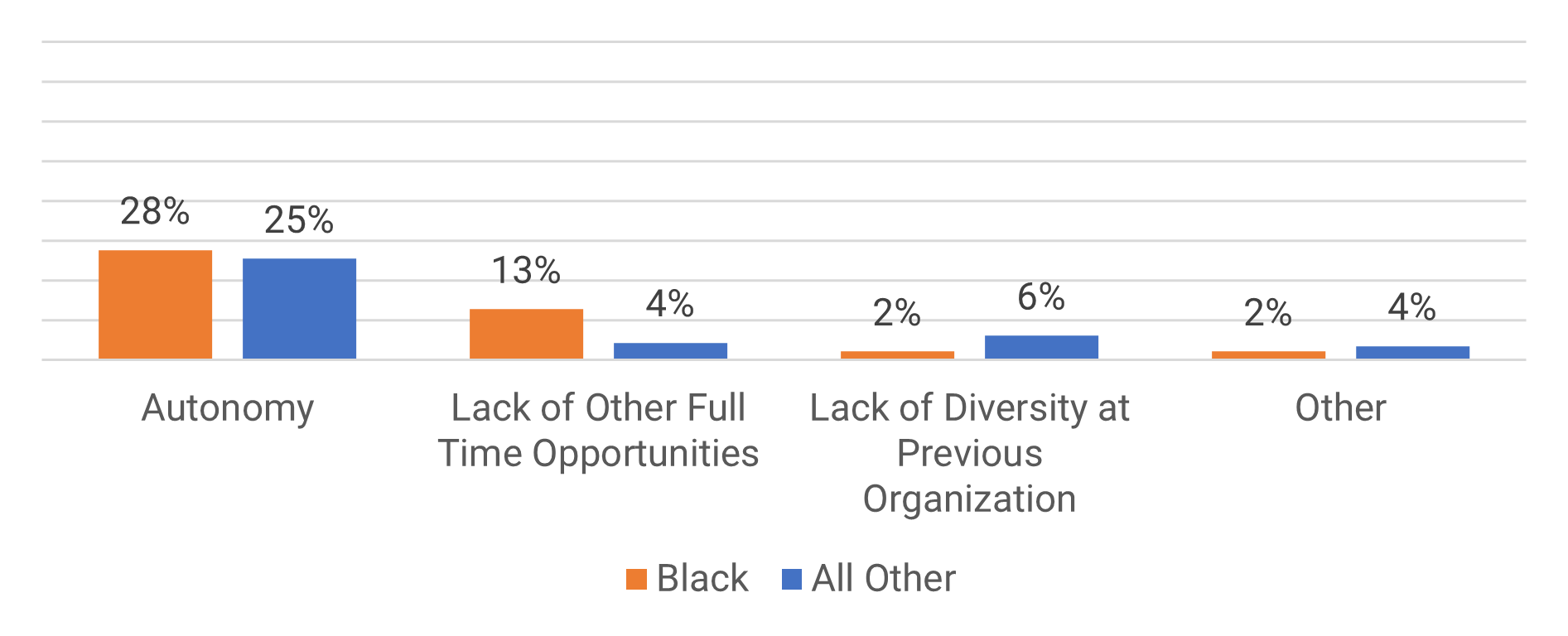
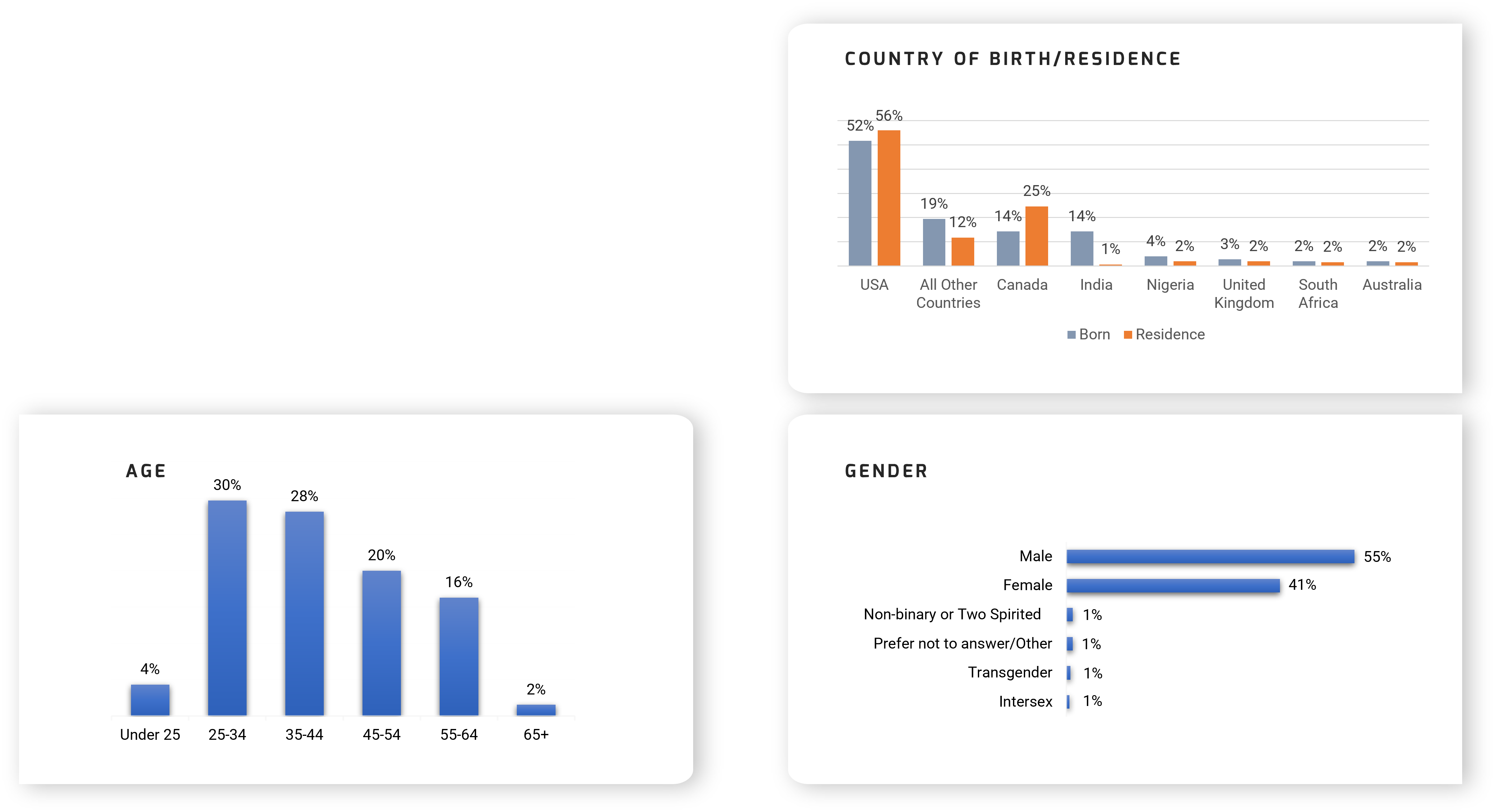
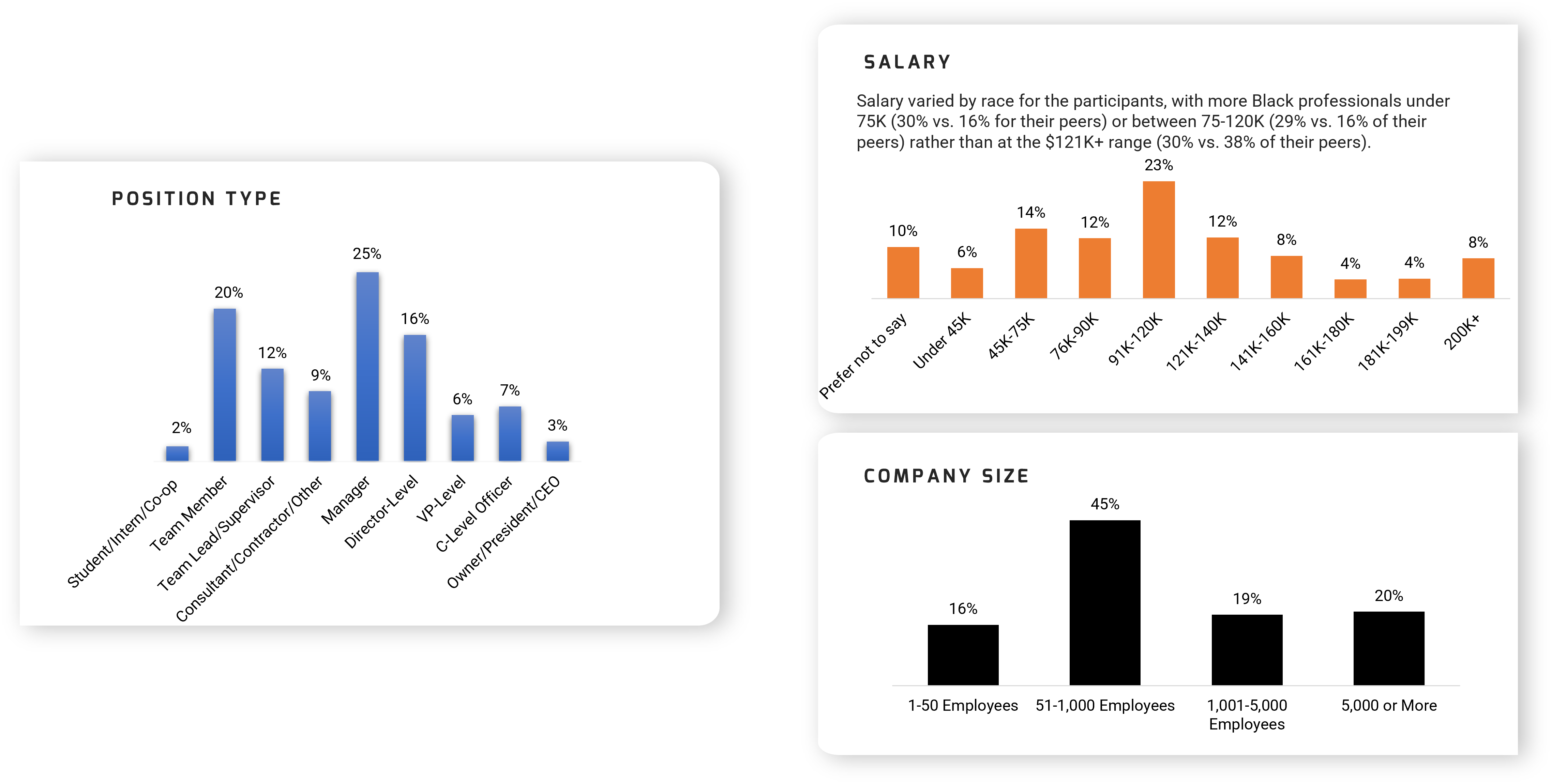
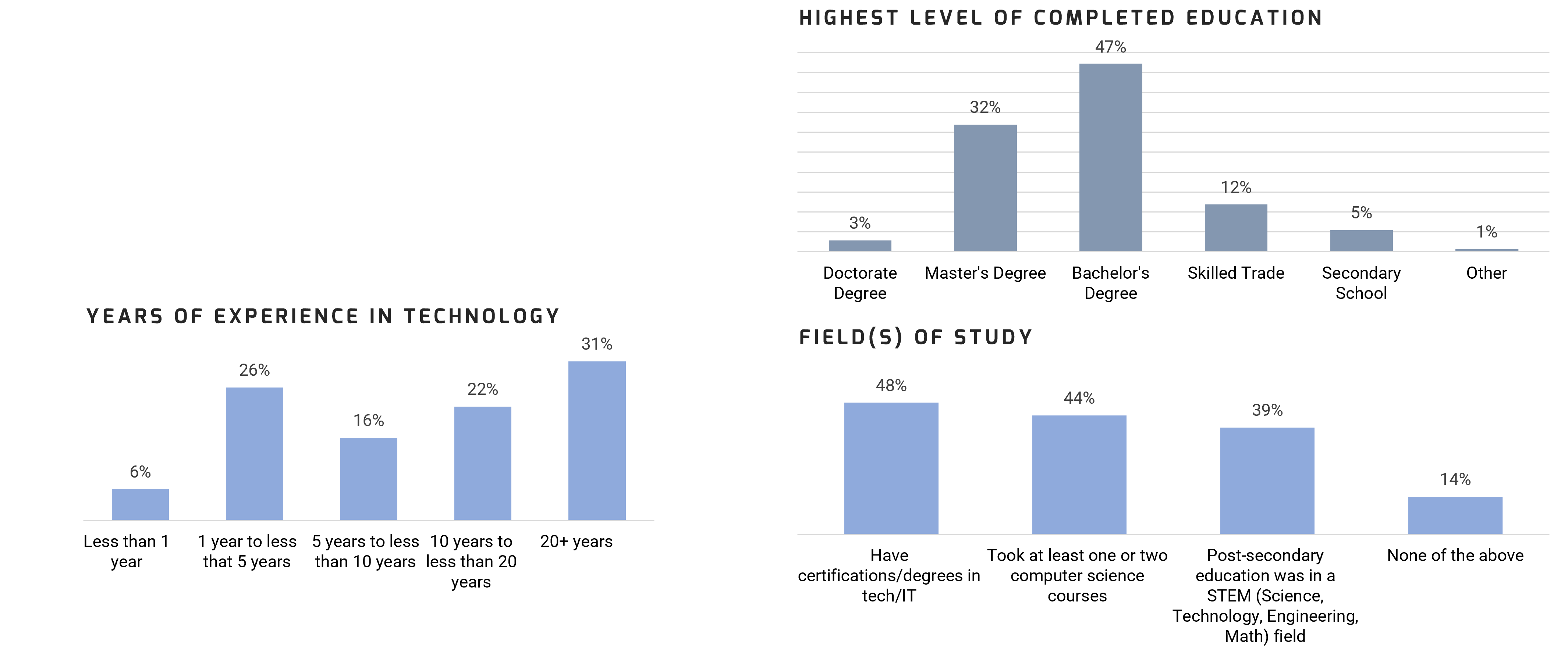



















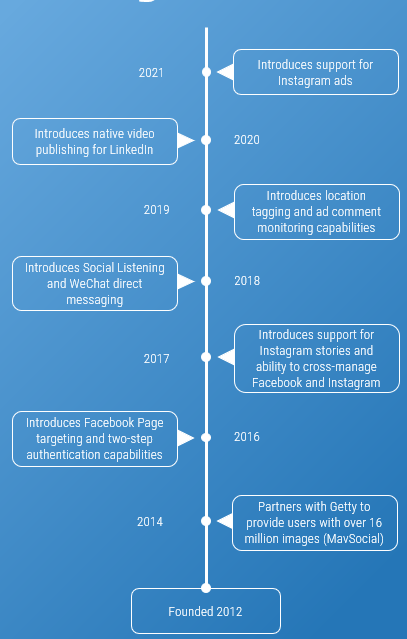

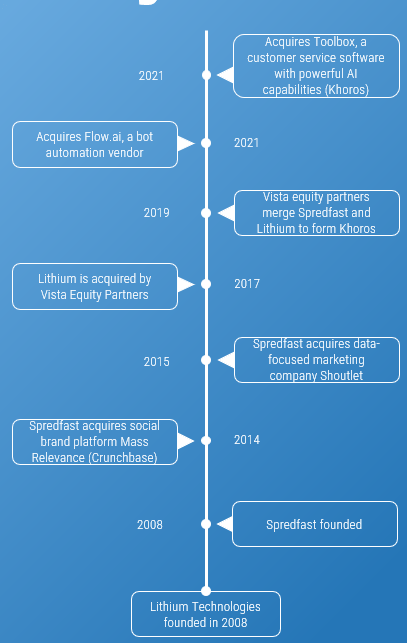










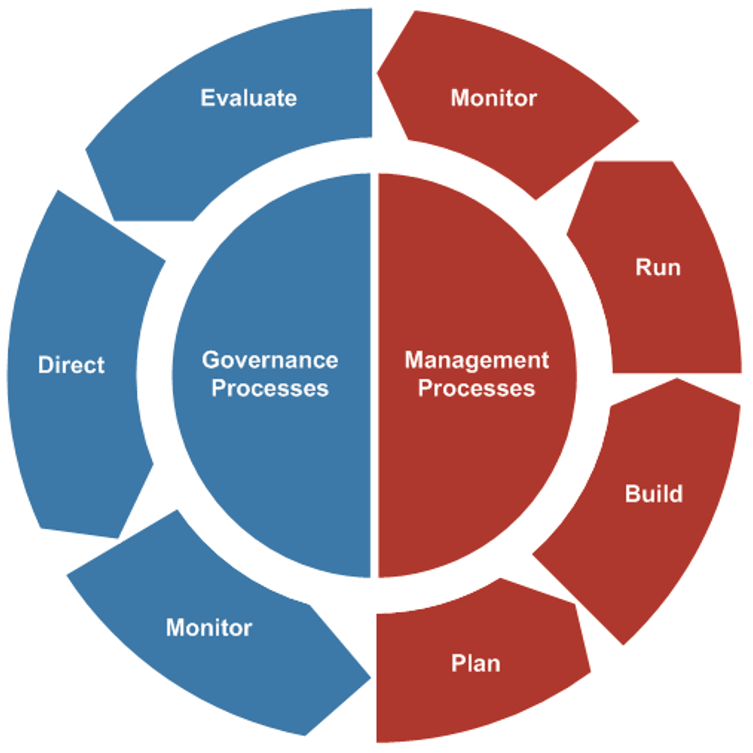




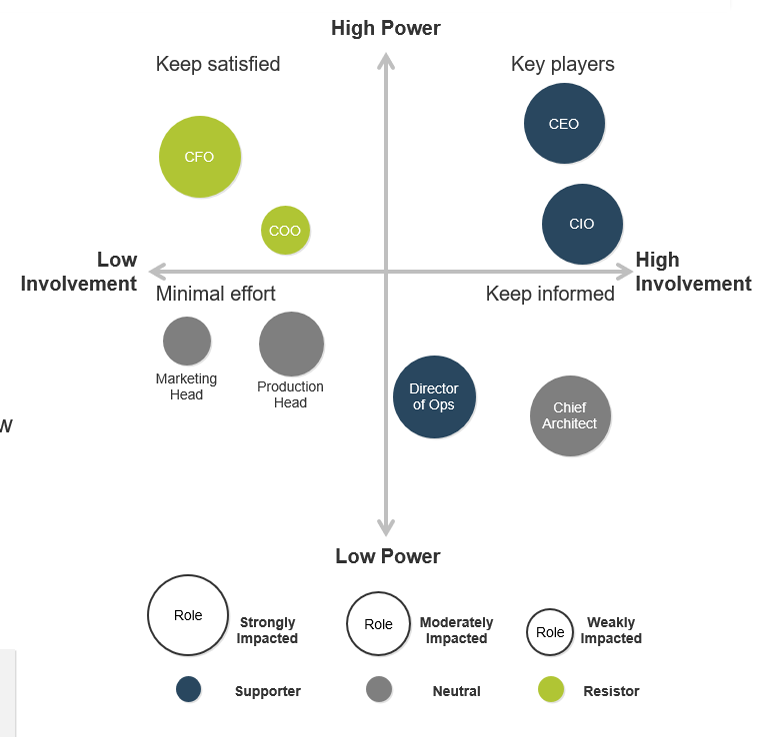
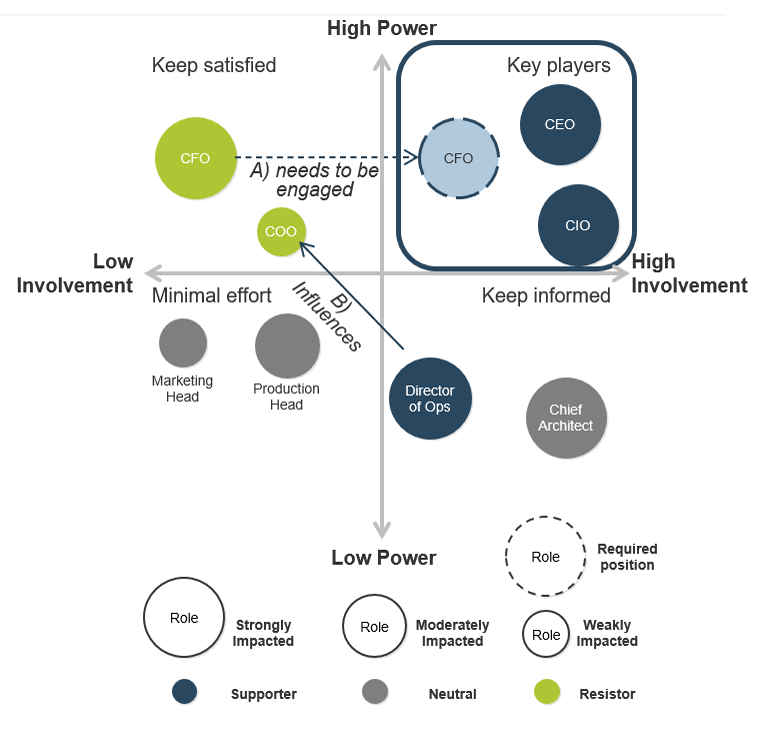



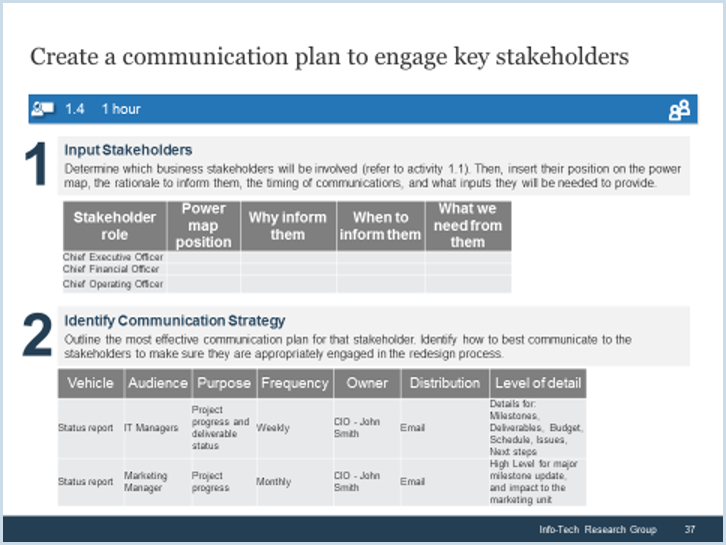

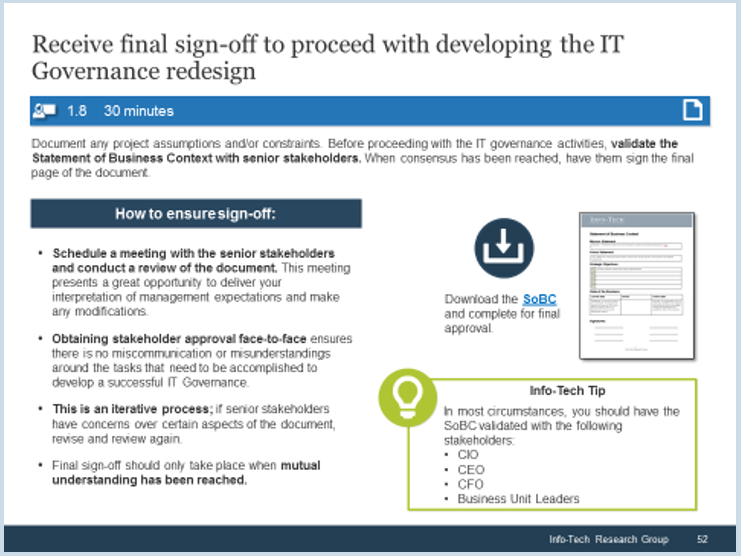
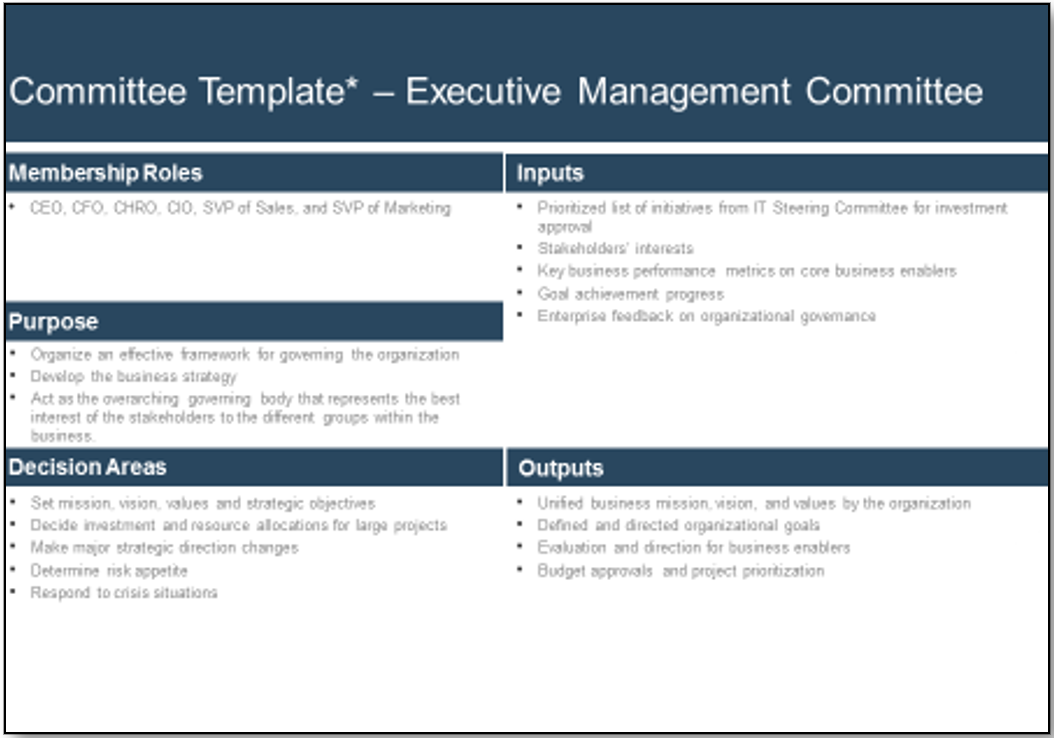
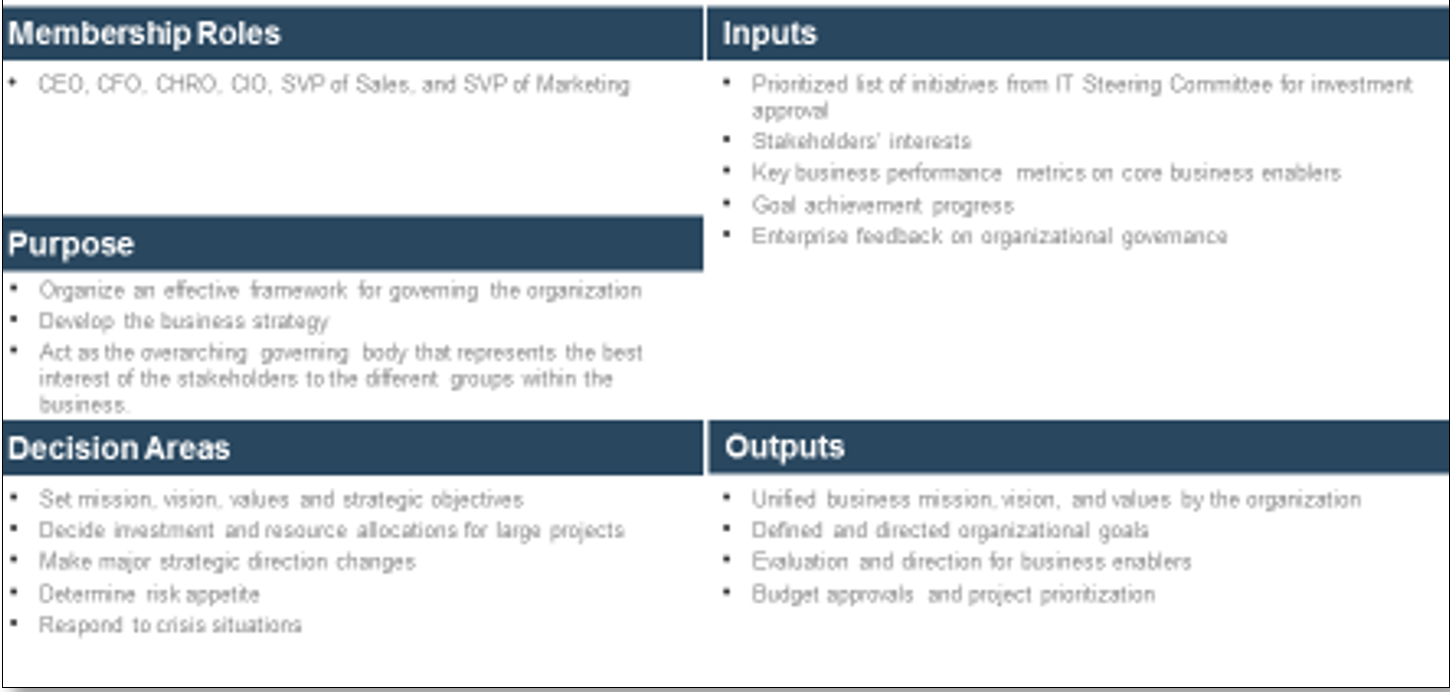
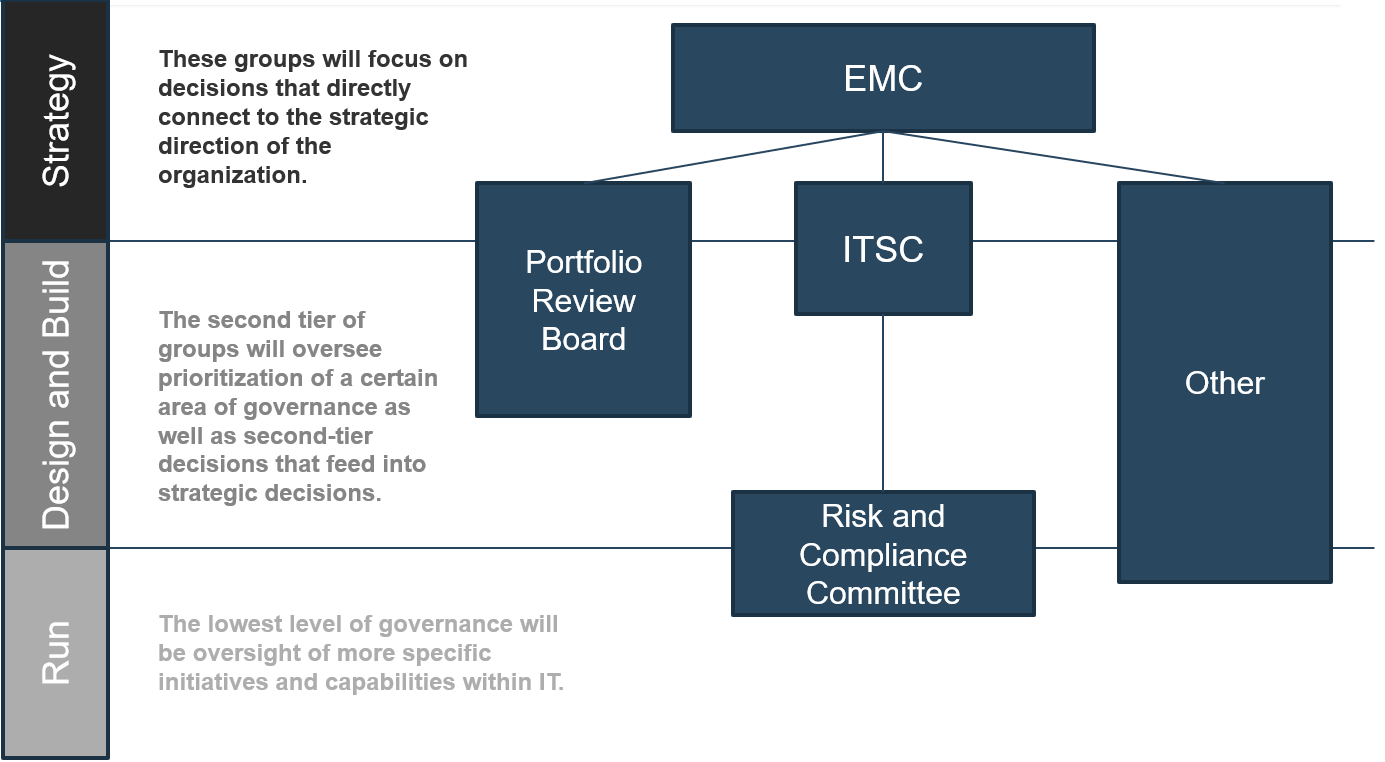
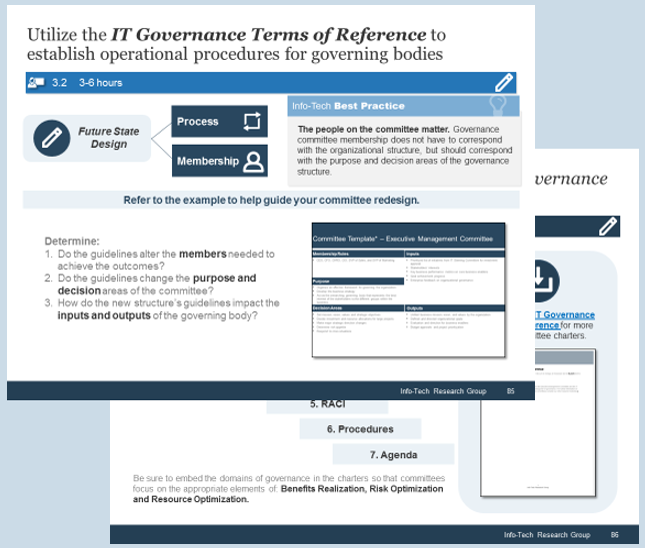
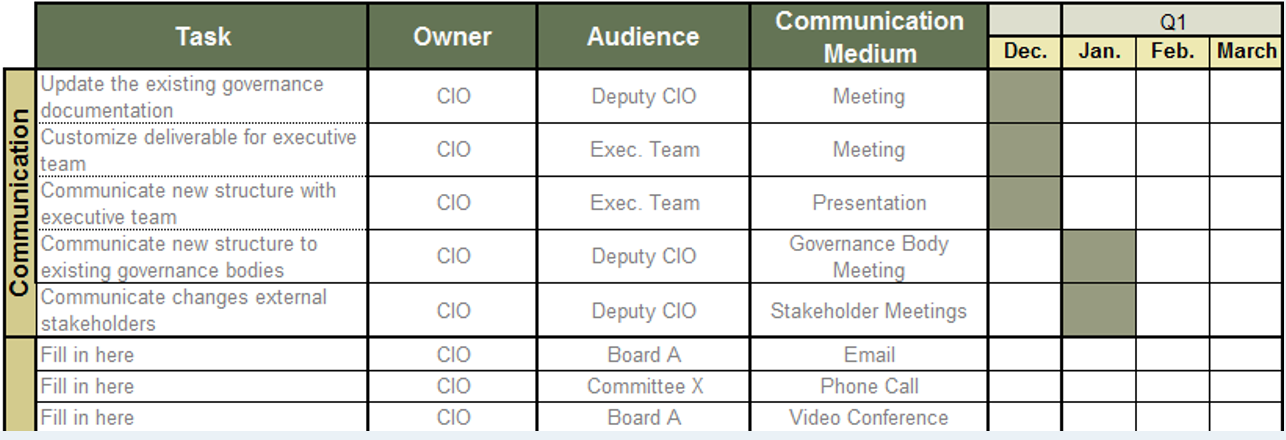
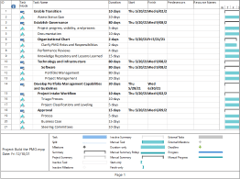
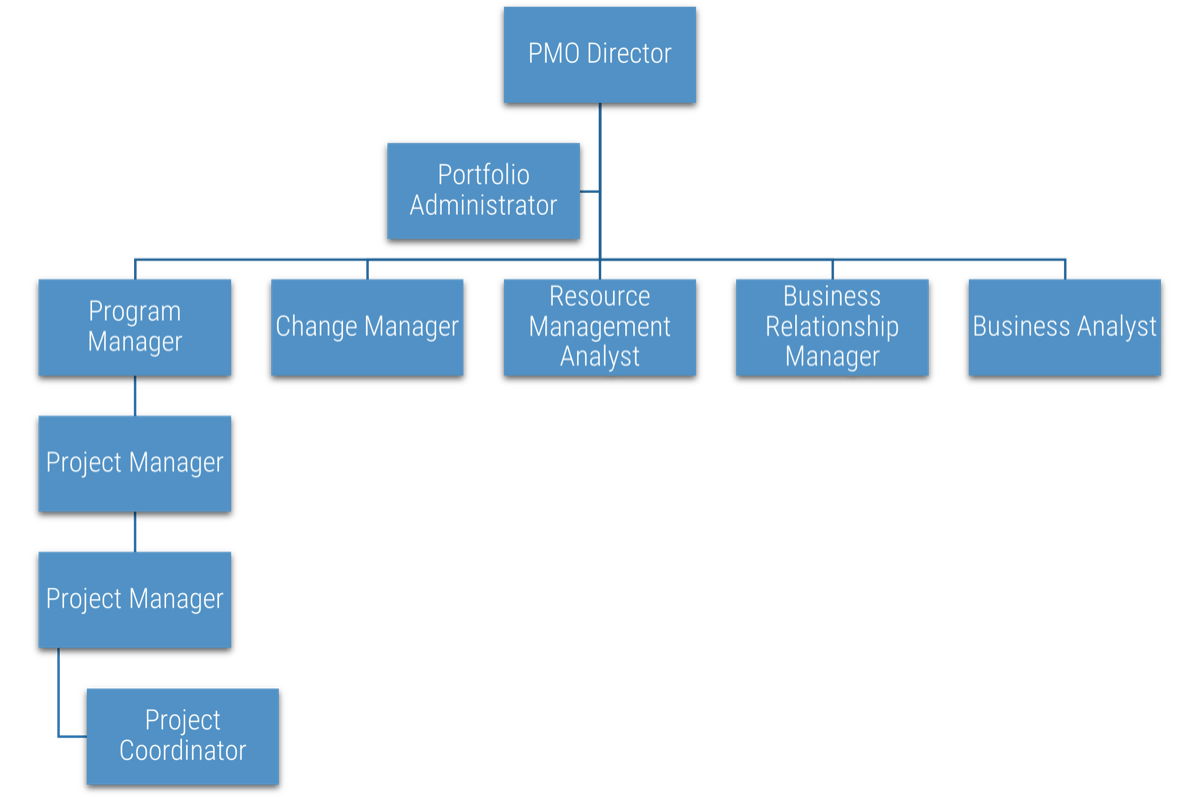
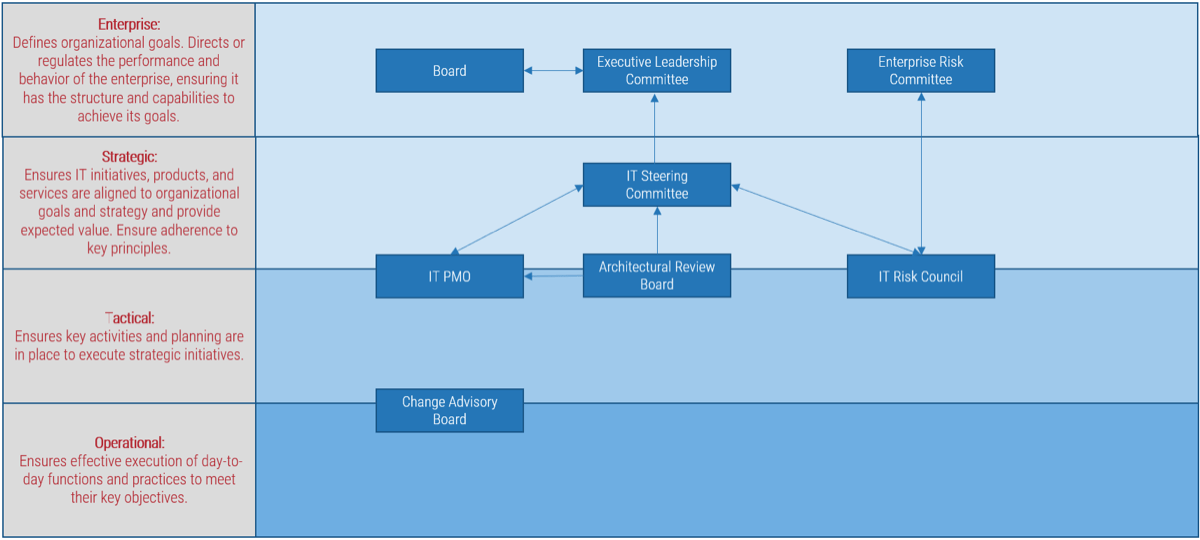
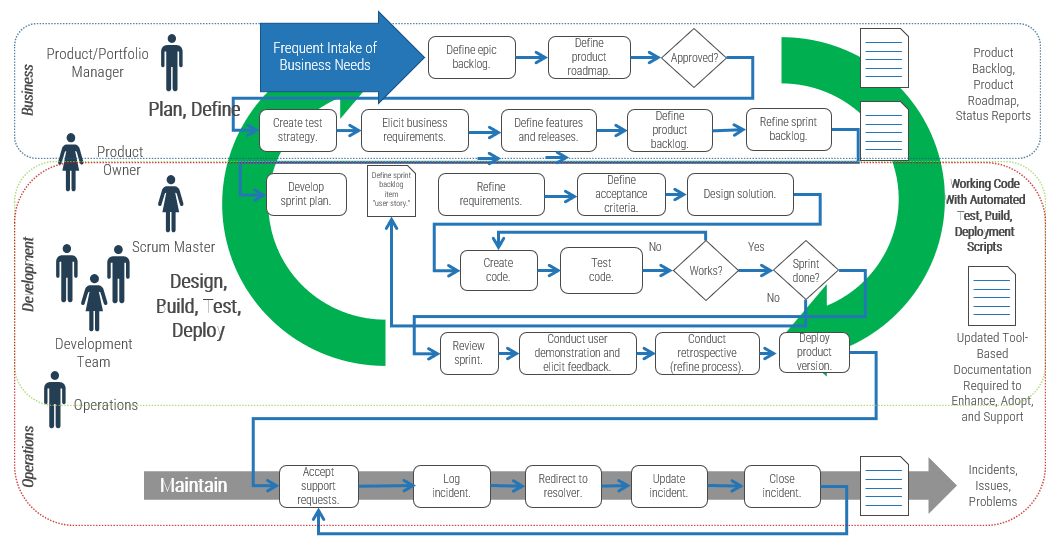
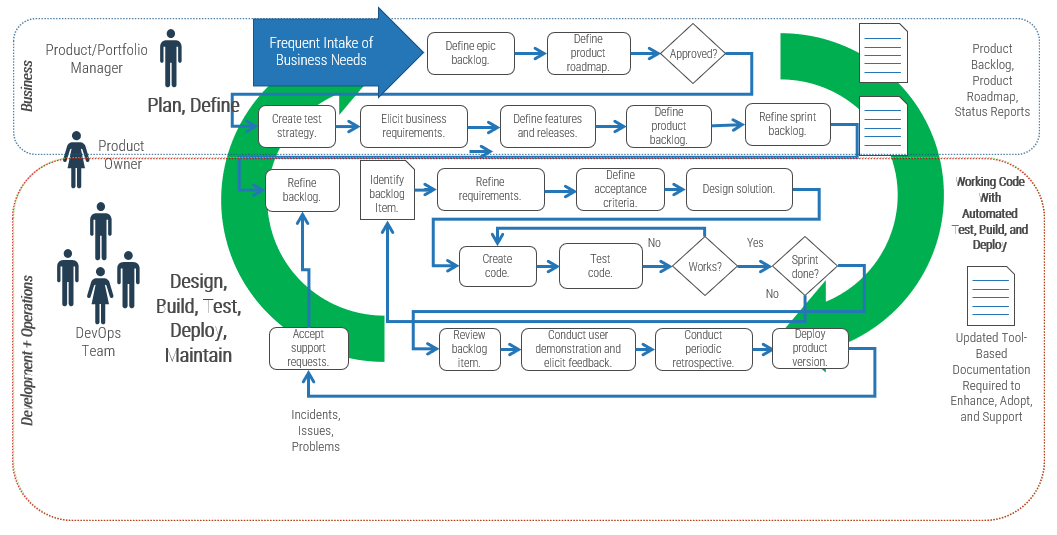
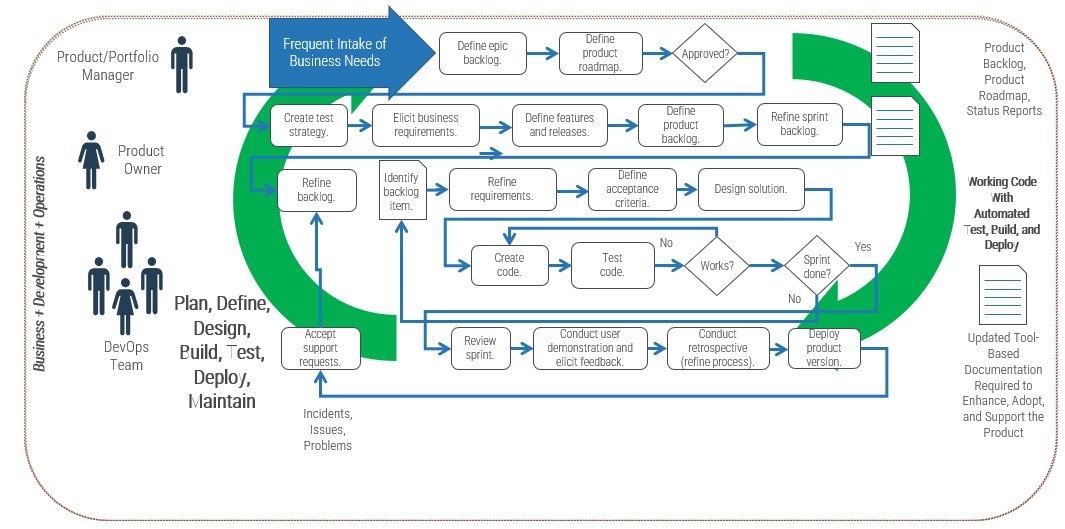
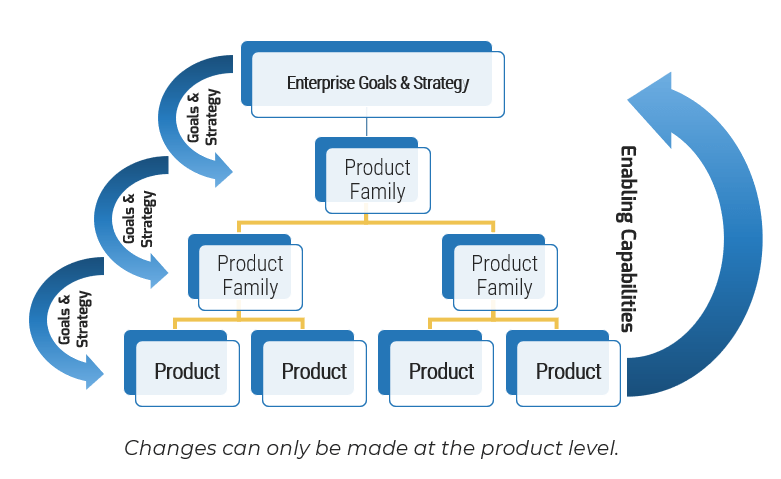
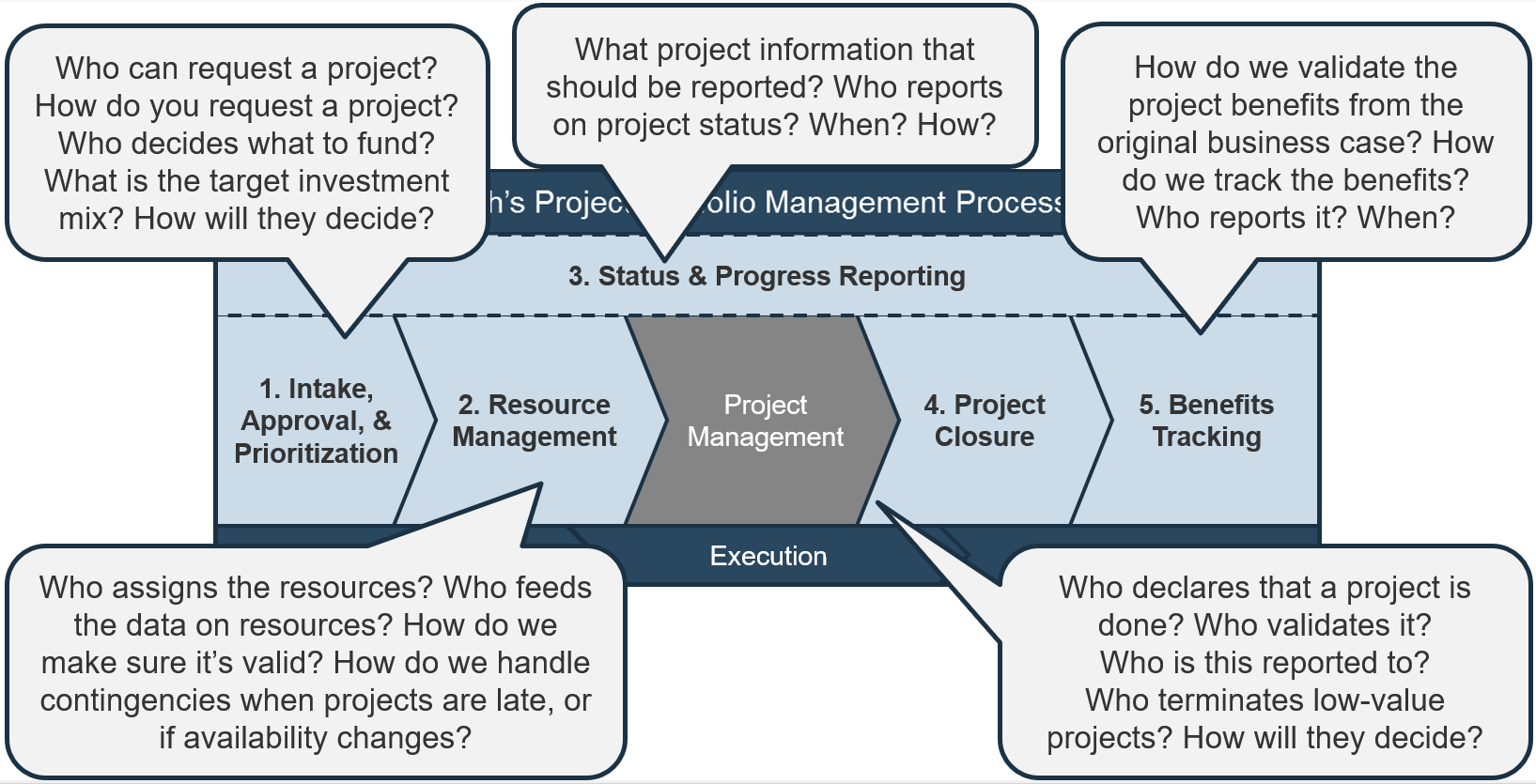
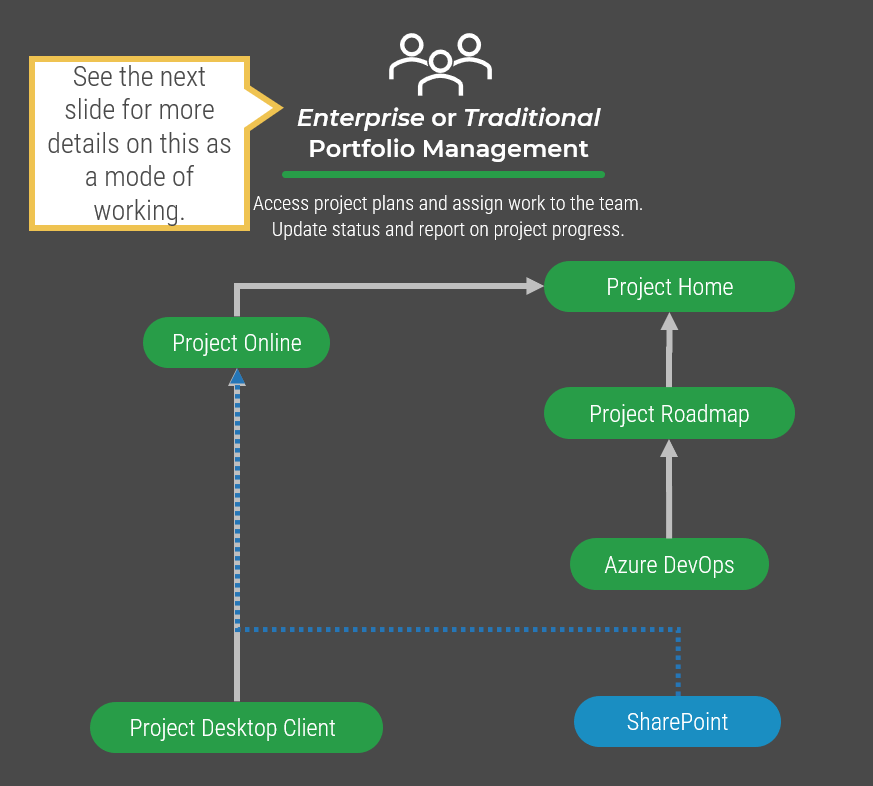
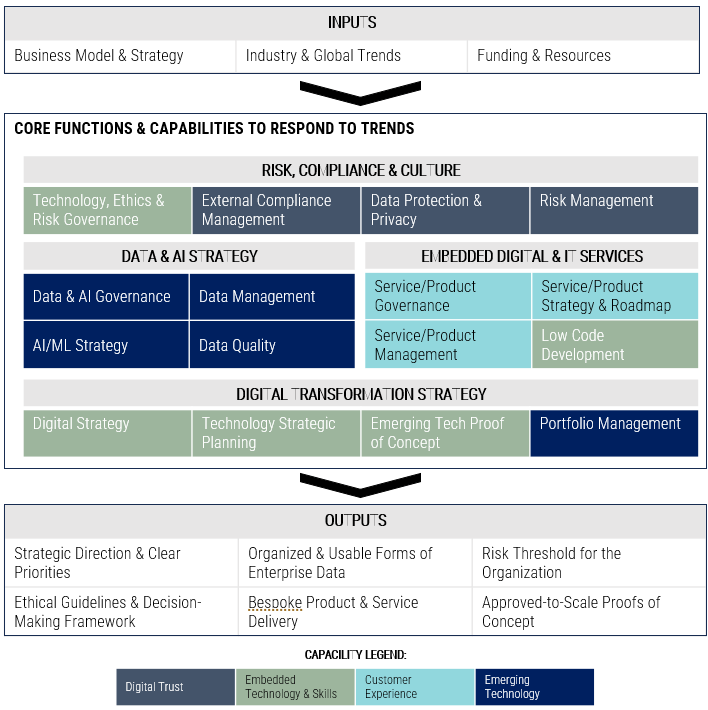
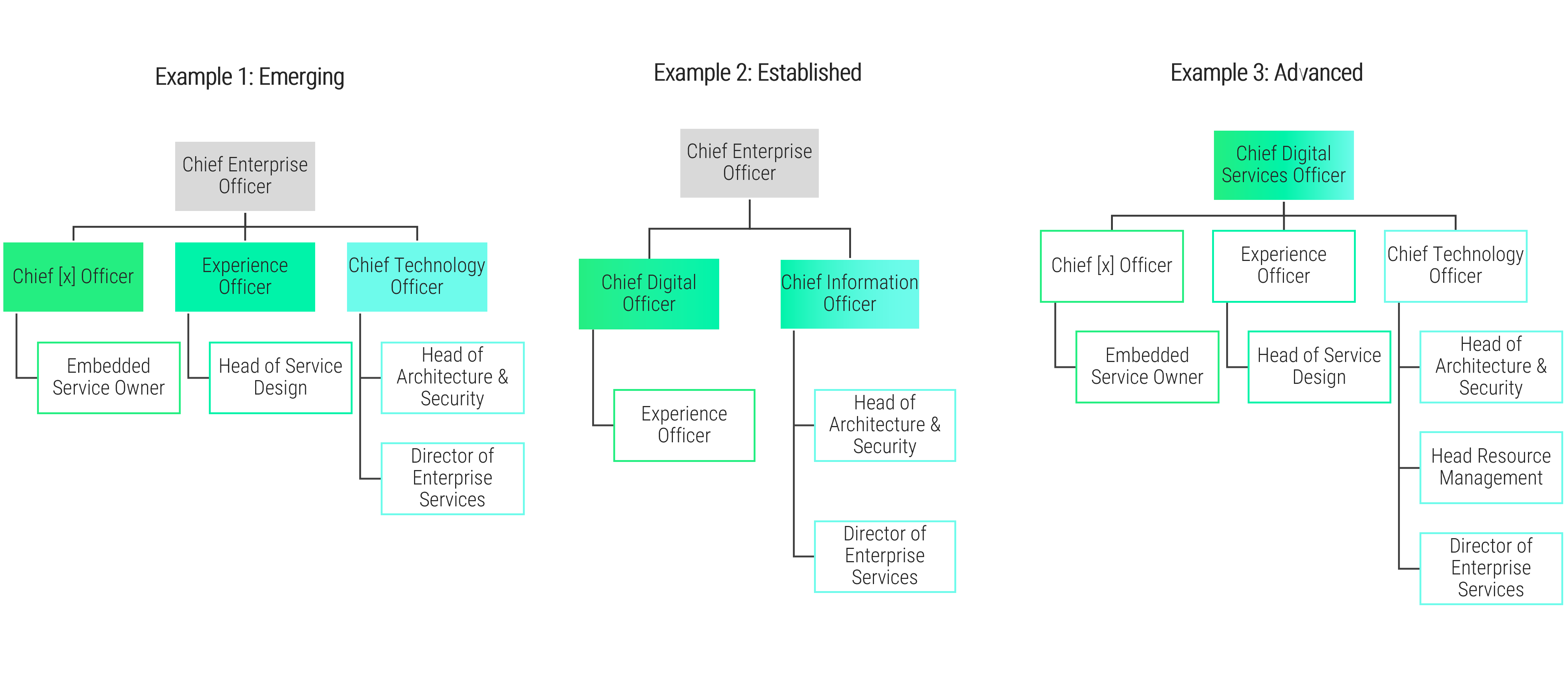
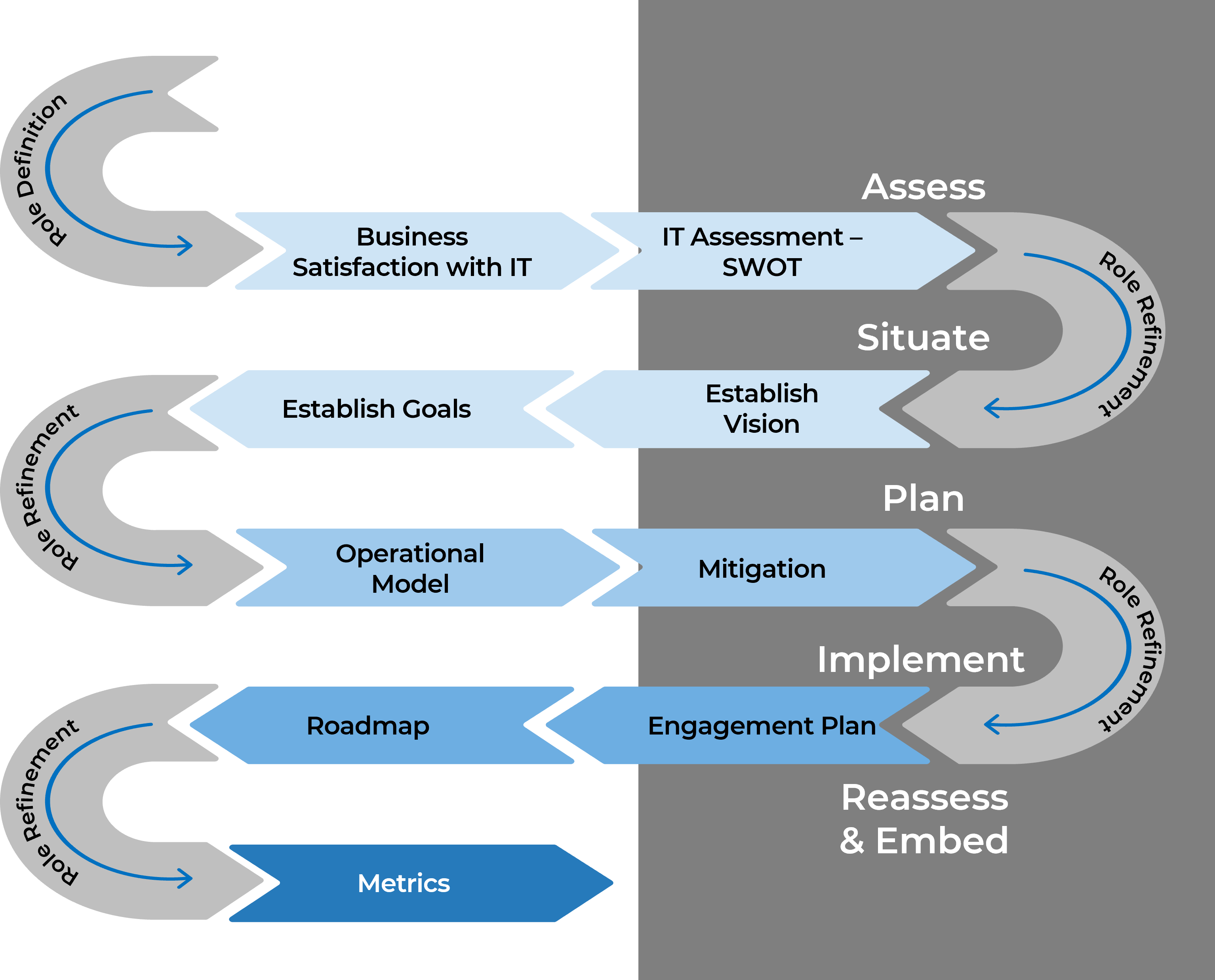
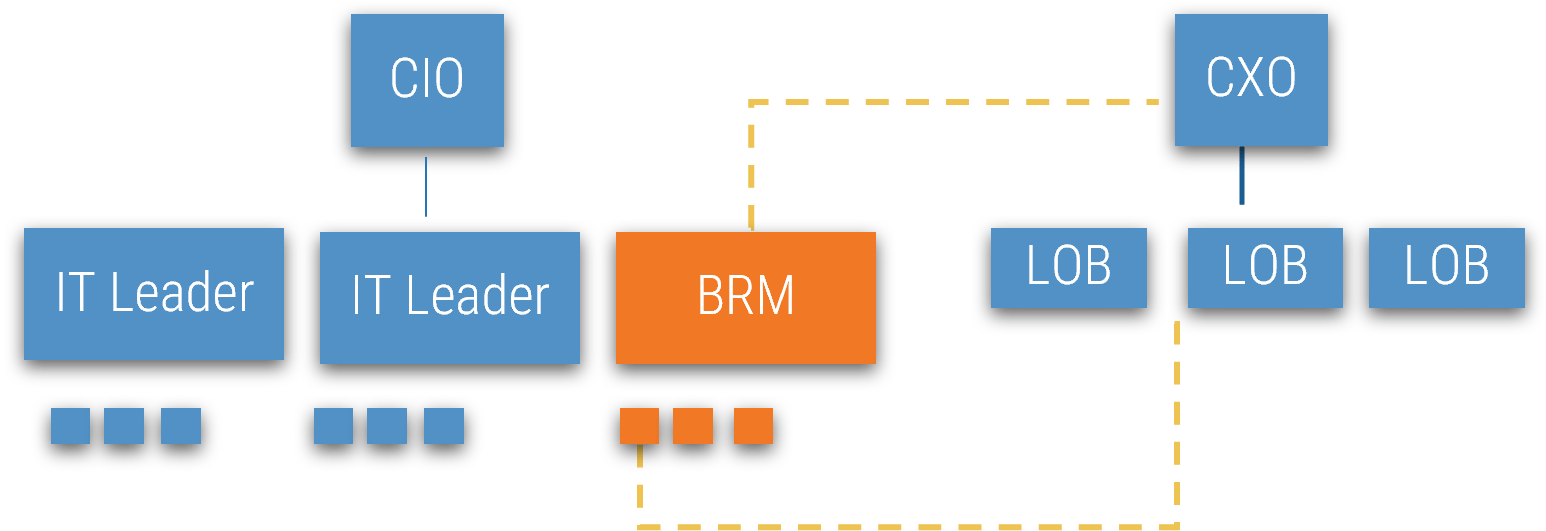
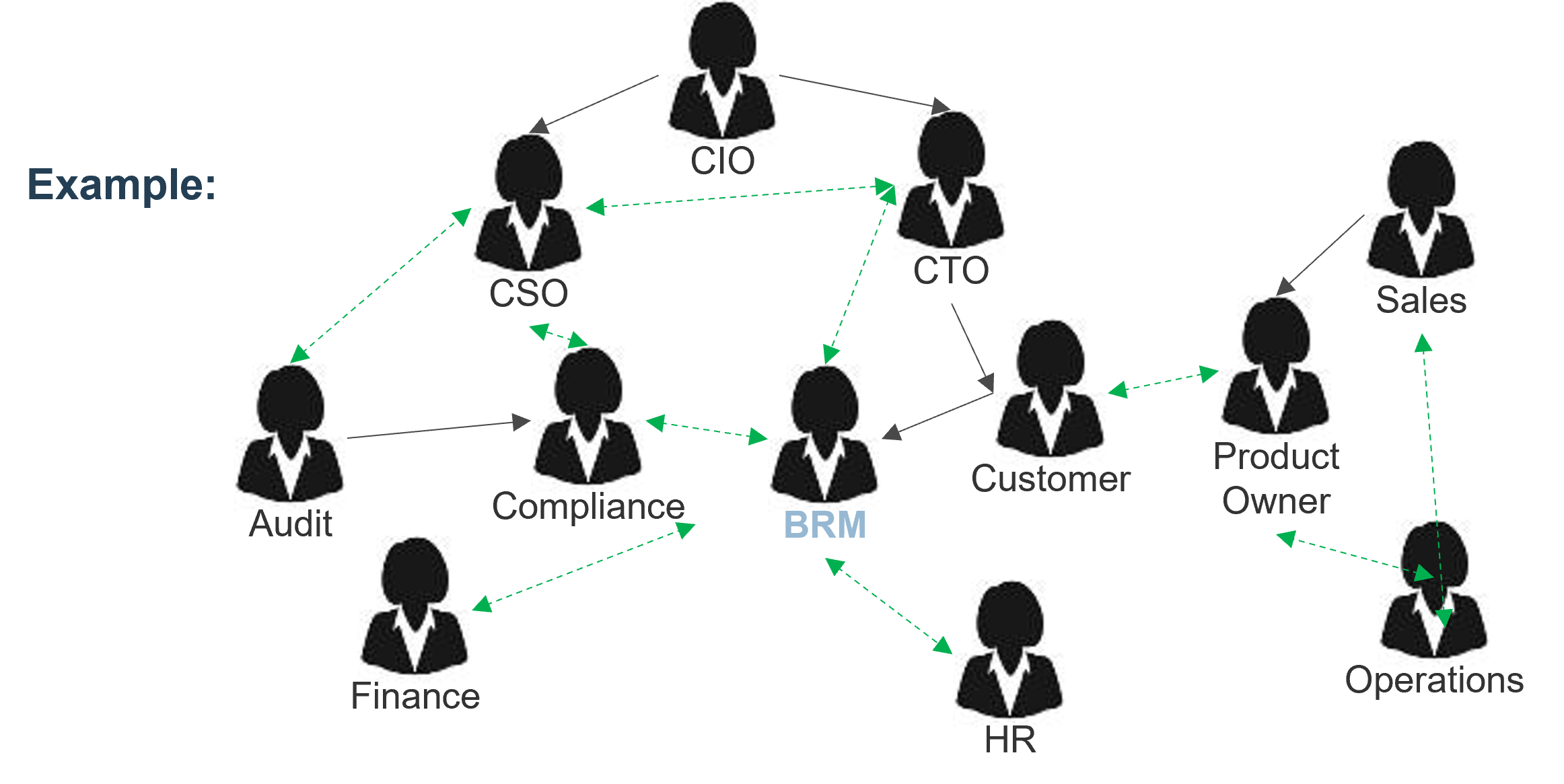
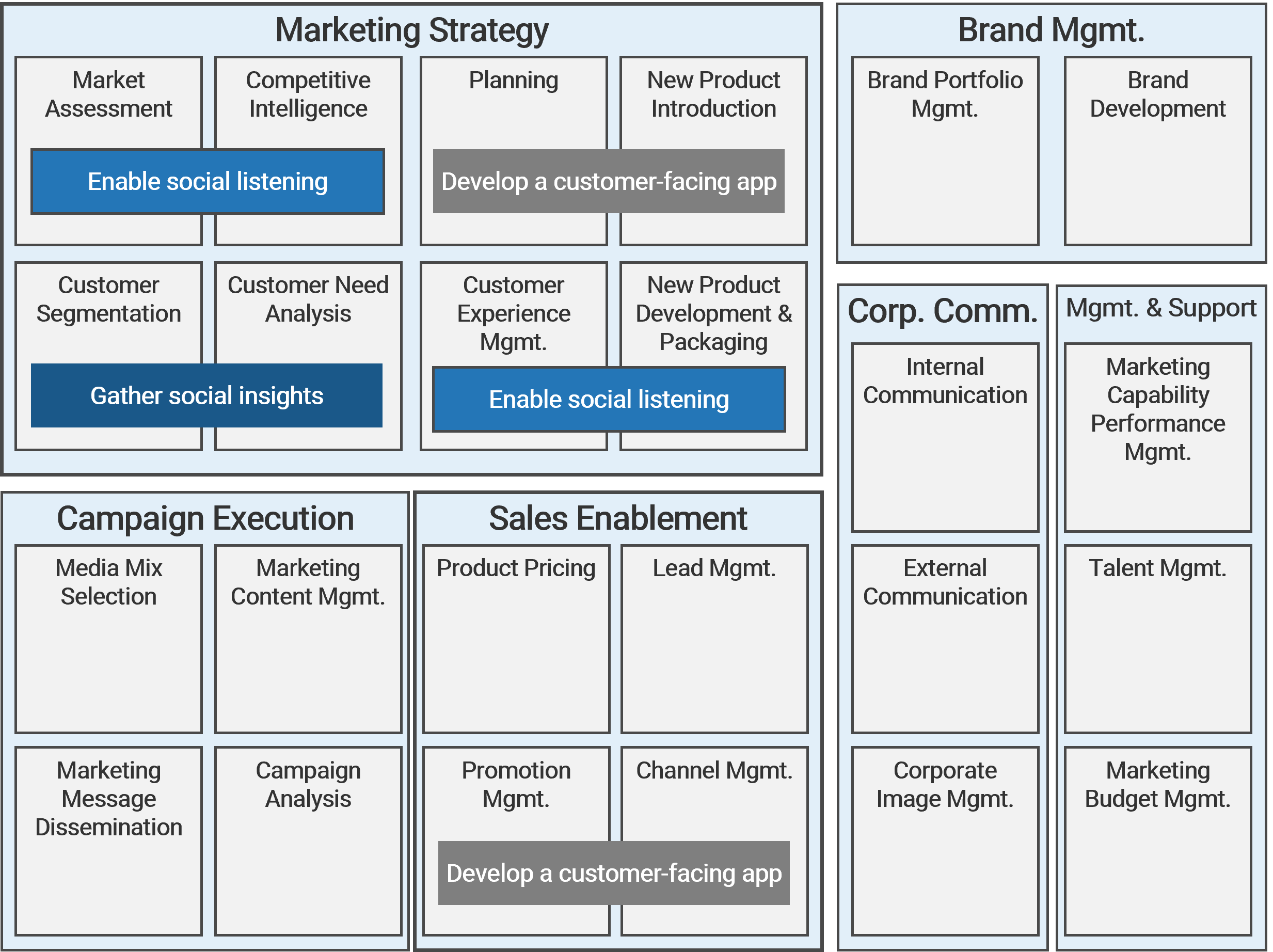
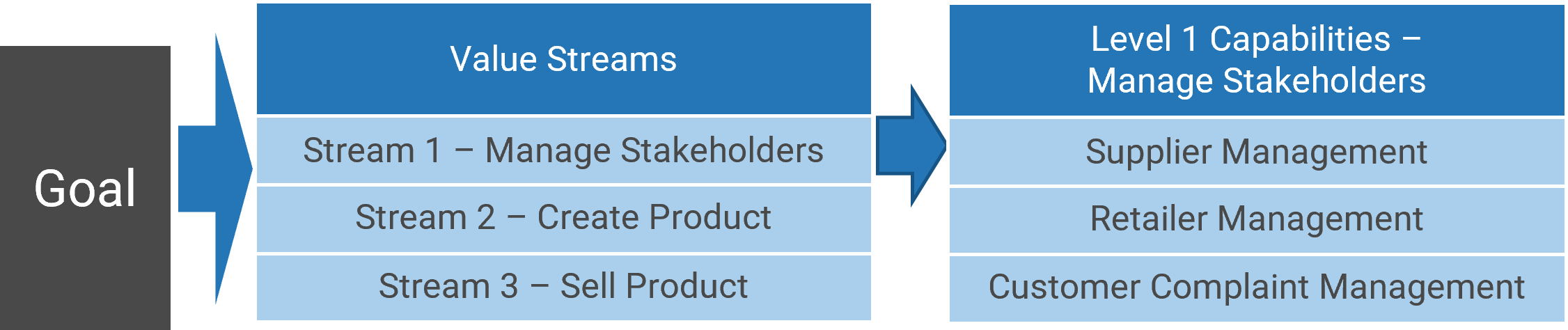
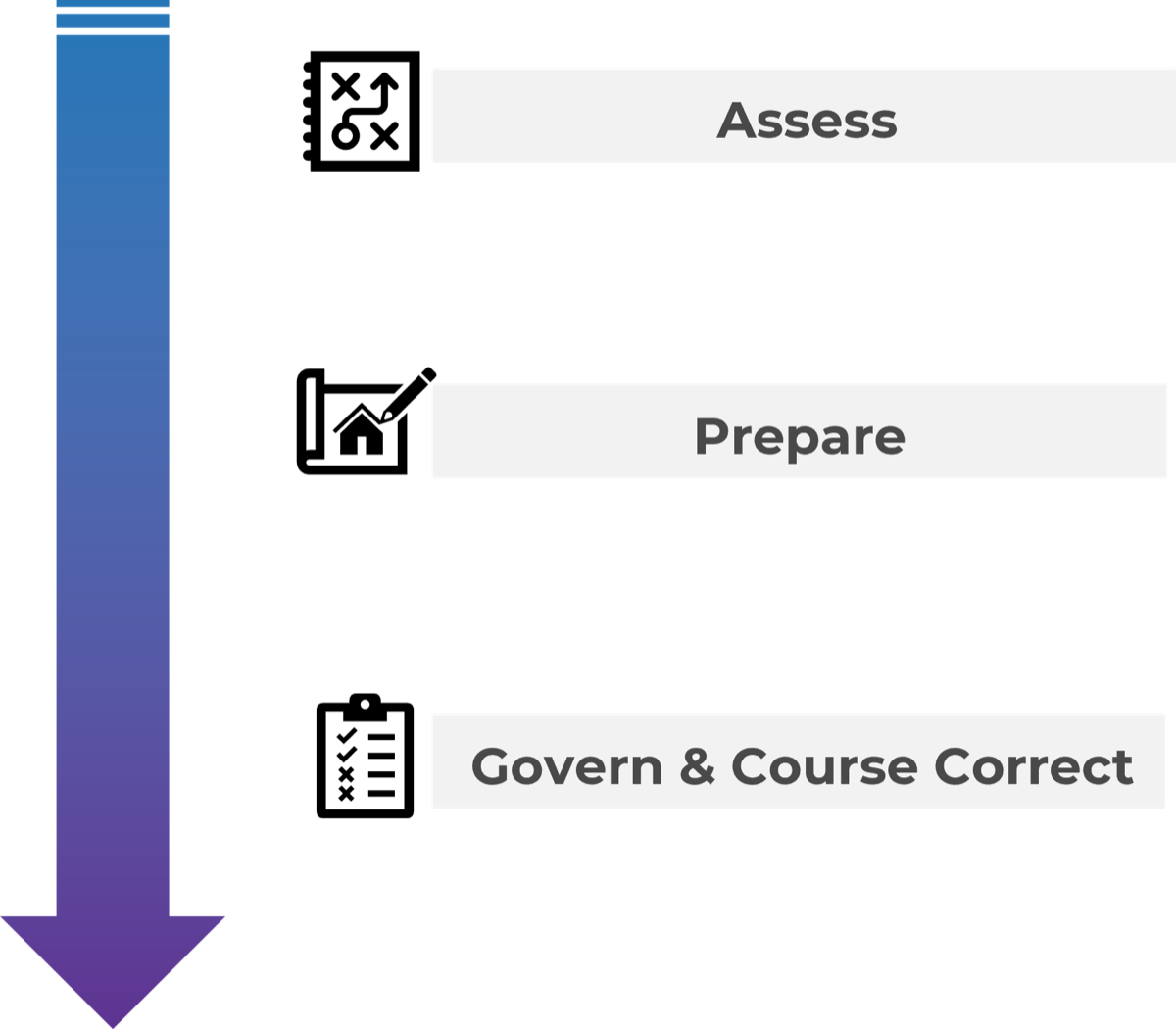
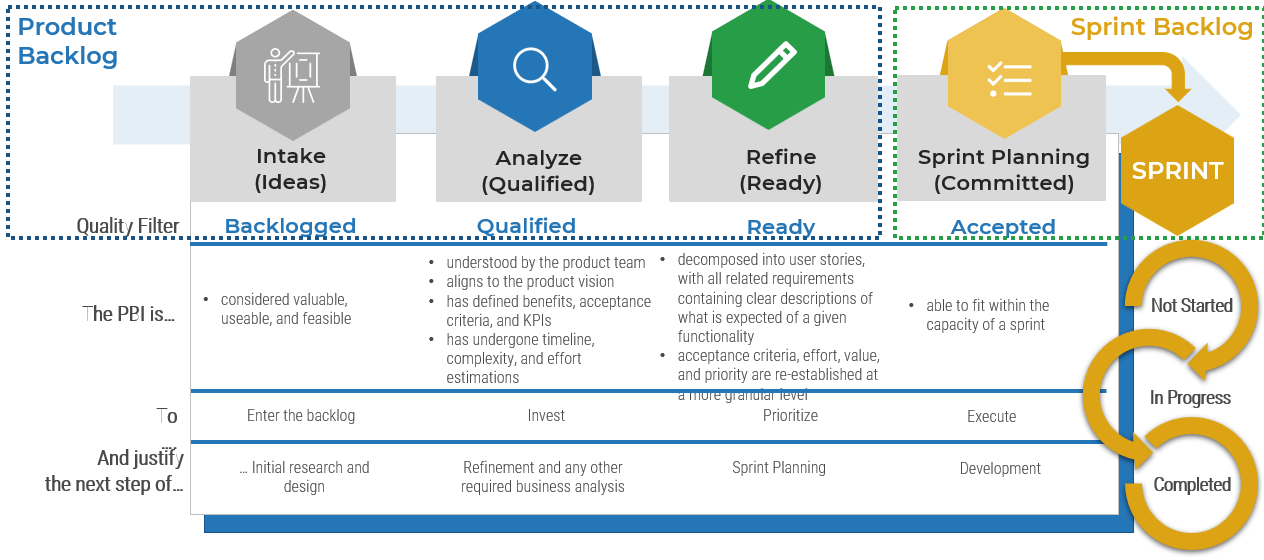
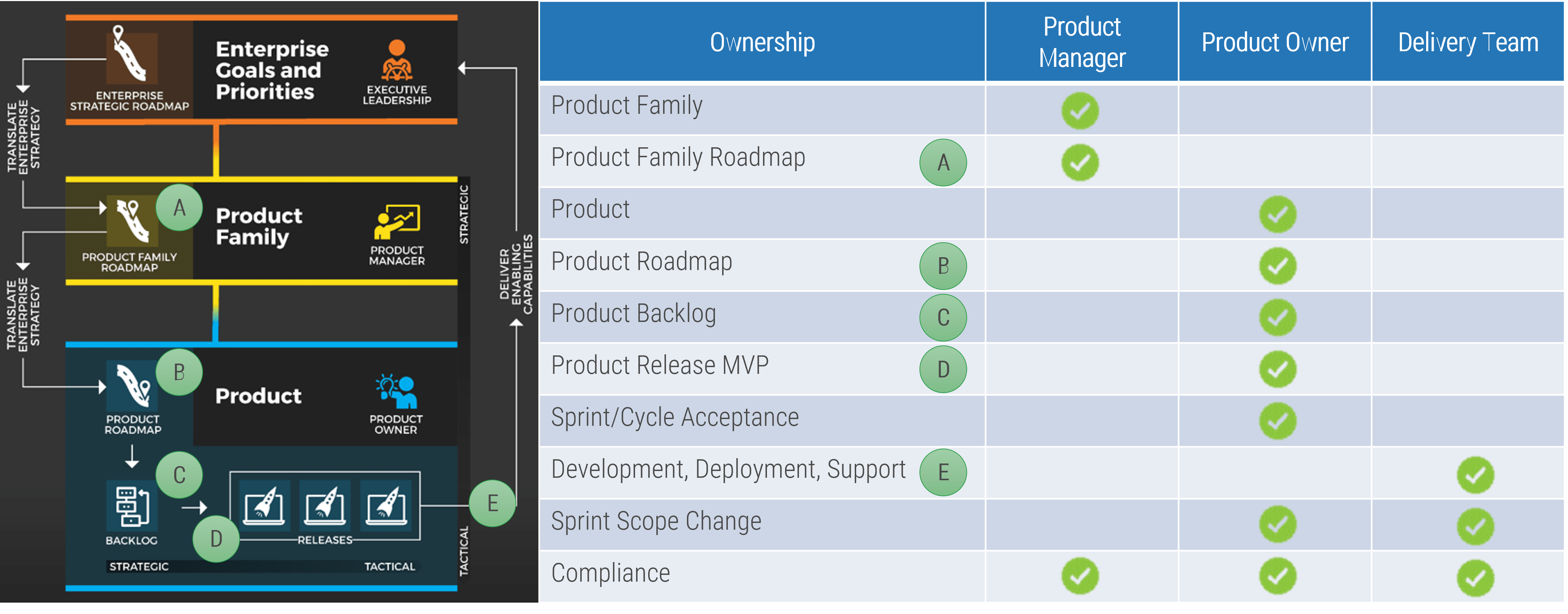
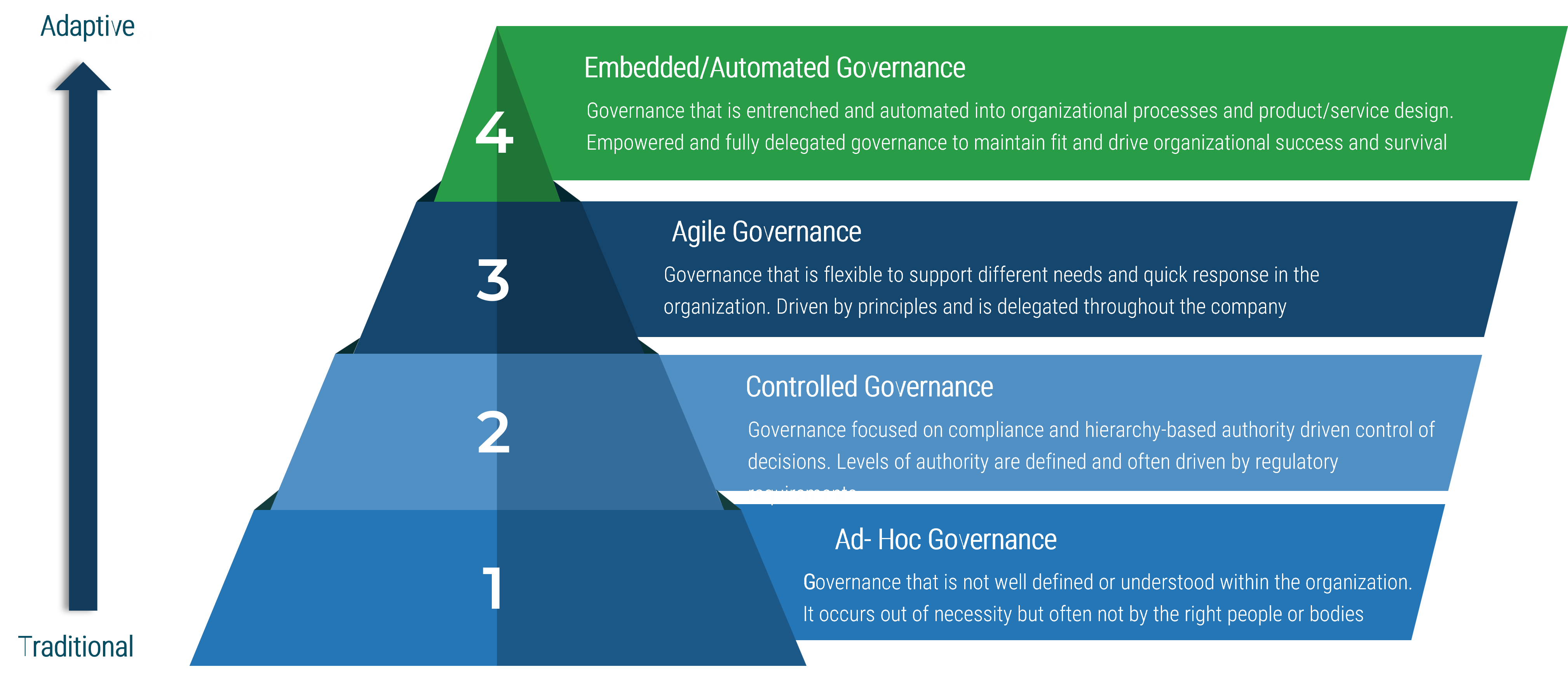
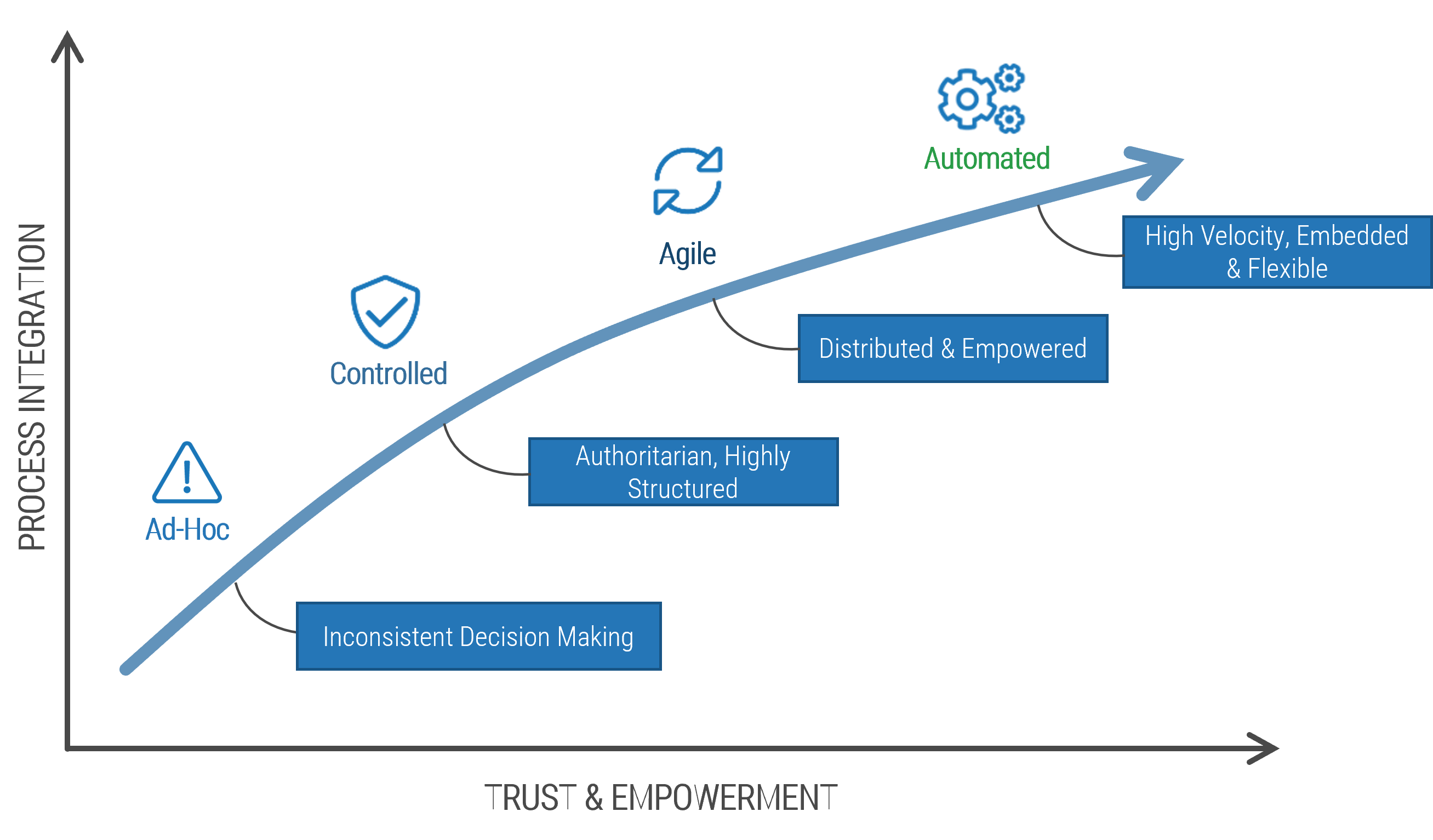
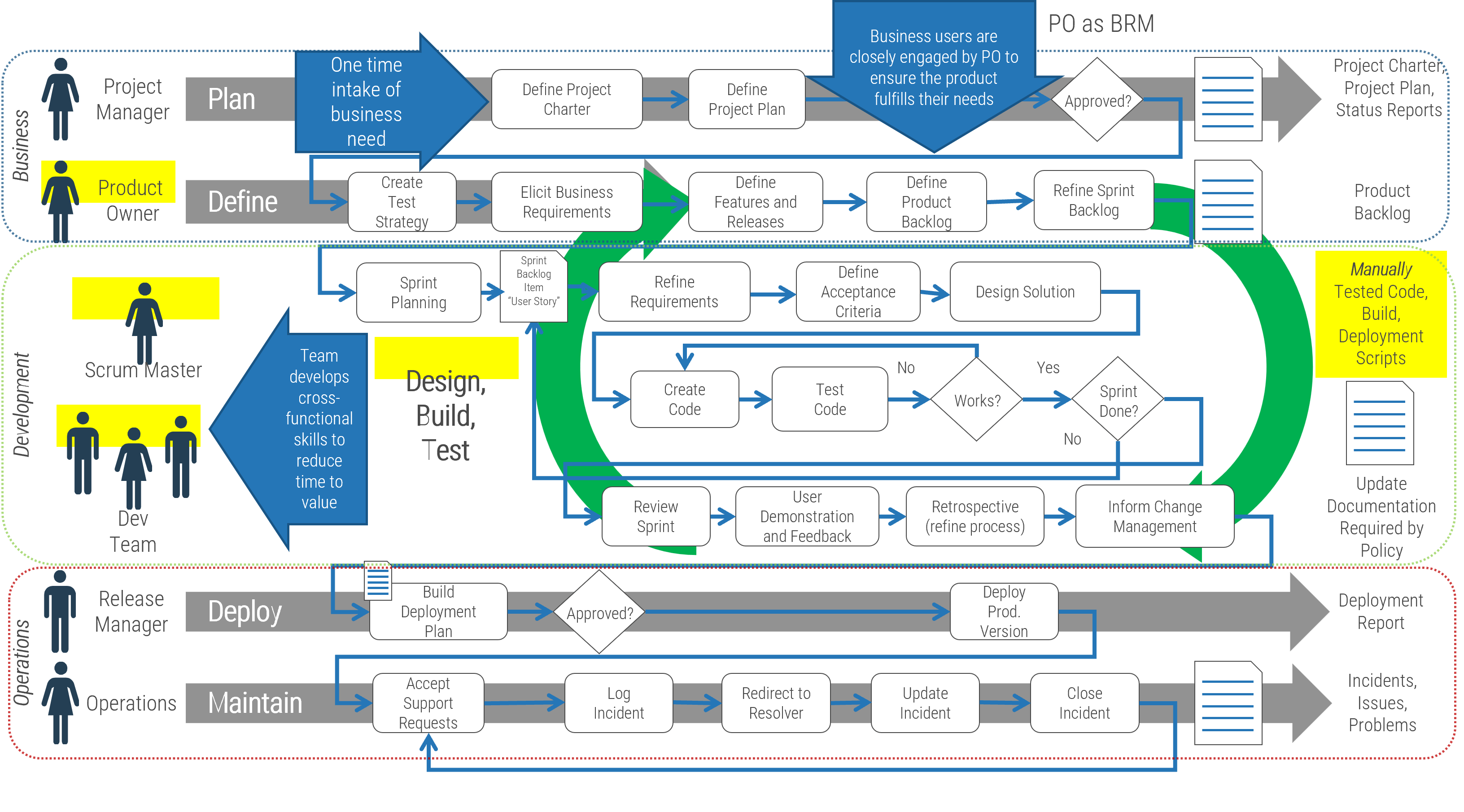
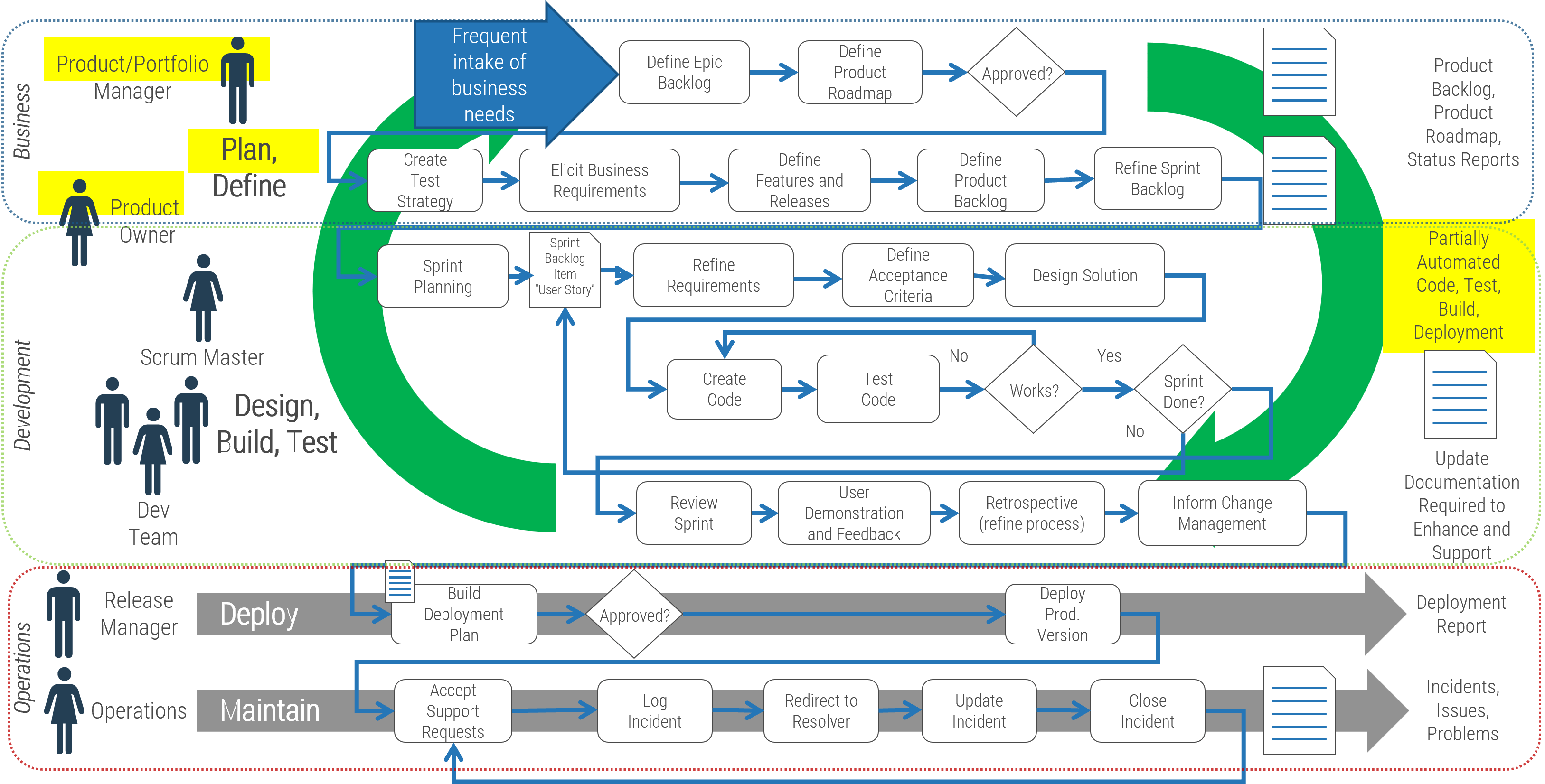
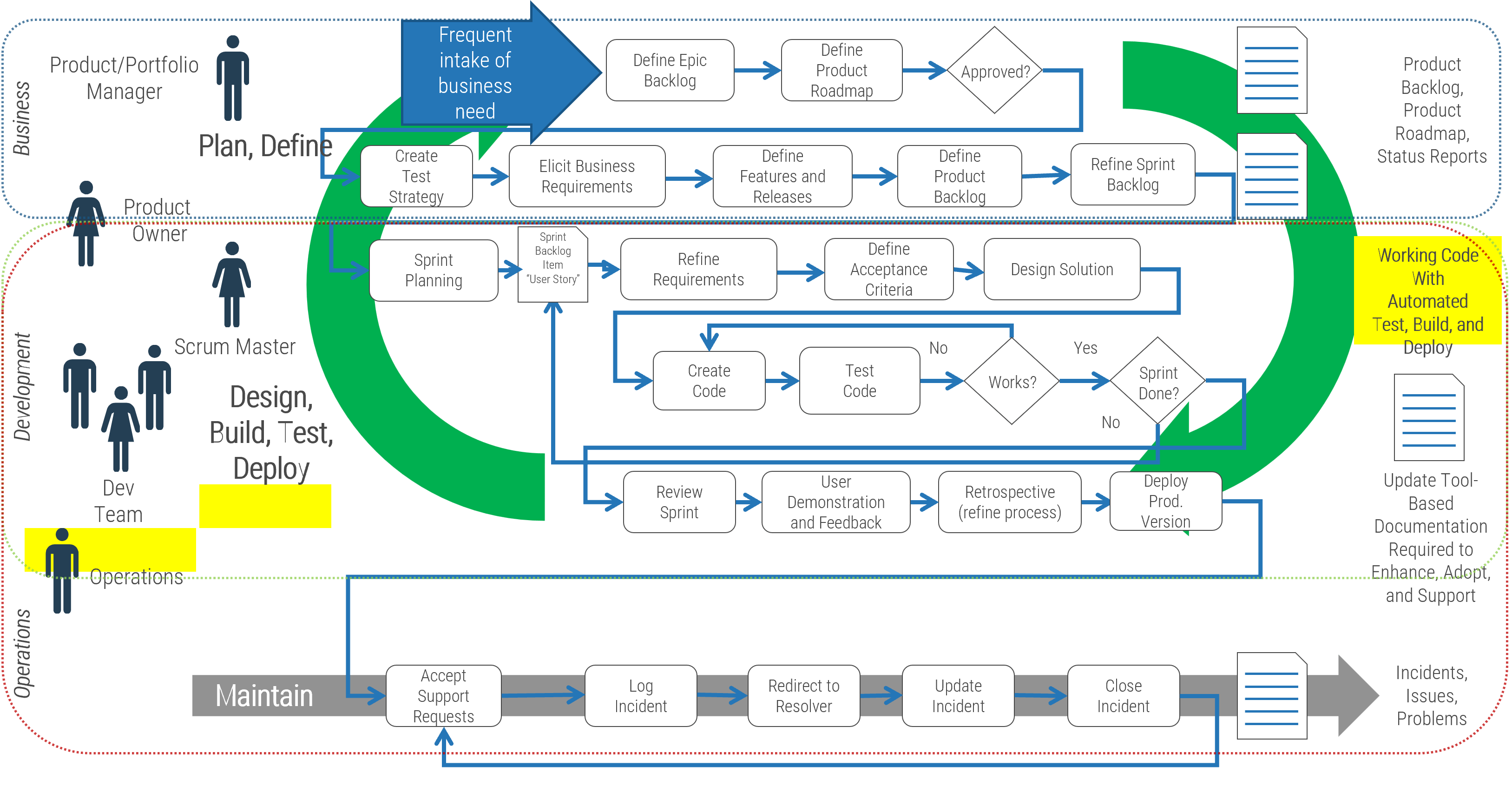
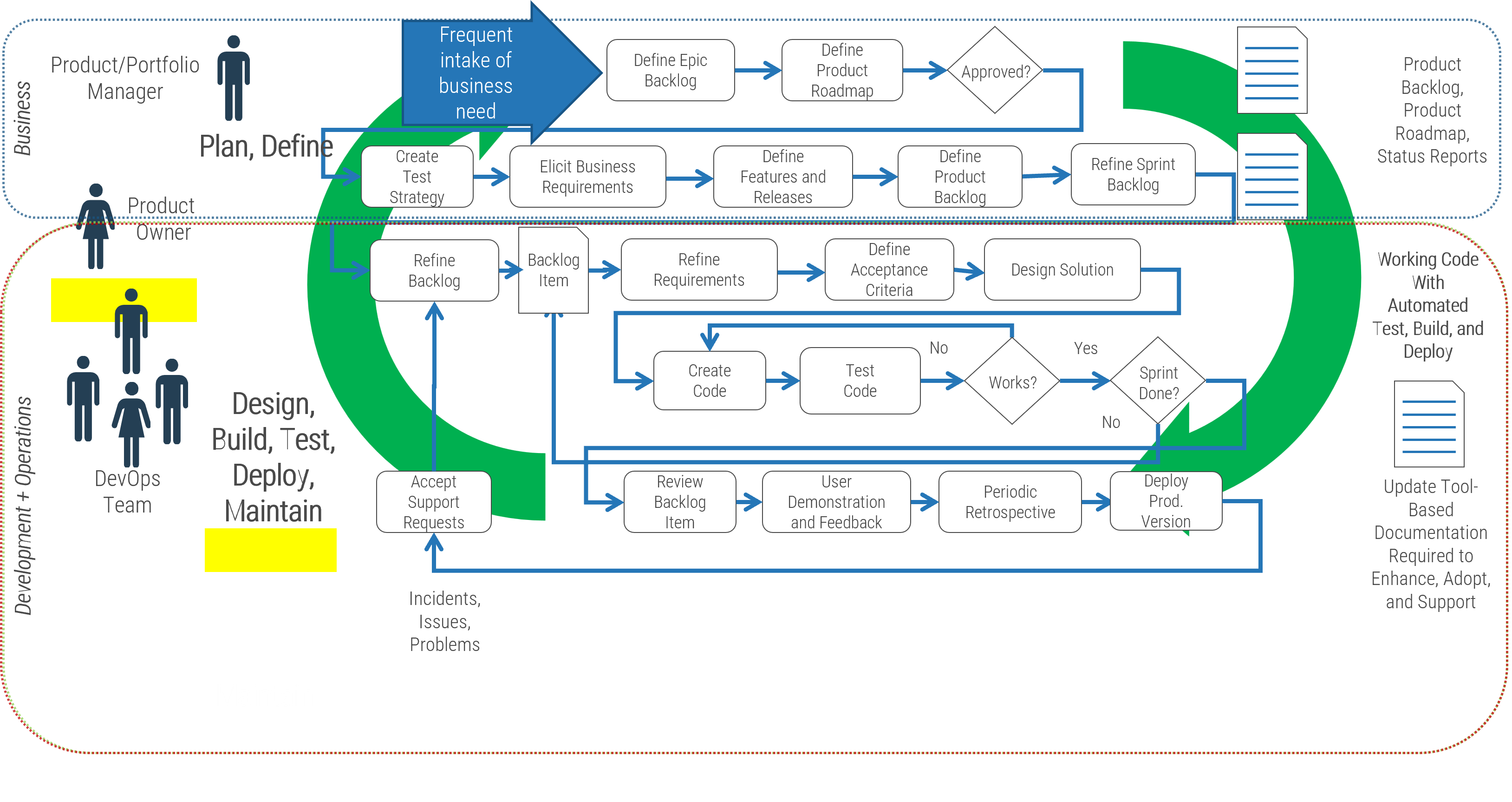
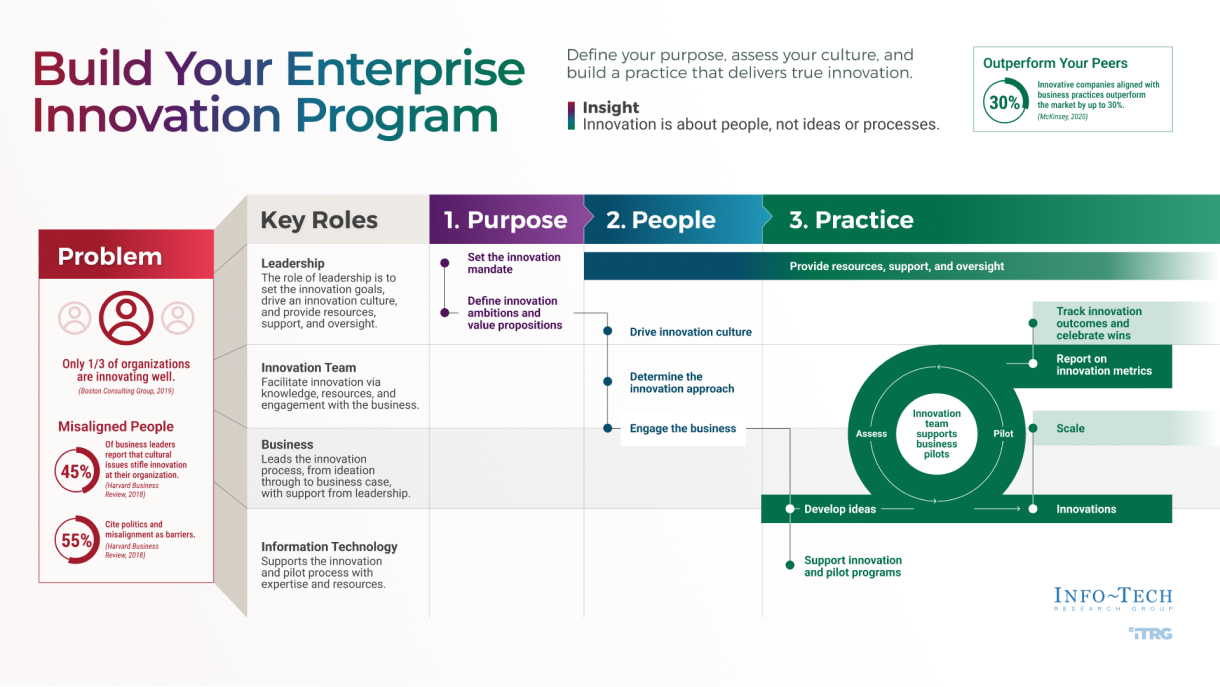
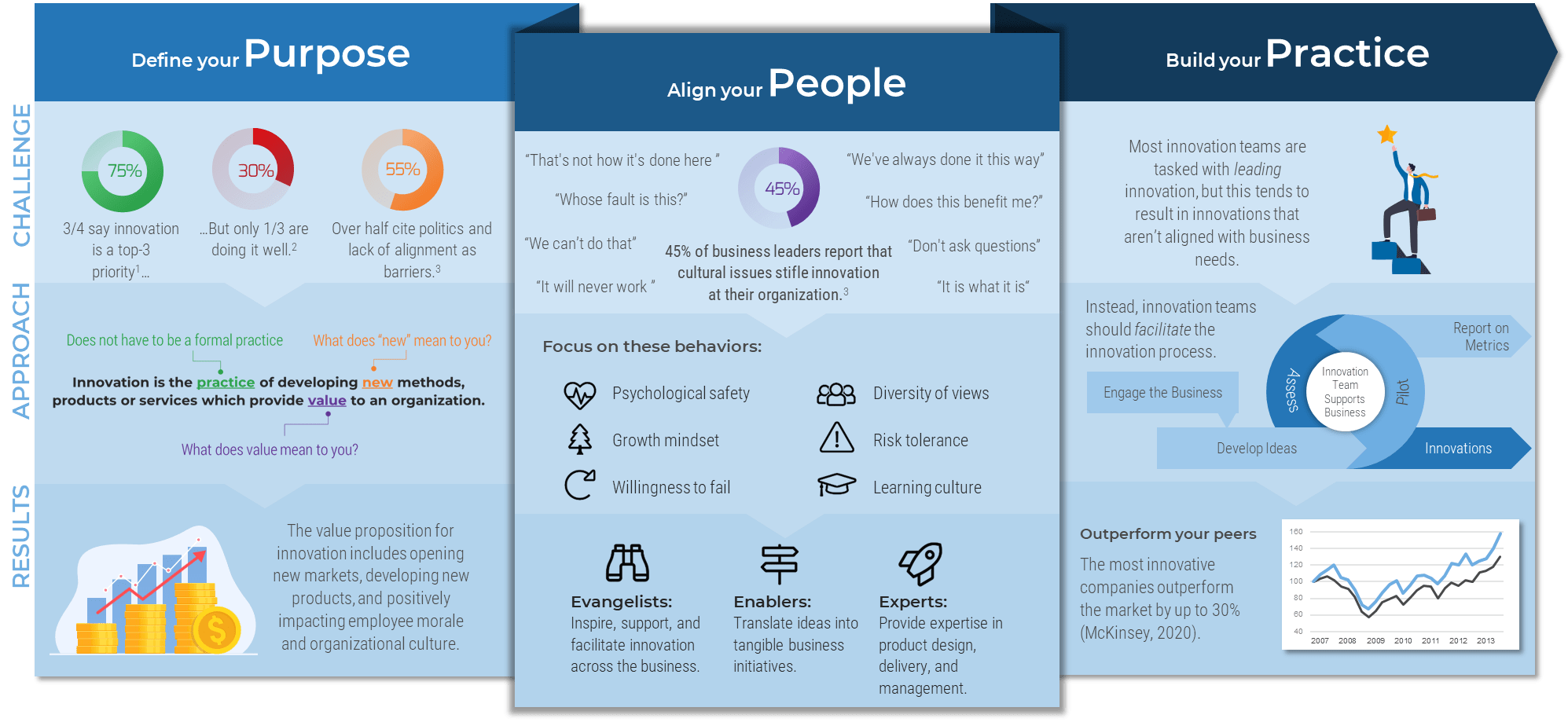
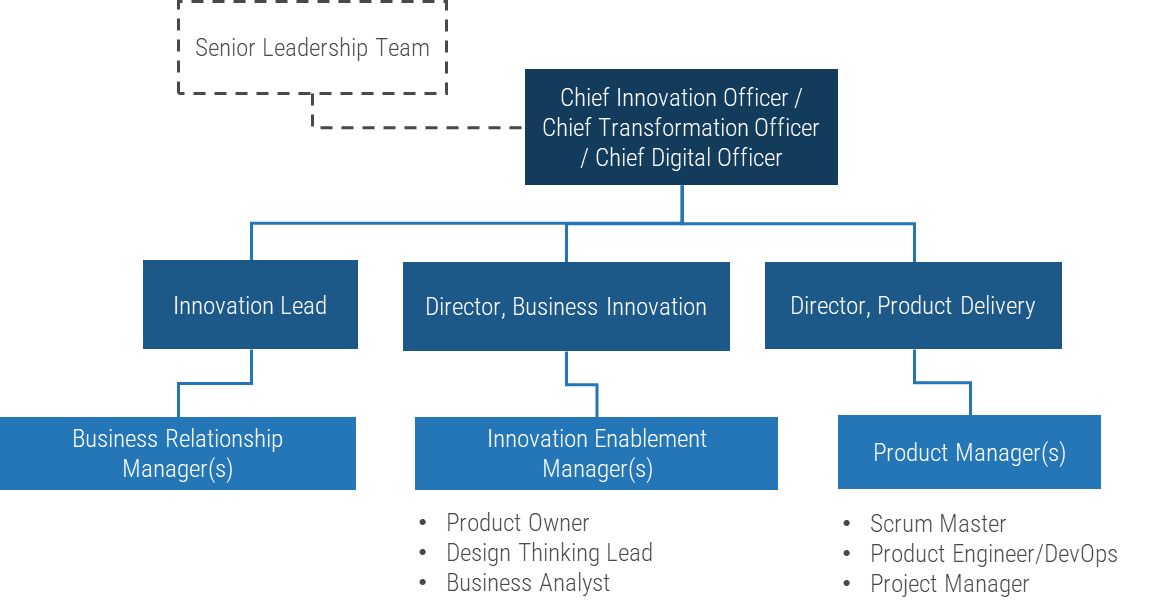
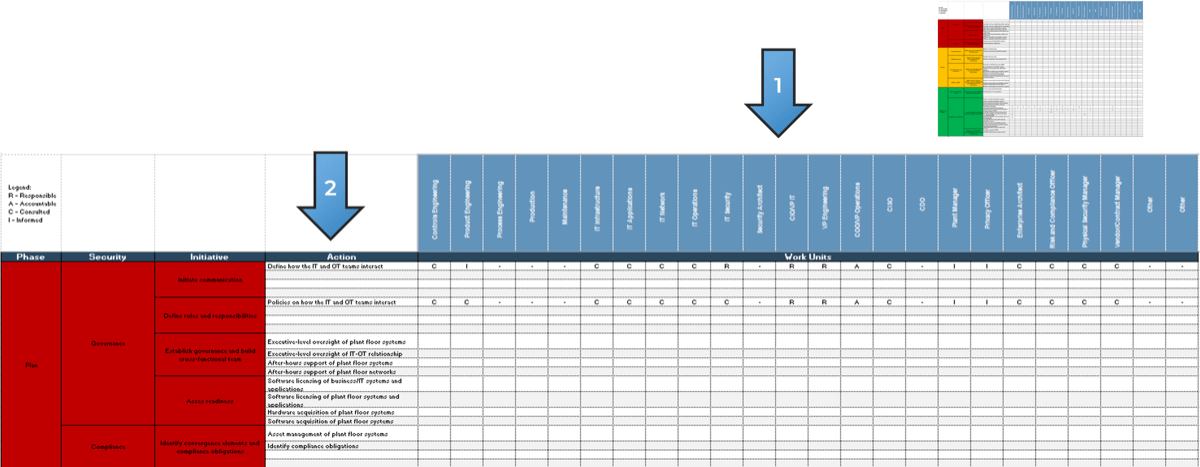
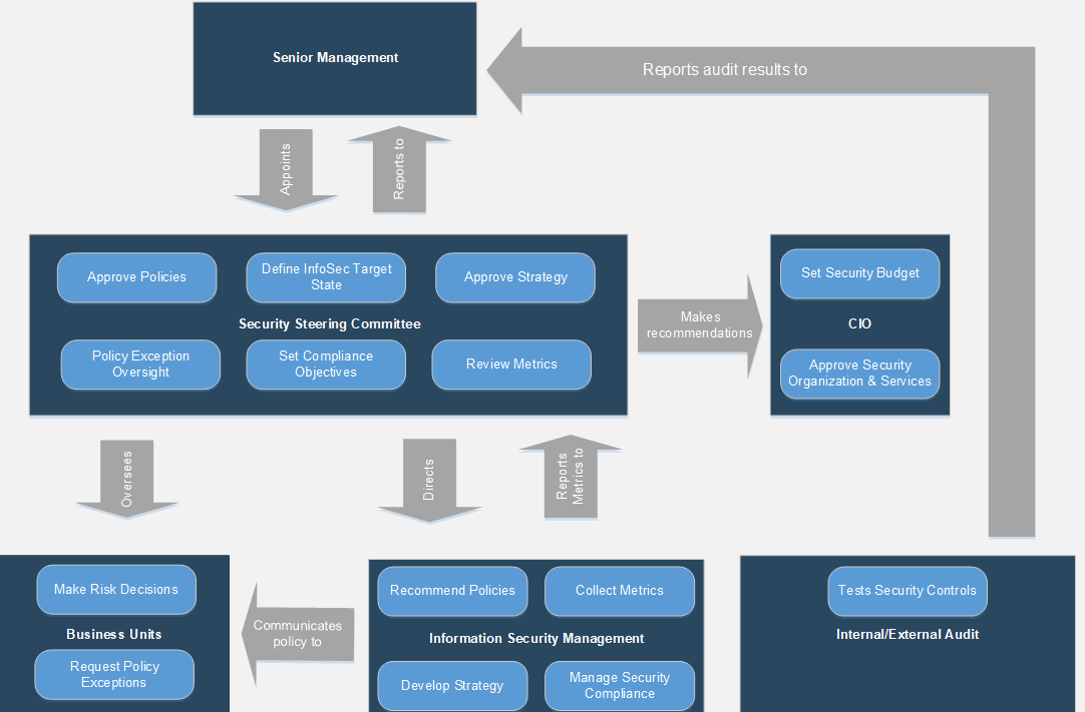
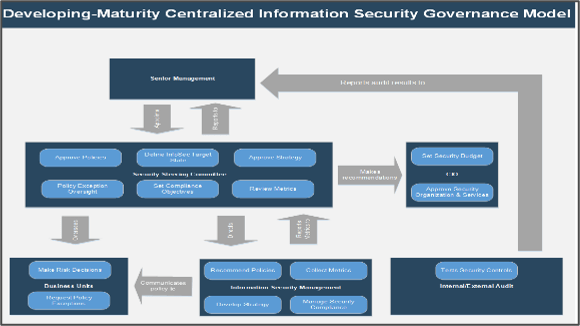
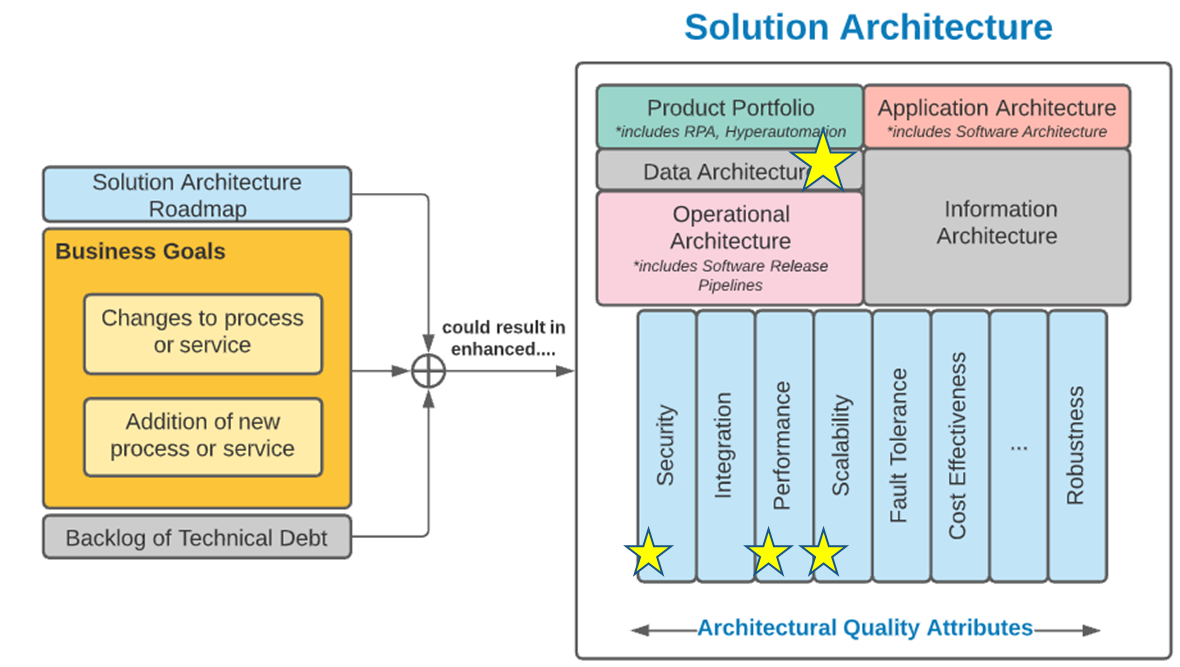
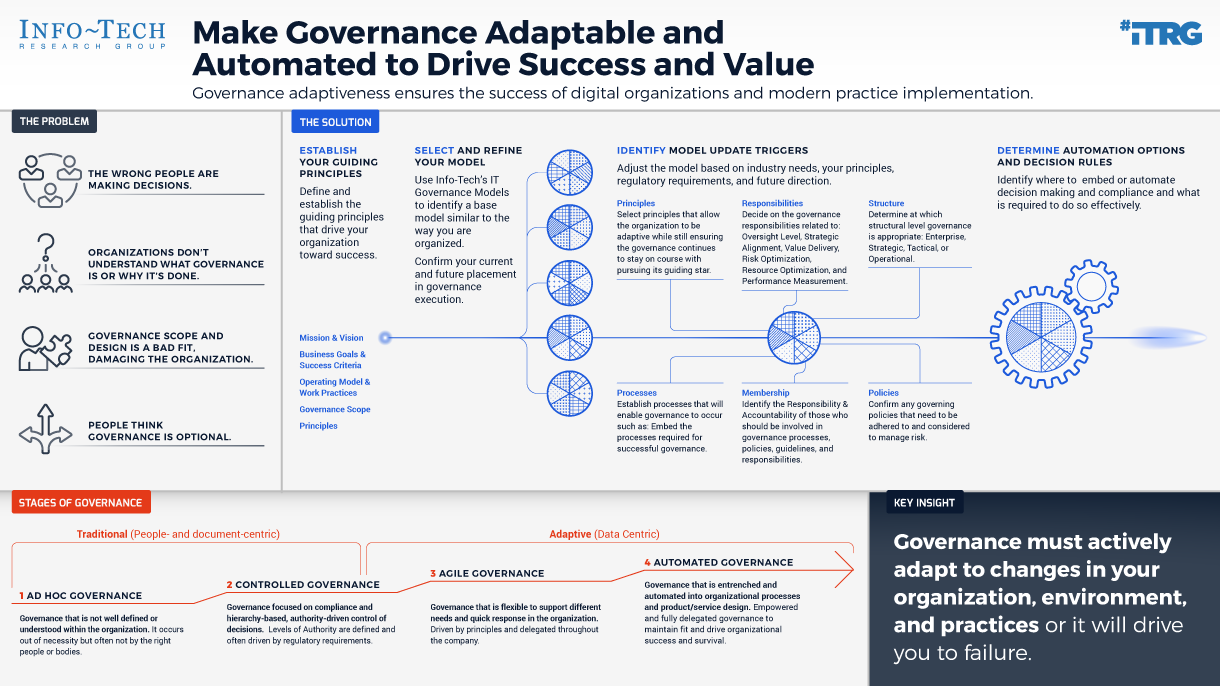
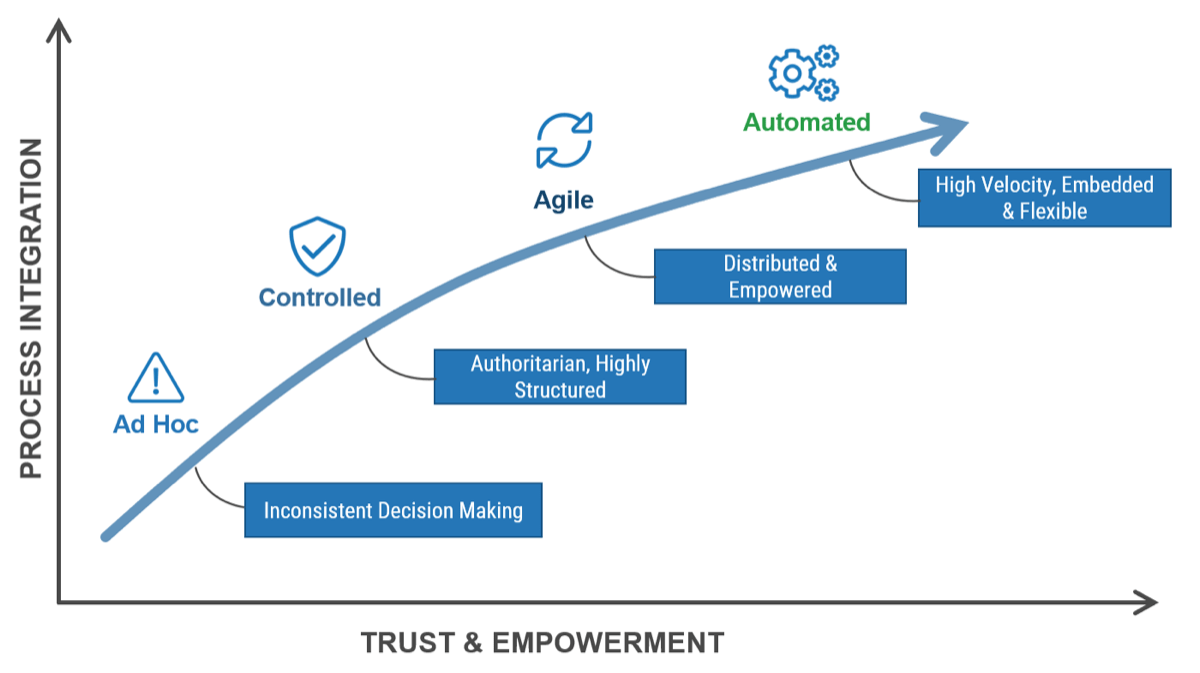
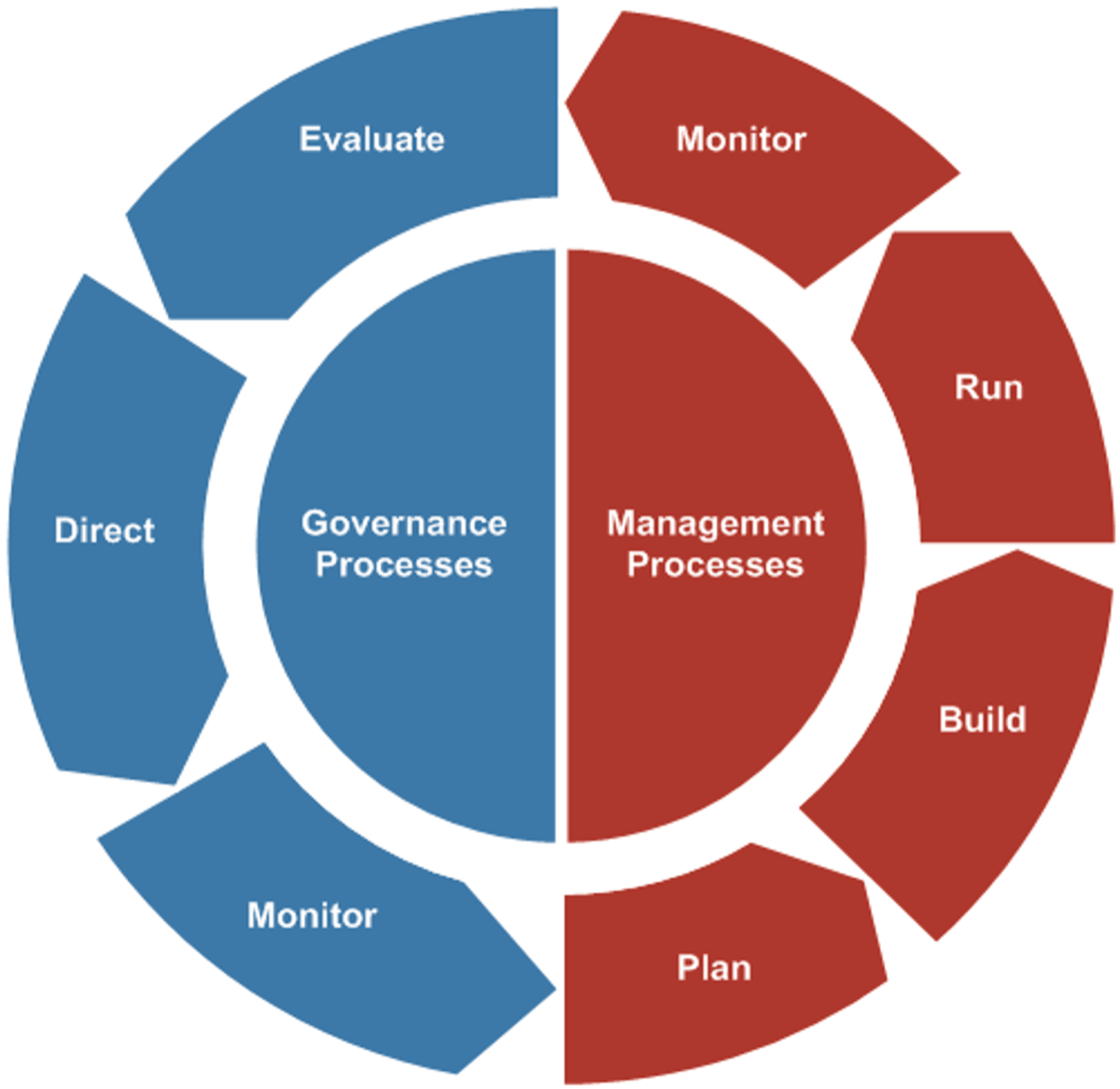
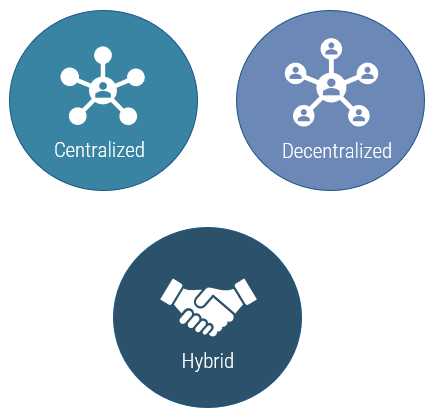
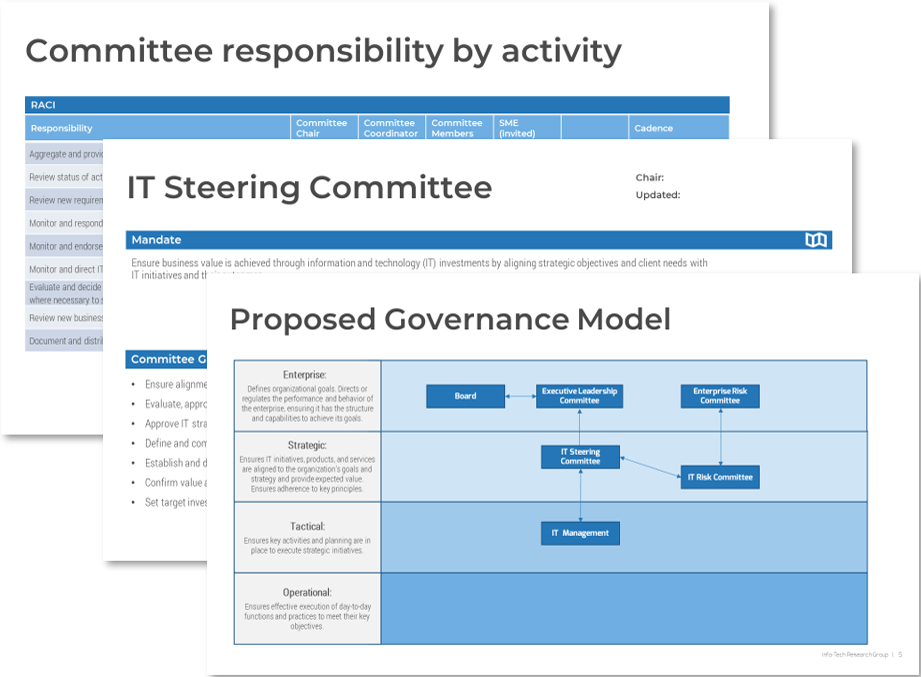
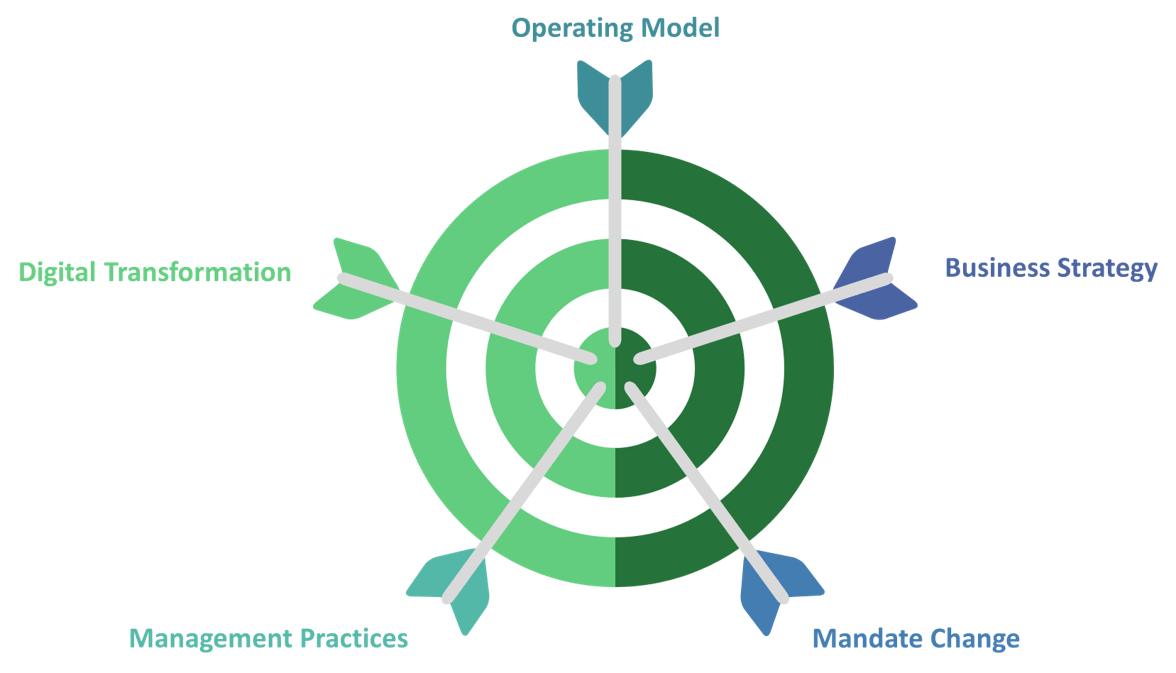
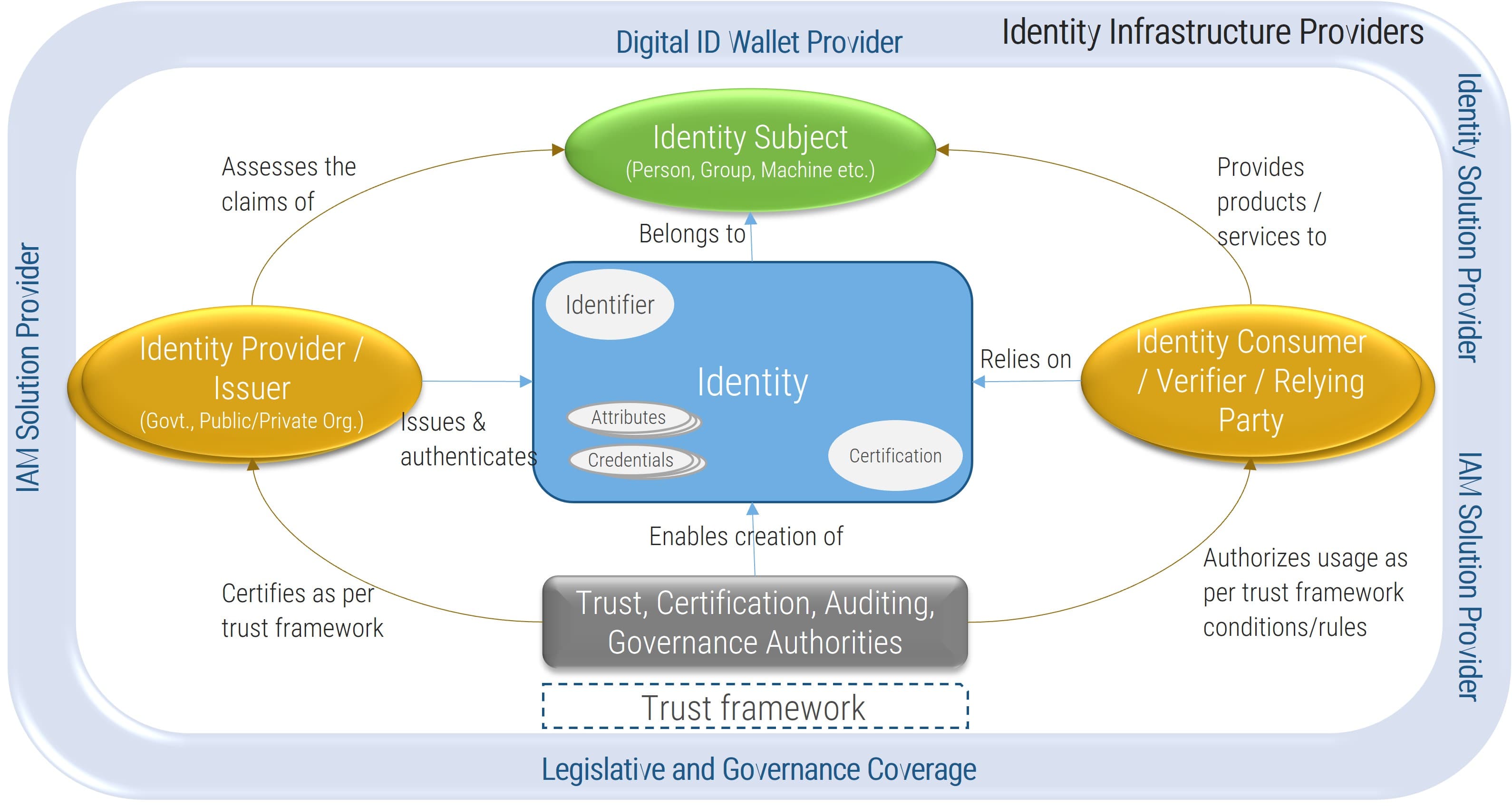
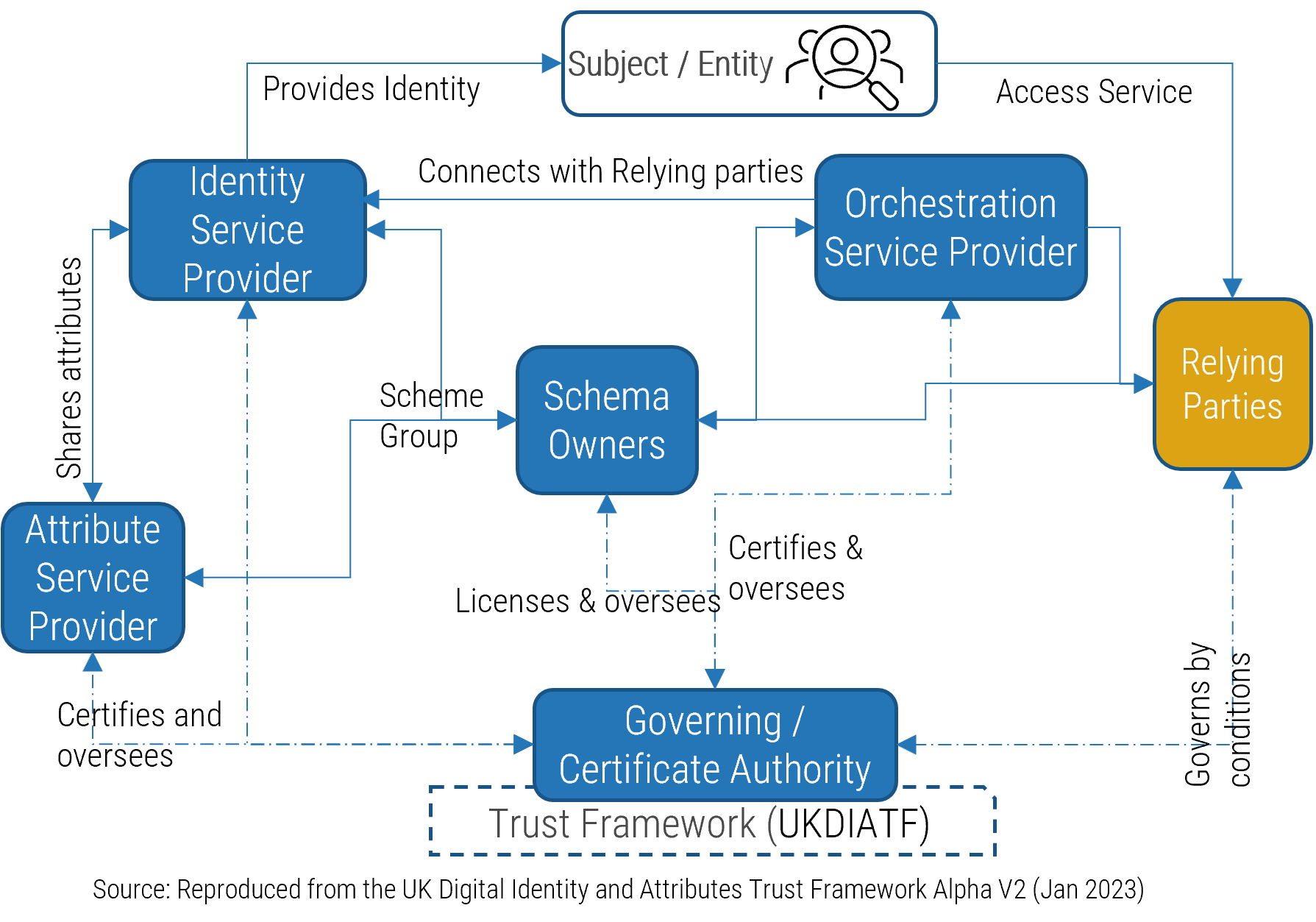
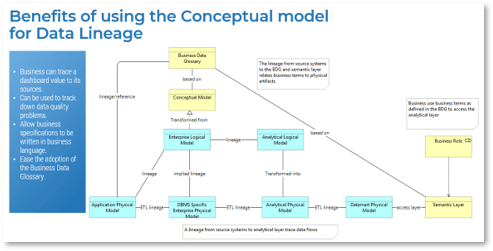
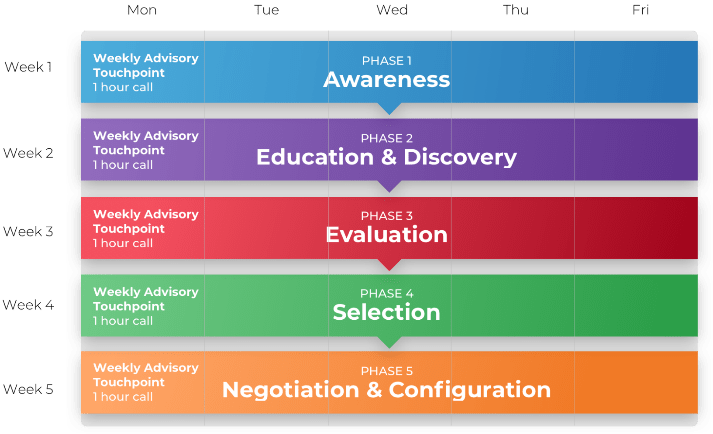
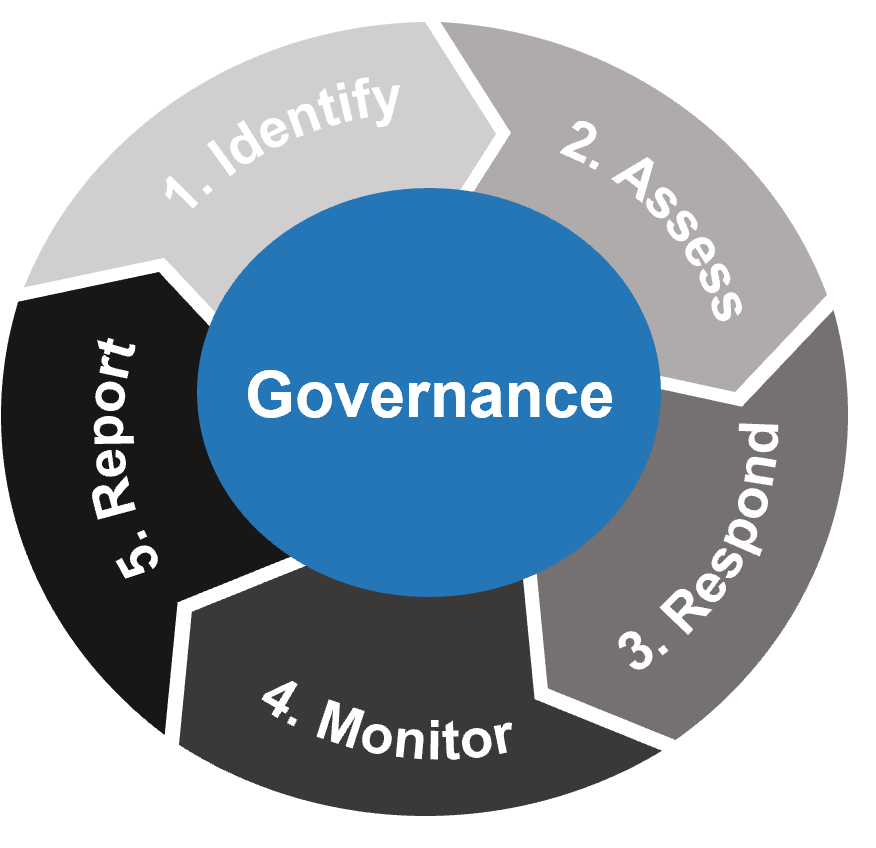
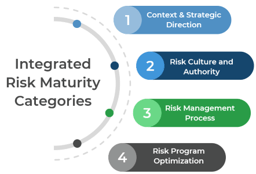
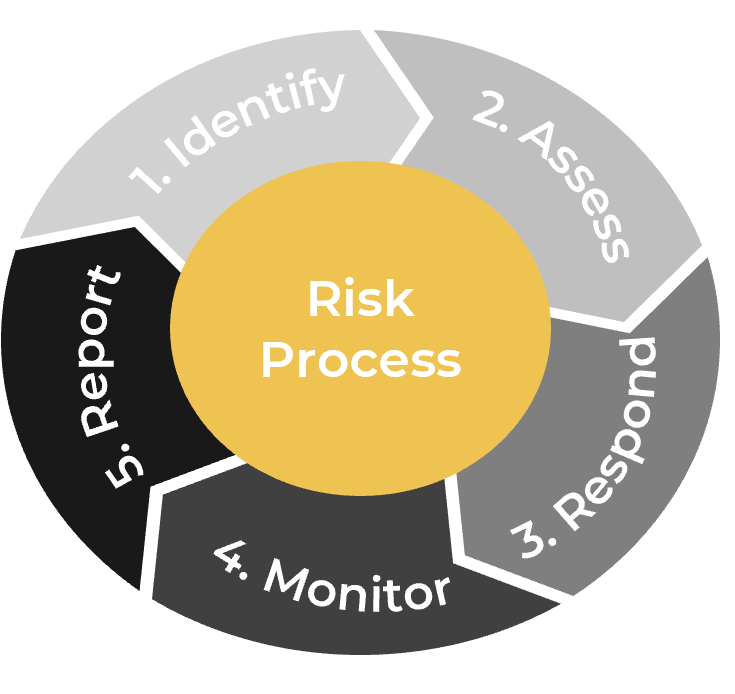
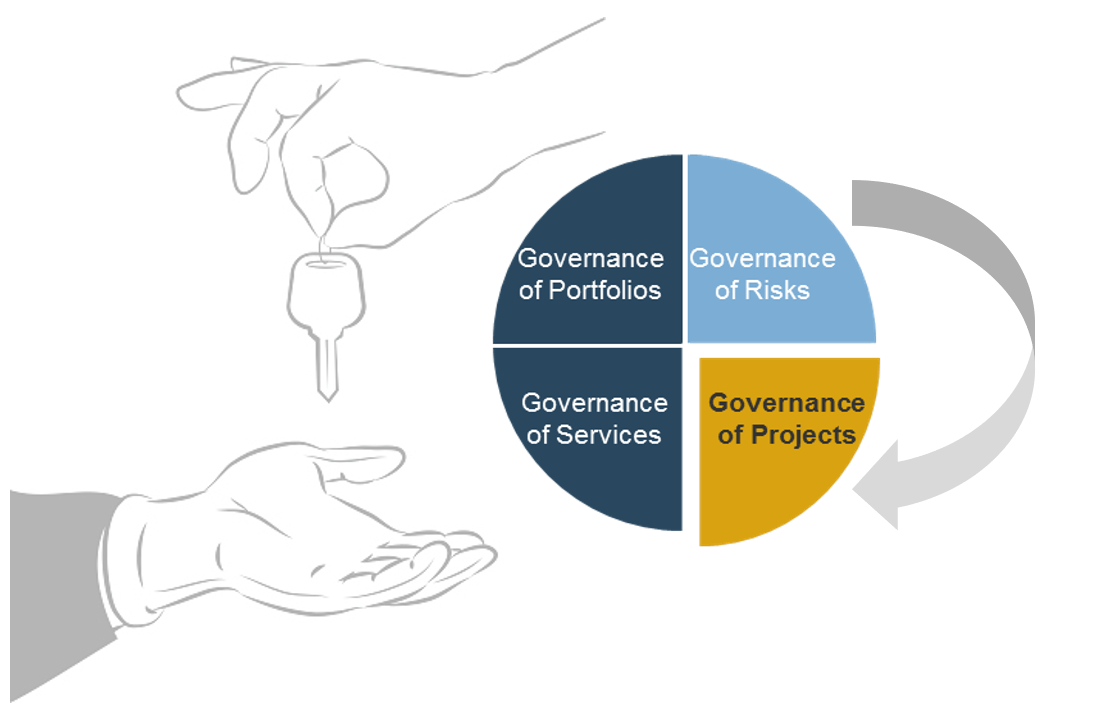
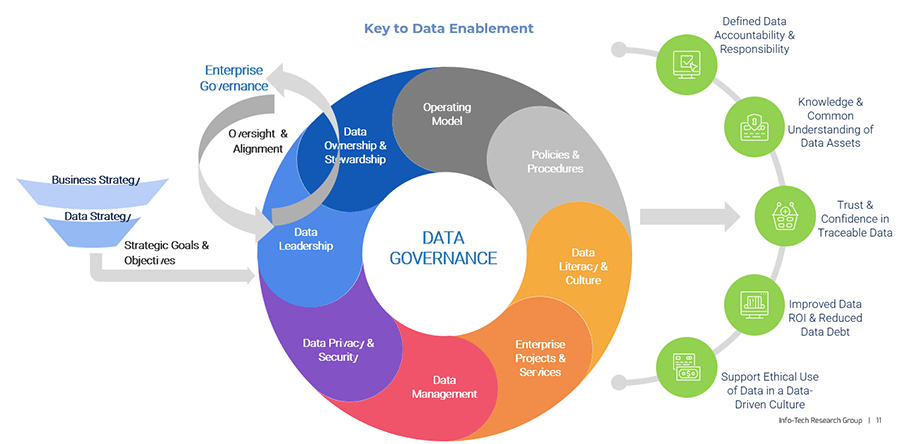
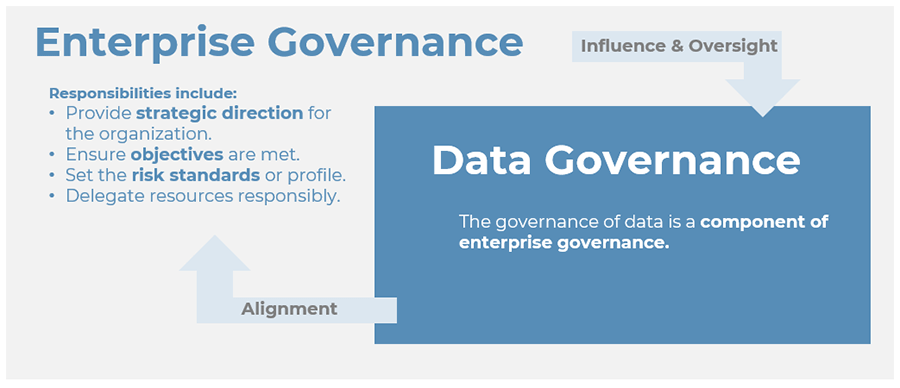
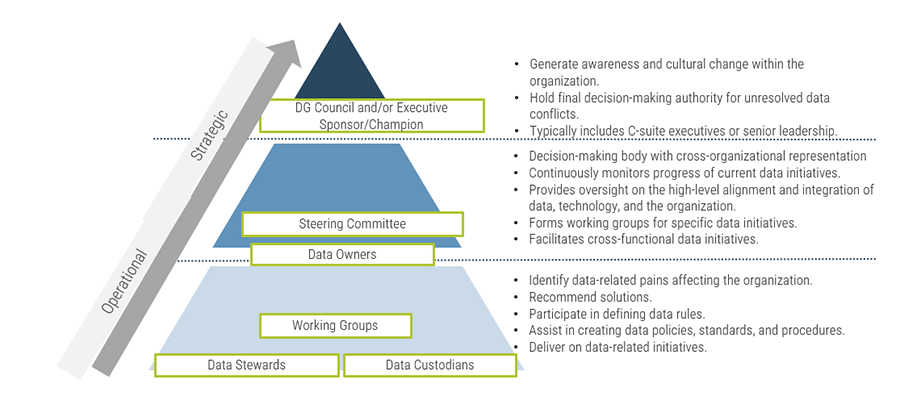
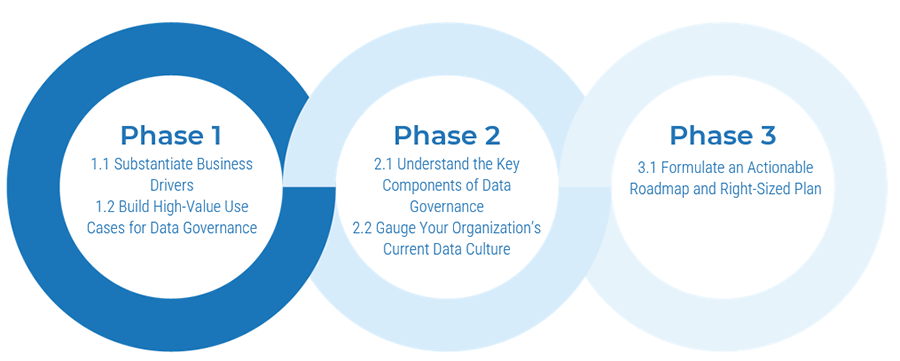
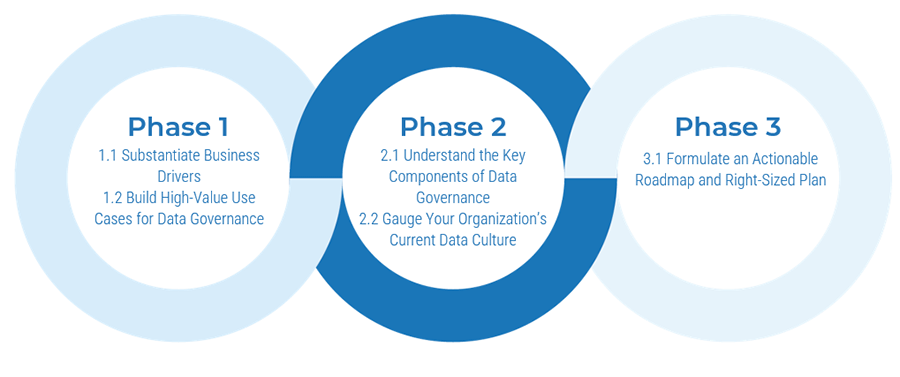
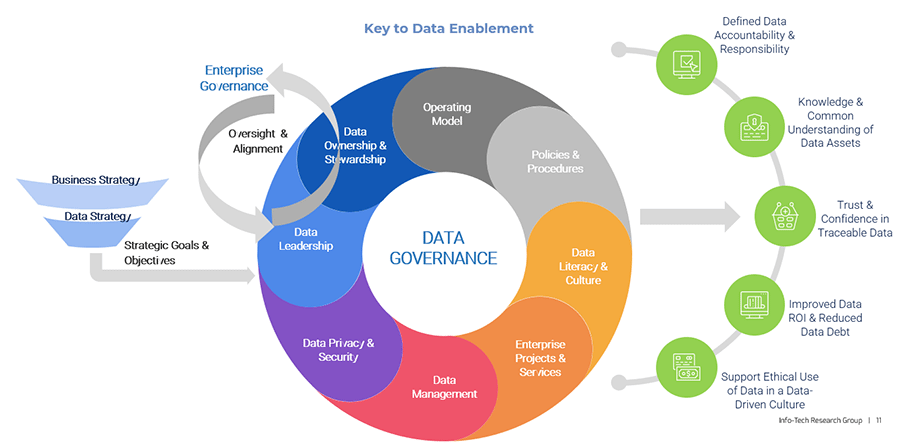
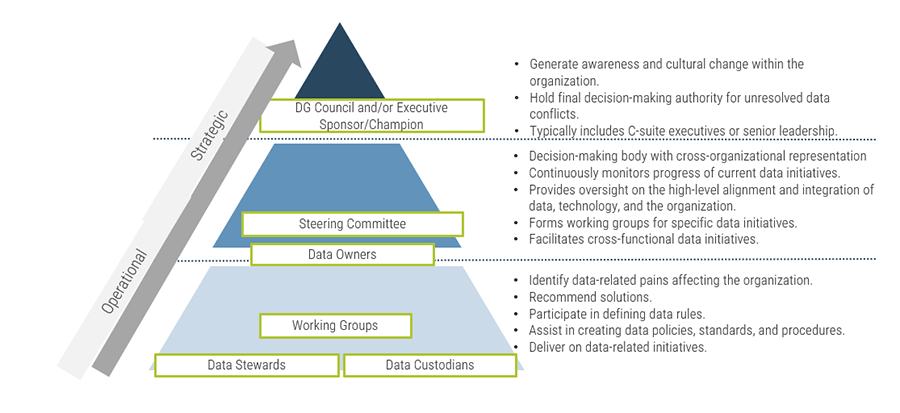
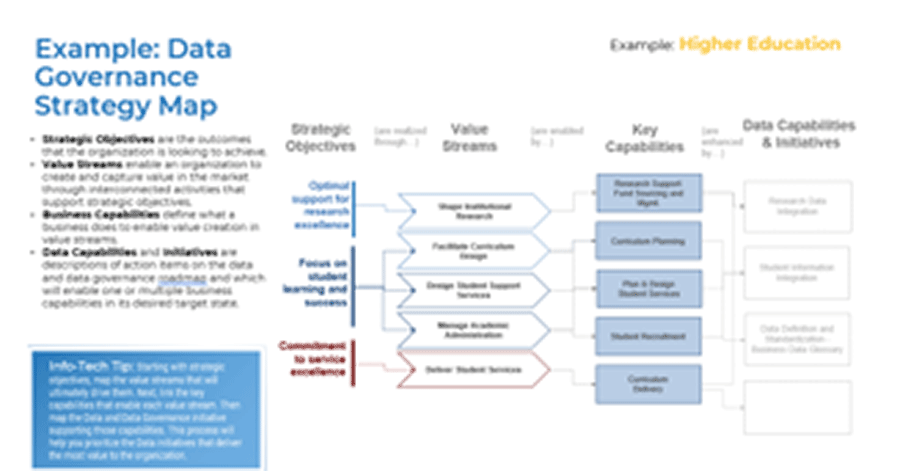
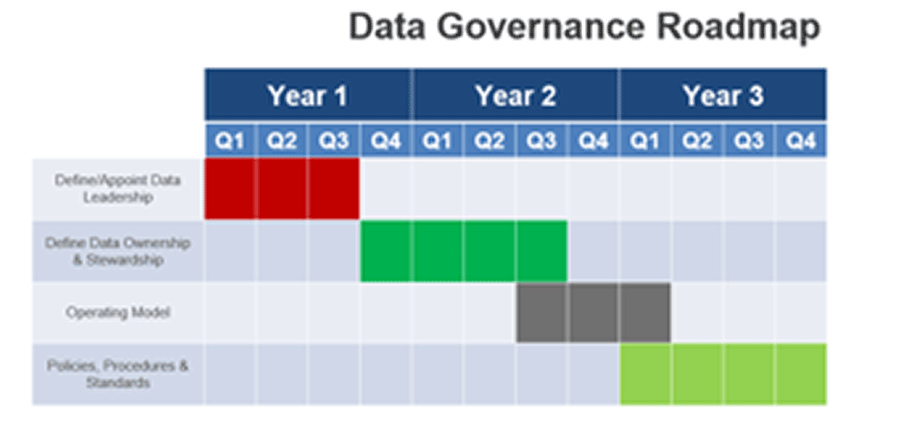
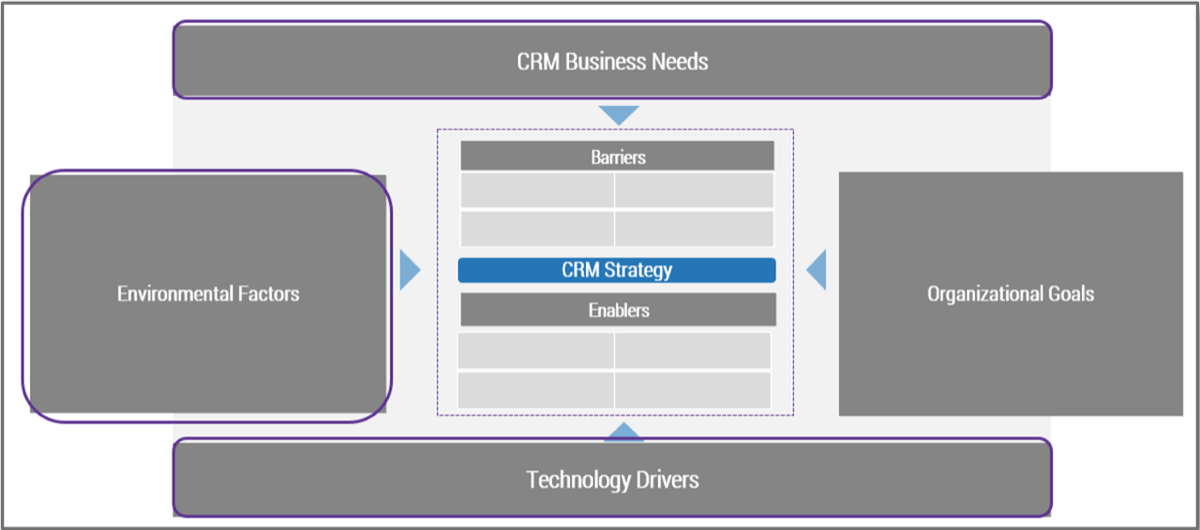
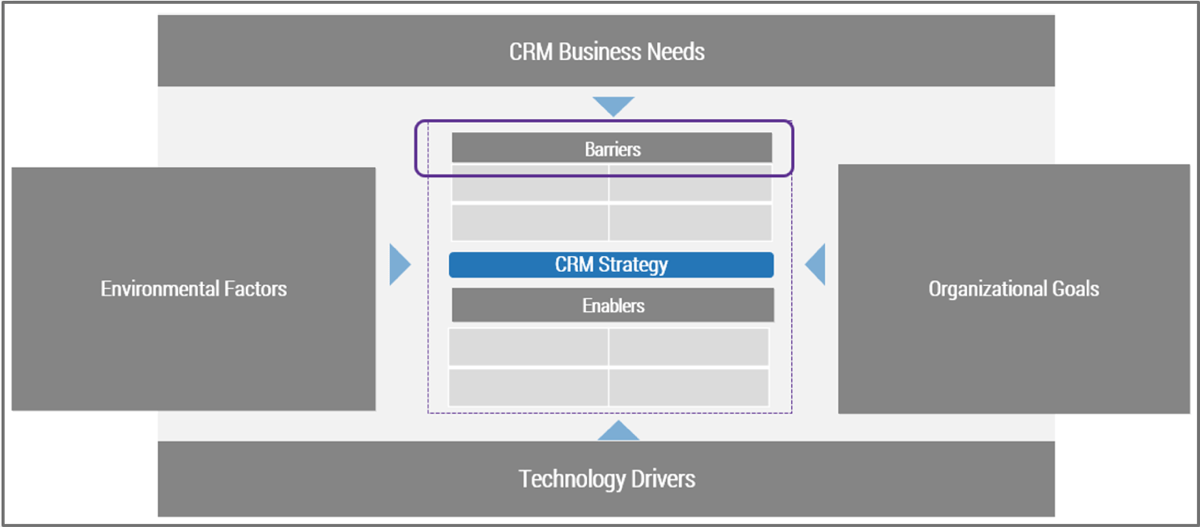
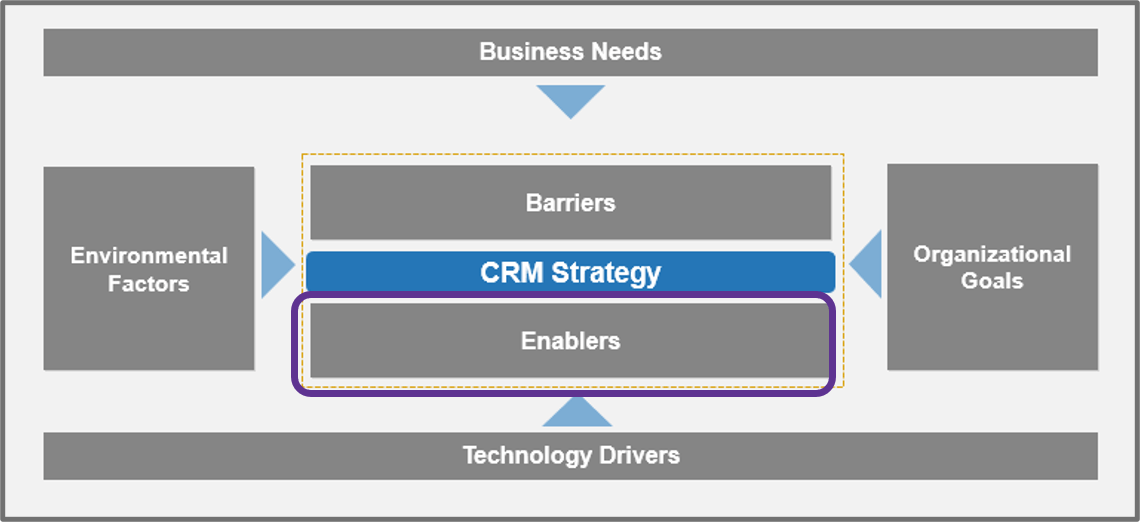
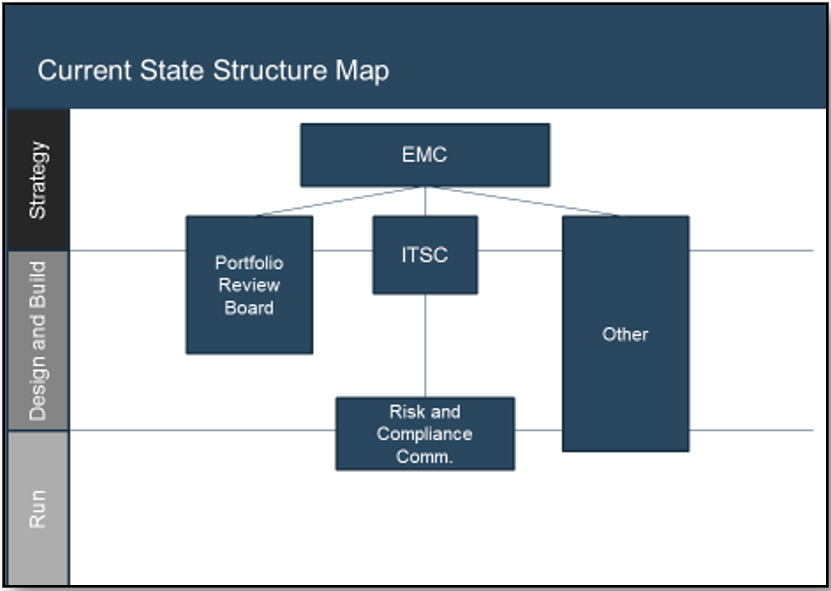 Using the outline provided, create your own governance structure map to represent the way the governing bodies interact and feed into each other.
This is crucial to ensure that the governing structure is streamlined. It will ensure that communication occurs efficiently and that there are no barriers to making decisions swiftly.
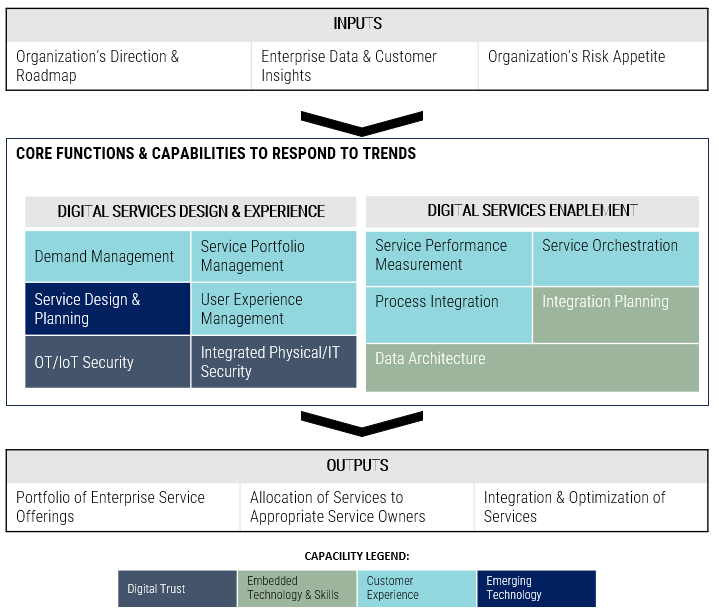
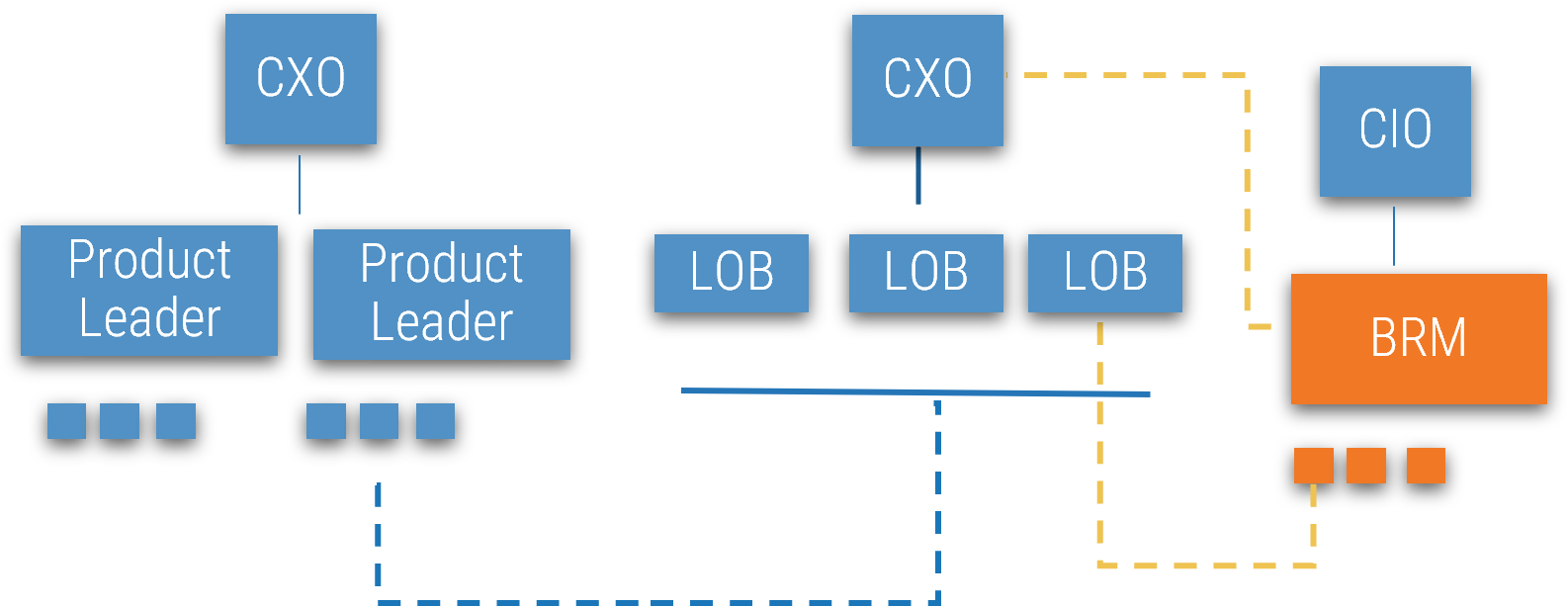
Using the outline provided, create your own governance structure map to represent the way the governing bodies interact and feed into each other.
This is crucial to ensure that the governing structure is streamlined. It will ensure that communication occurs efficiently and that there are no barriers to making decisions swiftly.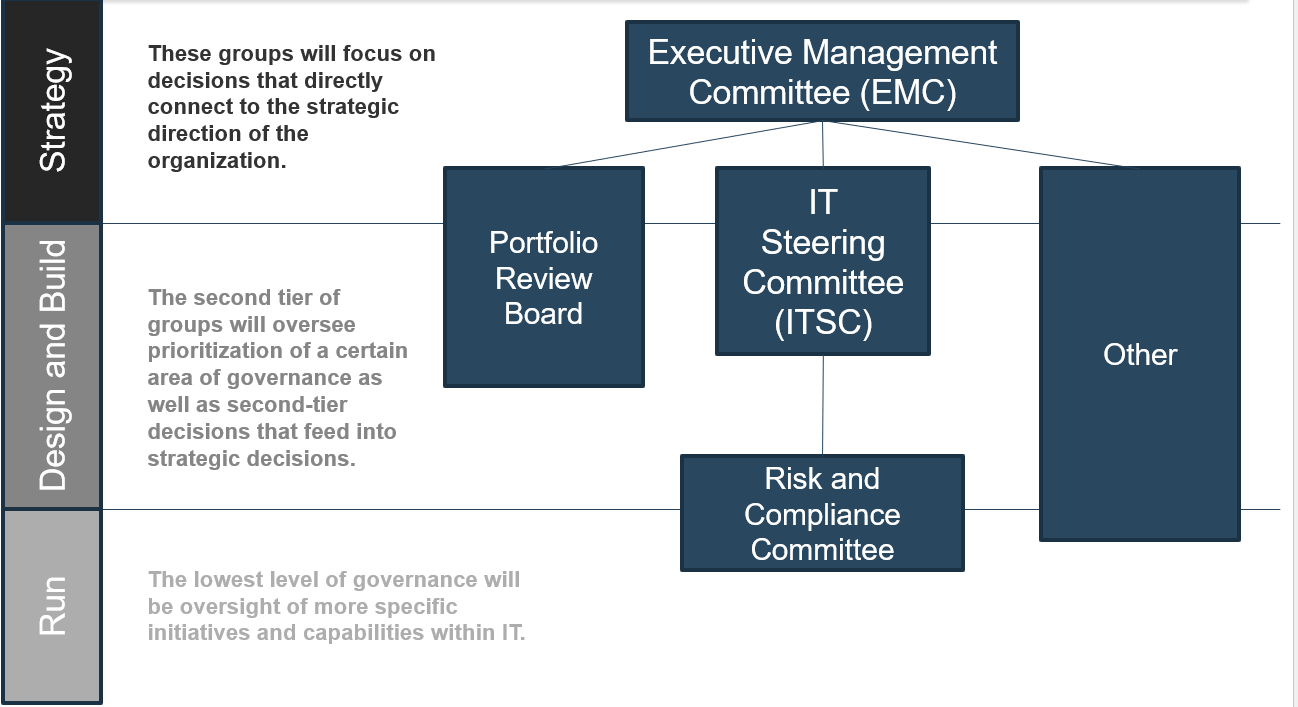
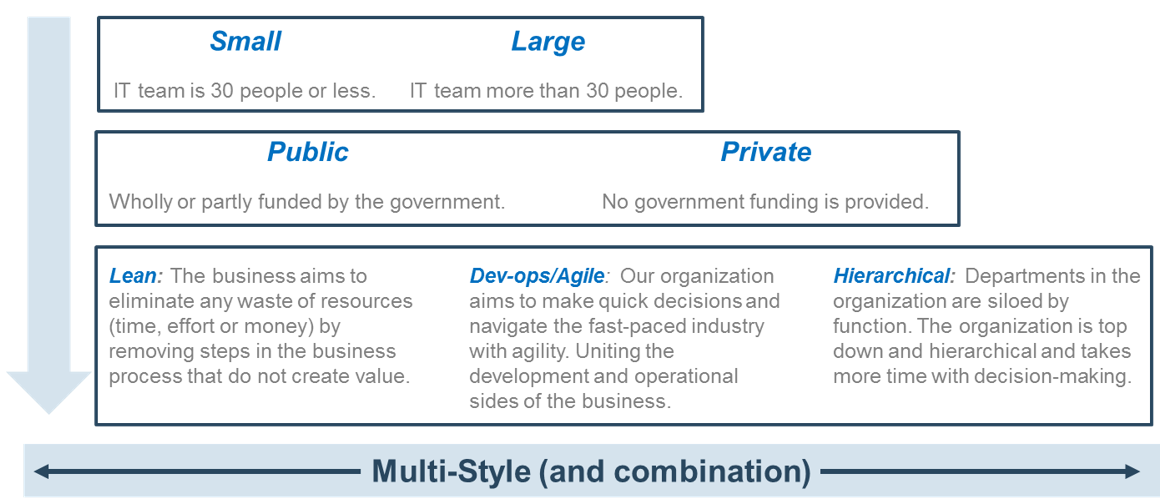
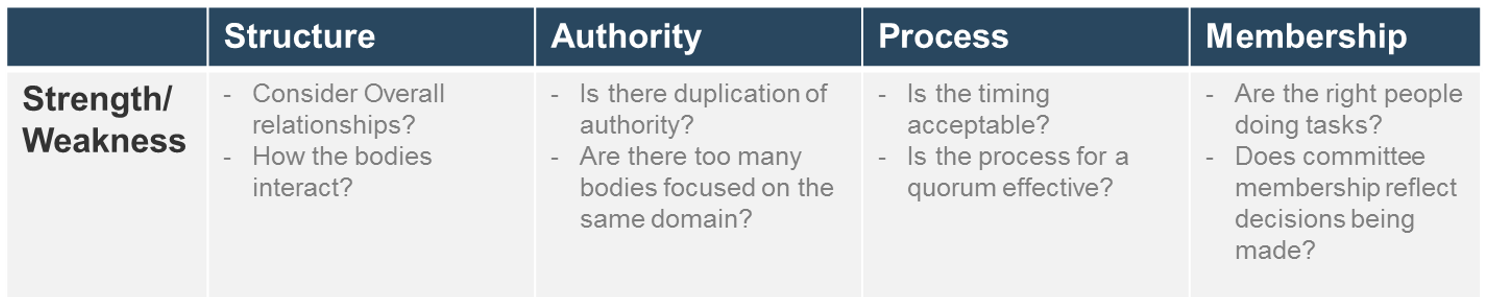
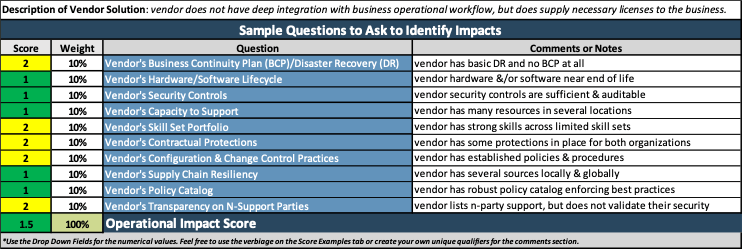
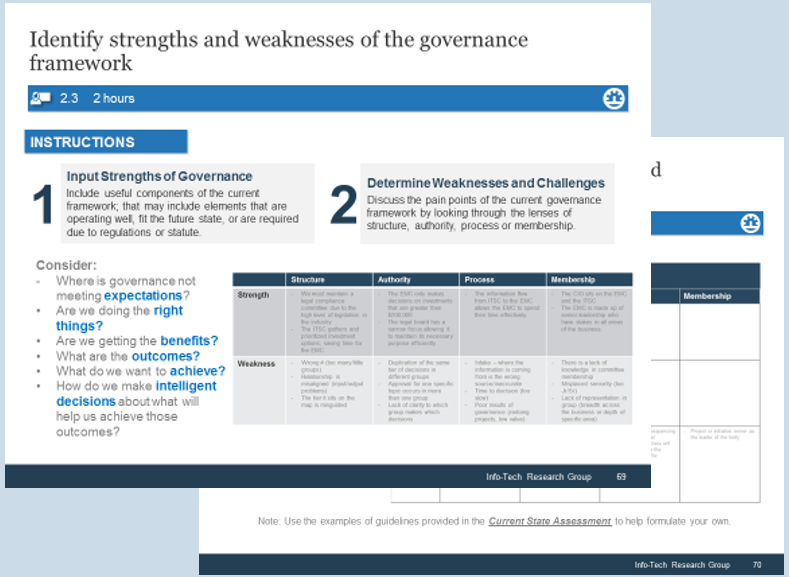
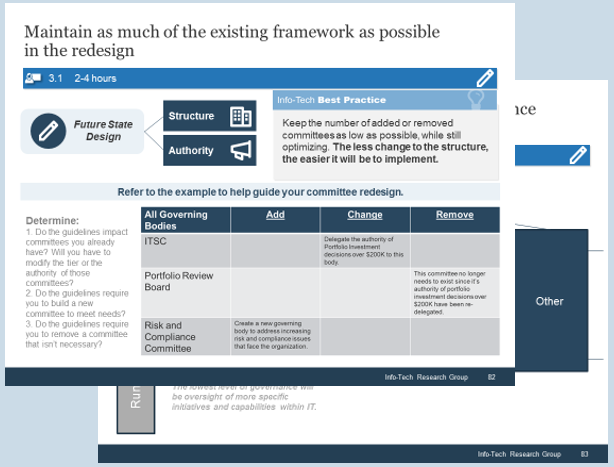
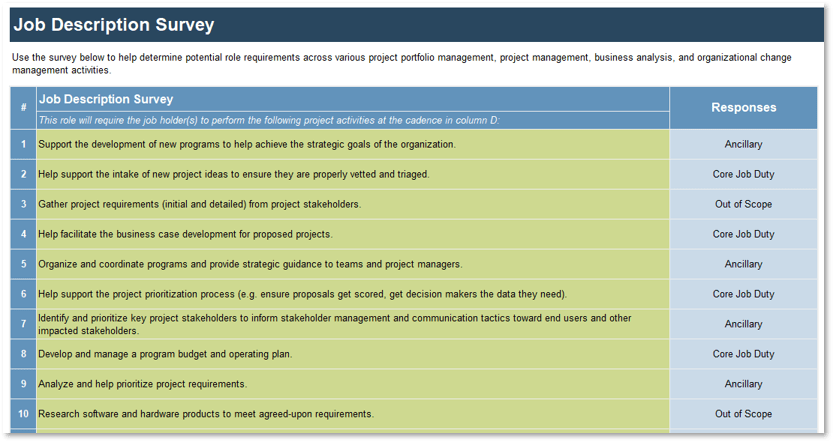
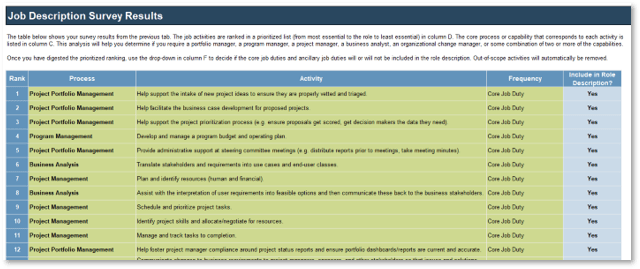
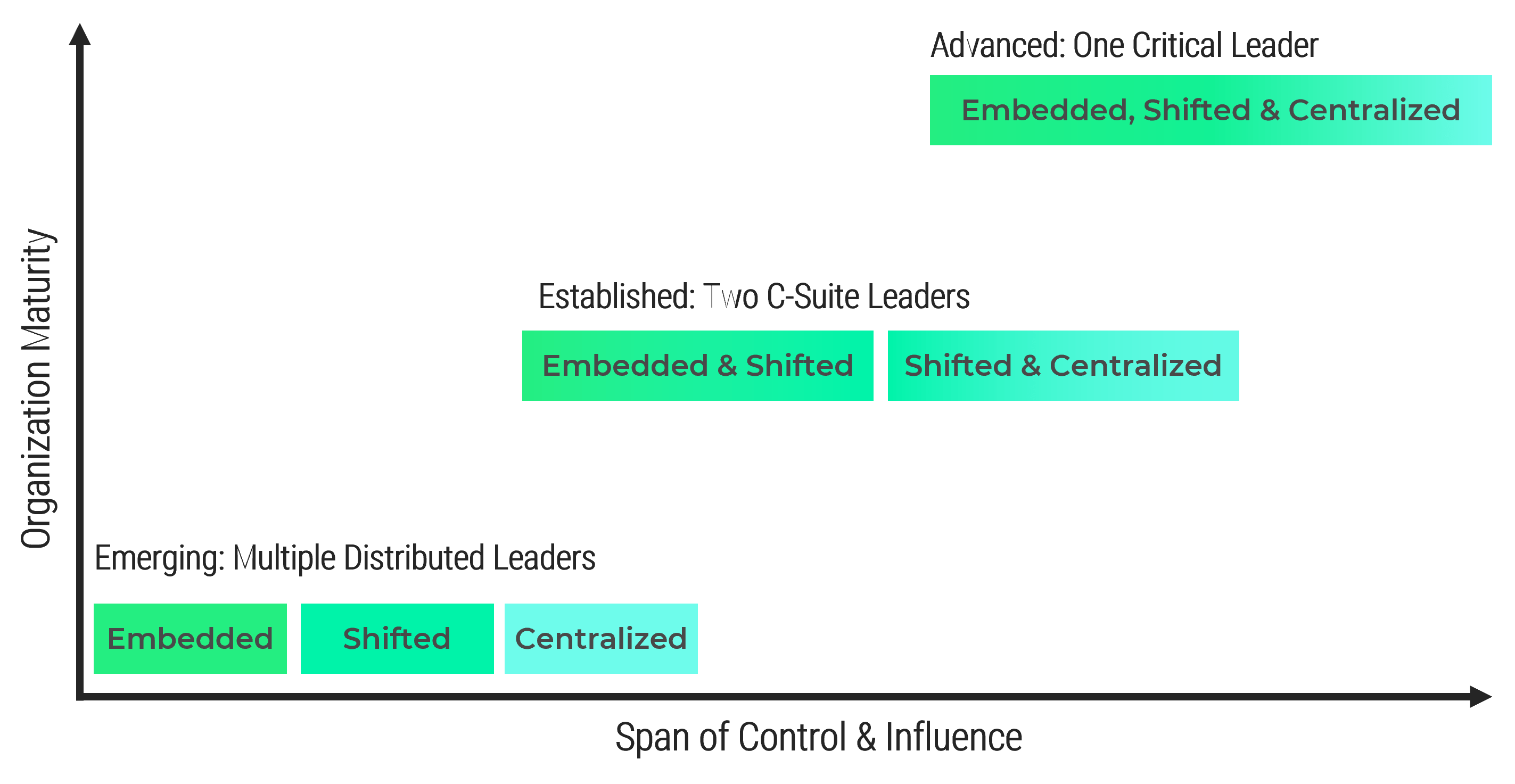
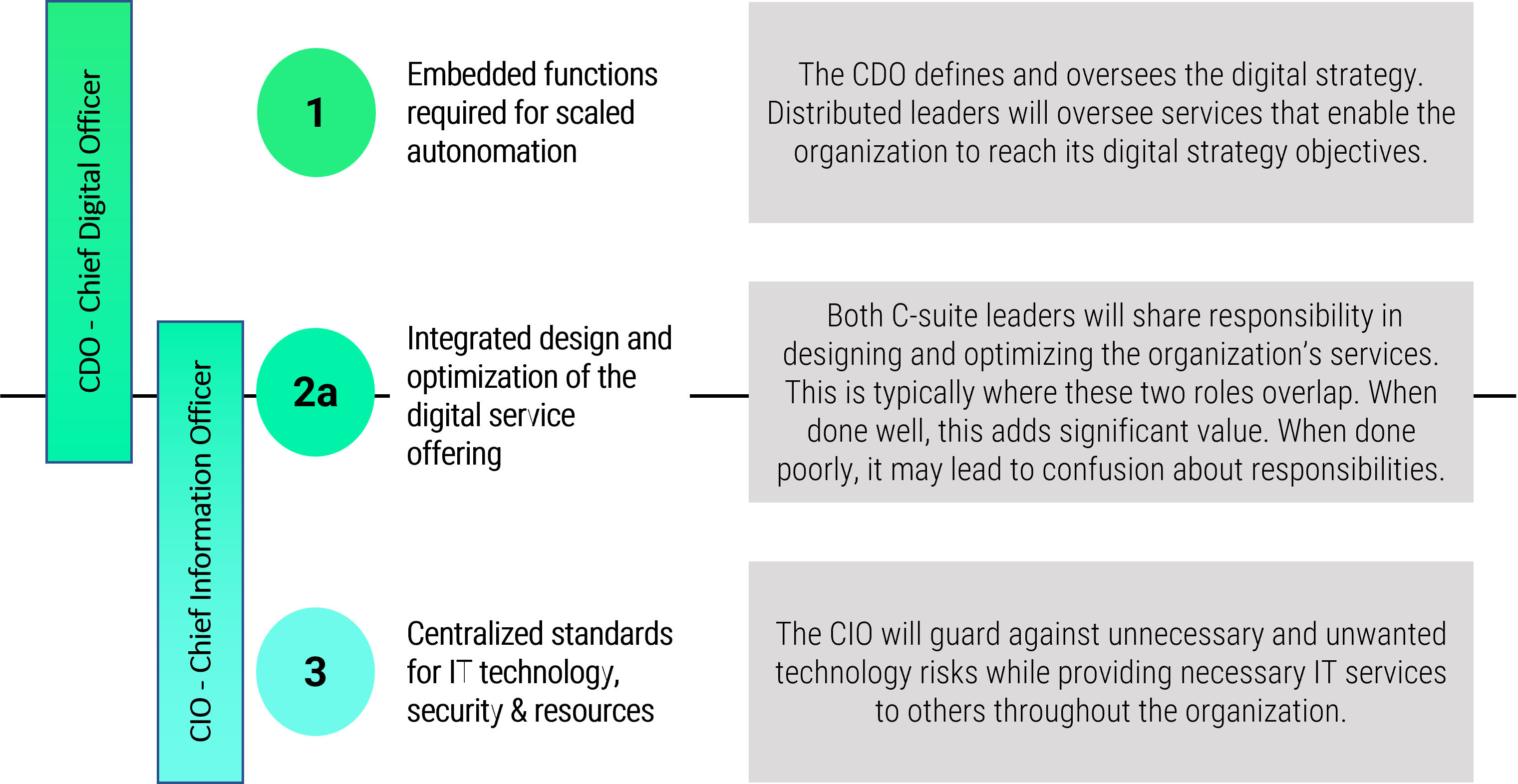
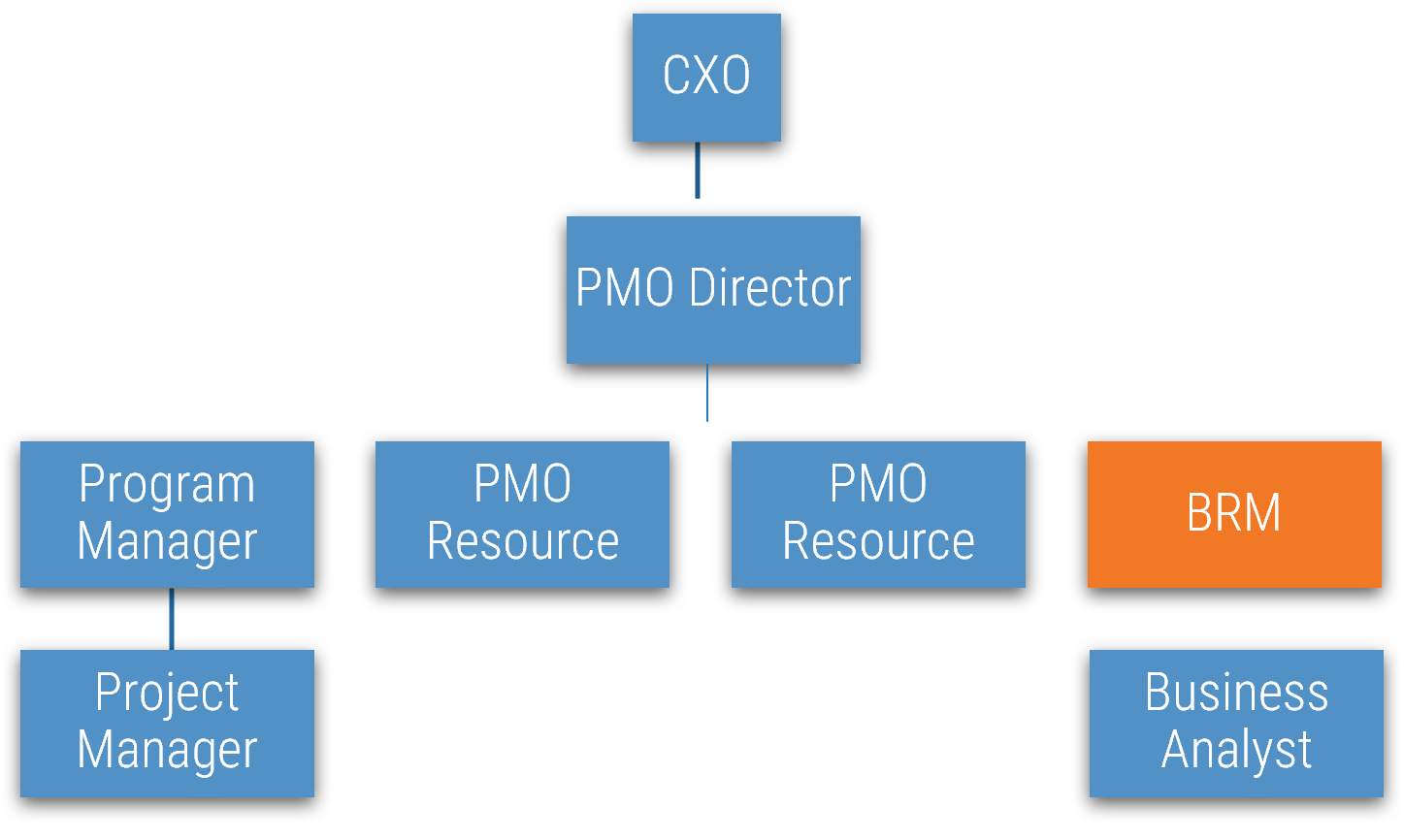
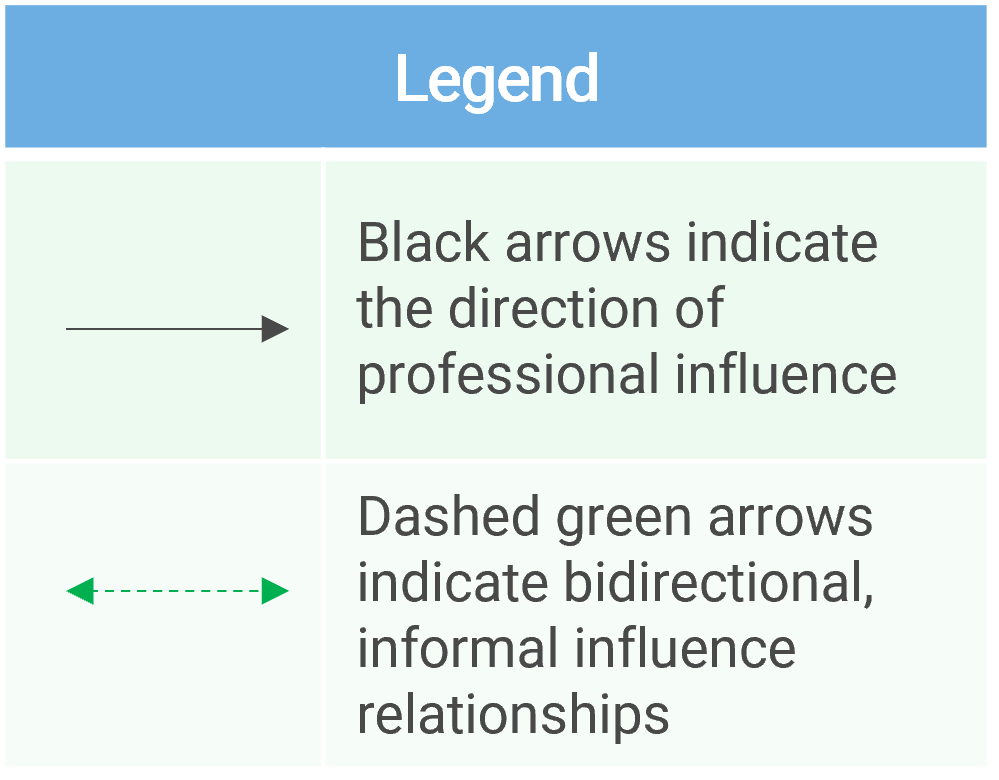
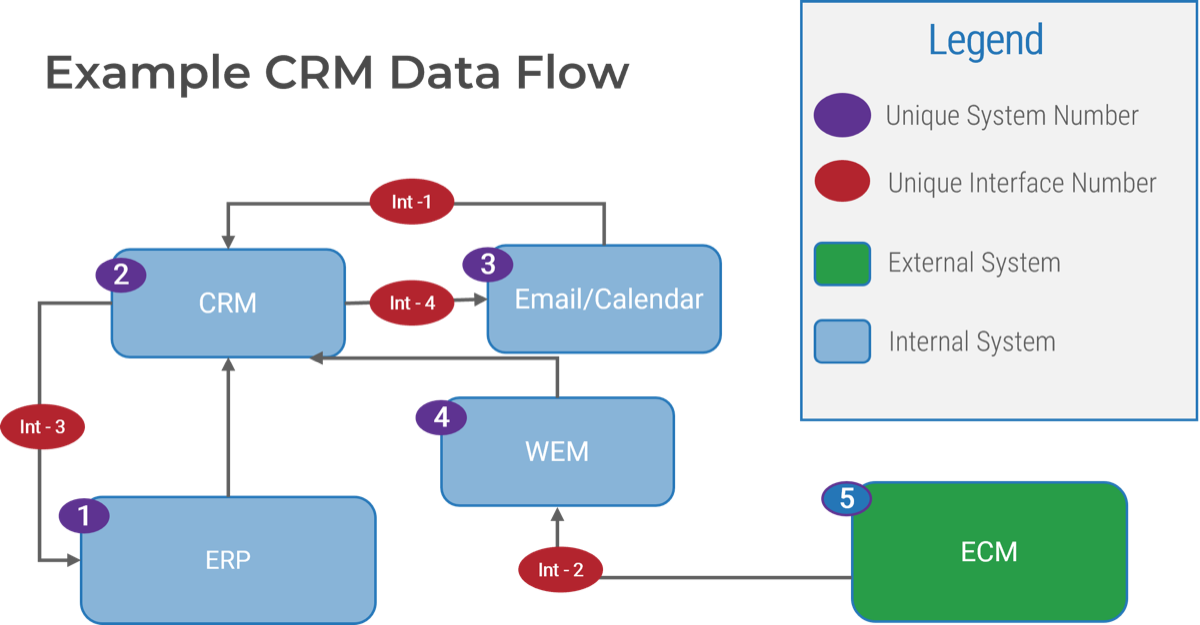
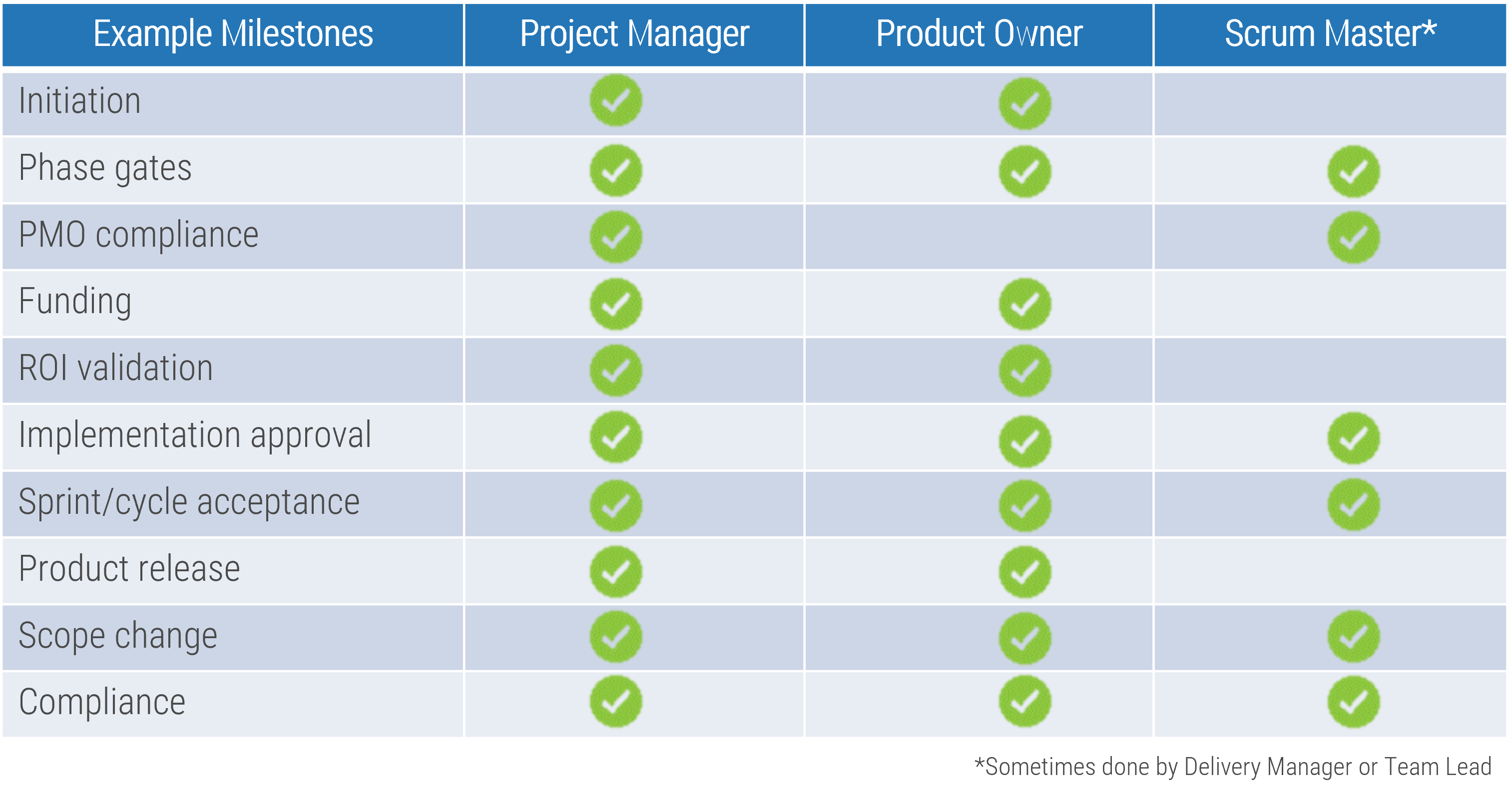
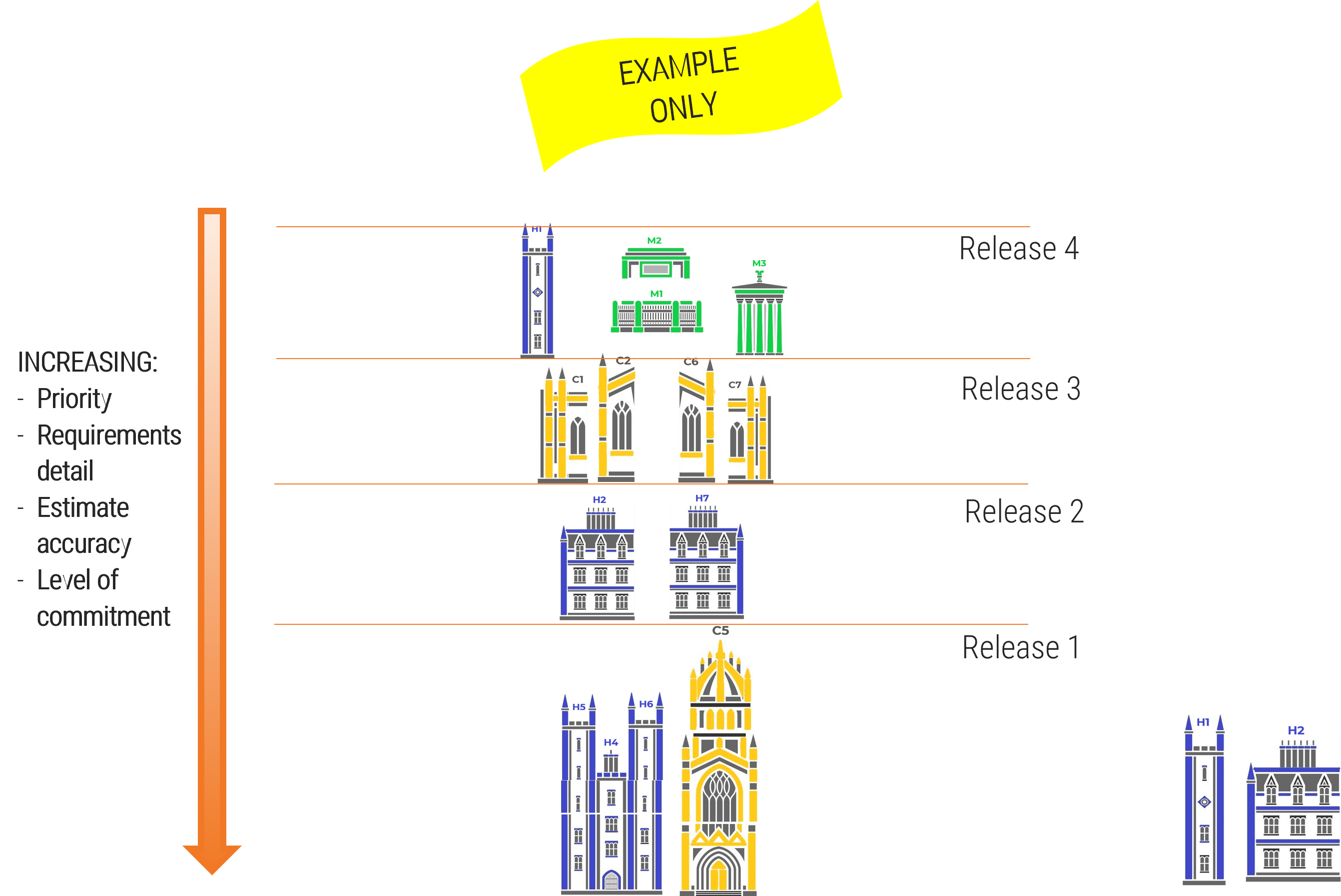
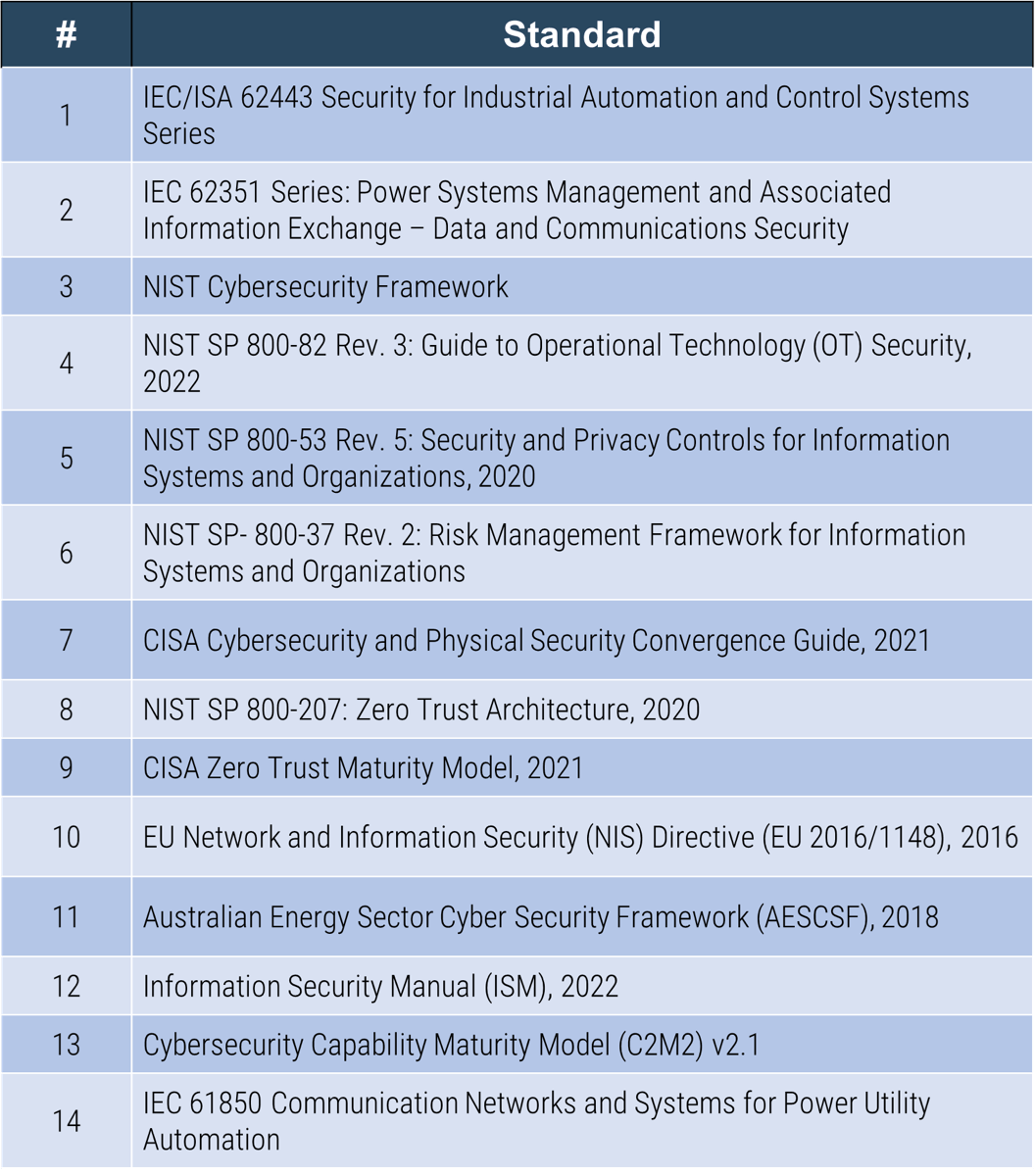
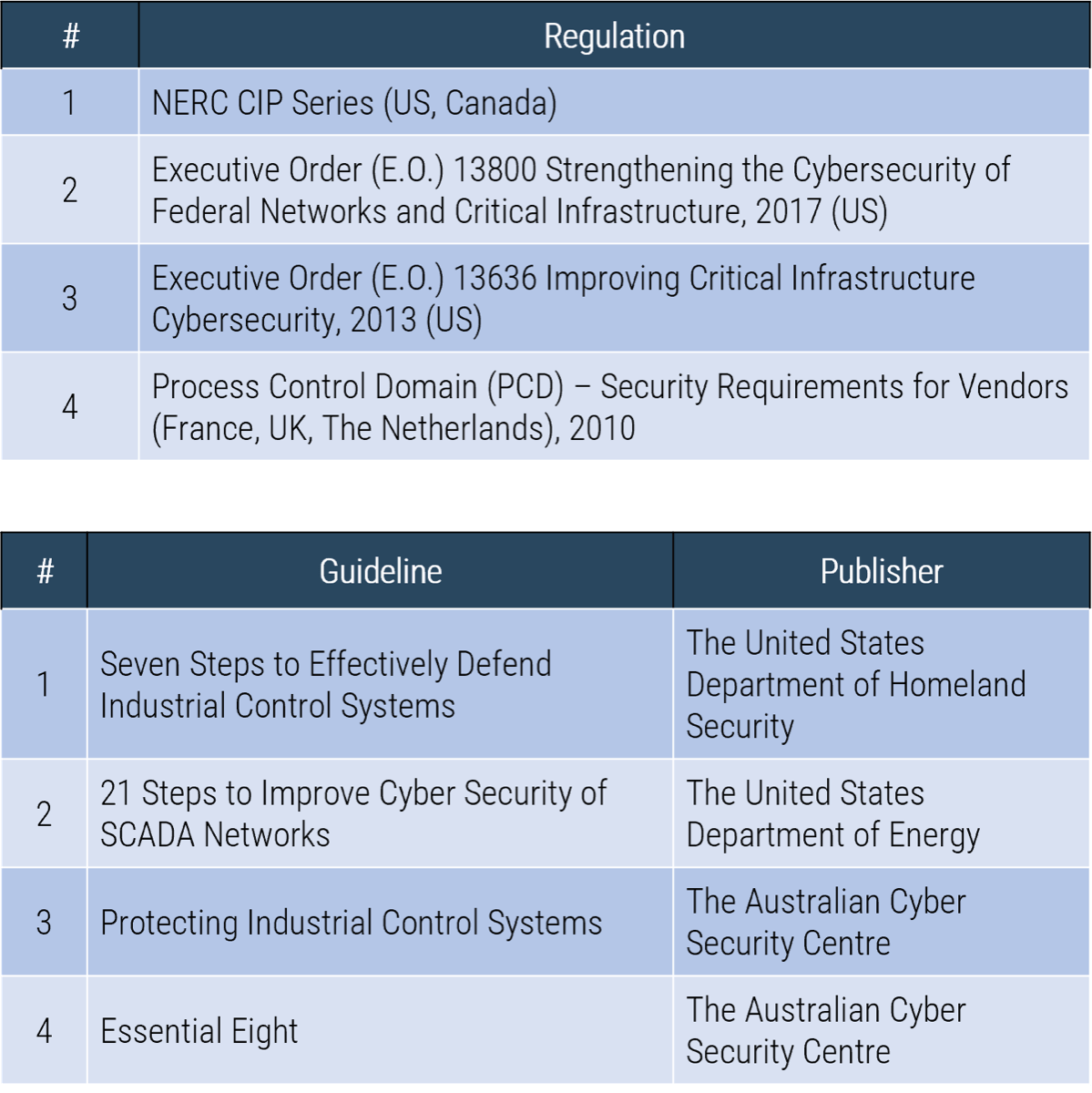
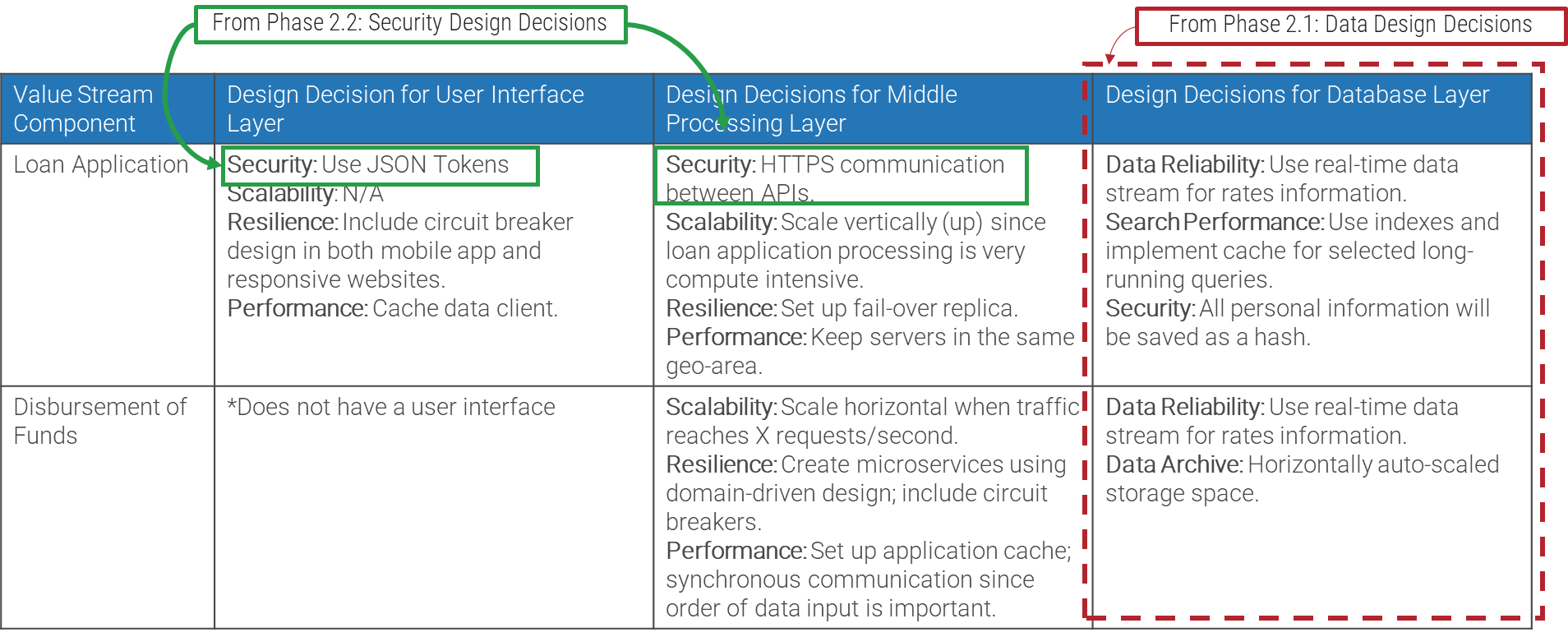
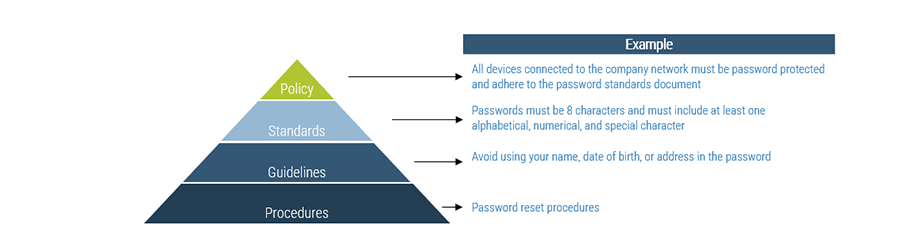
 Note: Refer to the example guidelines in the
Note: Refer to the example guidelines in the 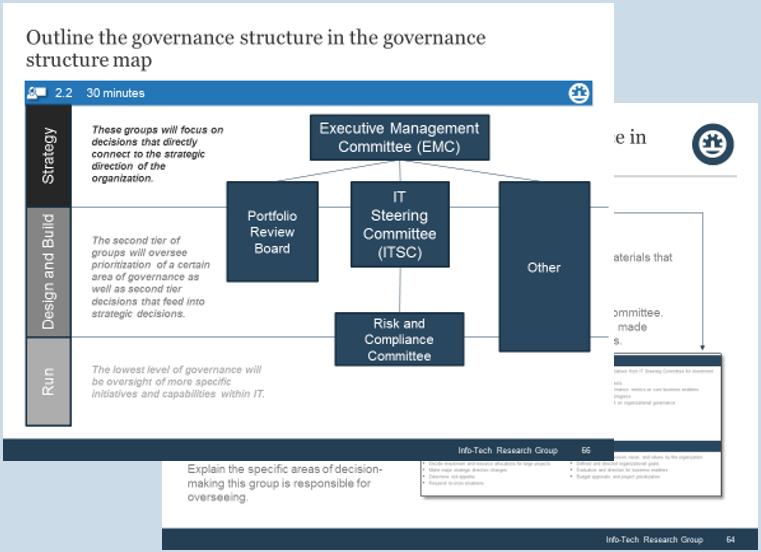





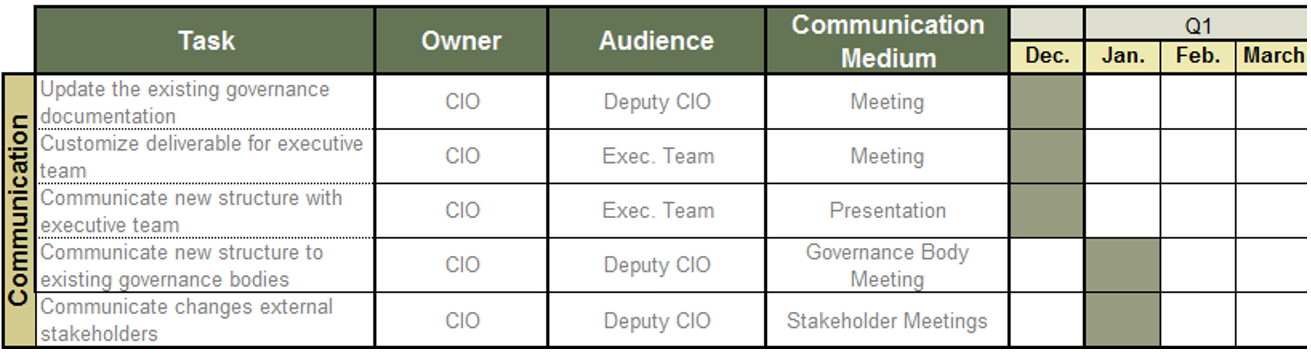








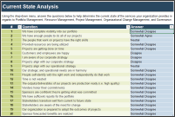












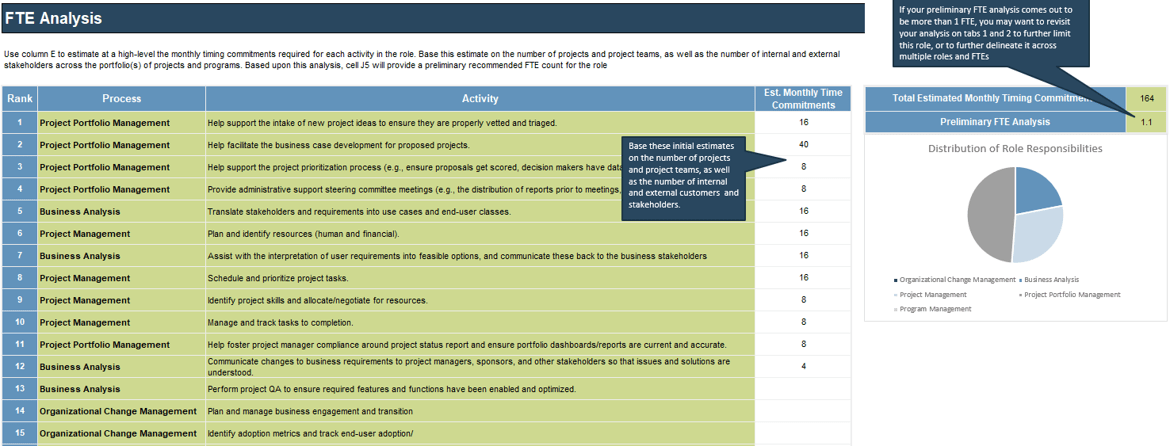
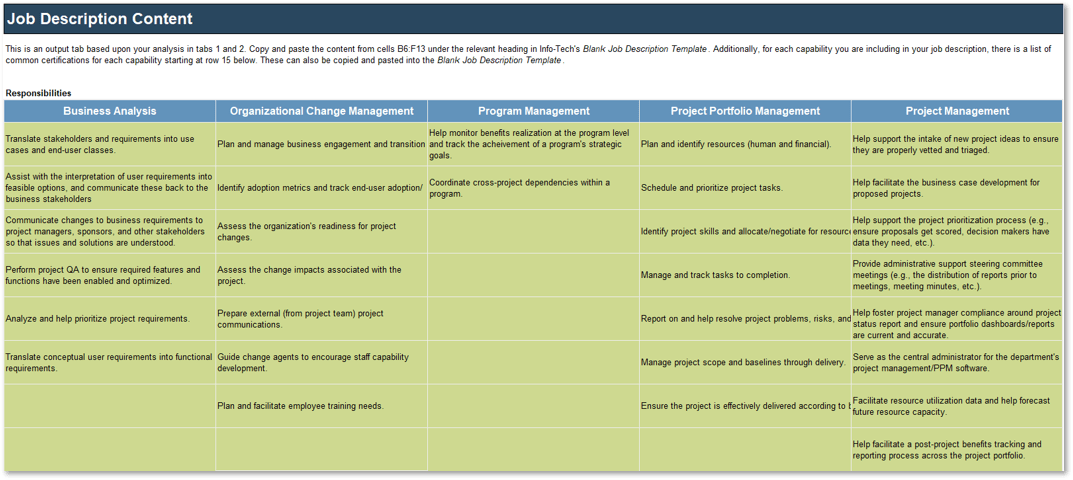
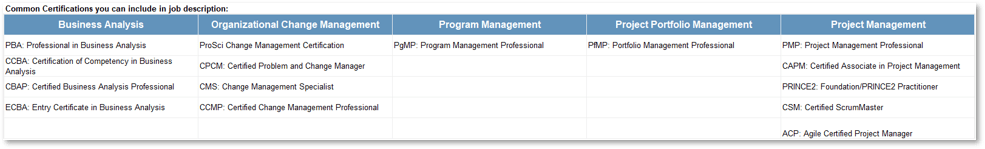








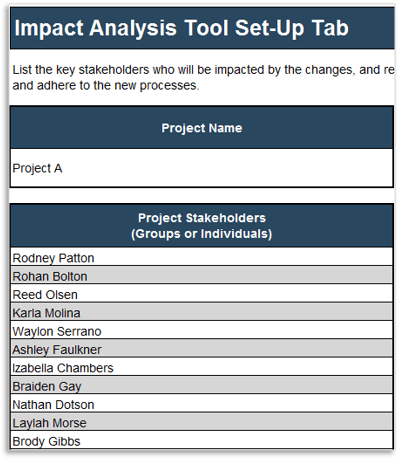
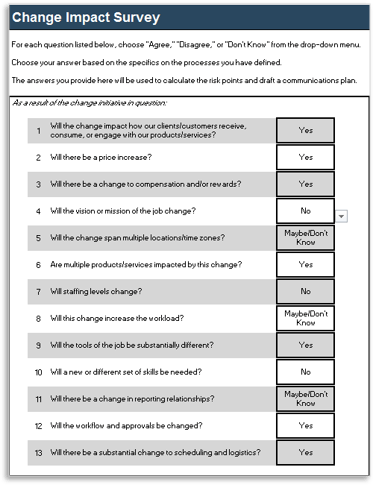
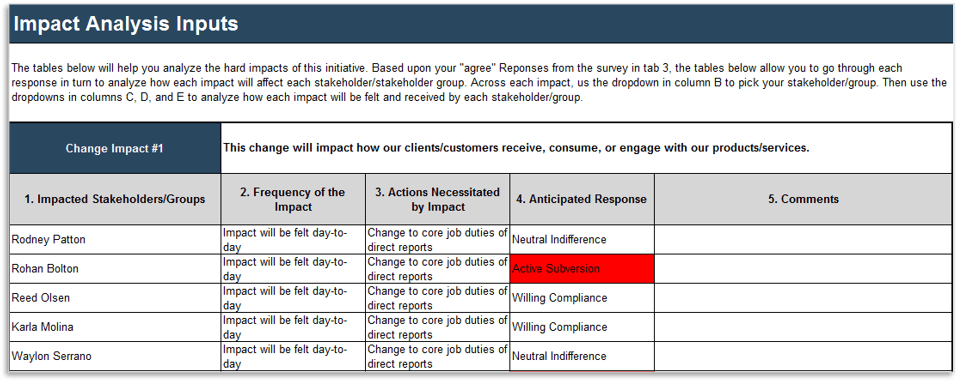
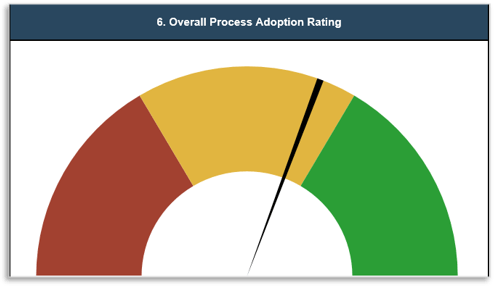










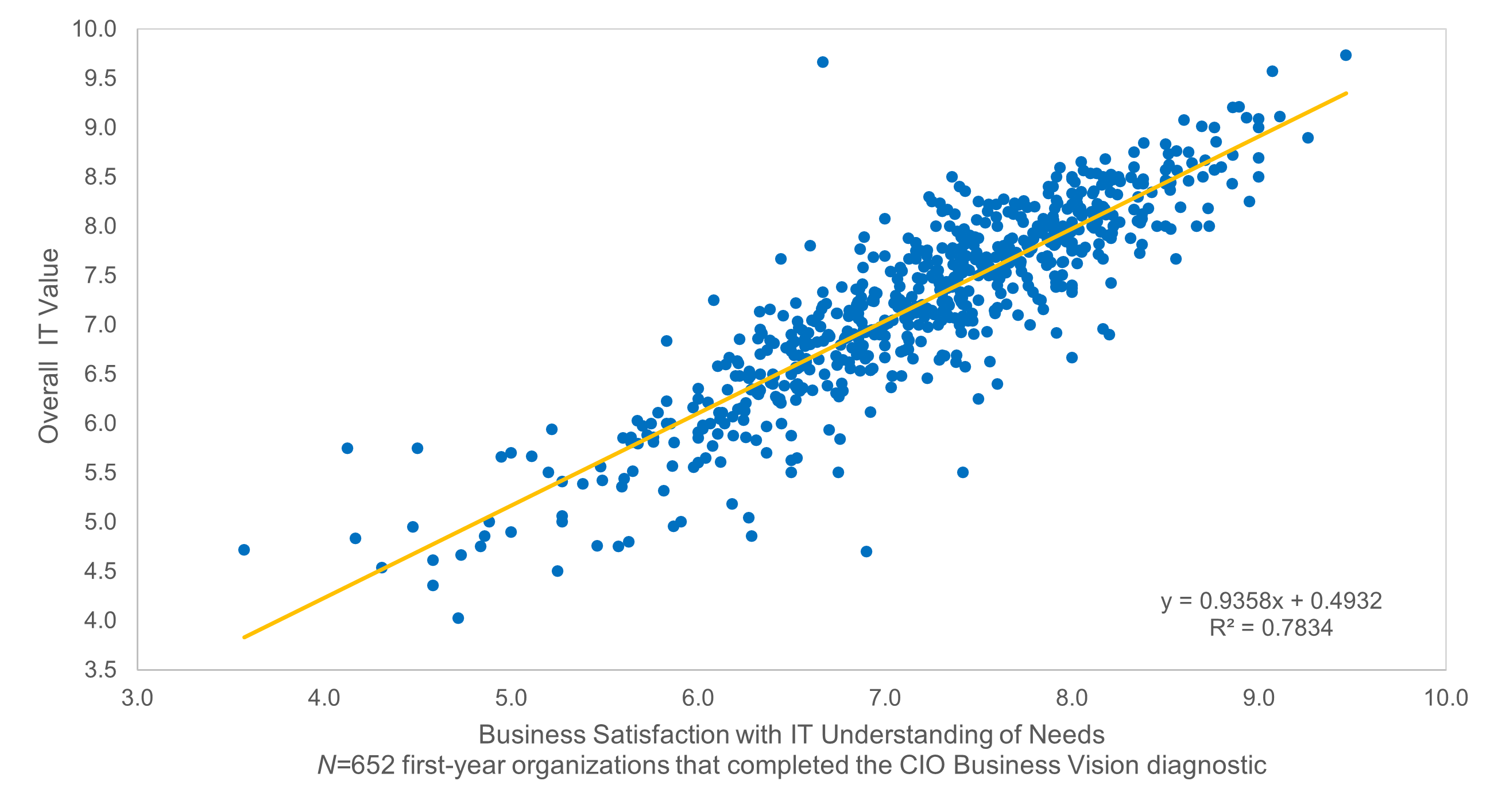
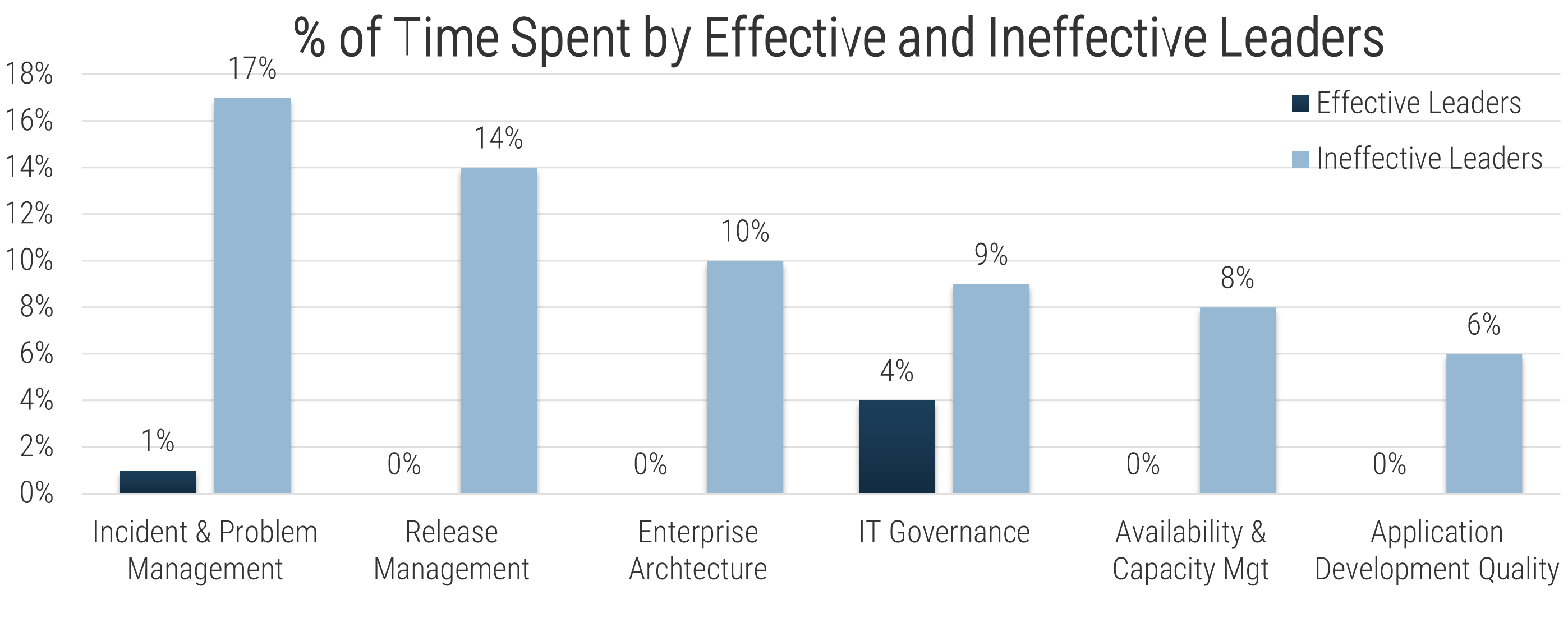
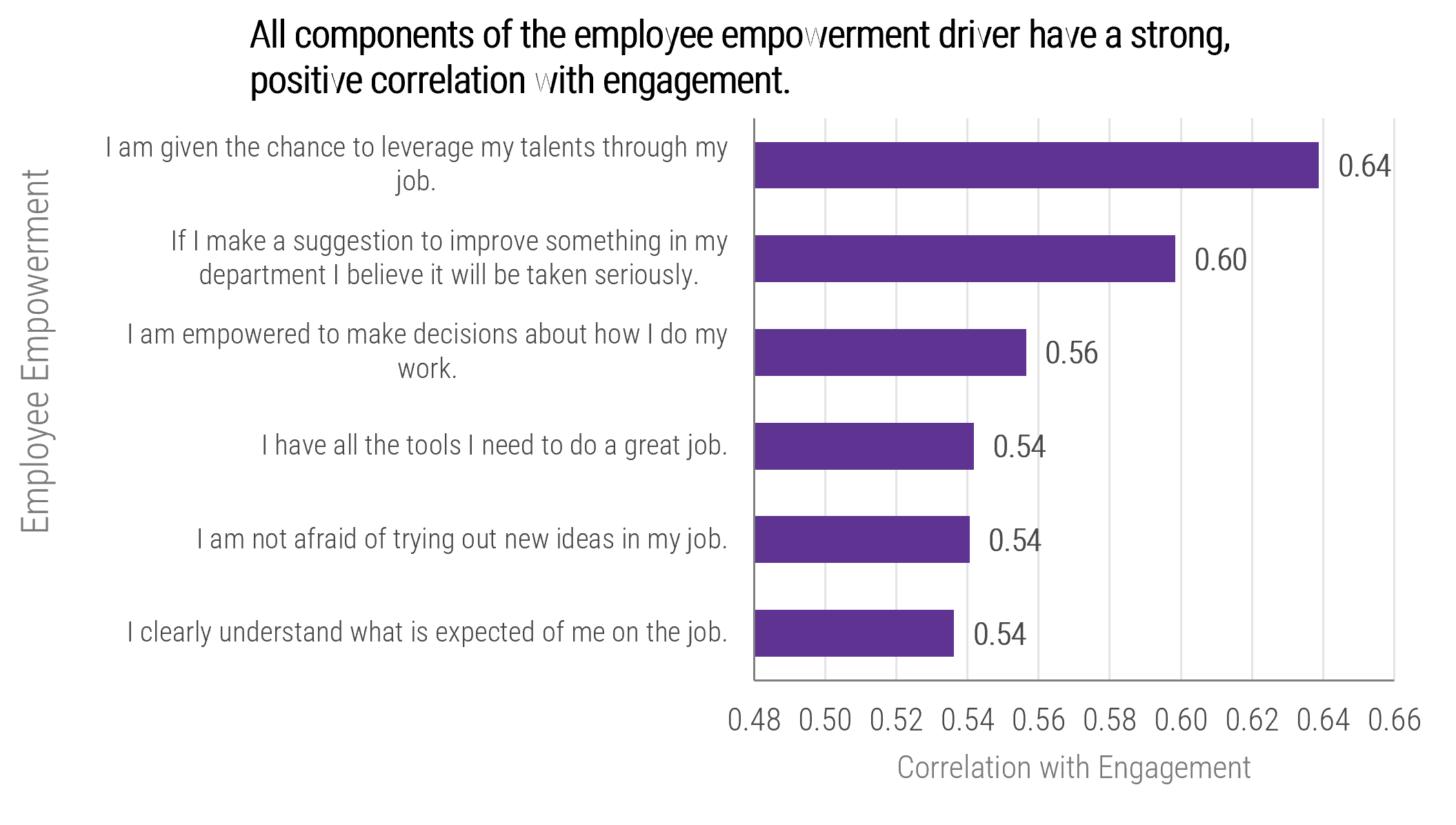



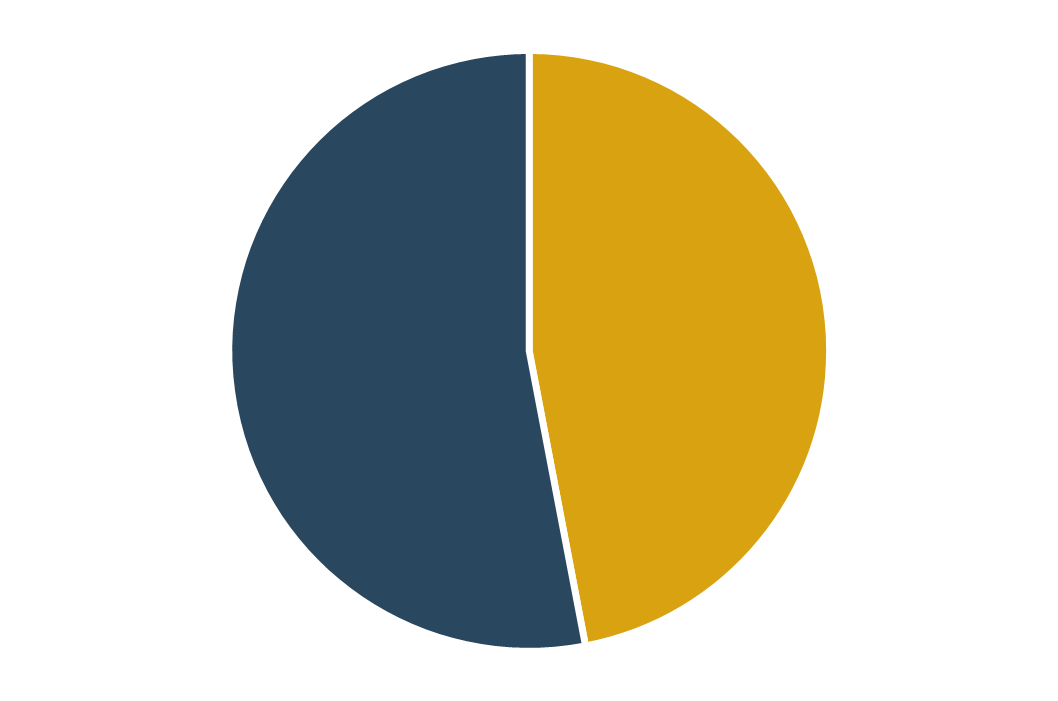
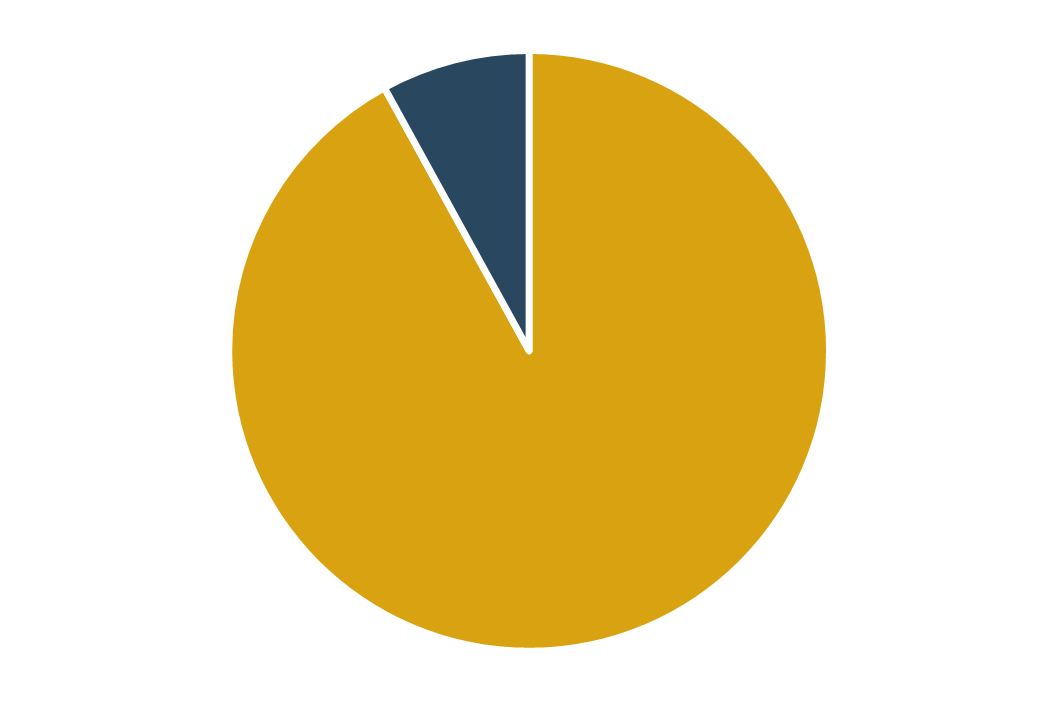
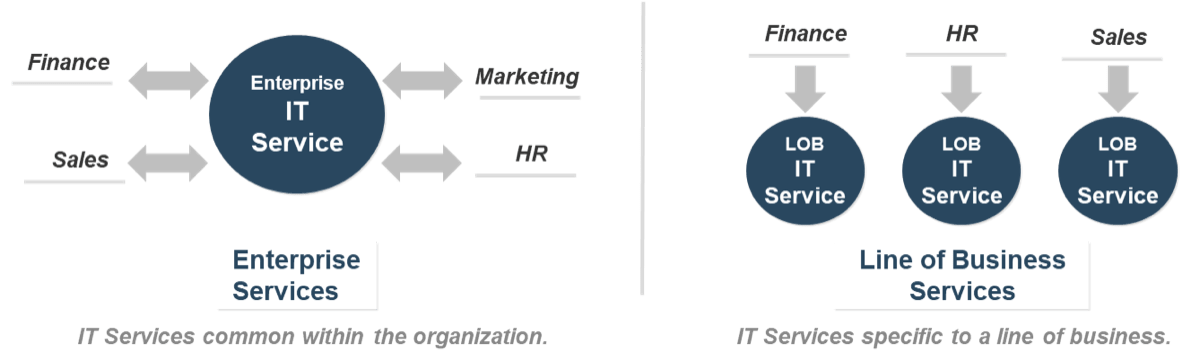
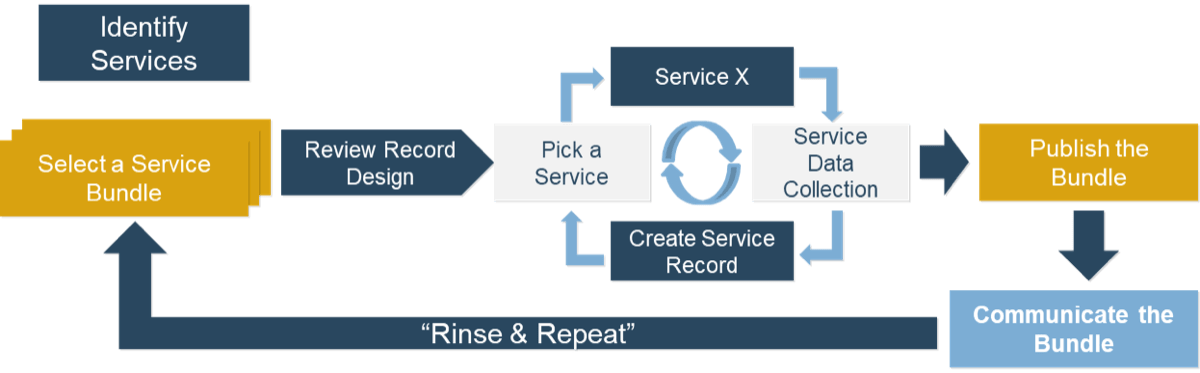

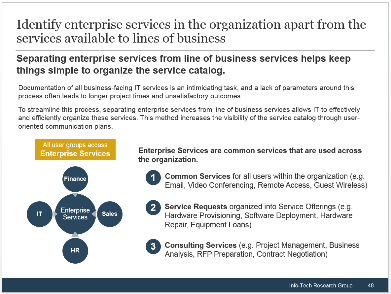

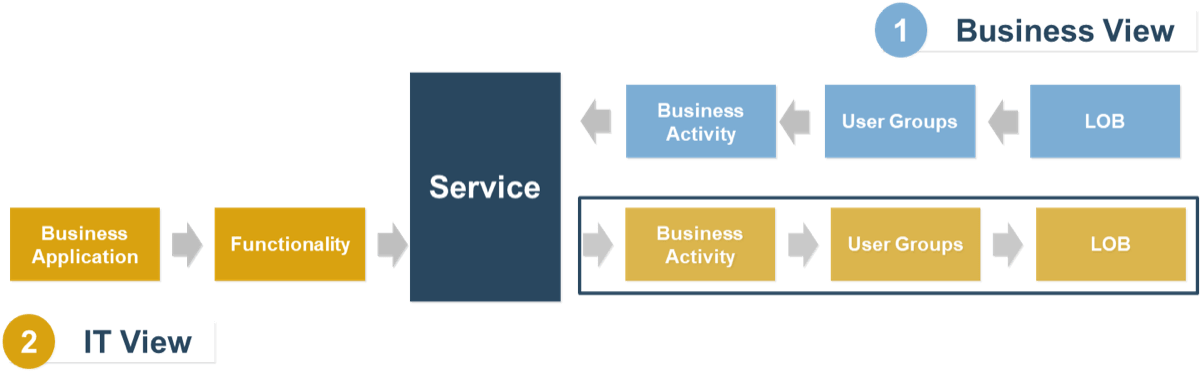
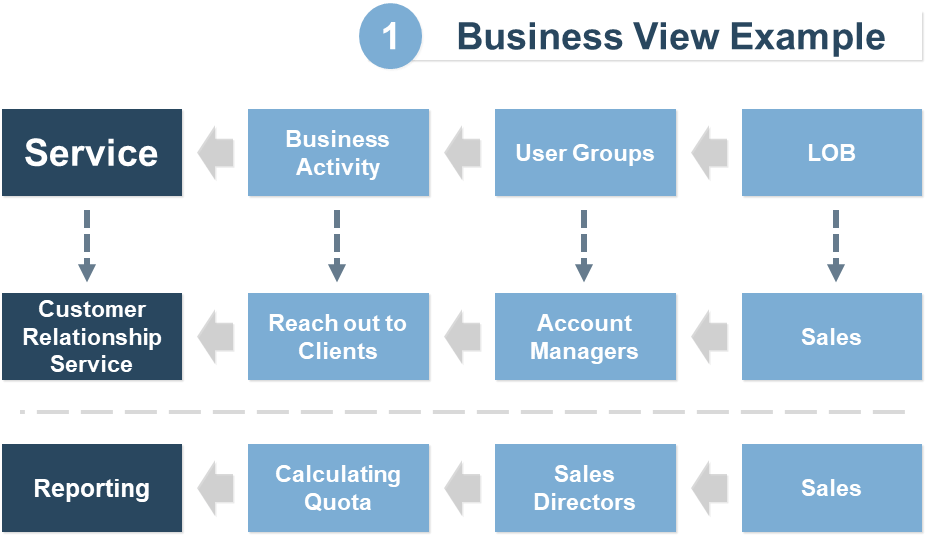
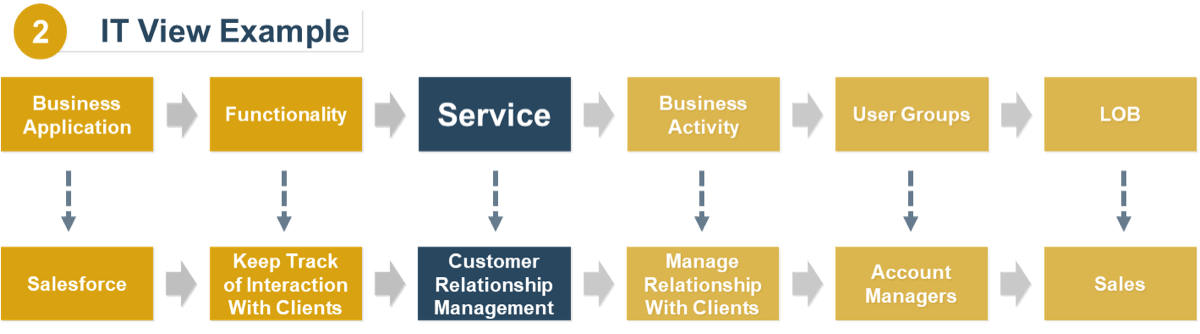
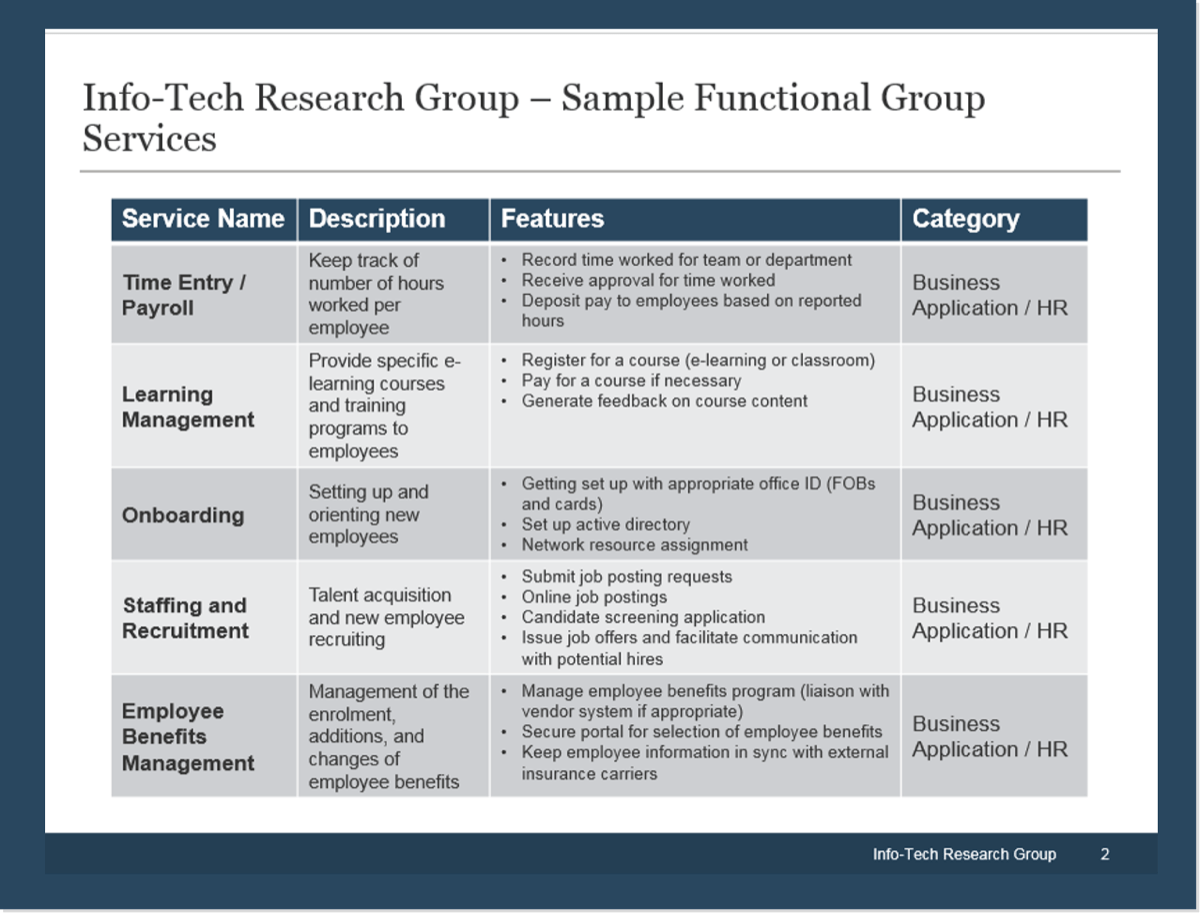
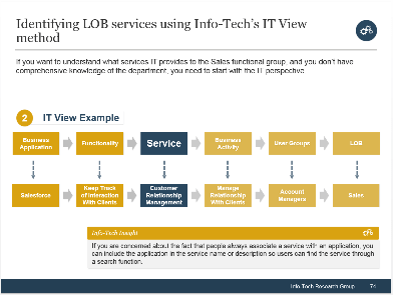
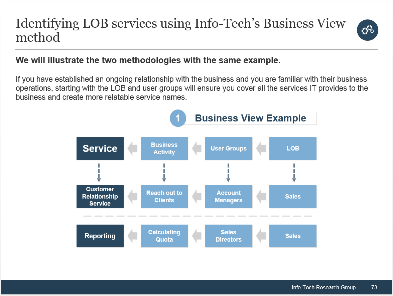
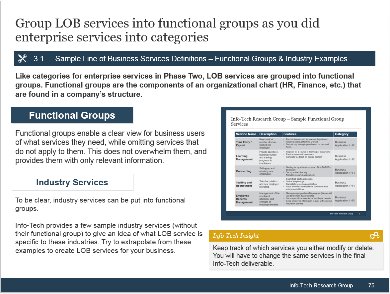
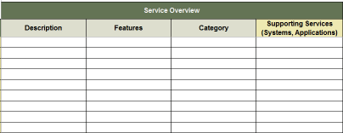
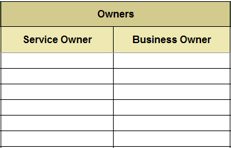




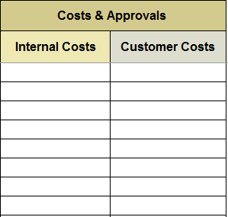
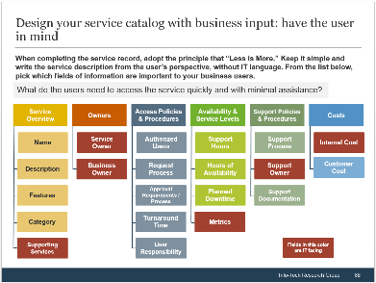



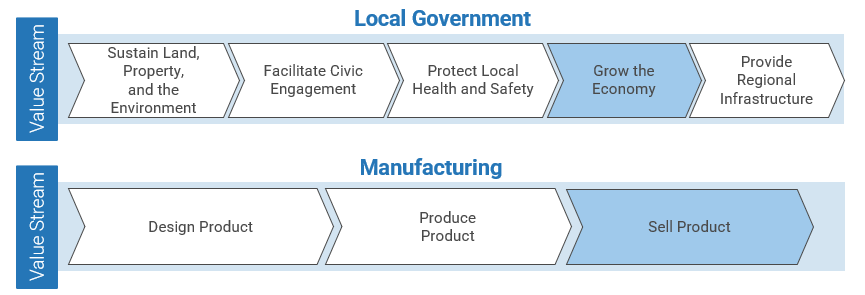
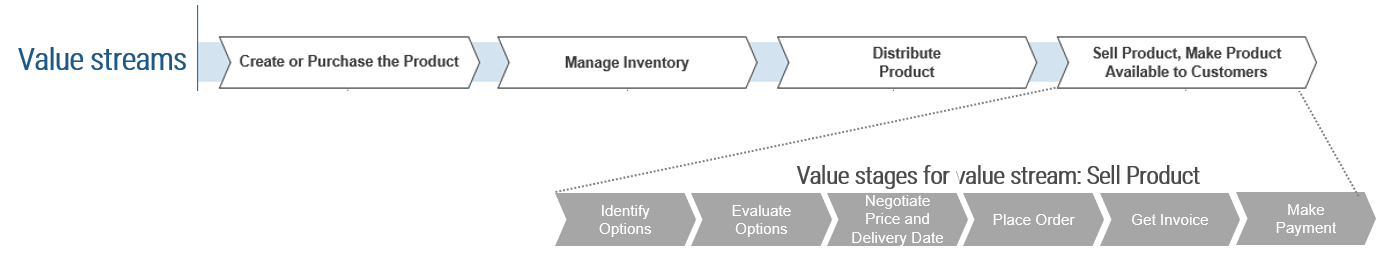
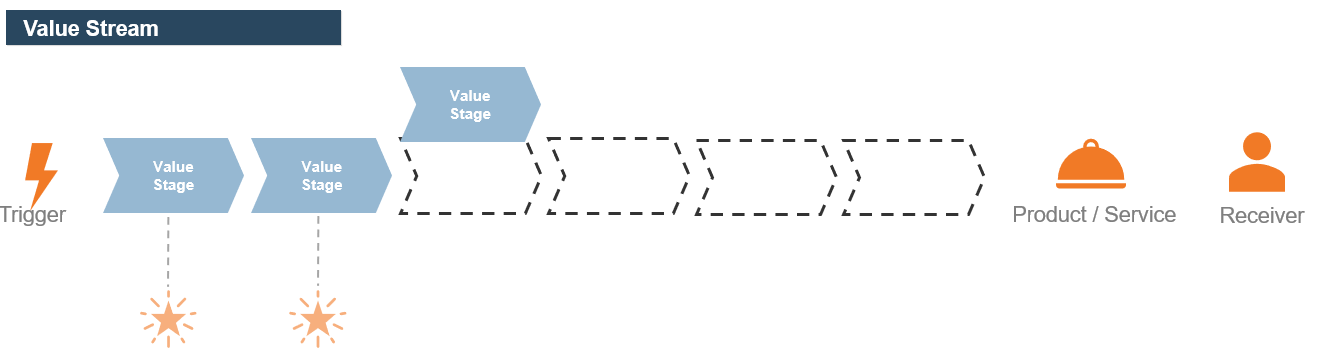
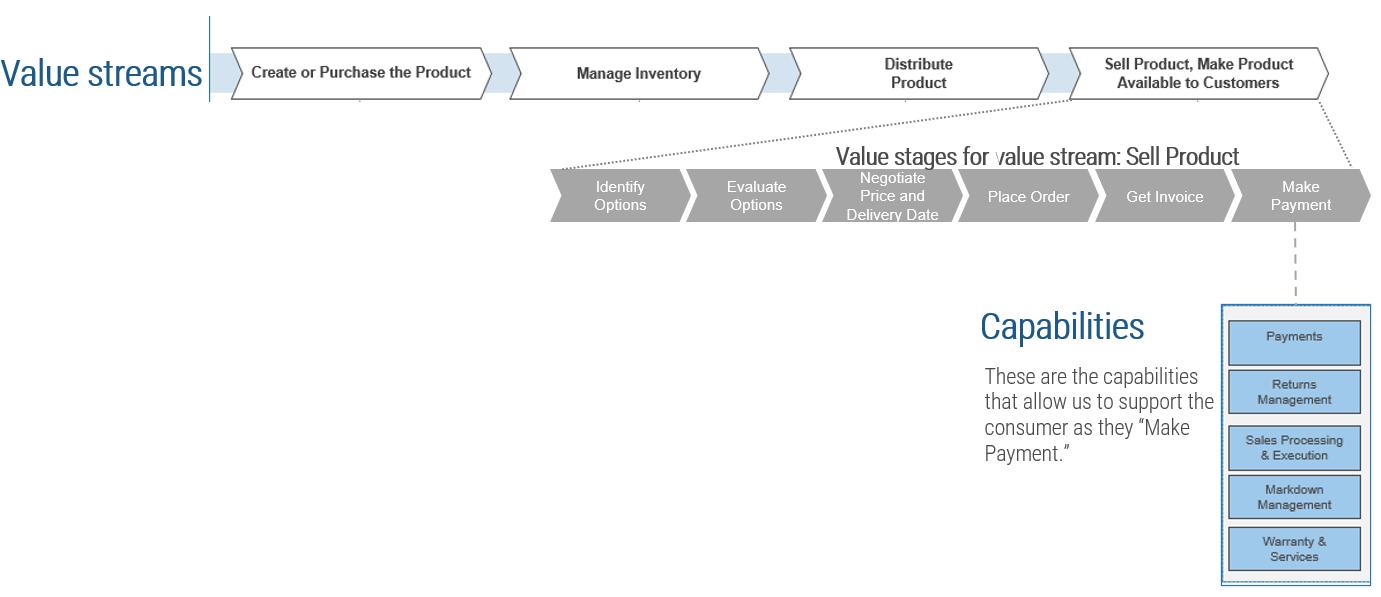
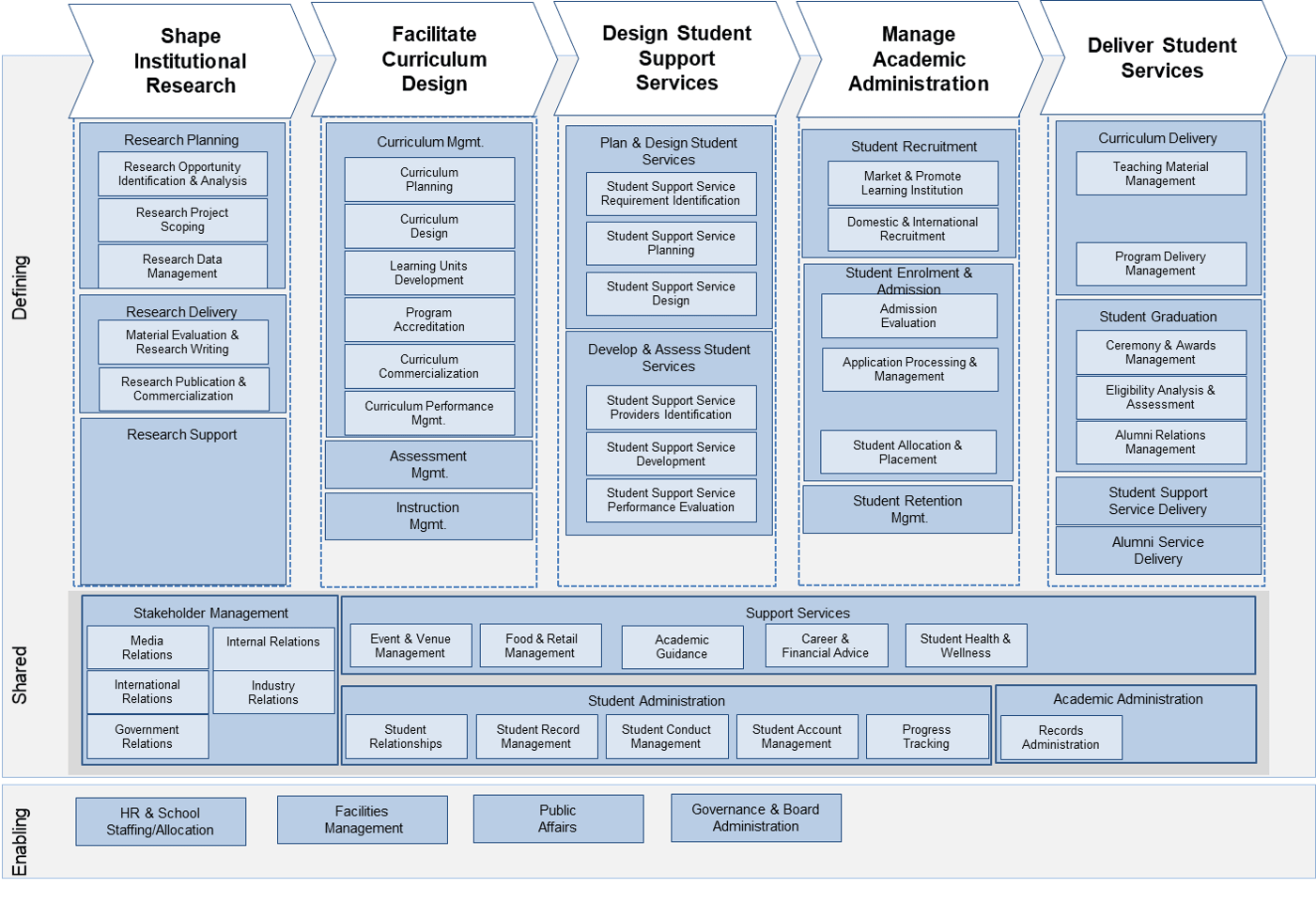
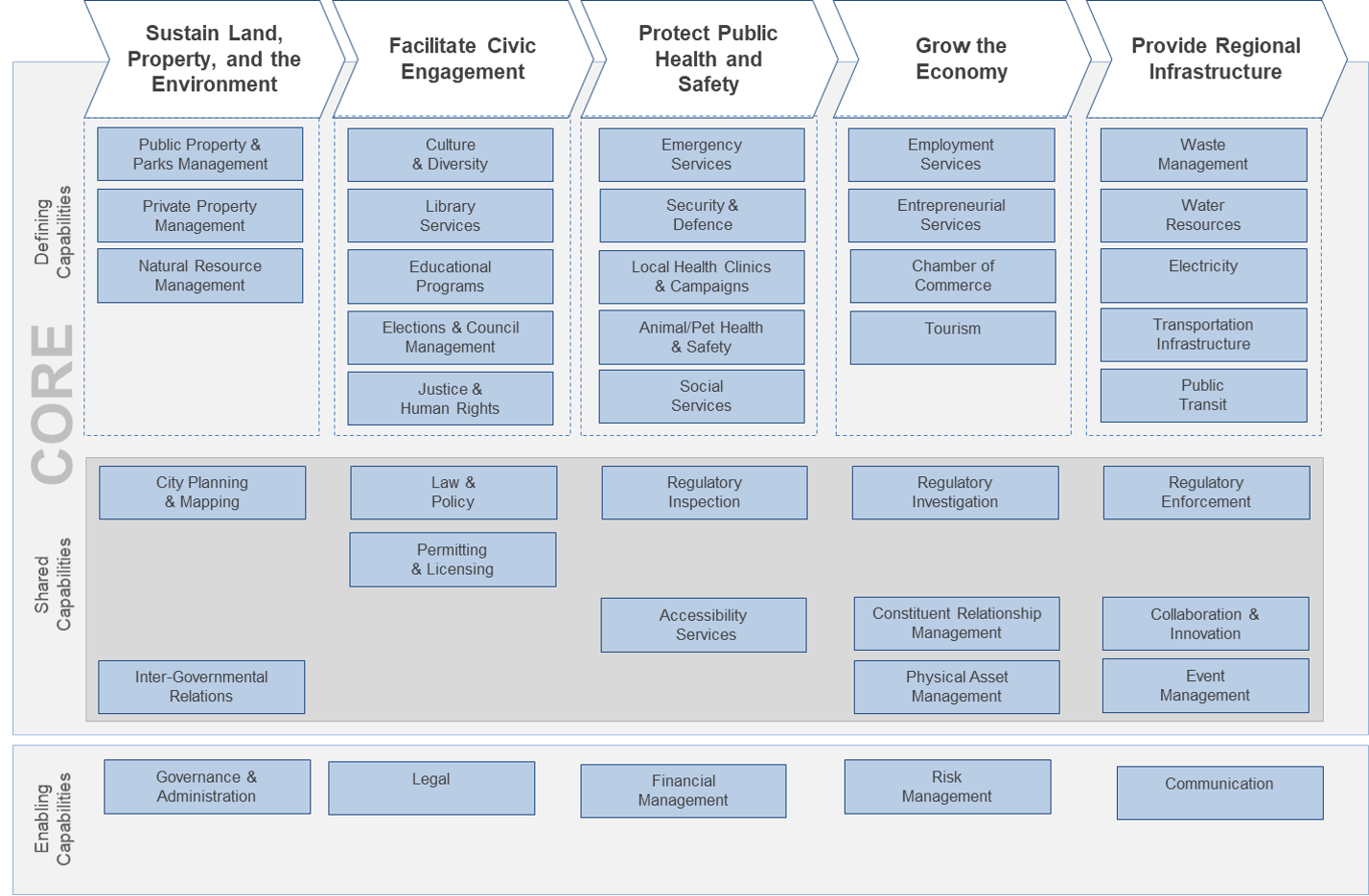
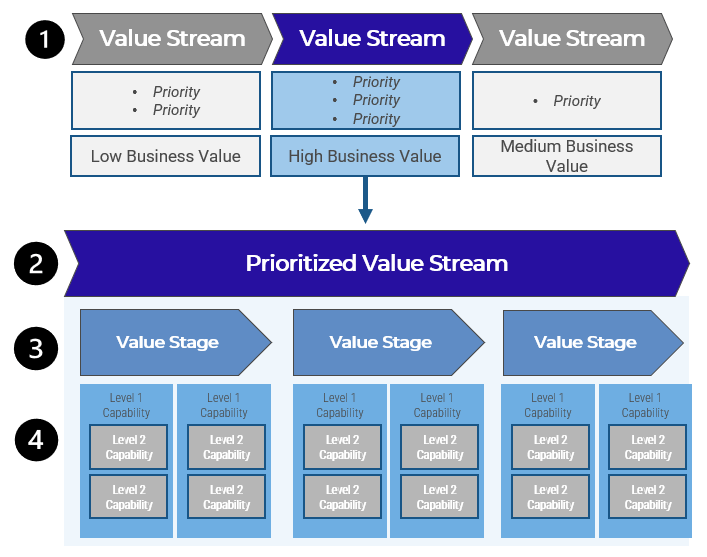
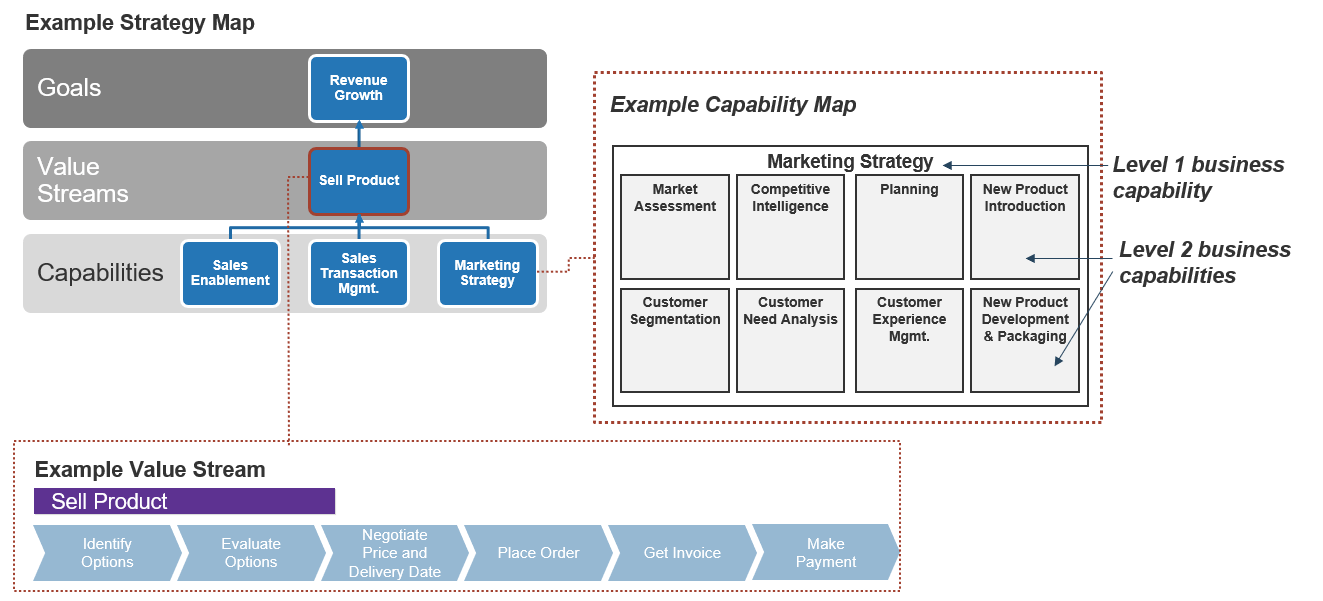
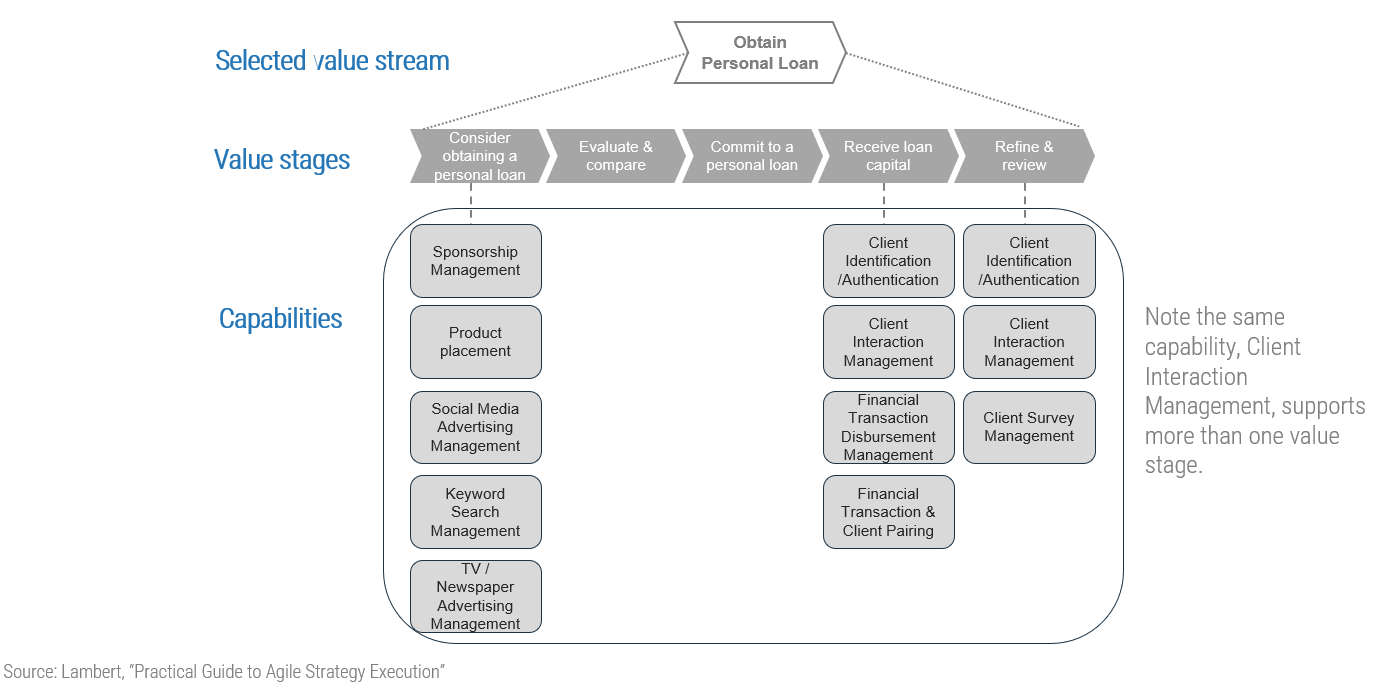
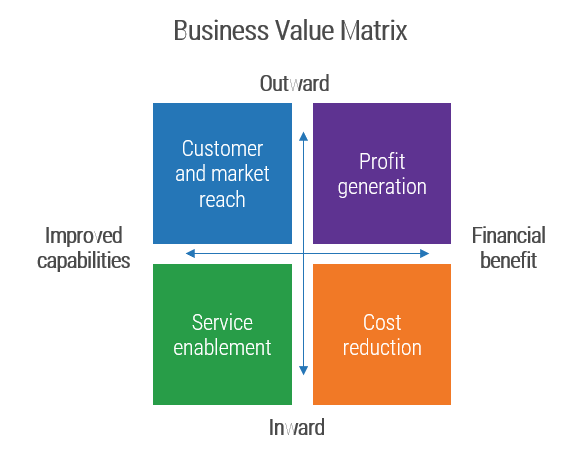
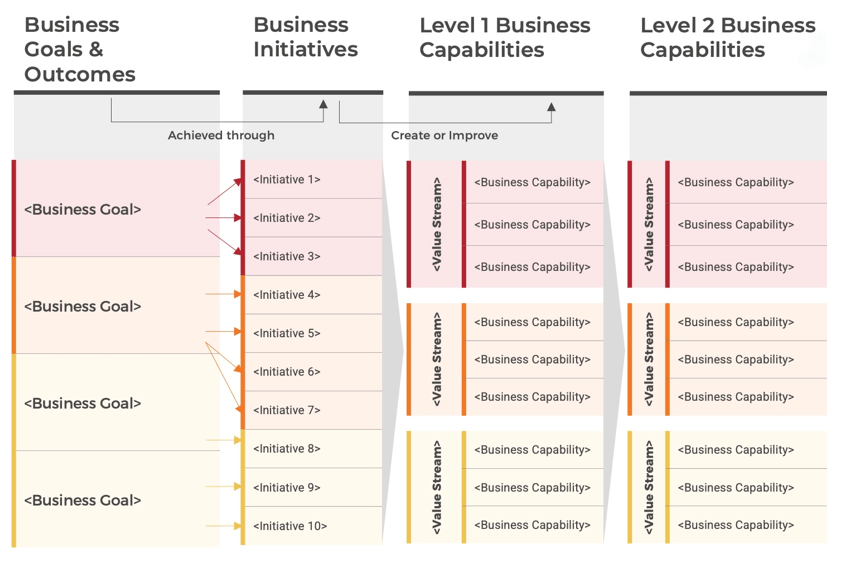
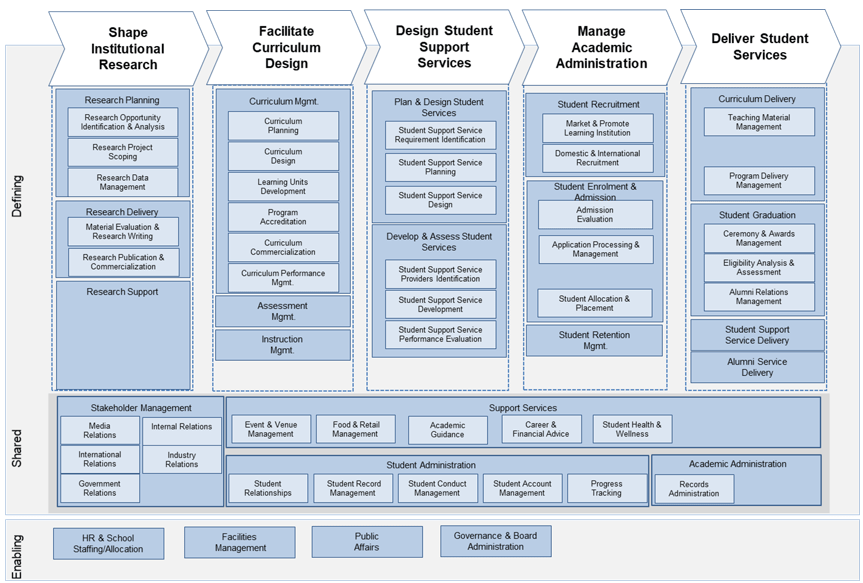
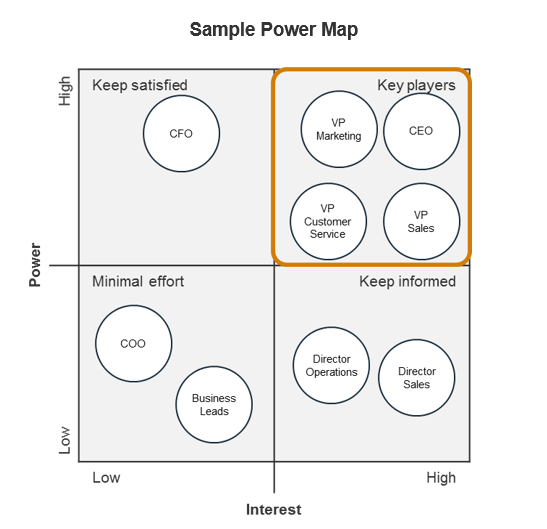
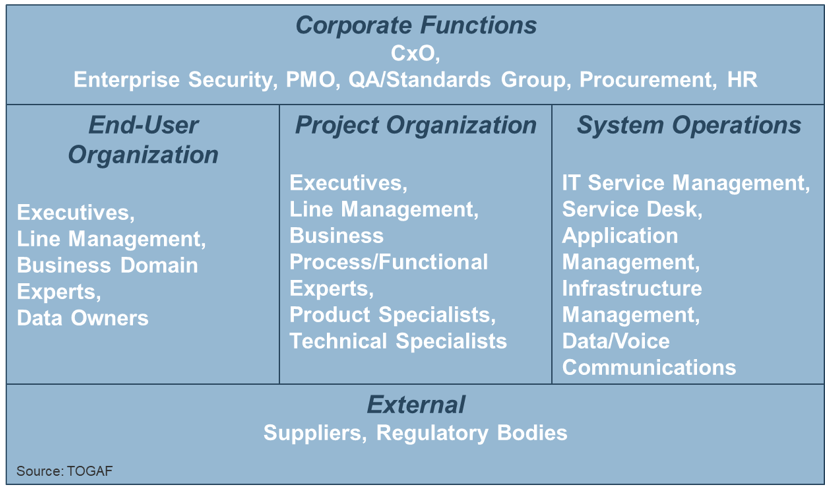
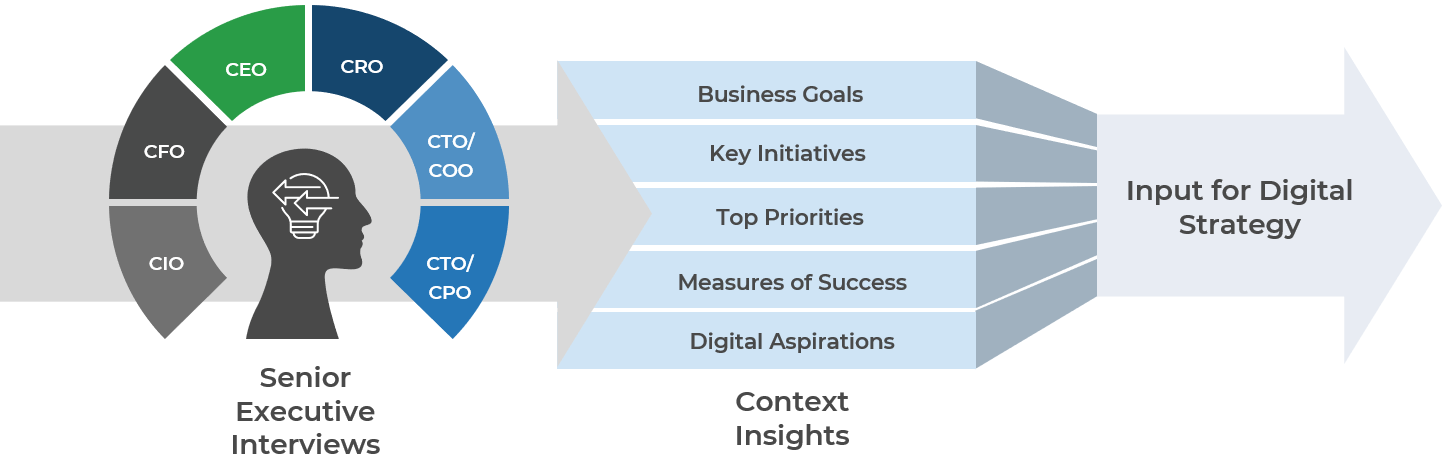
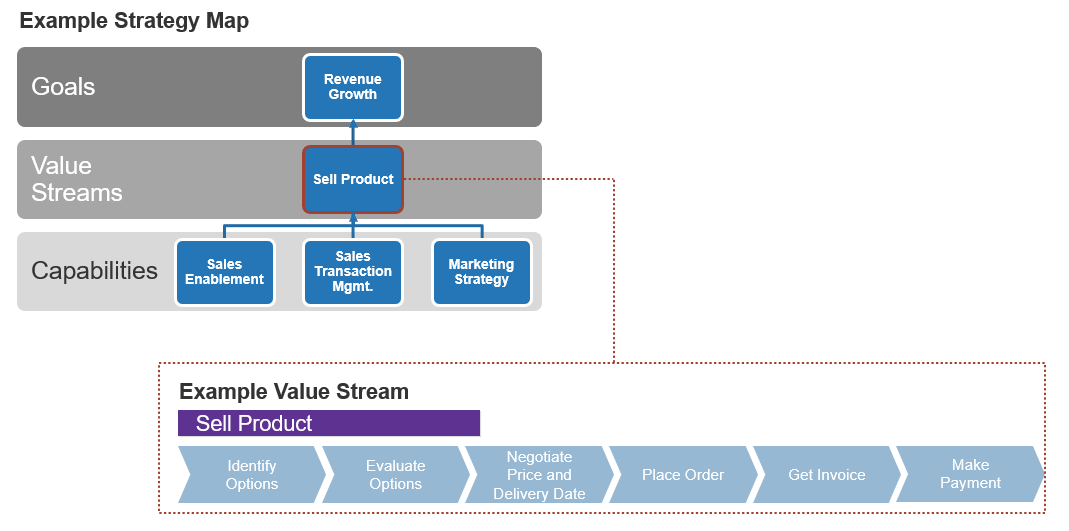
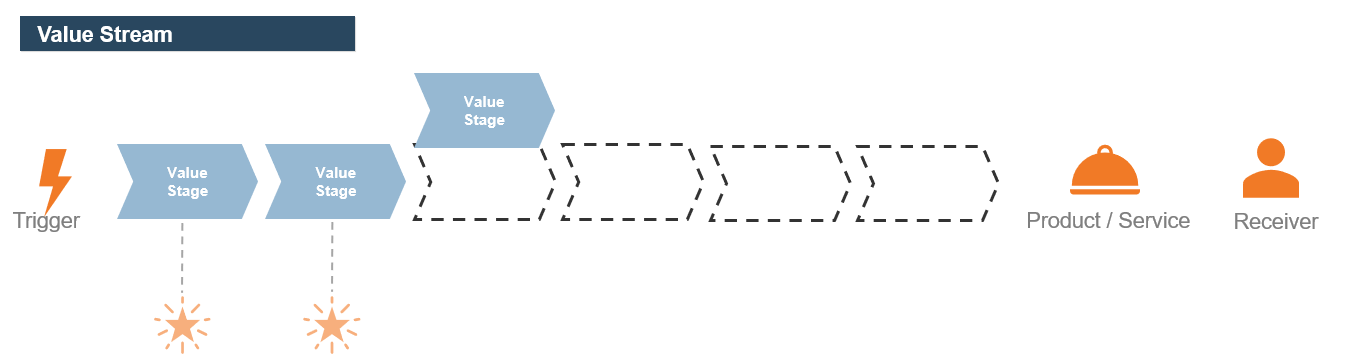
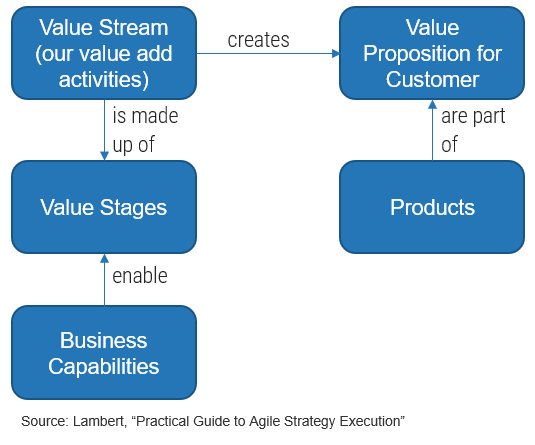
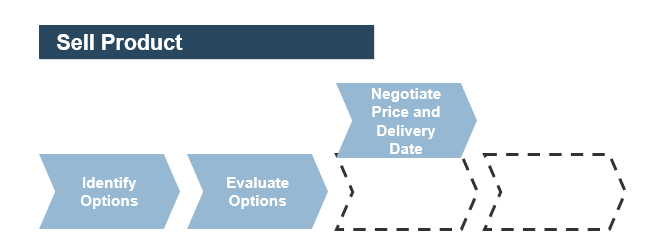
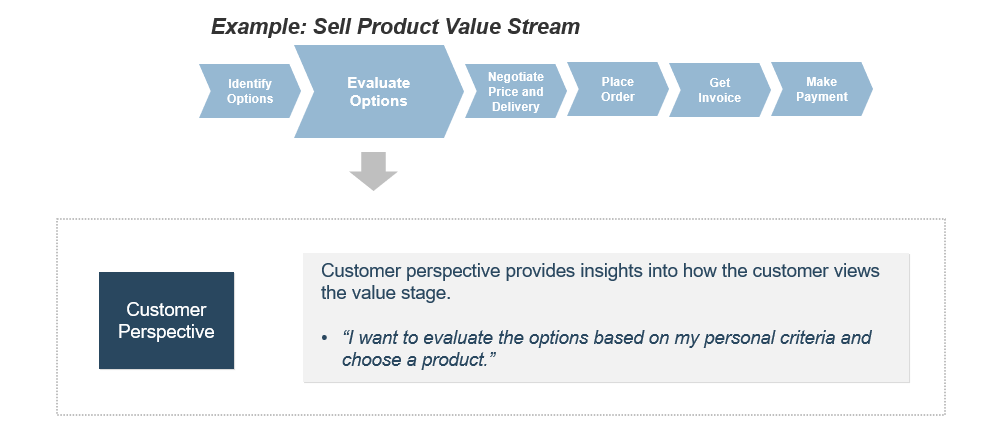
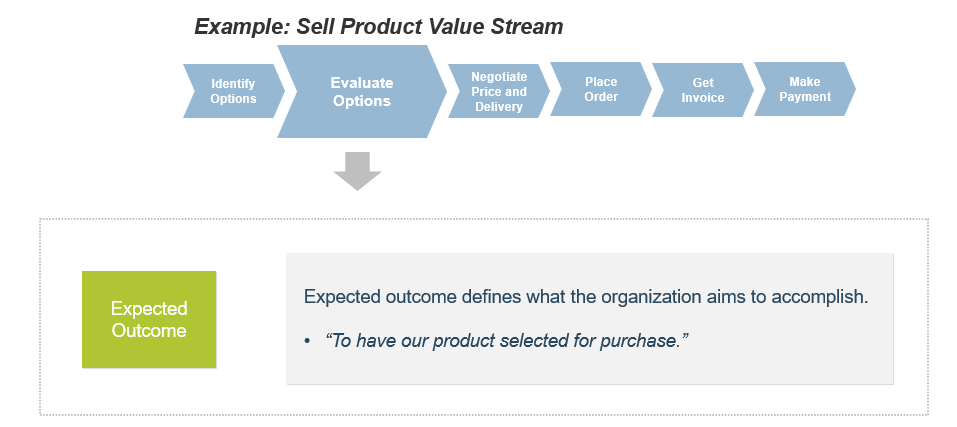
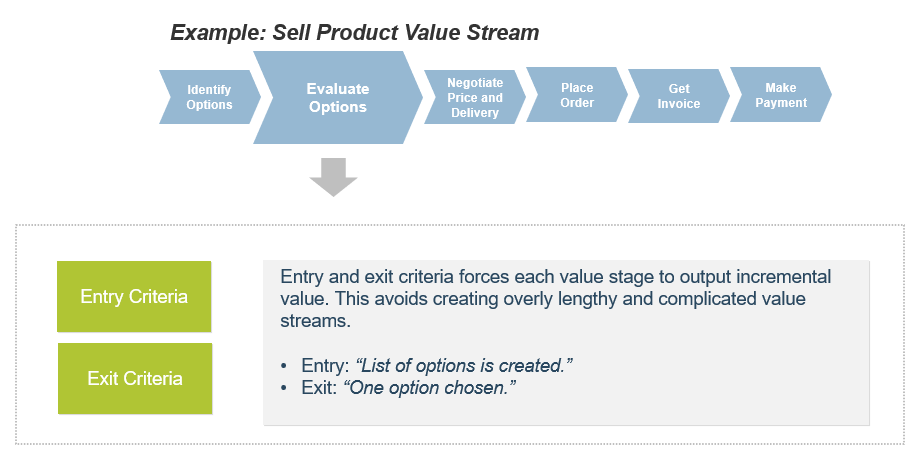
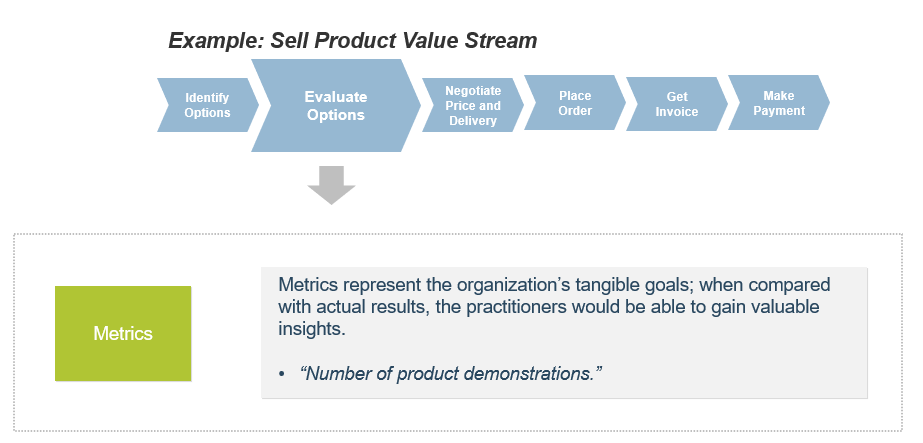
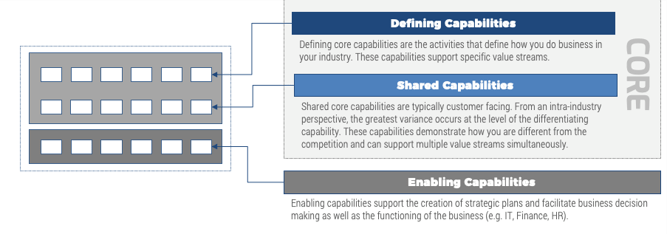
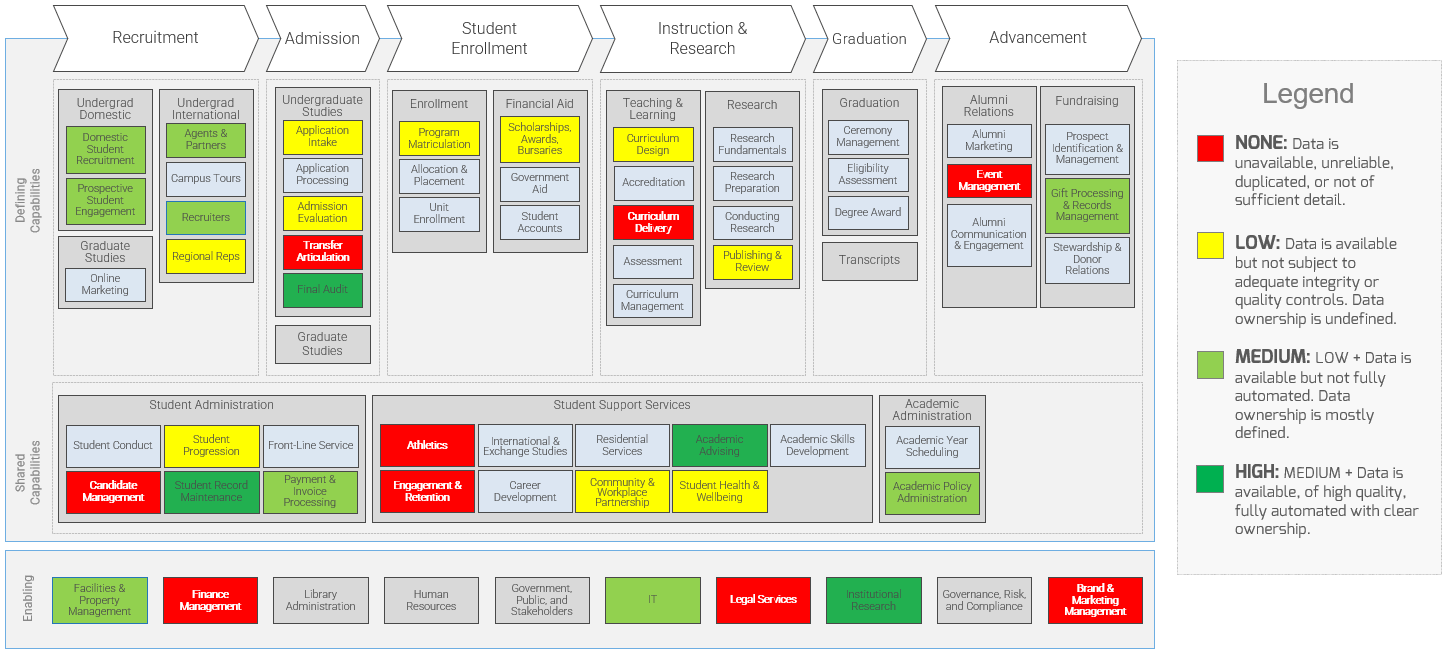
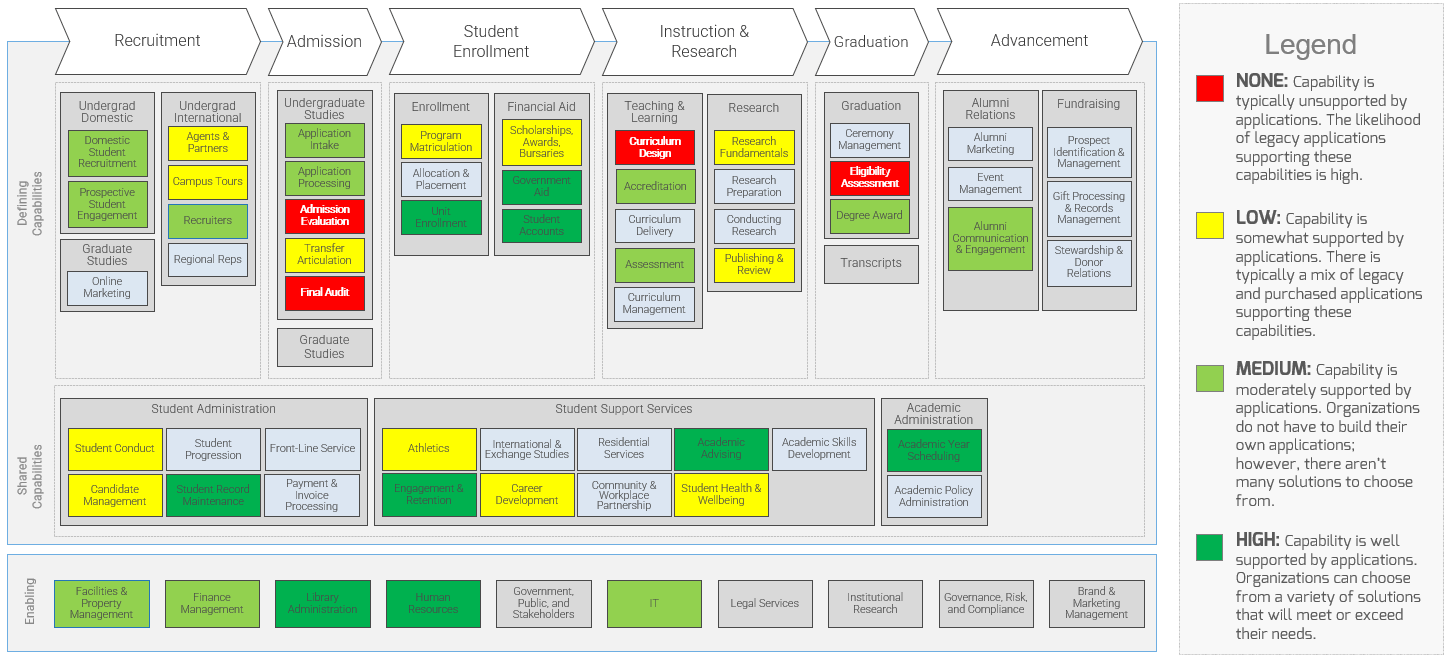
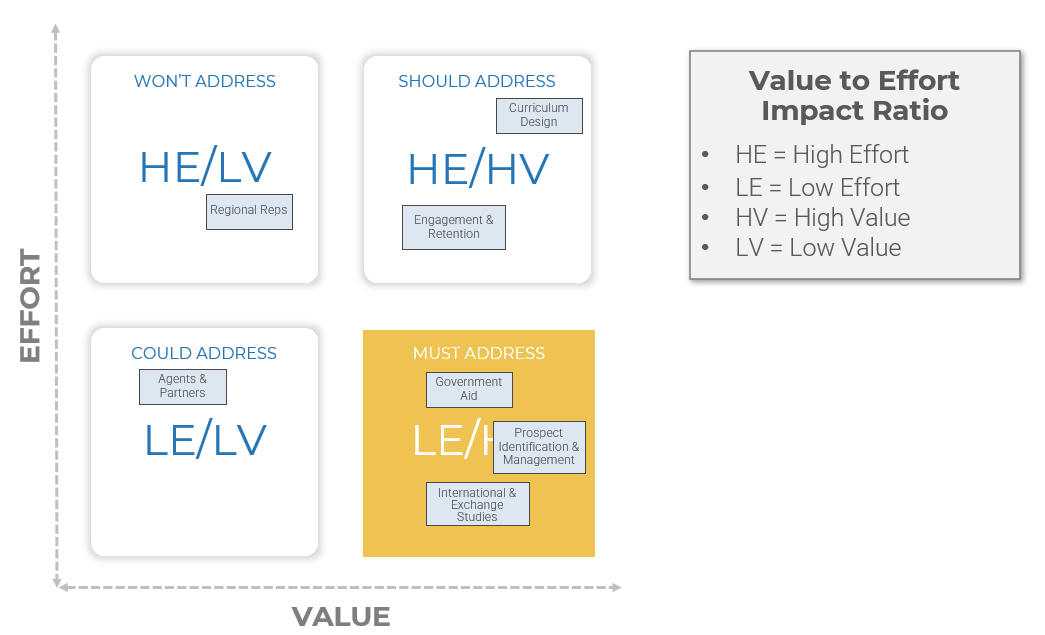




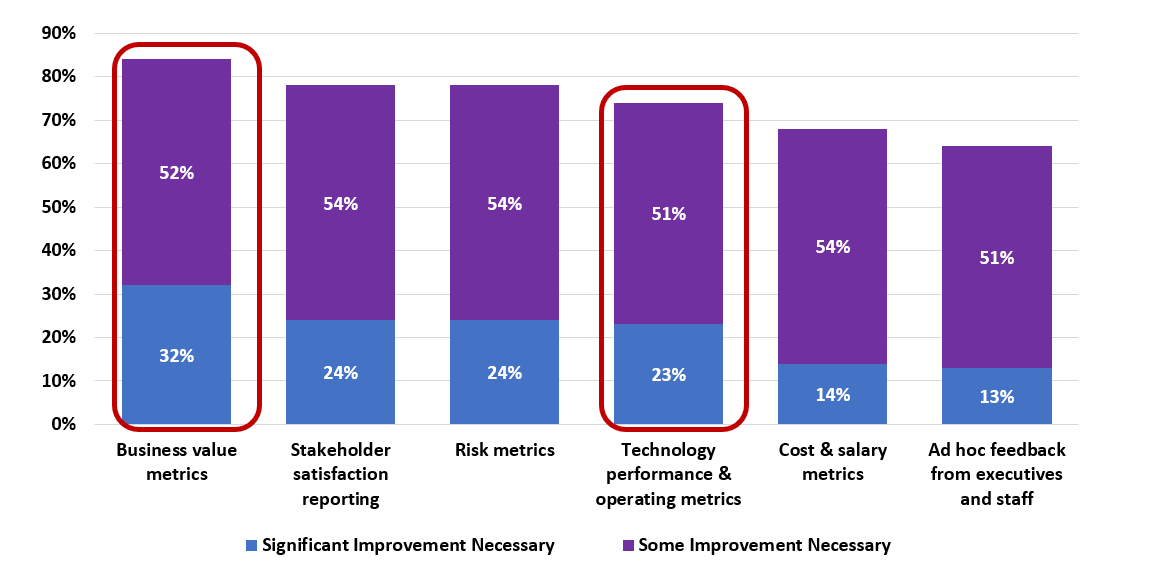

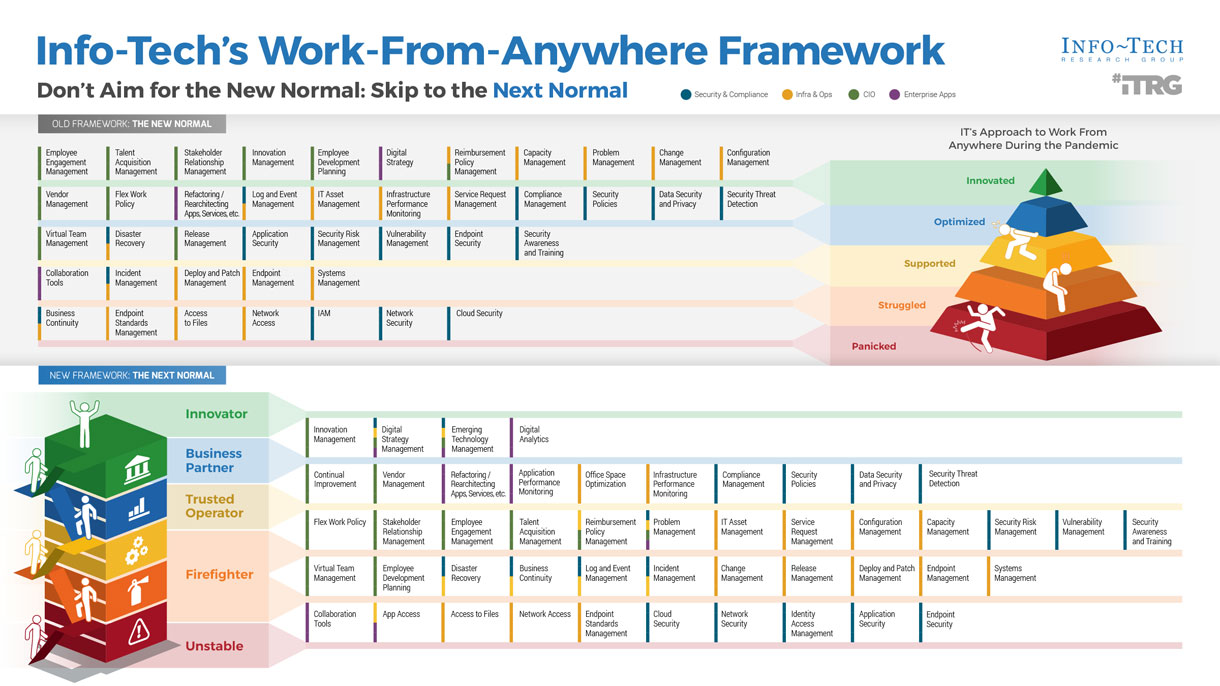











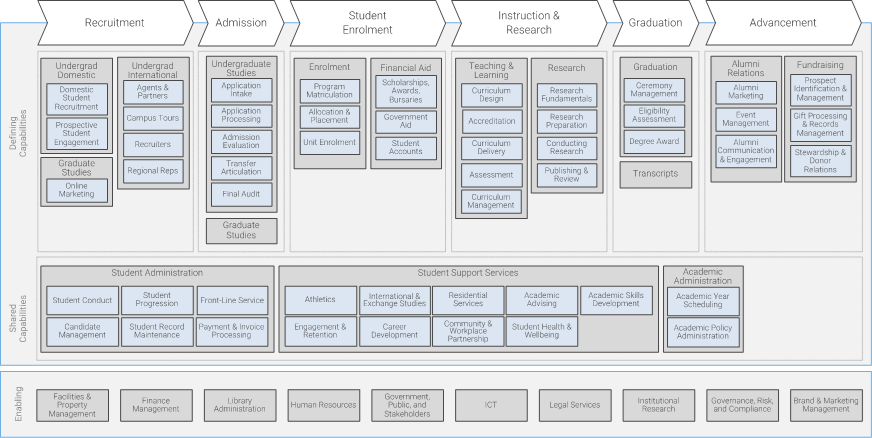
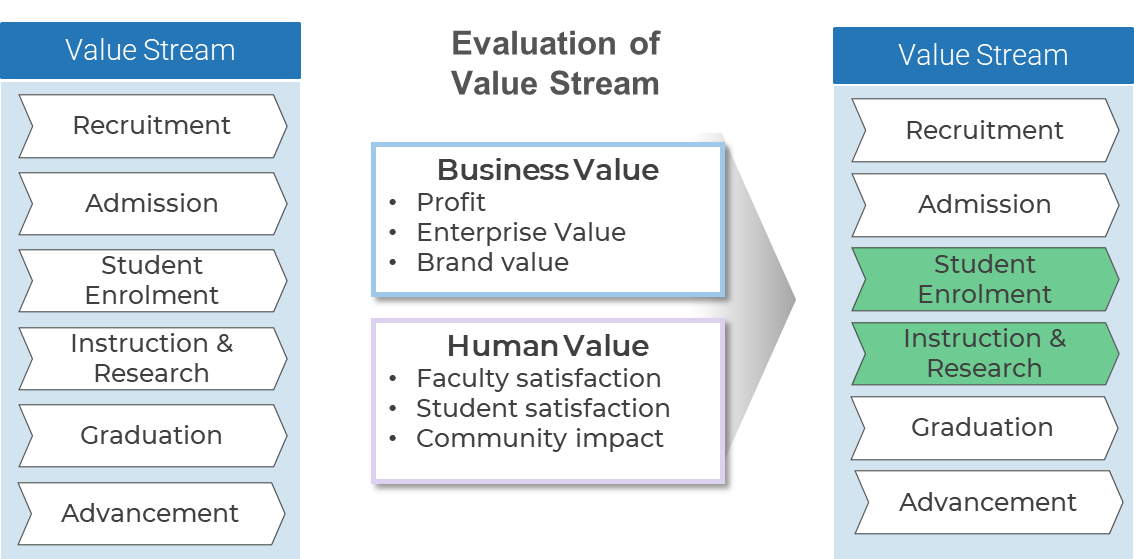
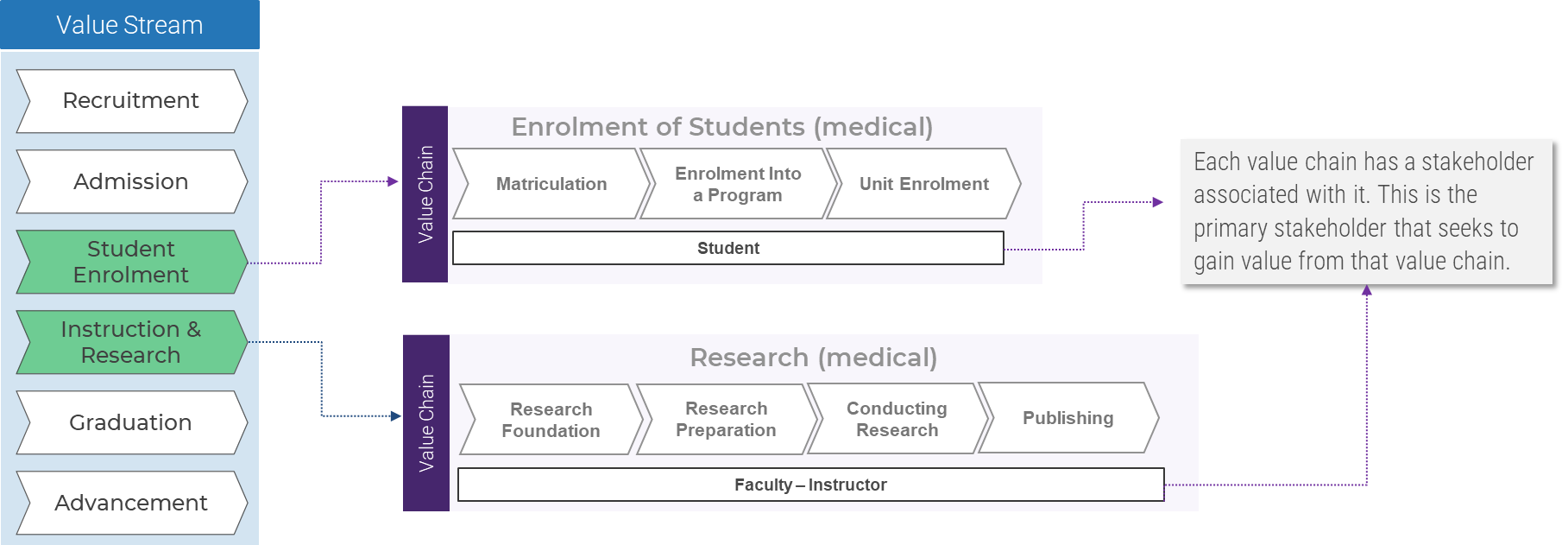
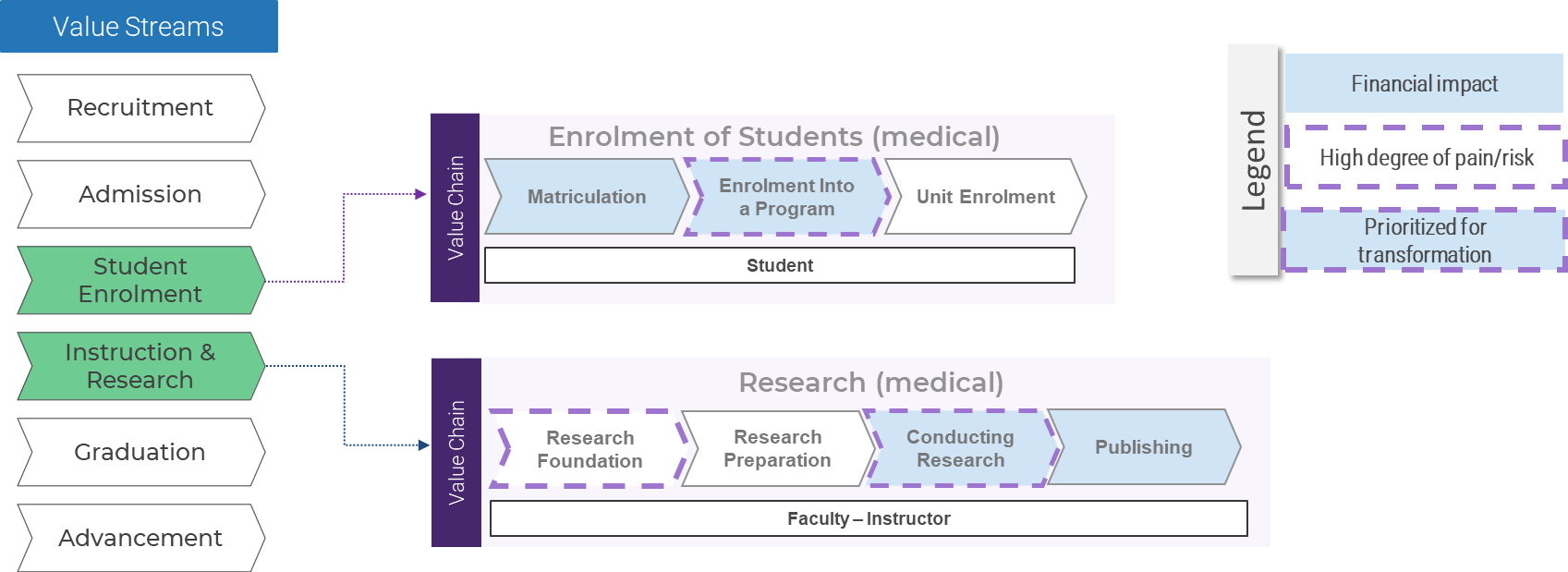
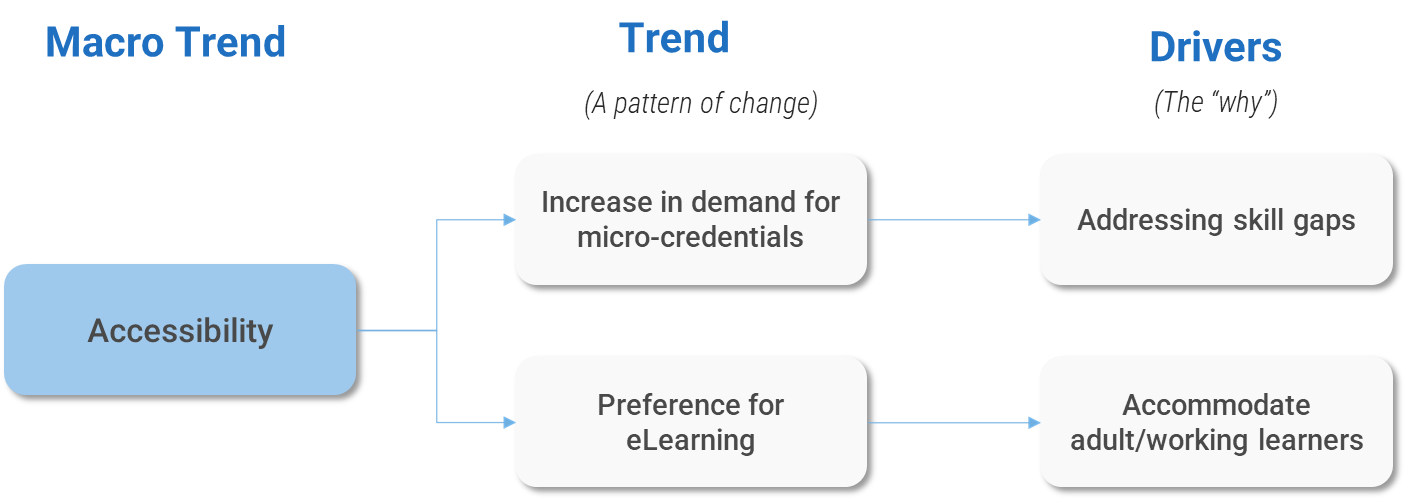
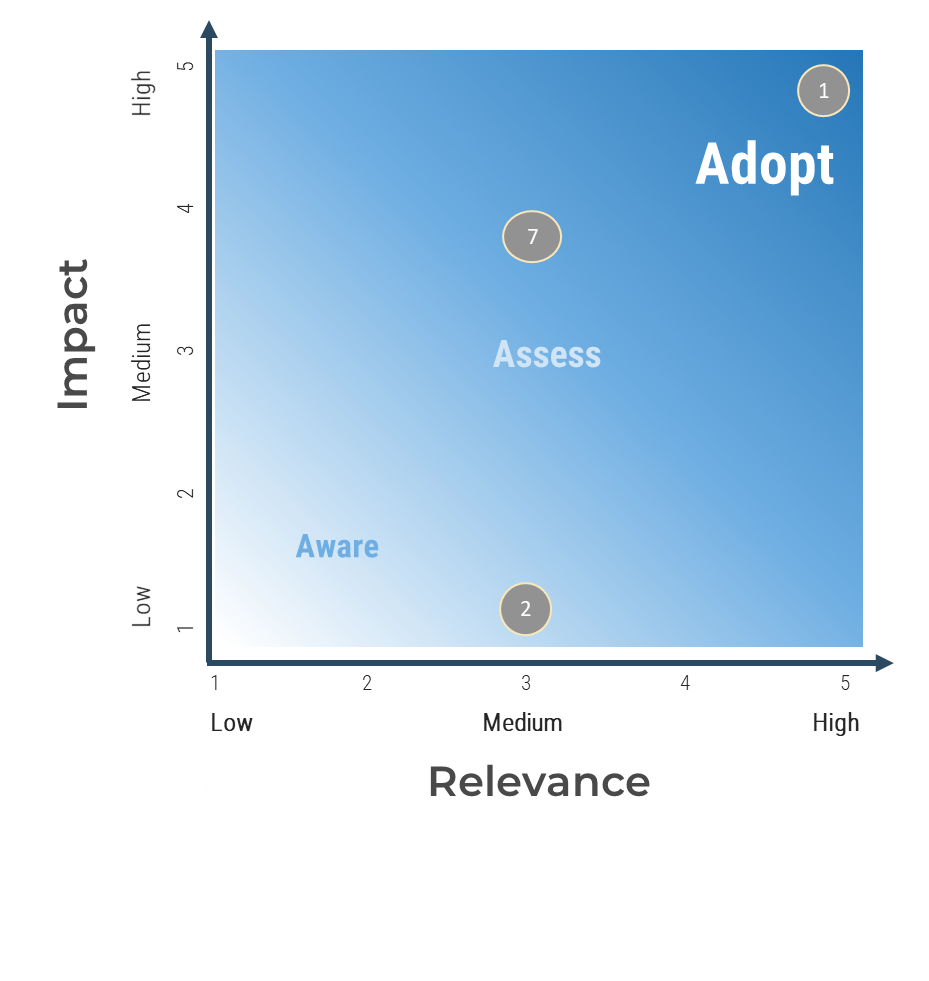
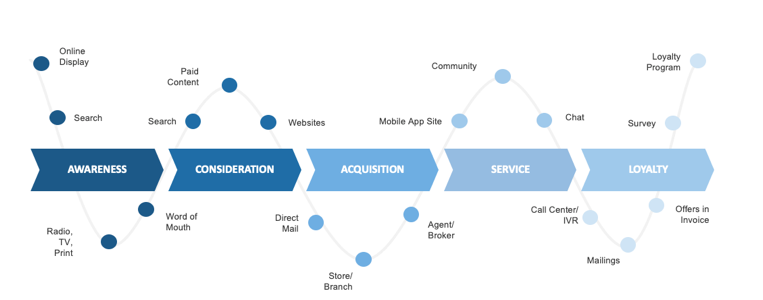
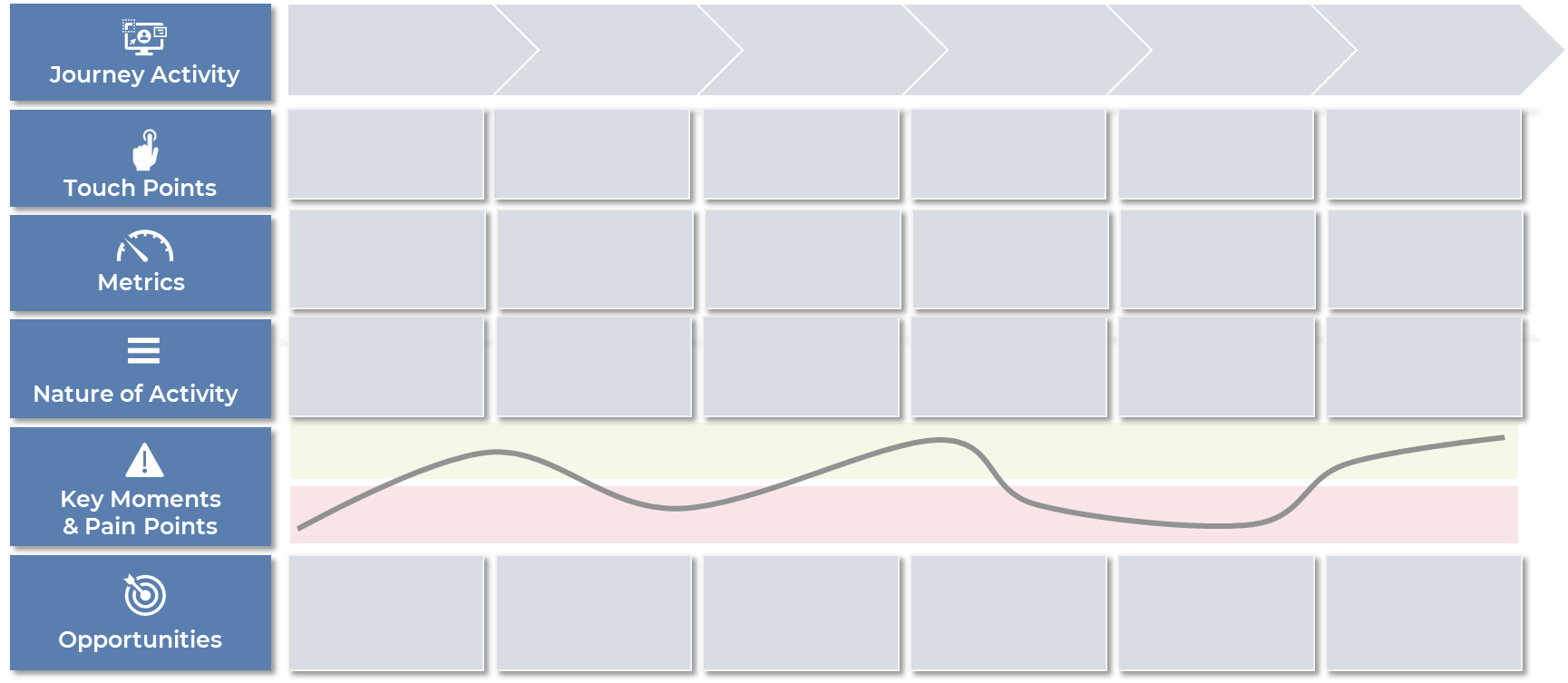
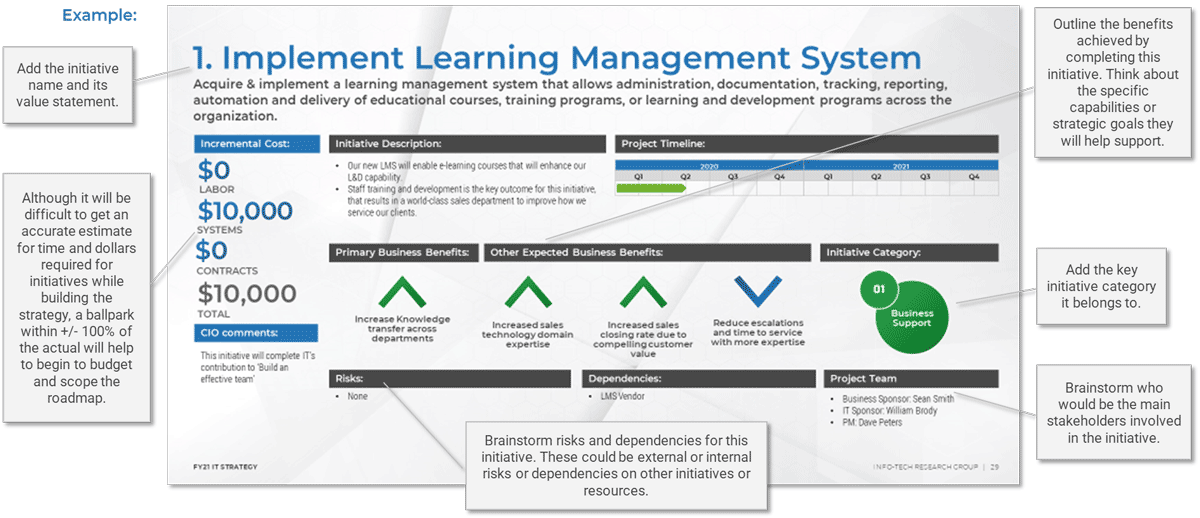
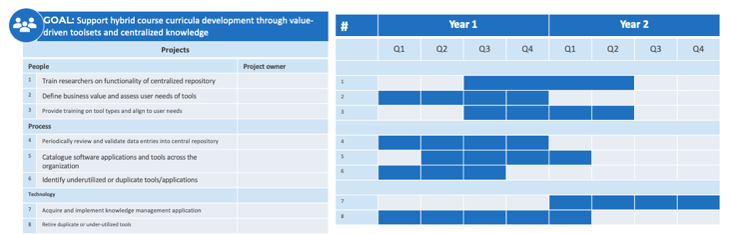








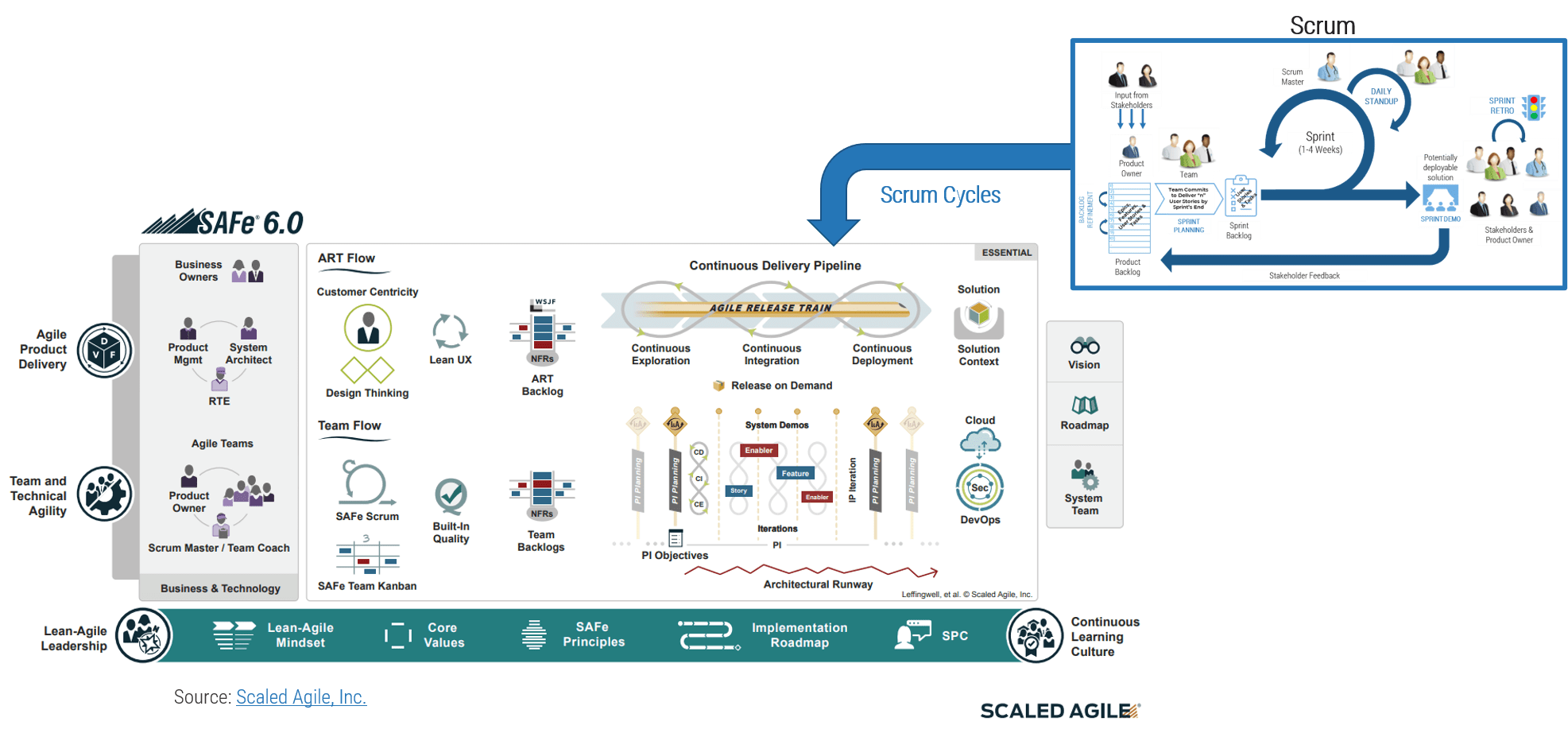
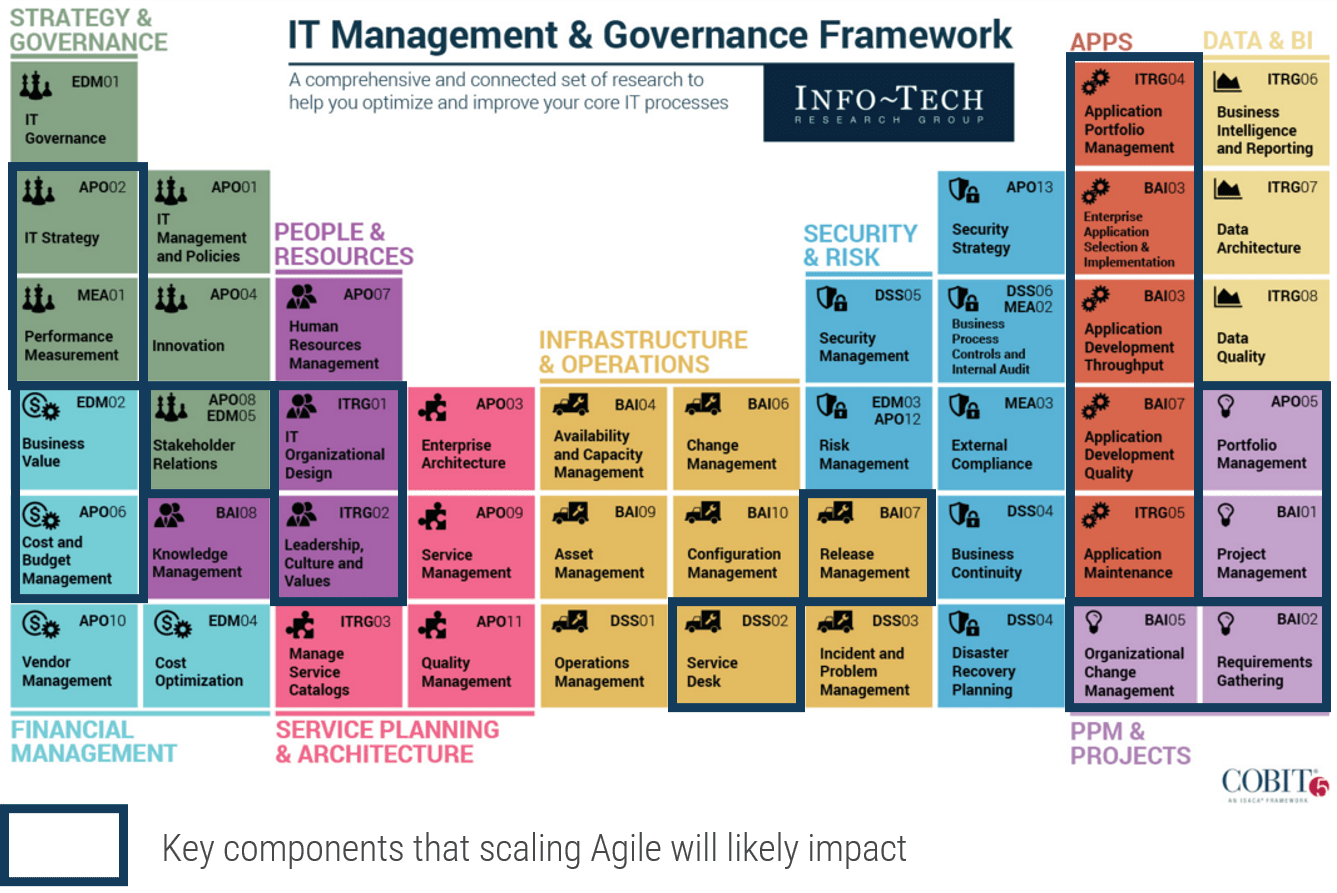
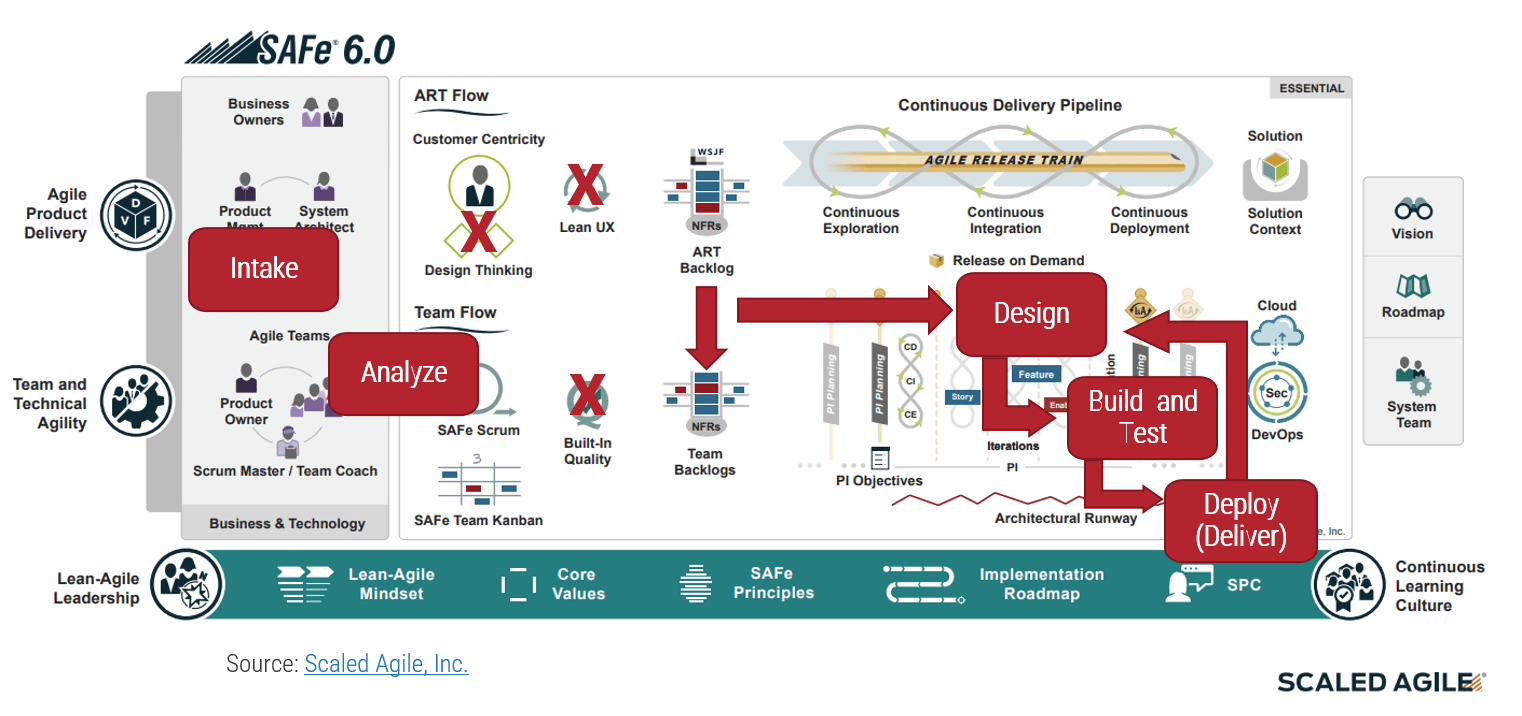






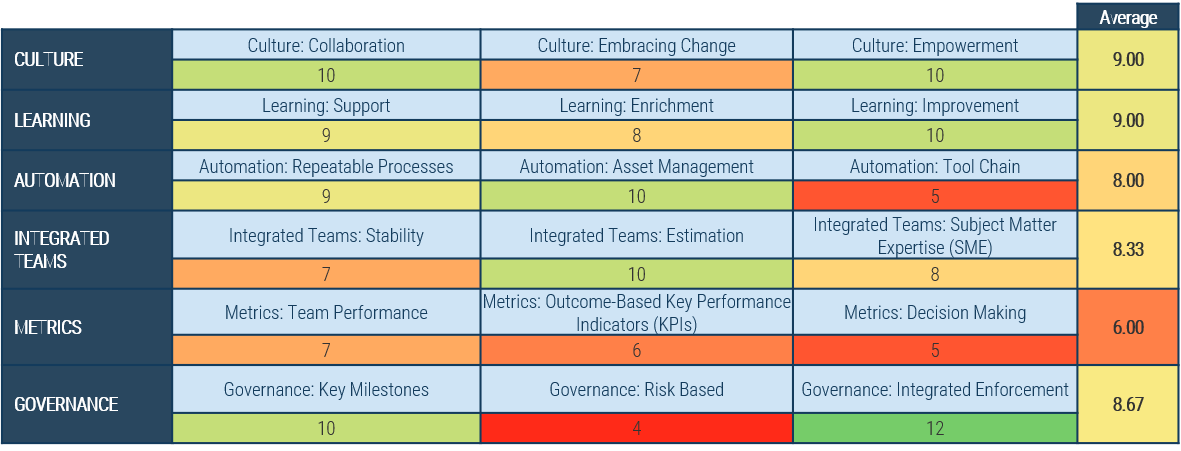
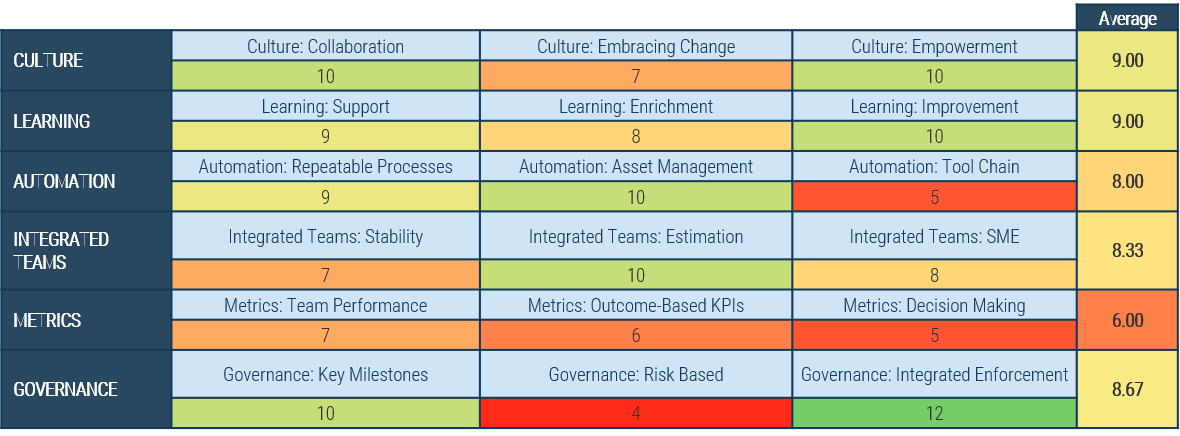
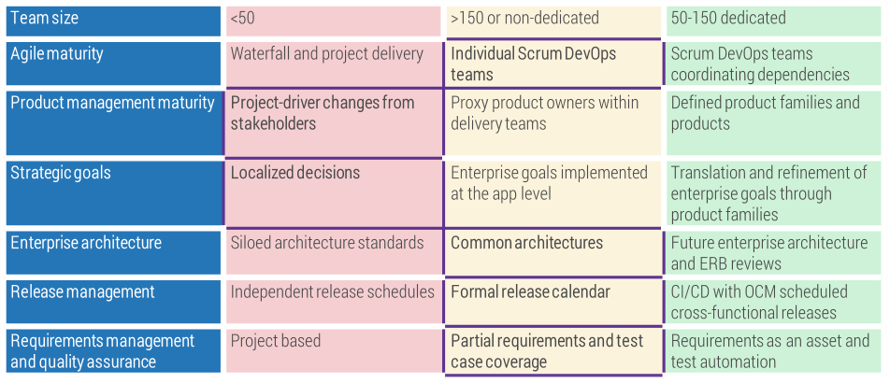
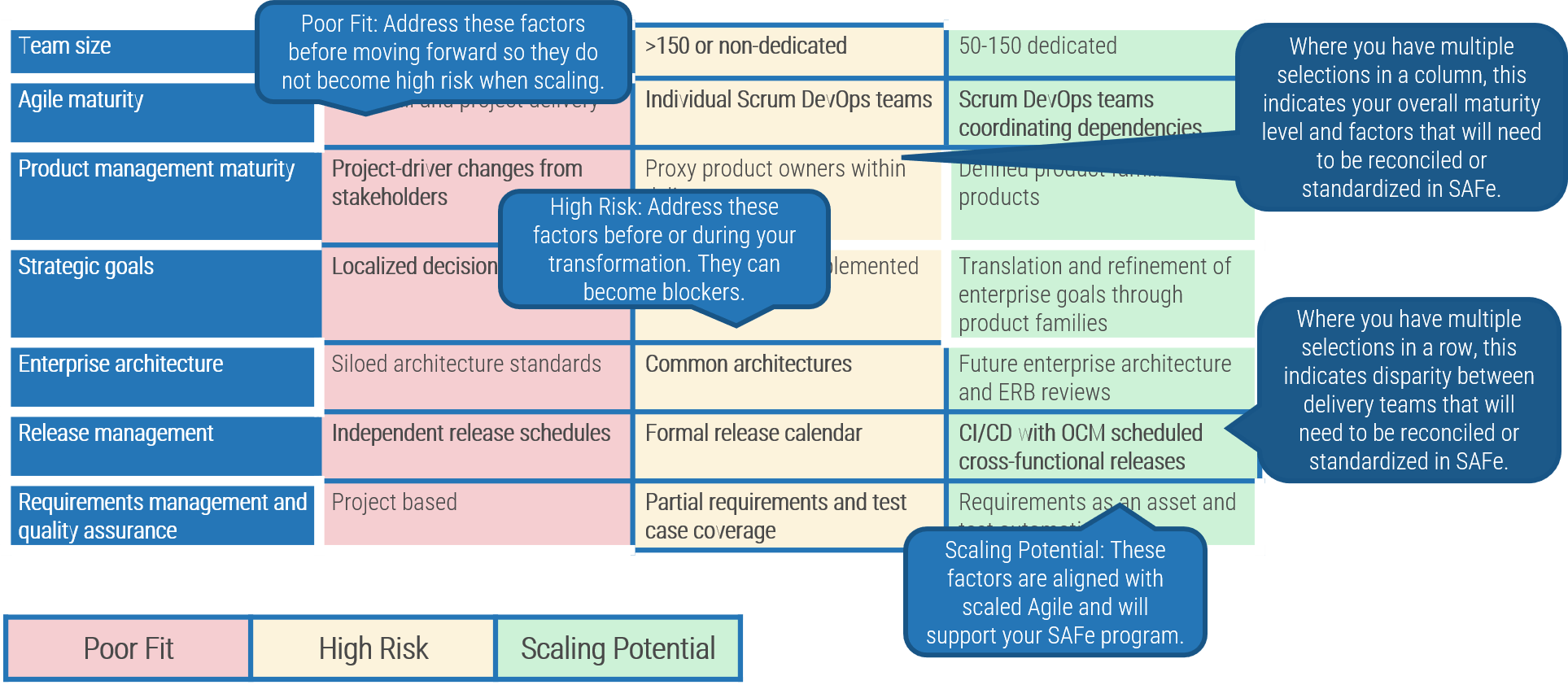
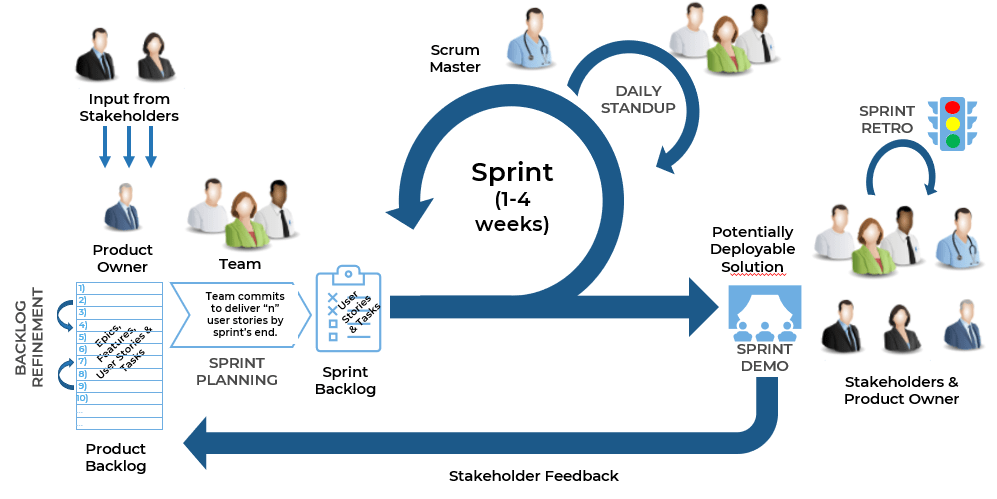
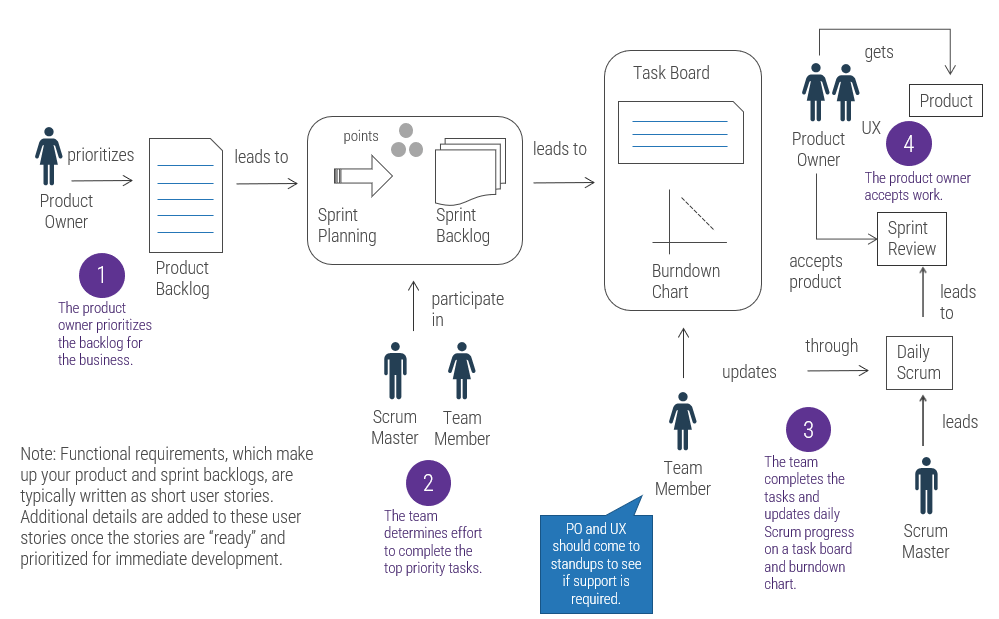
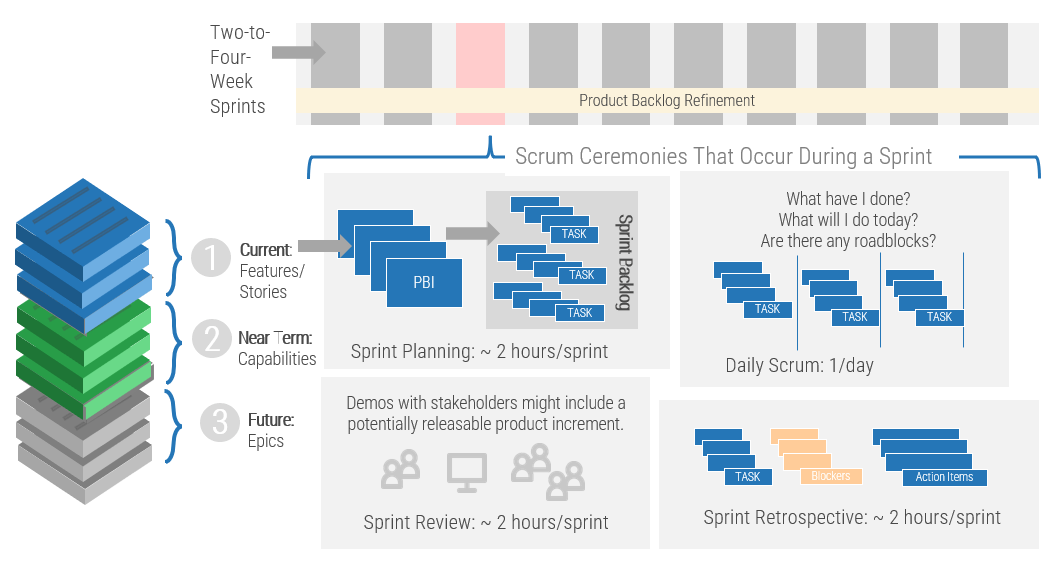
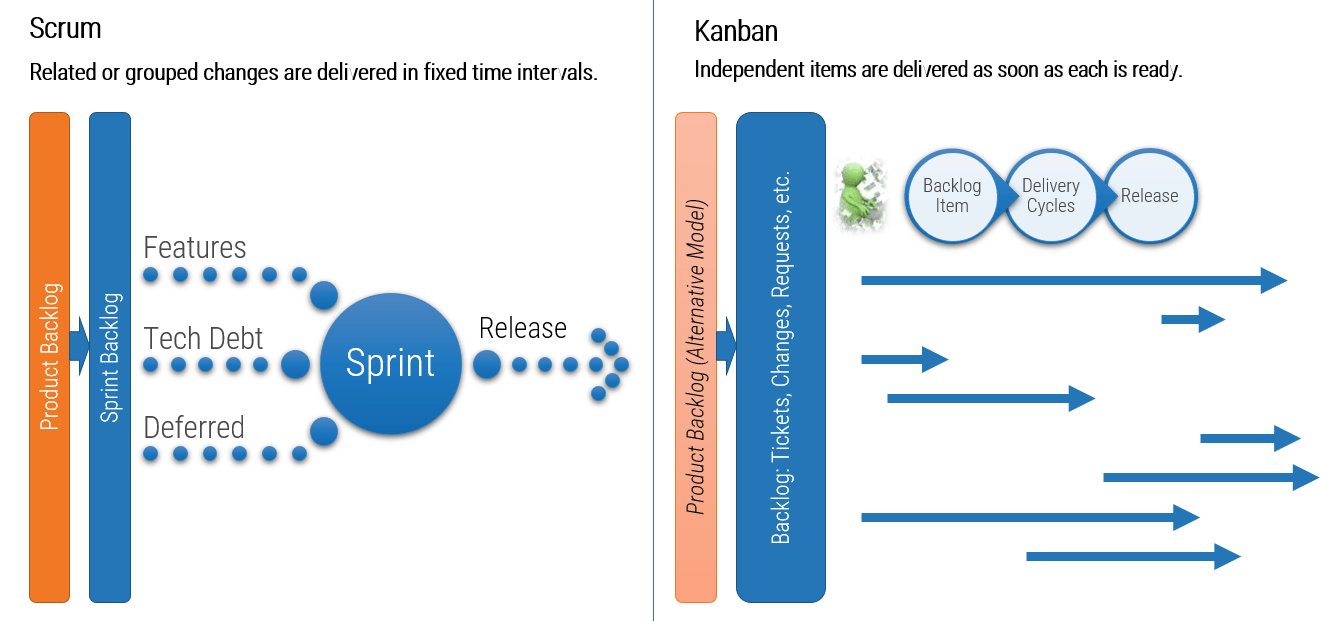
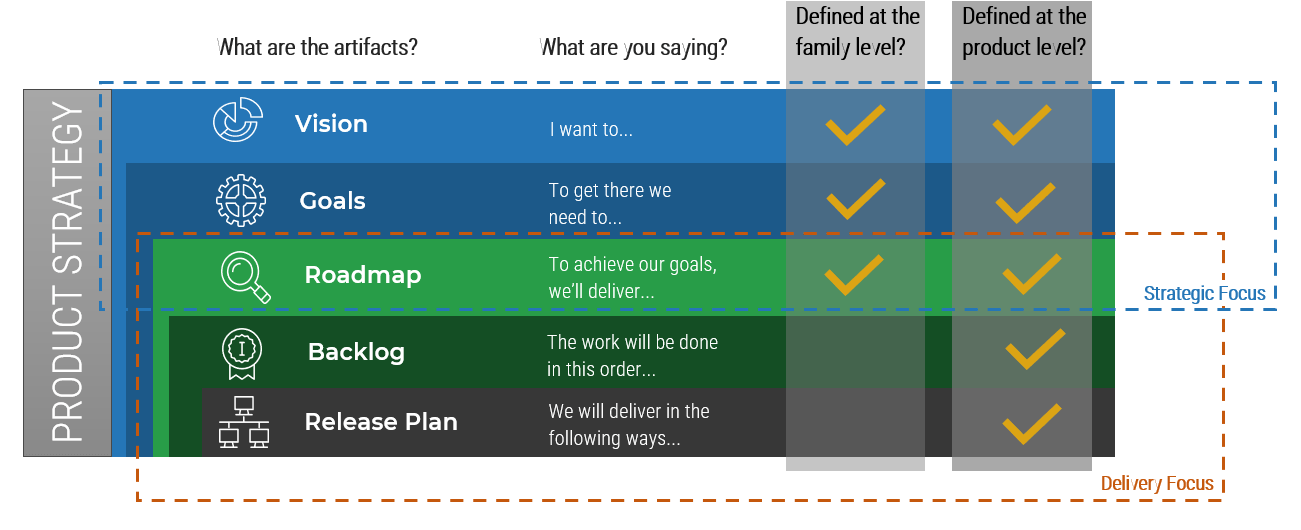
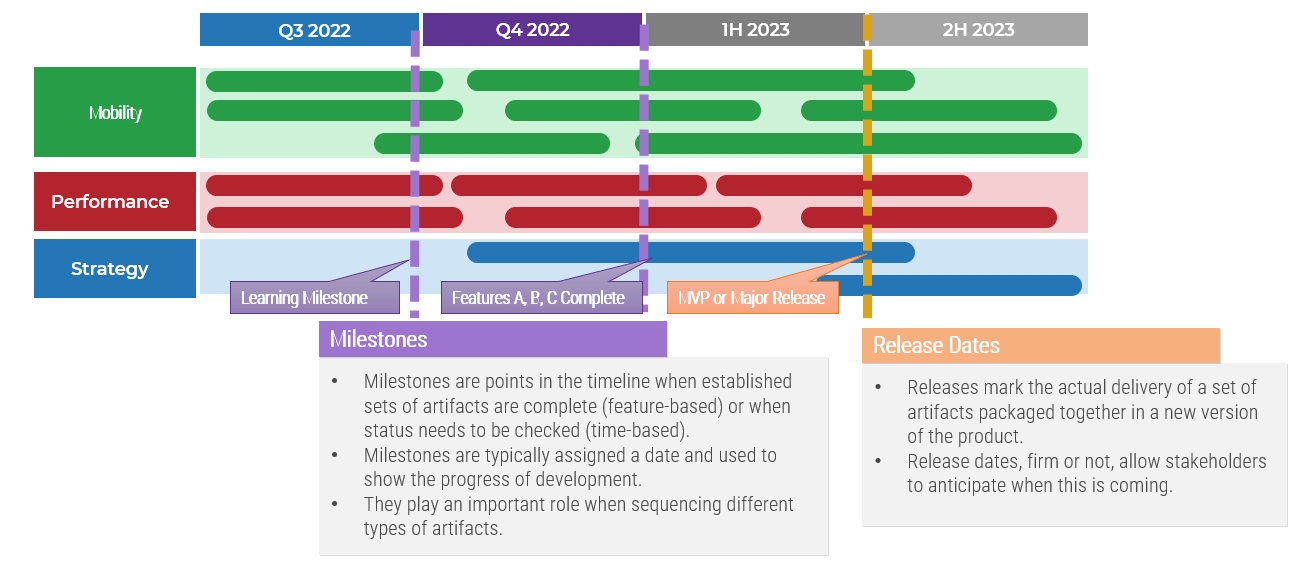
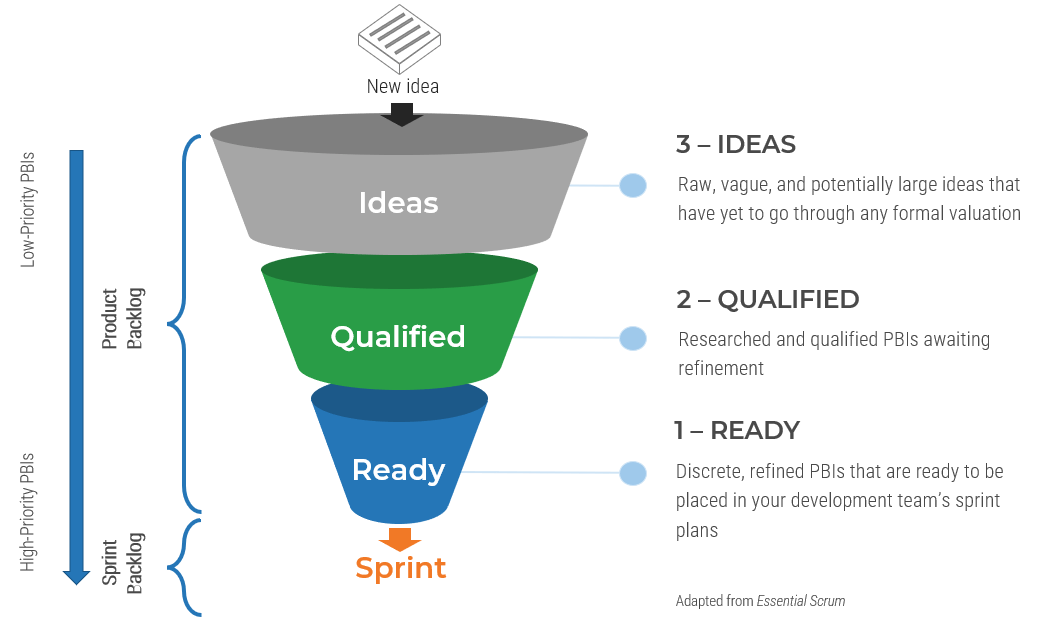
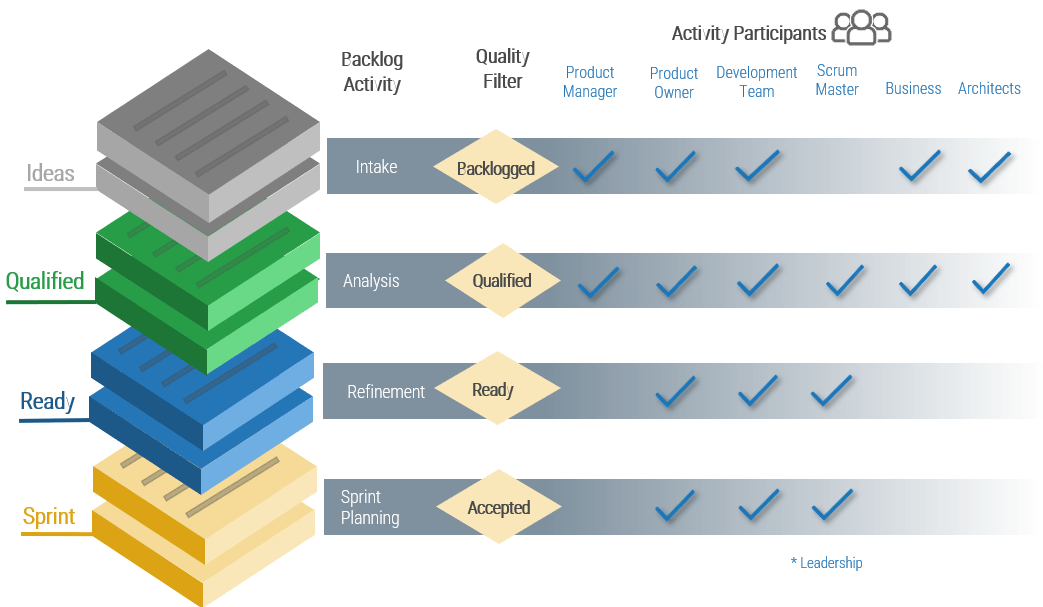
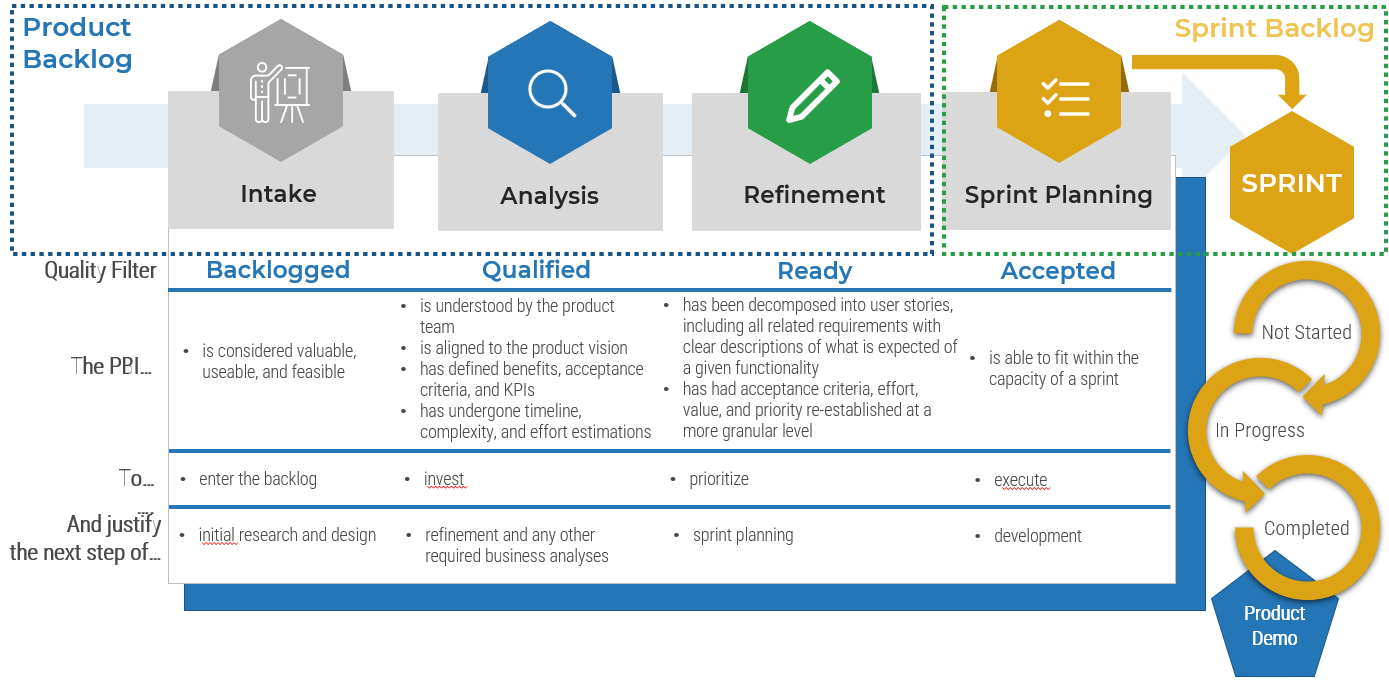
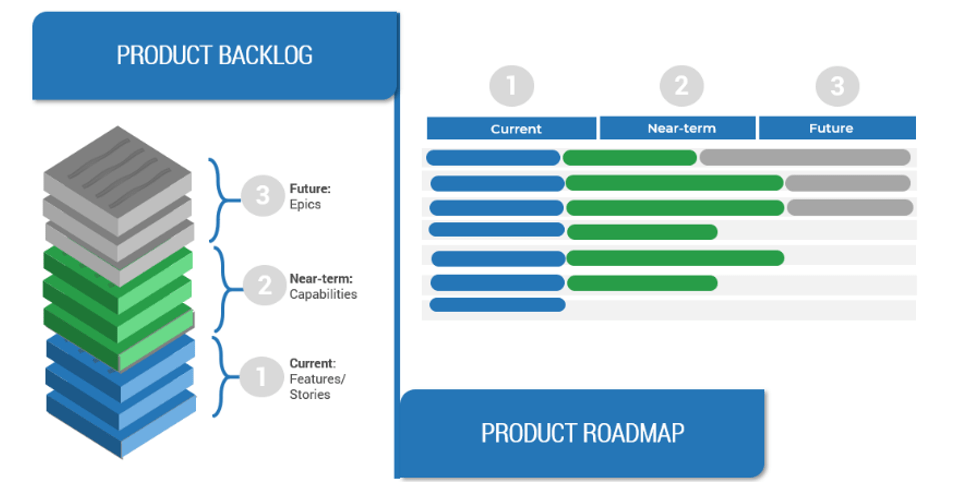
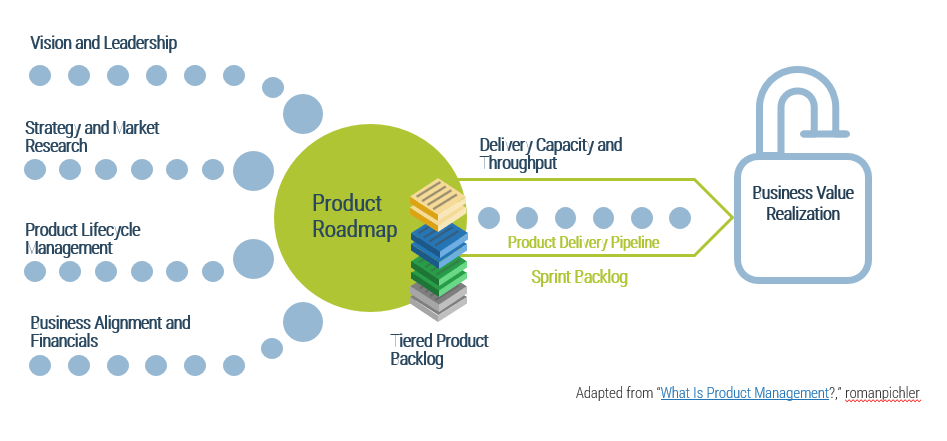

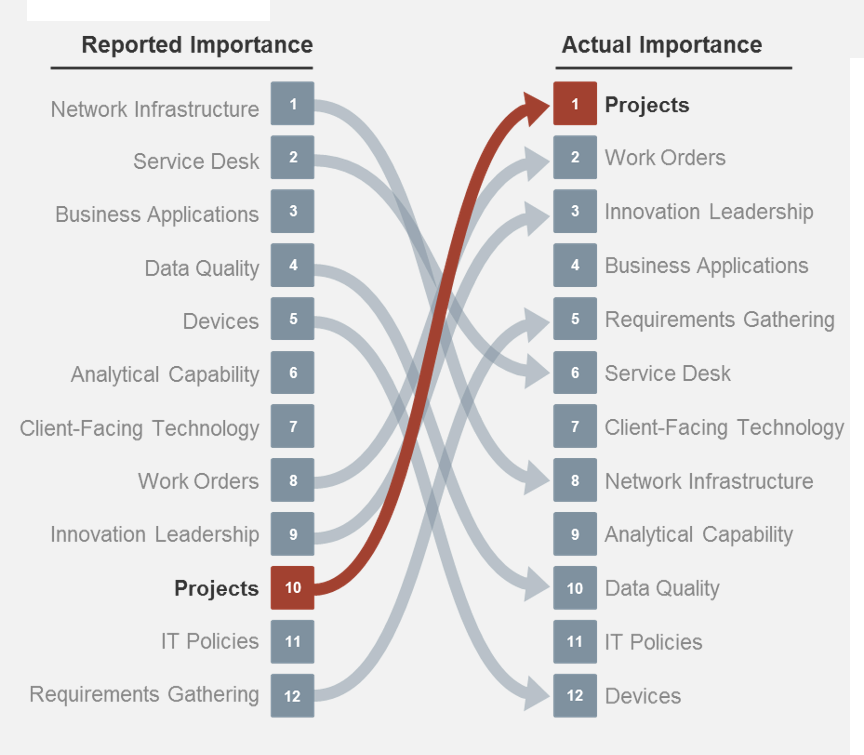
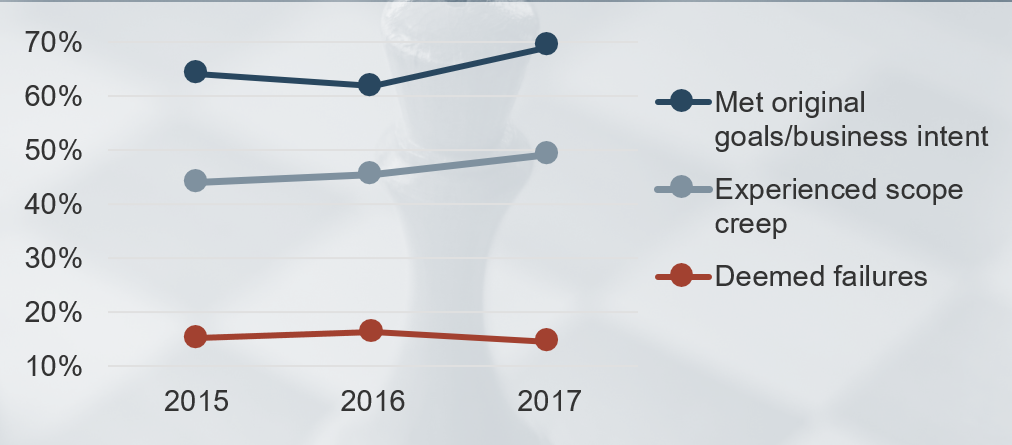
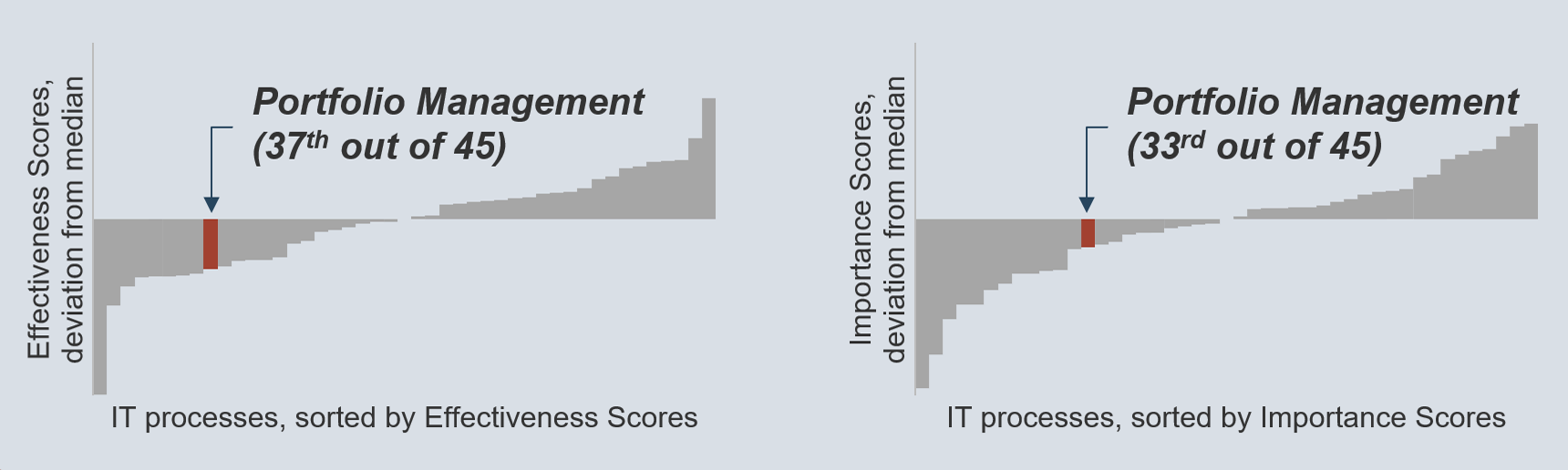
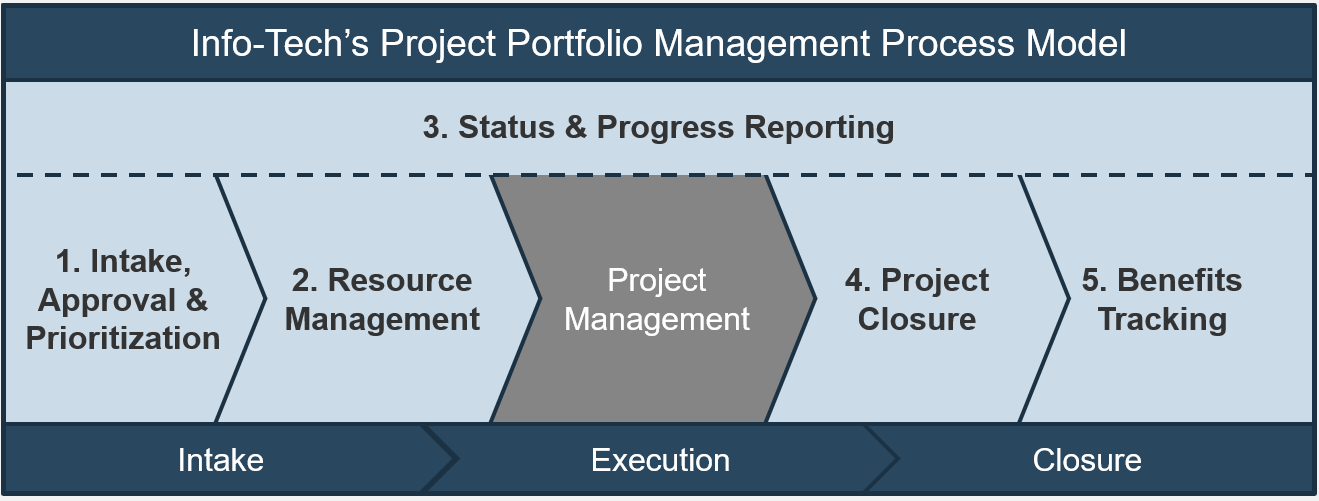
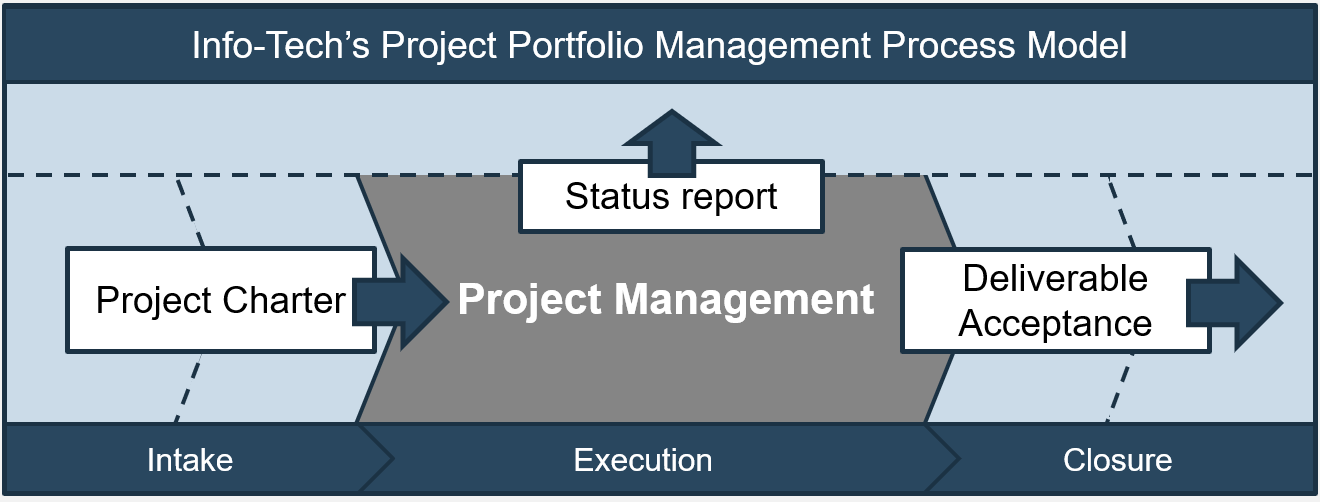
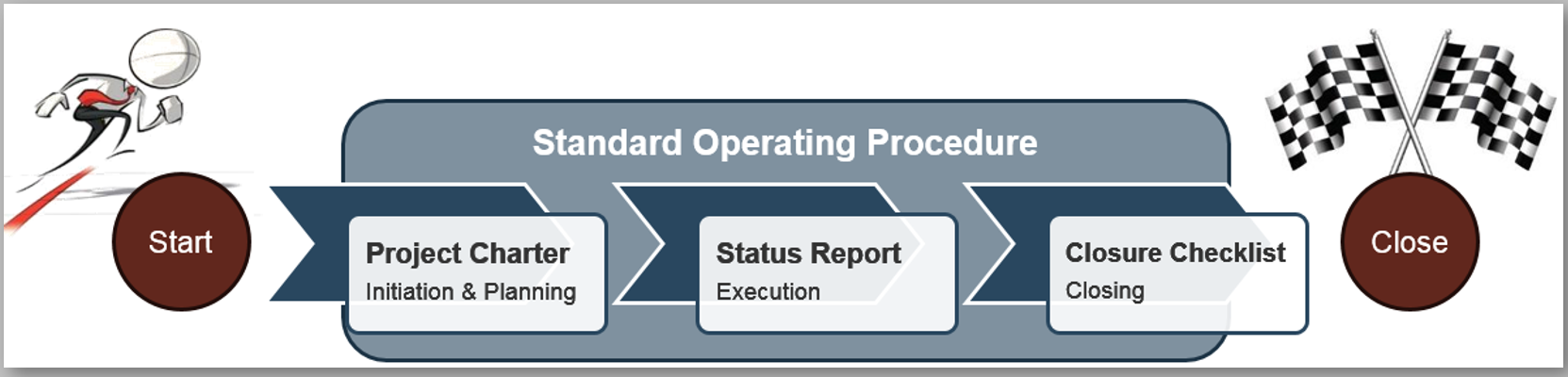






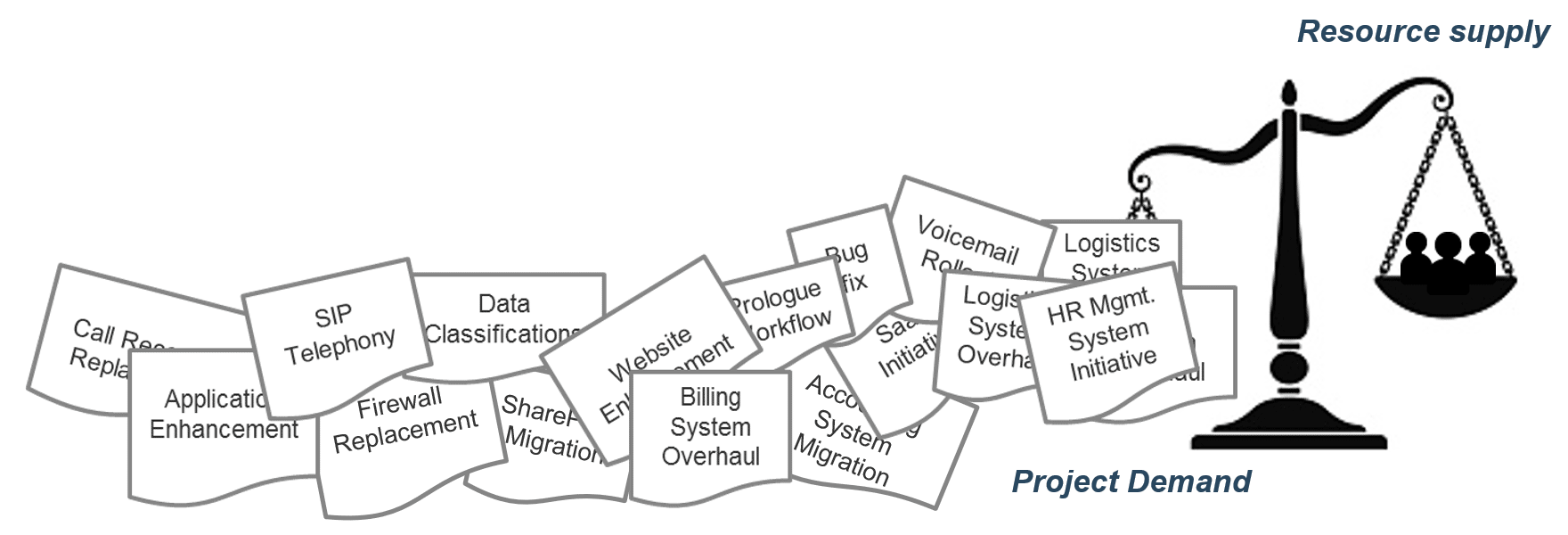
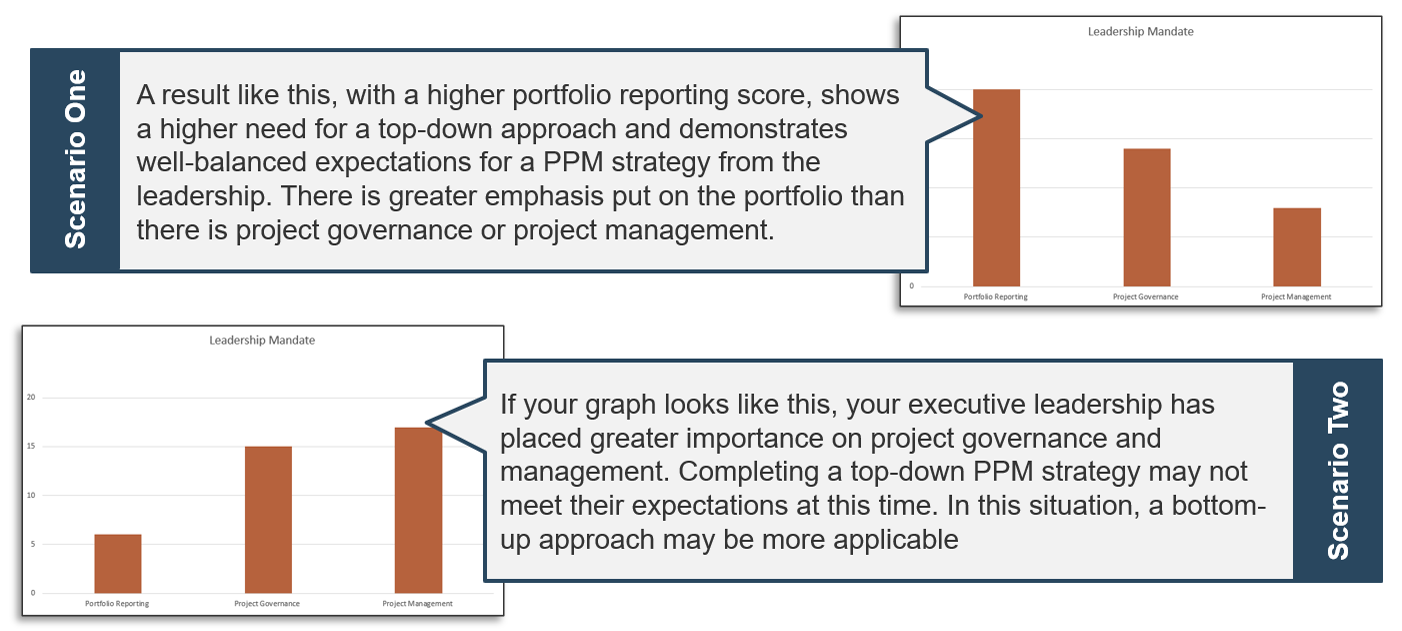
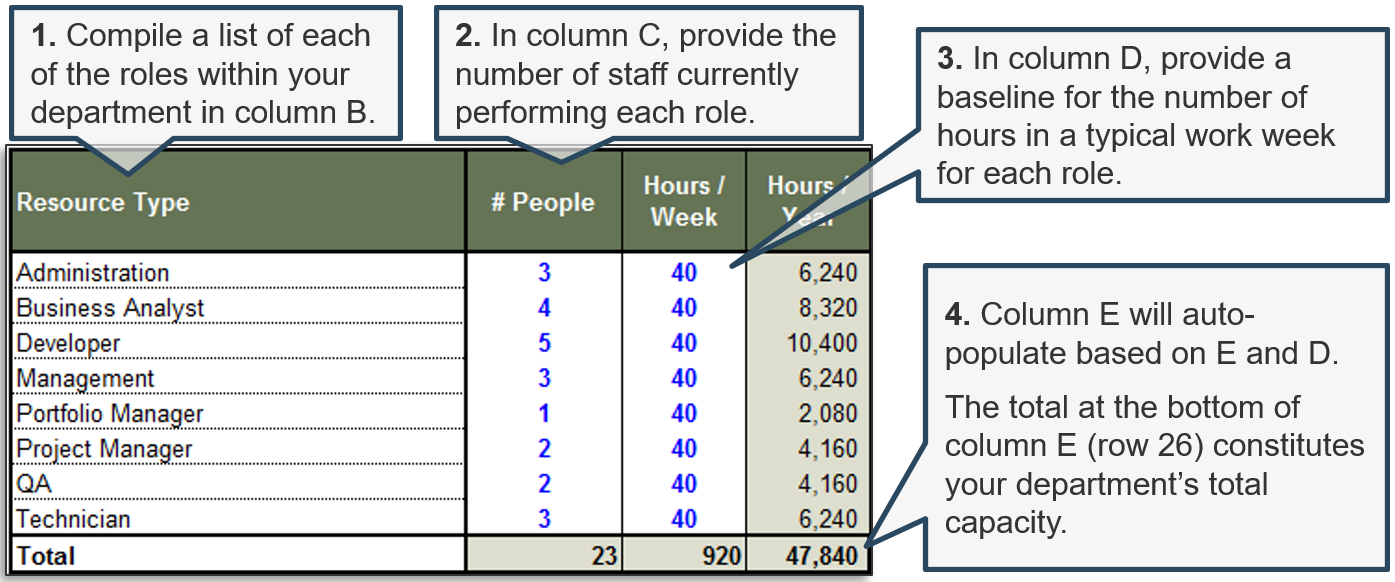
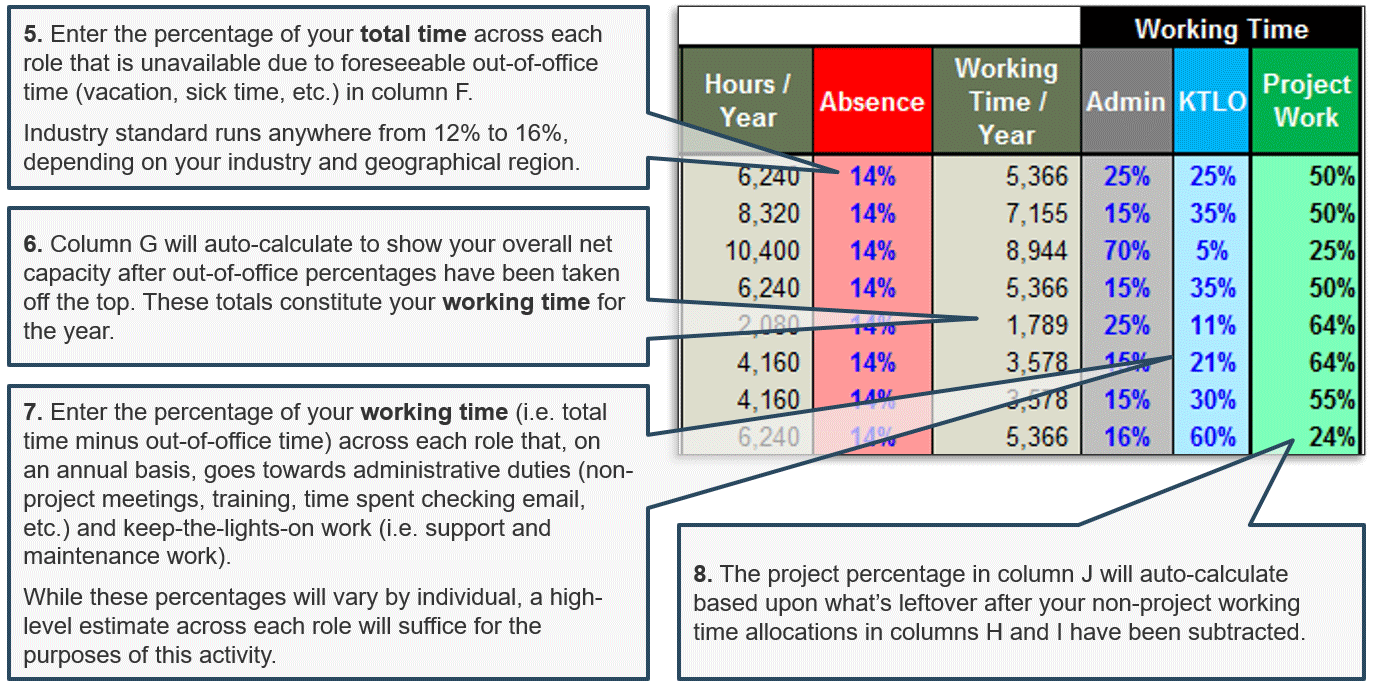
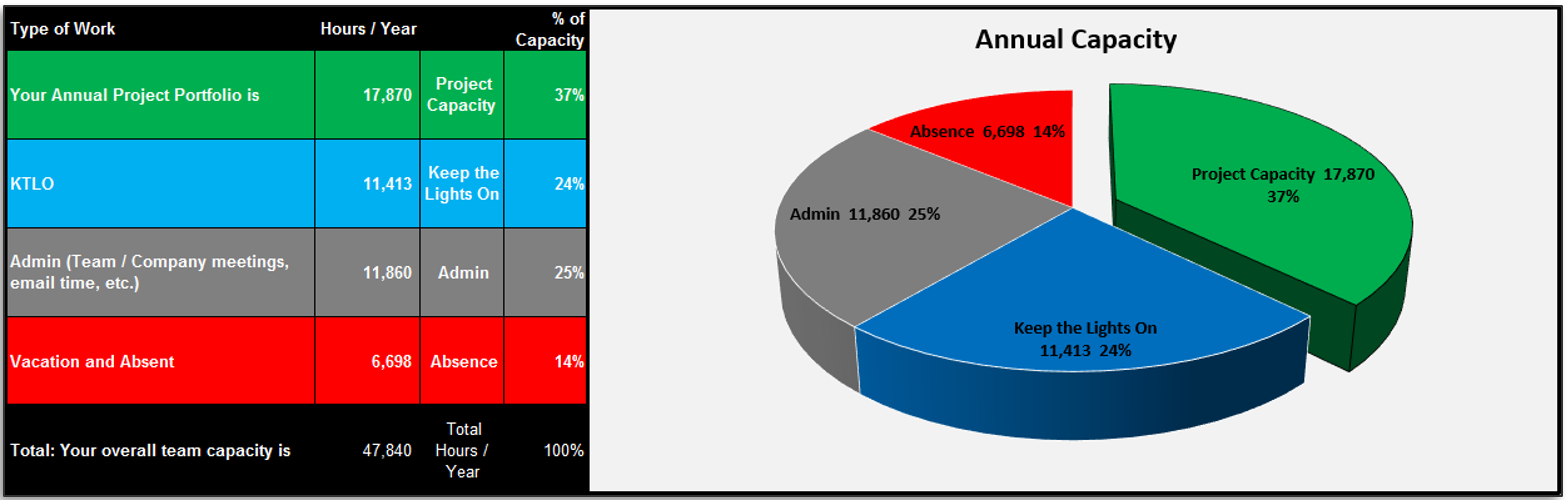
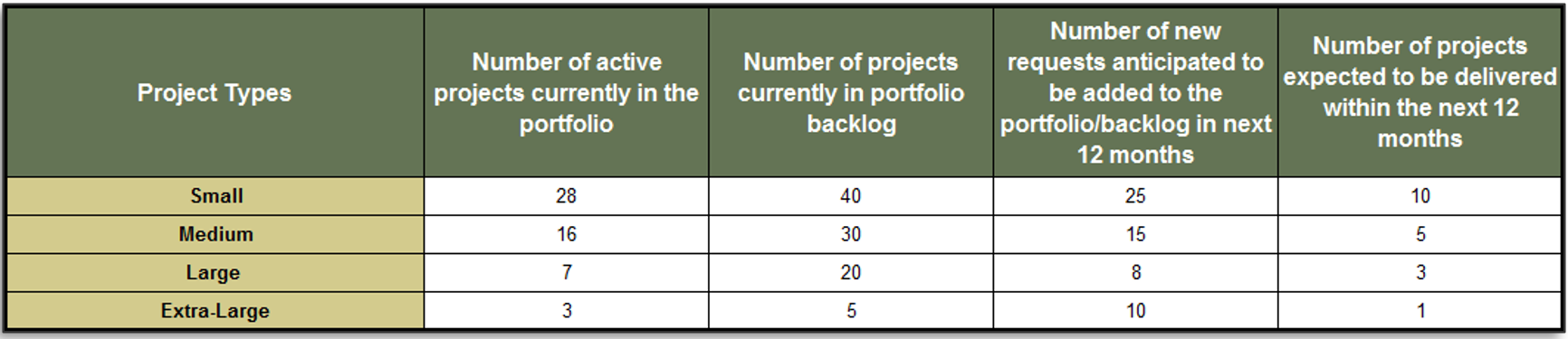
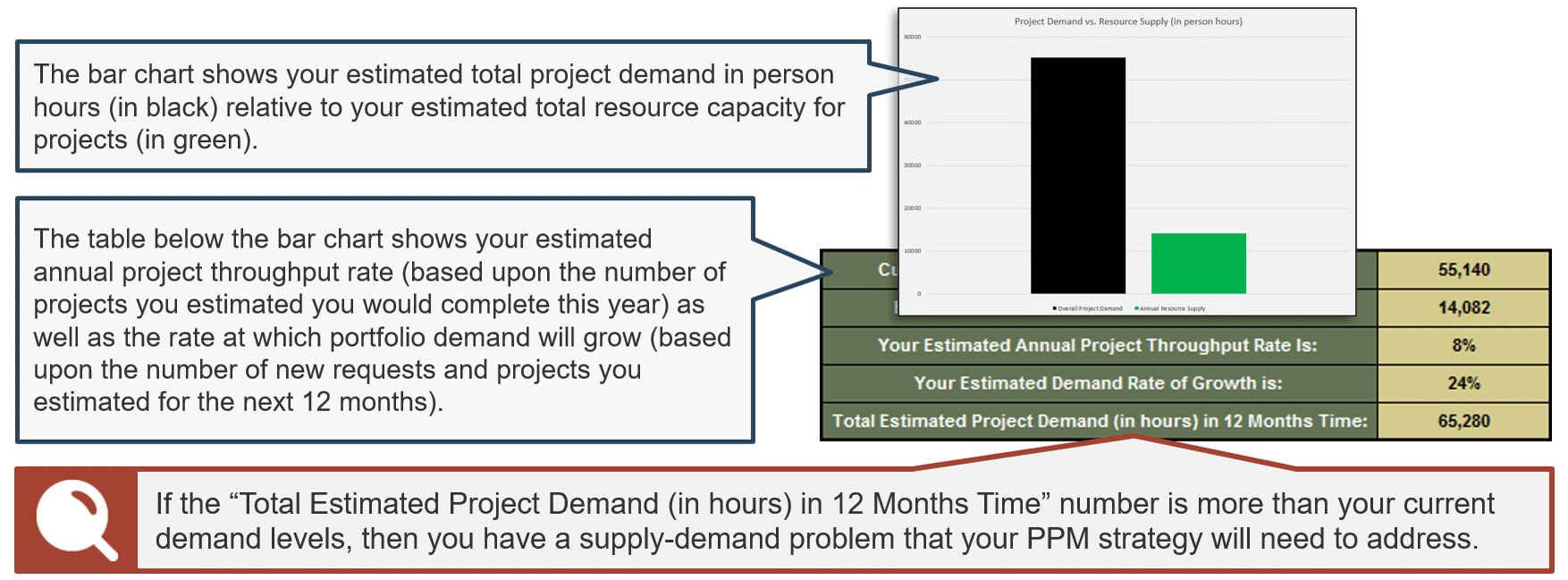
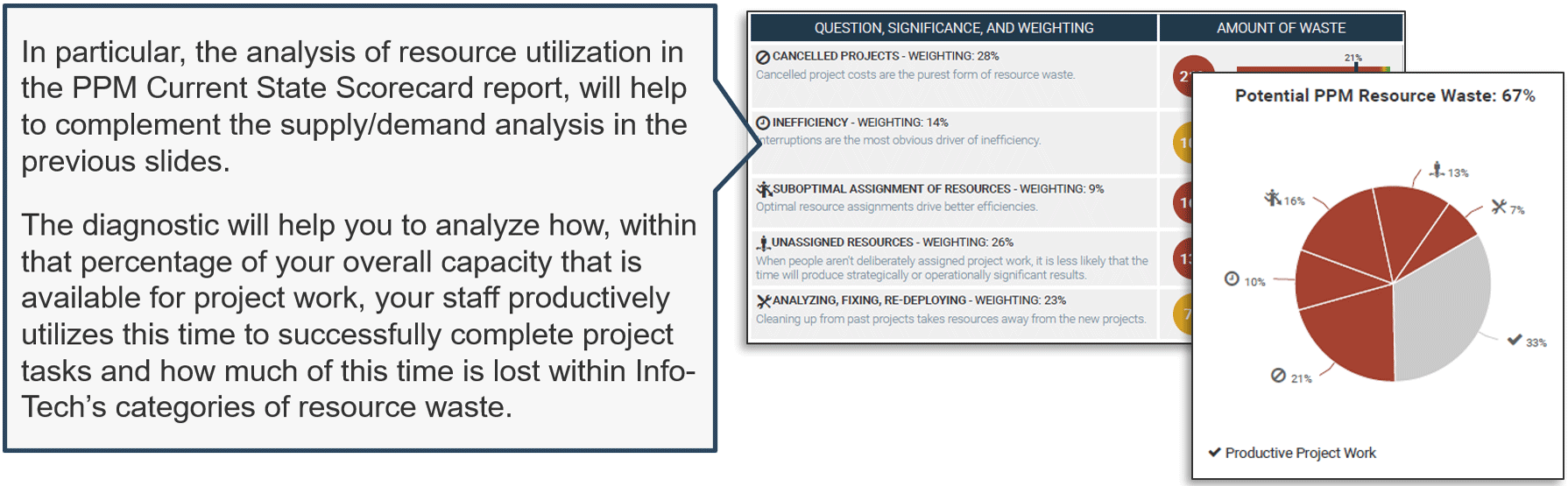

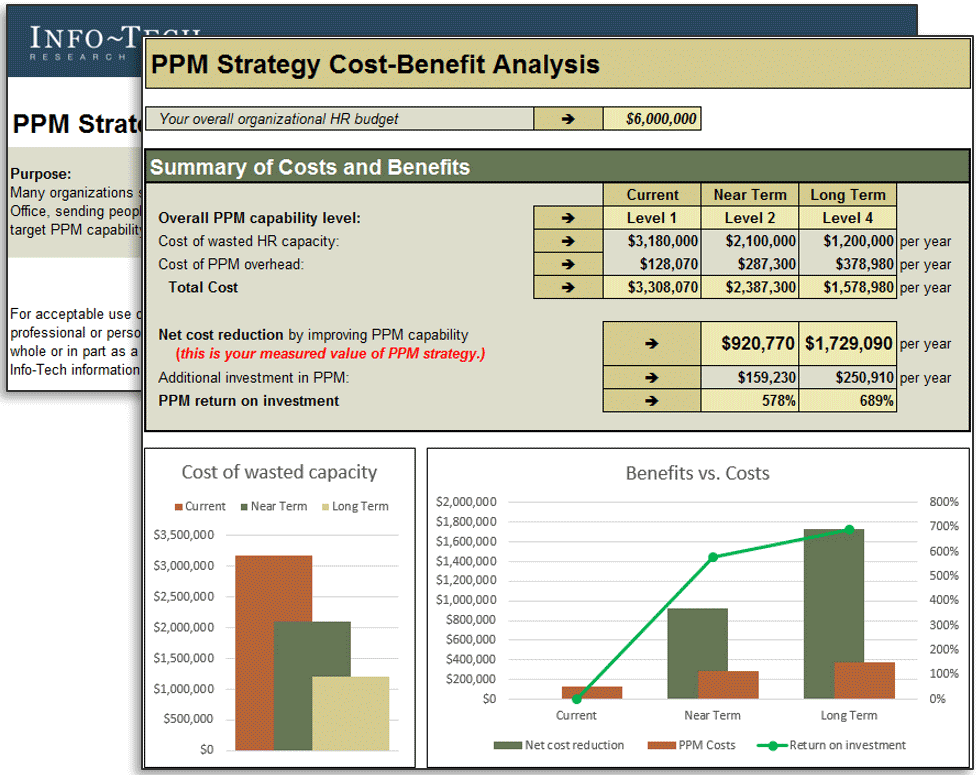
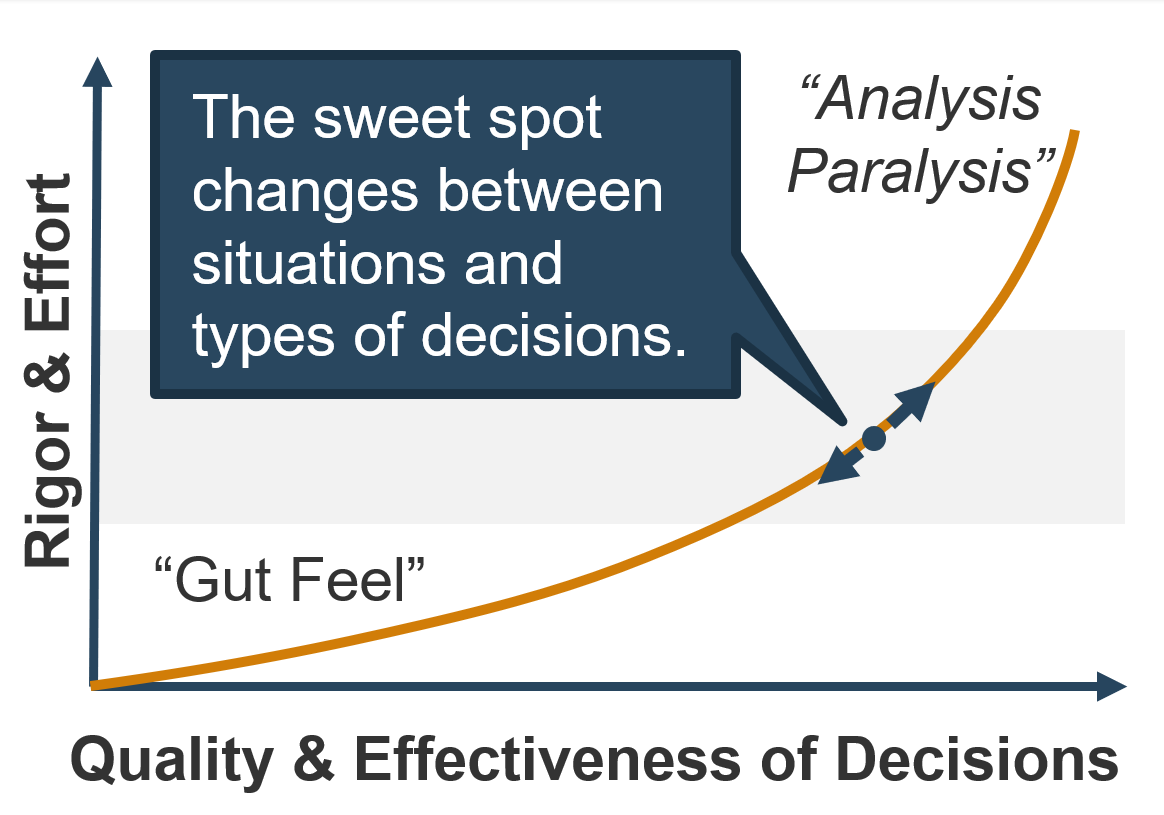
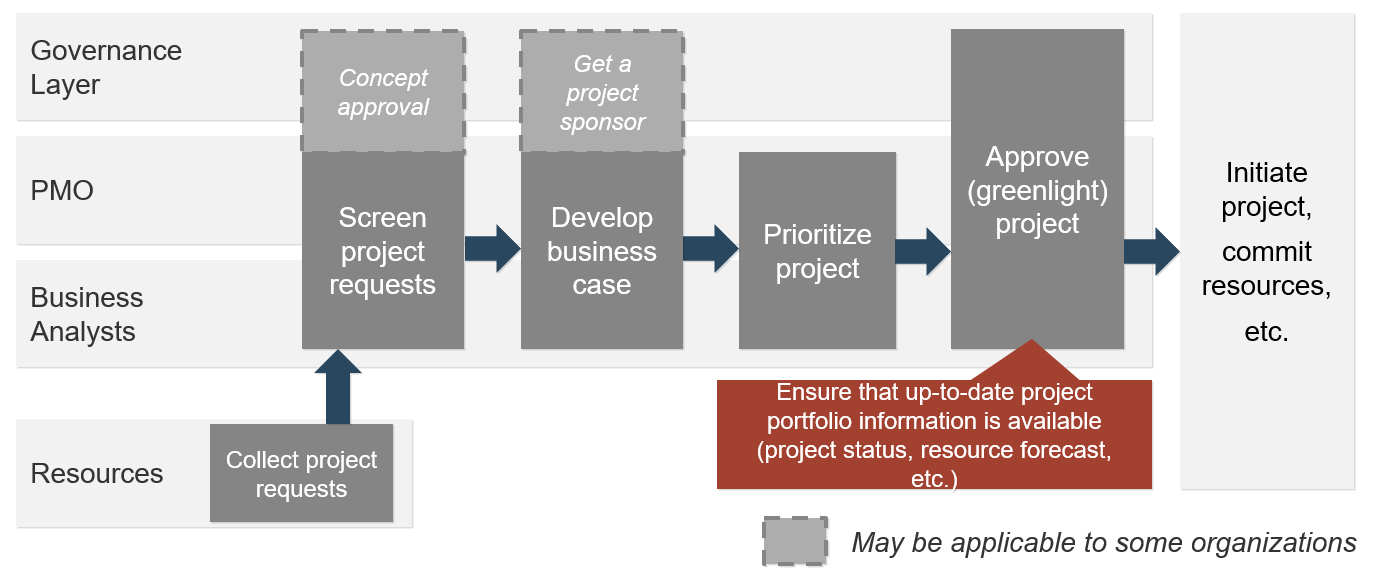
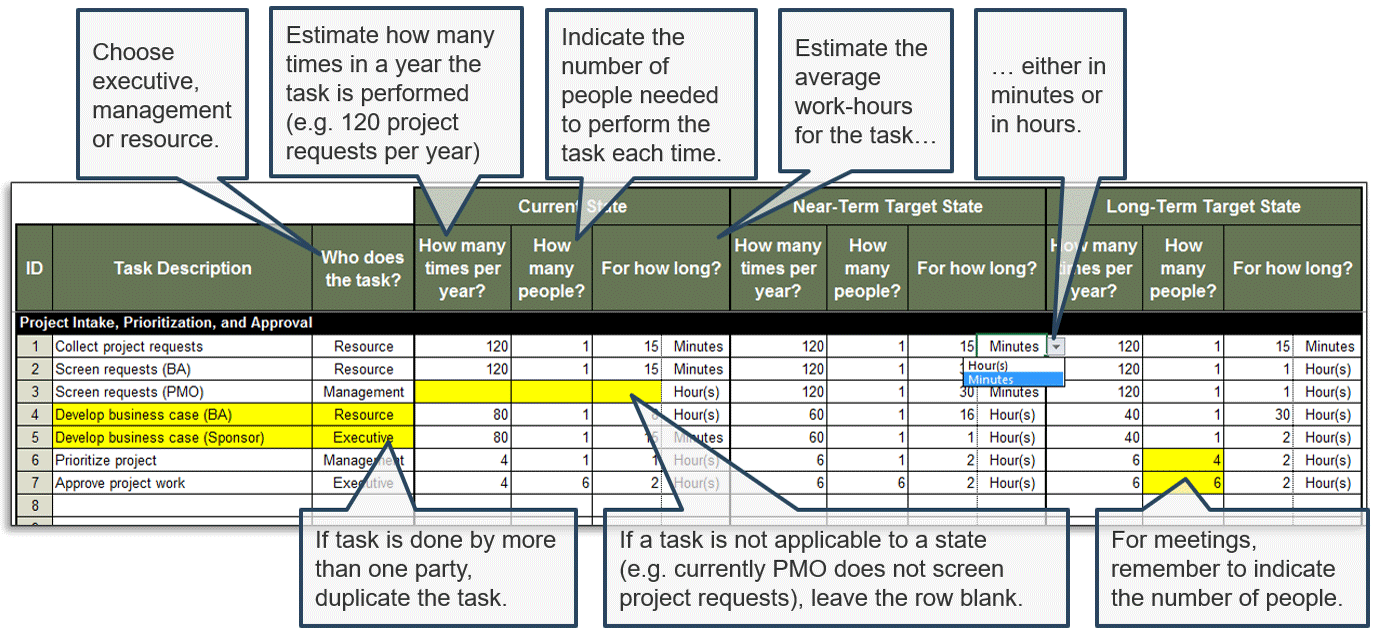

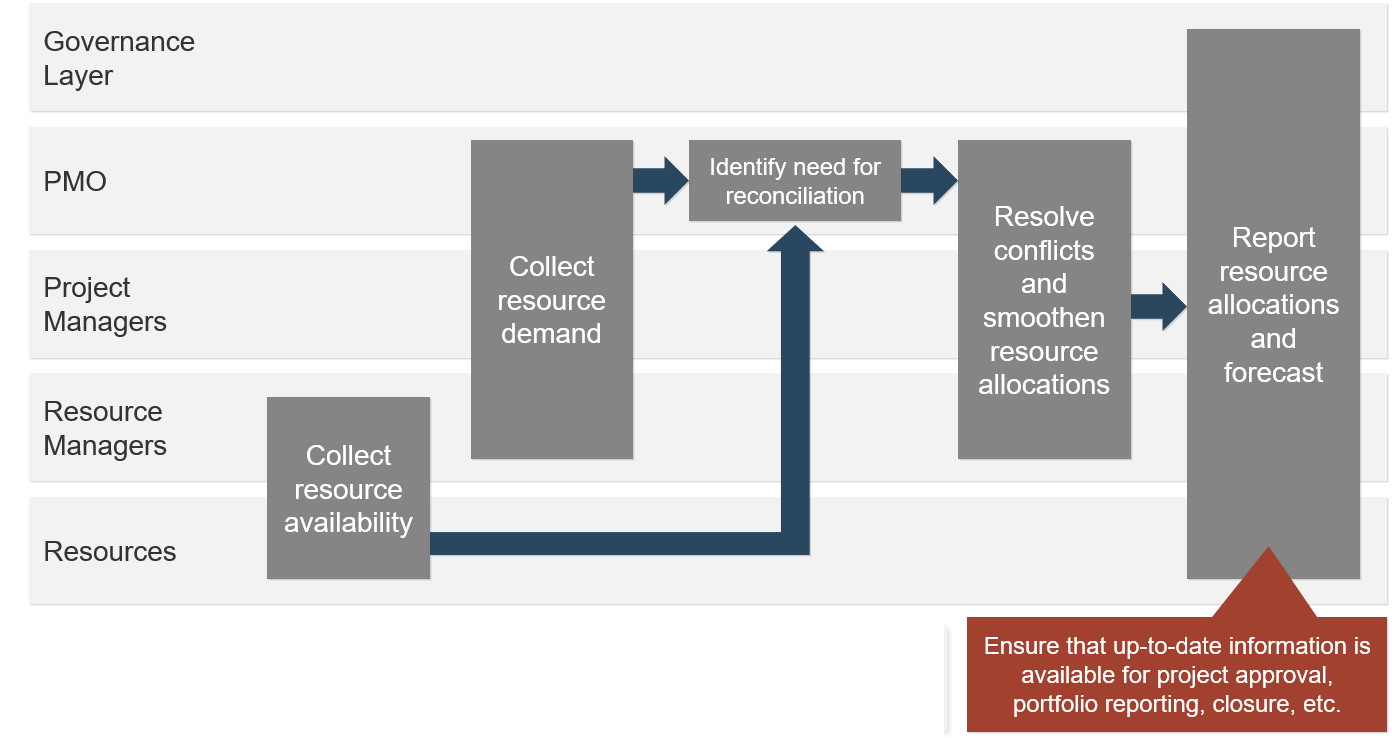
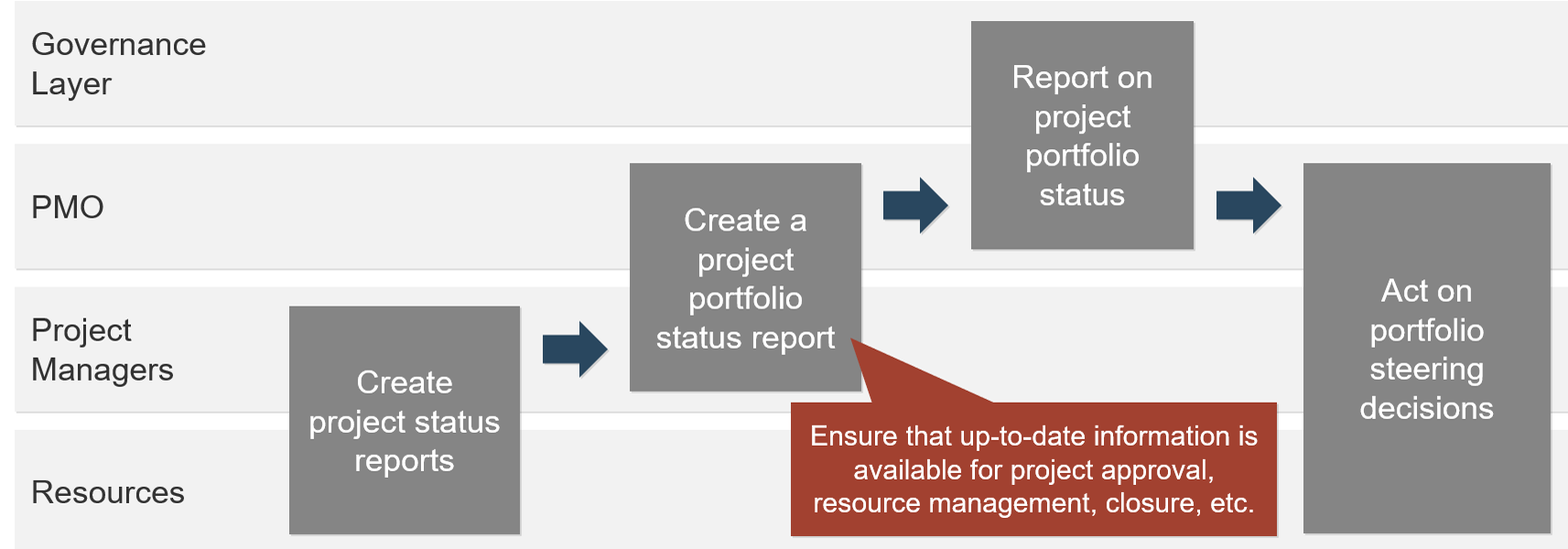
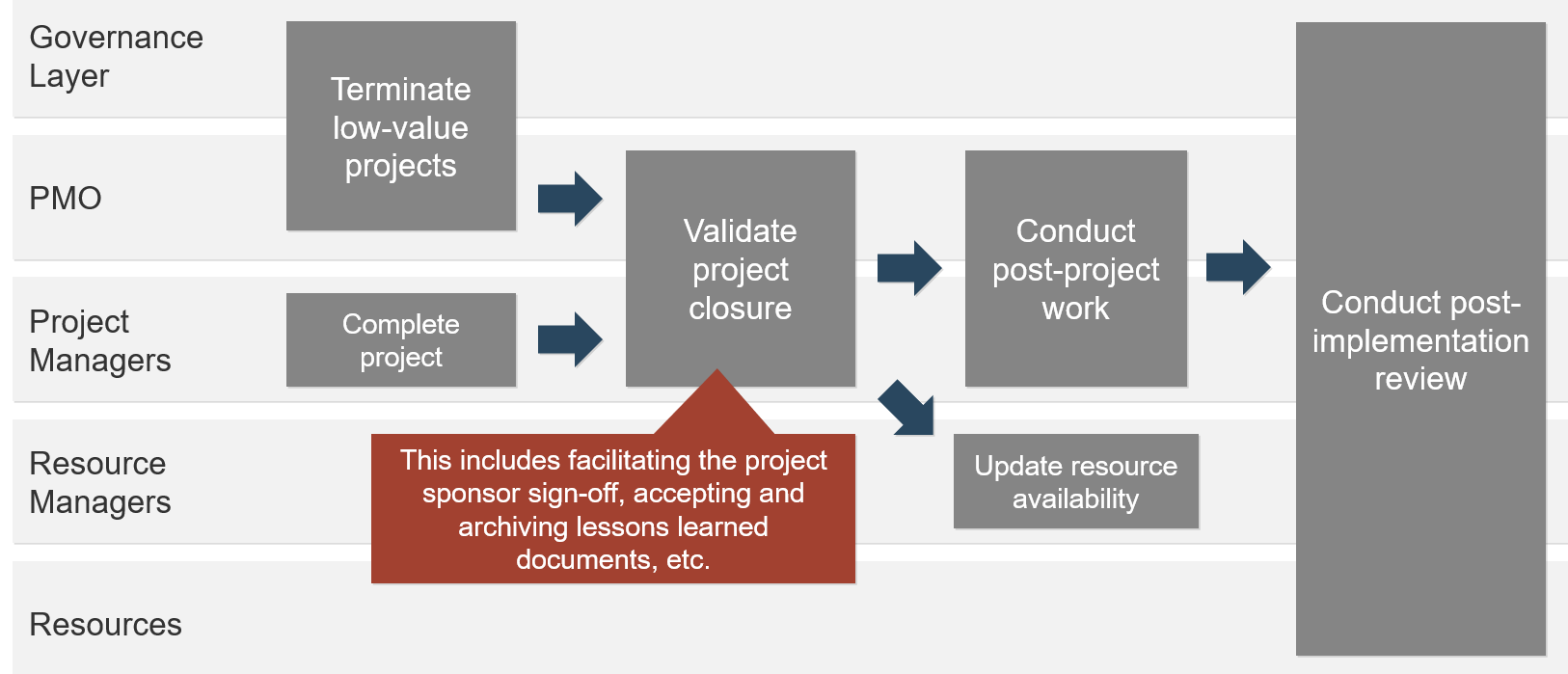
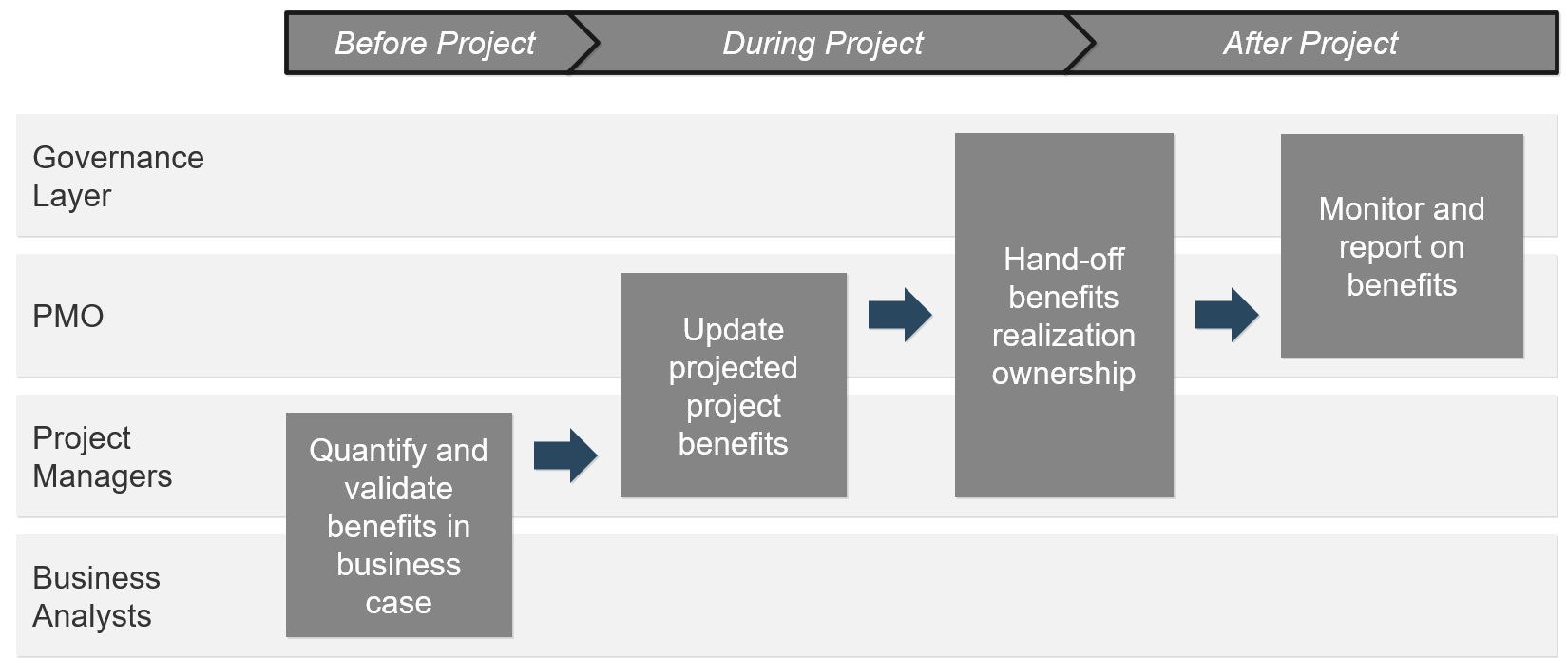
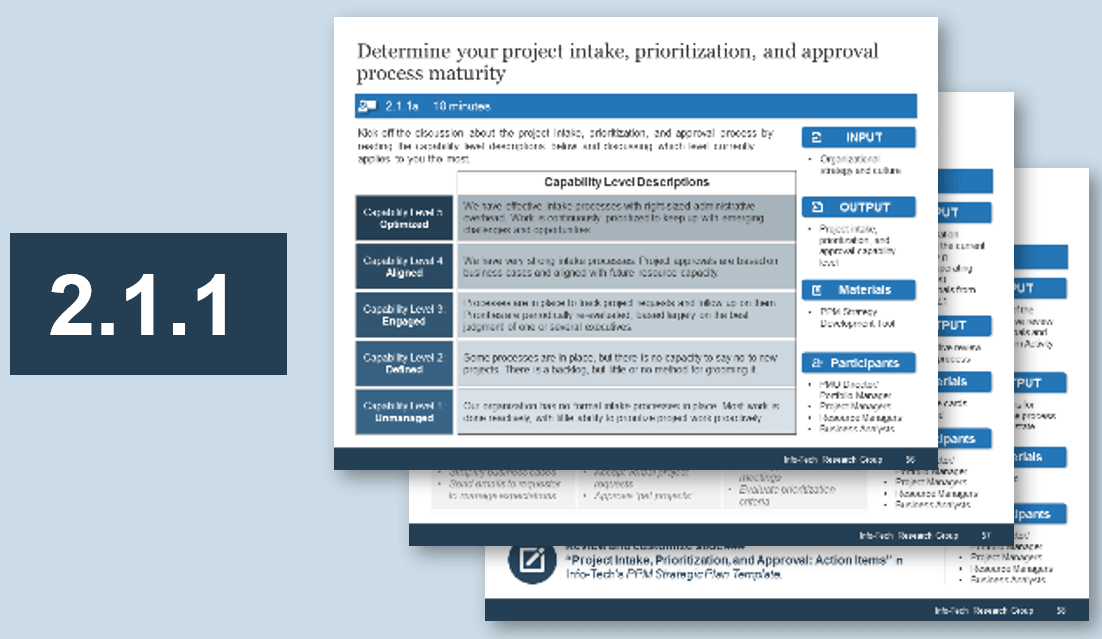
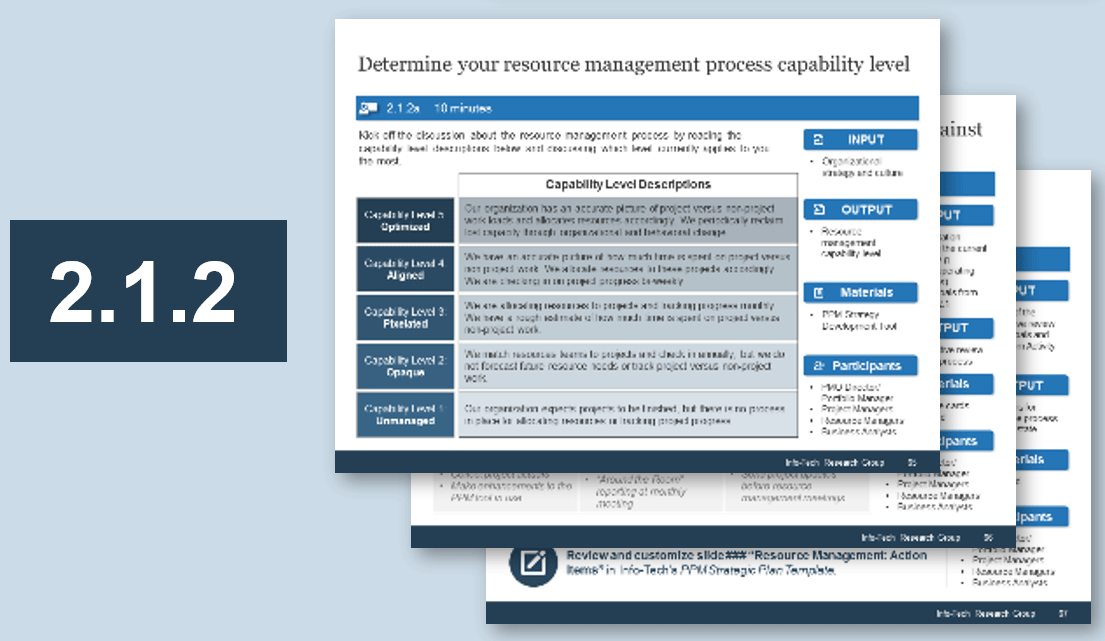
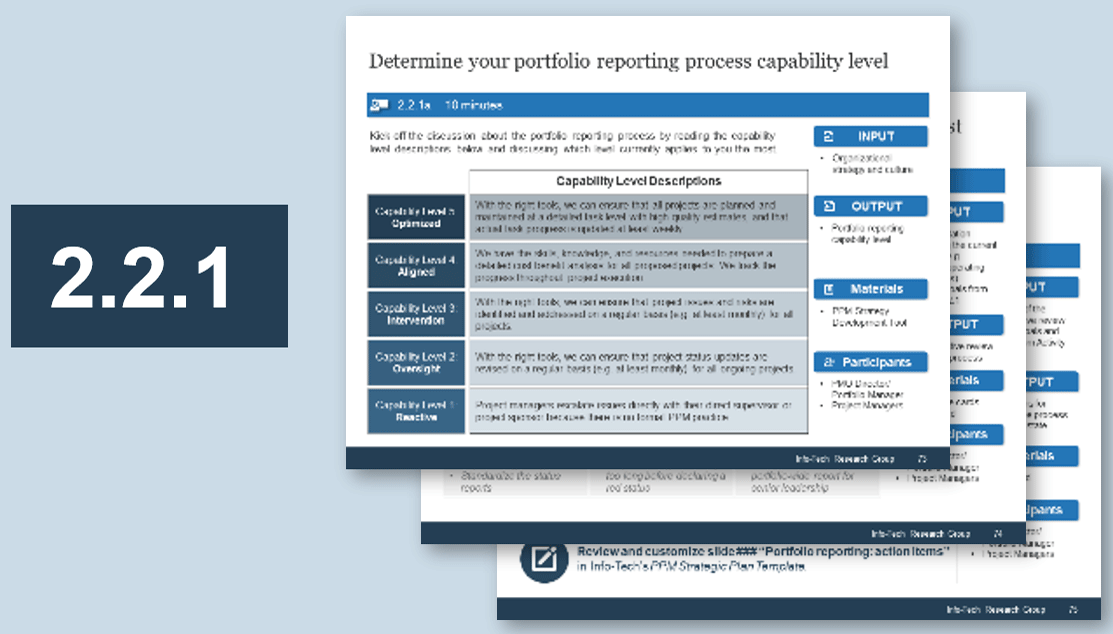
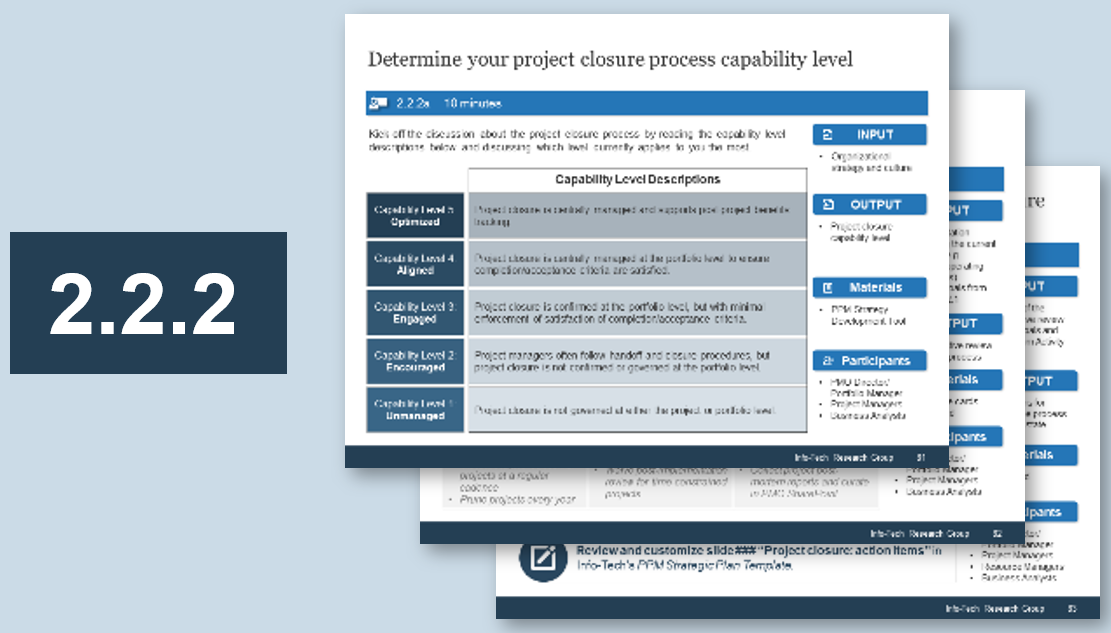
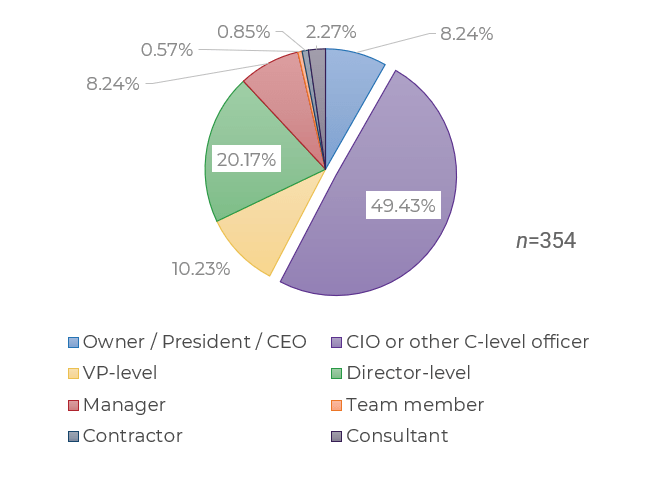
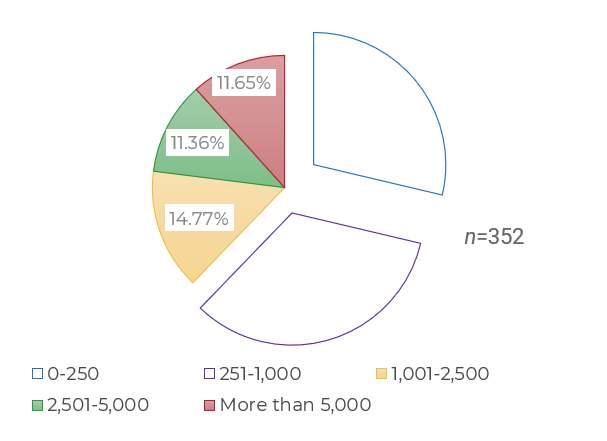
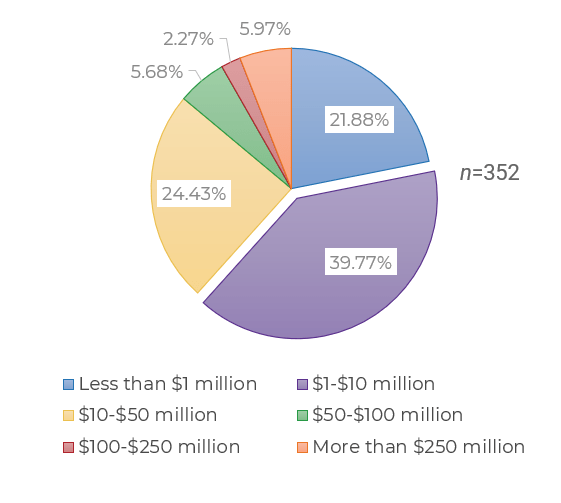
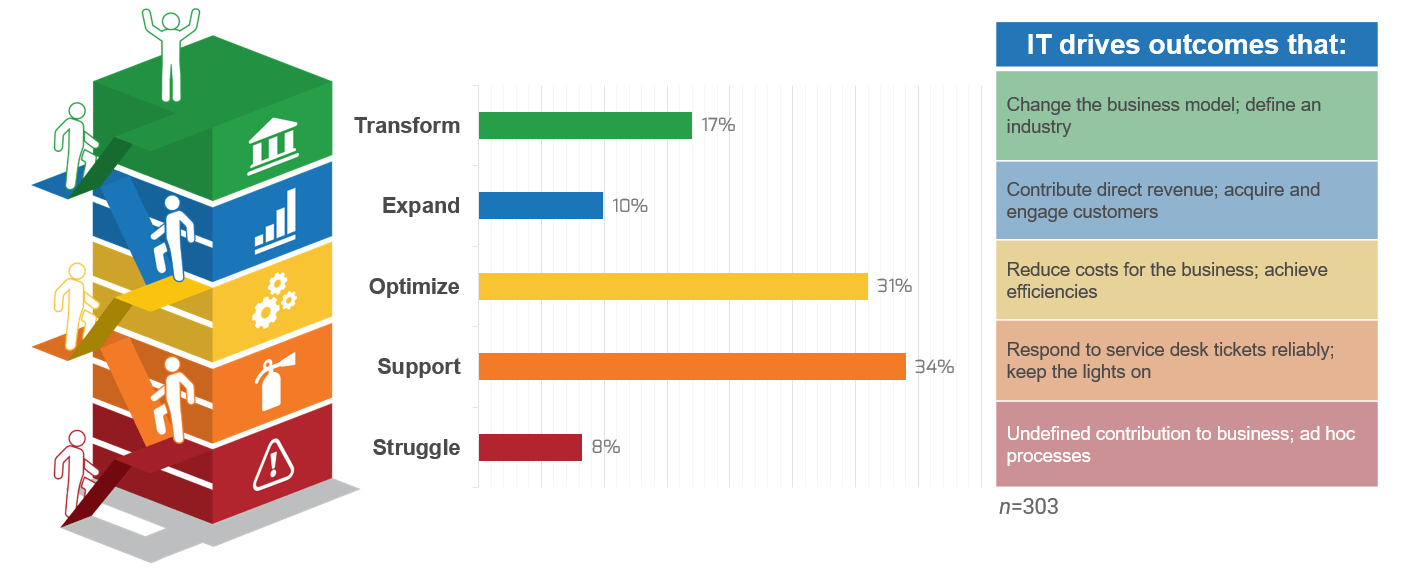
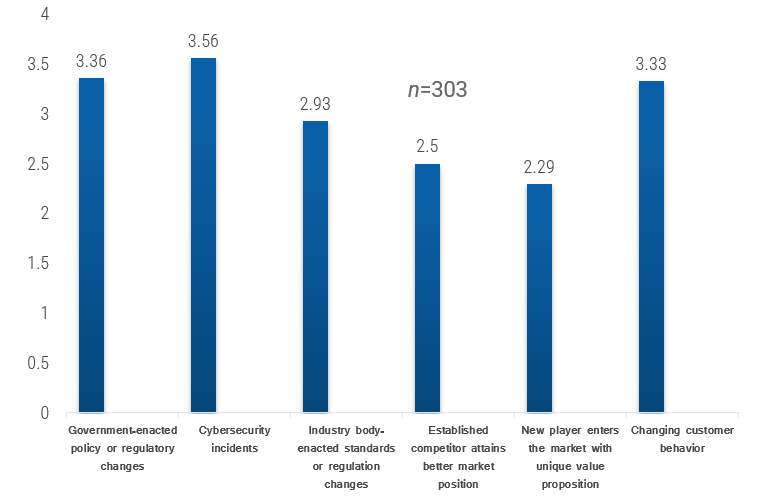
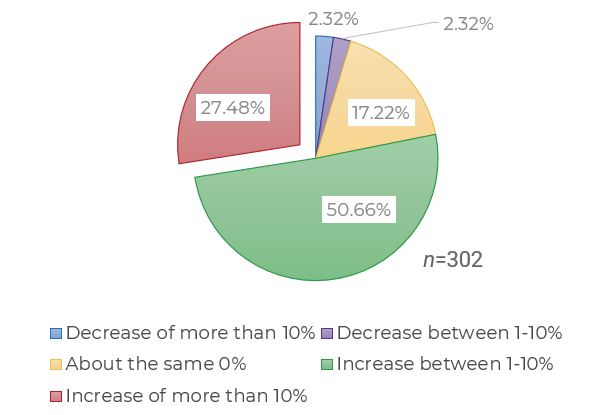
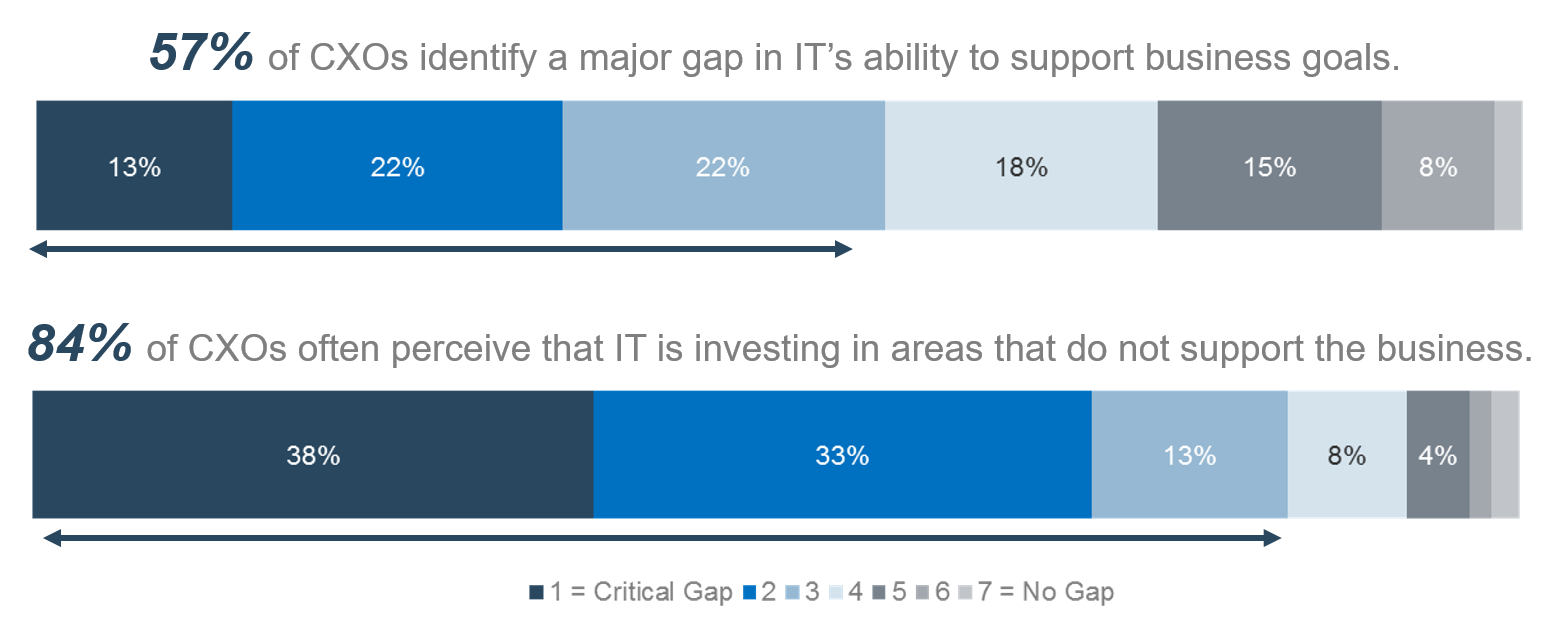
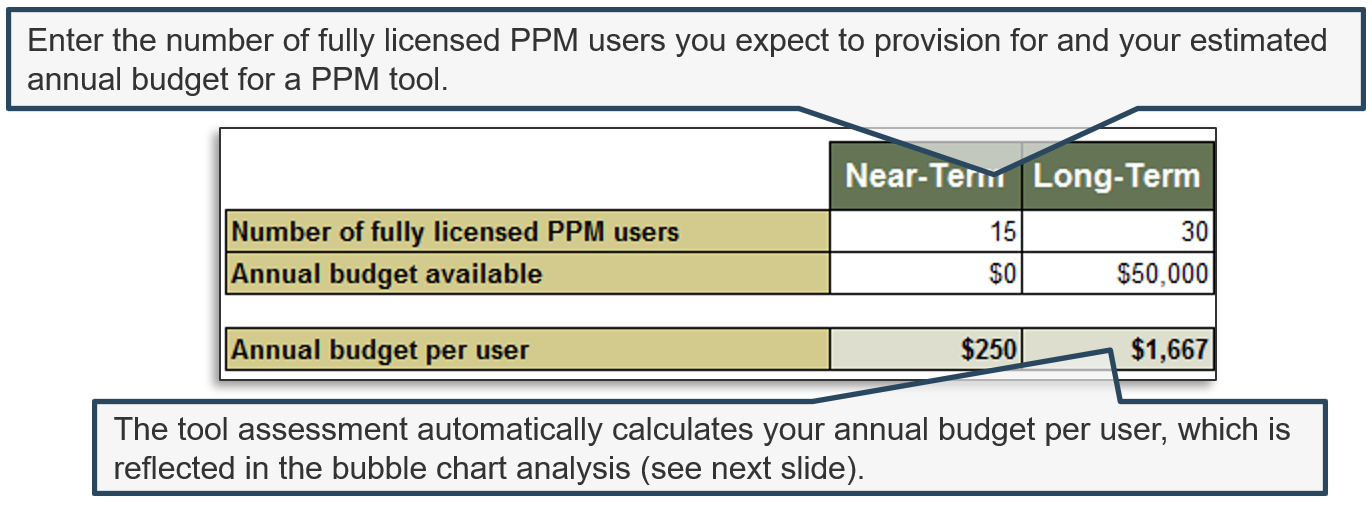
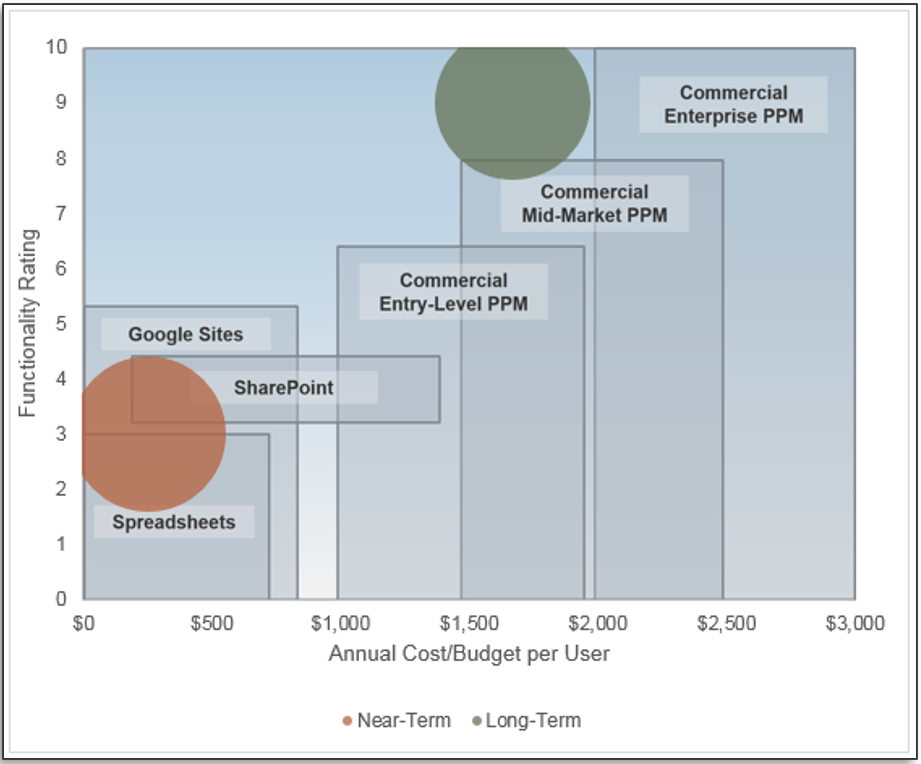
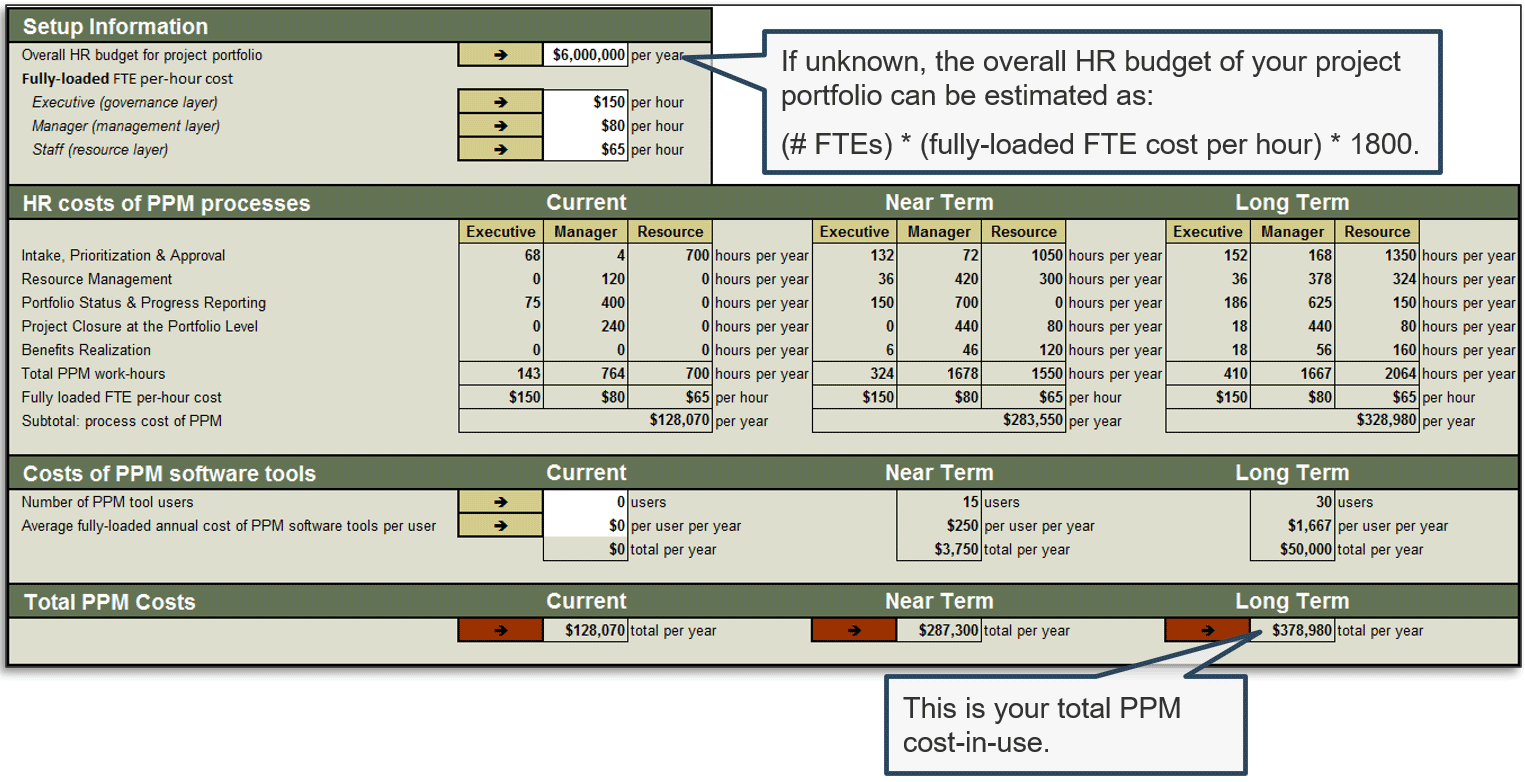
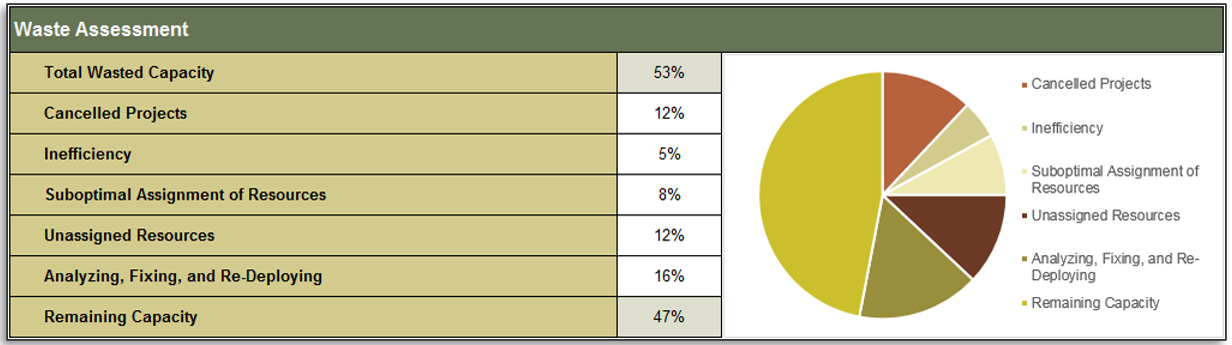
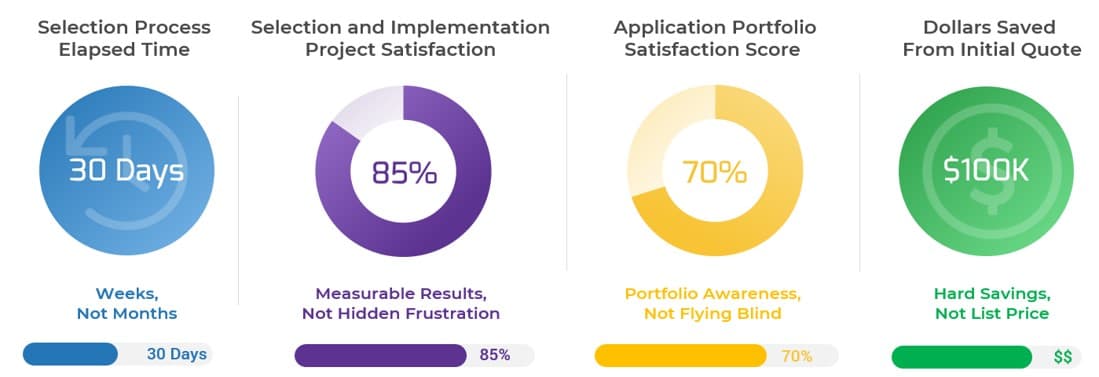
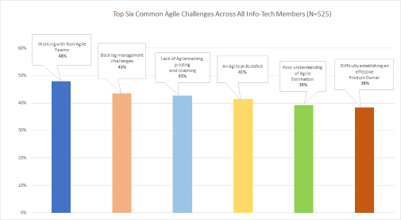
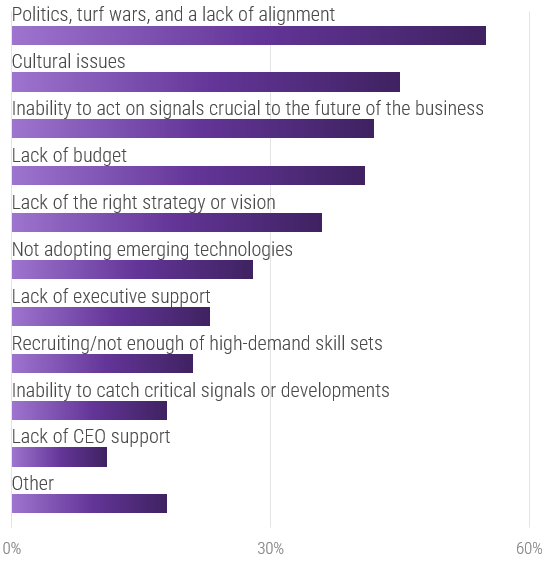
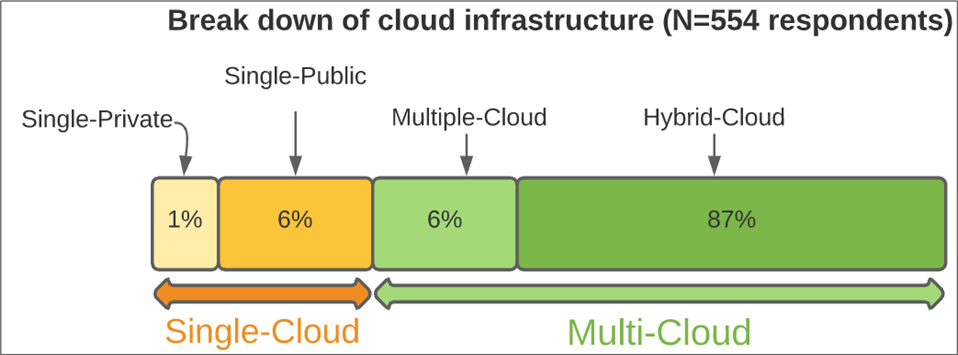
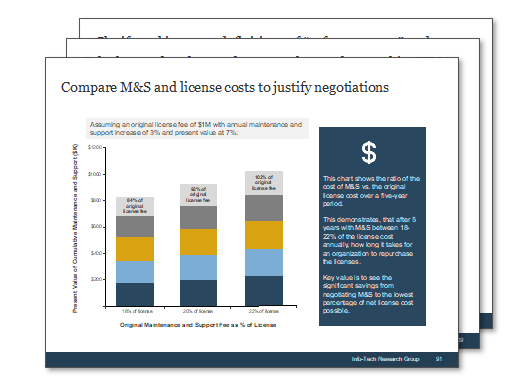
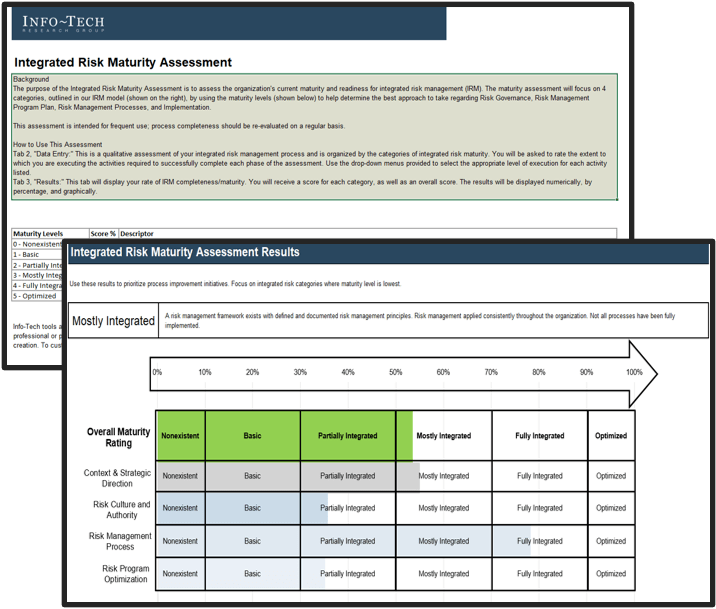
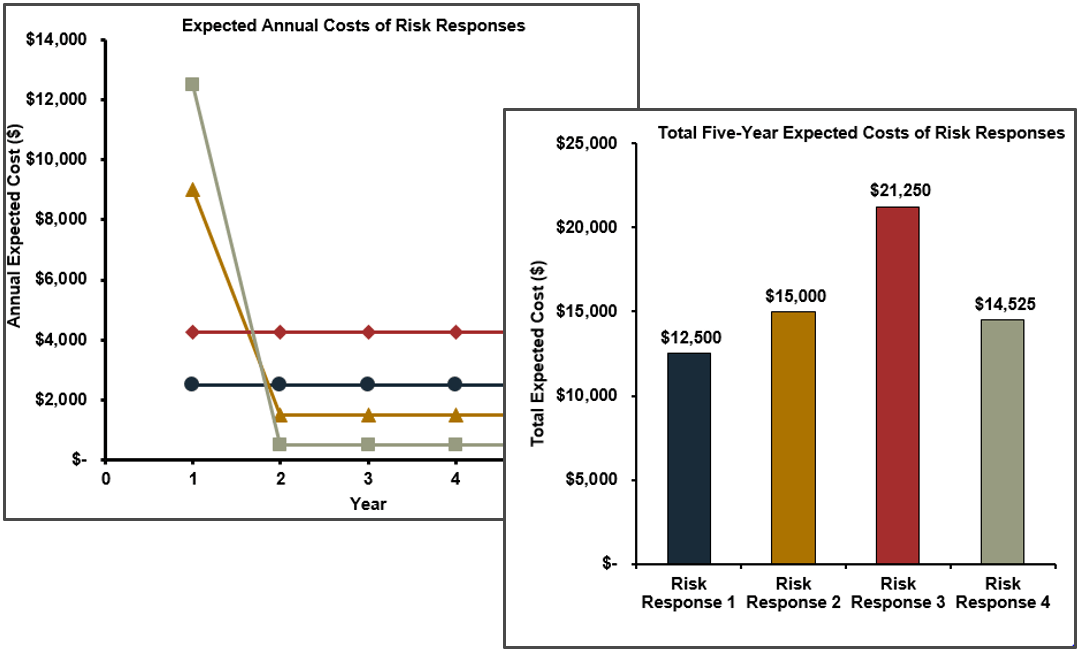
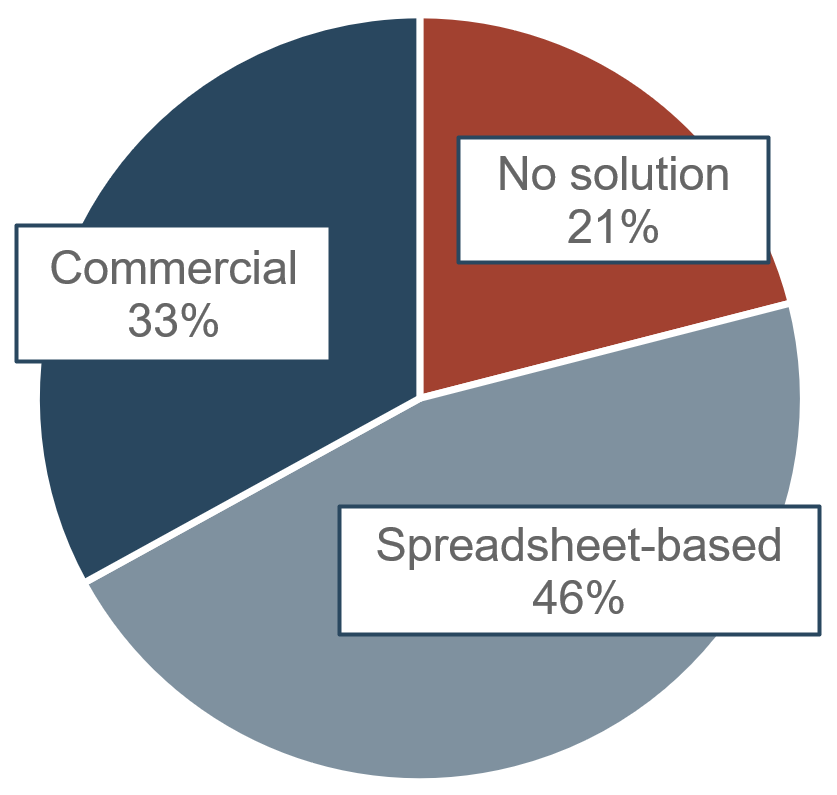 (Source: Info-Tech Research Group (2016), N=433)
(Source: Info-Tech Research Group (2016), N=433)































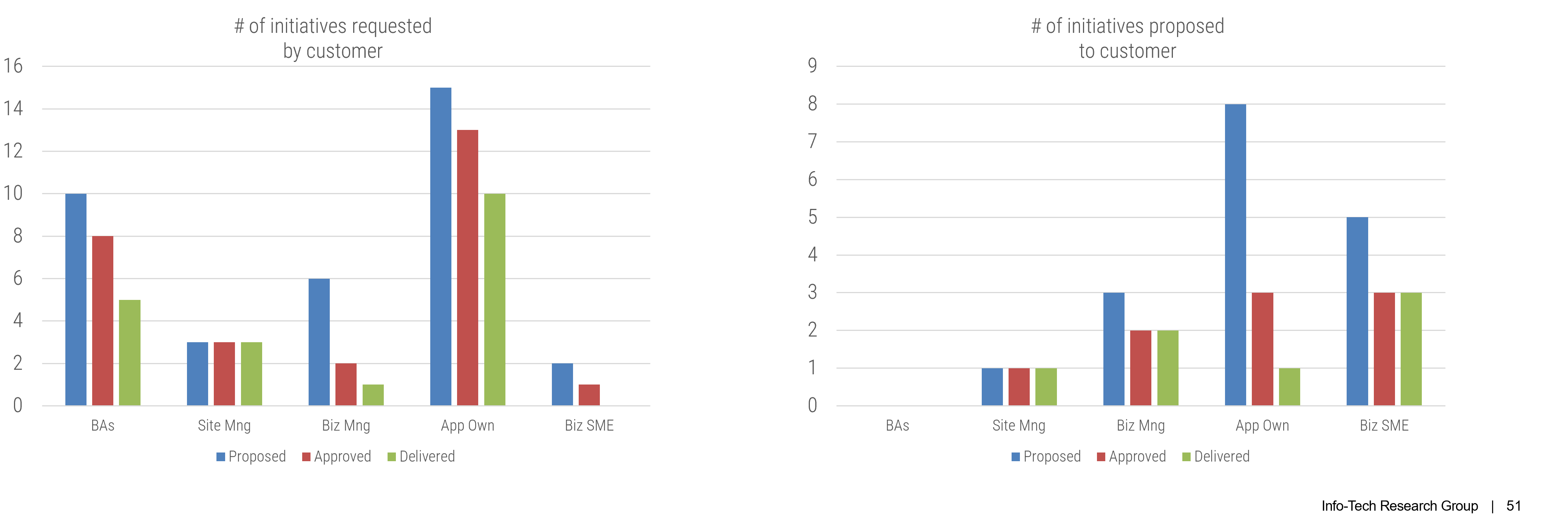



































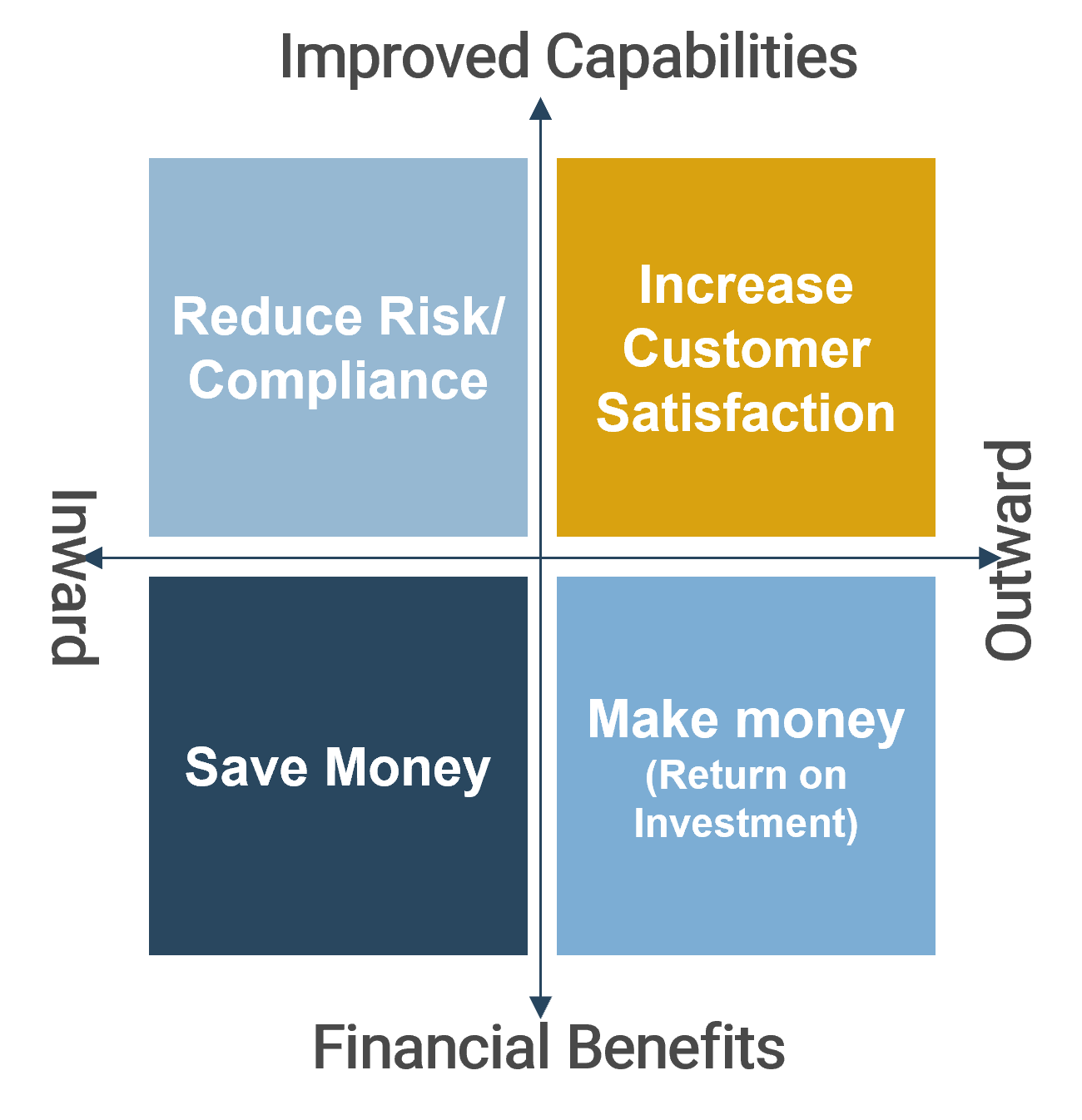
















































































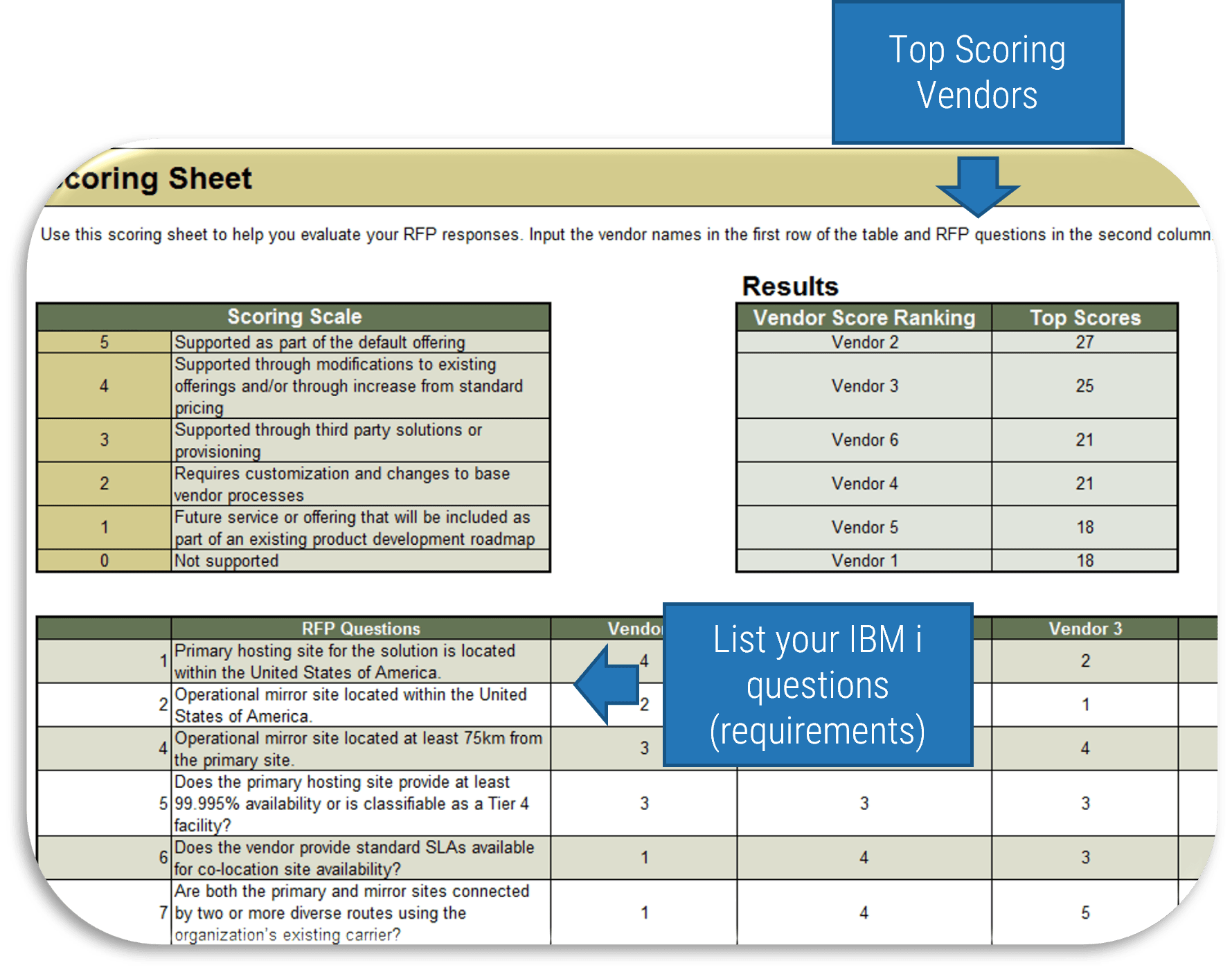
![Map different 'IBM i' scenarios with axes 'Importance to Business Outcomes - Low to High' and 'Vendor’s Performance Advantage - Low to High'. Quadrant labels are '[LI/LA] Potentially Outsource: Service management, Help desk, desk-side support, Asset management', '[LI/HA] Outsource: Application & Infra Support, Web Hosting, SAP Support, Email Services, Infrastructure', '[HI/LA] Insource (For Now): Application development tech support', and '[HI/HA] Potentially Outsource: Onshore or offshore application maintenance'.](/images/ITMGF/infra-and-operations/i-and-o-process-management/strategy-and-organizational-design/ibm-i-migration-considerations/04-ibmi-map-importance-advantage.png)













































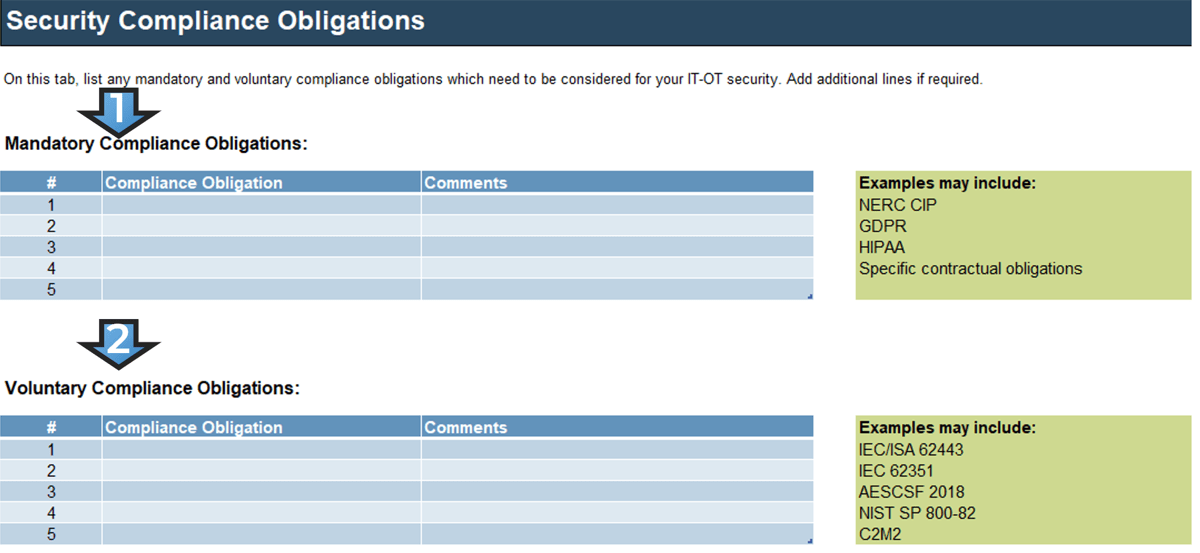
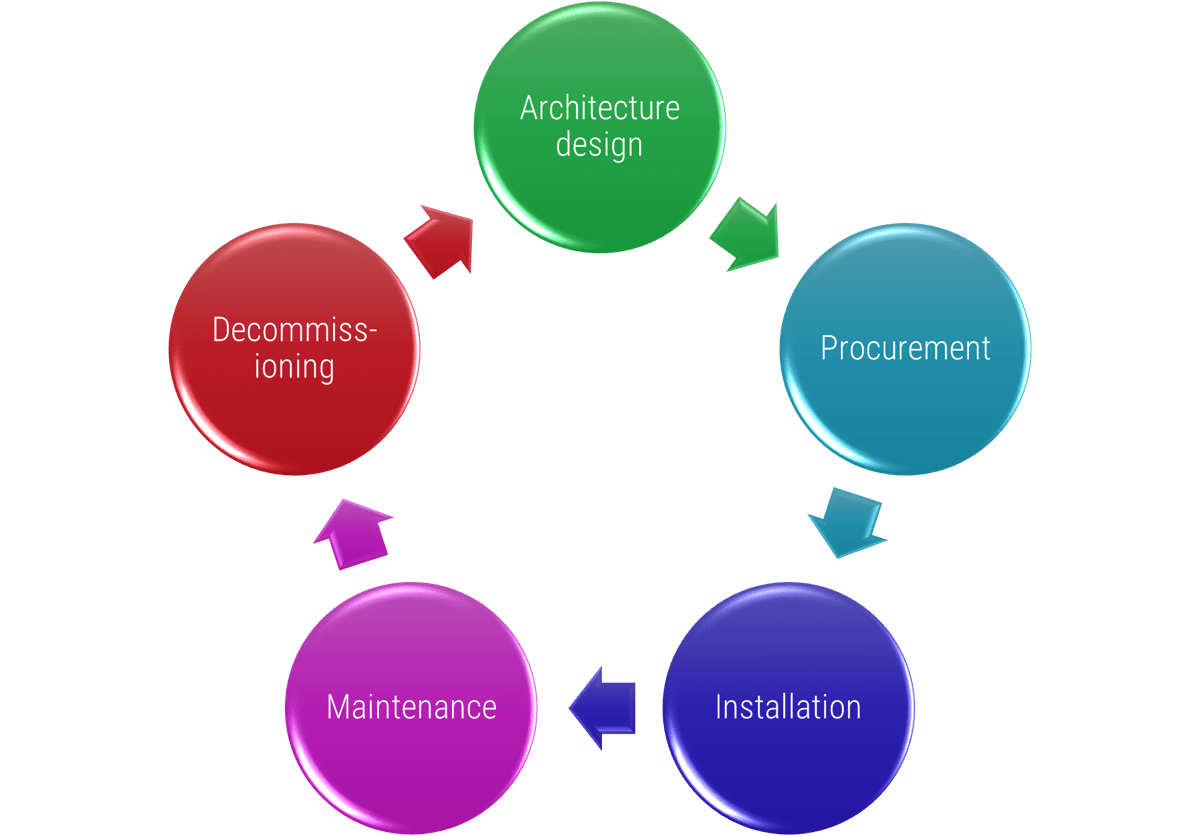
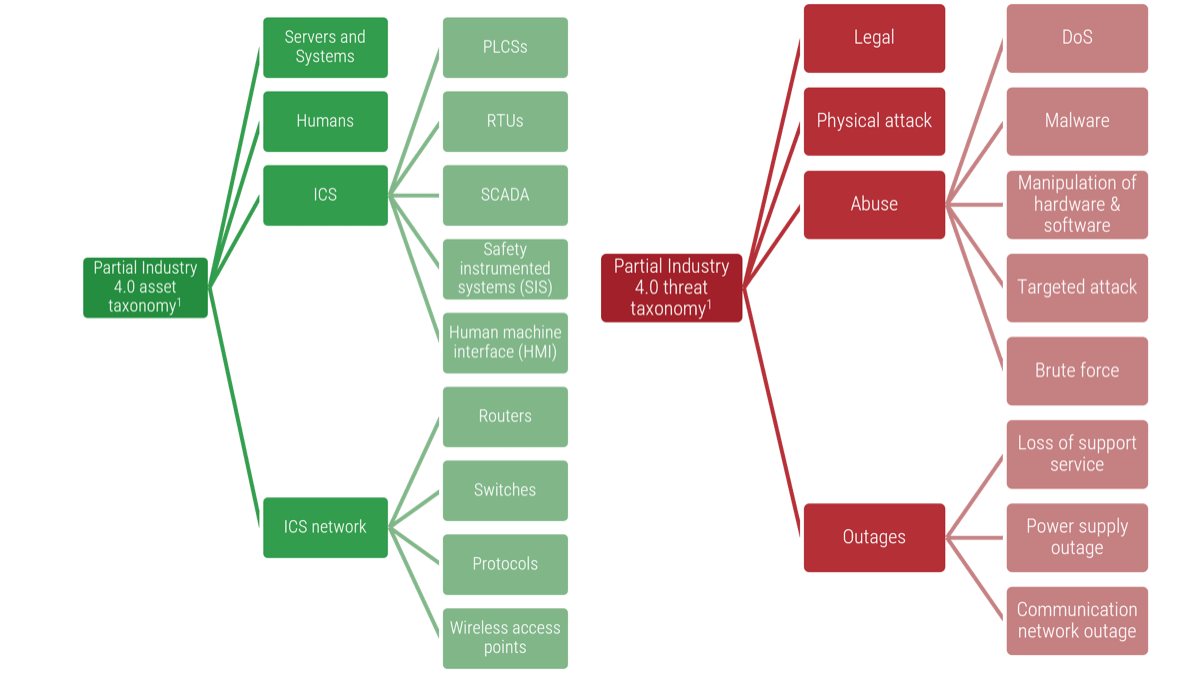
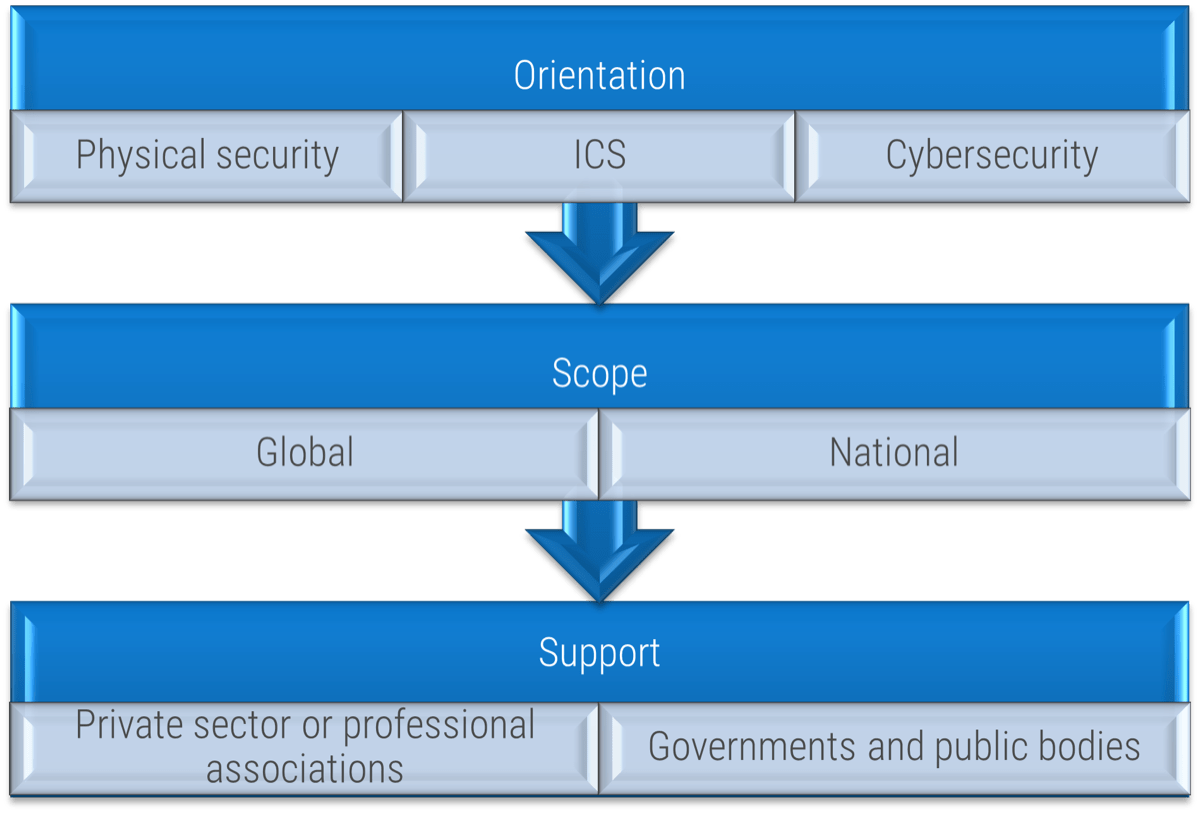 (Source: ENISA, 2015.)
(Source: ENISA, 2015.)
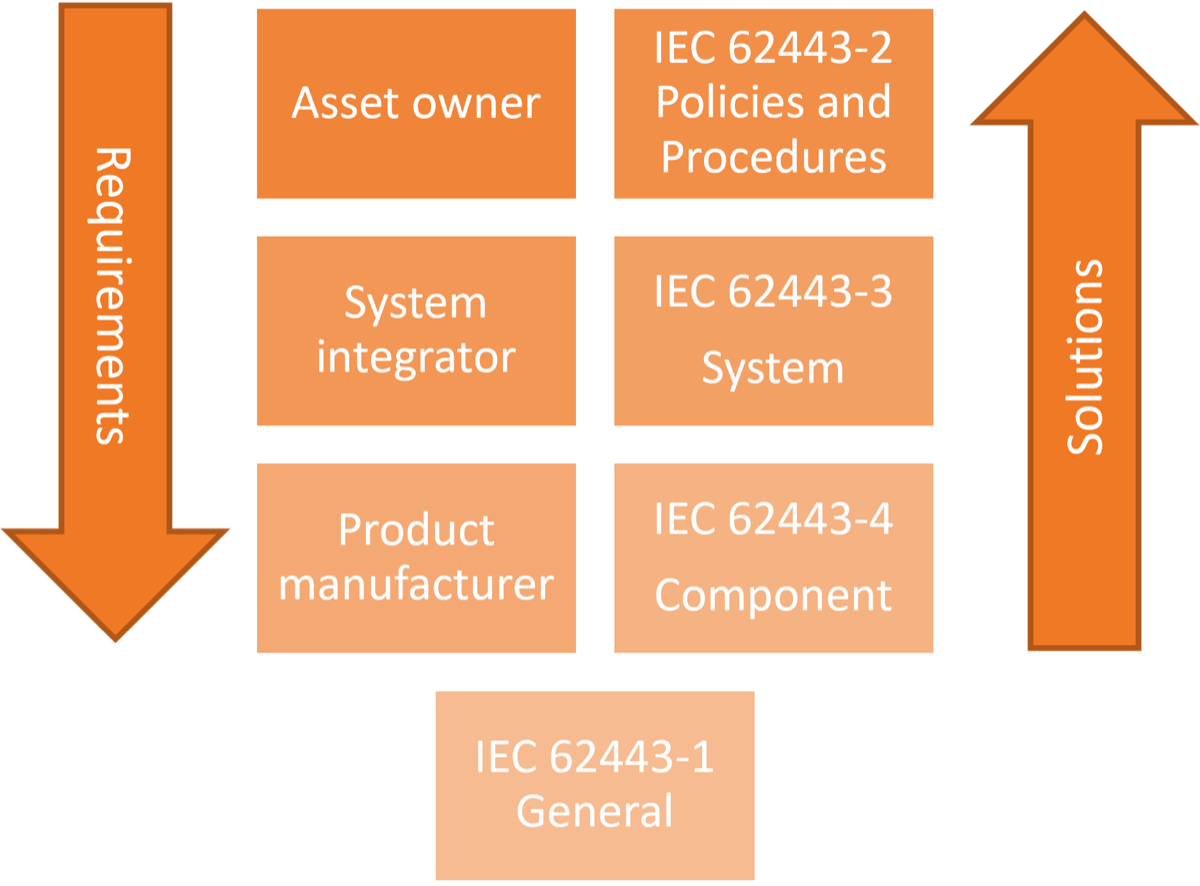
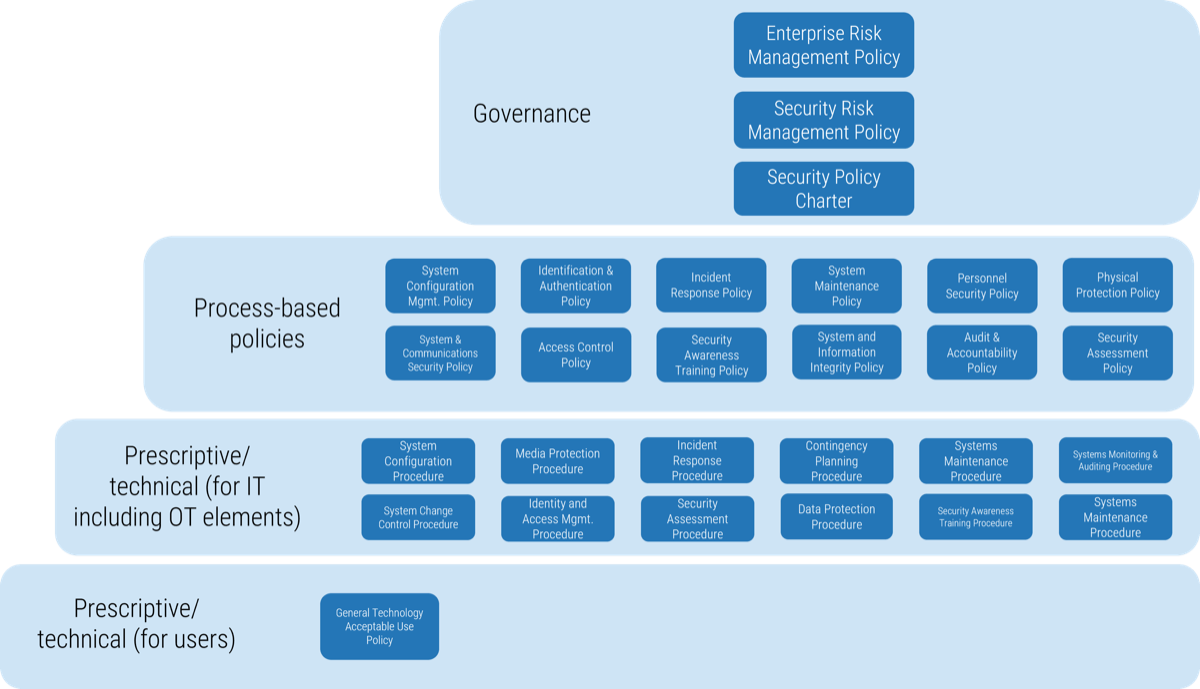
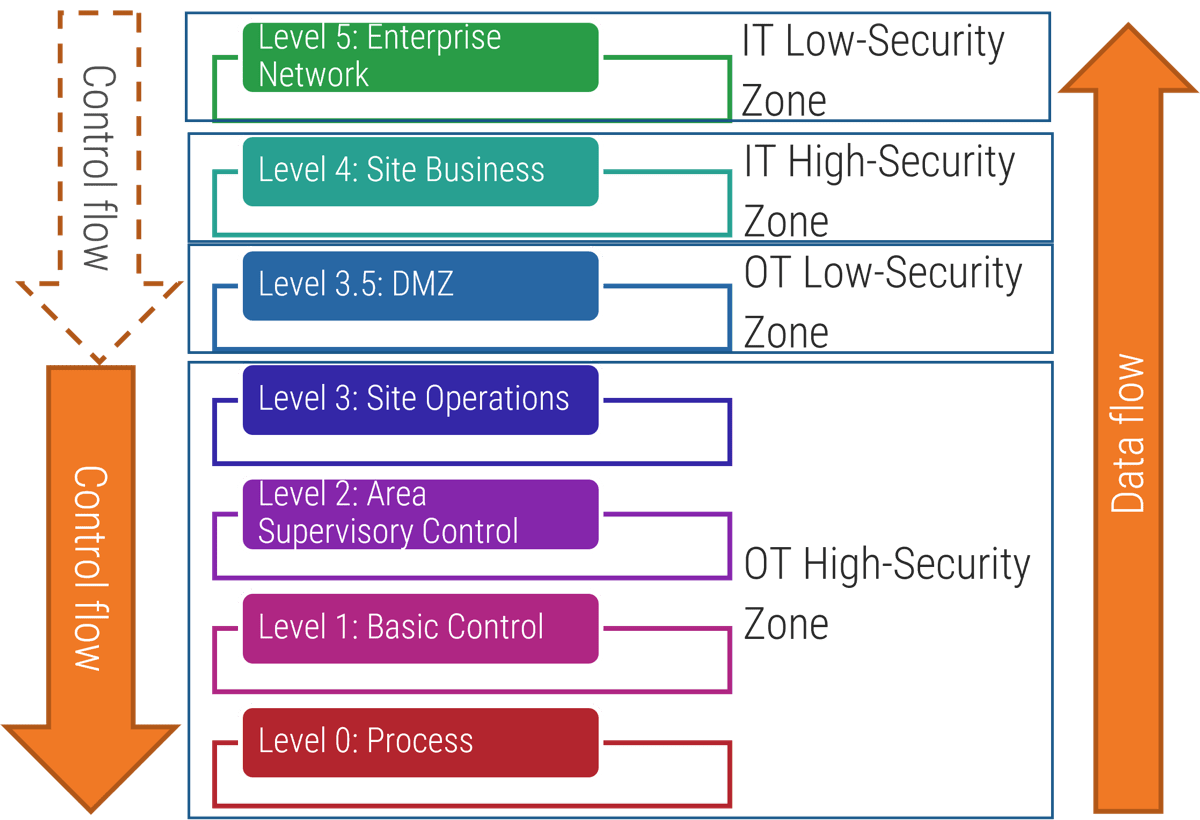 (Source: “Purdue Enterprise Reference Architecture (PERA) model,” ISA-99.)
(Source: “Purdue Enterprise Reference Architecture (PERA) model,” ISA-99.)




















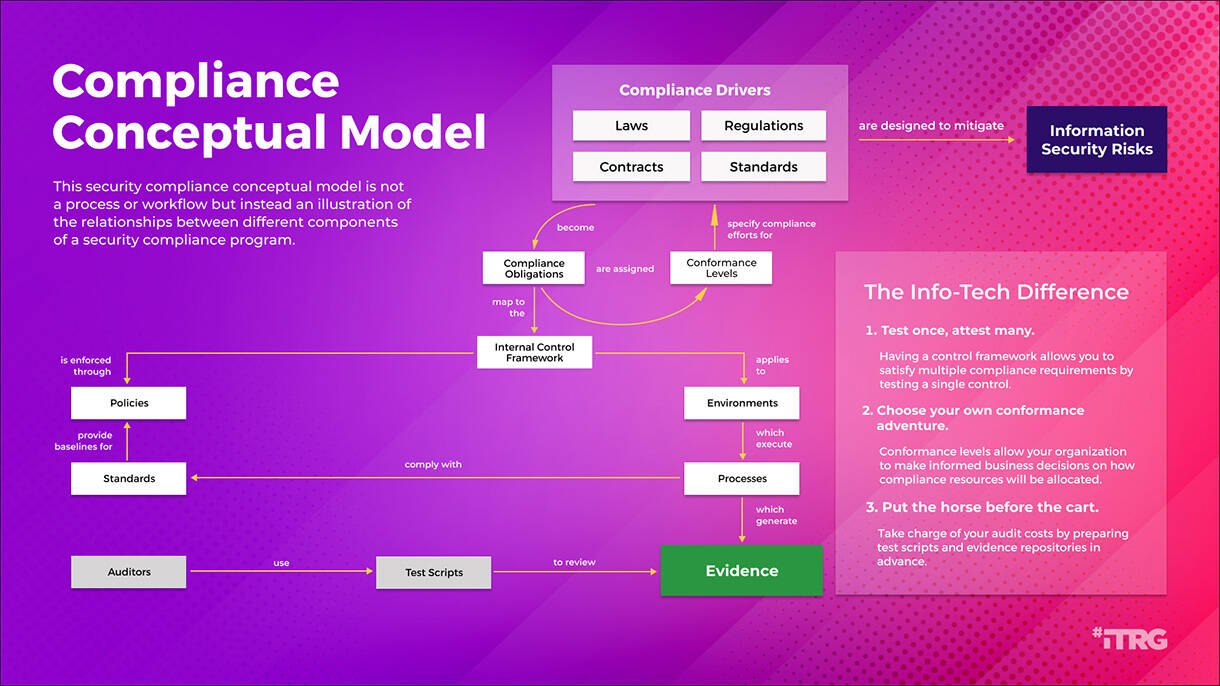


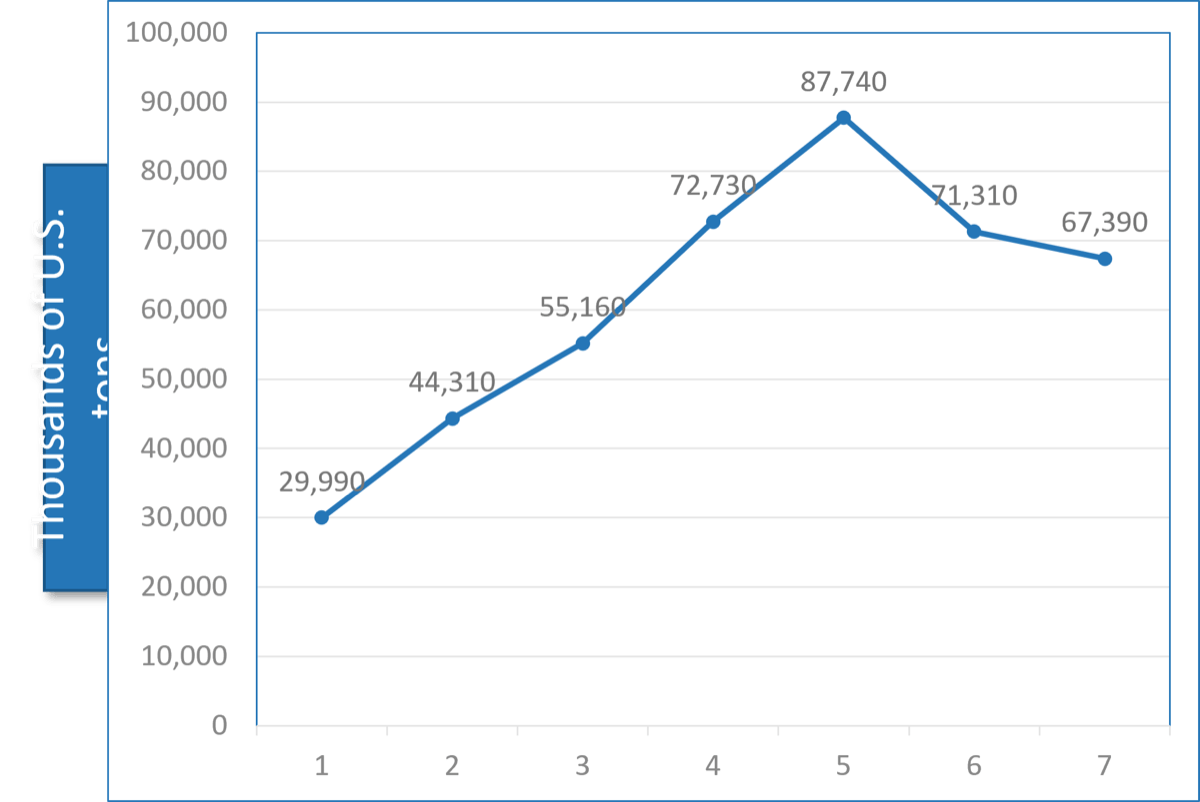







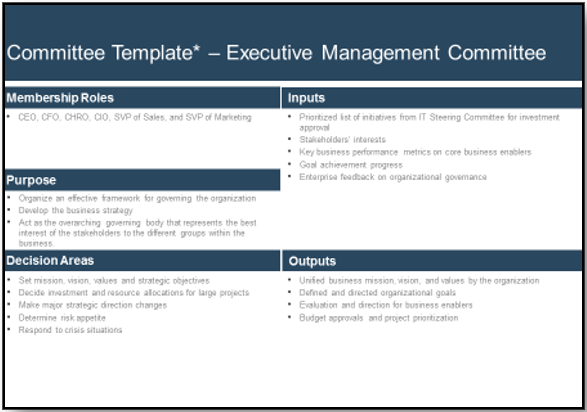
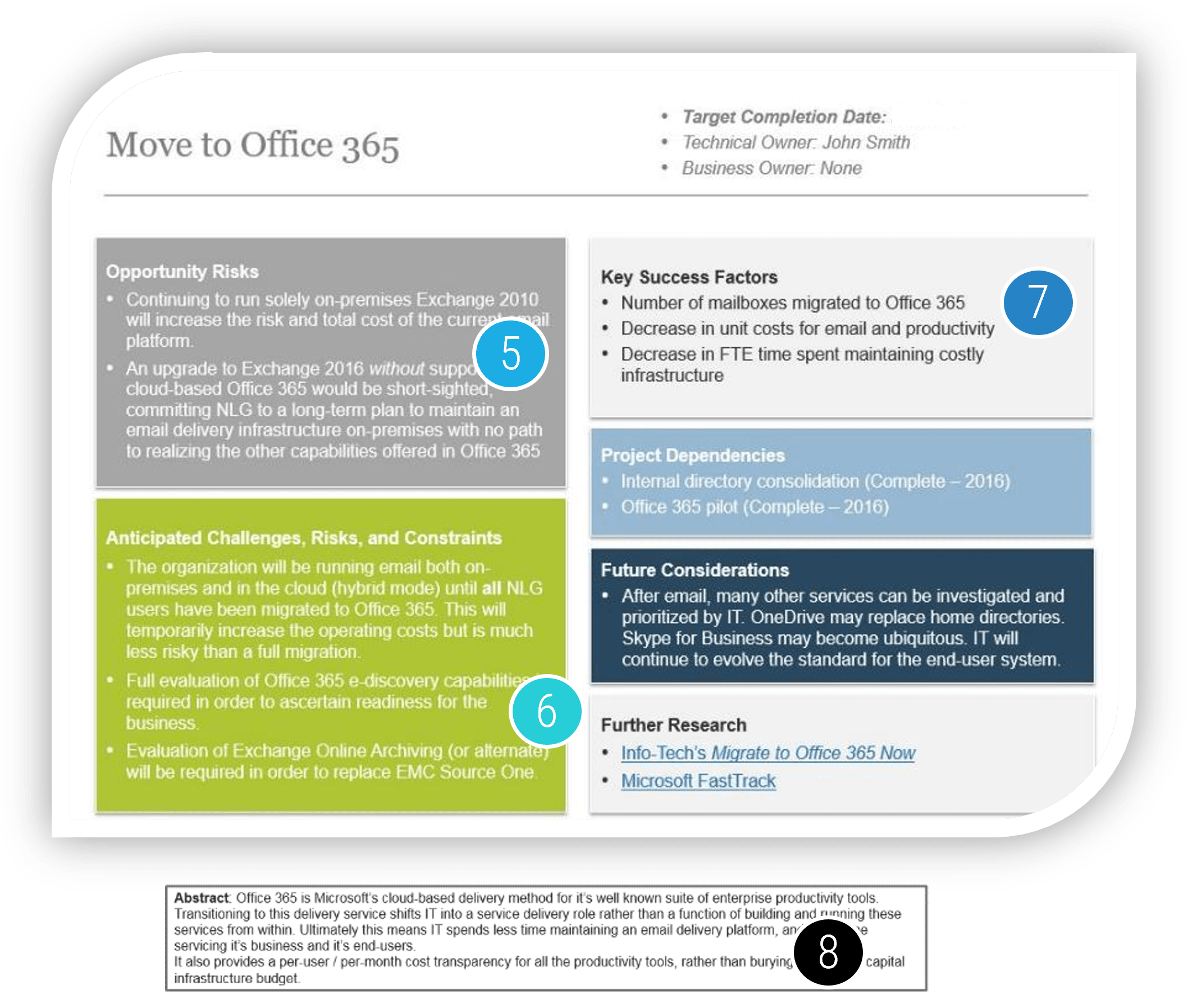
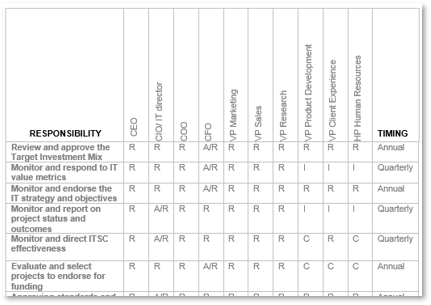
 IT Steering Committee Charter Template.">
IT Steering Committee Charter Template.">
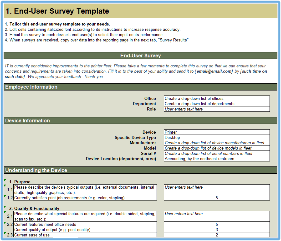
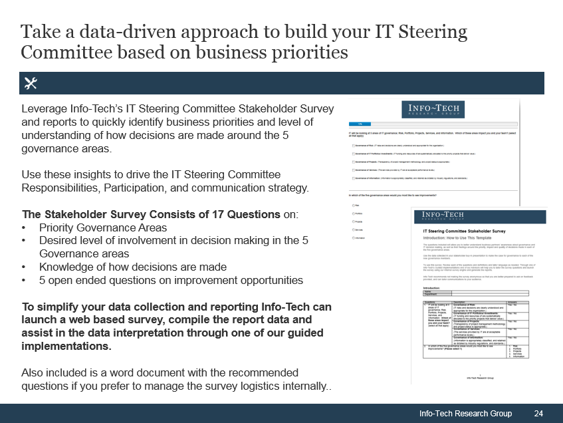
 IT Steering Committee Stakeholder Survey ">
IT Steering Committee Stakeholder Survey ">
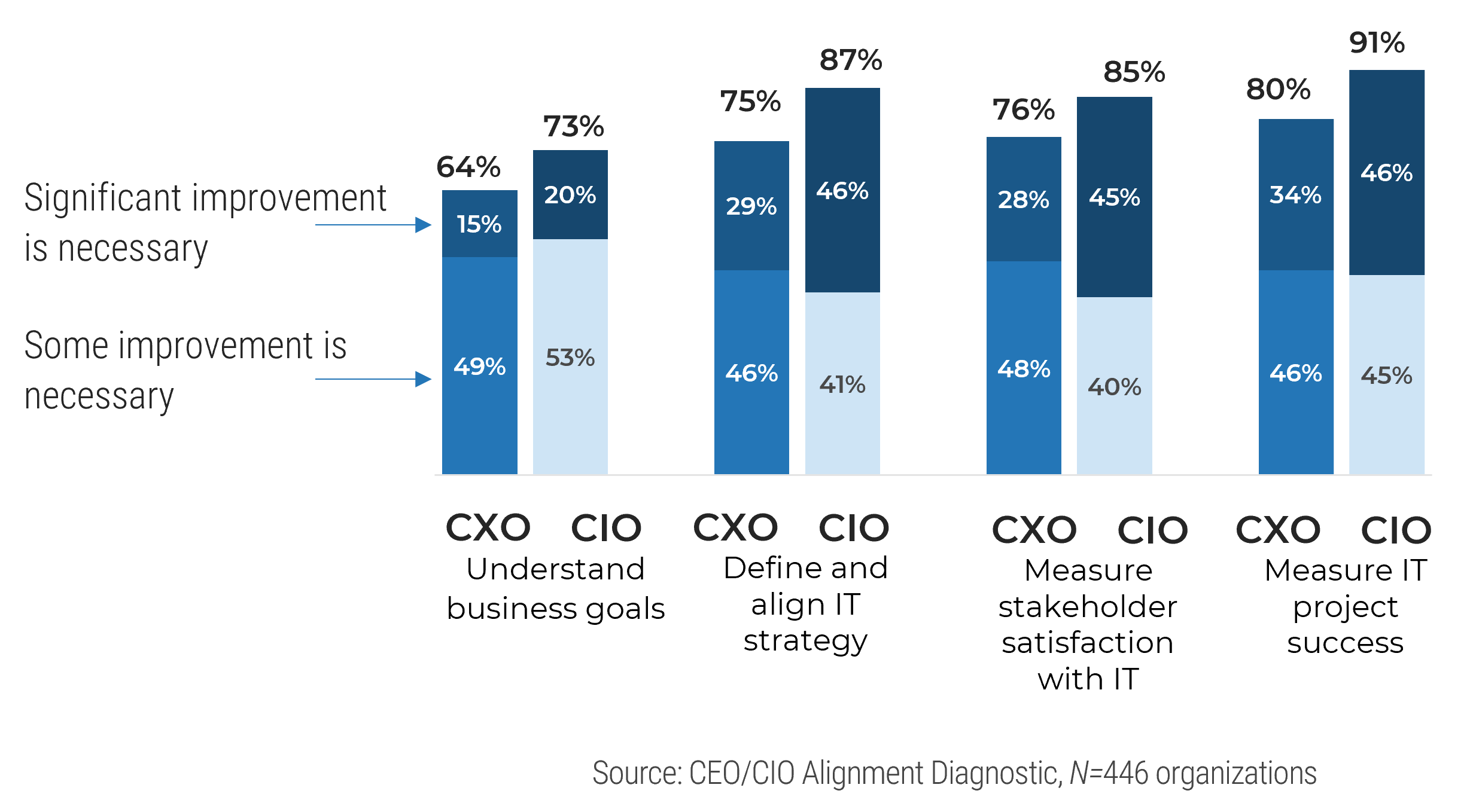
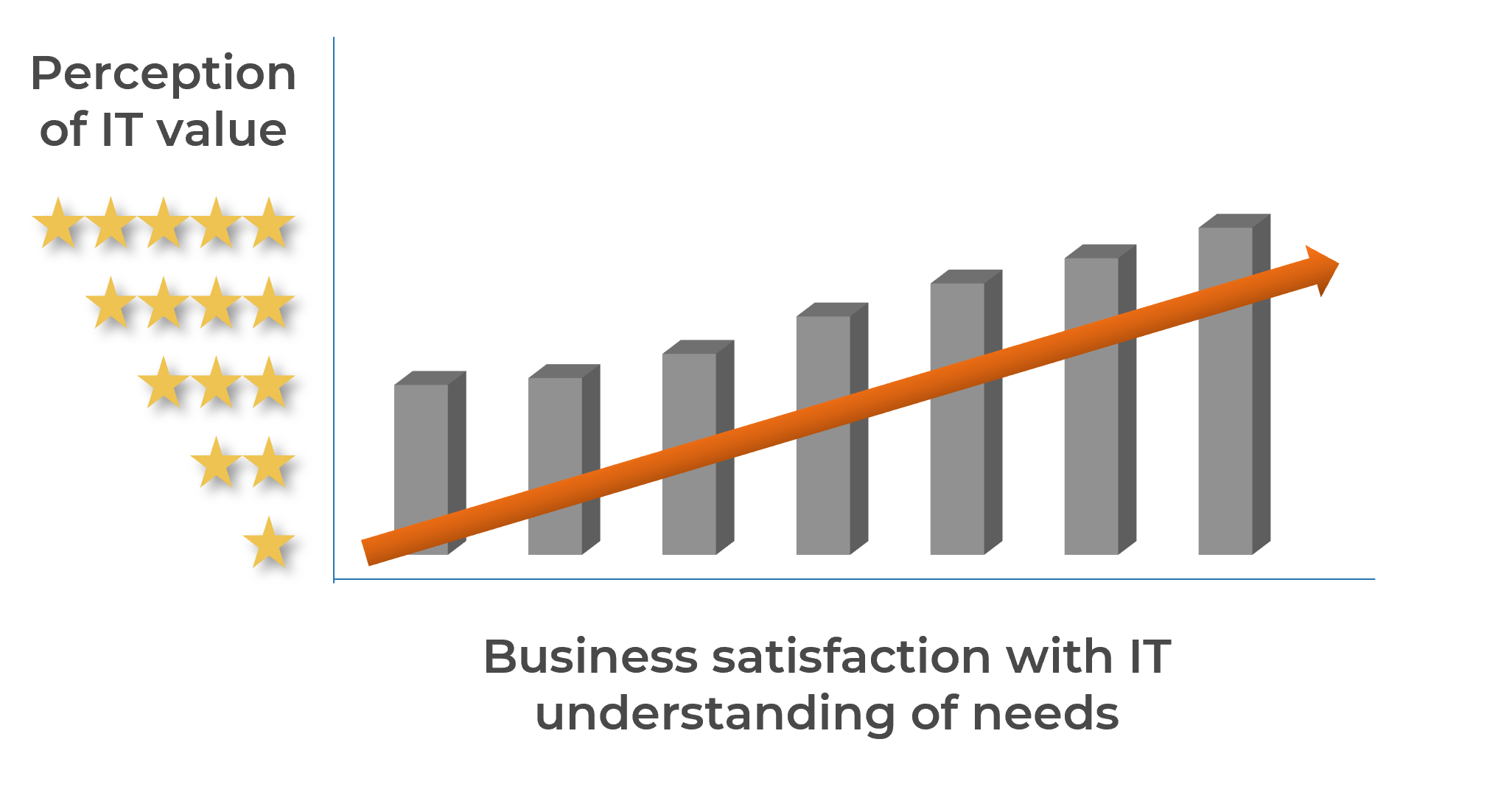
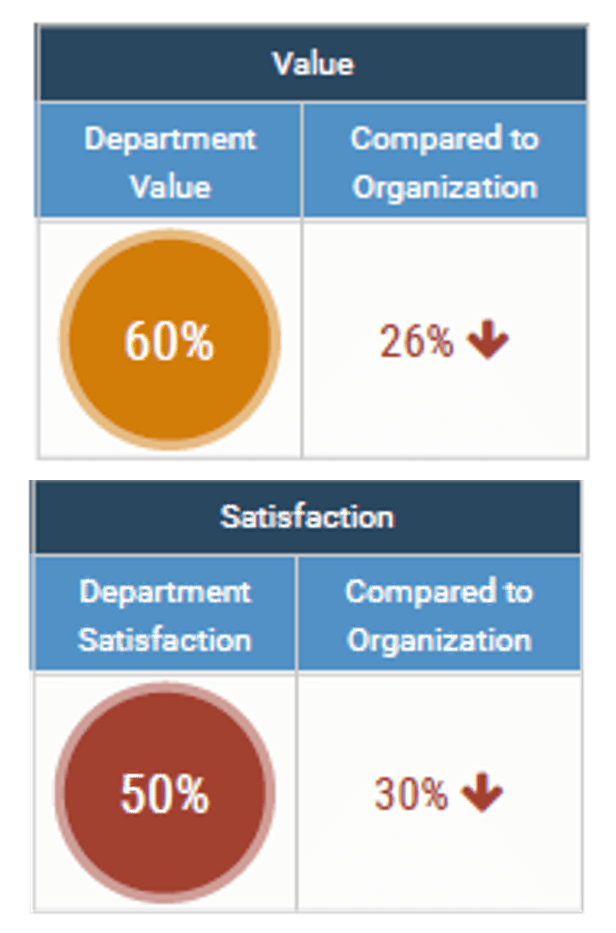
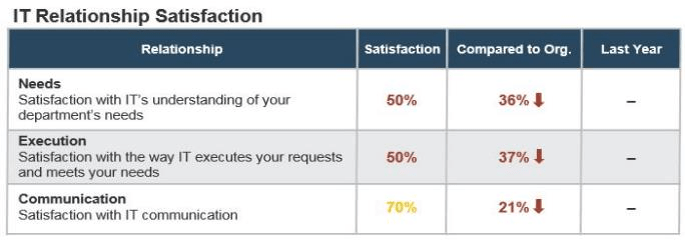
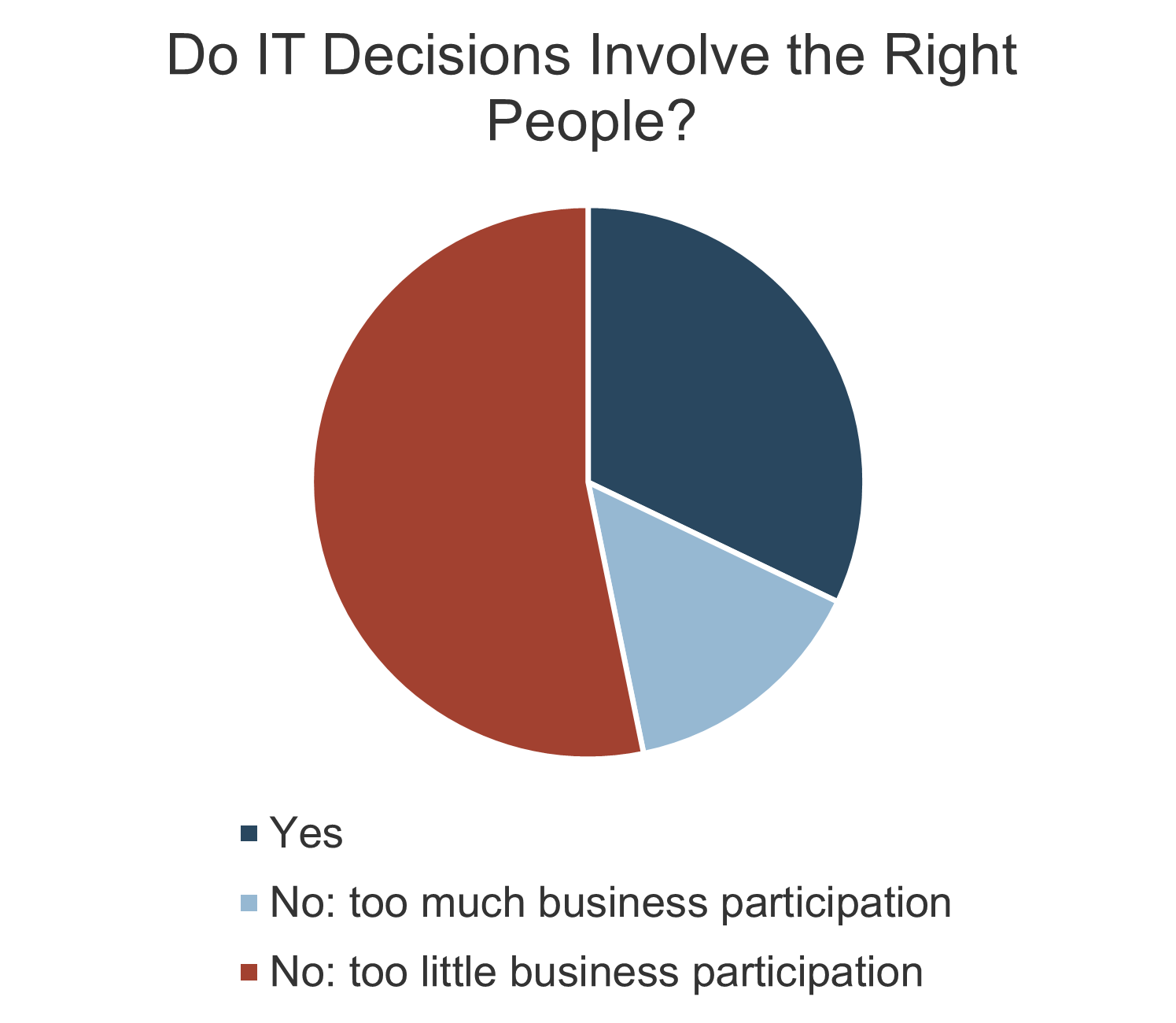
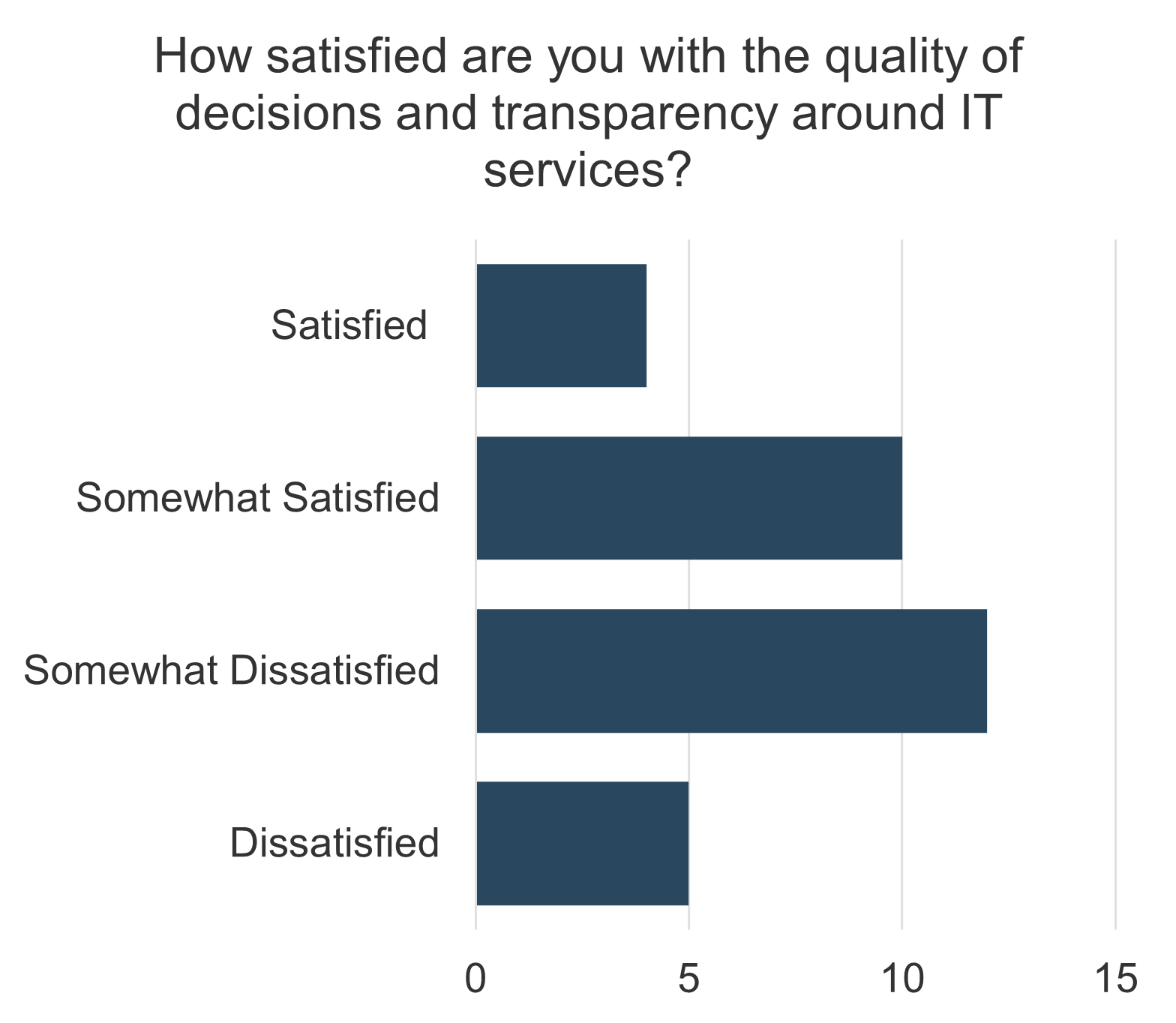
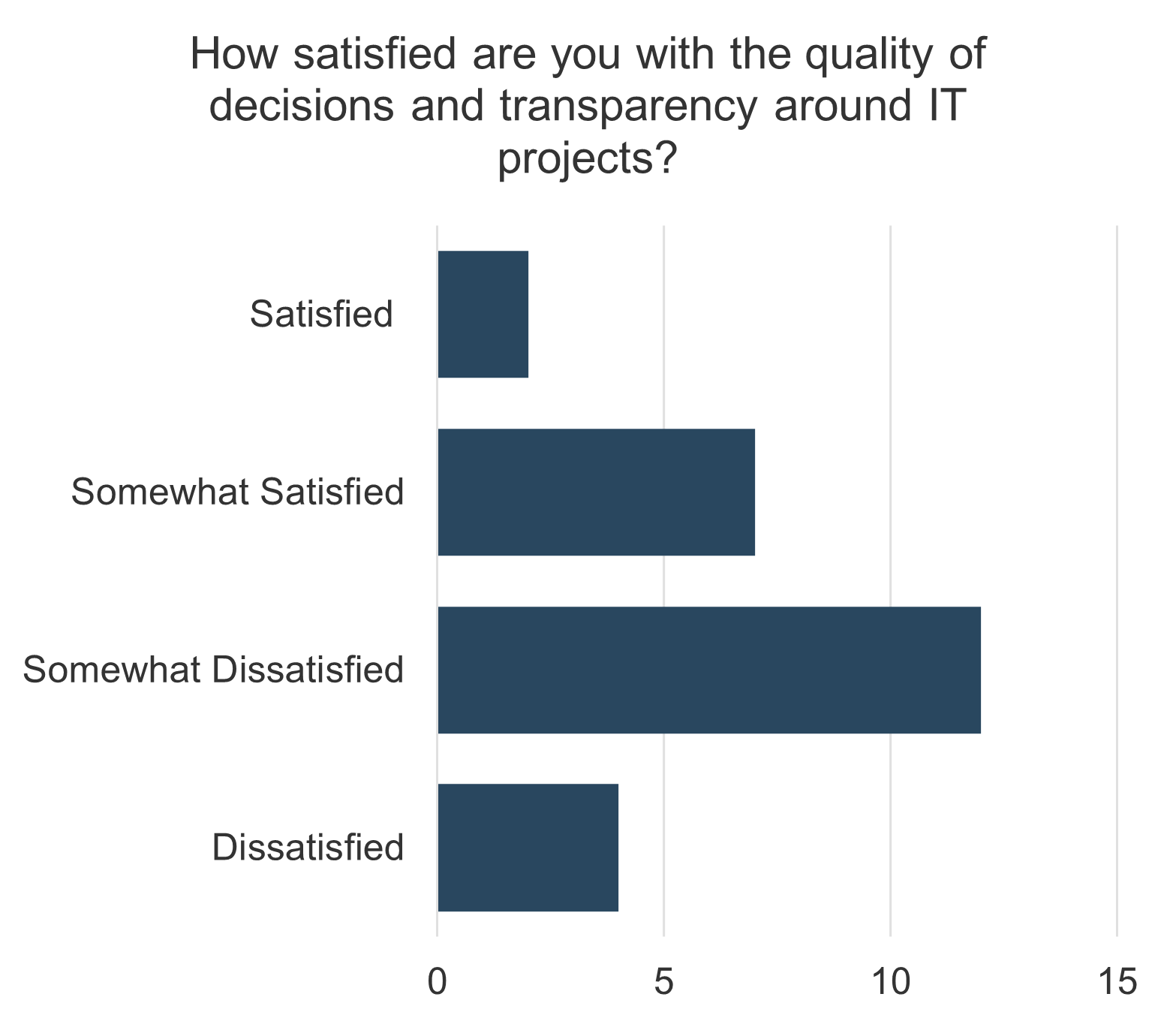
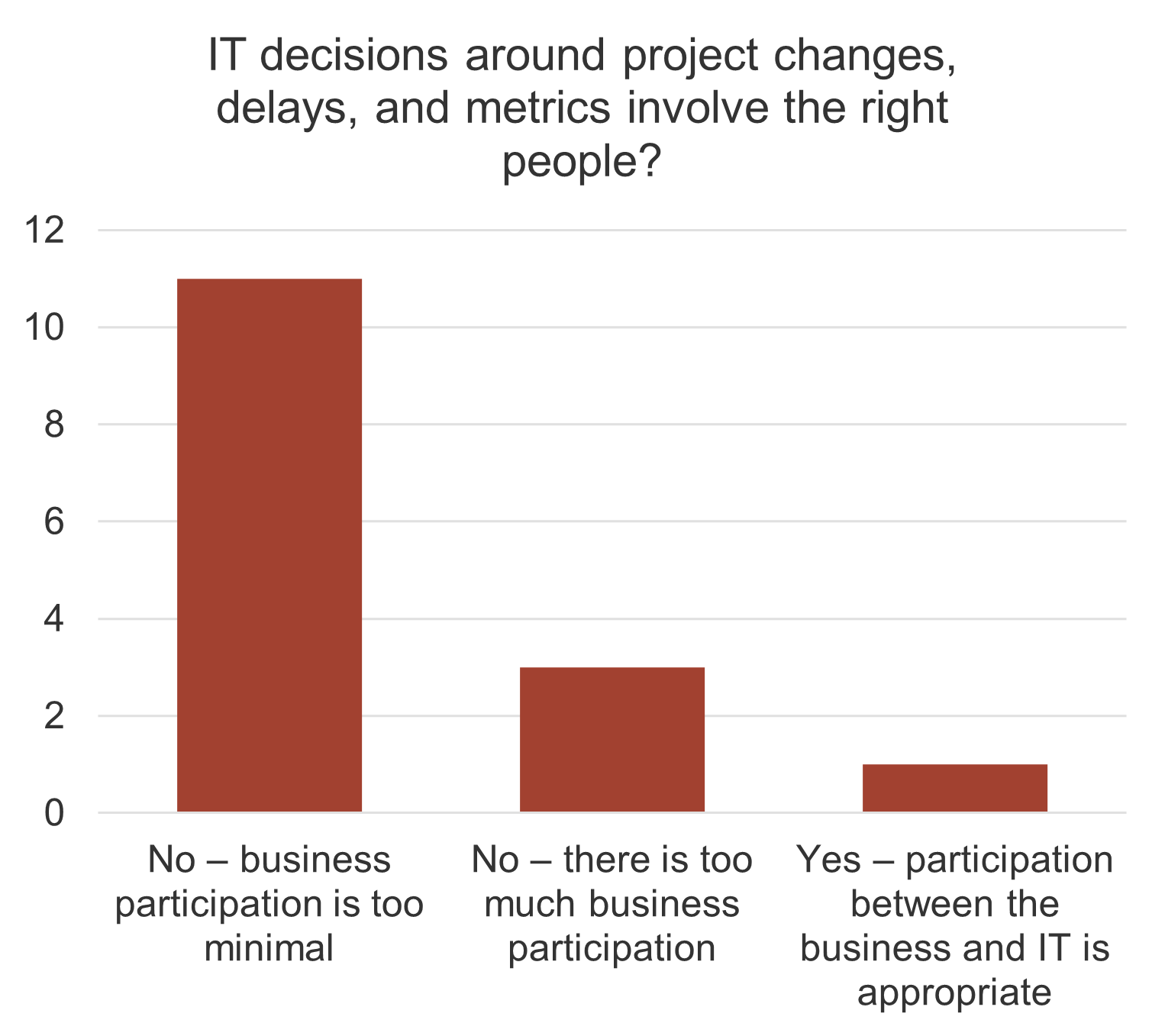
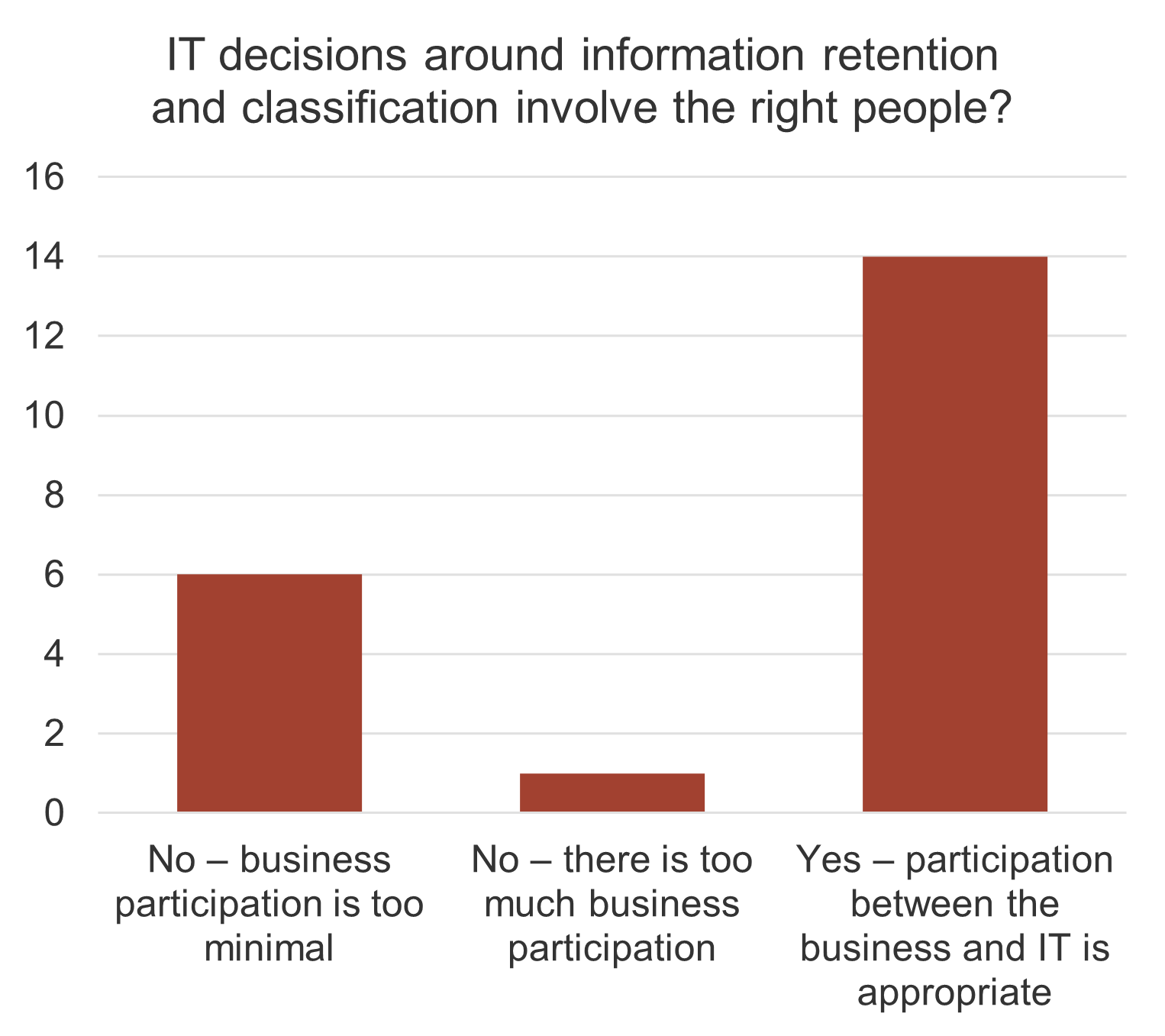
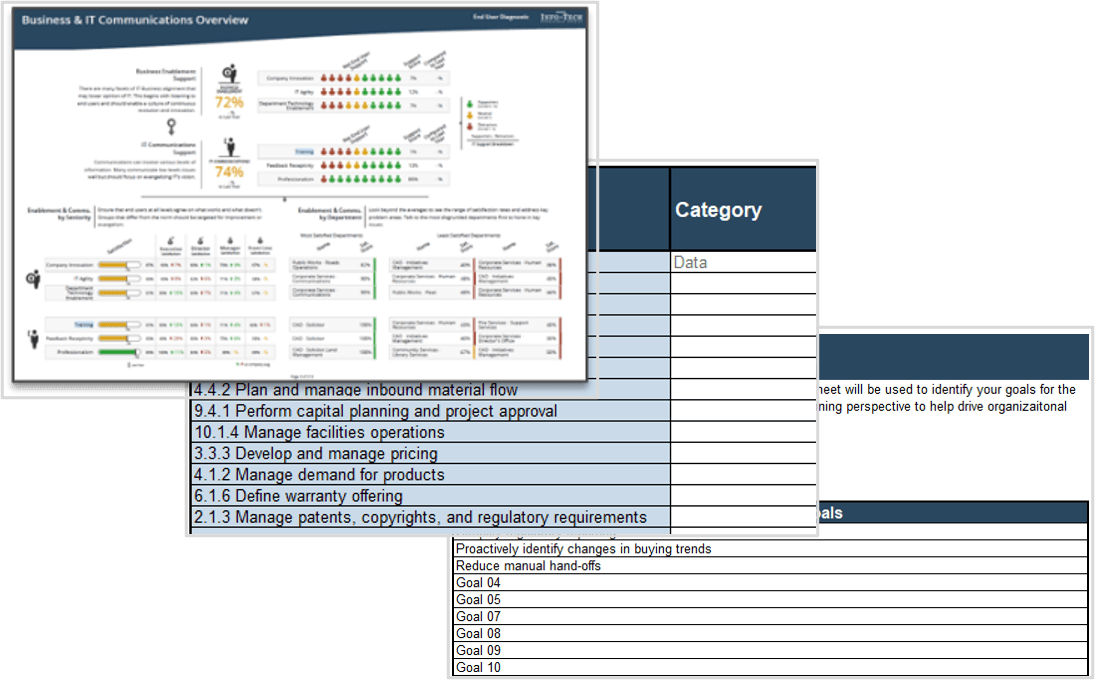
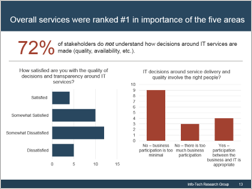 understand how decisions around IT services are made (quality, availability, etc.). Two graphs are included in the screenshot. One of the bar graphs shows the satisfaction with the quality of decisions and transparency around IT services. The other bar graph displays IT decisions around service delivery and quality that involve the right people.">
understand how decisions around IT services are made (quality, availability, etc.). Two graphs are included in the screenshot. One of the bar graphs shows the satisfaction with the quality of decisions and transparency around IT services. The other bar graph displays IT decisions around service delivery and quality that involve the right people.">
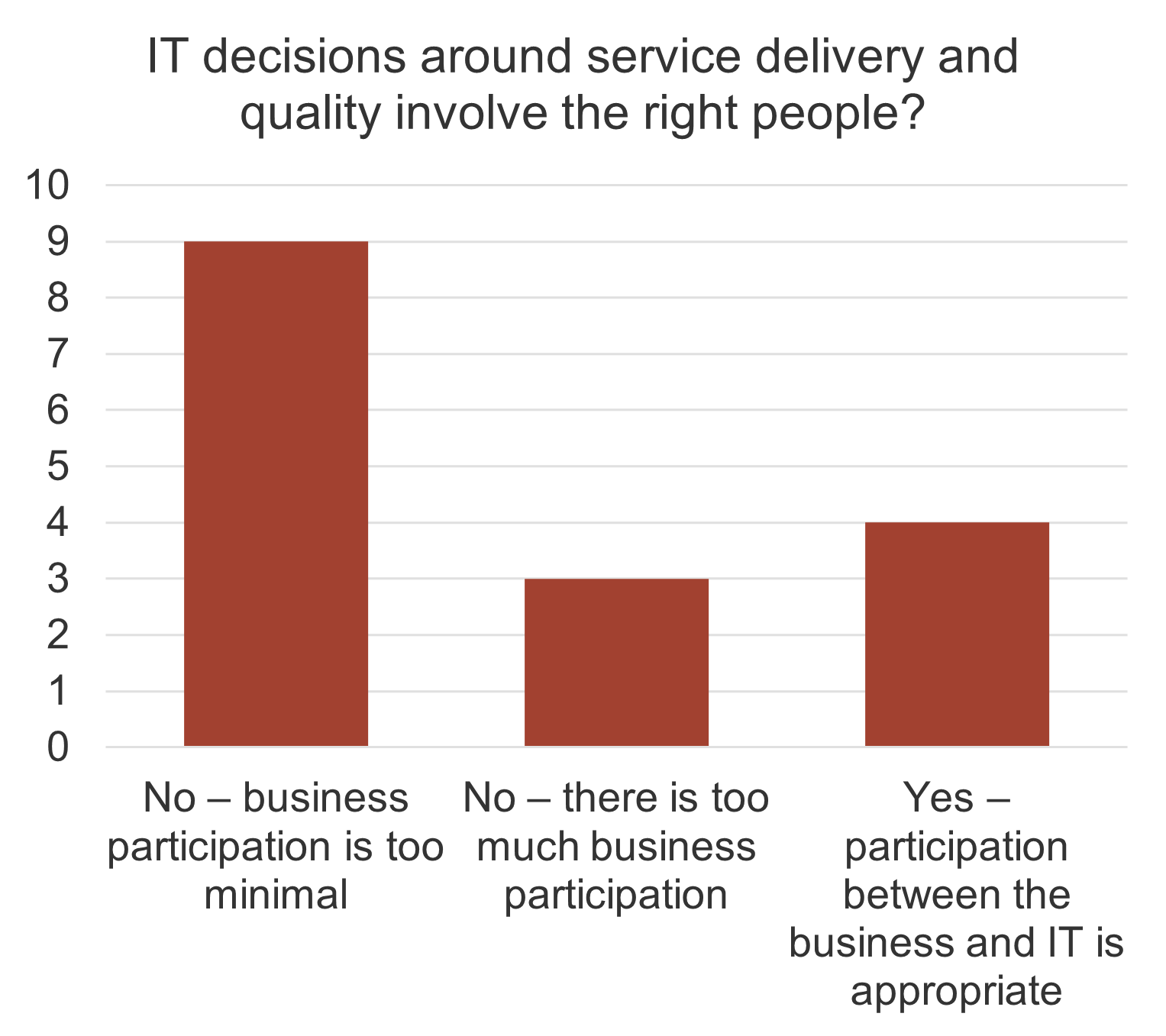
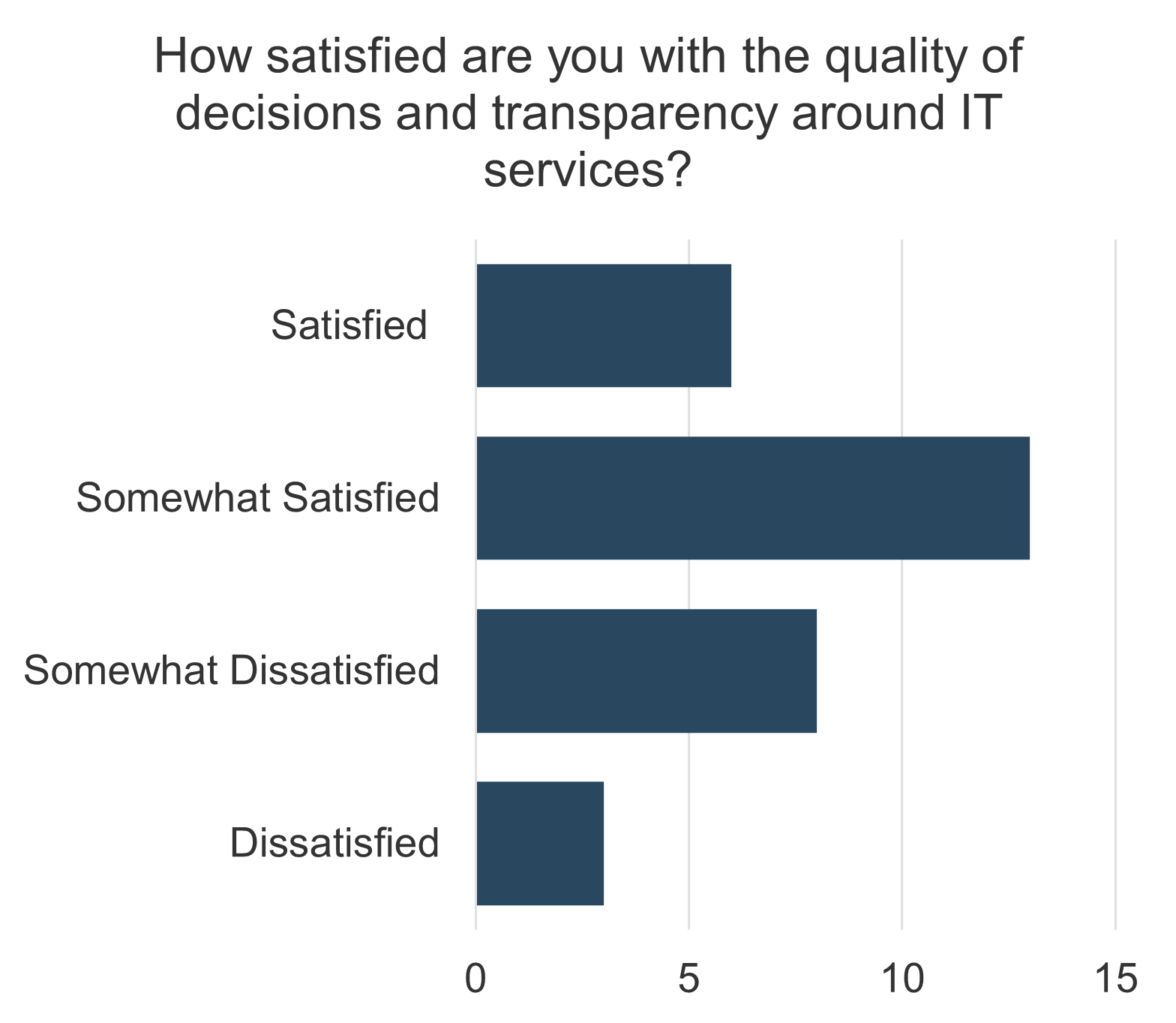
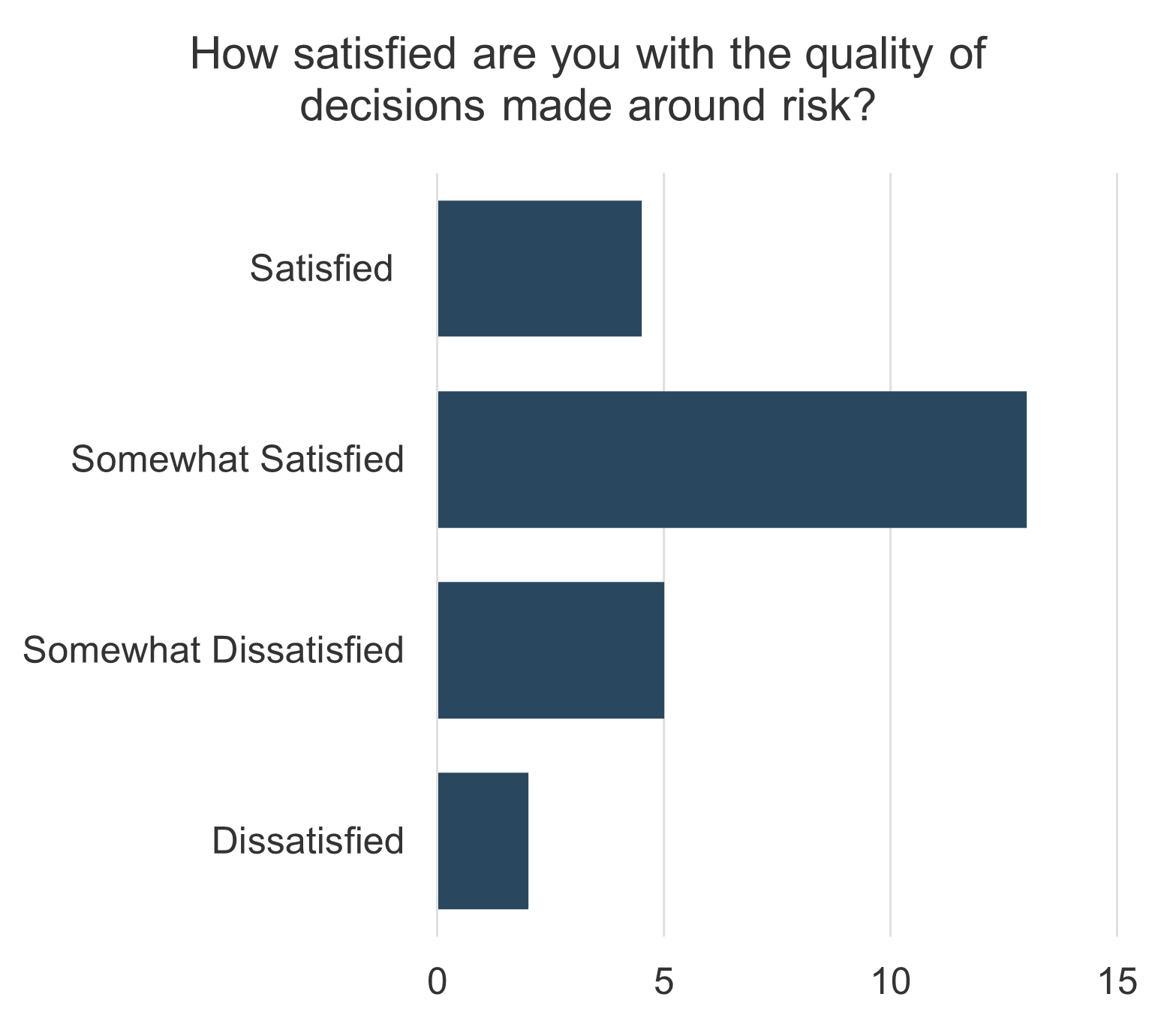
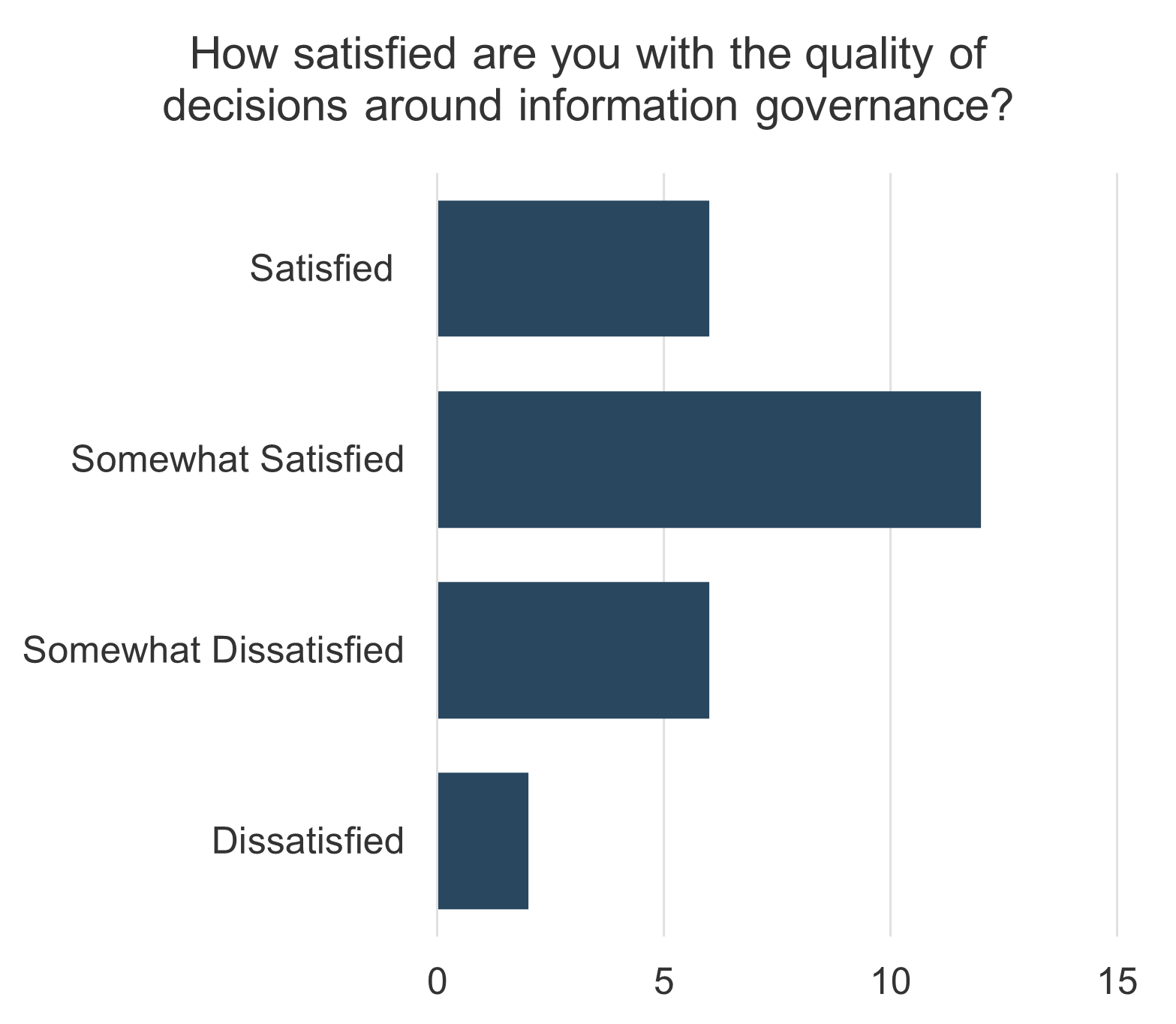
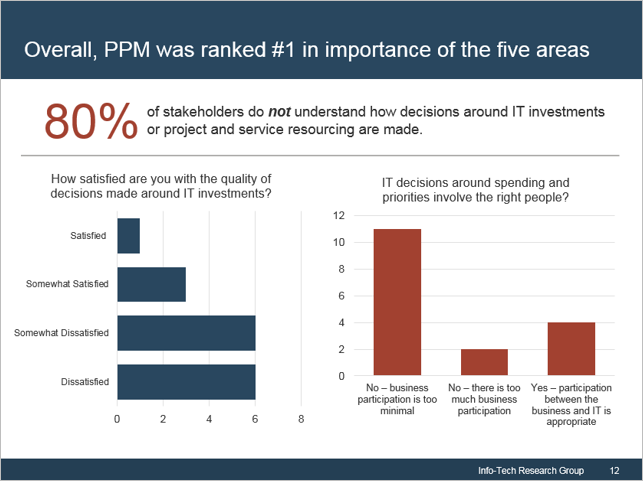 not understand how decisions around IT investments or project and service resourcing are made. Two bar graphs are displayed. One of the bar graphs shows the satisfaction with the quality of decisions made around IT investments. The other graph display IT decisions around spending priorities involving the right people.">
not understand how decisions around IT investments or project and service resourcing are made. Two bar graphs are displayed. One of the bar graphs shows the satisfaction with the quality of decisions made around IT investments. The other graph display IT decisions around spending priorities involving the right people.">


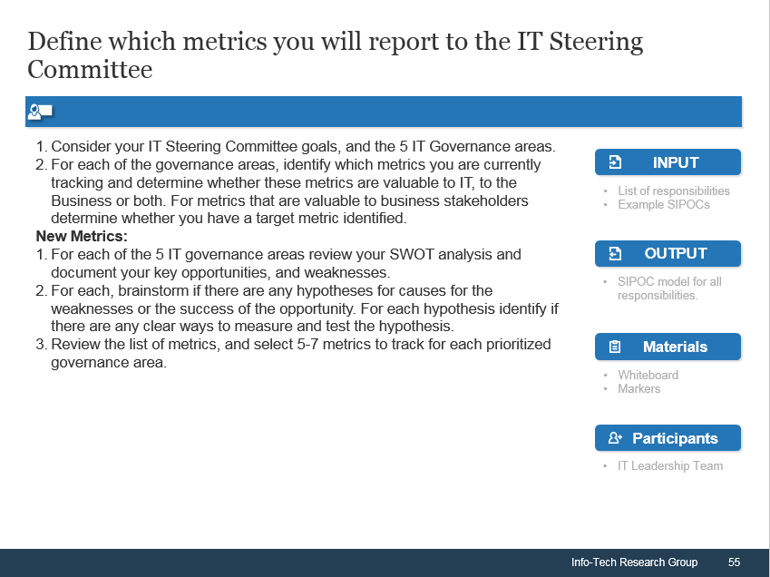



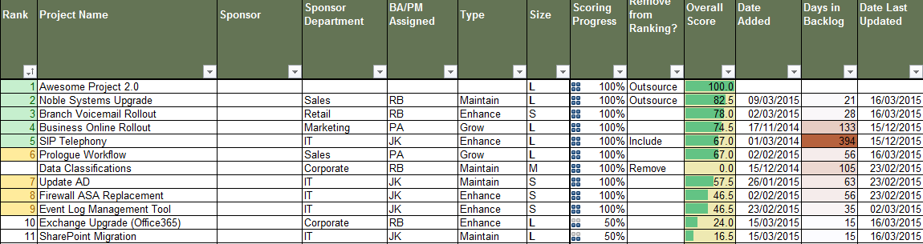
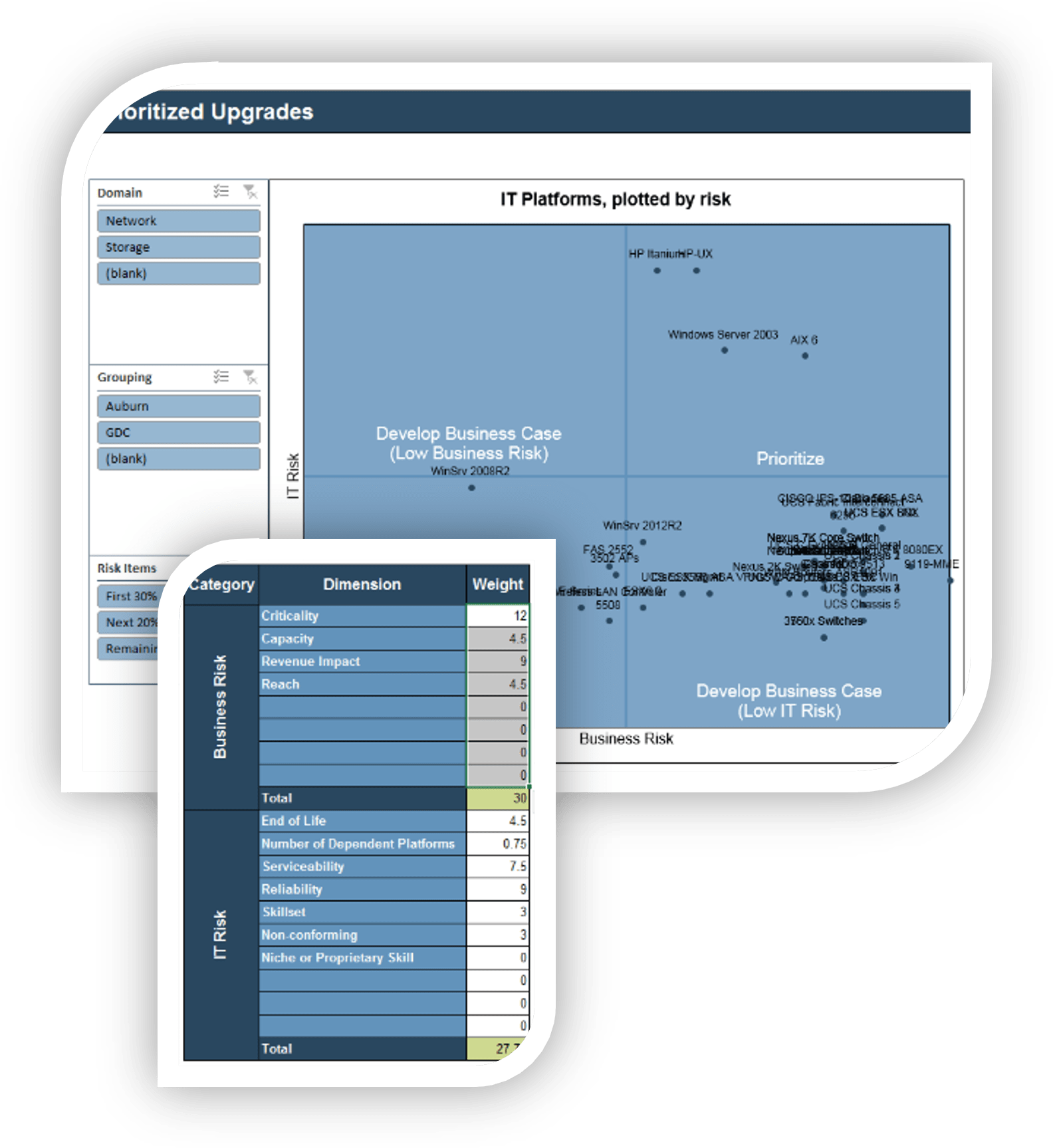
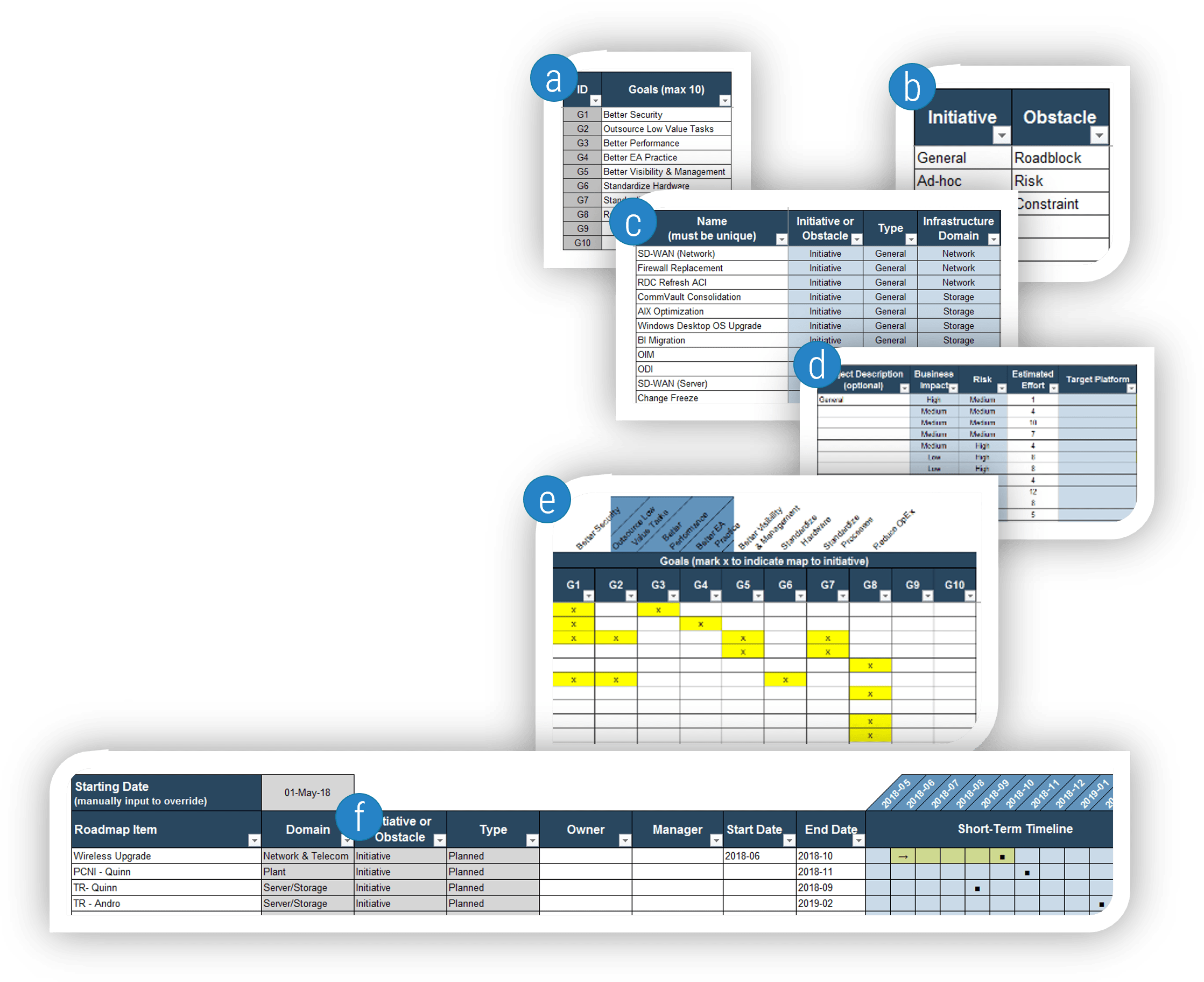
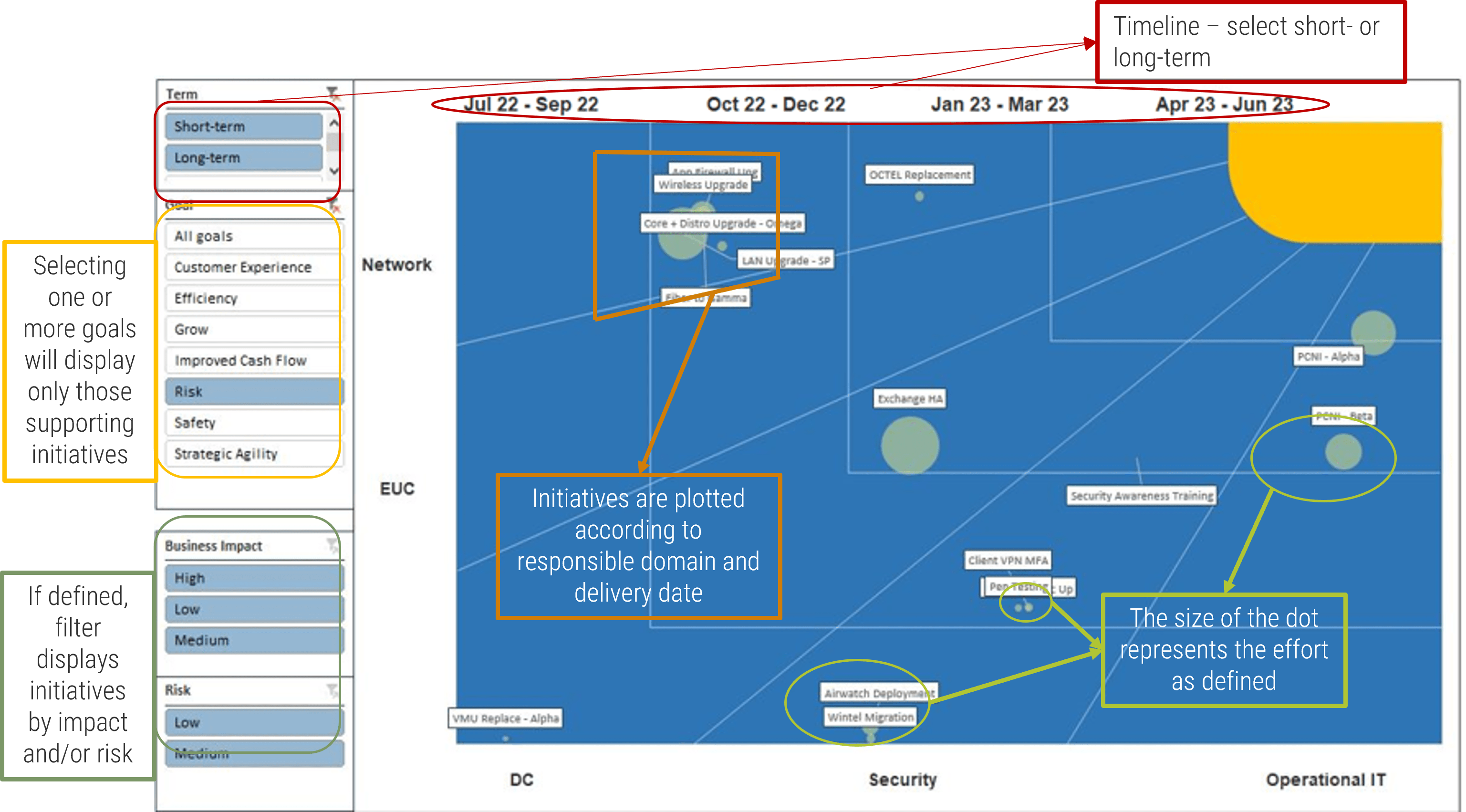
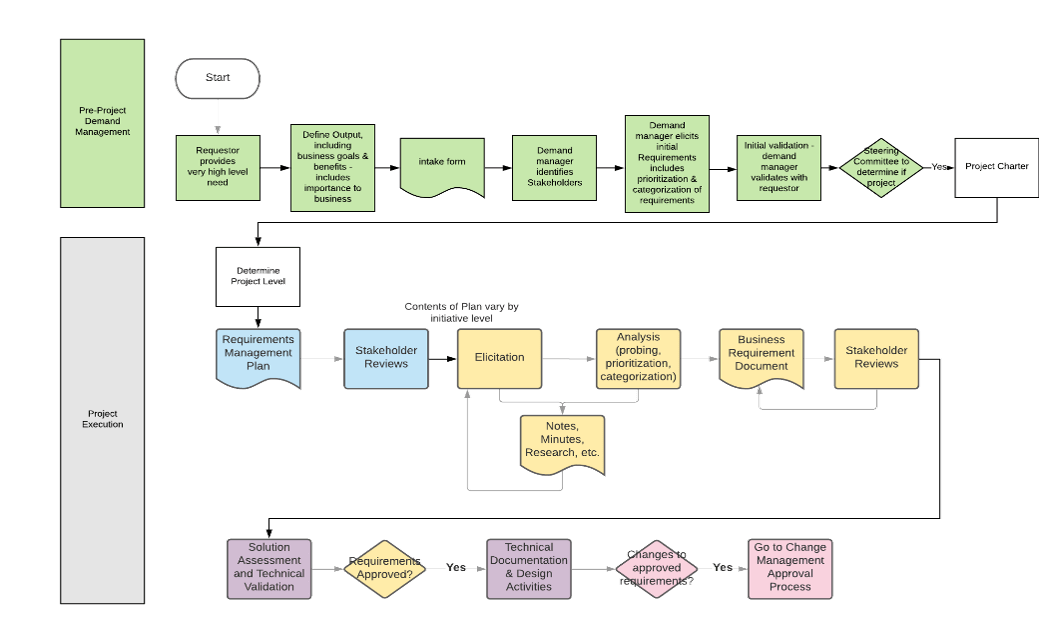
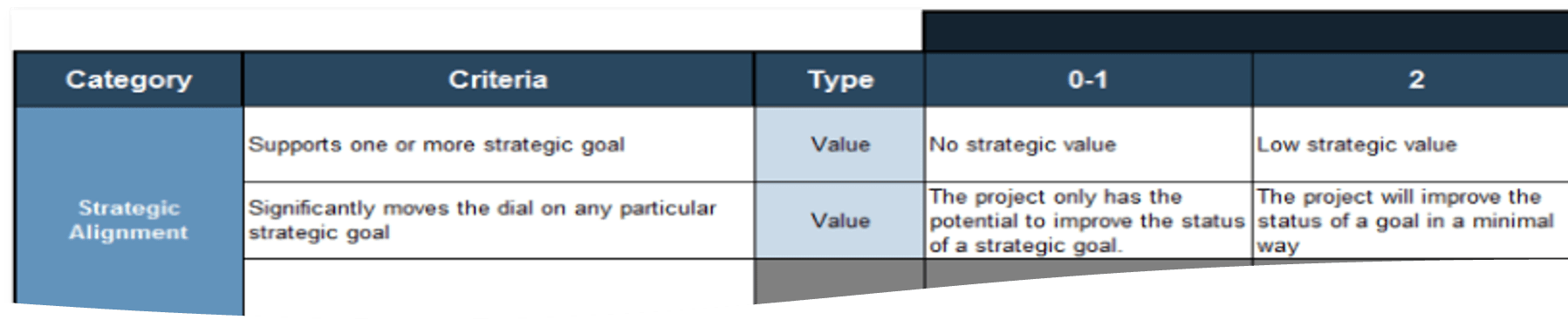
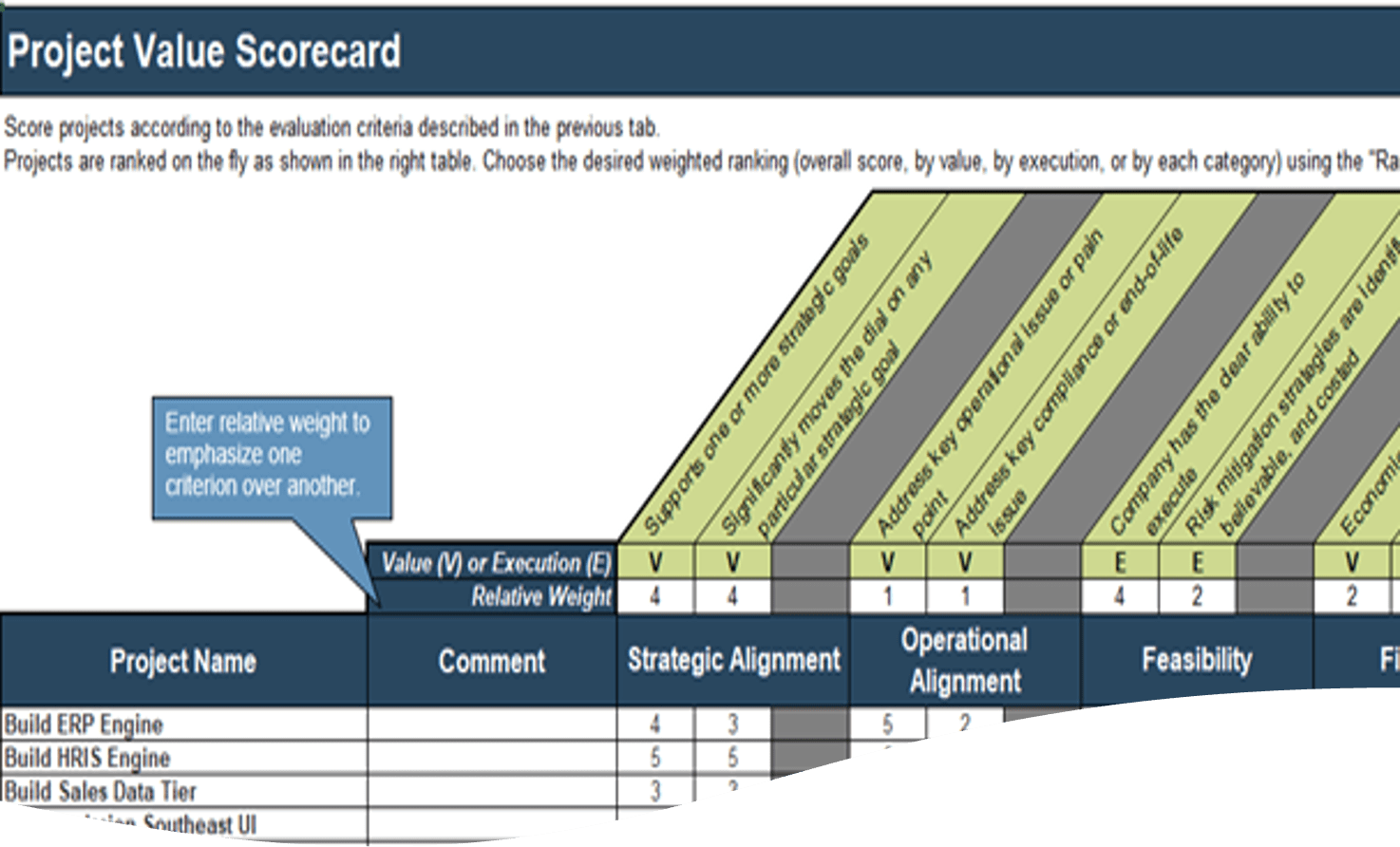
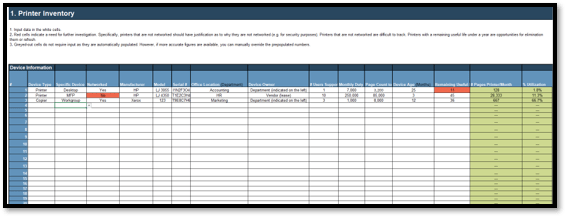
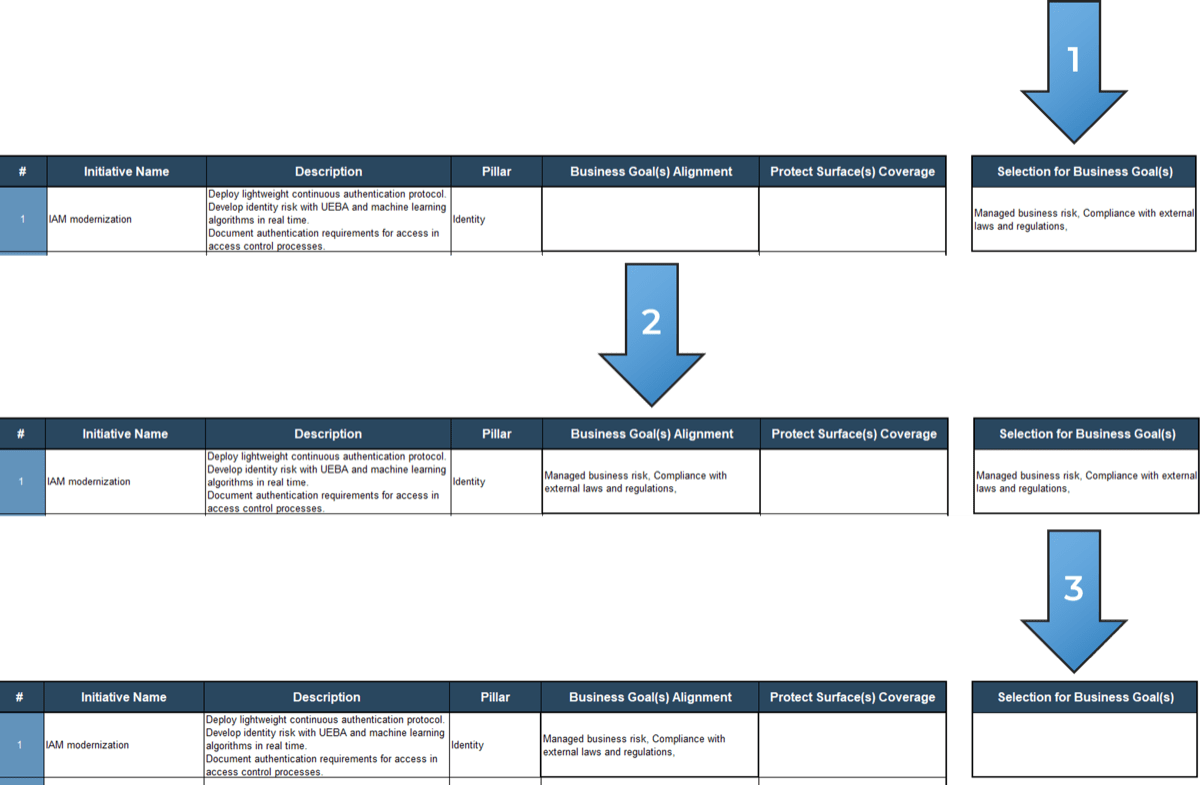
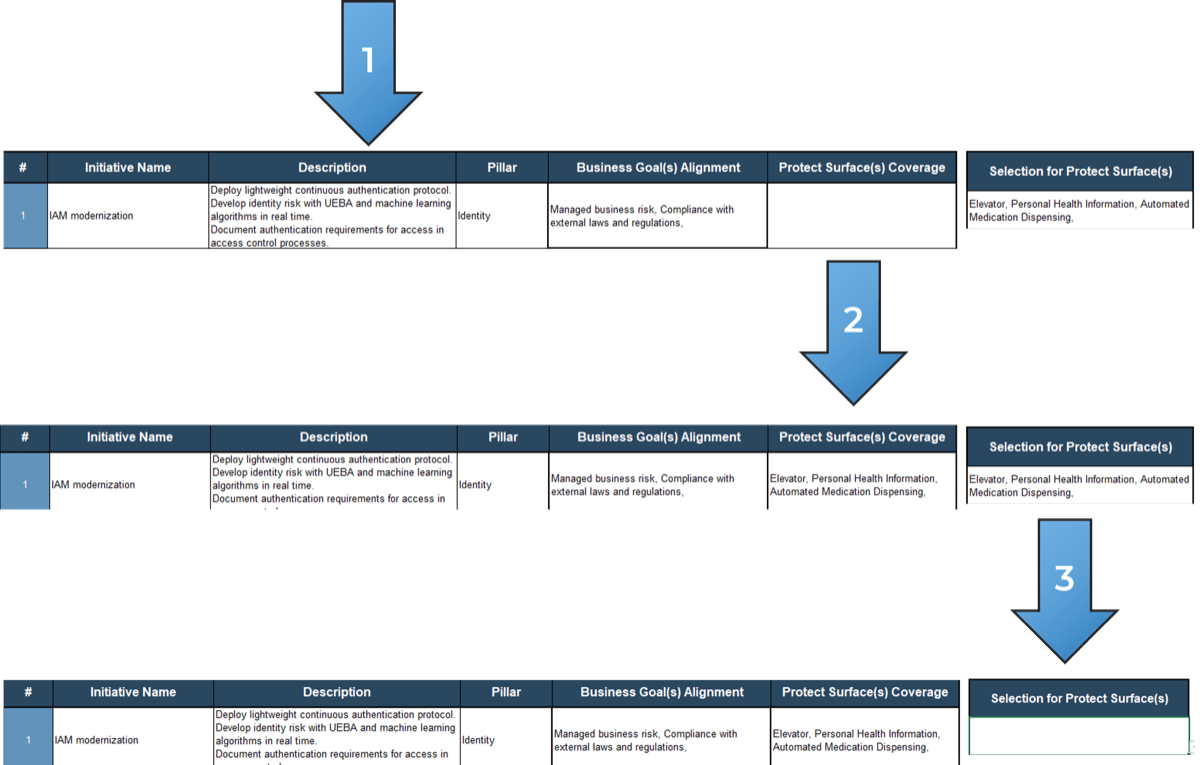
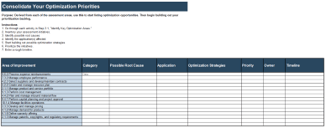
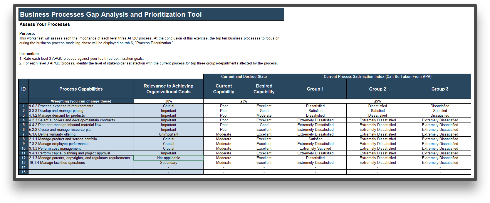
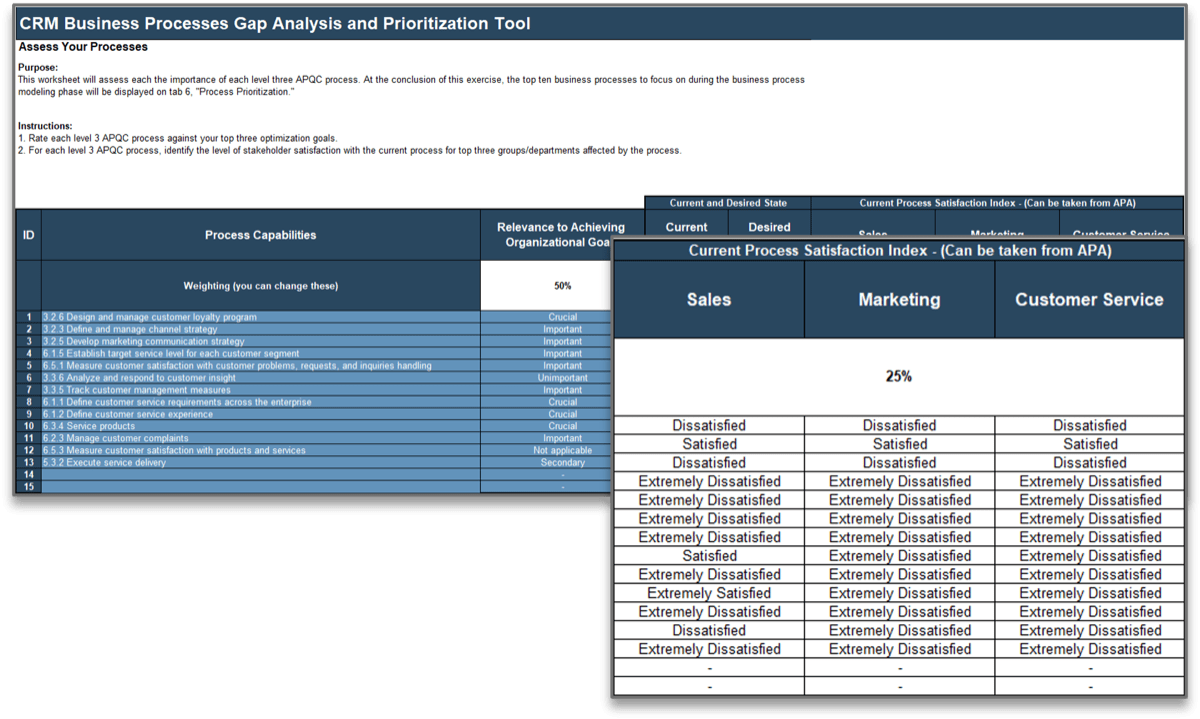
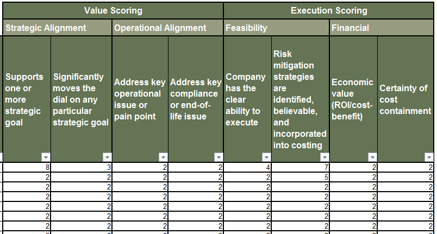 IT Steering Committee Project Prioritization Tool is depicted. The Data Tab is shown.">
IT Steering Committee Project Prioritization Tool is depicted. The Data Tab is shown.">

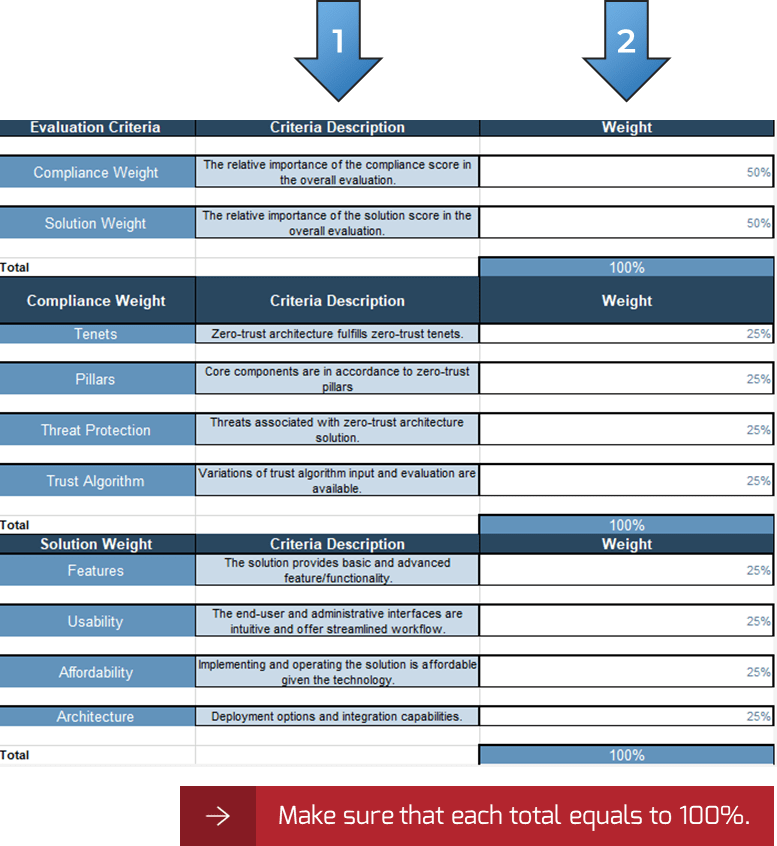
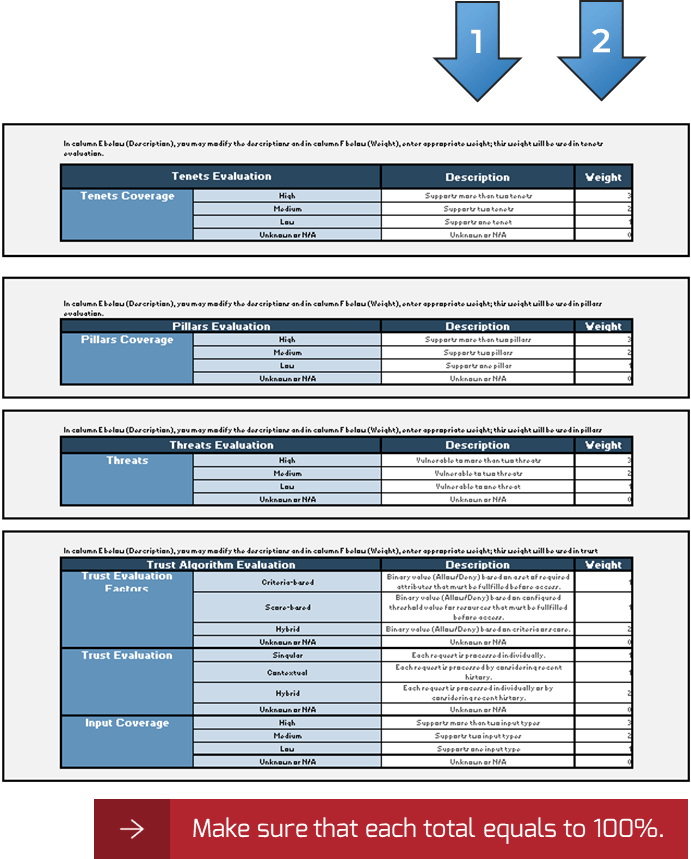
 IT Steering Committee Project Prioritization Tool.">
IT Steering Committee Project Prioritization Tool."> 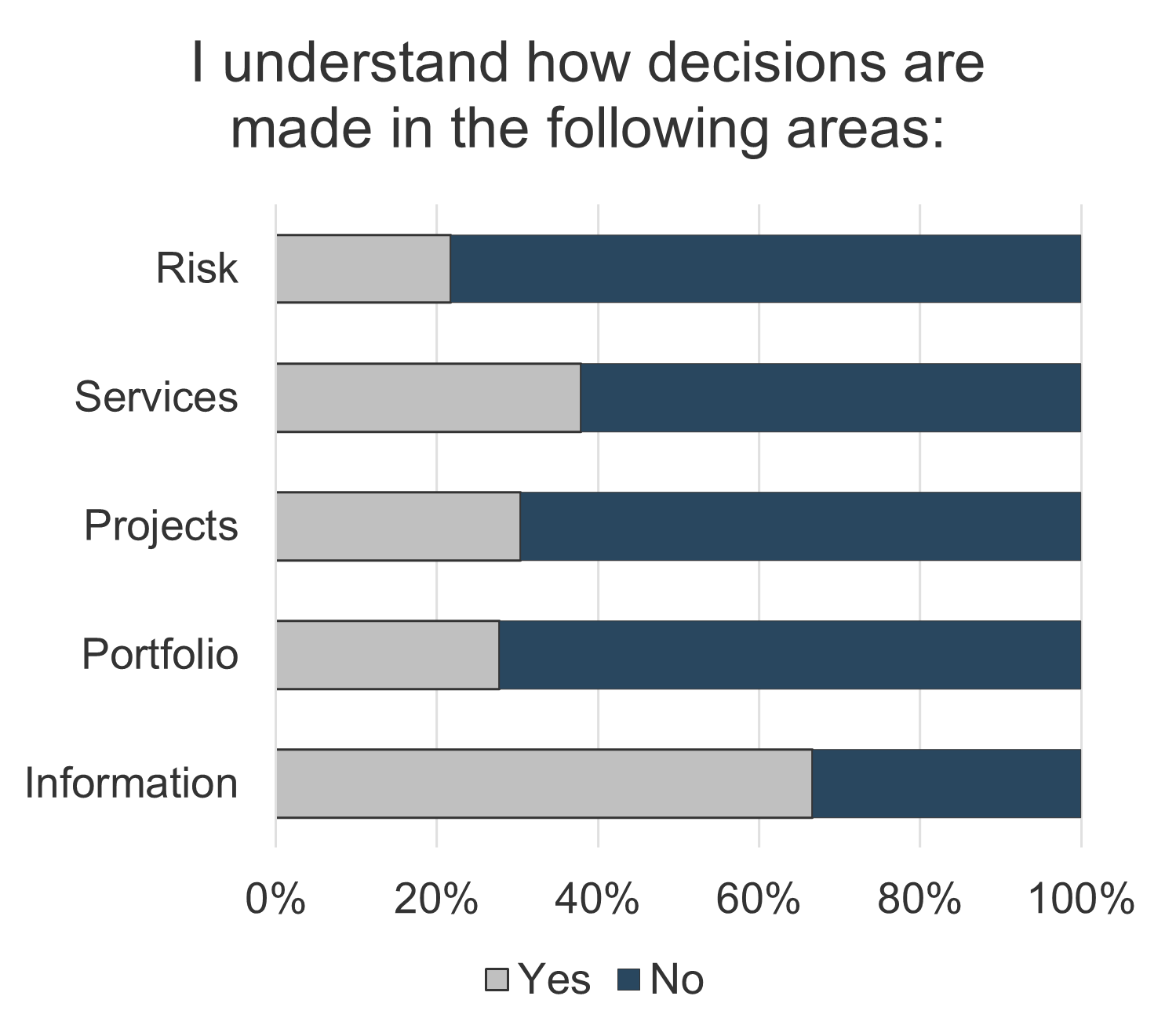





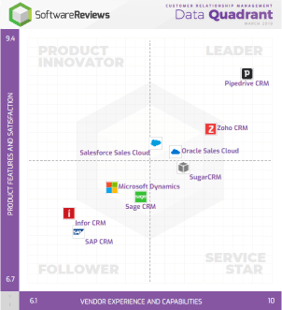
 New Results'.">
New Results'.">

























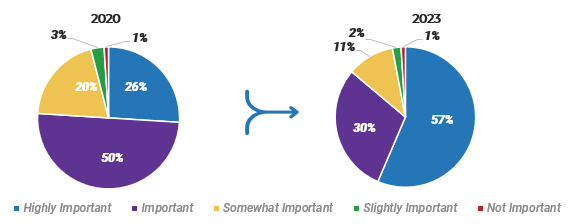
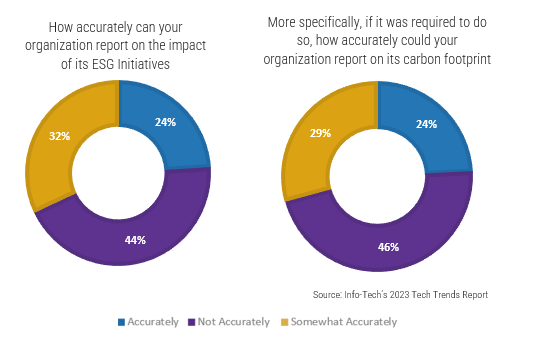
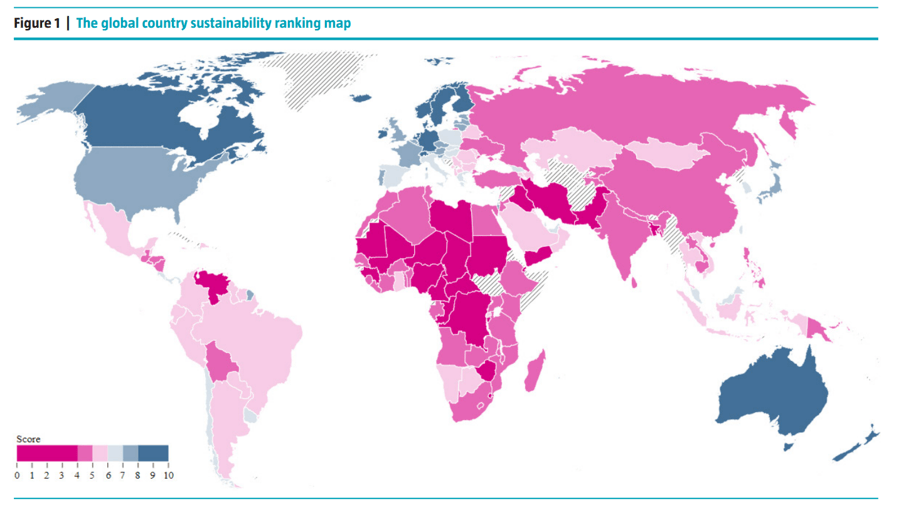
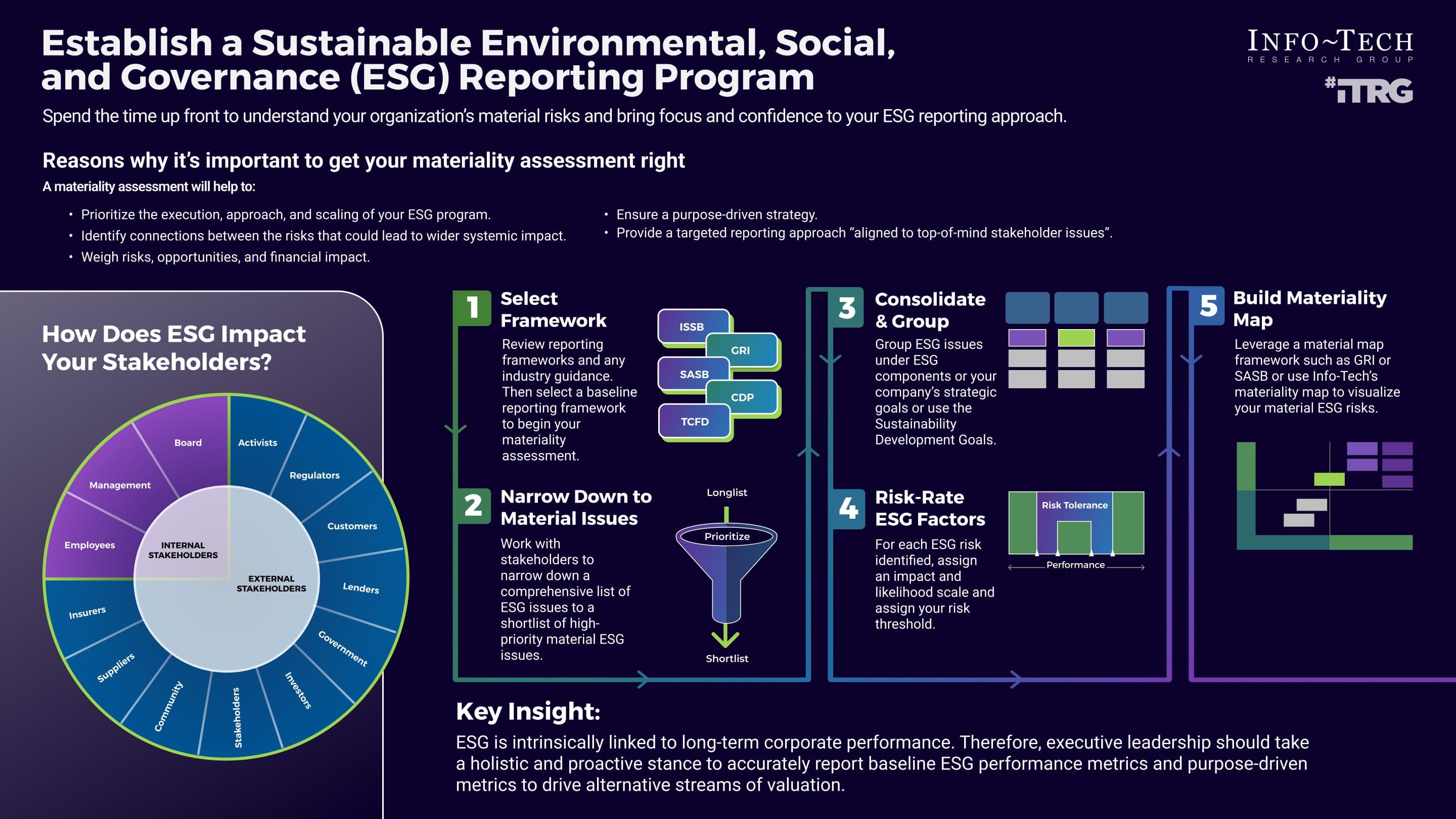


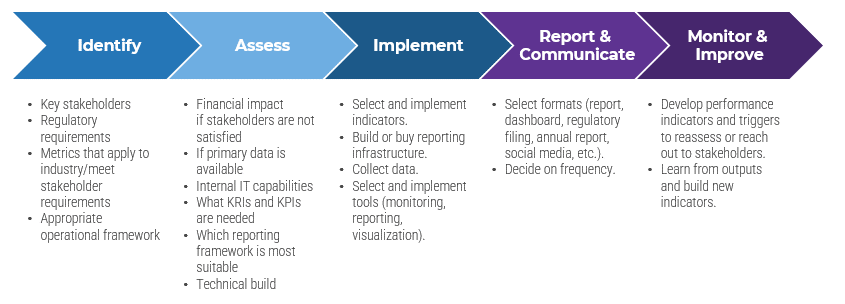
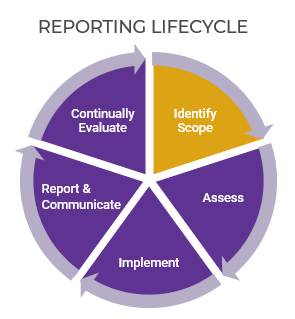
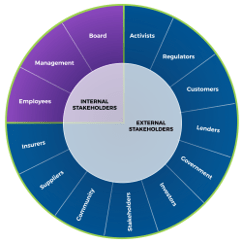
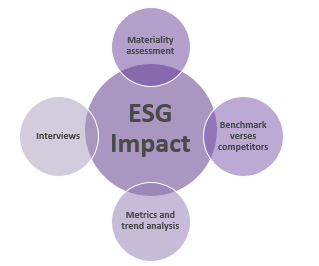





























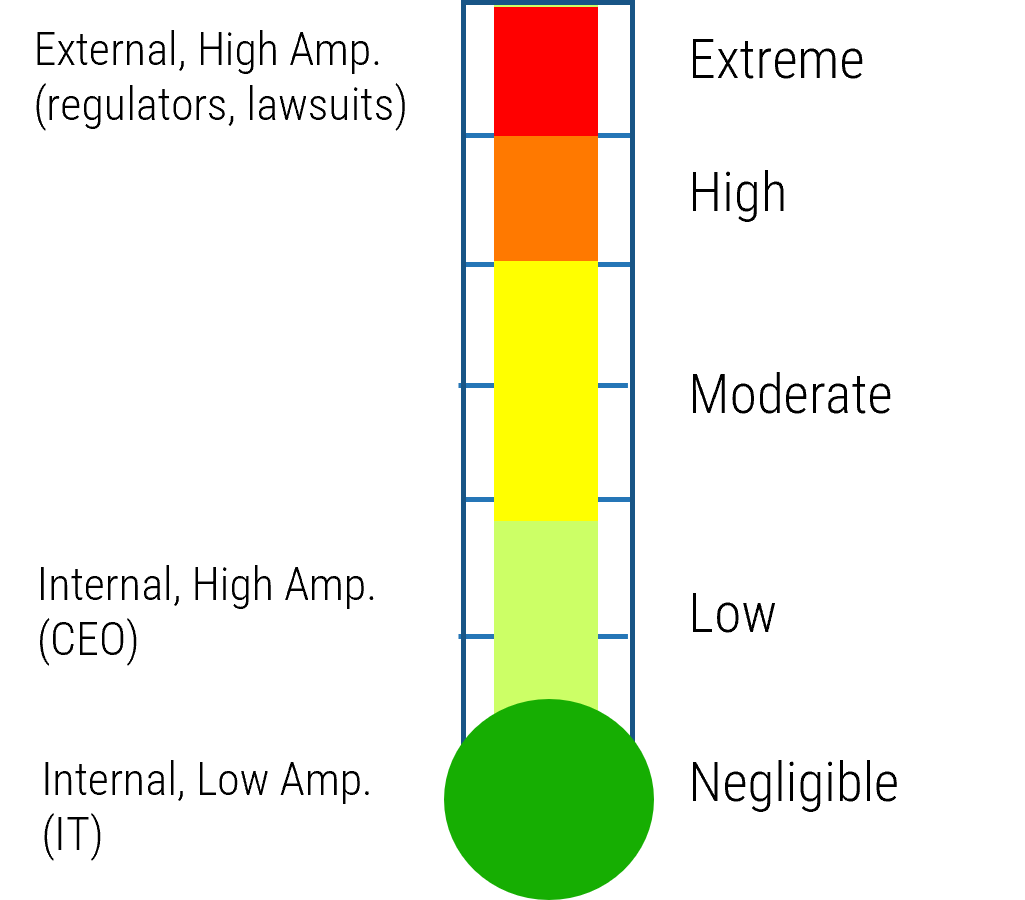
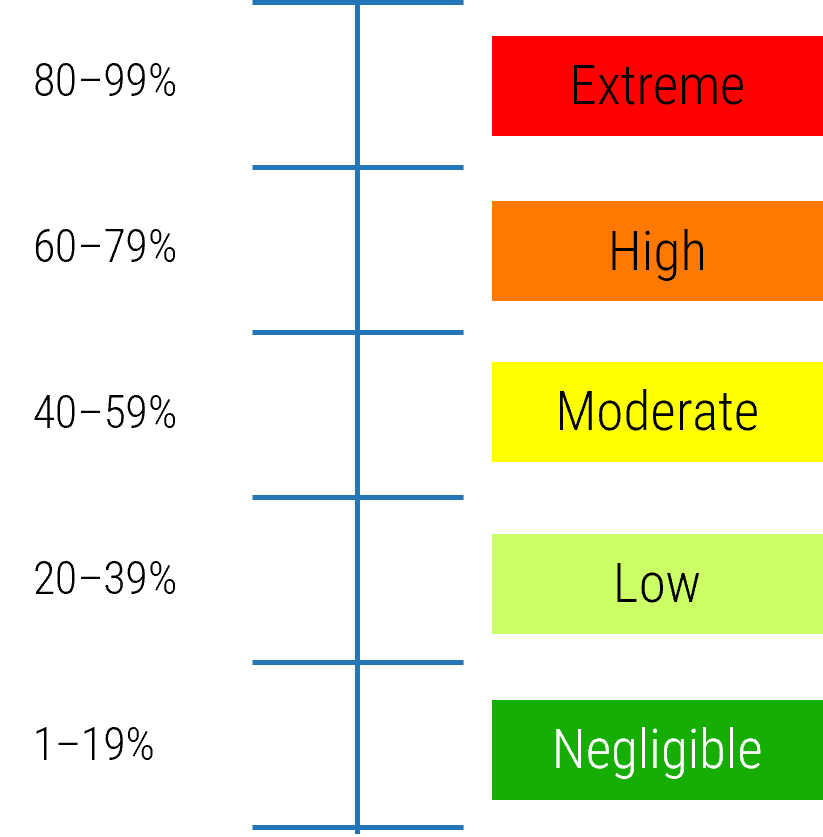
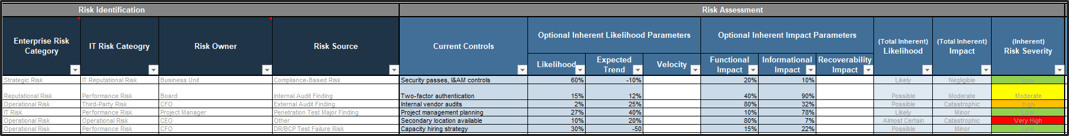
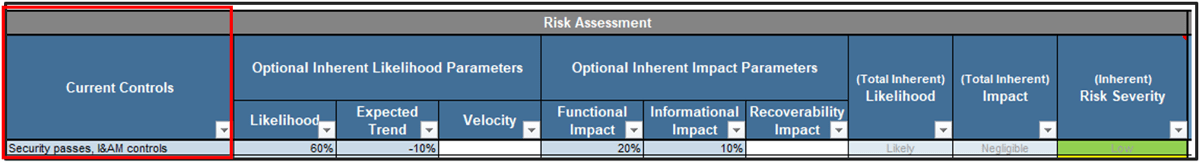

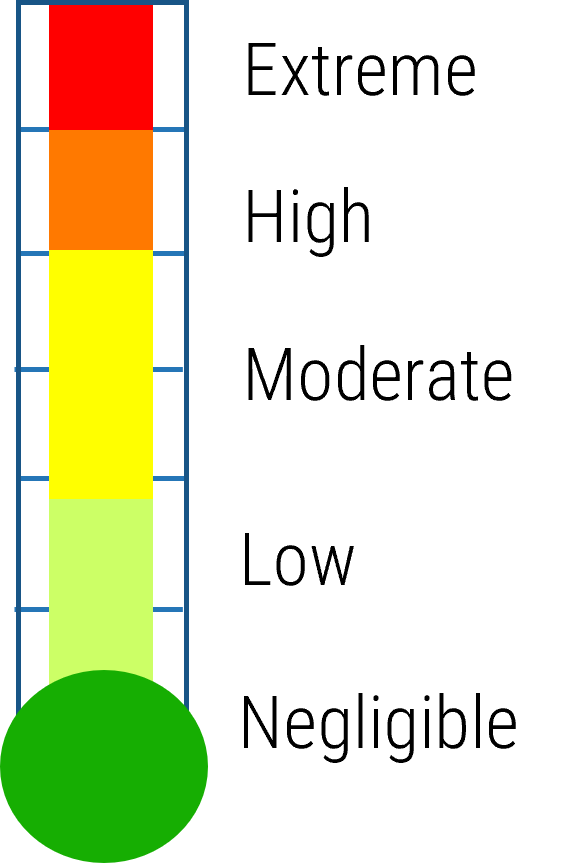
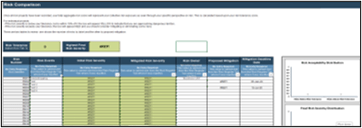
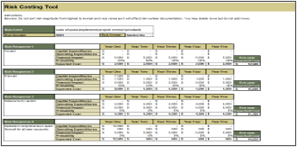
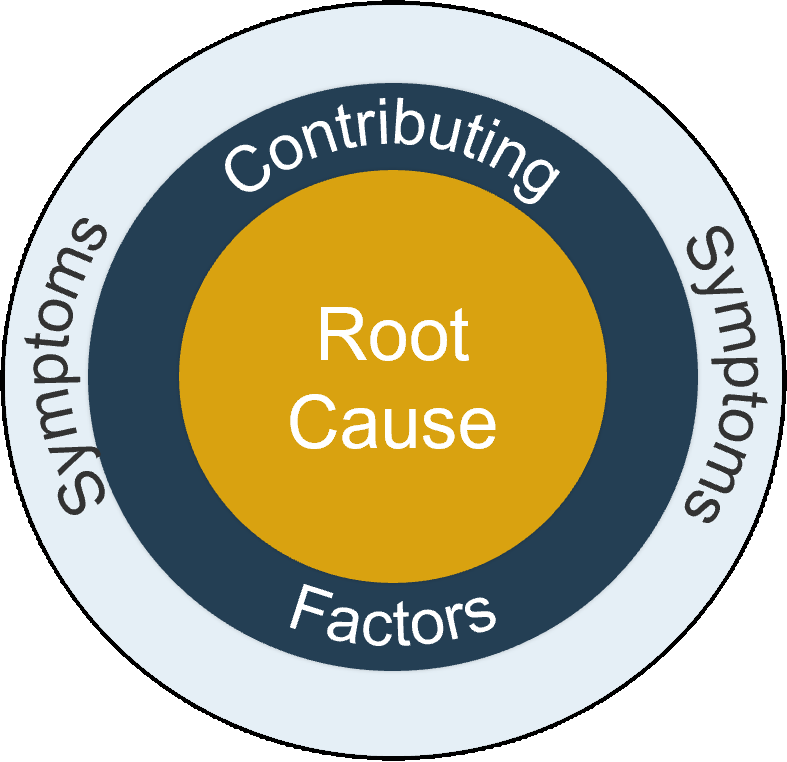









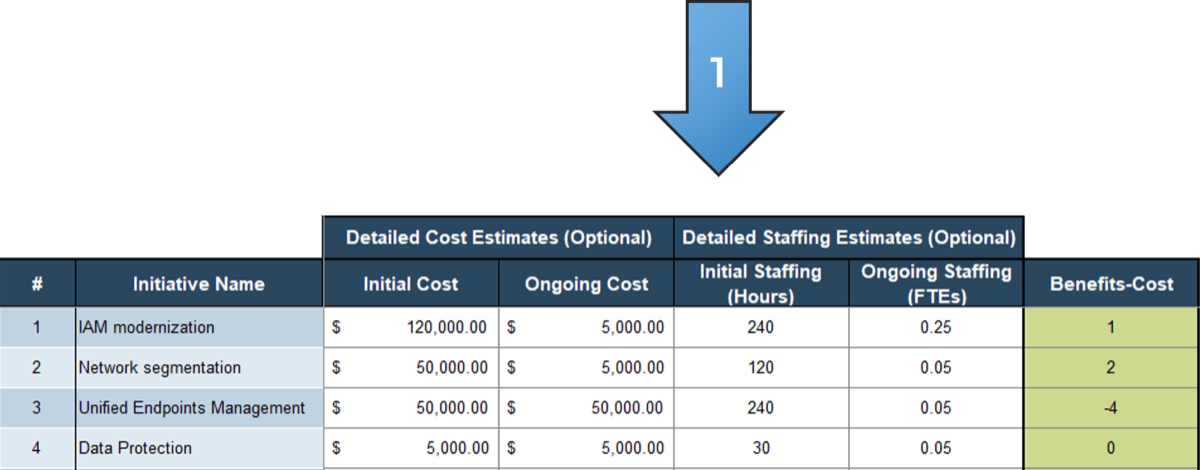
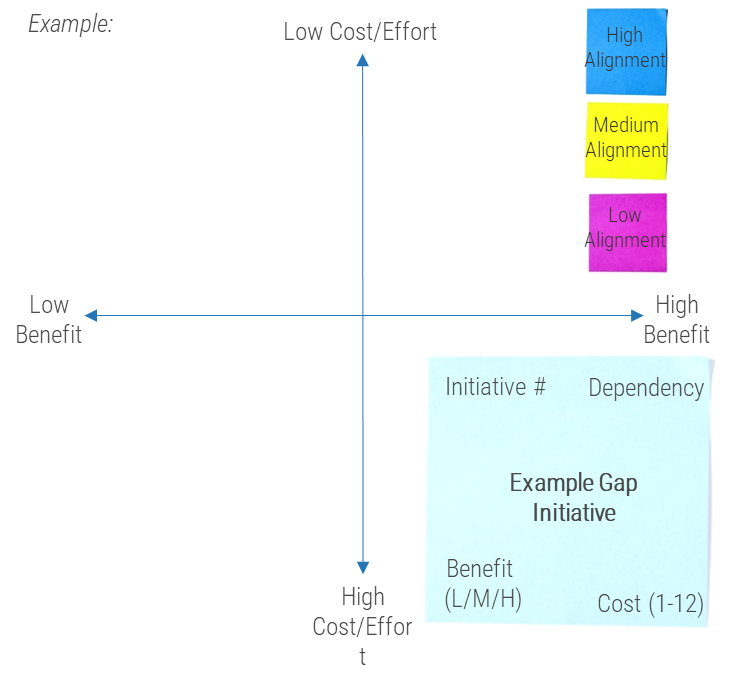
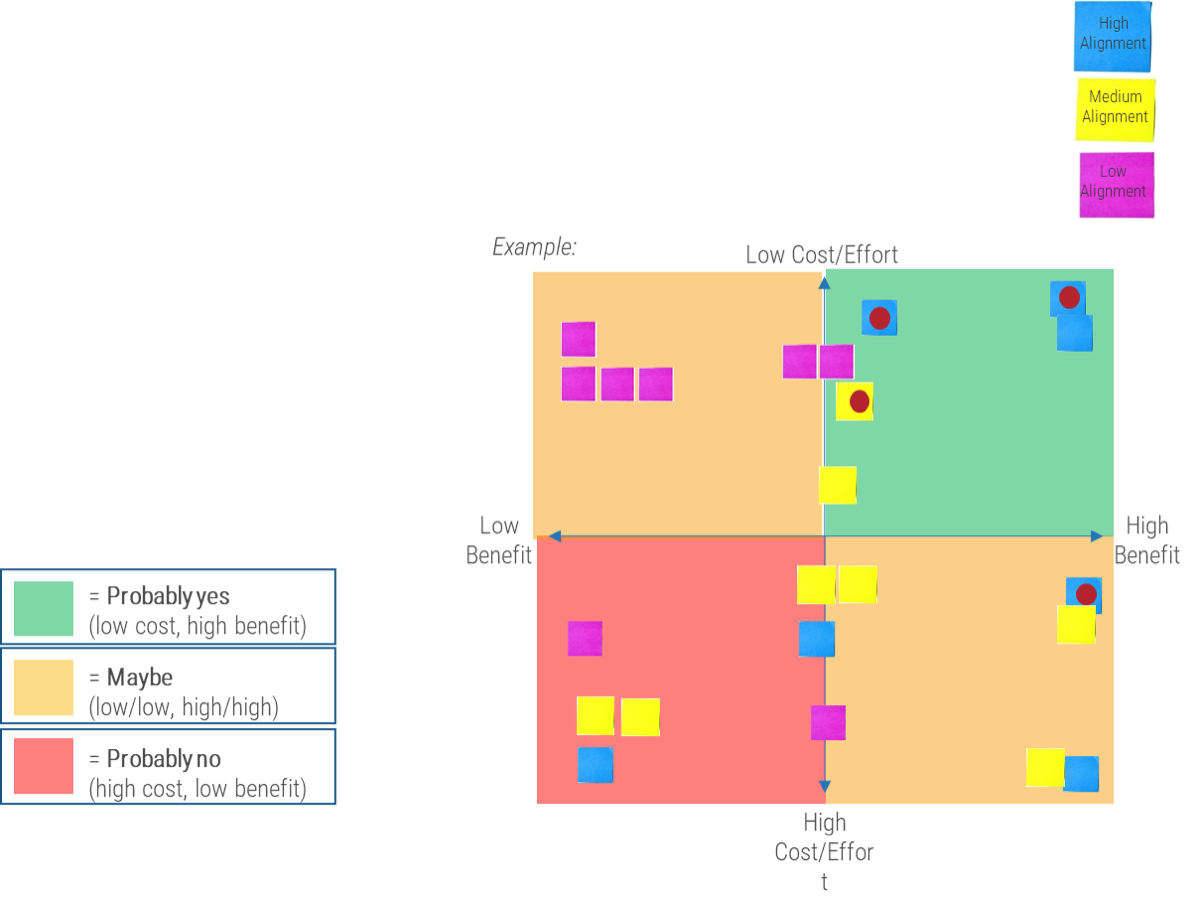
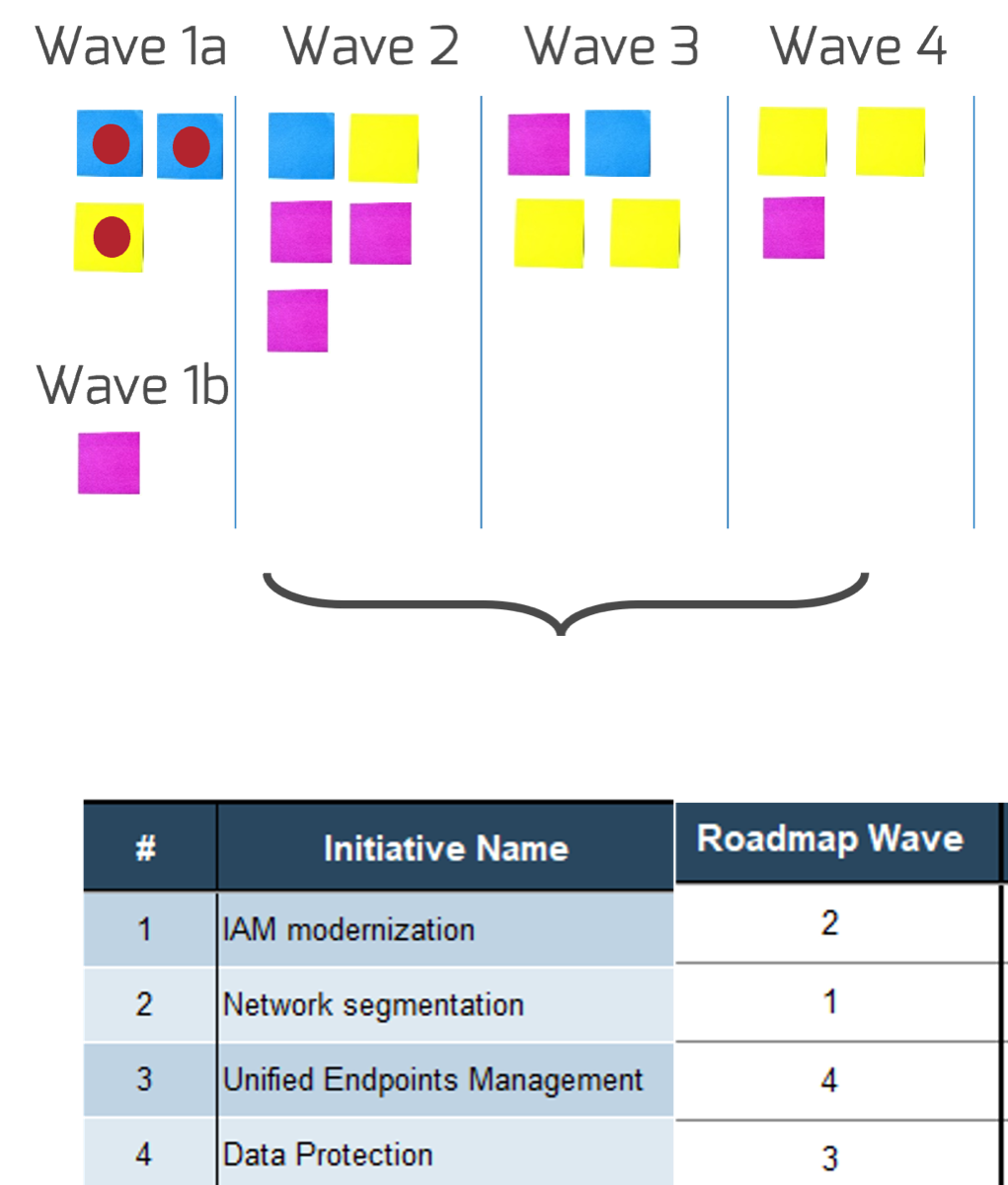
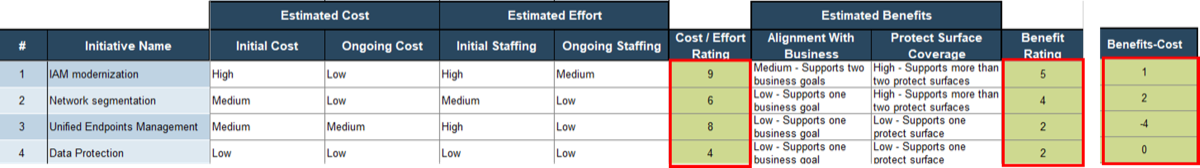
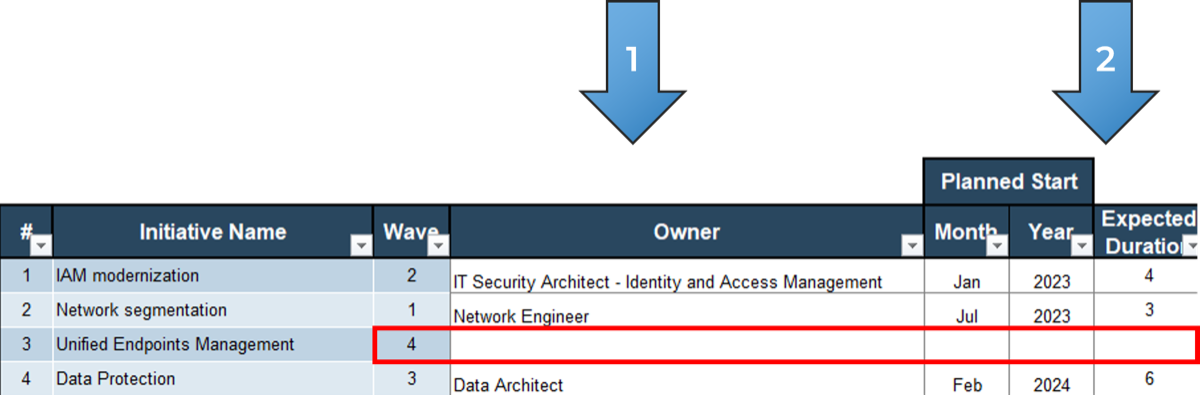
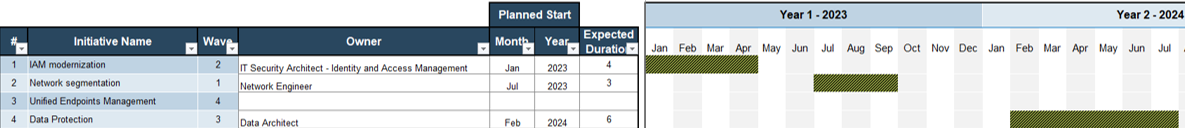
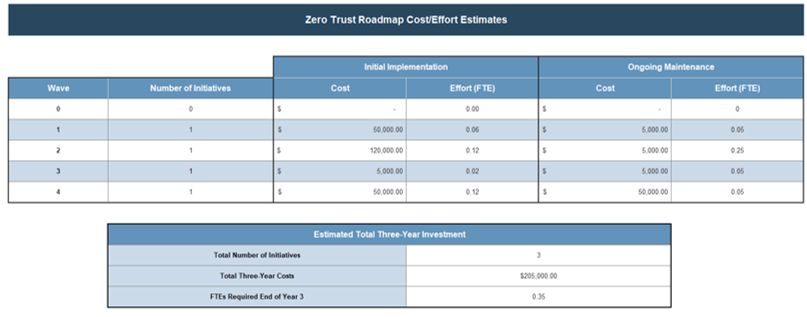










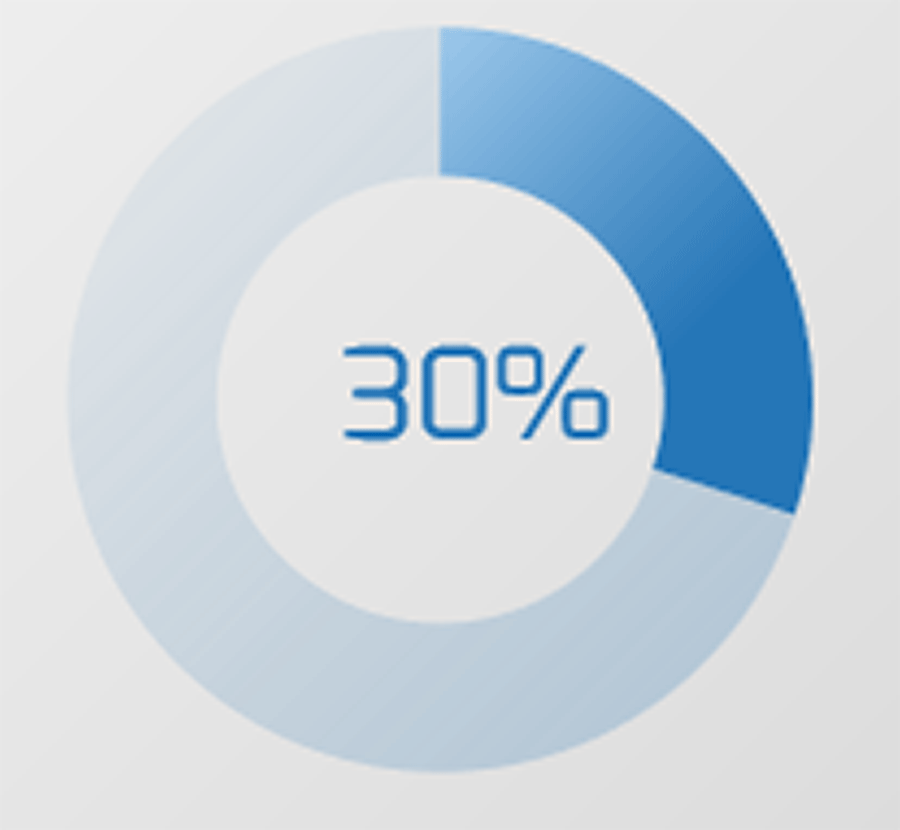
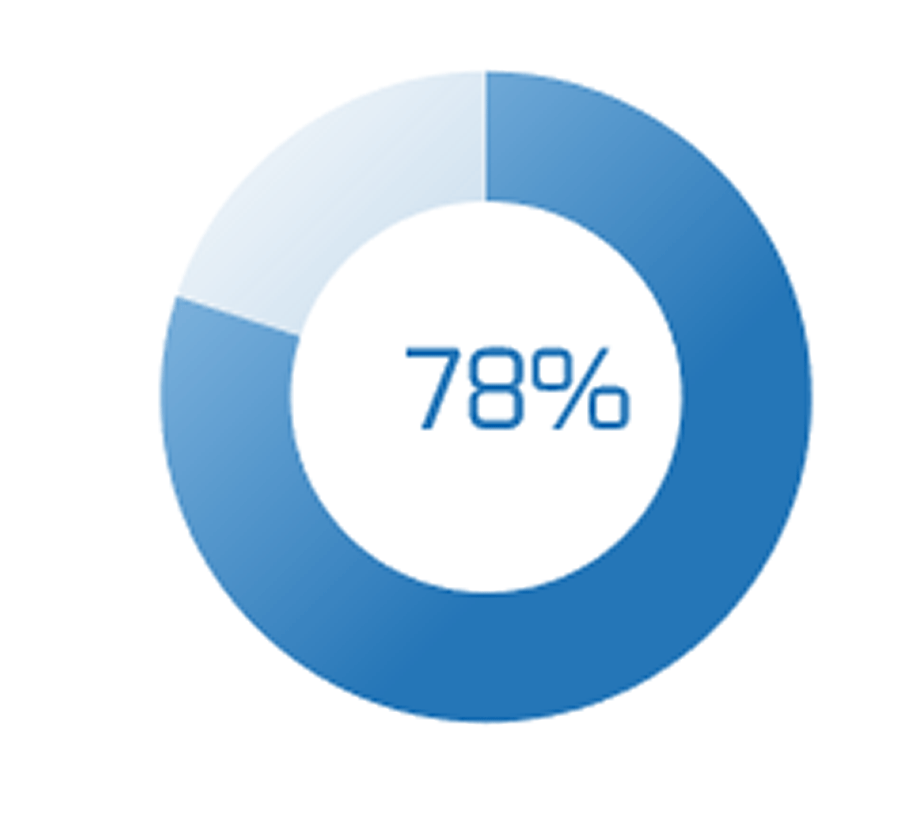
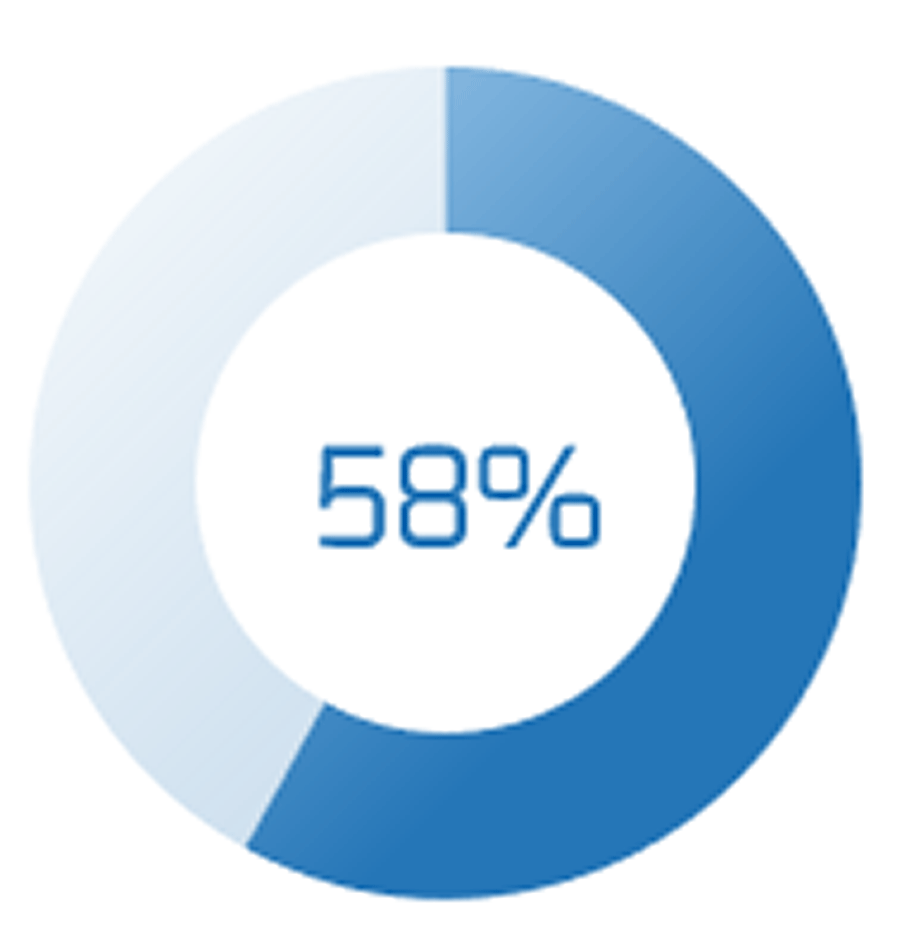













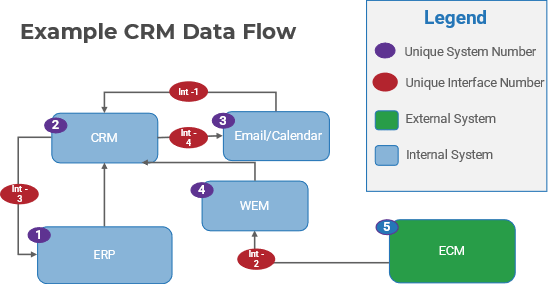
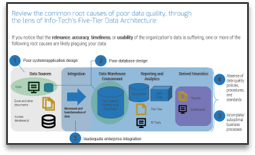
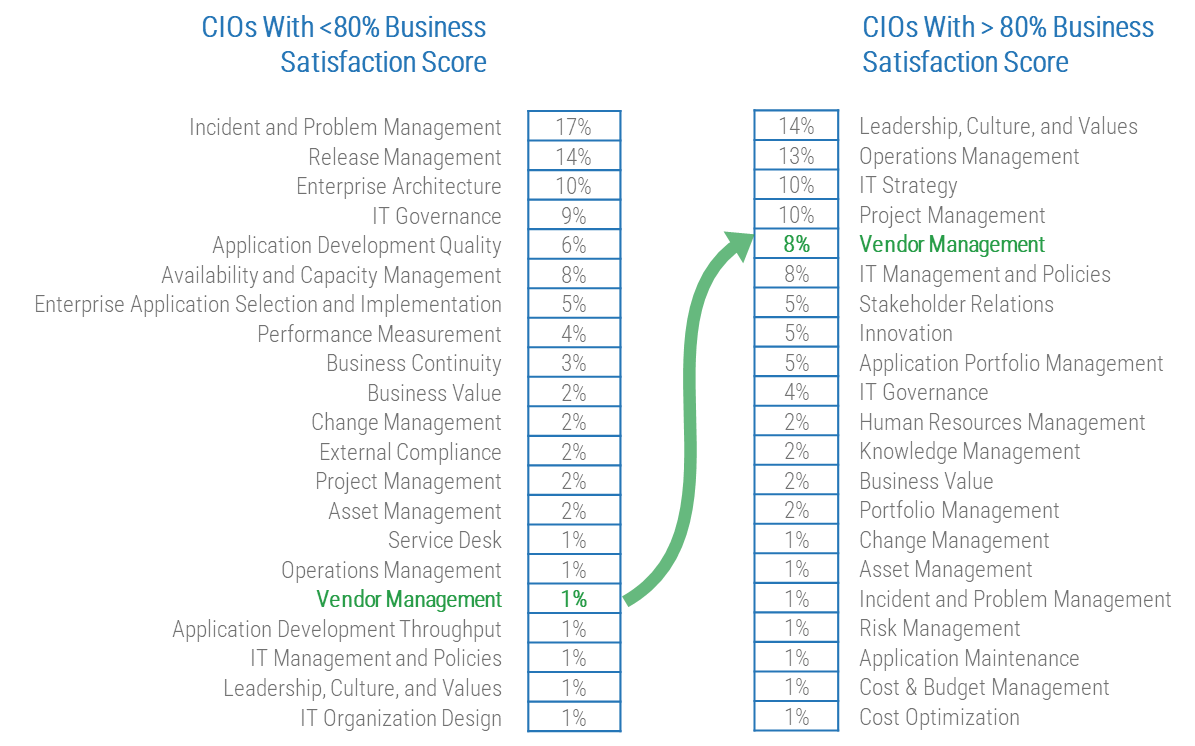 80% satisfaction score, and the other list is CIOs with <80% satisfaction score.">
80% satisfaction score, and the other list is CIOs with <80% satisfaction score.">